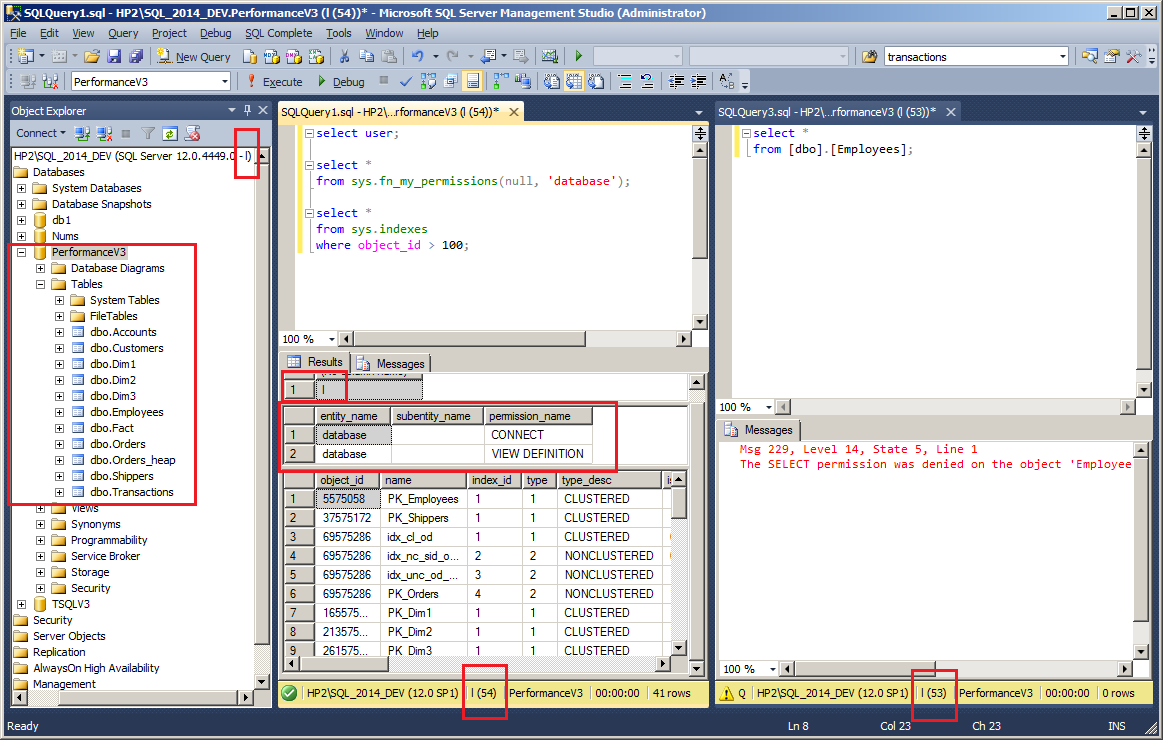
As the OP updated the question saying he's open to another code, and the login is already granted access to the database, I suggest to only grant VIEW DEFINITION permissiononly grant VIEW DEFINITION permission on database to the user in question and use sys.allocation_units to get out index sizes like this:
And here is the link to technet article describing VIEW DEFINITION Permission
The
VIEW DEFINITIONpermission lets a user see the metadata of the securable on which the permission is granted. However, VIEW DEFINITION permission does not confer access to the securable itself. For example, a user that is granted onlyVIEW DEFINITIONpermission on a table can see metadata related to the table in the sys.objects catalog view. However, without additional permissions such asSELECTorCONTROL, the user cannot read data from the table. For more information about viewing metadata, seeGRANT(Transact-SQL).
In our case we grant VIEW DEFINITION on a database, so the user granted has no access to data itself but to all the metadata:
Database Scope
VIEW DEFINITIONgranted at this scope effectively negates permissions-based metadata access for the grantee in the specified database. This means that the grantee can see all metadata in the database context in which the GRANT statement is executed, unless the grantee is deniedVIEW DEFINITIONorCONTROLpermissions at the schema scope or for an individual entity such as a table. For information about the syntax to use for this permission at this scope, seeGRANT(Transact-SQL).