I'm trying to figure out the password that is used to access the U-Boot shell, as mentoined in my previous question.
I'm having trouble understanding how exactly the code works. Here is an image of the code from IDA. The part in the yellow box (loc_8080FF28) is what I don't understand. What is it doing to the user input? Also I would like to understand what the subroutine in the orange box (sub_8081ECE4) does with the user input. I have added a few comments that I thought are relevant. 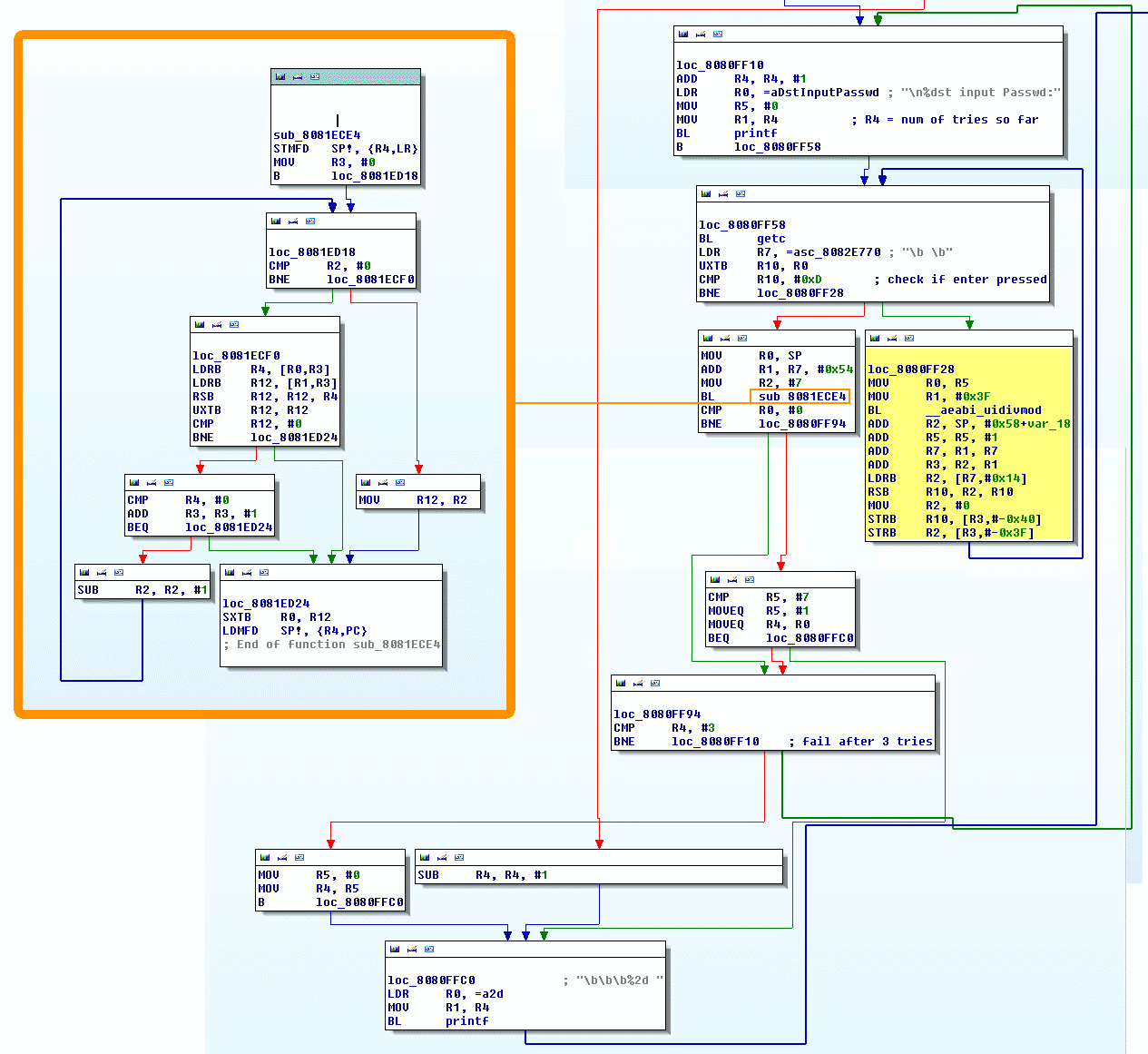
Here is the code in text form:
loc_8080FF10 ADD R4, R4, #1 LDR R0, =aDstInputPasswd ; "\n%dst input Passwd:" MOV R5, #0 MOV R1, R4 ; R4 = num of tries so far BL printf B loc_8080FF58 loc_8080FF28 MOV R0, R5 MOV R1, #0x3F BL __aeabi_uidivmod ADD R2, SP, #0x58+var_18 ADD R5, R5, #1 ADD R7, R1, R7 ADD R3, R2, R1 LDRB R2, [R7,#0x14] RSB R10, R2, R10 MOV R2, #0 STRB R10, [R3,#-0x40] STRB R2, [R3,#-0x3F] loc_8080FF58 BL getc LDR R7, =asc_8082E770 ; "\b \b" UXTB R10, R0 CMP R10, #0xD ; check if enter pressed BNE loc_8080FF28 MOV R0, SP ADD R1, R7, #0x54 MOV R2, #7 BL sub_8081ECE4 CMP R0, #0 BNE loc_8080FF94 CMP R5, #7 MOVEQ R5, #1 MOVEQ R4, R0 BEQ loc_8080FFC0 loc_8080FF94 CMP R4, #3 BNE loc_8080FF10 ; fail after 3 tries MOV R5, #0 MOV R4, R5 B loc_8080FFC0 loc_8080FFA8 MOV R0, #0x2710 ADD R7, R7, #1 BL sub_8081F1D8 CMP R7, #0x64 BNE loc_8080FEEC SUB R4, R4, #1 loc_8080FFC0 ; "\b\b\b%2d " LDR R0, =a2d MOV R1, R4 BL printf ; end of check passwd sub_8081ECE4 STMFD SP!, {R4,LR} MOV R3, #0 B loc_8081ED18 loc_8081ECF0 LDRB R4, [R0,R3] LDRB R12, [R1,R3] RSB R12, R12, R4 UXTB R12, R12 CMP R12, #0 BNE loc_8081ED24 CMP R4, #0 ADD R3, R3, #1 BEQ loc_8081ED24 SUB R2, R2, #1 loc_8081ED18 CMP R2, #0 BNE loc_8081ECF0 MOV R12, R2 loc_8081ED24 SXTB R0, R12 LDMFD SP!, {R4,PC} ; End of function sub_8081ECE4