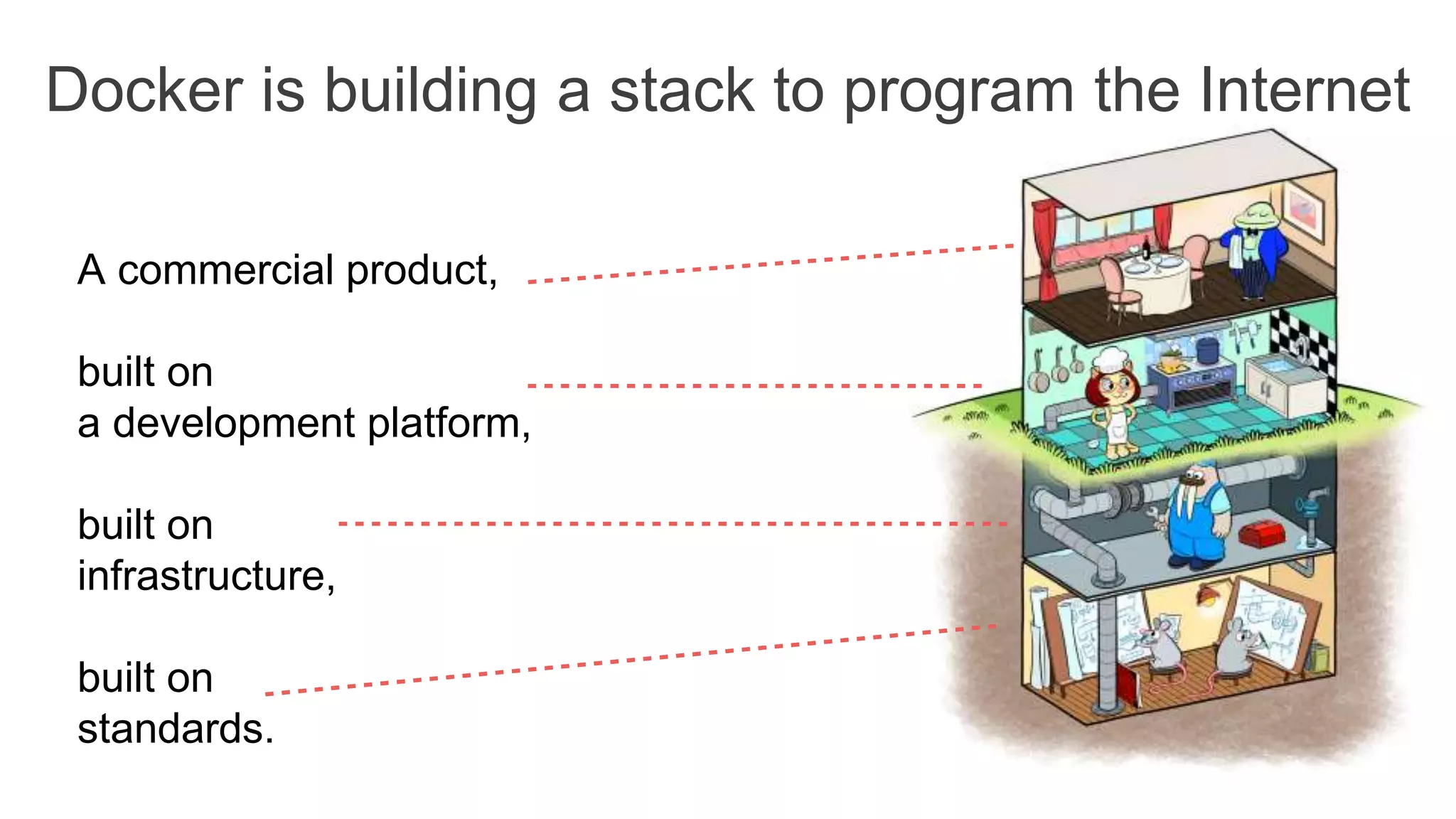
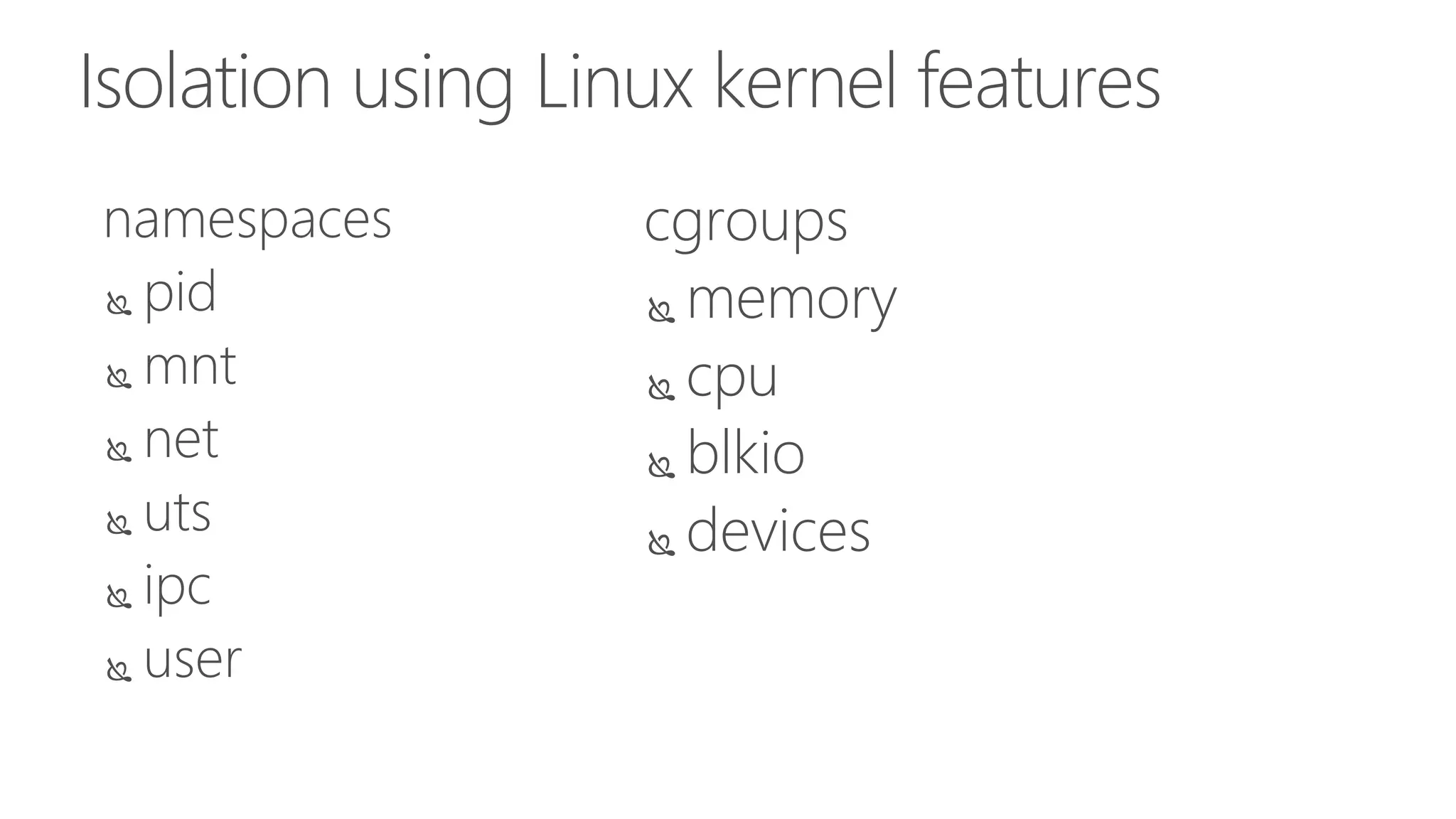
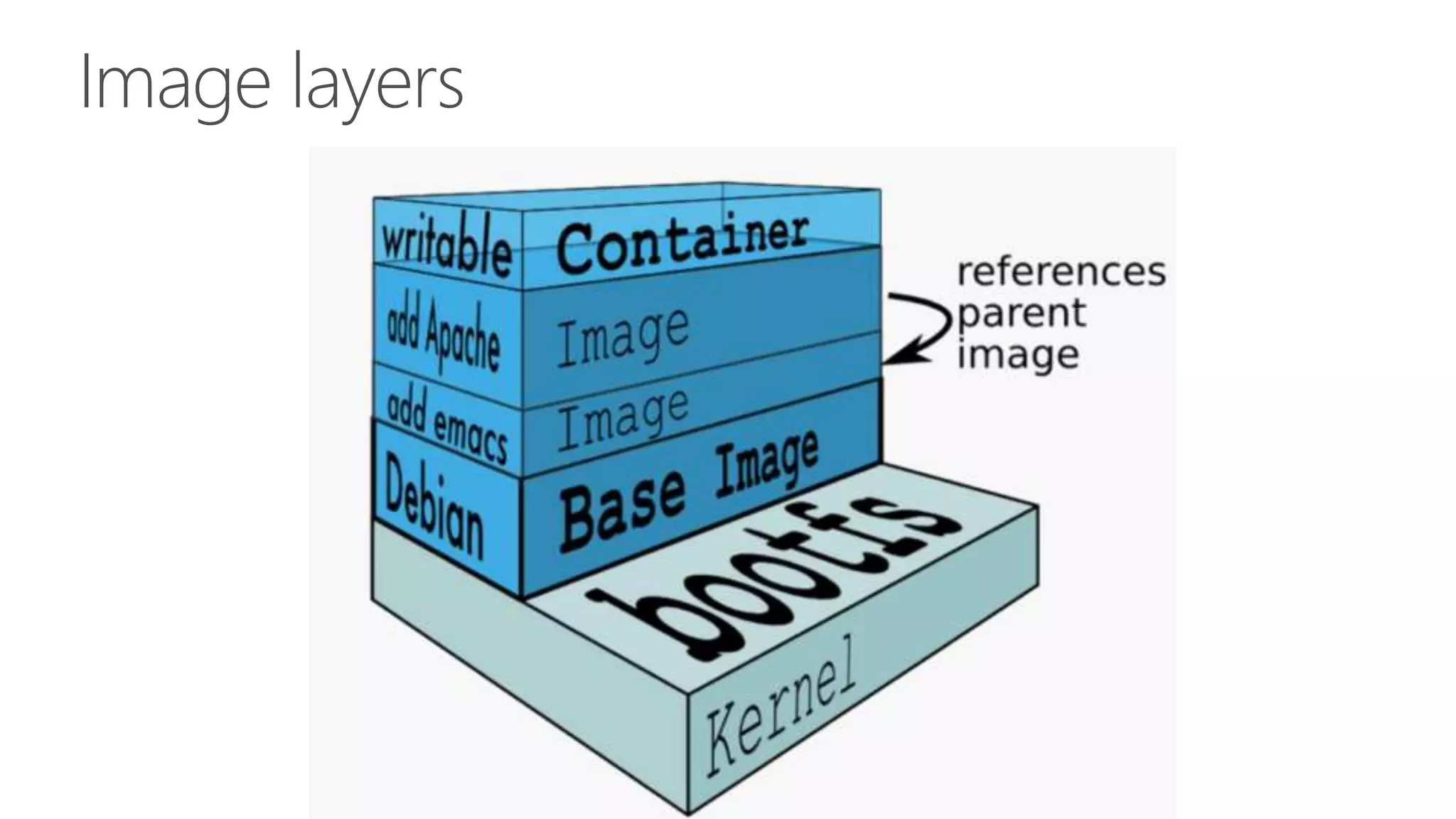
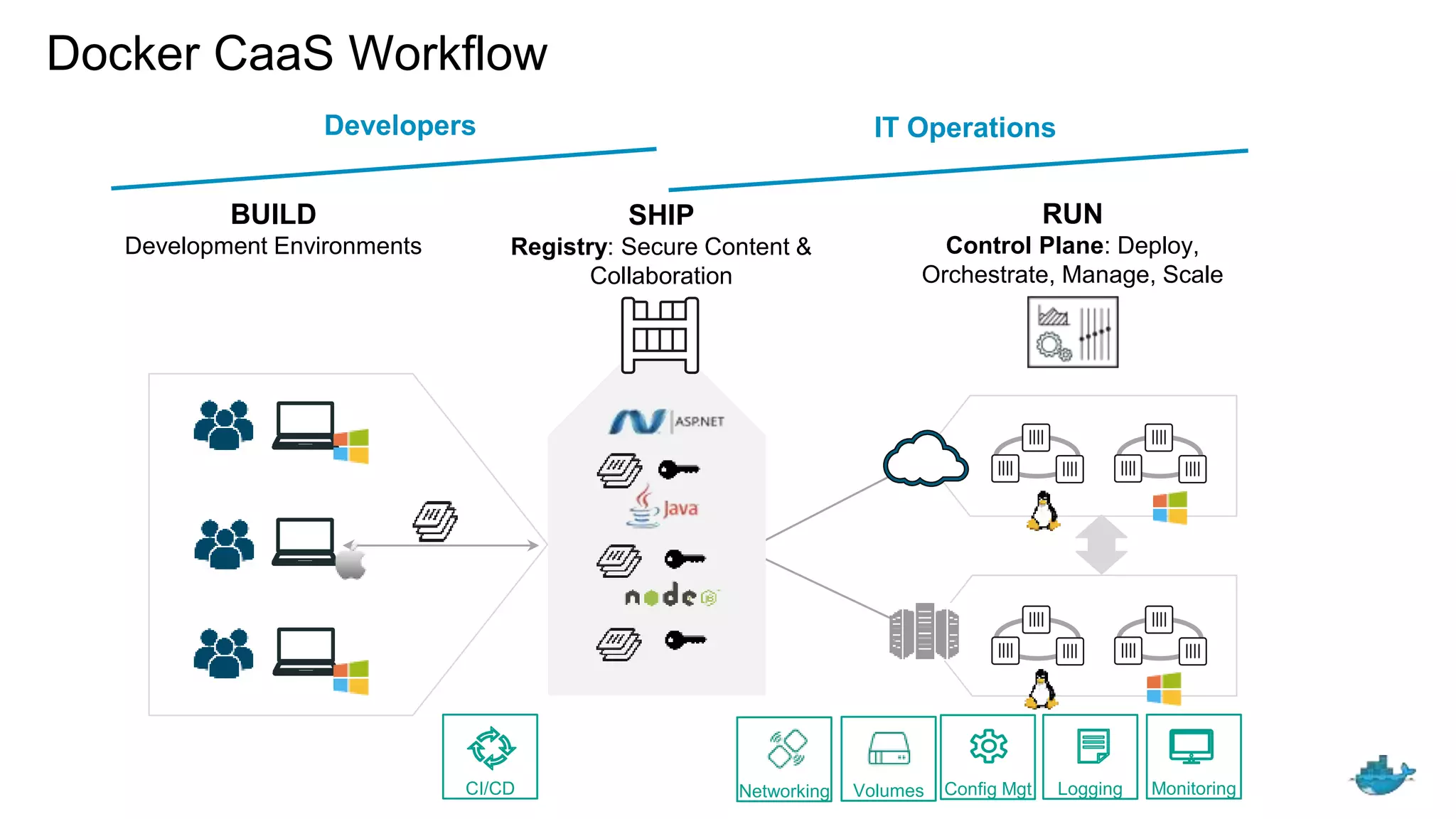
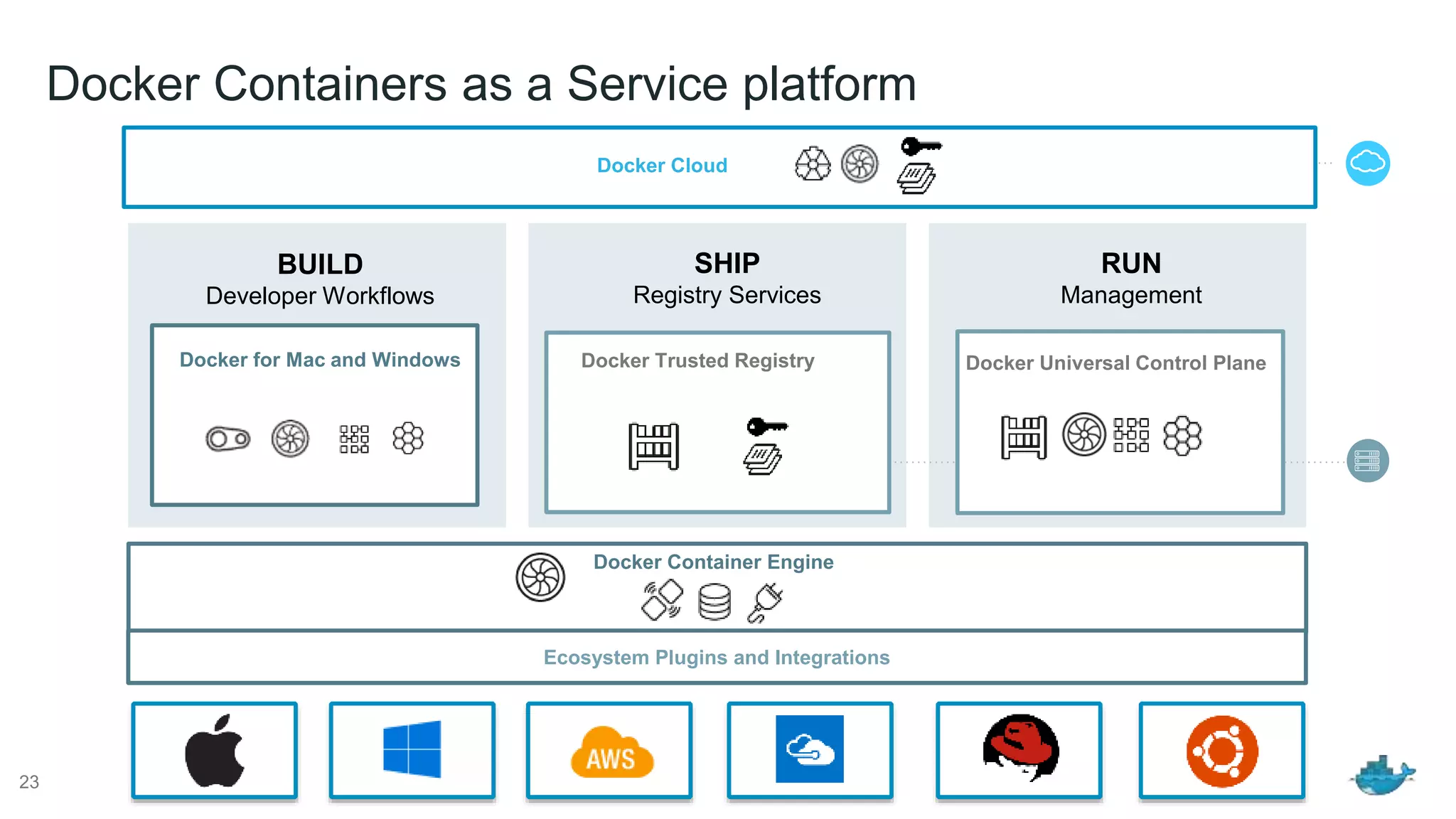
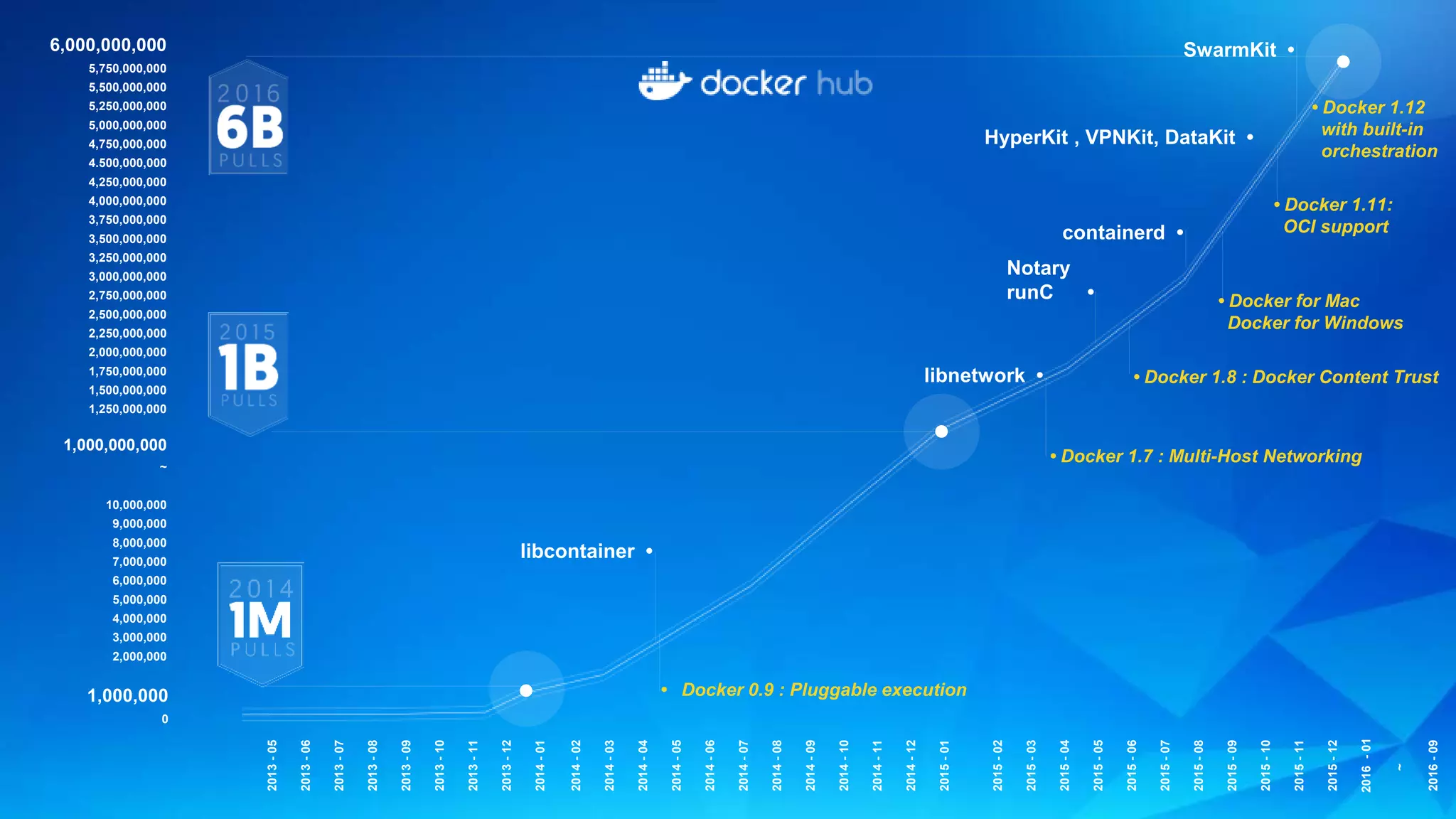
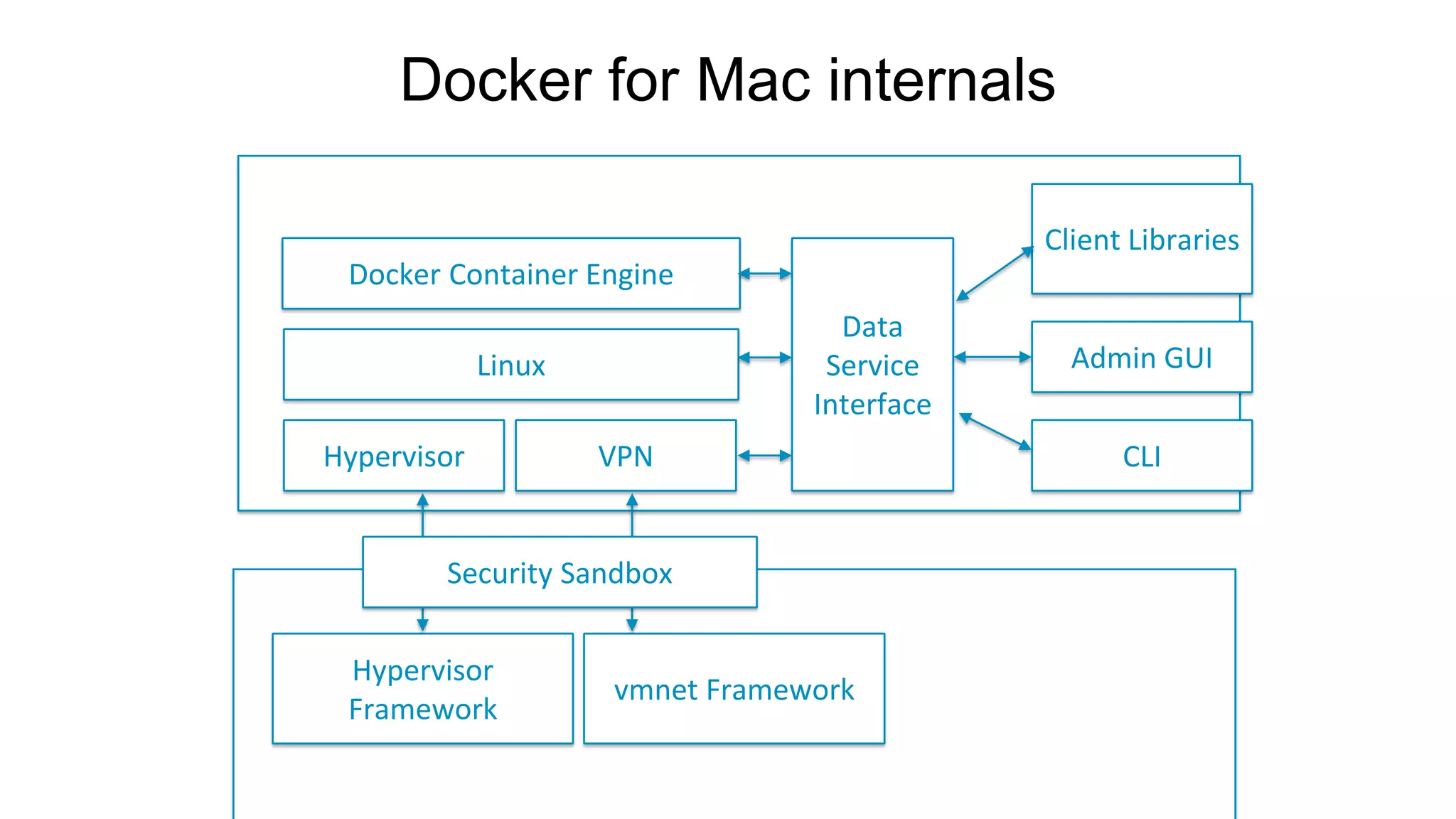
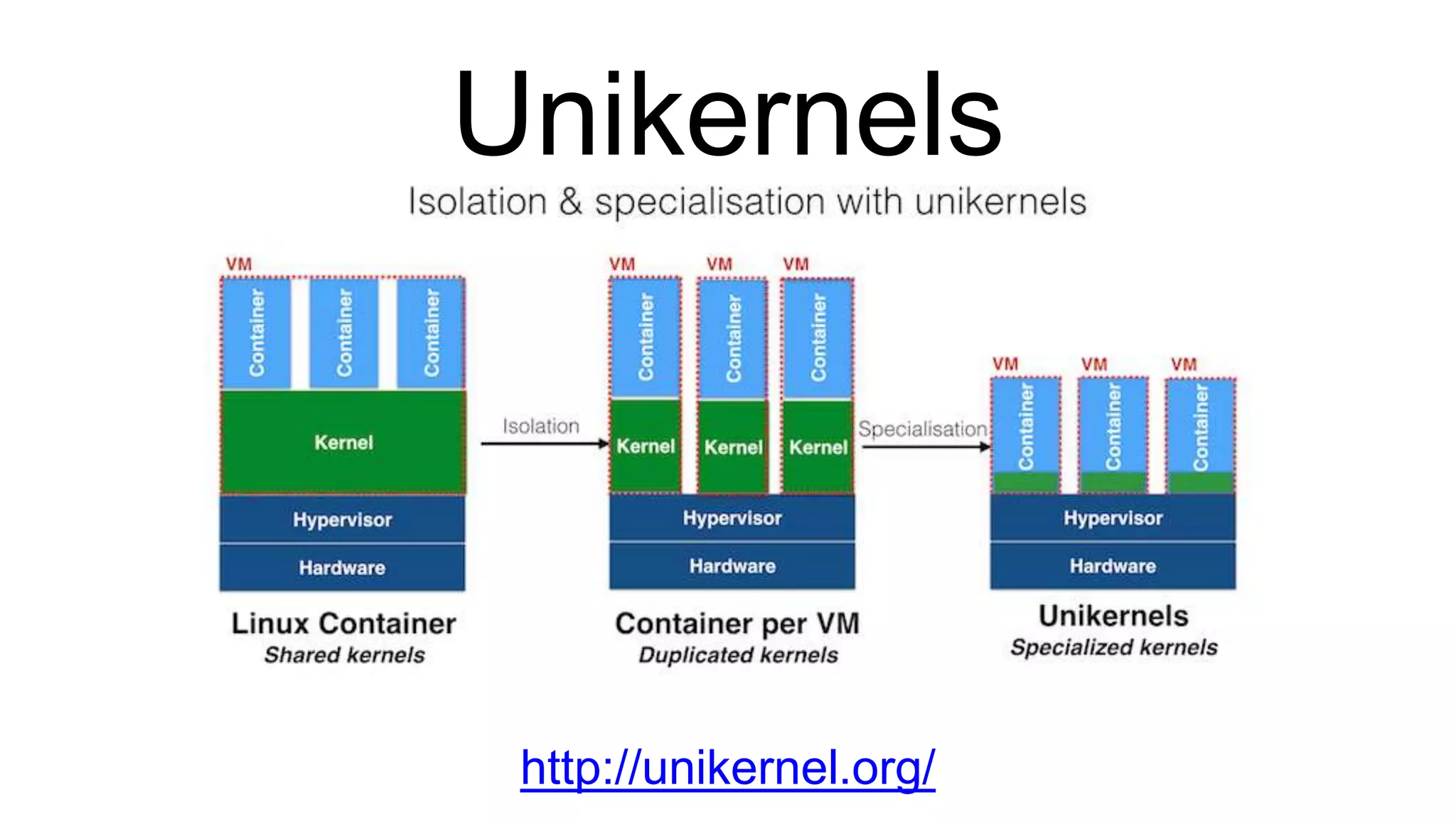
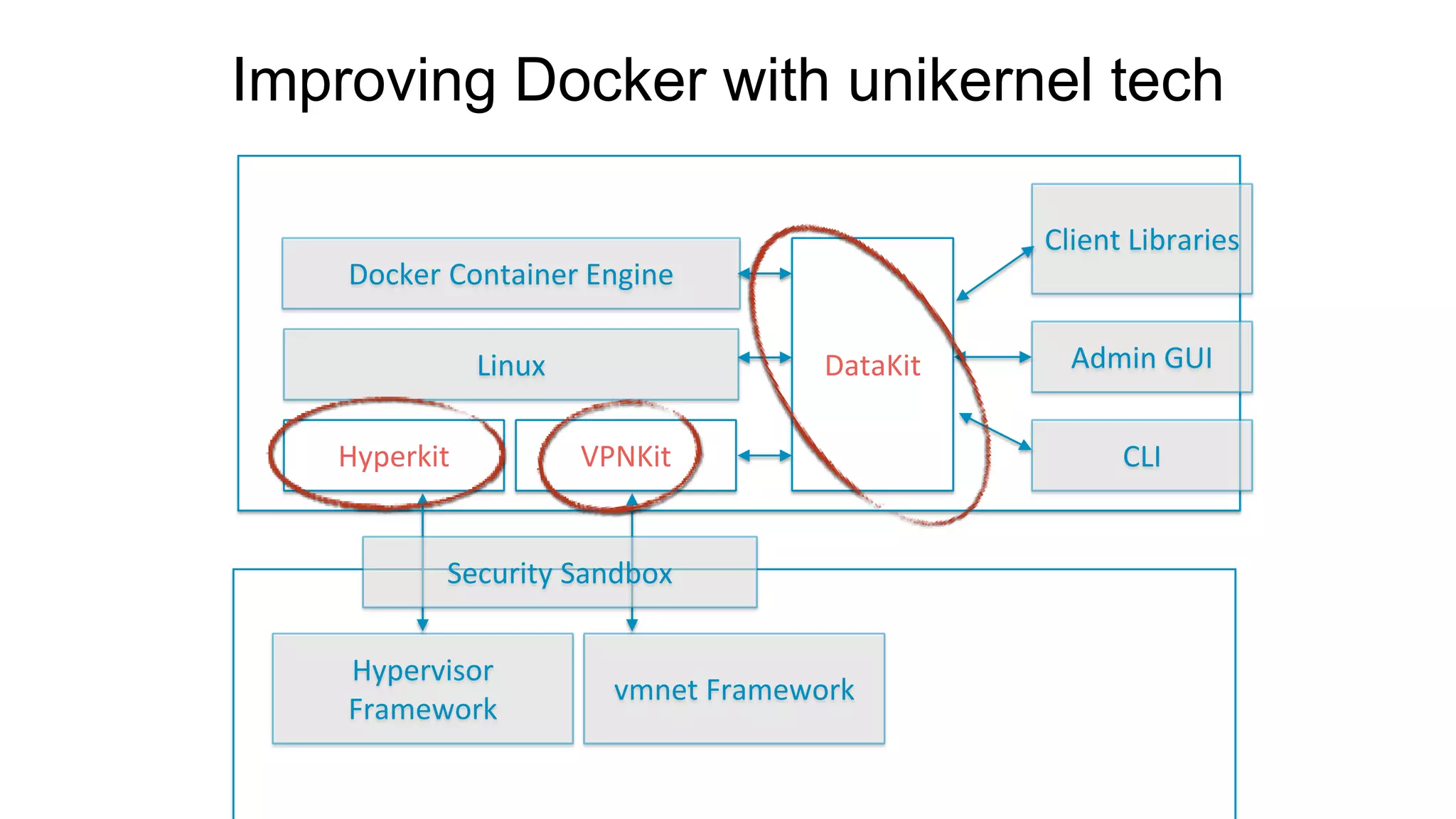
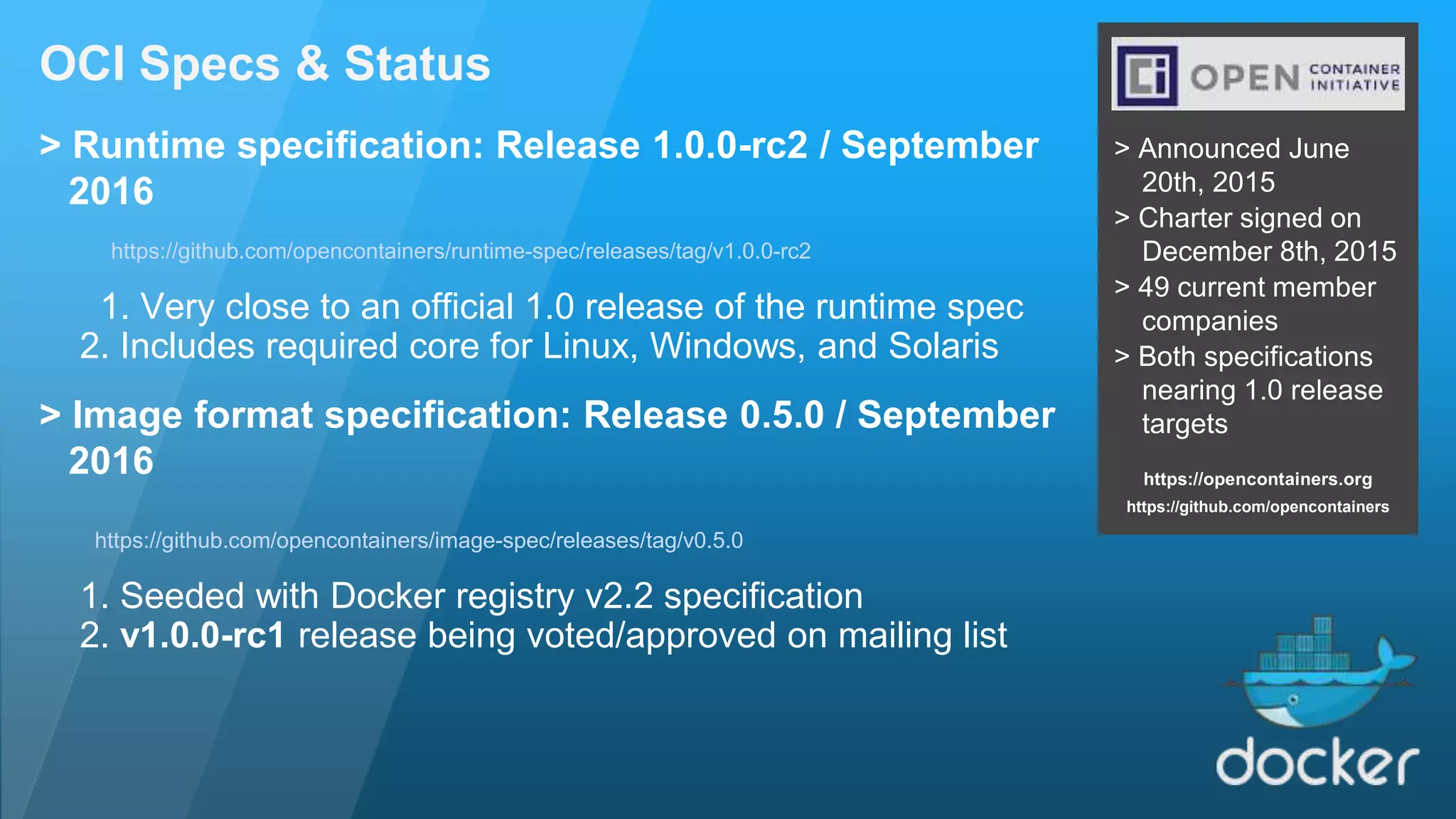
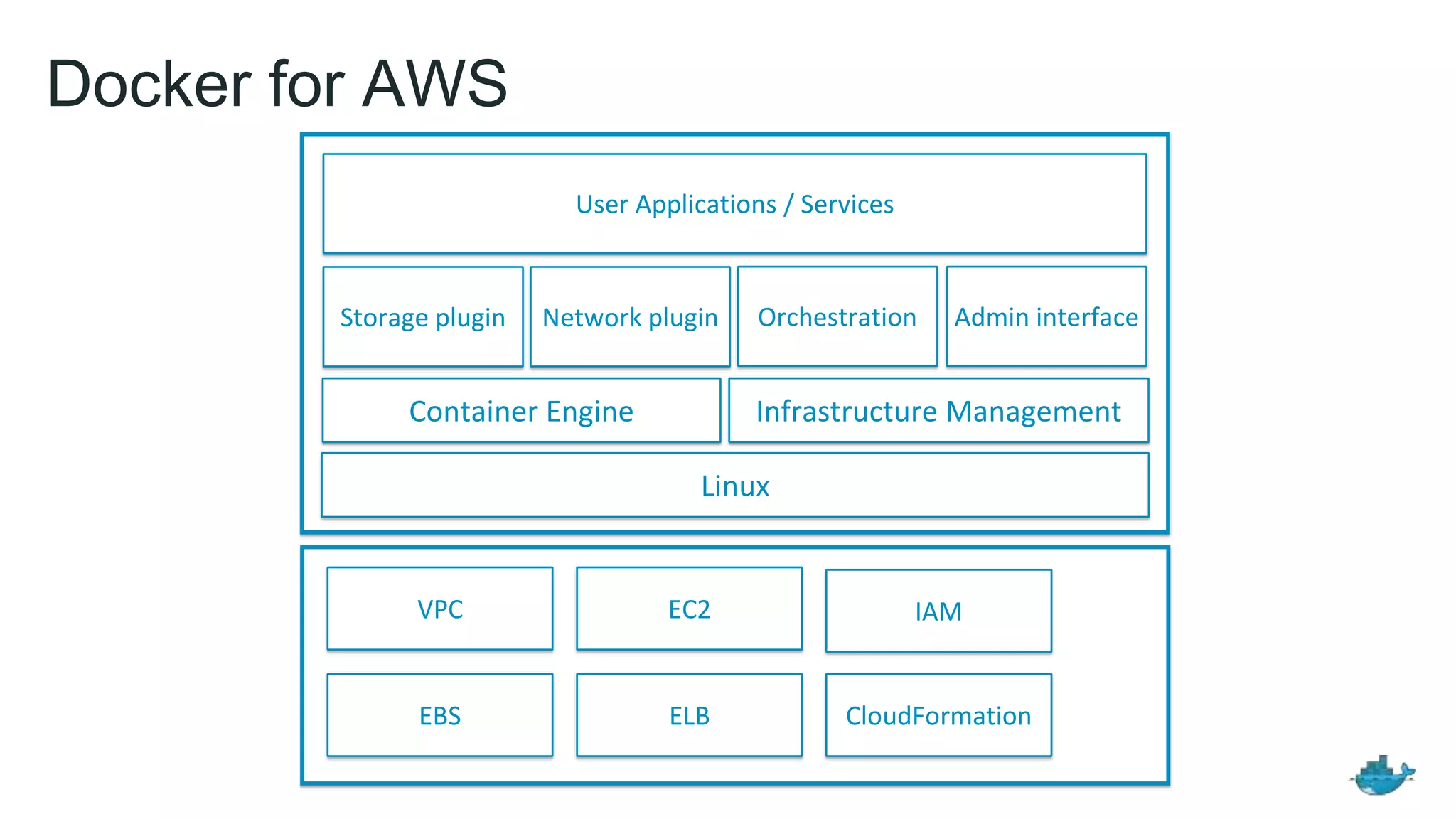
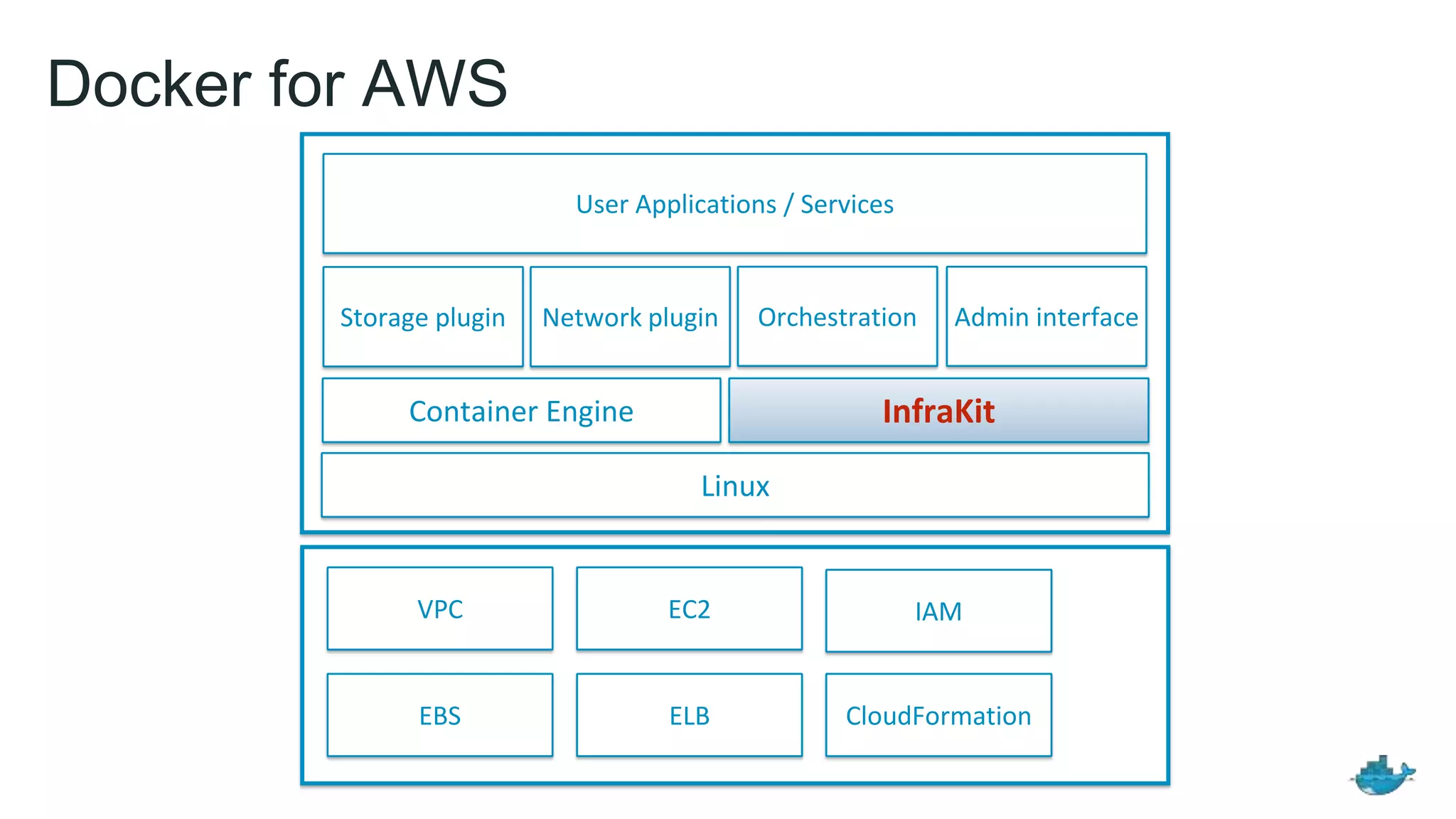
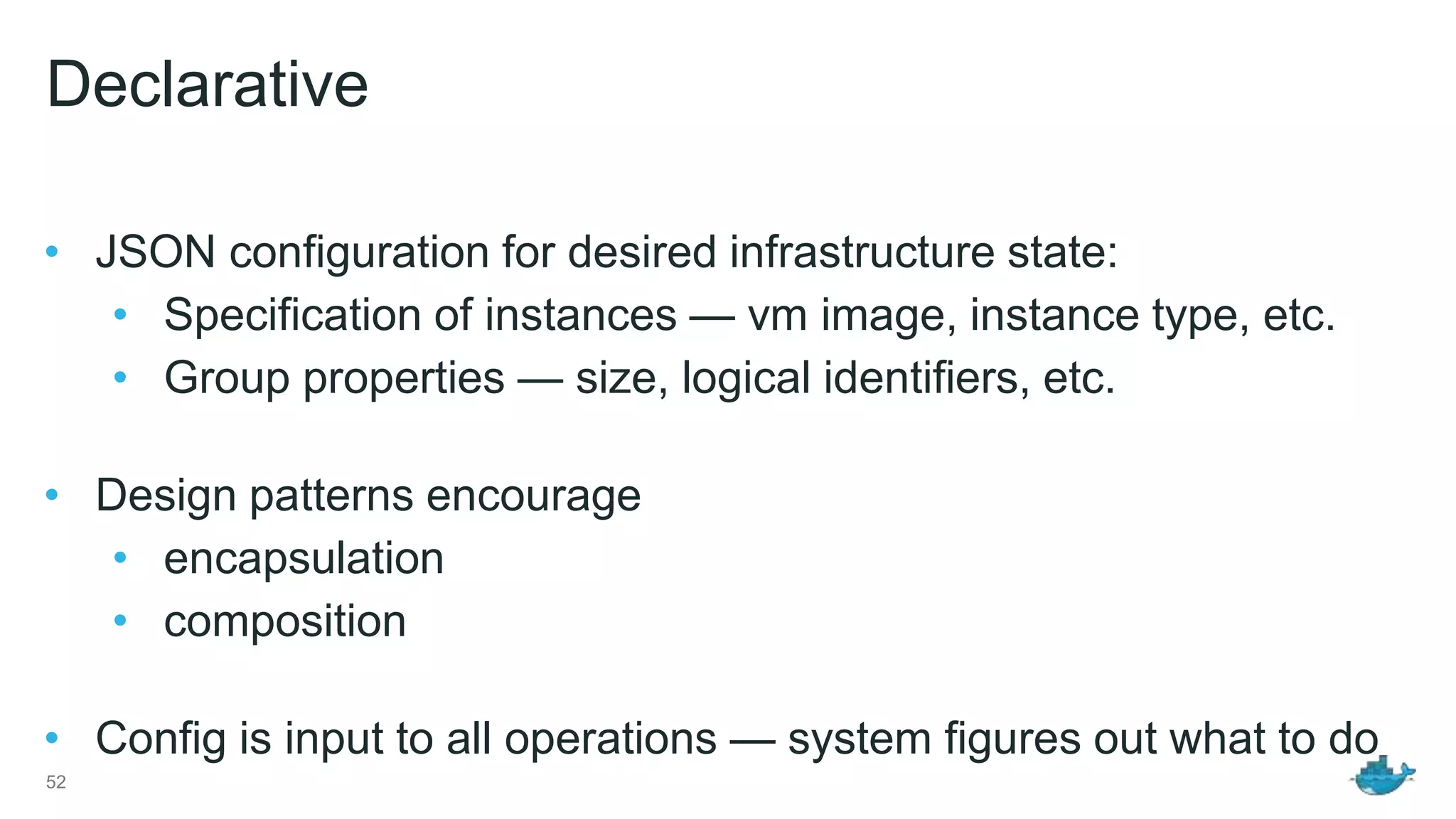
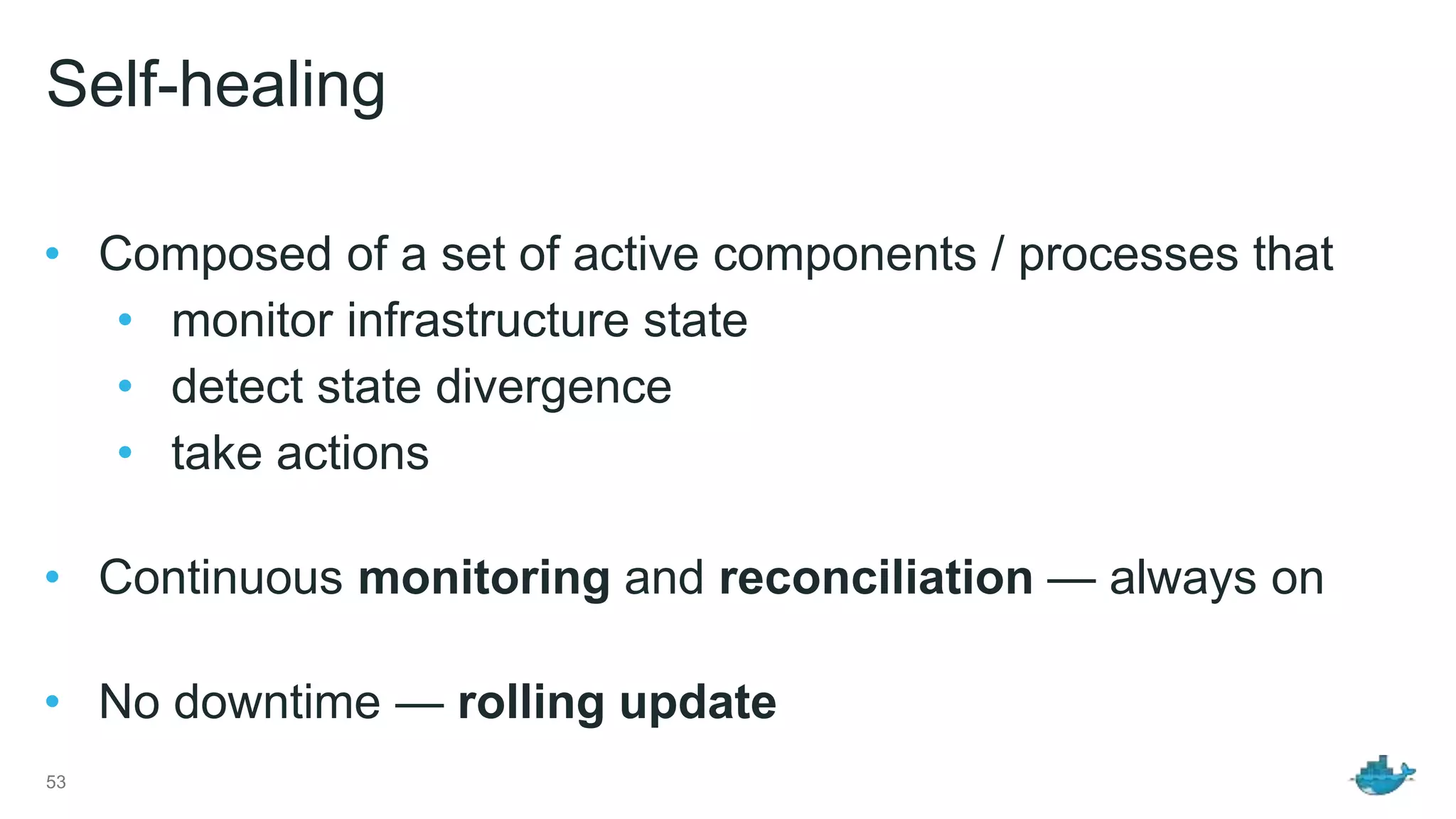
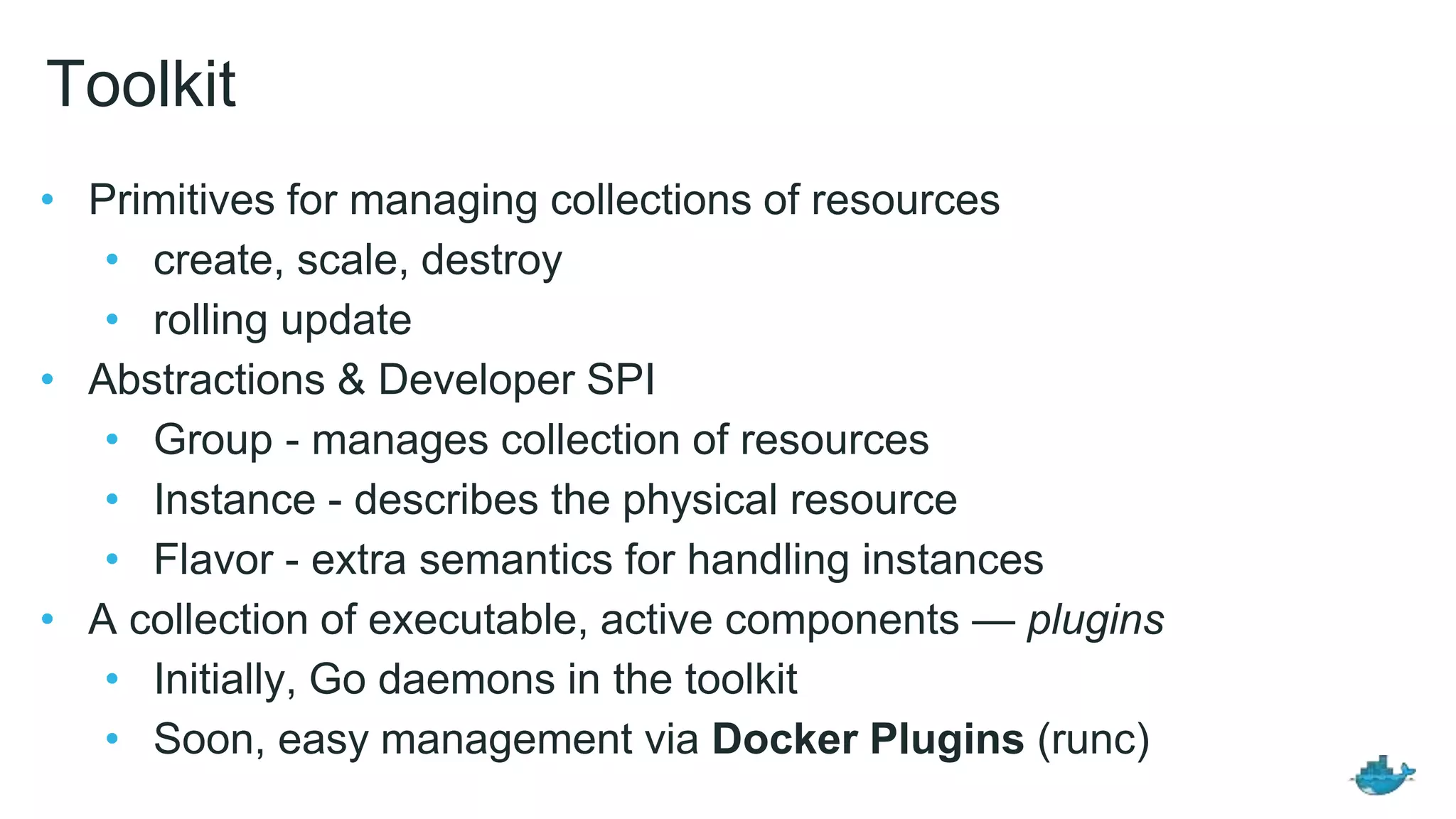
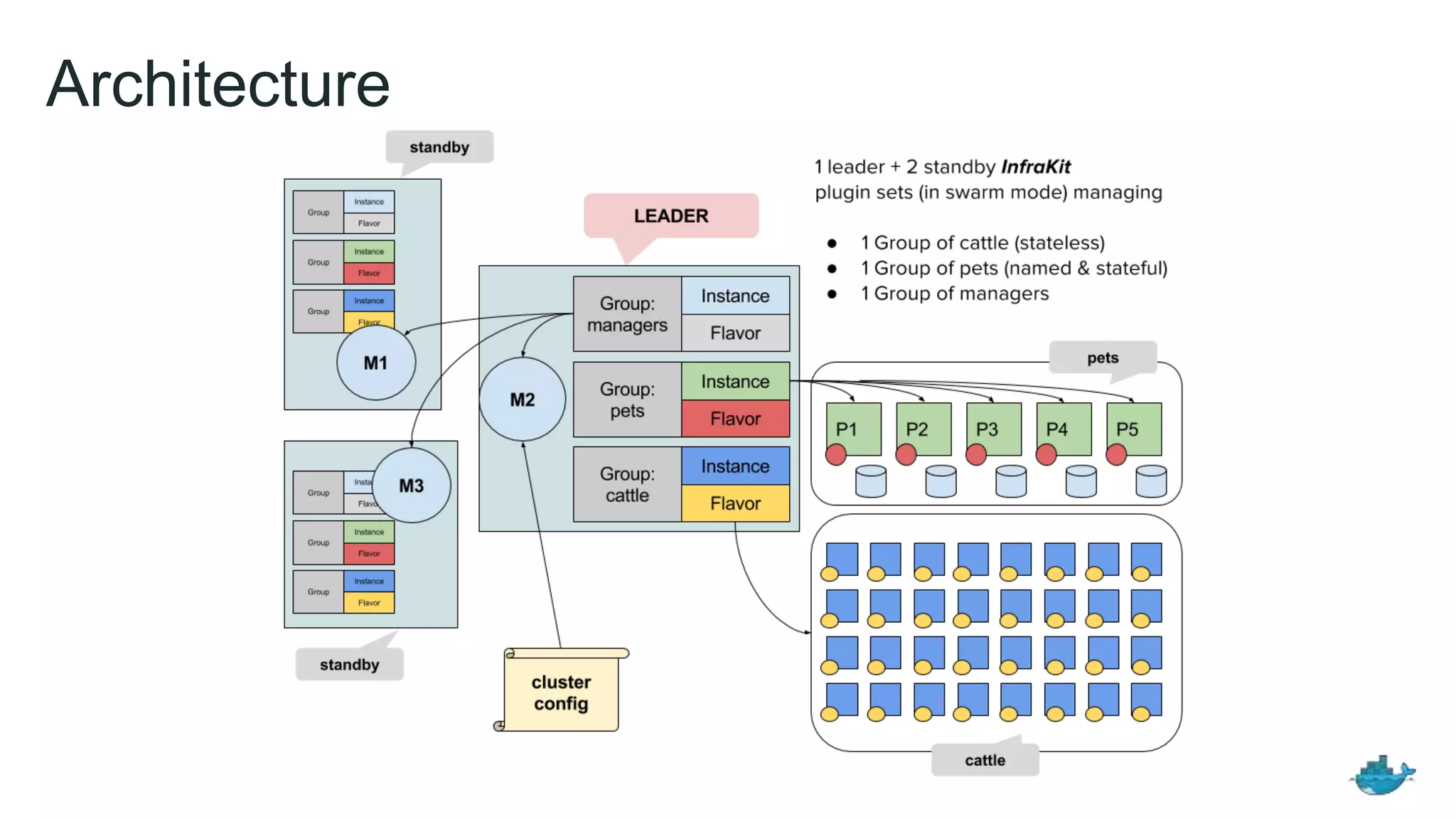
The document discusses the development and features of Docker as a platform for building and orchestrating distributed systems, highlighting its use of system isolation, container technology, and built-in orchestration capabilities. It emphasizes the importance of a container as a service (CaaS) strategy for developers and operators, along with Docker's role in standardizing container runtime through initiatives like OCI. Additionally, it introduces Infrakit, a toolkit for managing declarative and self-healing infrastructure, and outlines various Docker presentations and tutorials scheduled for a conference.














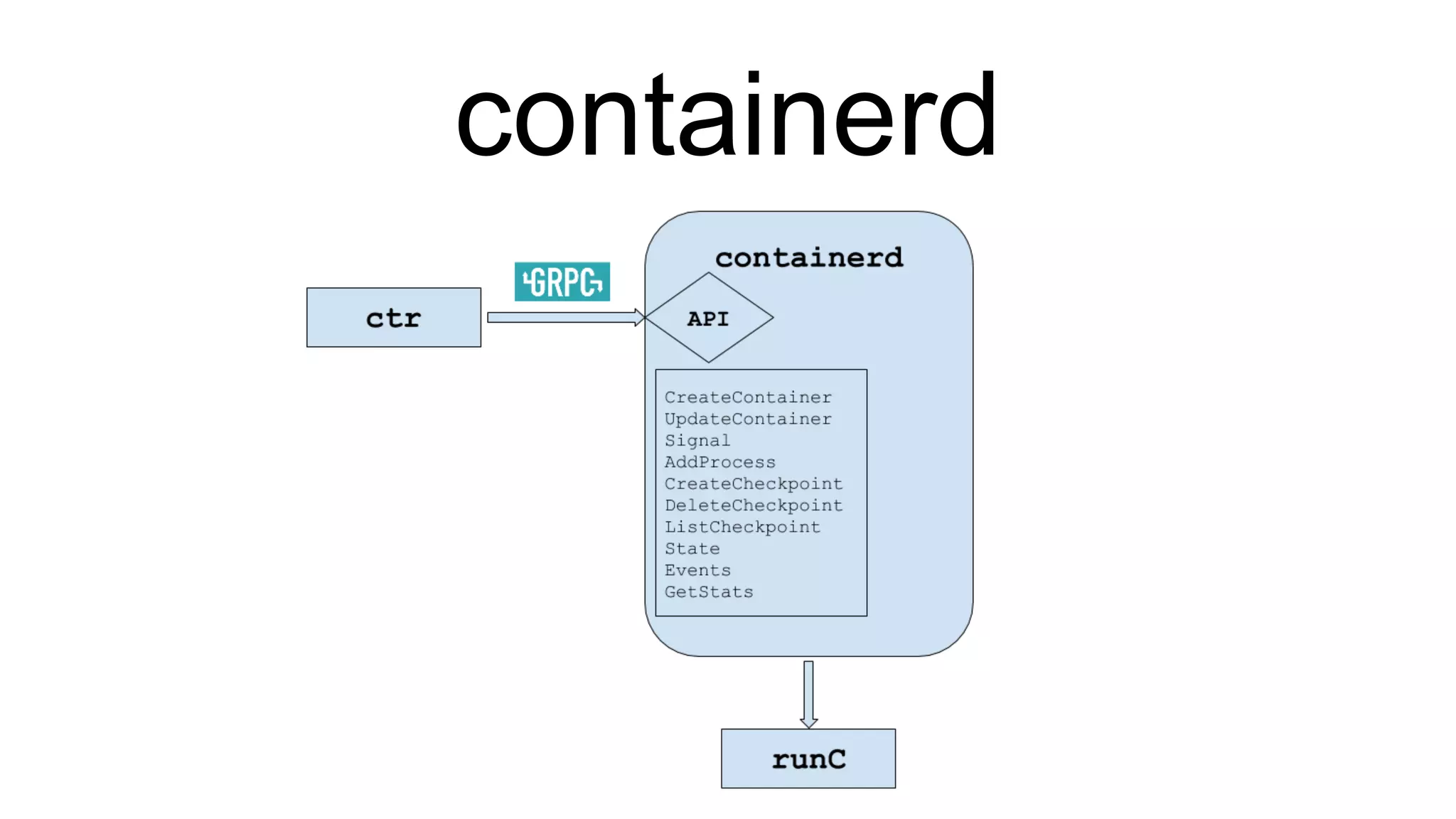
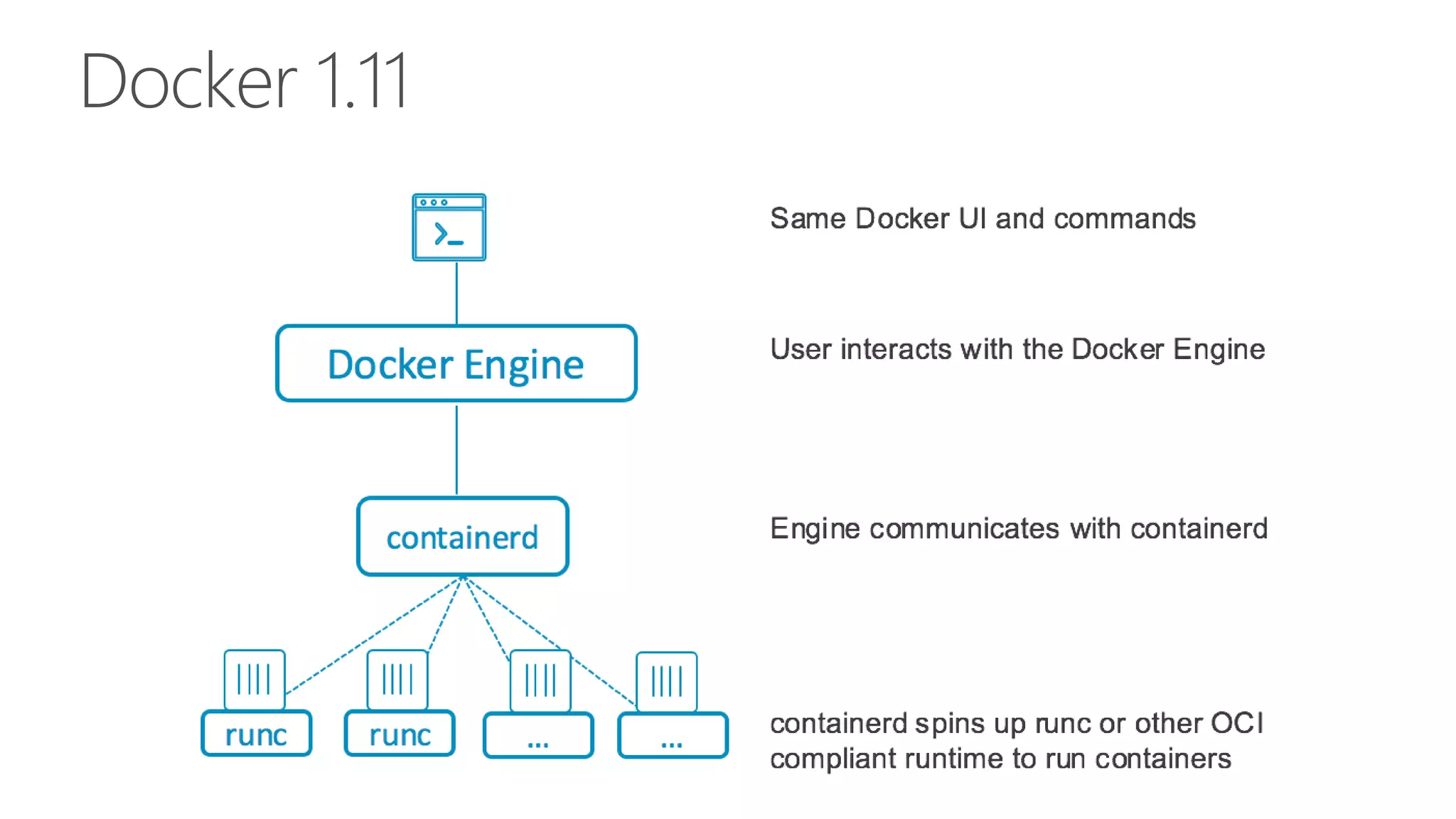


![Introduction to `runc` > runc is a client wrapper around libcontainer > Libcontainer is the OS level interface for containers Other platforms and architectures can implement the libcontainer API via their own primitives/system-level container concepts $ docker run -it --read-only -v /host:/hostpath alpine sh /# { "ociVersion": "0.6.0-dev", "platform": { "os": "linux", "arch": "amd64" }, "process": { "terminal": true, "args": [ "sh" ], "env": [ "PATH=/usr/local/sbin:/usr/local/bin:/bin” config.json](https://image.slidesharecdn.com/linuxcon-containers-without-docker-161006081055/75/Building-Distributed-Systems-without-Docker-Using-Docker-Plumbing-Projects-LinuxCon-Berlin-2016-37-2048.jpg)





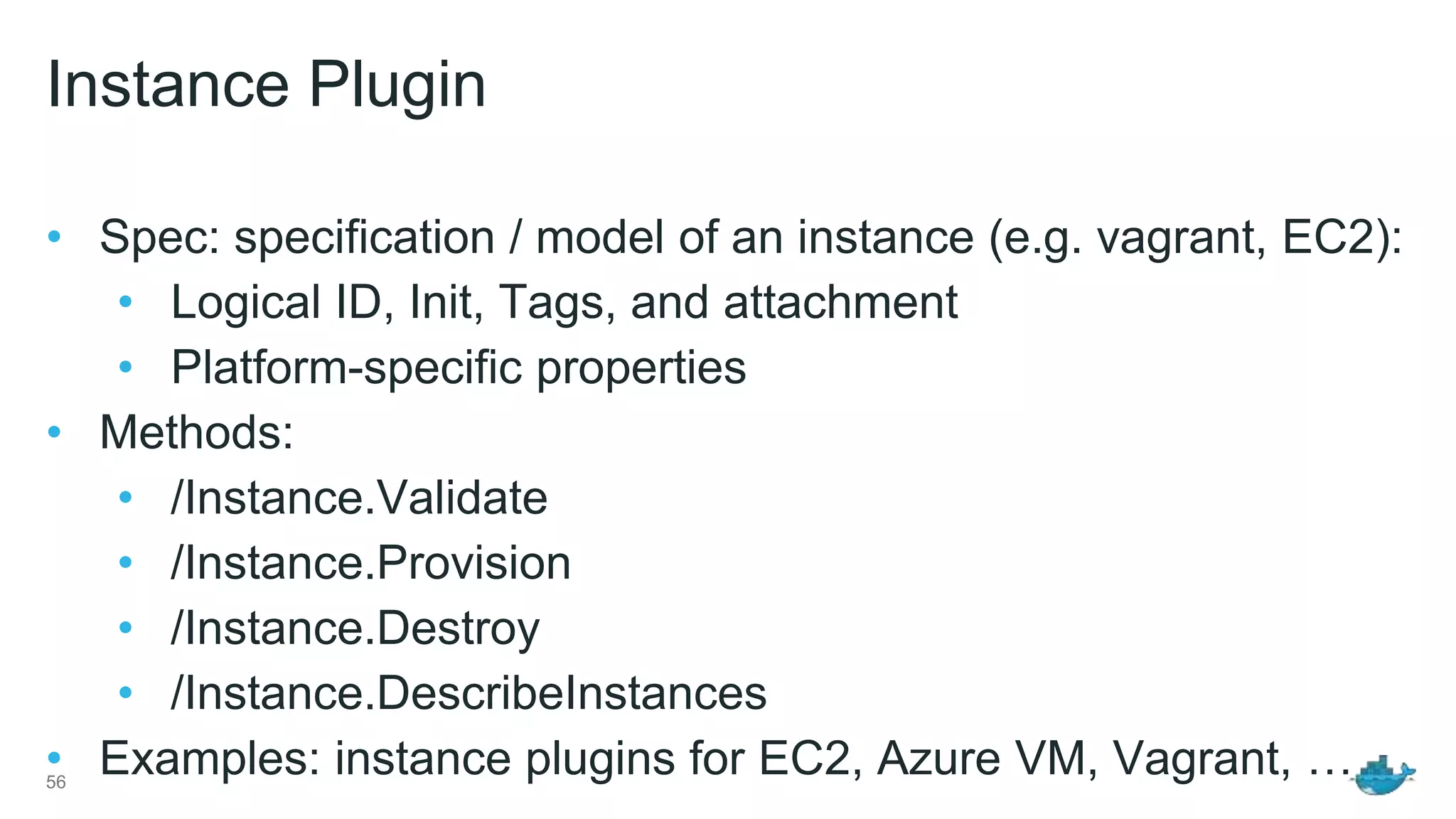


![Configuration Example config file (zk.conf): Group configuration = Instance + Flavor { "Properties": { /* raw configuration */ } } { "groups" : { "my_zookeeper_nodes" : { "Properties" : { "Instance" : { "Plugin": "instance-vagrant", "Properties": { "Box": "bento/ubuntu-16.04" } }, "Flavor" : { "Plugin": "flavor-zookeeper", "Properties": { "type": "member", "IPs": ["192.168.1.200", "192.168.1.201", "192.168.1.202"] } } } } } }](https://image.slidesharecdn.com/linuxcon-containers-without-docker-161006081055/75/Building-Distributed-Systems-without-Docker-Using-Docker-Plumbing-Projects-LinuxCon-Berlin-2016-56-2048.jpg)