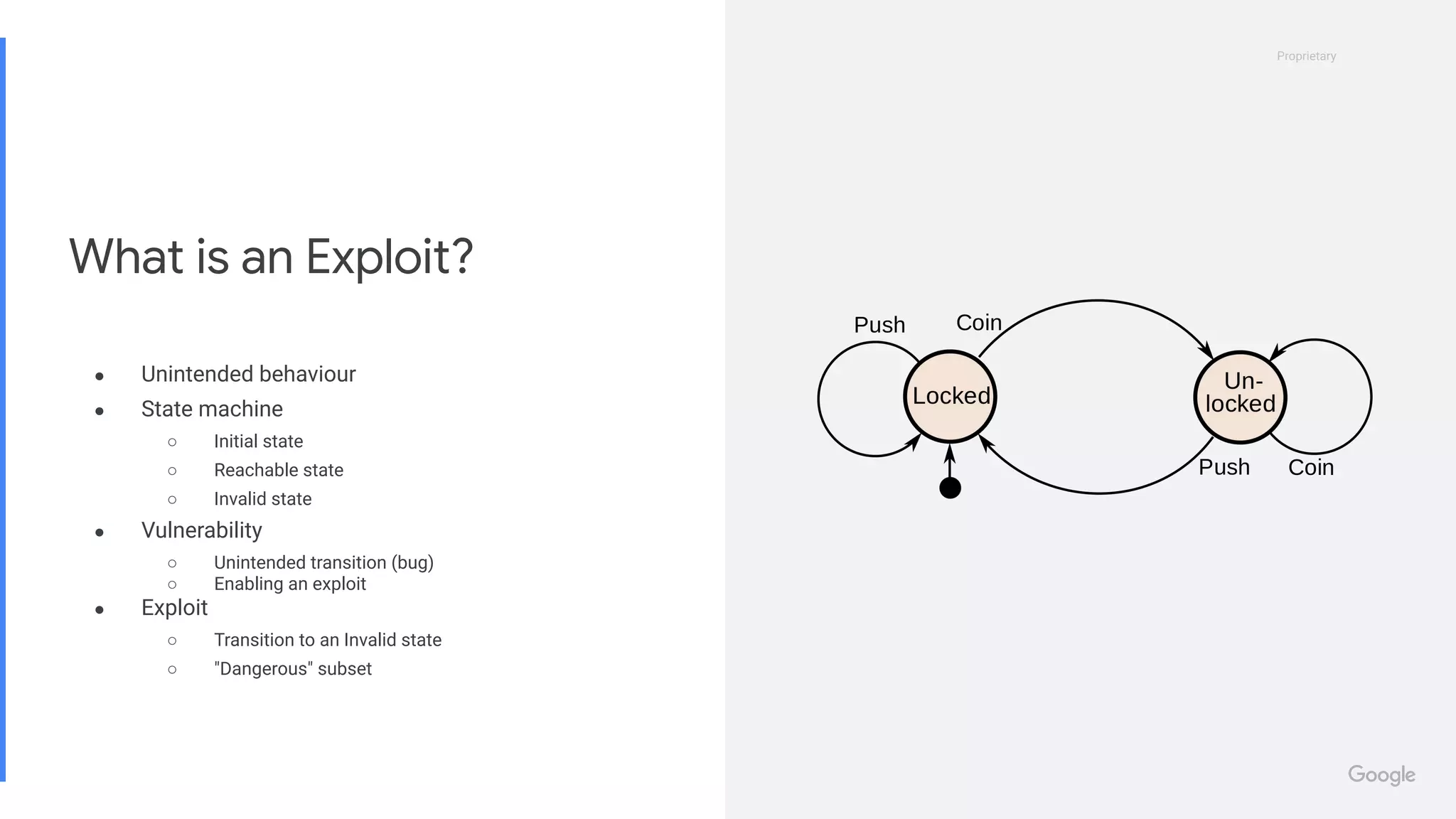
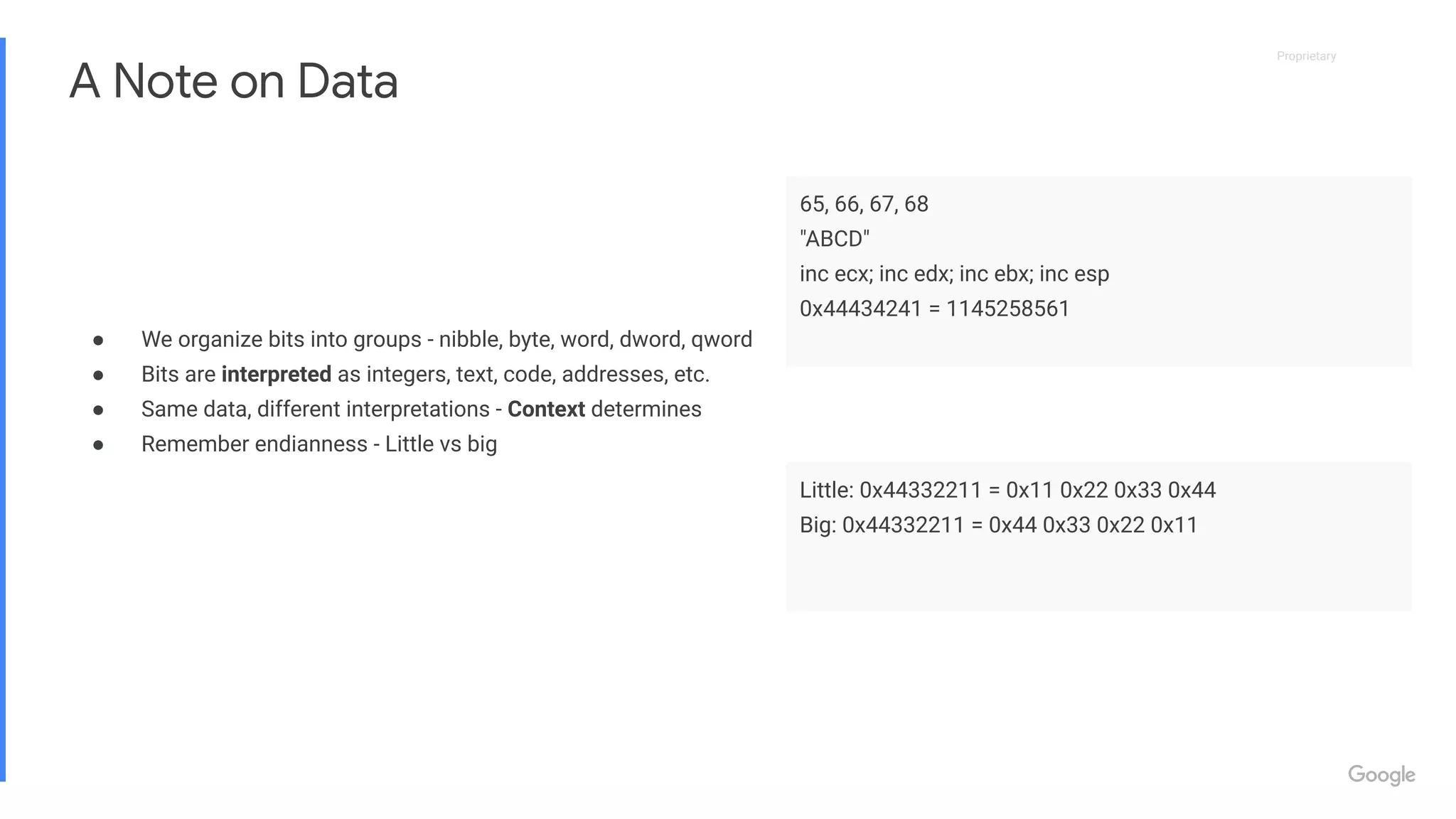
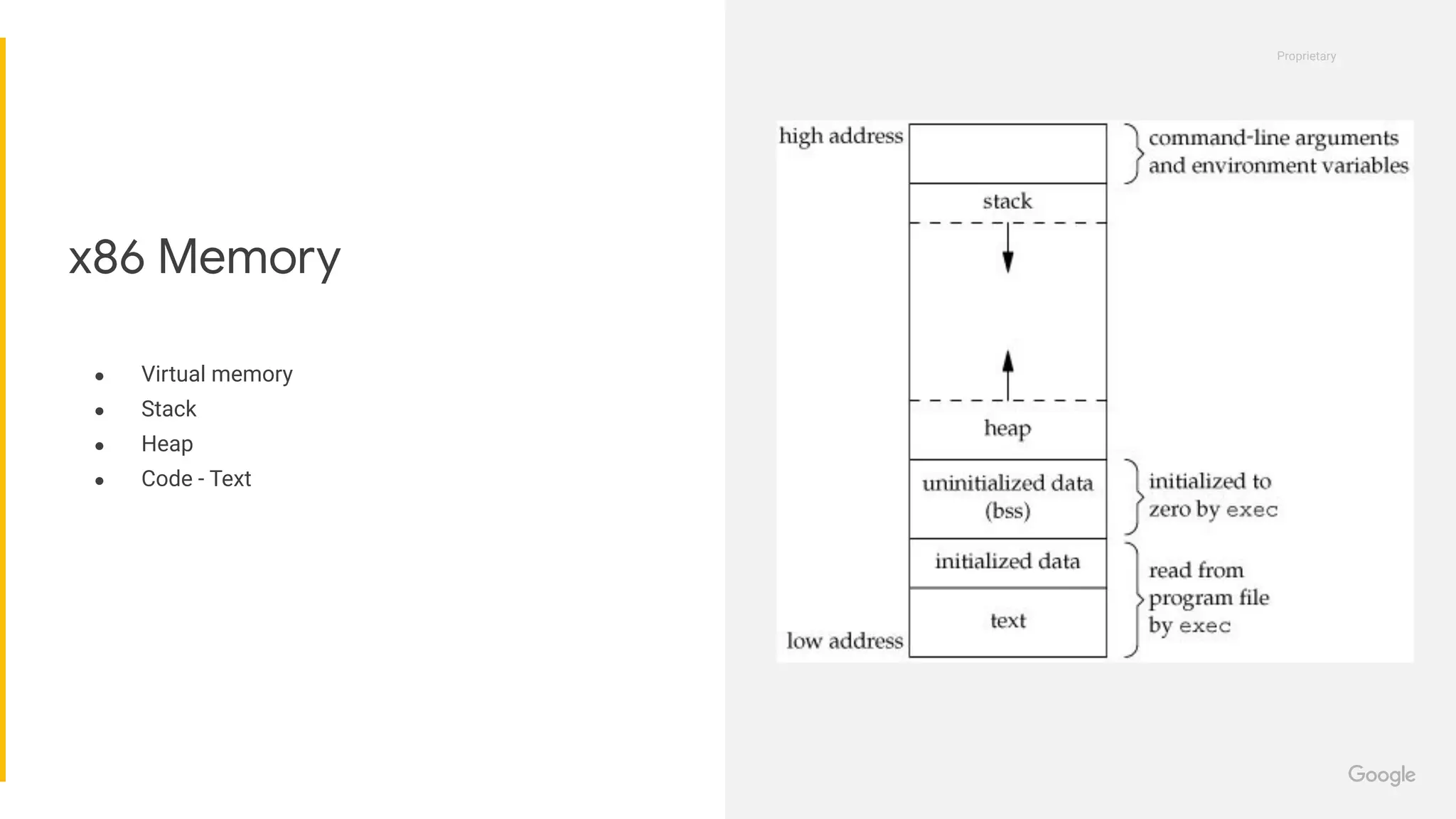
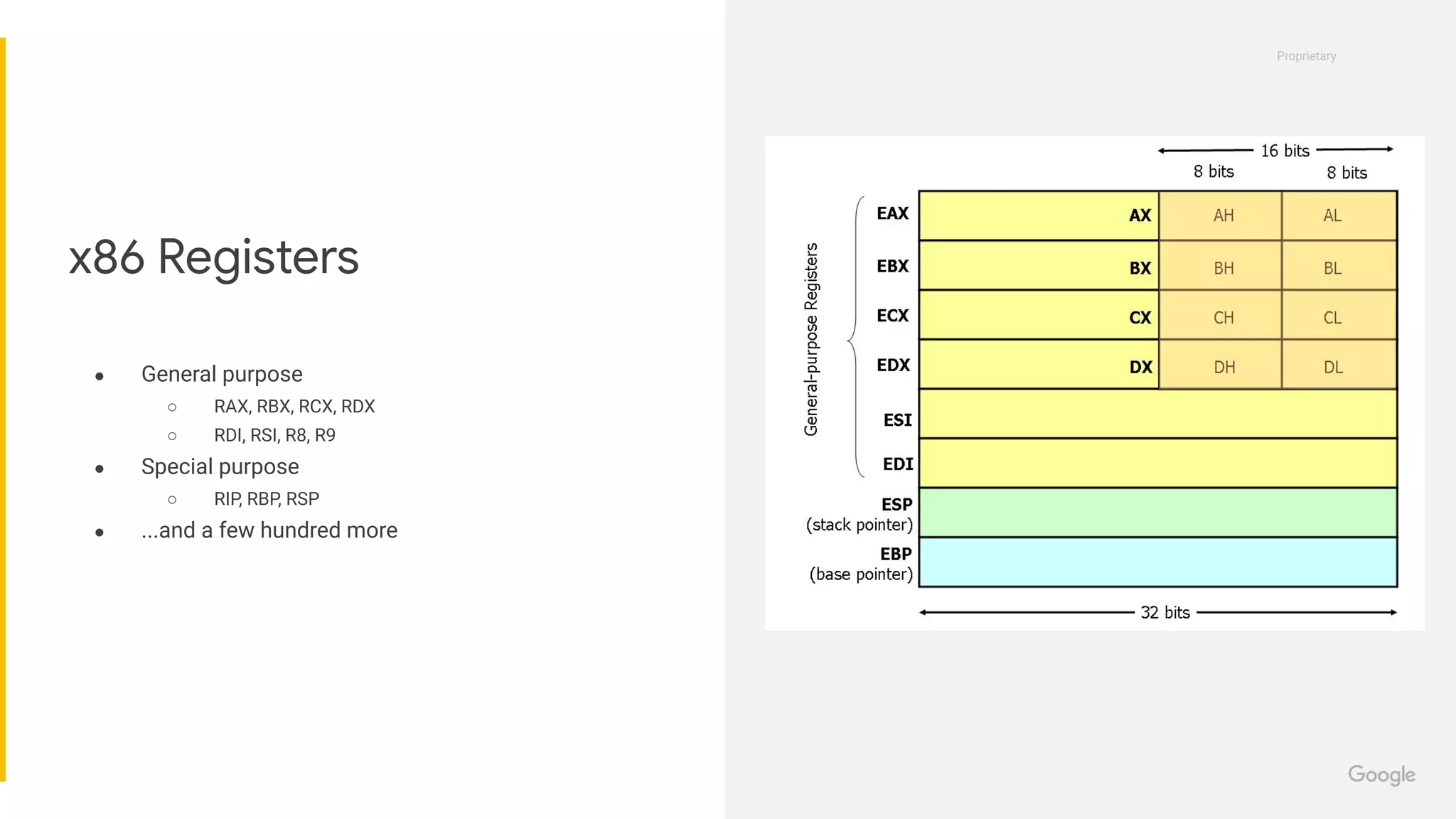
This document provides an introduction to concepts in computer security, focusing on exploitation techniques such as stack and heap overflows, as well as protections against these vulnerabilities. It covers technical details of memory and CPU architecture, various forms of exploits, and their corresponding countermeasures. Additionally, it offers resources for further learning and opportunities in the field of security engineering.



![Proprietary Proprietary ● Unchecked write ● Overwrite adjacent memory ● Overwrite return address Stack buffer Overflow void vuln() { long local1; char buf[16]; fgets(buf); } Program received signal SIGSEGV, Segmentation fault. 0x4B4B4B4B4A4A4A4A in example1 () [buf (16 bytes)] [local1 (8 bytes)] [saved bp (8 bytes)] [return address (8 bytes)] [AAAABBBBCCCCDDDD] [EEEEFFFF] [GGGGHHHH] [JJJJKKKK]](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-14-2048.jpg)
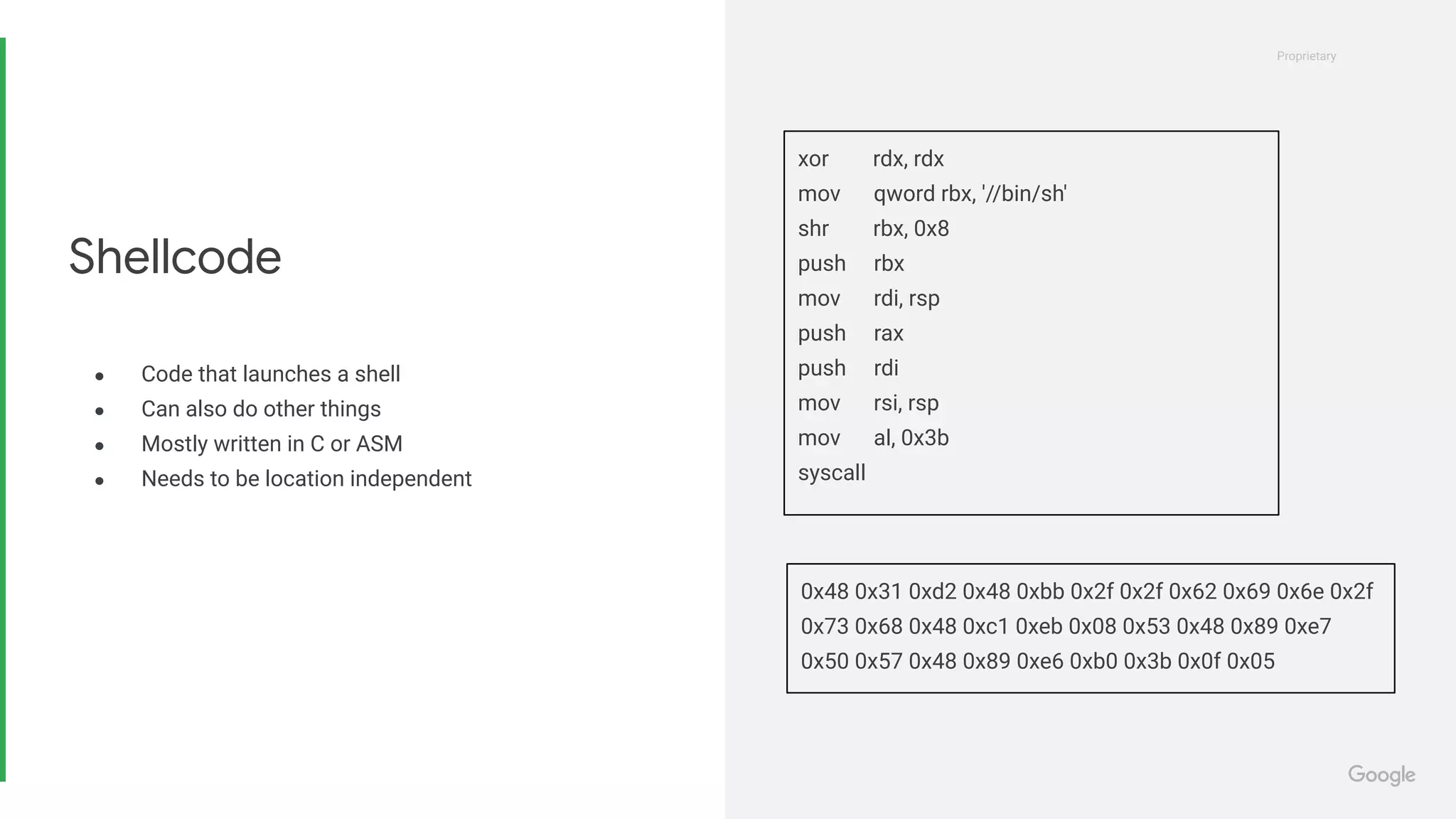
![Proprietary Proprietary ● No protections present ● No longer viable ● A simple attack ○ Inject code ○ Overwrite return address with shellcode location Stack buffer overflow -96 void vuln() { long local1; char buf[16]; fgets(buf); } $ uname -a Linux pwnbox 5.4.0-12.15-generic... [buf (16 bytes)] [local1 (8 bytes)] [saved bp (8 bytes)] [return address (8 bytes)] 0x00007FFFDEADC0DE: [0x48 0x31 0xd2 0x48 ...] [...] [... 0x3b 0x0f 0x05] [0x00007FFFDEADC0DE]](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-16-2048.jpg)
![Proprietary Proprietary ● Shellcode can be moved around ● For example further down the stack ● If exact location is unknown ○ NOP sled Shellcode placement void vuln() { long local1; char buf[12]; fgets(buf); } $ uname -a Linux pwnbox 5.4.0-12.15-generic... [buf (12 bytes)] [local1 (8 bytes)] [saved bp (8 bytes)] [return address (8 bytes)] [prev frame (? bytes)] 0x00007FFFDEADC0DE: [...] [...] [...] [0x00007FFFDEADC102] [0x48 0x31 0xd2 …]](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-17-2048.jpg)
![Proprietary Proprietary ● Address Space Layout Randomization ● Randomize location of stack and heap ○ 32 bit: 12 bit entropy ○ 64 bit: 28 bit entropy ● So far code location still known ● Location of buffer now unknown ● Code reuse ○ Gadgets Protection: ASLR -01 0x00007FFFCAFECAFE: jmp rsp $ uname -a Linux pwnbox 5.4.0-12.15-generic... [buf (16 bytes)] [local1 (8 bytes)] [saved bp (8 bytes)] [return address (8 bytes)] [prev frame (? bytes)] 0x????????: [...] [...] [...] [0x00007FFFCAFECAFE] [0x48 0x31 0xd2 …]](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-18-2048.jpg)
![Proprietary Proprietary ● Adds permission bits to memory ○ Code: RX ○ Heap+Stack: RW ● Shellcode on stack not possible ● Code location know ● Gadgets ○ Return-oriented programming Protection: NX/DEP -97 0x4000104A: ... pop eax ret 0x4000106A: ... pop ebx pop ecx ret 0x????????: [AAAA...DDDD] [EEEE] [FFFF] [0x4000104A] [0xDEADBEEF] [0x4000106A] [0xCAFEBABE] [0xFEEDF00D] eax = 0xDEADBEEF ebx = 0xCAFEBABE ecx = 0xFEEDF00D](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-19-2048.jpg)
![Proprietary Proprietary ● Catch the overflow before damage ● Canary - random secret value ● The crash becomes controlled ● Relies on canary being secret ○ Memory leak ○ Forking servers Protection: StackGuard -98 void vuln() { long local1; char buf[12]; fgets(buf); } *** stack smashing detected ***: ./a.out terminated ======= Backtrace: ========= SECRET = ??? [...] [...] [SECRET] [saved bp (8 bytes)] [return address (8 bytes)] [...] [...] [0x4141414141414141] [0x4141414141414141] [0x00007FFFDEADC0DE] void vuln() { push_cookie(); long local1; char buf[12]; fgets(buf); check_cookie(); }](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-20-2048.jpg)
![Proprietary Proprietary ● Program Linkage Table, PLT ● Global Offset Table, GOT ● PLT contains stubs with jumps ● GOT contains addresses to libraries ● Overwrite GOT entry and call function GOT/PLT Overwrite ... call printf@plt ... printf@plt: jmp [printf@got] printf@got: 0x7FFFC0DECAFE printf@got: 0x7FFFDEADDEAD … call printf@plt -> 0x7FFFDEADDEAD ...](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-21-2048.jpg)
![Proprietary Proprietary ● RELocation Read Only, RELRO ● “Partial RELRO” ○ GOT before BSS ● Full RELRO ○ Actually Read Only ○ Handled by loader Protection: RELRO ... call printf@plt ... printf@plt: jmp [printf@got] printf@got: 0x7FFFC0DECAFE printf@got: 0x7FFFDEADDEAD … call printf@plt -> 0x7FFFC0DECAFE ...](https://image.slidesharecdn.com/introductiontobinaryexploitation-210201095832/75/DSC-Introduction-to-Binary-Exploitation-22-2048.jpg)