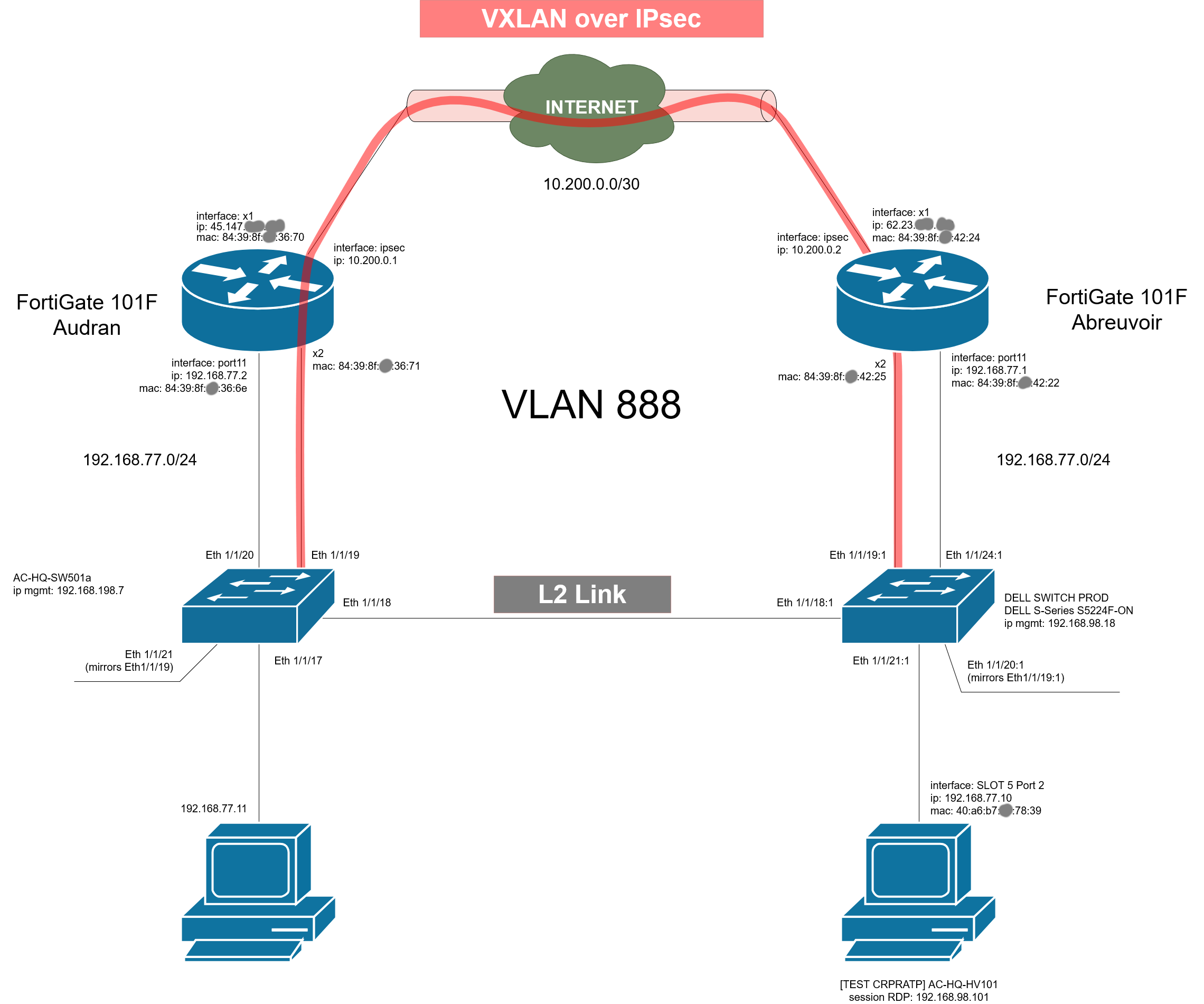
Is there any specific best practice when combining VXLAN over IPsec with such a Layer 2 setup?
Bluntly: Yes, there is a best practice: Do not do this.
Unless your are confident and you are prepared to jump over fences and through fire rings, and your are bold enough to extort compliance from the sysadmin and software people running the end systems and their applications.
Packet Size Problem:
Assuming the internet path will give you 1500bytes of IP payload size from Audran to Aubrevoir...
- IPSec will use up to 100 bytes of that for ESP and outer IP headers.
- VXLAN header will use up another 50bytes
- 20 bytes for an inner IP header,
- 8 bytes of UDP header,
- 8 bytes bytes VXLAN header (incl 24bit VXLAN ID). .
- 14 inner (original) Ethernet
This leaves - possibly - 1350 bytes of IP MTU through the VXLAN-over-IPsec tunnel.
Since this is a L2 construct, none of the devices along the paths (switches, vxlan encapsulating/decapsulating fortigates) can be expected to either "L2-fragment" packets or to signal to the end hosts that they should be using smaller L3 payload sizes. (Basically, there is no such thing as PMTUd at Layer 2 or fragmentation of ethernet frames. Then again, you never know what the Fortigate people come up with... )
You'll have to make sure that all participating systems on this VLAN/subnet are aware of the reduced maximum L3 packet size in all of VLAN 888, and are configured appropriately, including MTU settings of their network interfaces and possibly even data chunk size at the application layer.
And even then: Redundant paths at L2
You will still need to make sure that there is proper loop detection/prevention in the quadrilateral AC-HQ-SW501a - Fortigate(Audran) - VXLAN-o-IPSec - Fortigate(Abreuvoir) - DELL Switch - L2 Link. Be sure to thoroughly understand how switches and fortigates interact in this.
Also: be aware of the consequences of a failure of "L2 Link" and traffic flows within VLAN 888. Can the fortigates and their internet links take the load? How will the end systems in VLAN 888 deal with a network path that just changed characteristics abruptly (Latency, Jitter, Loss) ?
If management wants to force this upon you, have them sign a waiver absolving you from any consequences, for an element of questional stability they make you introduce to VLAN 888 and possibly the entire network.
Suggestion:
Review and question deeply and thoroughly (applicaton of spanish inquisition practices optional) the true and actual need for end systems 192.168.77.11 and 192.168.77.10 to be in the same broadcast domain.
More often than not, a requirement like this is "just given", but the people requiring it could just not be bothered (or their product resp IP stack is so broken or so outdated it cannot route). In that case: see waiver-from-management, above.
For the classic case of hard-coded or licence-bound IP addresses in the applications, there's better tricks which give you the freedom and stability of routing. For example: Add the hard-coded IP addresses to the host as 2ndary IP or loopback with /32, bind server/listener and client to said 2ndary IP, and eventually add & redistribute static routes on the network accordingly ... but that's already touching the limits of on-topic-ness of this board.