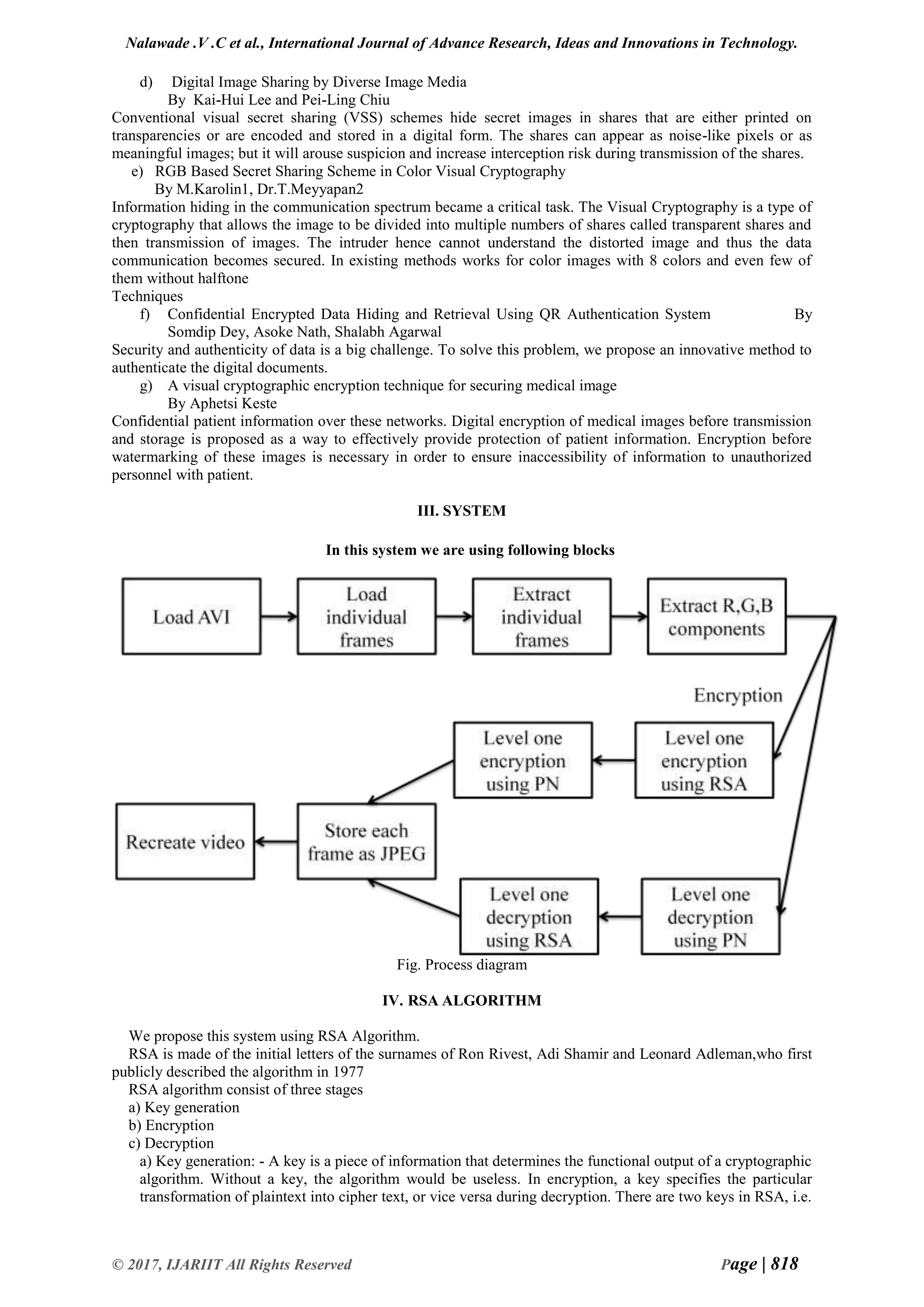
The document proposes a dual-layer video encryption method using RSA and pseudo-noise sequence algorithms. It discusses encrypting the audio and video components separately with two layers of encryption. The video encryption uses RSA followed by pseudo-noise encryption. It describes the RSA algorithm key generation, encryption, and decryption processes. The expected results show the original video being separated into R, G, B components, then undergoing four stages of encryption and three stages of decryption when being reconstructed. The dual-layer approach aims to provide high security without compromising speed or decryption ratio.


![Nalawade .V .C et al., International Journal of Advance Research, Ideas and Innovations in Technology. © 2017, IJARIIT All Rights Reserved Page | 820 Decryption stages: CONCLUSIONS This system will help to secure the secret data from unauthorized use. new method of dual layer encryption methodology which enables to achieve zero visual resemblance and high security while not being severely penalized in Speed and Decryption ratio The dual layer approach presents a promising approach to achieving a highly secure way of video encryption while not being very computationally intensive and time consuming. . ACKNOWLEDGMENT We are very thankful to our guide who has always helped us. Thanks to our college for providing us the best facilities and environment for research. Special thanks to our parents who has always been a source of inspiration for us. REFERENCES [1] Aswathy Nair, Deepu Job, “A Secure Dual Encryption Scheme Combined with Steganography” International Journal of Engineering Trends and Technology (IJETT) – Volume 13 Number 5 – Jul 2014 [2] Vineeta Khemchandani, Kulvinder Kaur, “Securing Visual Cryptographic Shares using Public Key Encryption”. [3] D. Kahn, “Cryptography Goes Public”, IEEE Communications Magazine, Vol. 18, 19–28, 1980. [4] Kulvinder Kaur “Securing Visual Cryptographic Shares using Public Key Encryption” , 2013 3rd IEEE International Advance Computing Conference (IACC). [5] D. Jena and S. Jena “A Novel Visual Cryptography Scheme”. 2008 IEEE DOI 10.1109 [6] Young-Chang Hou, "Visual cryptography for color images”,Journal of Pattern Recognition, Vol.36, pp.1619 – 1629, 2009. STAGE 5 After level 2 decryption STAGE 6 After level 1 decryption STAGE 7 After recombining all R,G,B components](https://image.slidesharecdn.com/v3i1-1379-170713062640/75/Dual-Layer-Video-Encryption-and-Decryption-using-RSA-Algorithm-4-2048.jpg)