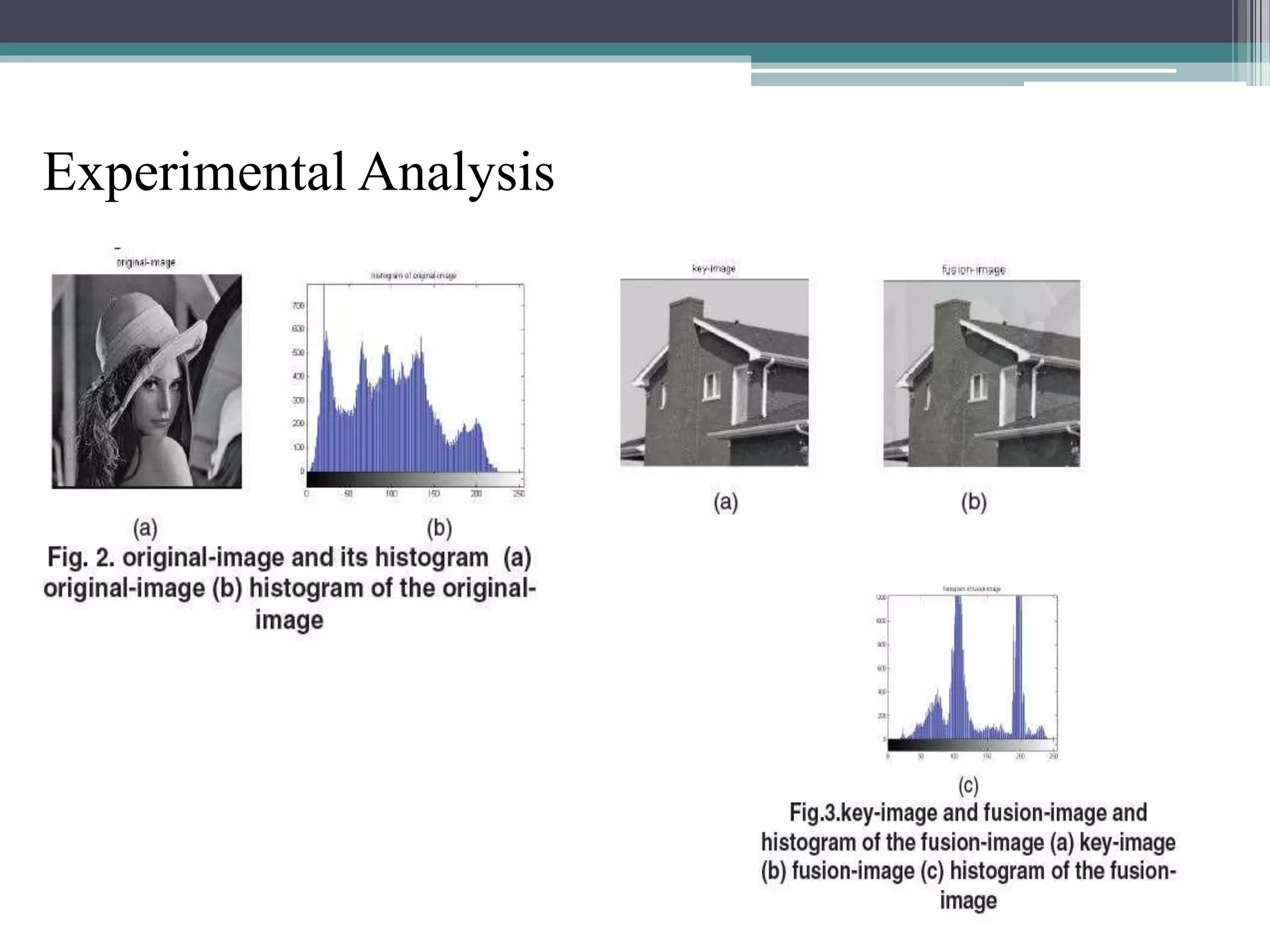
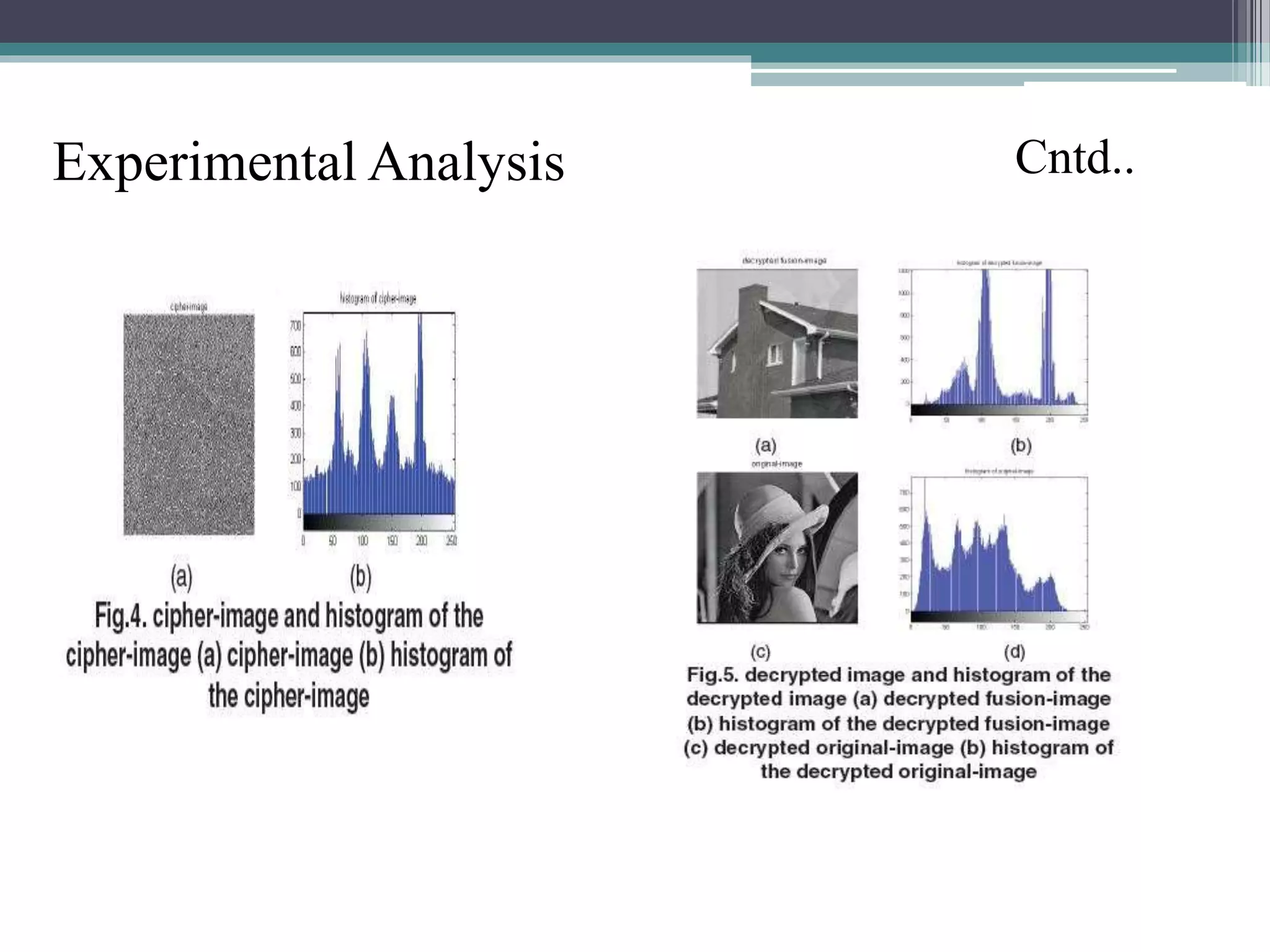
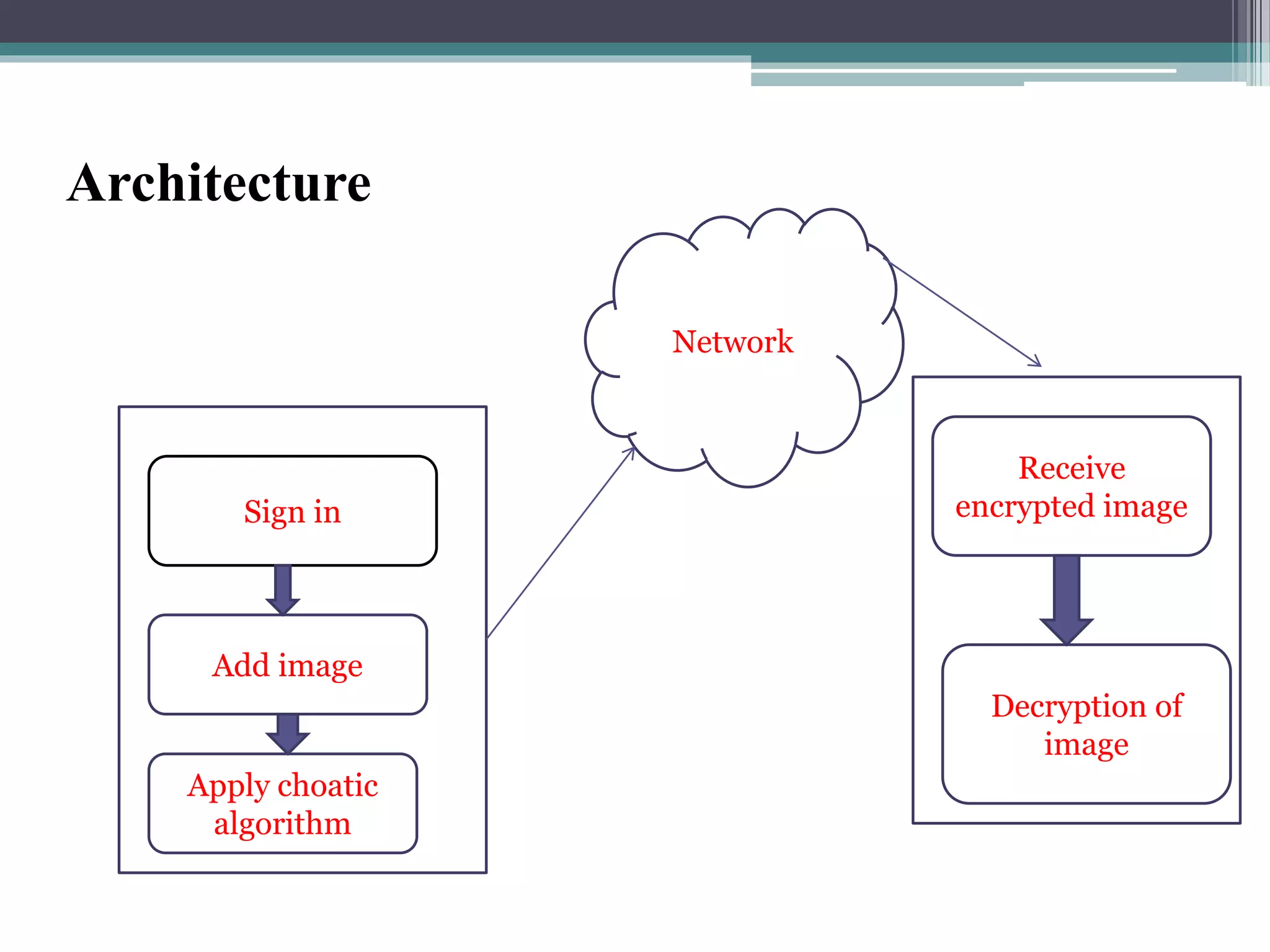
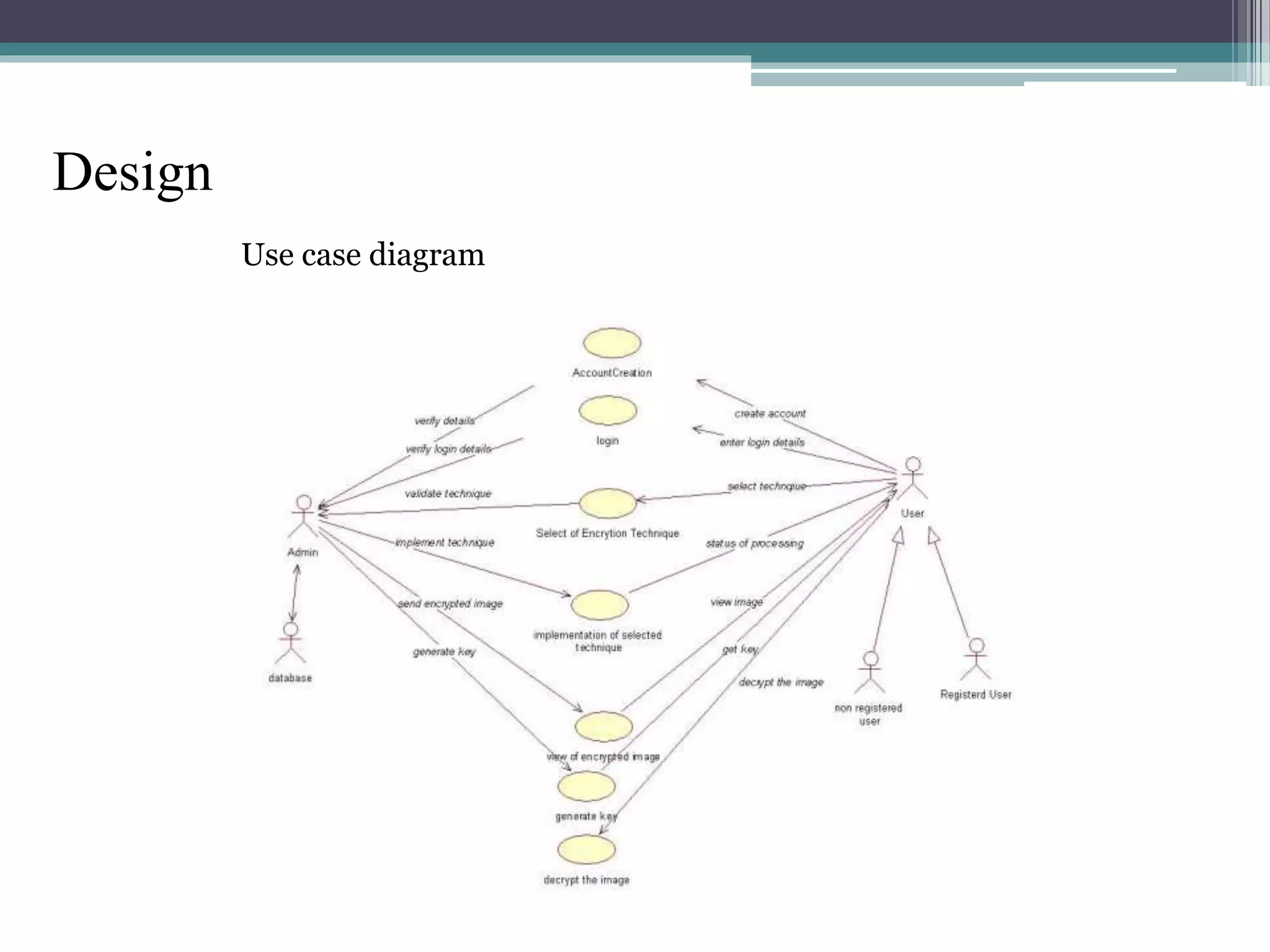
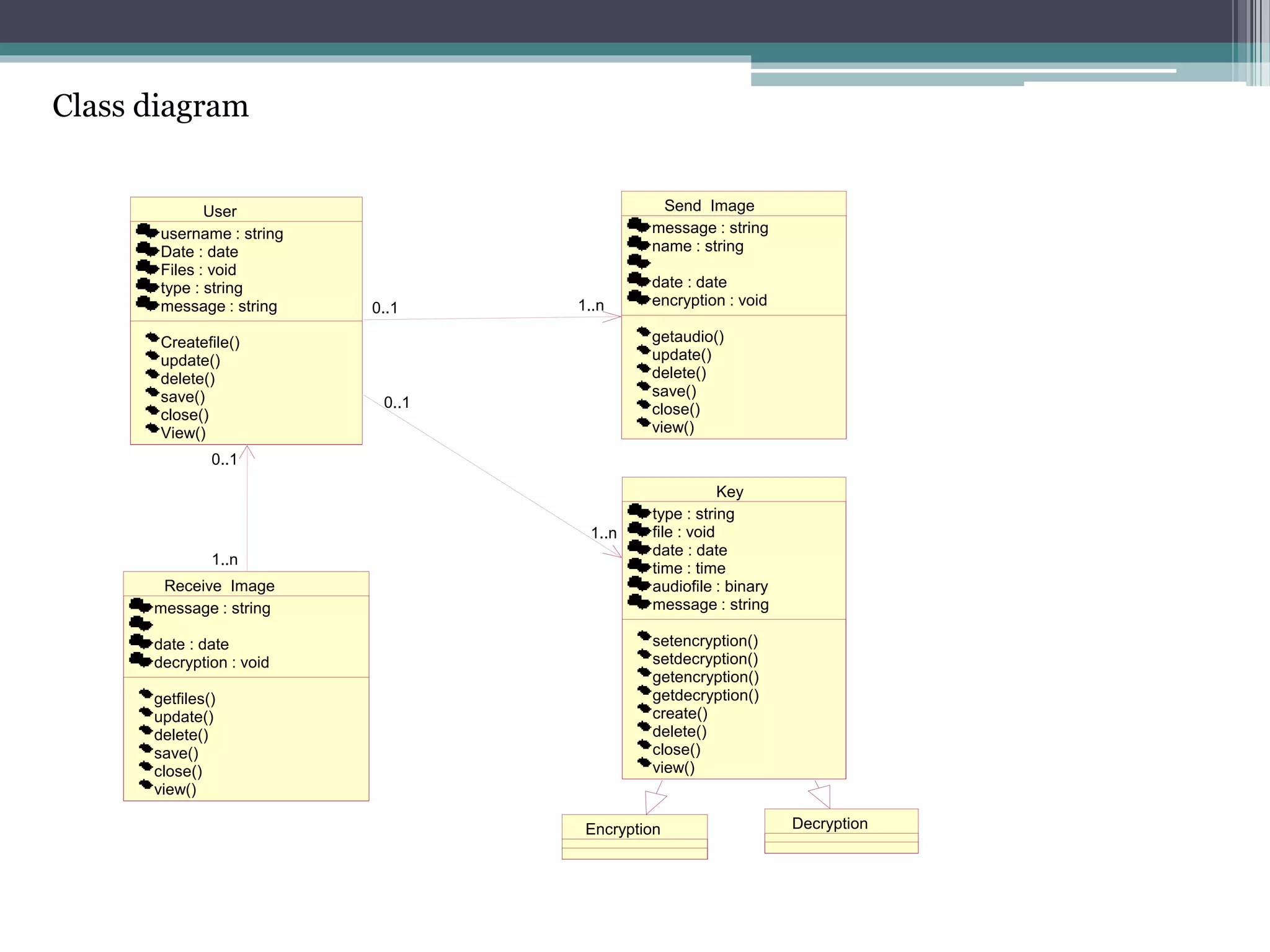
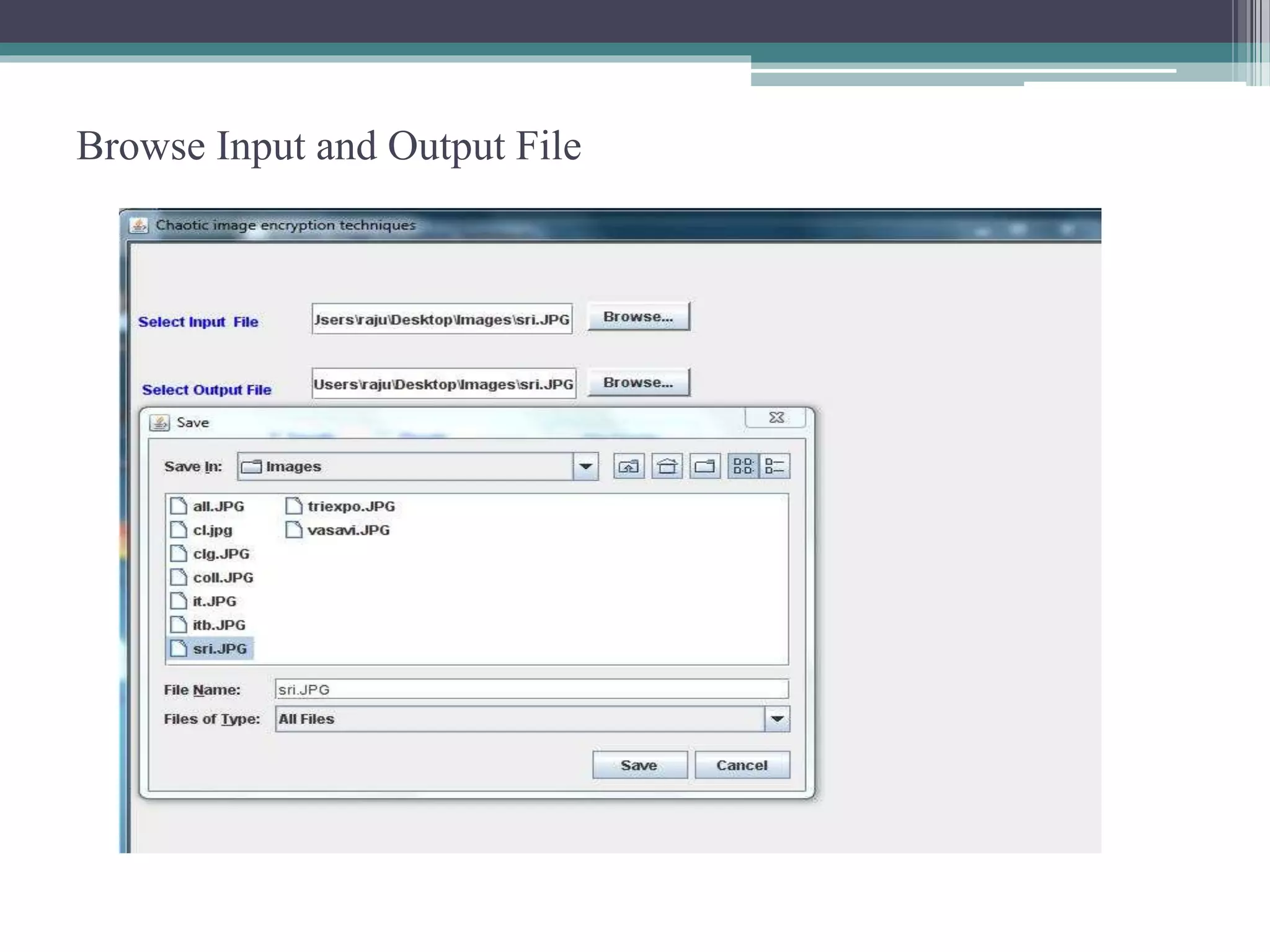
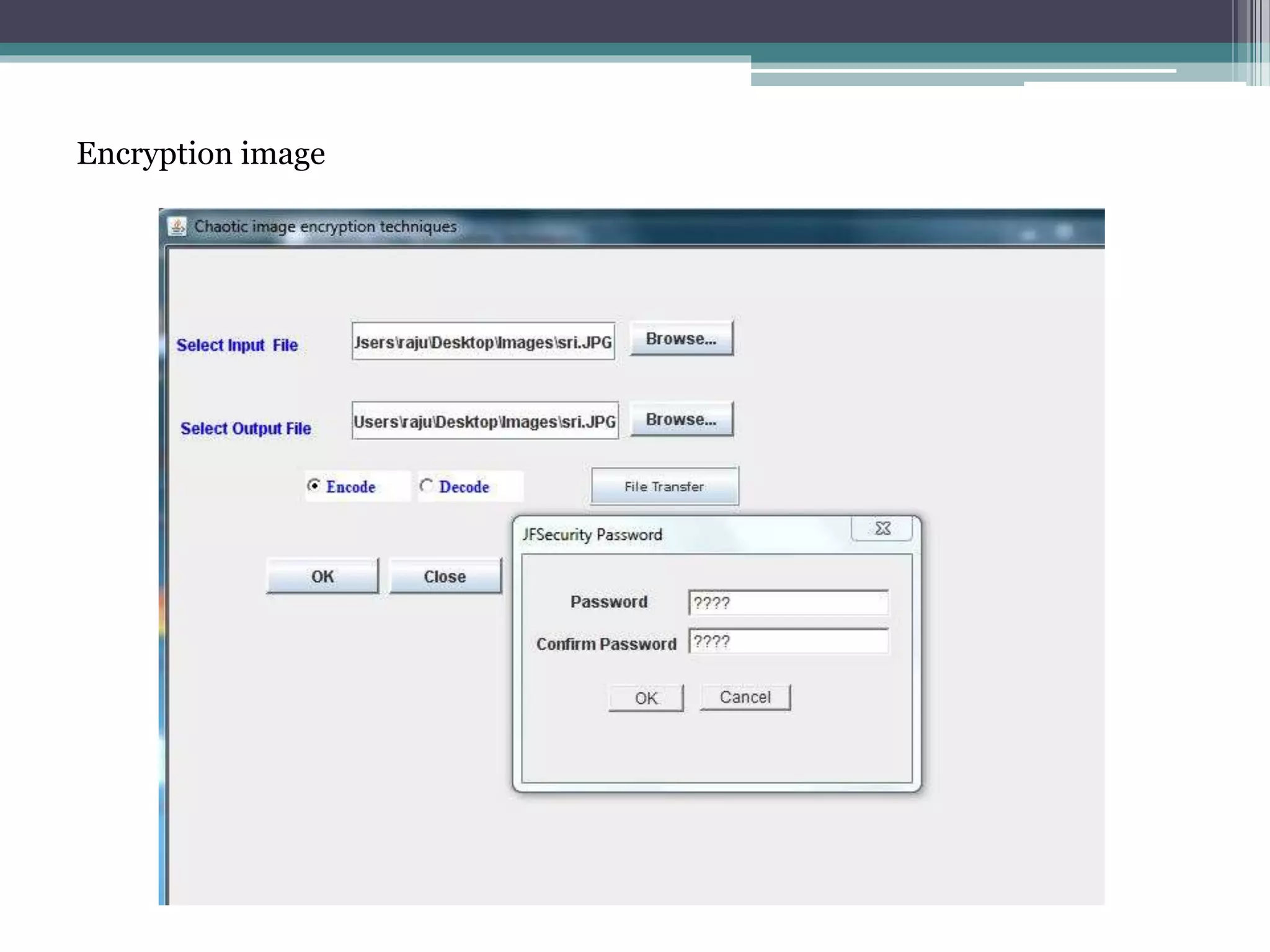
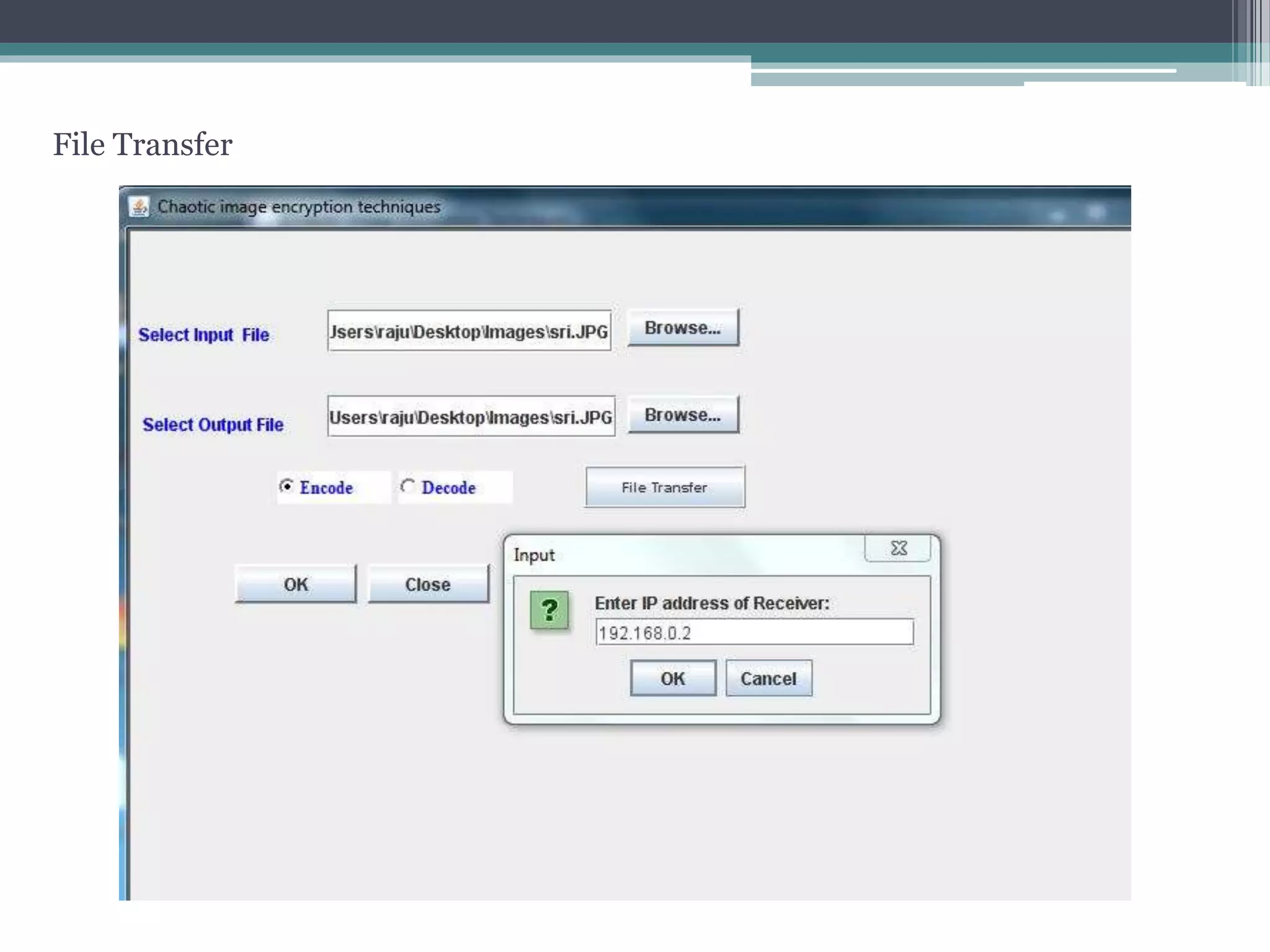
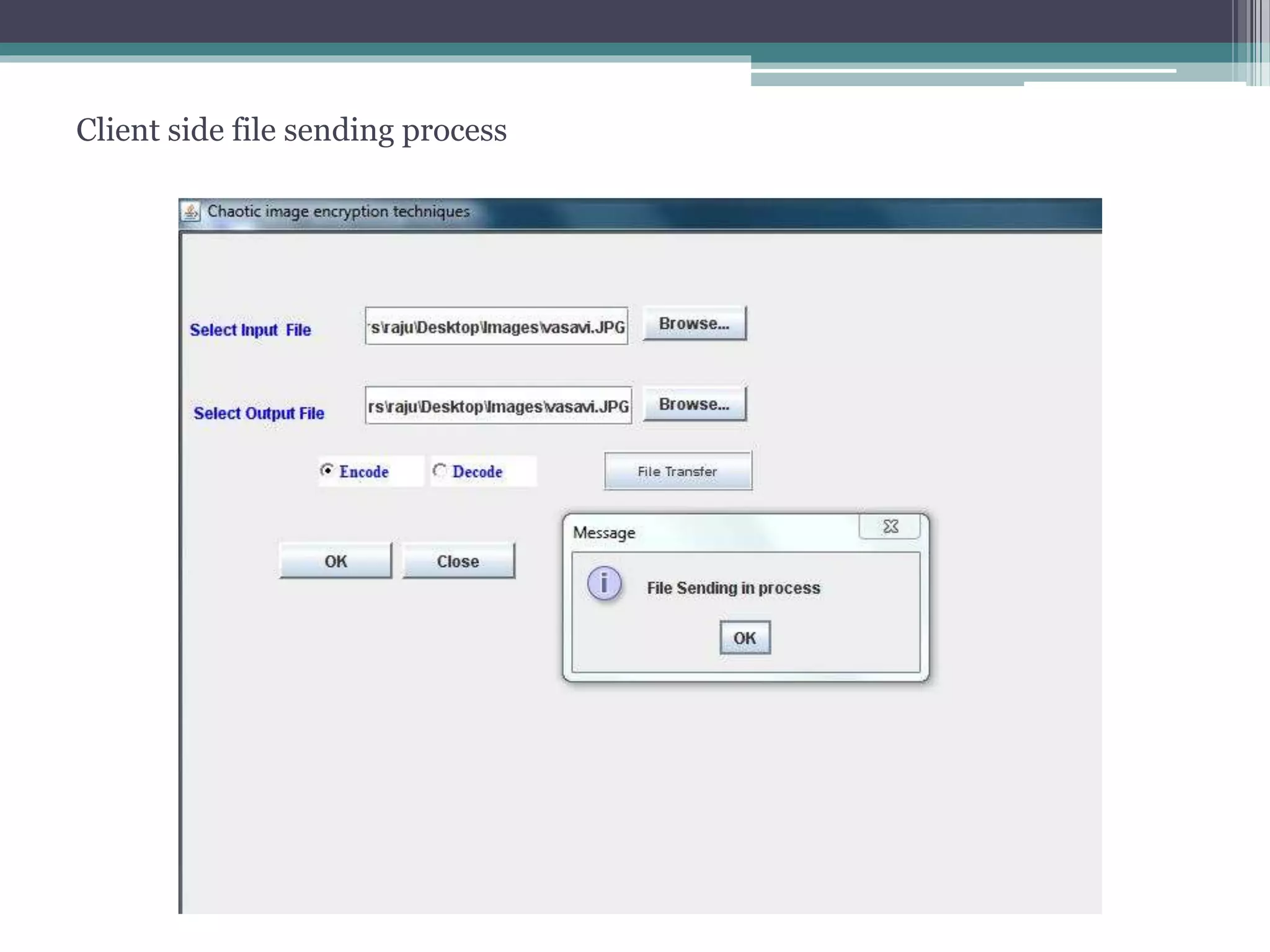
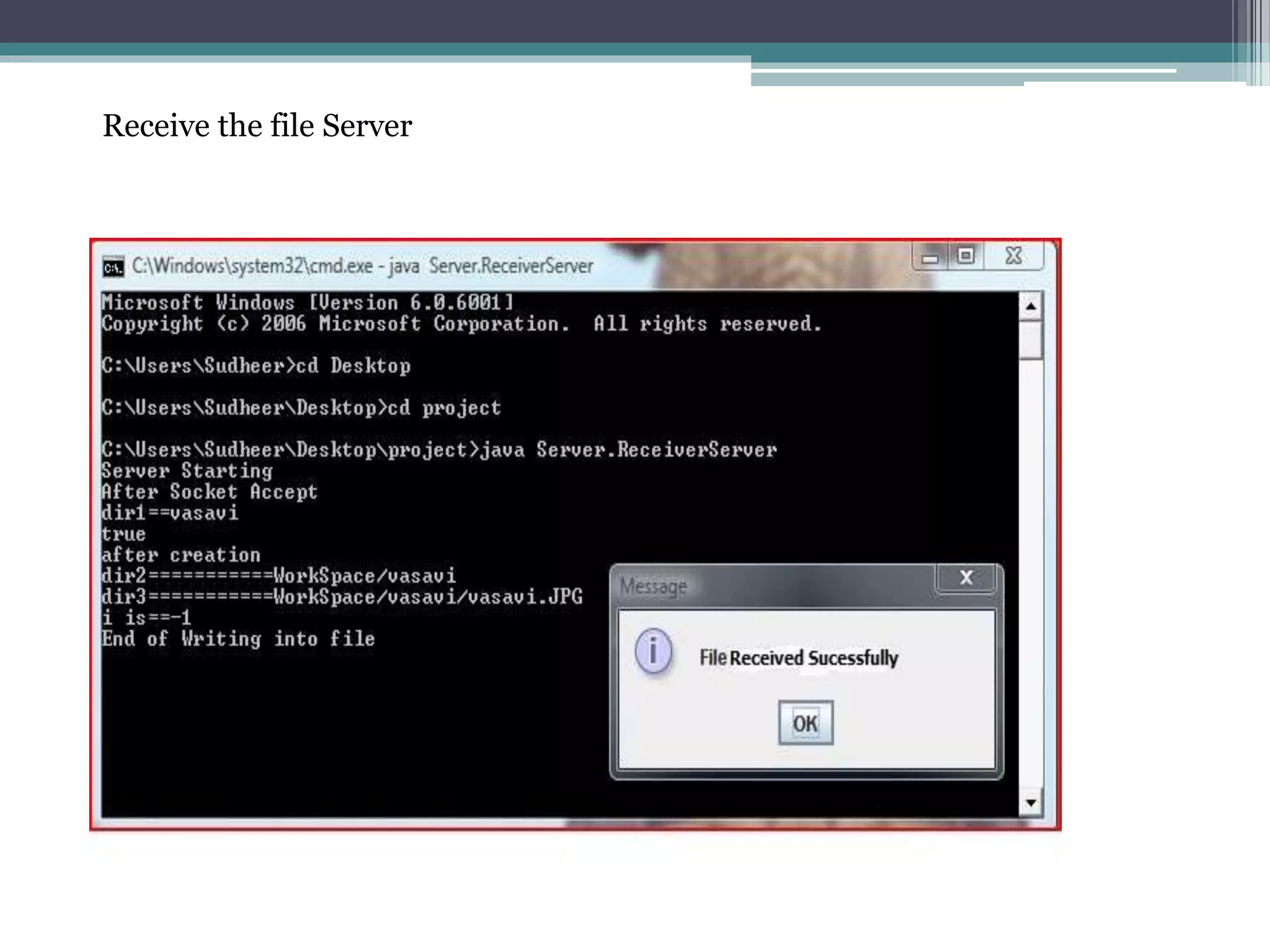
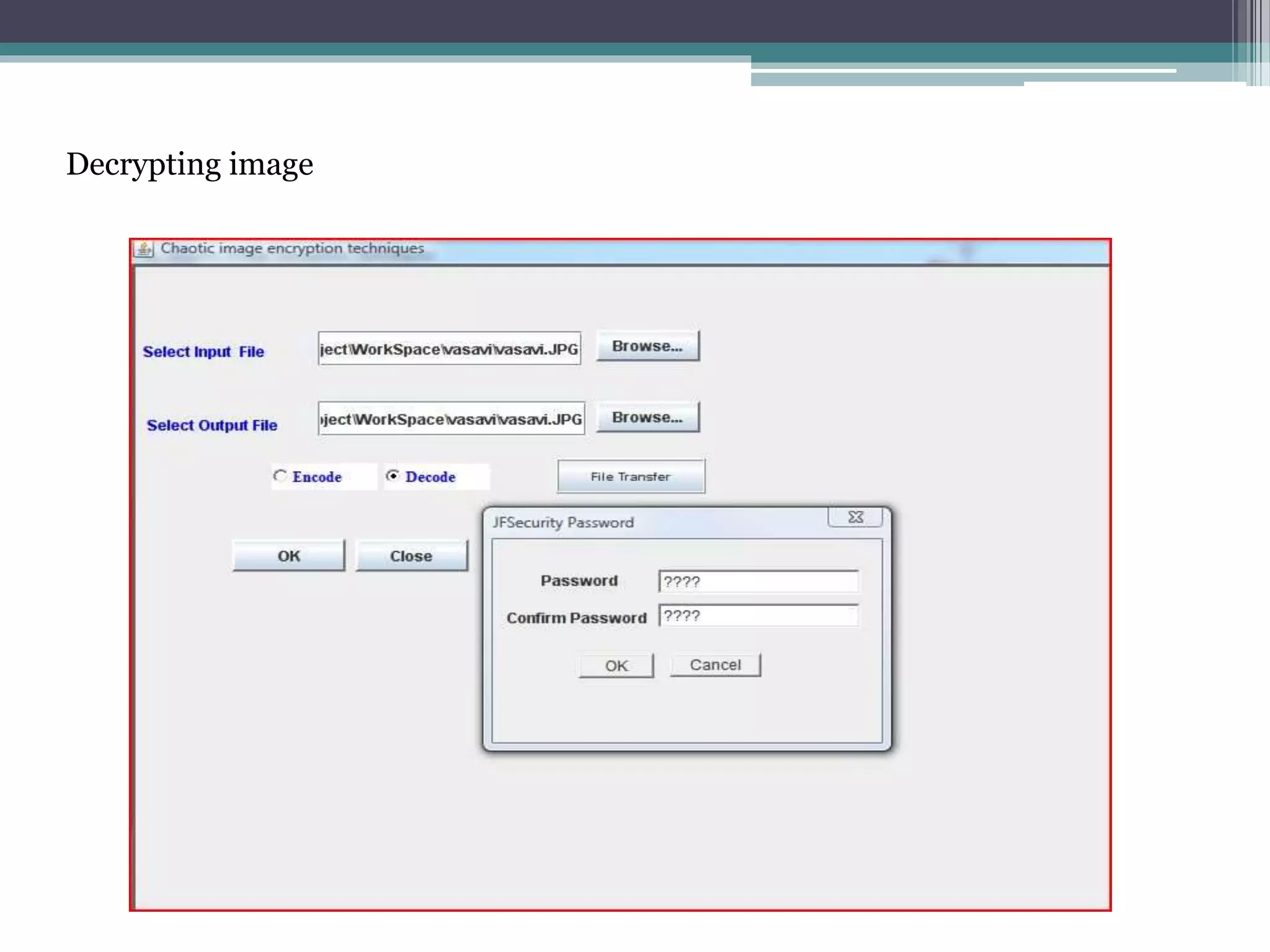
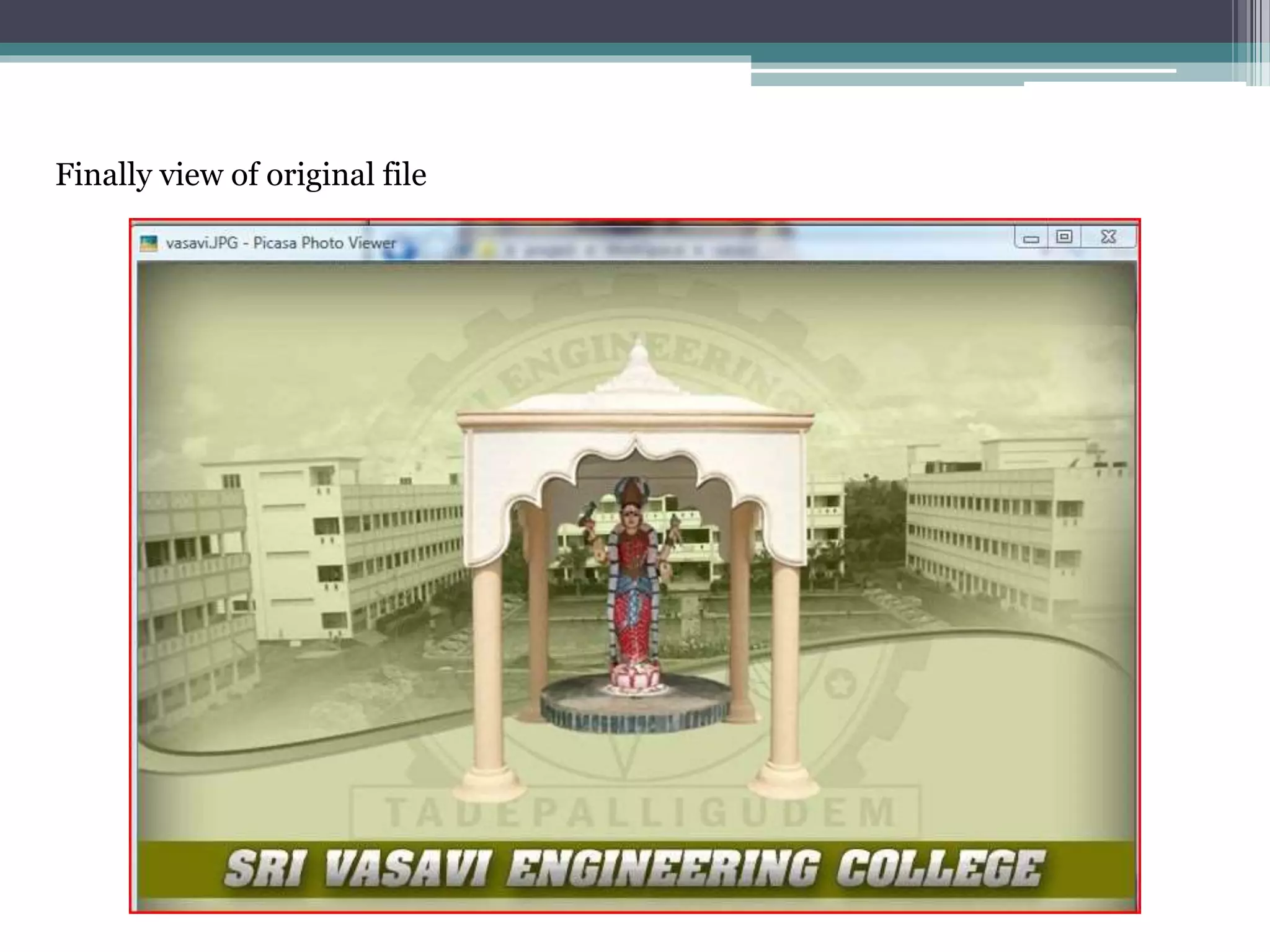
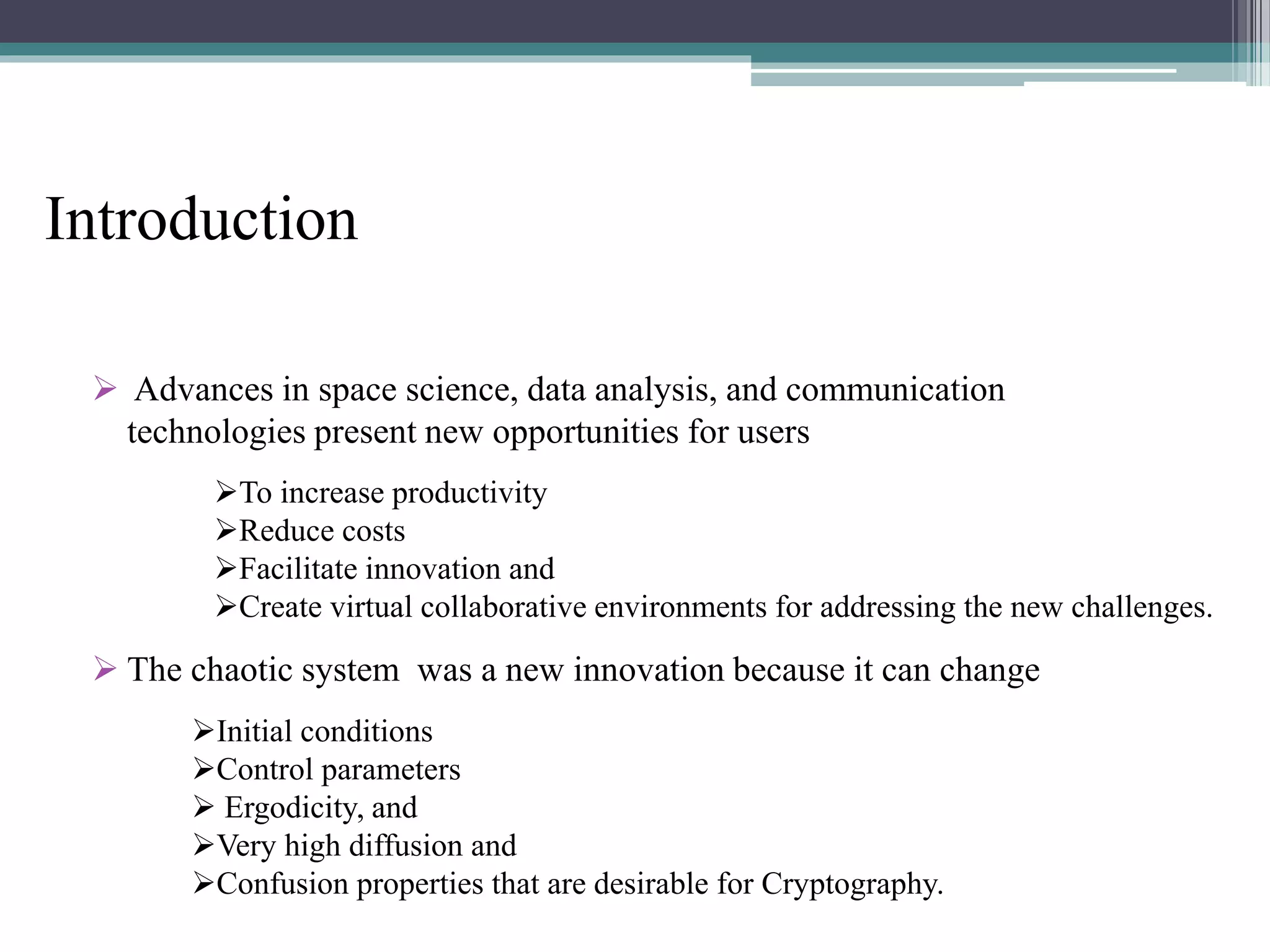
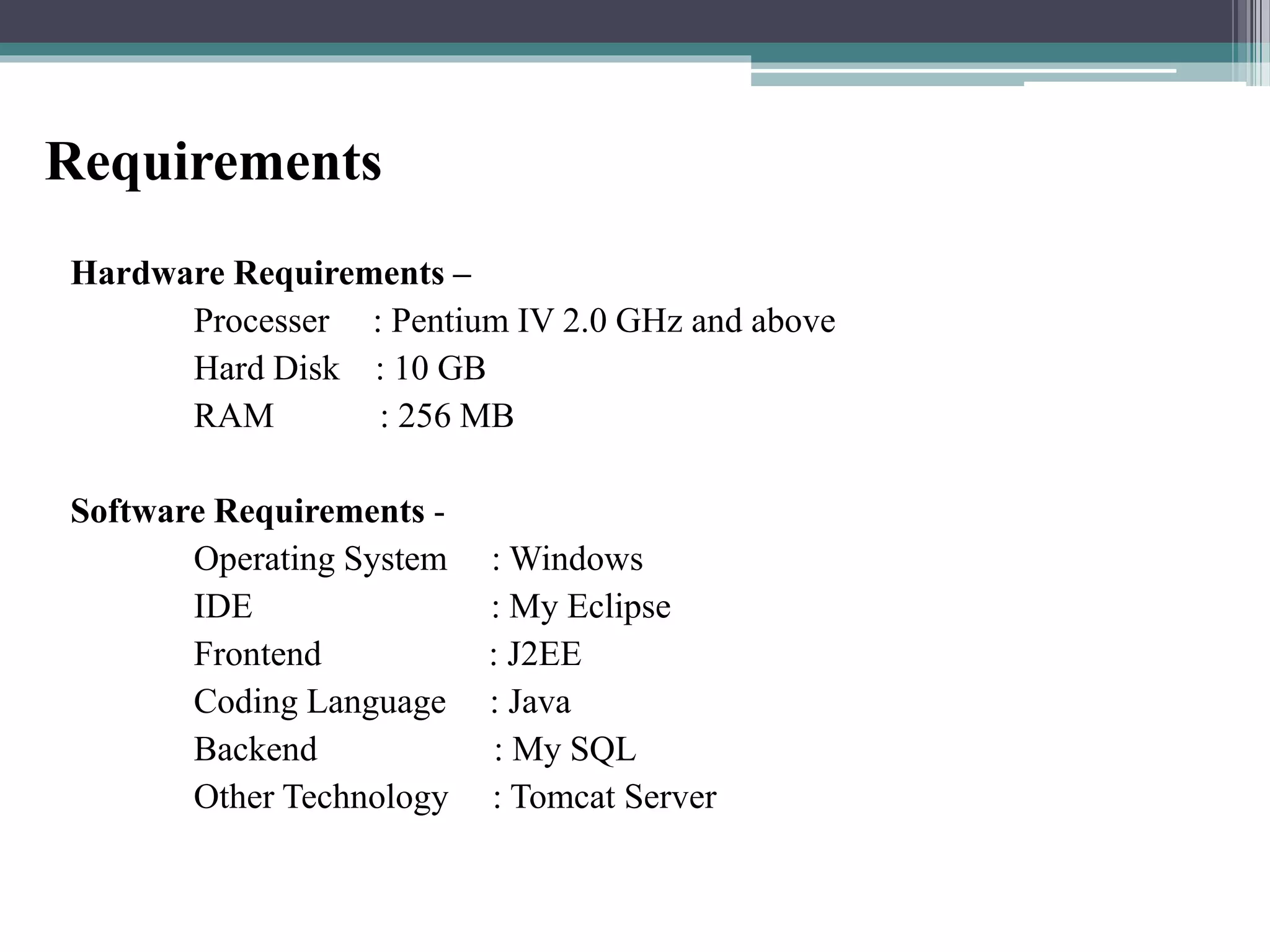
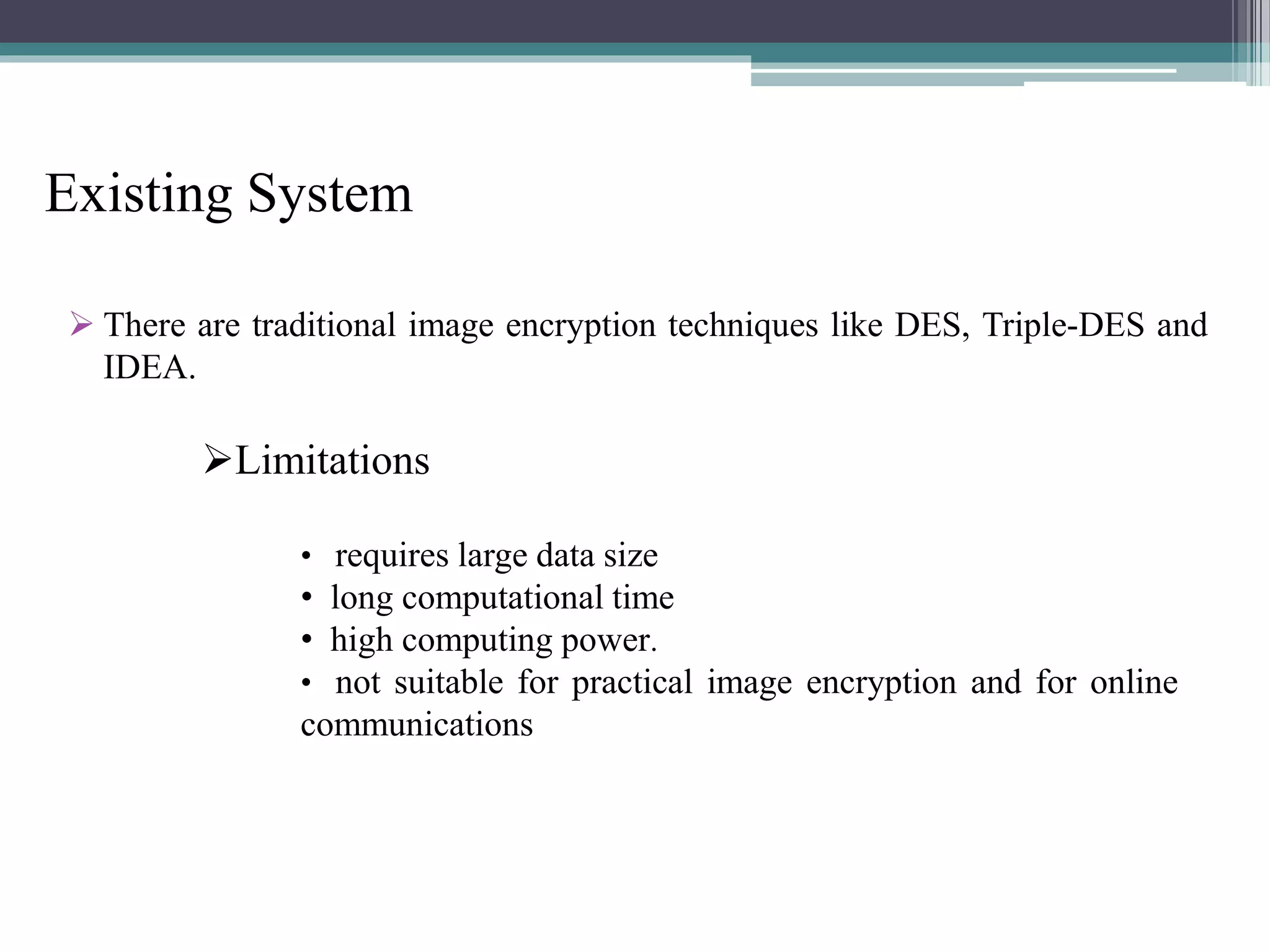
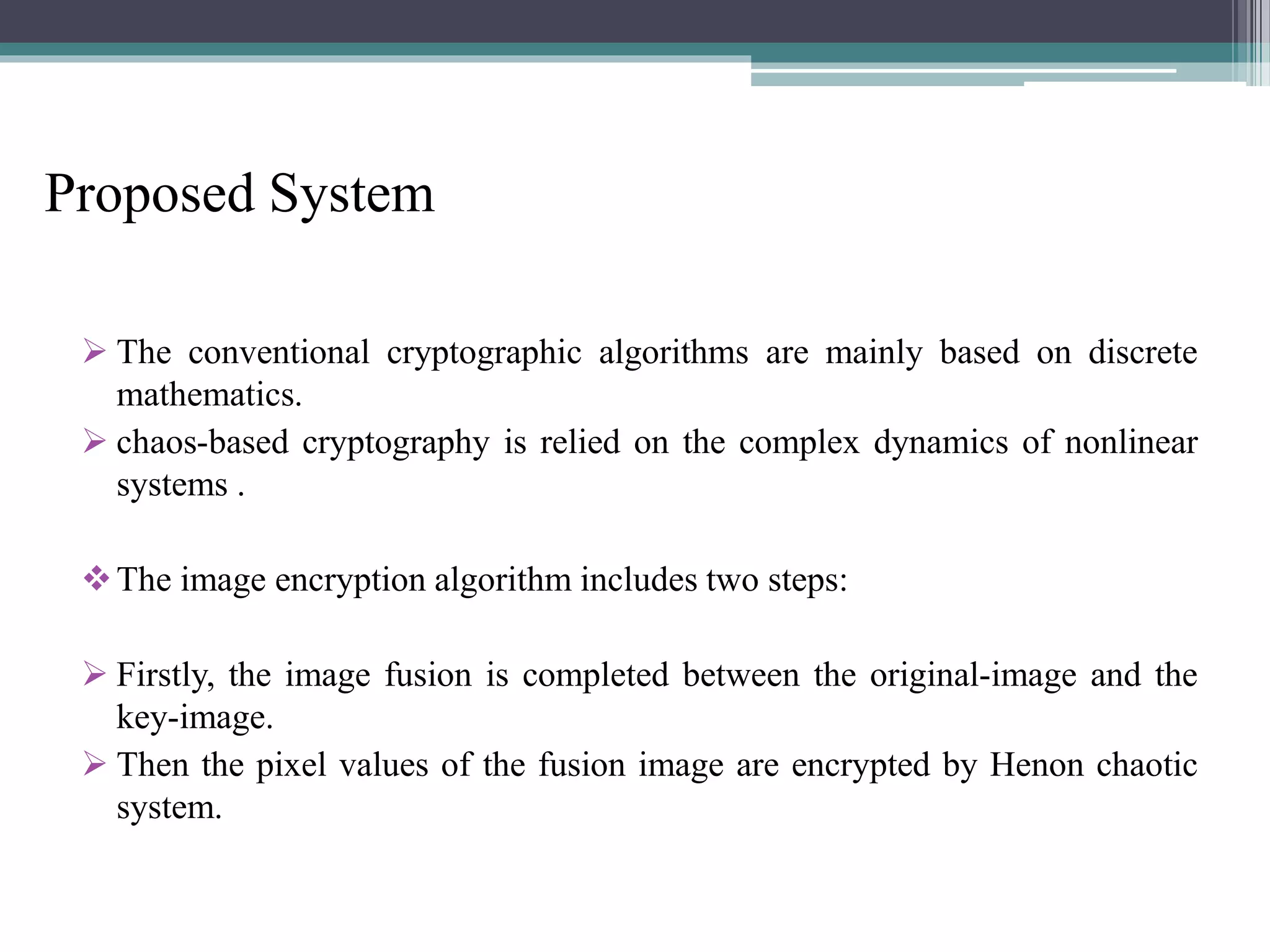
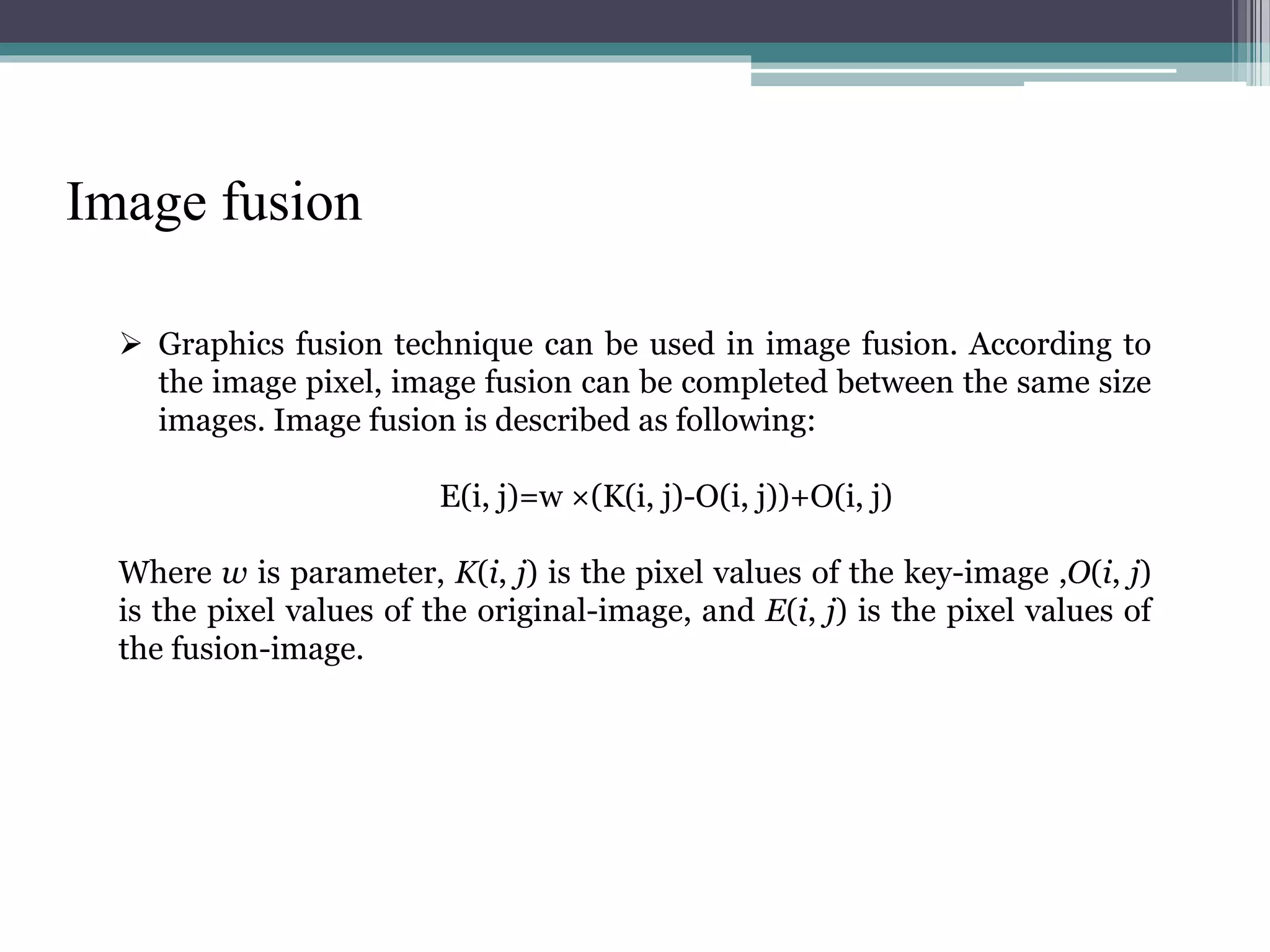
The document proposes a chaotic image encryption technique using Henon chaotic systems. It consists of two main steps: 1) Image fusion between the original image and a key image. 2) Encrypting the pixel values of the fused image using a Henon chaotic map. The technique aims to provide high security with less computational time compared to traditional encryption methods. Experimental results show the algorithm is sensitive to keys and resistant to brute force attacks. The technique can be used for applications like secure internet image transmission.



![Encryption by Henon chaotic Algorithm In our scheme, Henon chaotic system is adopted to encrypt the fusion- image. Step1: The Henon chaotic system is converted into one-dimensional chaotic map which is defined as: Xi+2=1-aX2i+1+bxi Where a = 0.3 , b∈[1.07,1.4] .The parameter a , the parameter b , initial value x0 and initial value x1 may represent the key. Step2: Set encryption key for the fusion-image, including structural parameters a , b and initial values x0 ,x1 . After image fusion, we adopt Henon chaotic map to change the pixel values of the fusion-image.](https://image.slidesharecdn.com/batch17-140806114506-phpapp02/75/Image-Encryption-in-java-ppt-11-2048.jpg)