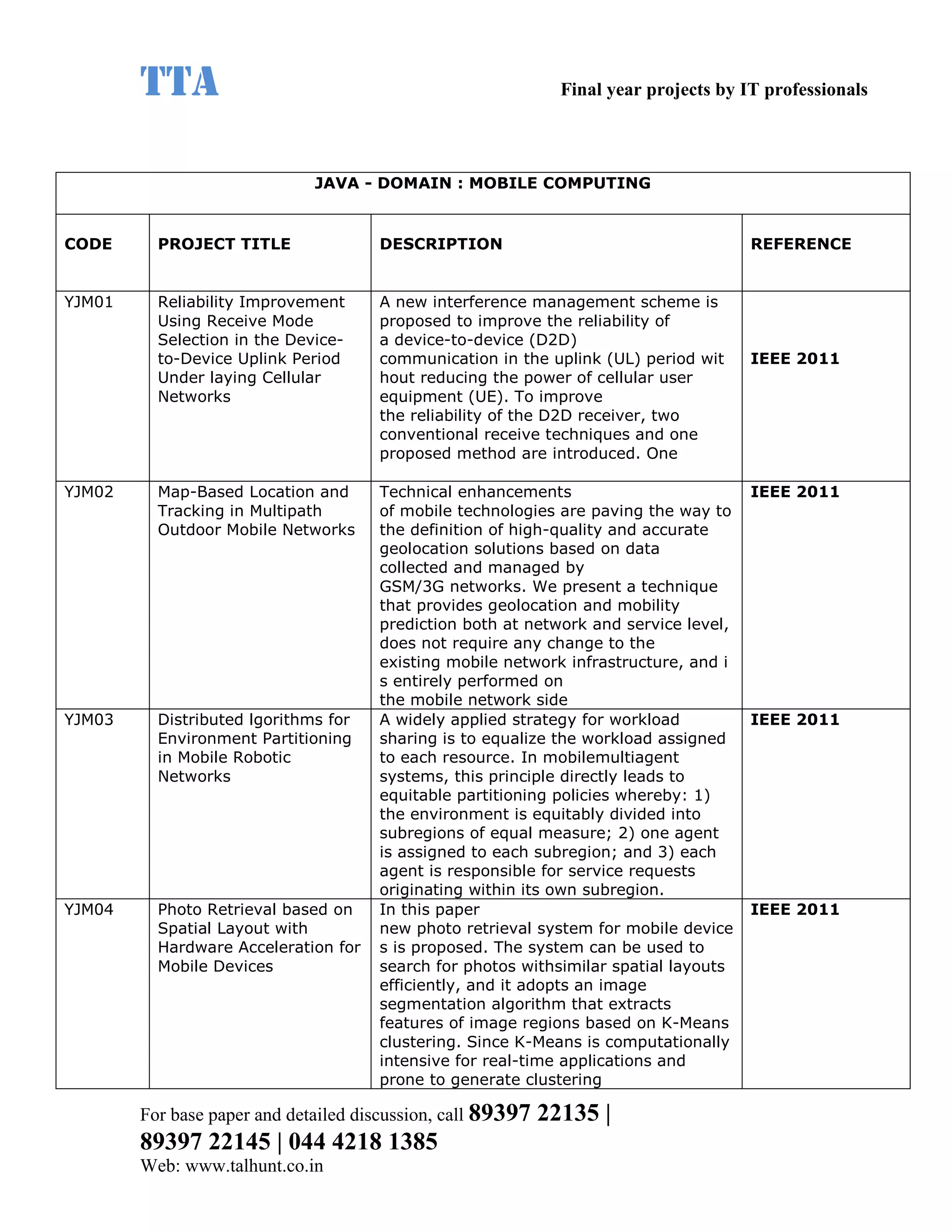
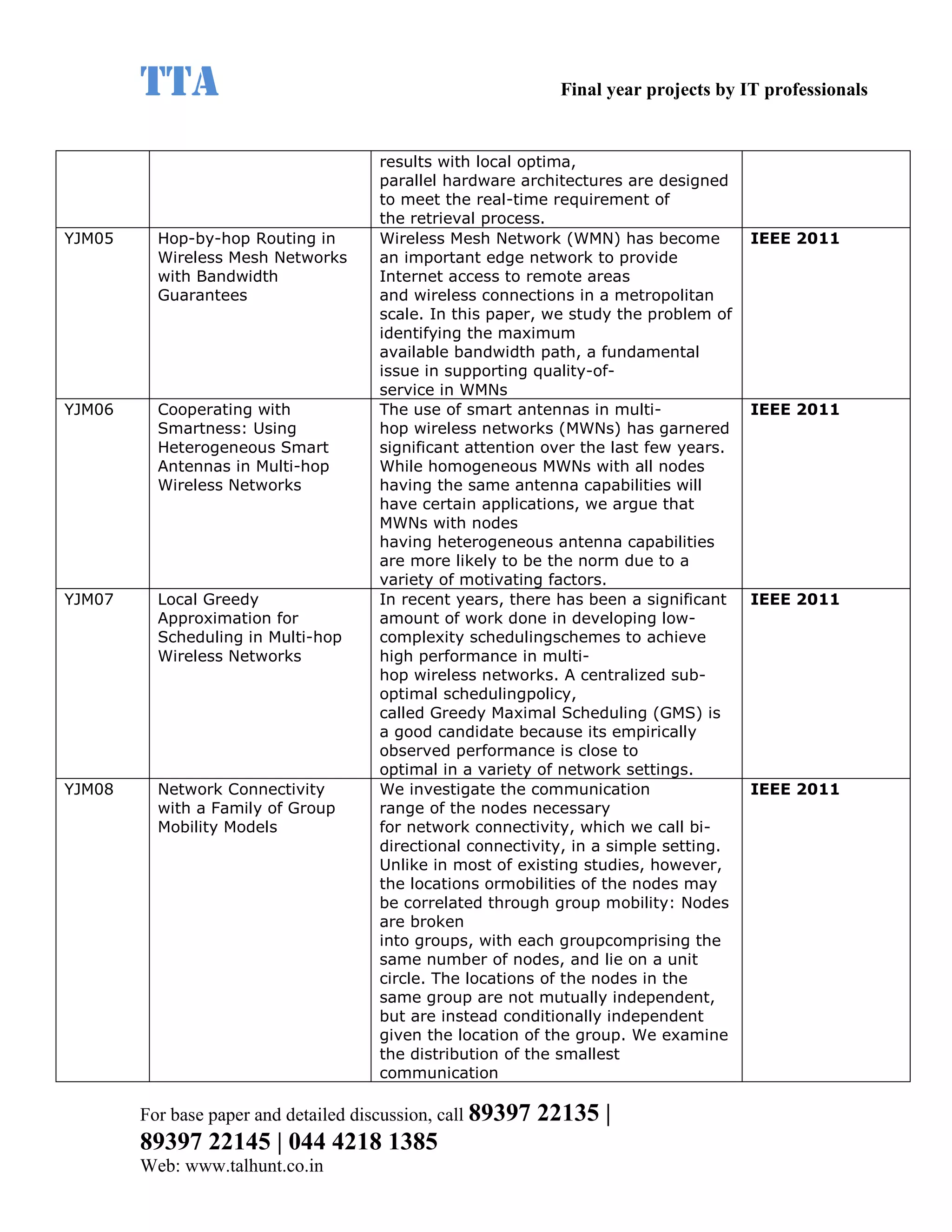
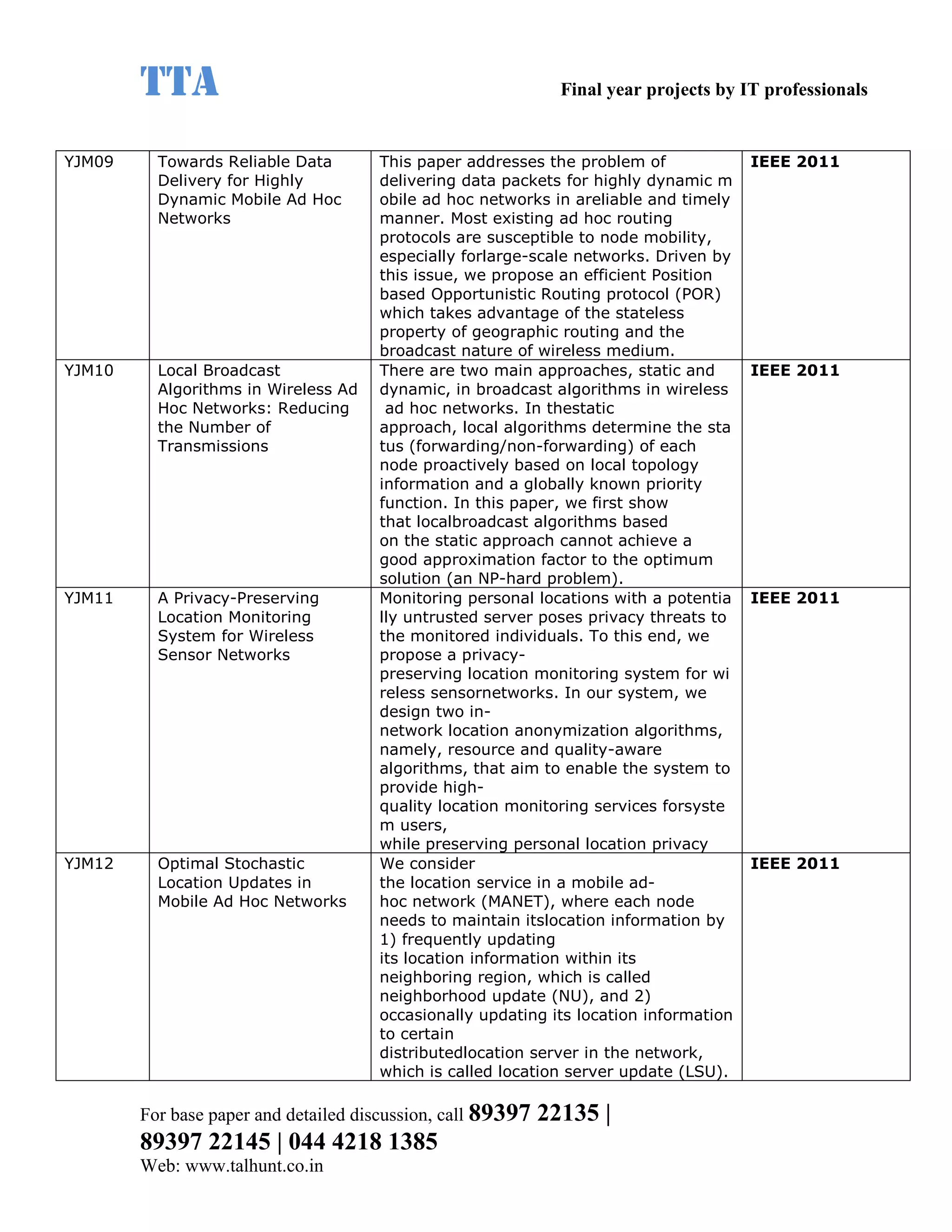
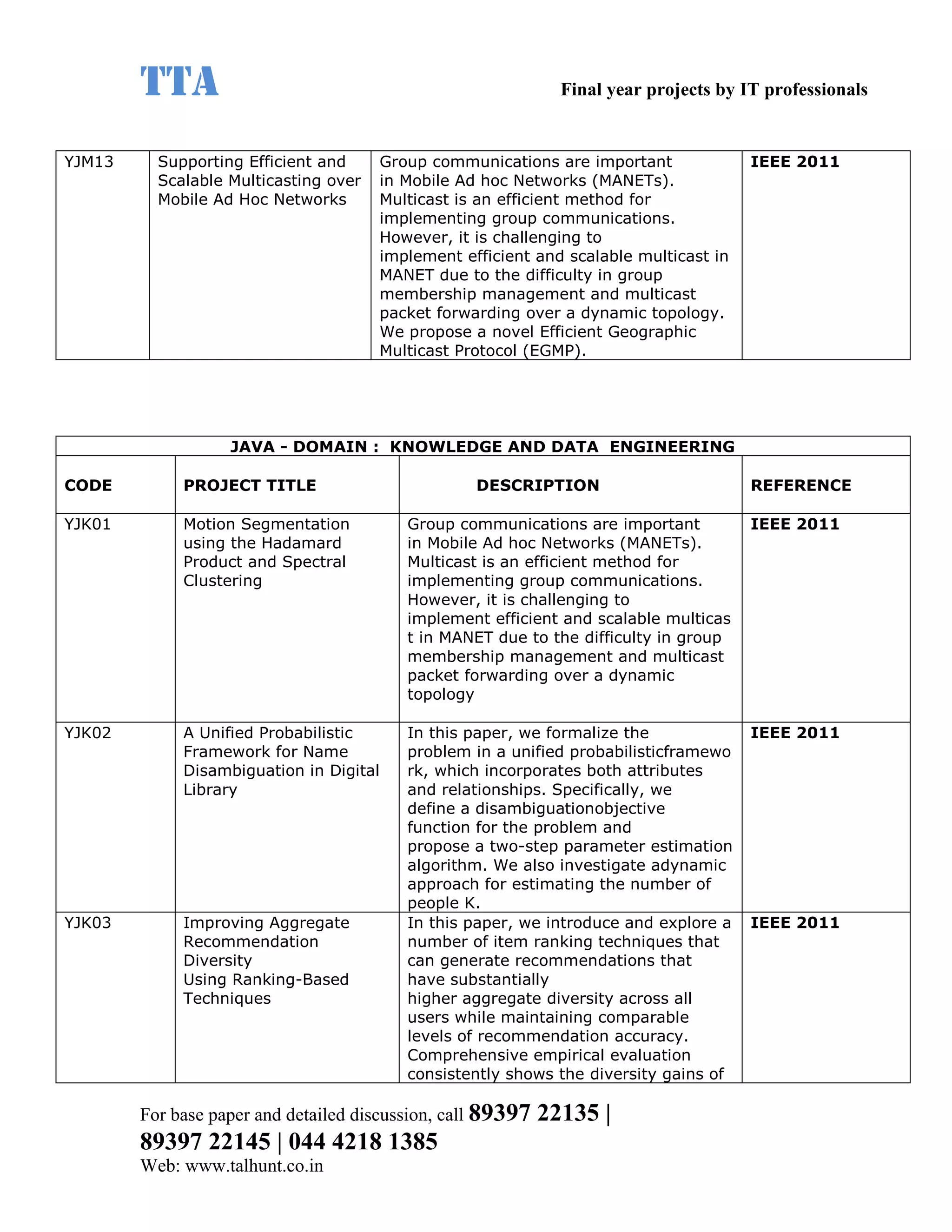
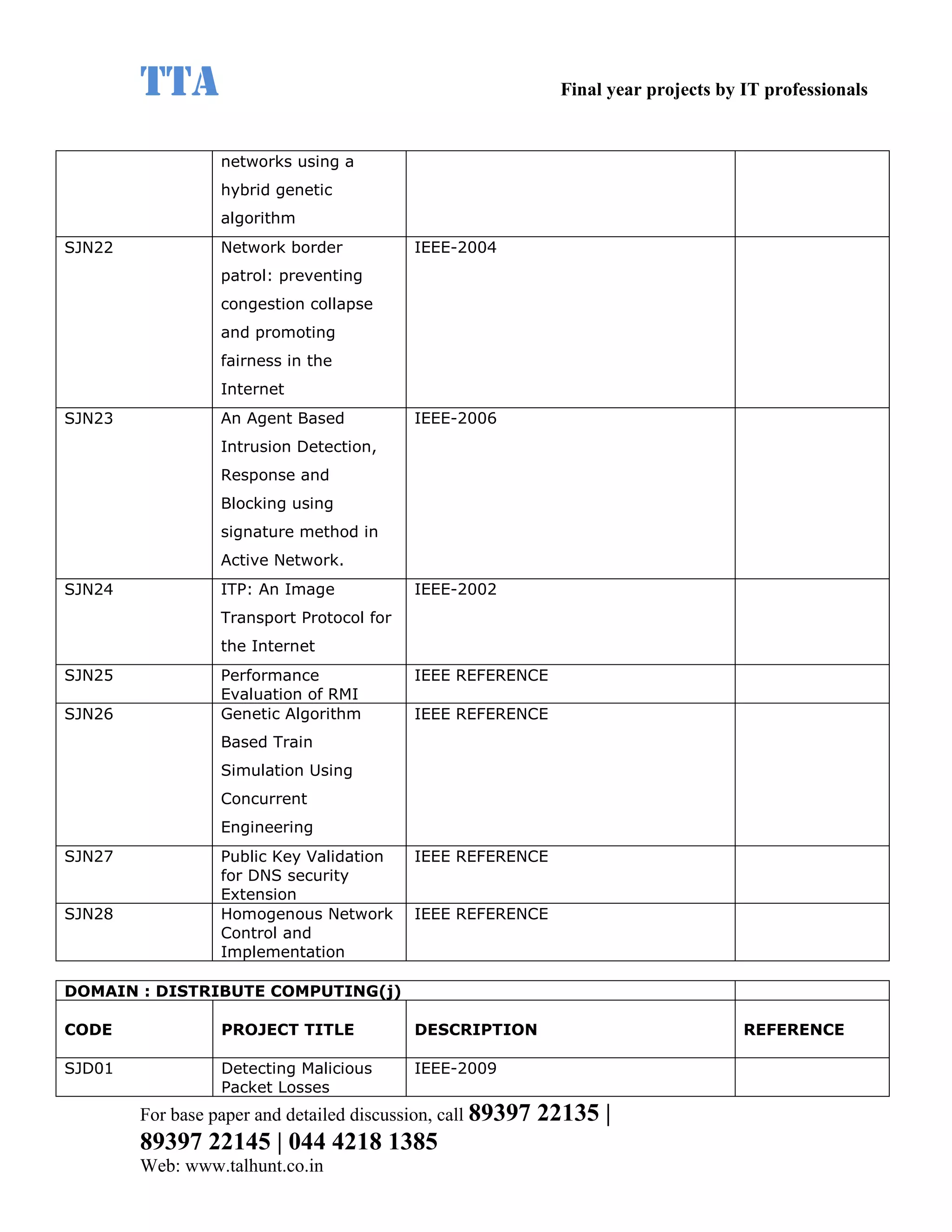
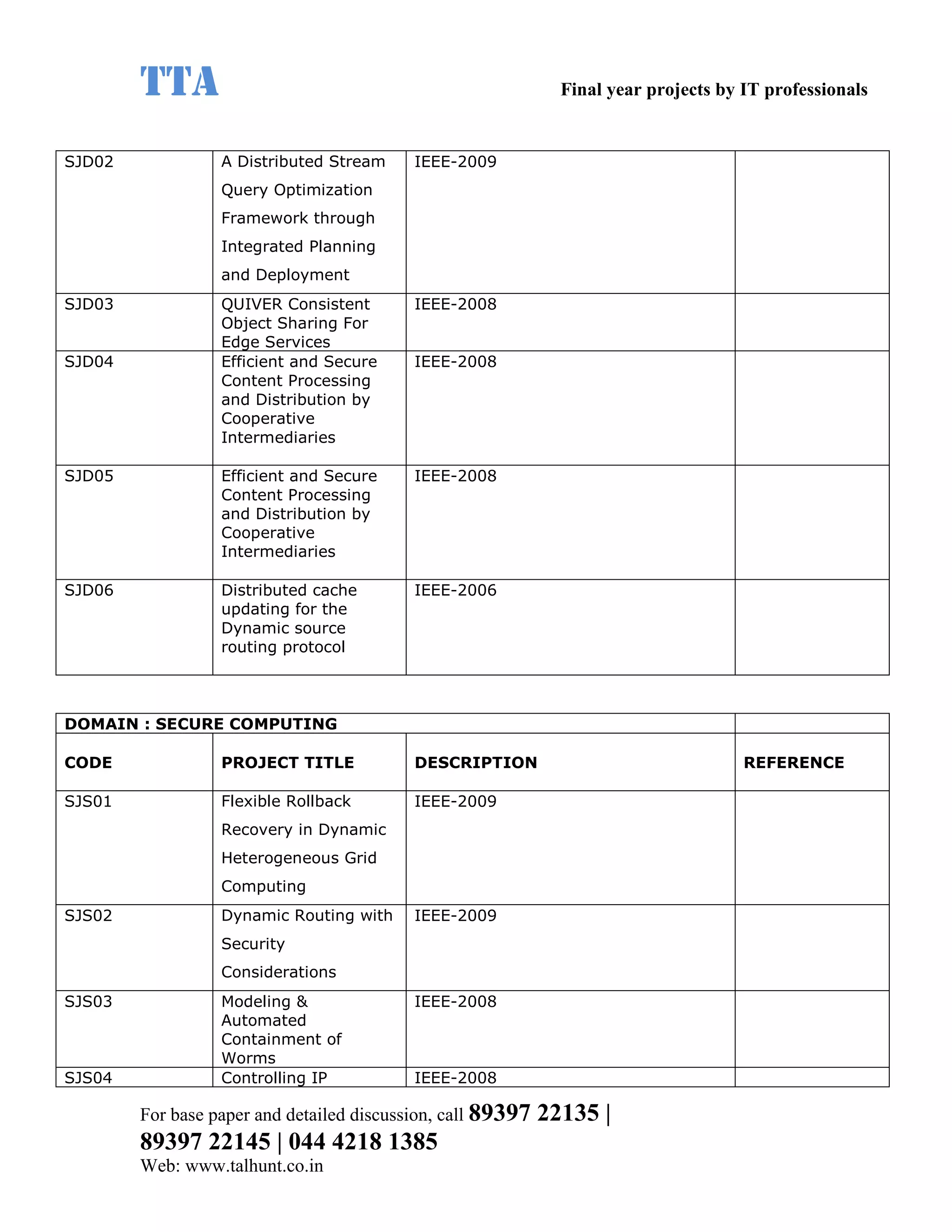
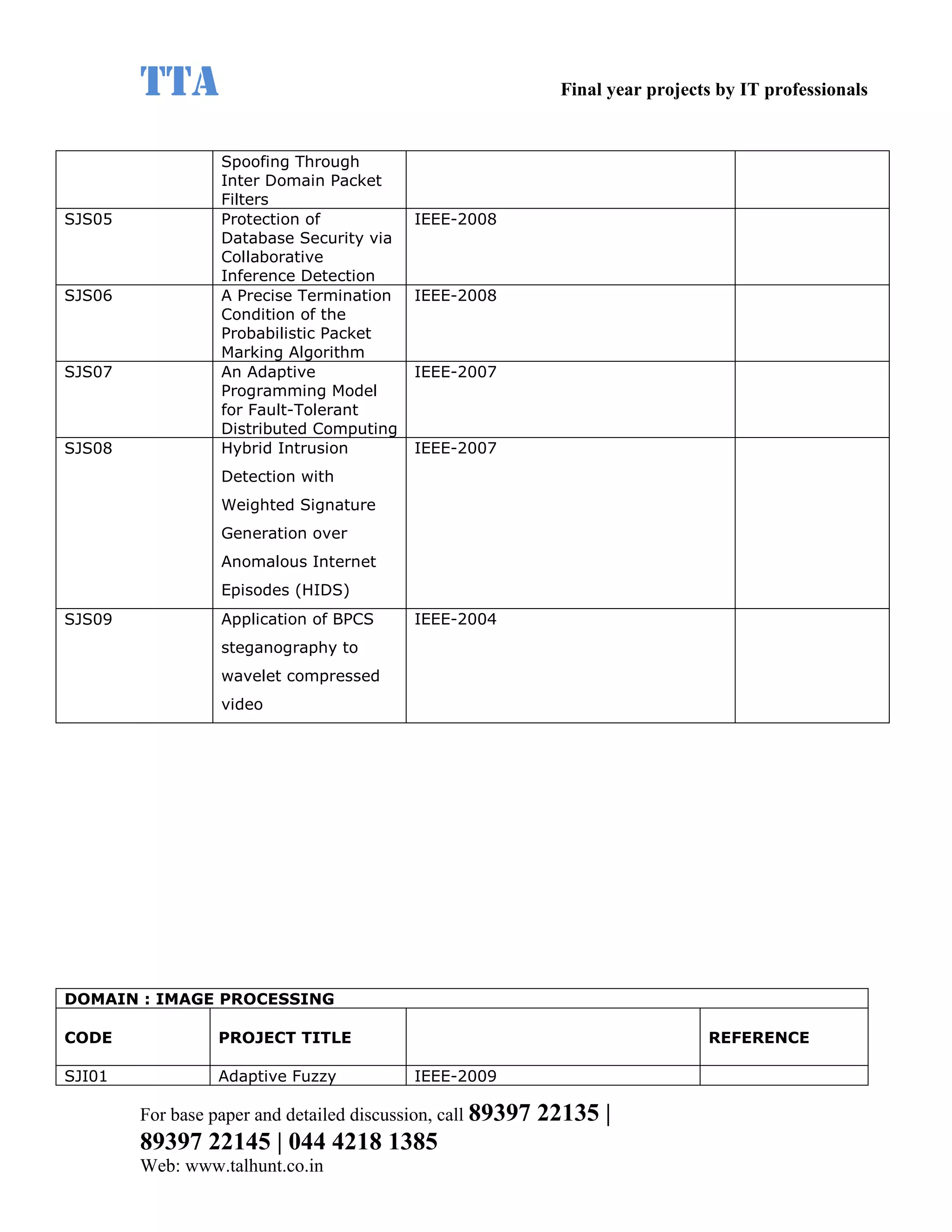
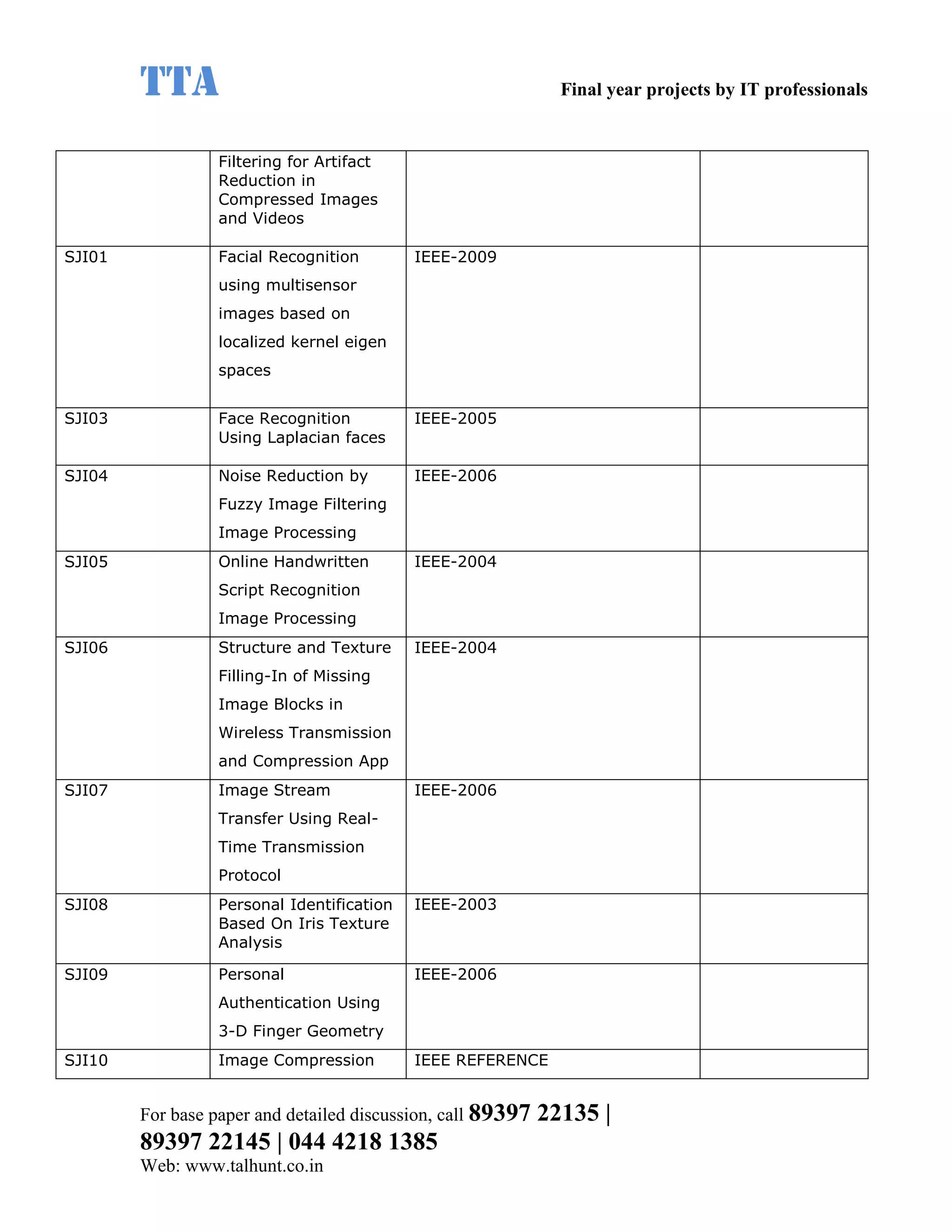
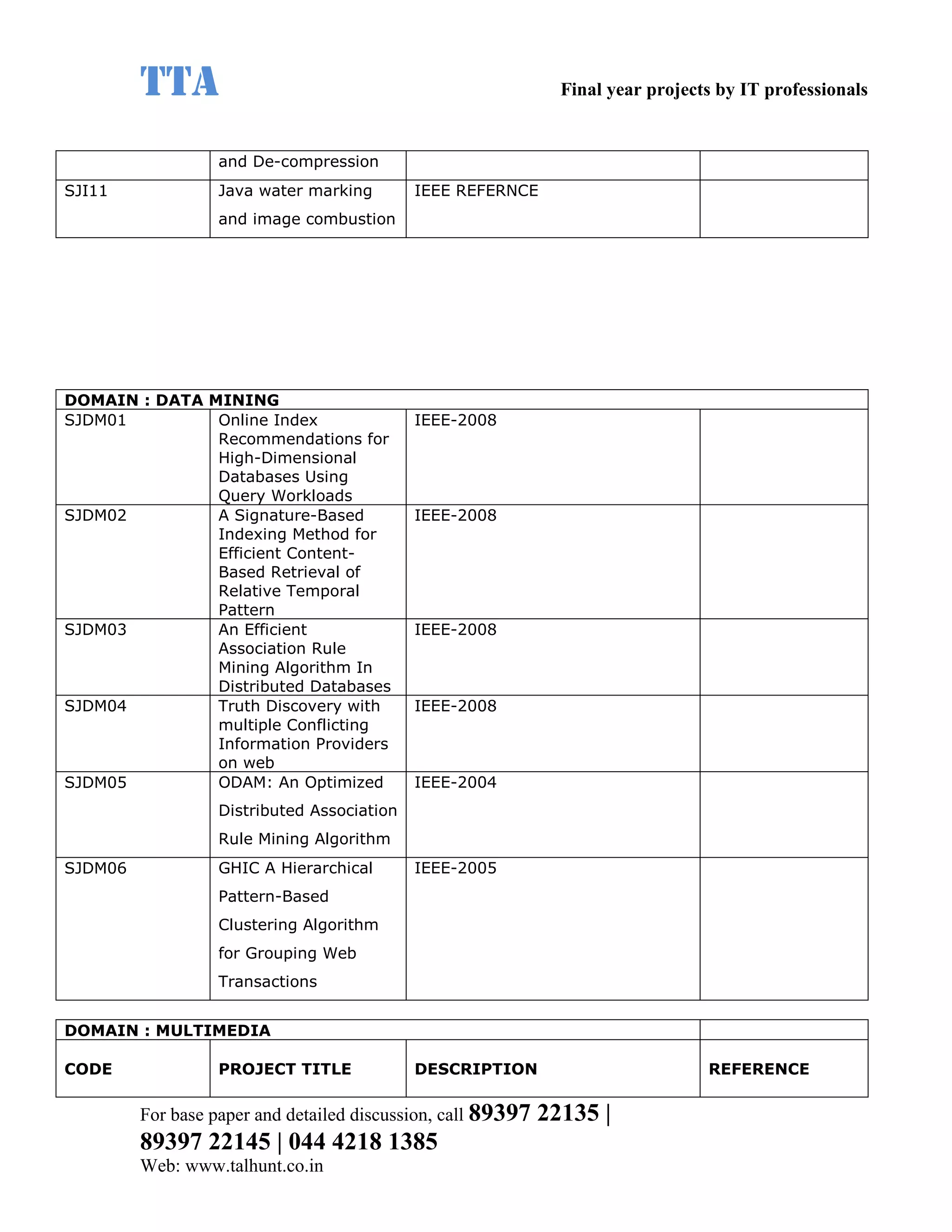
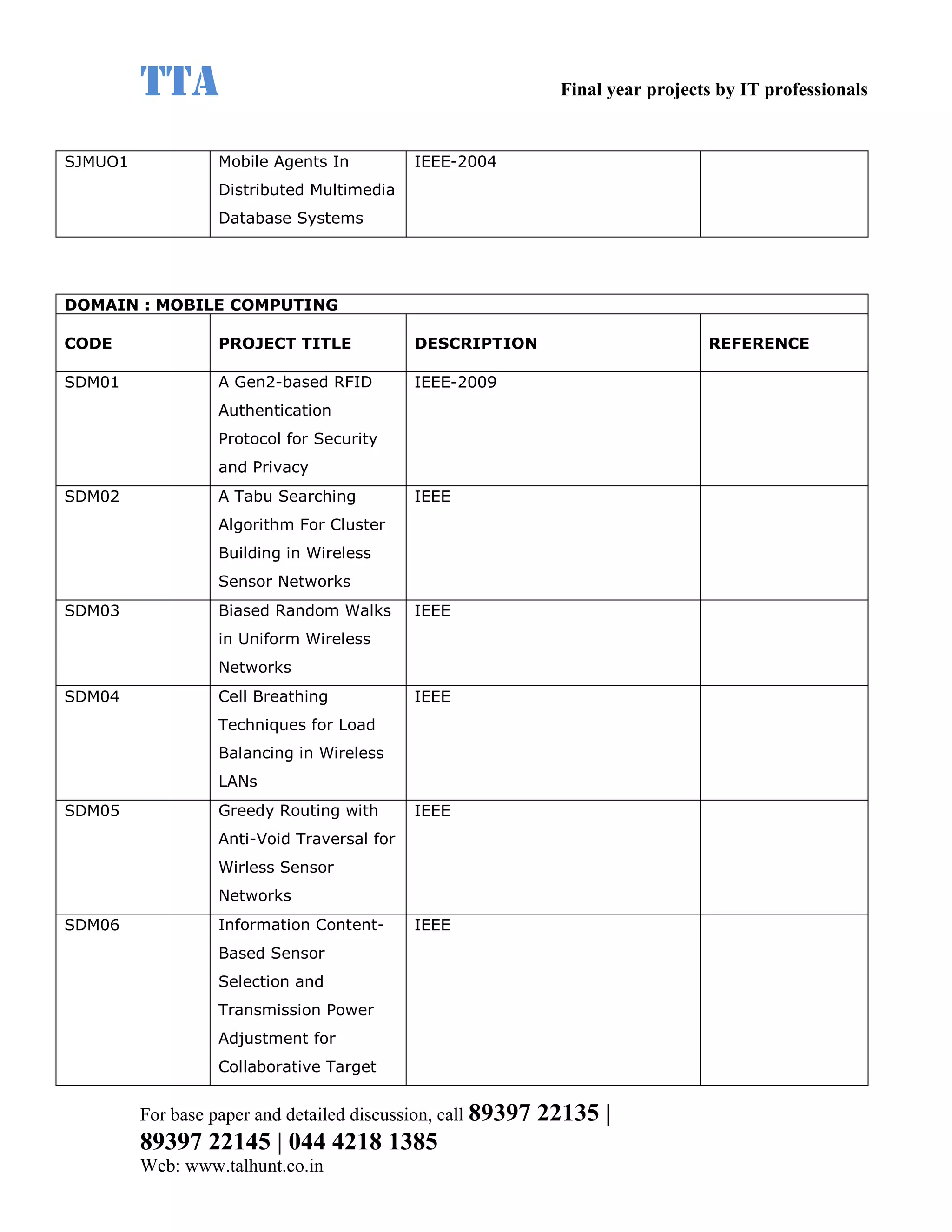
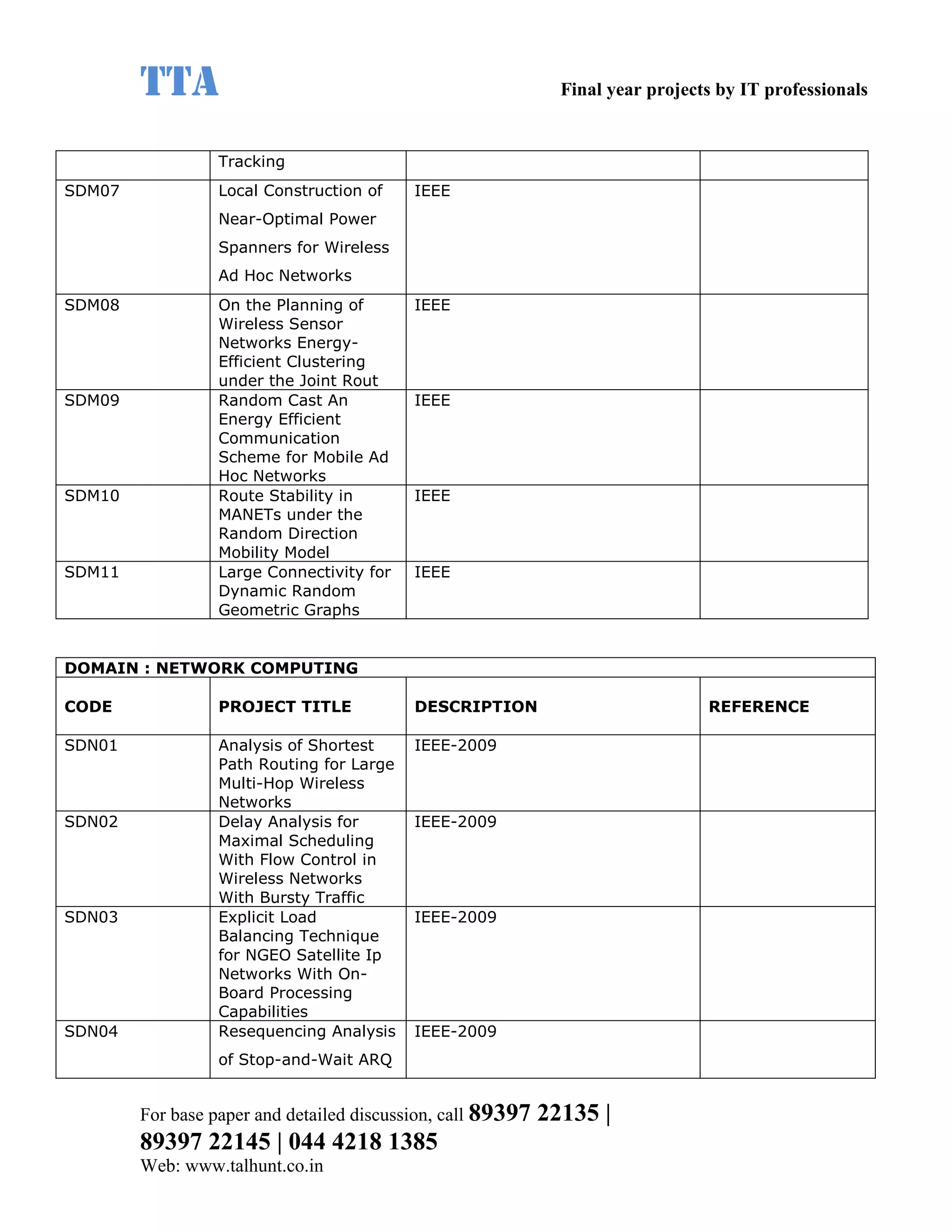
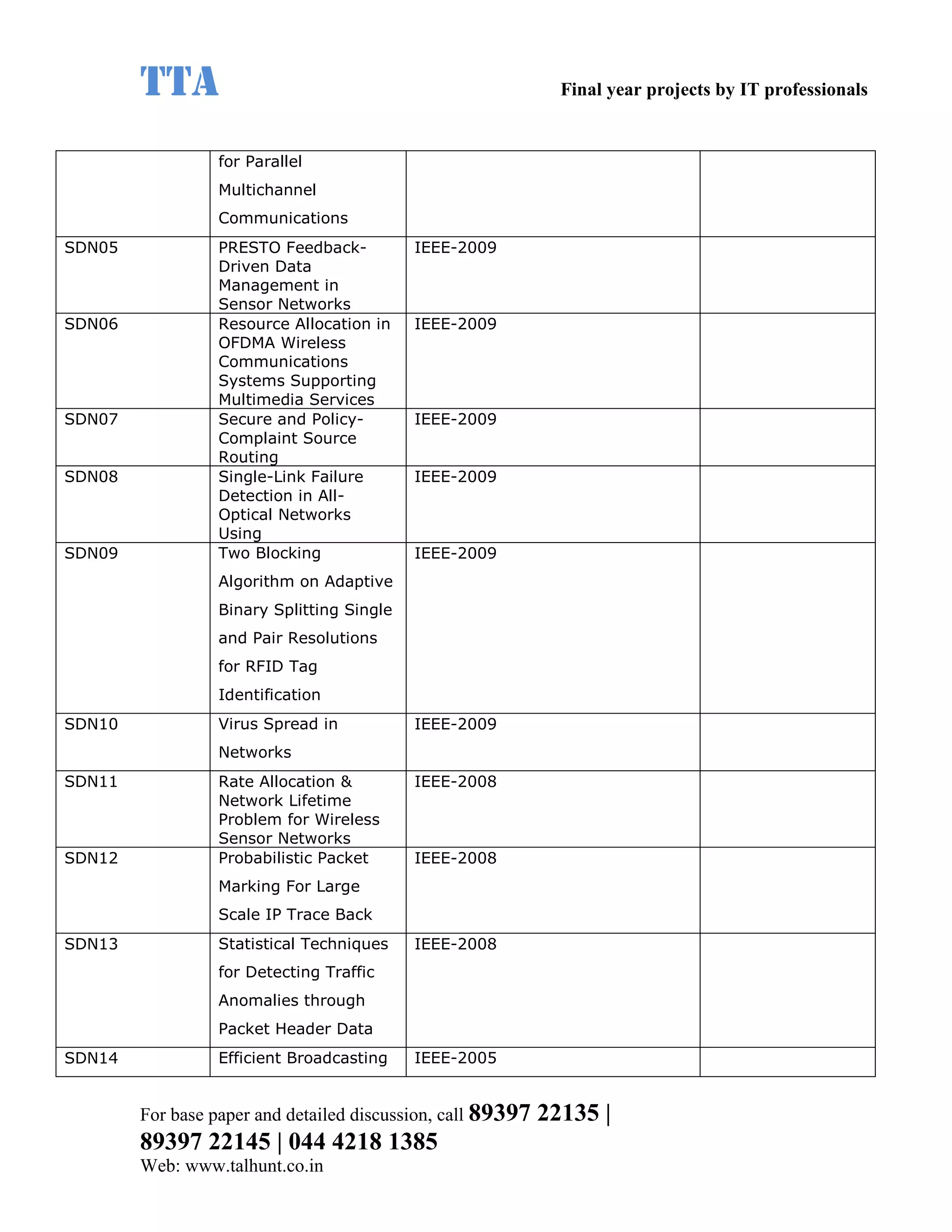
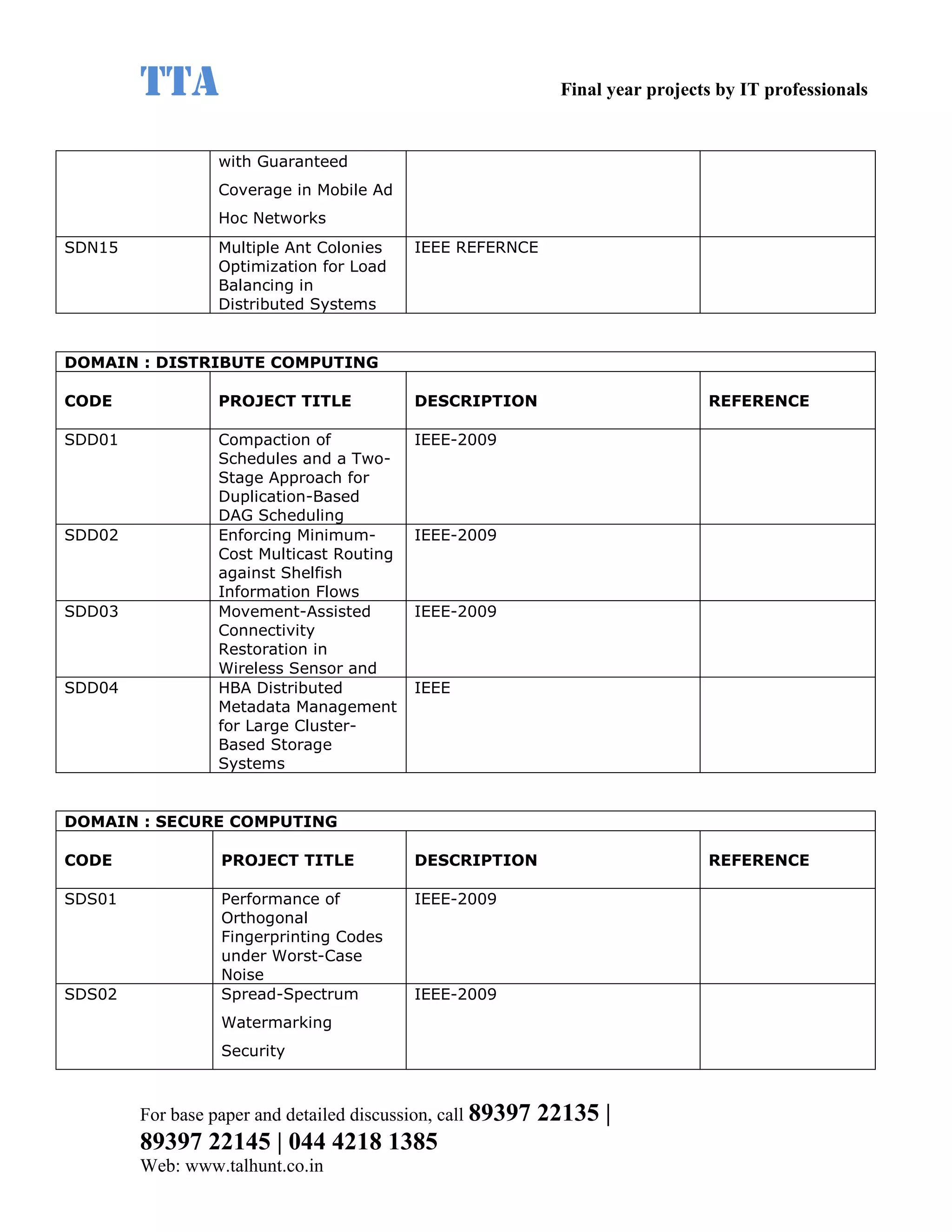
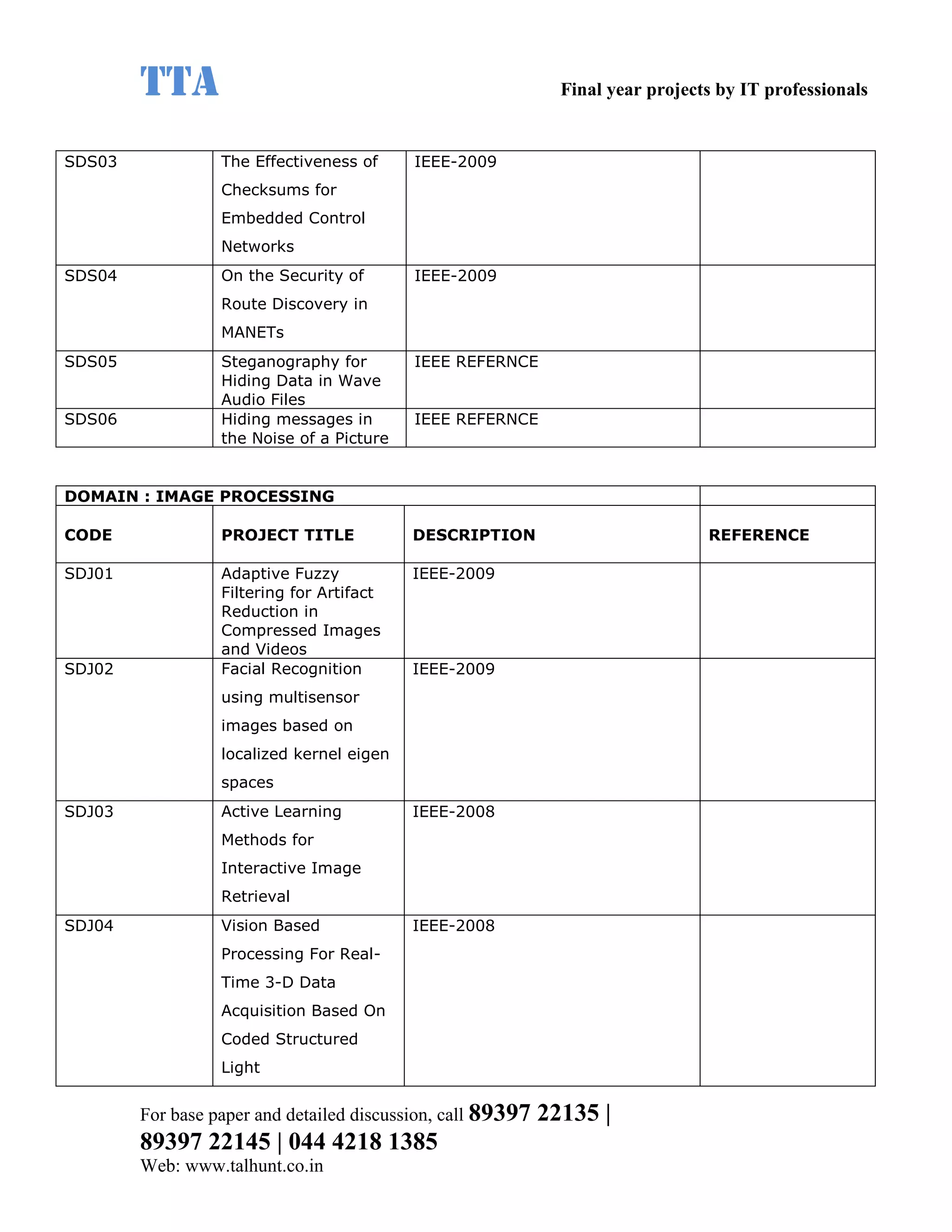
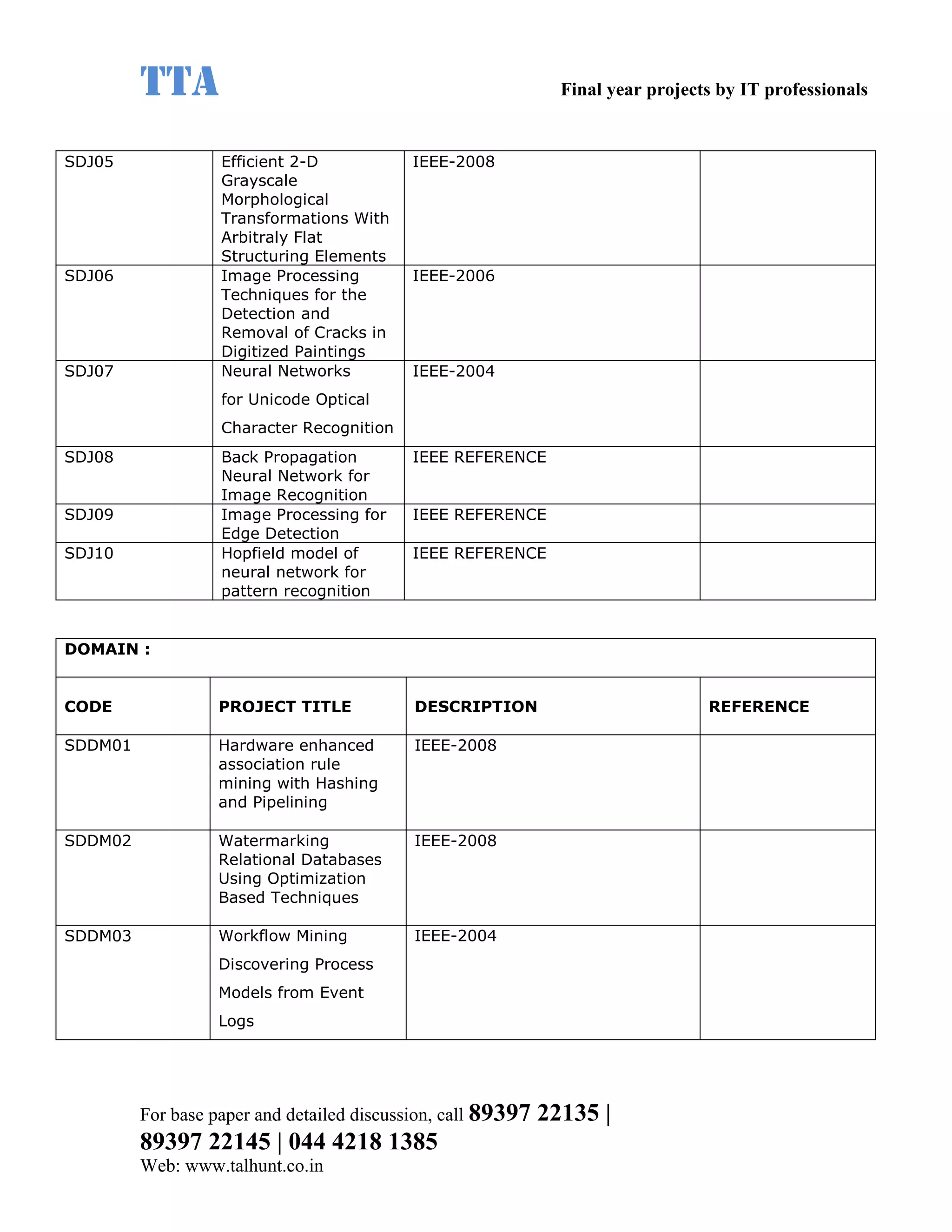
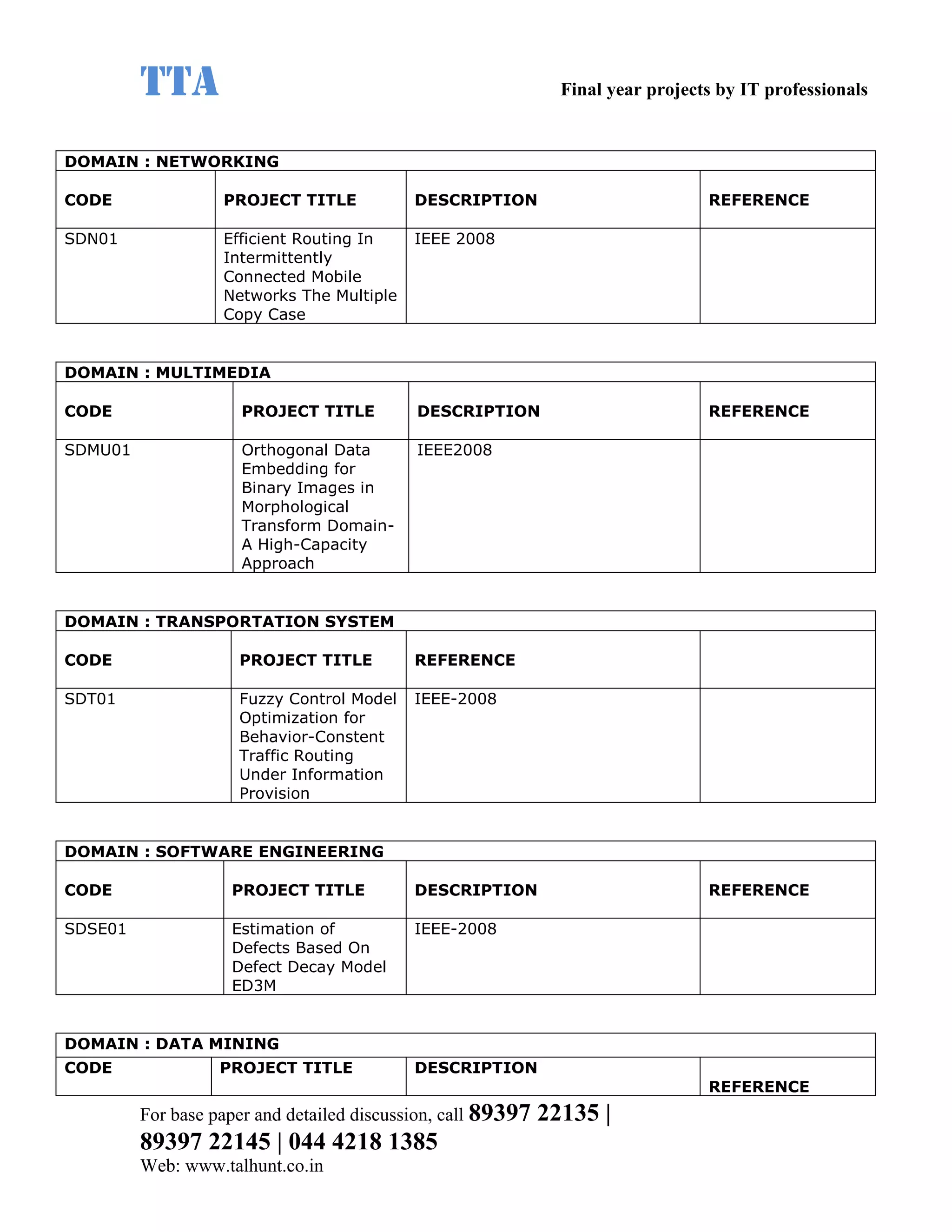
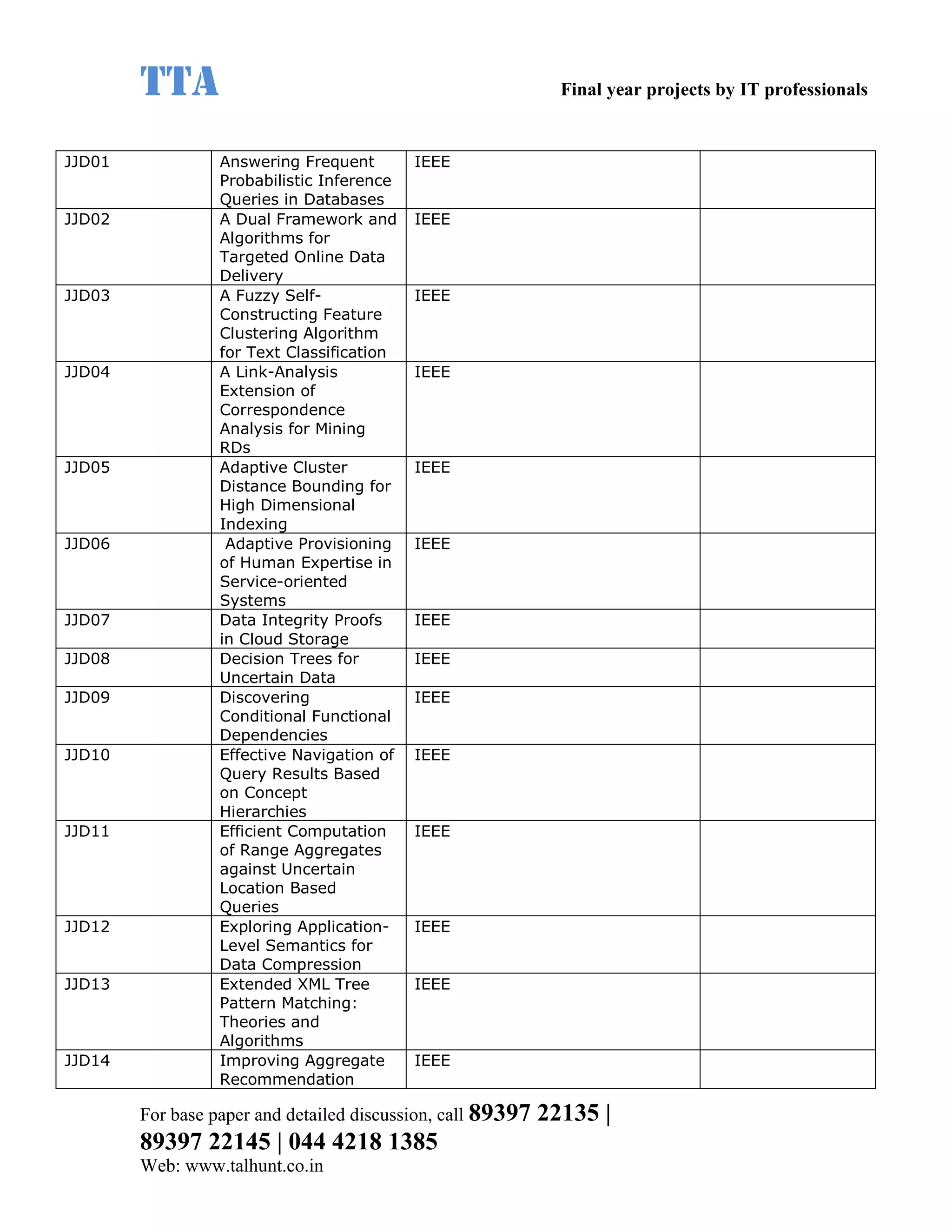
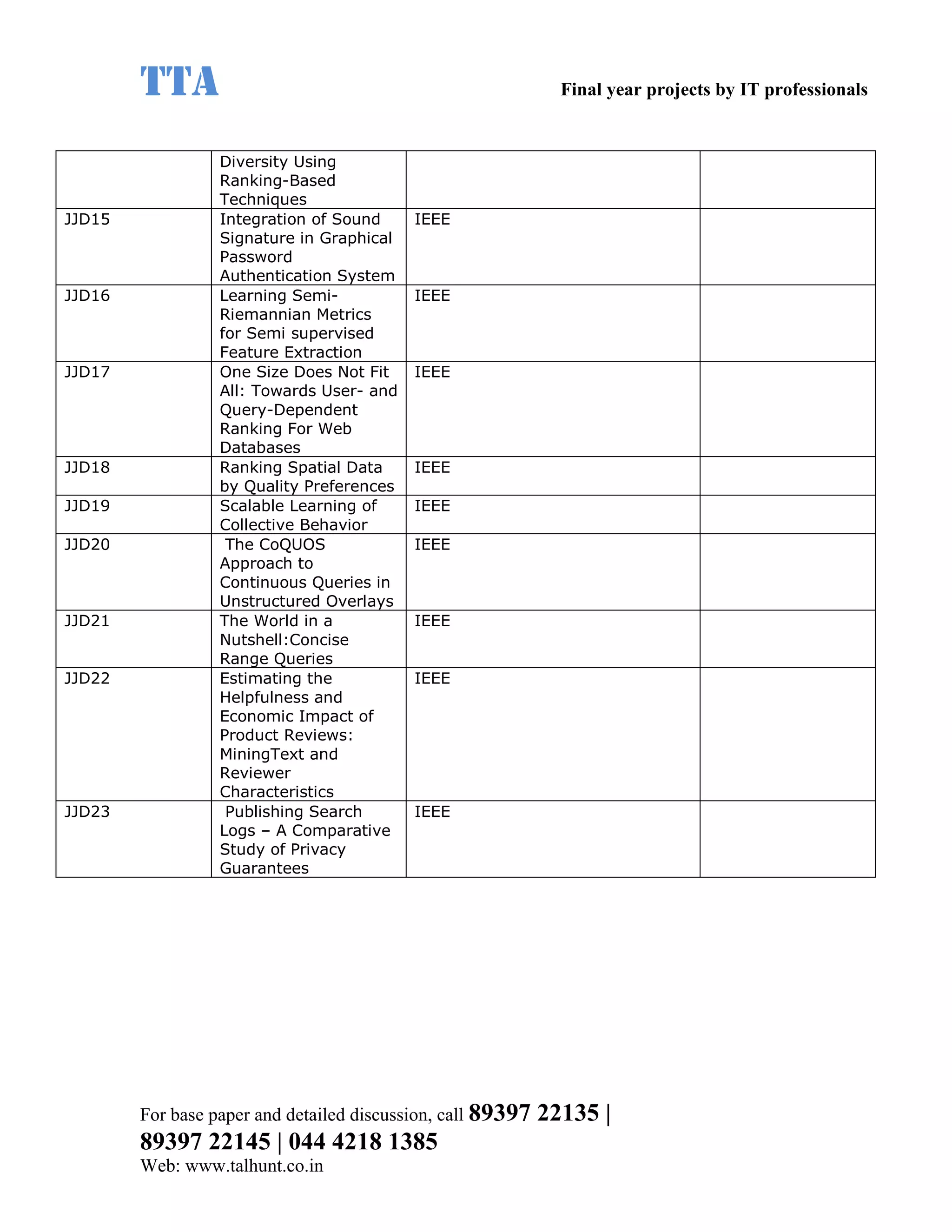
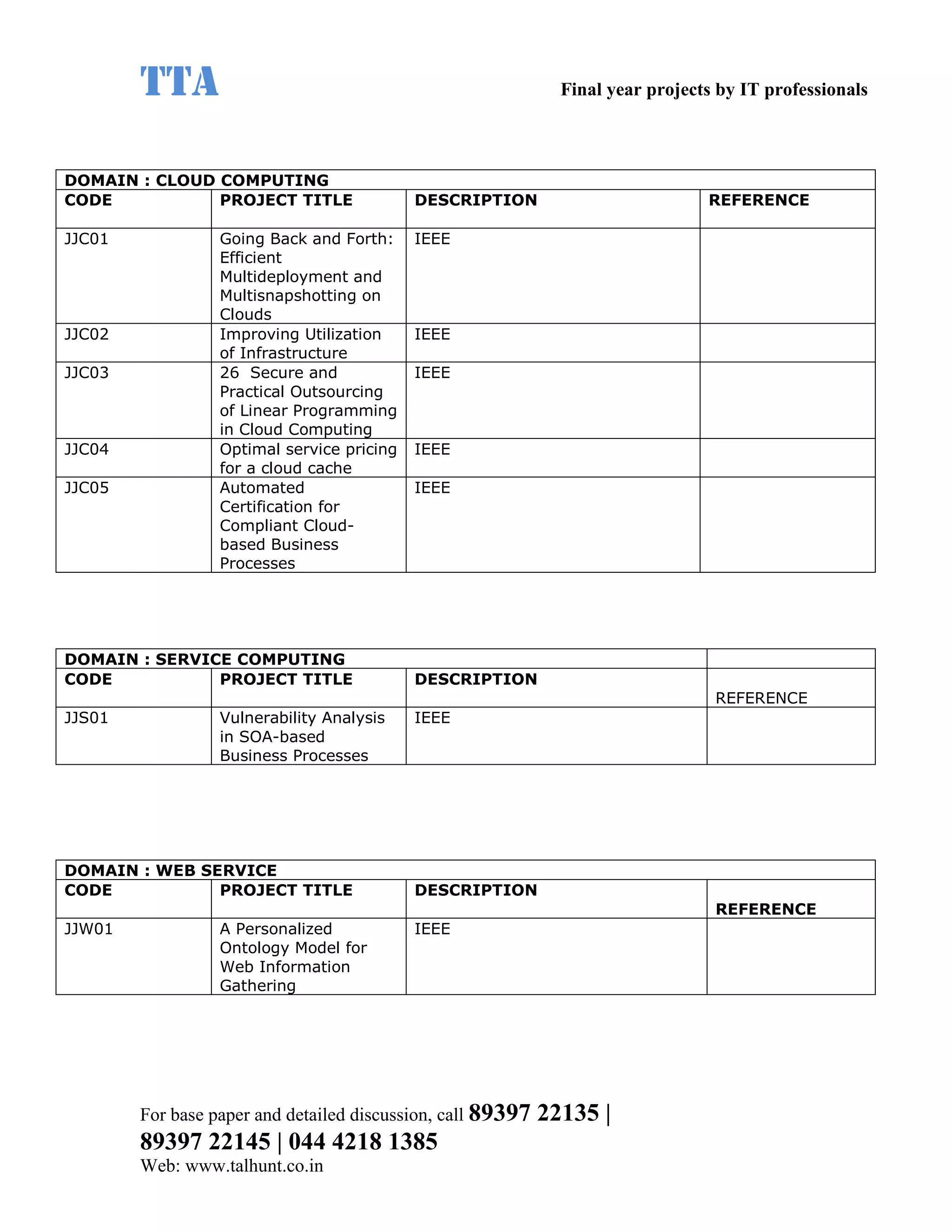
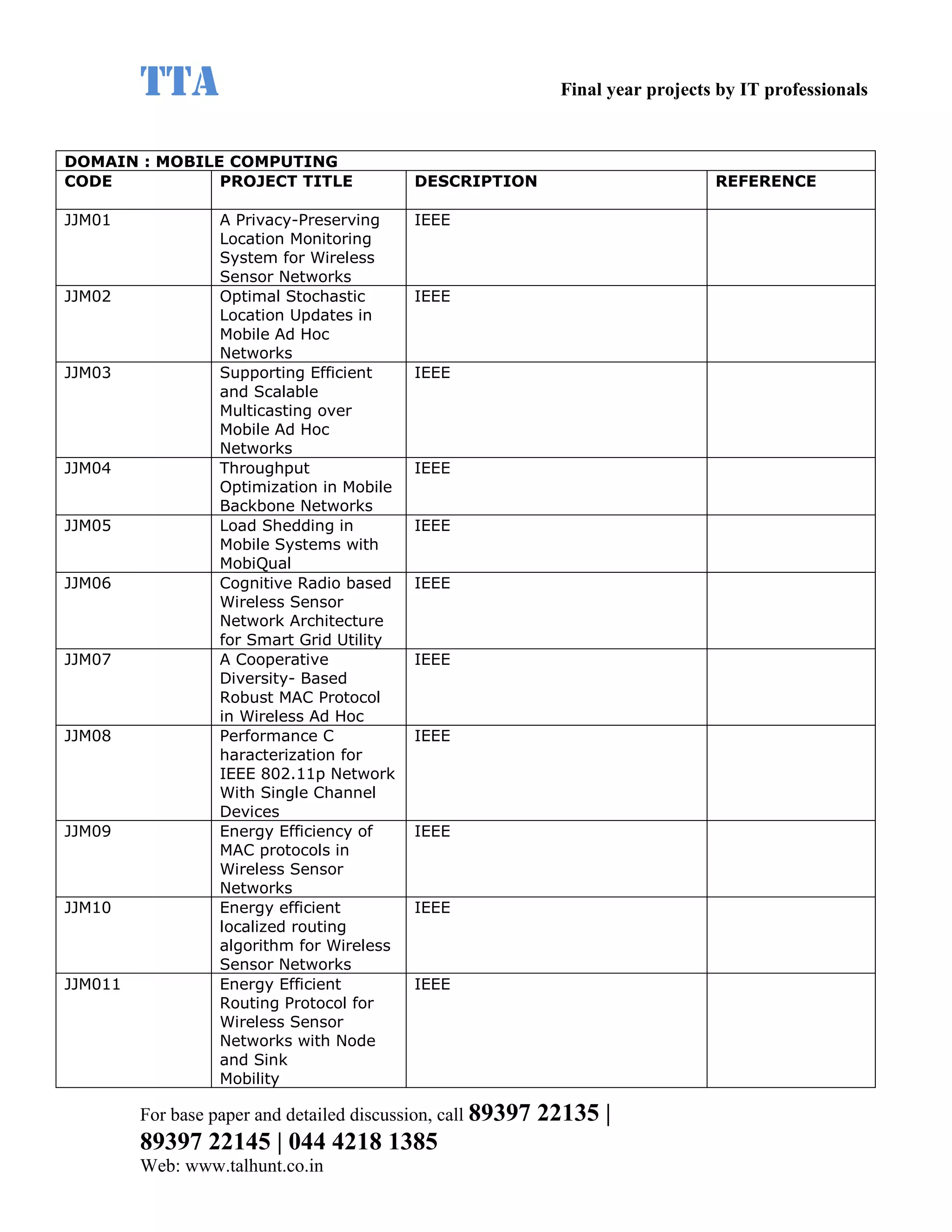
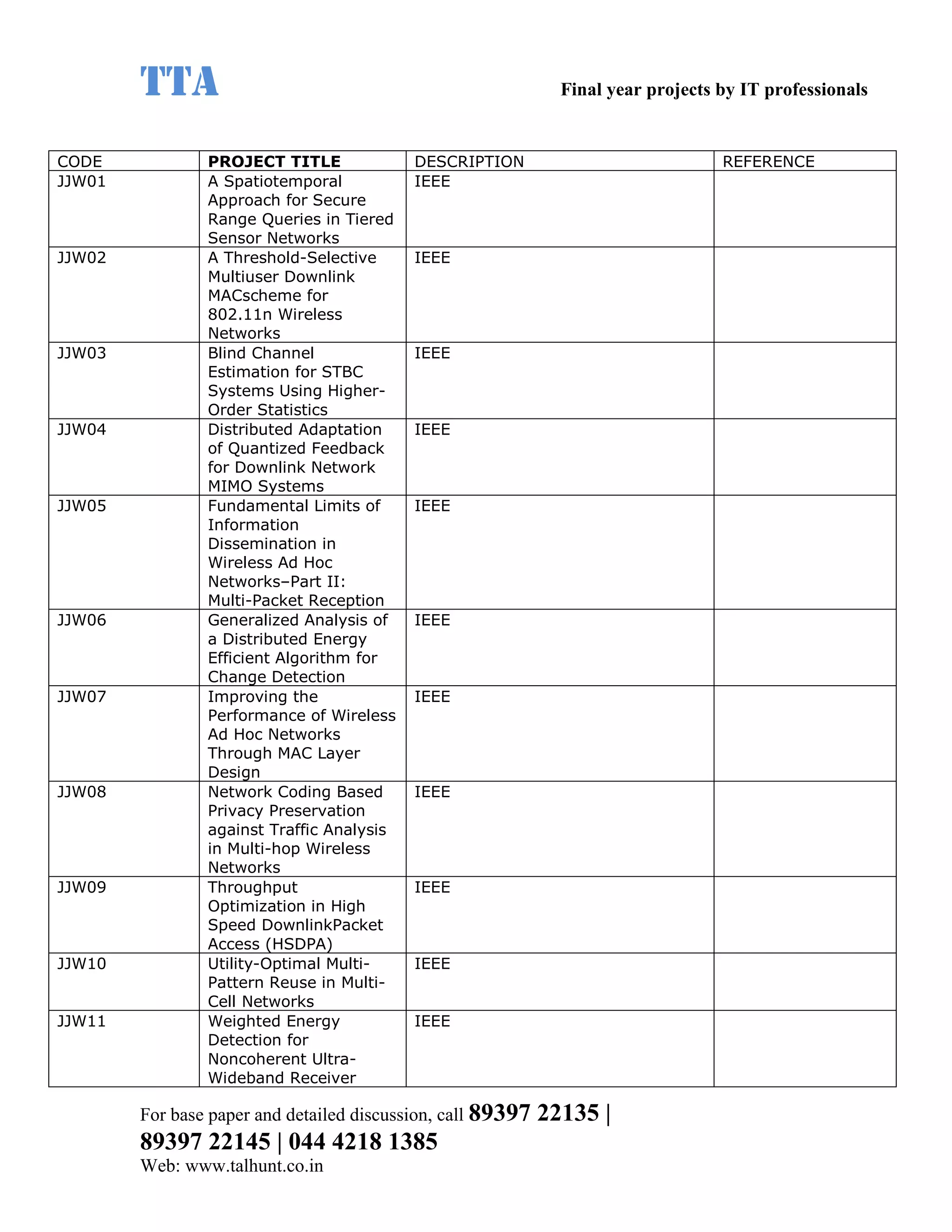
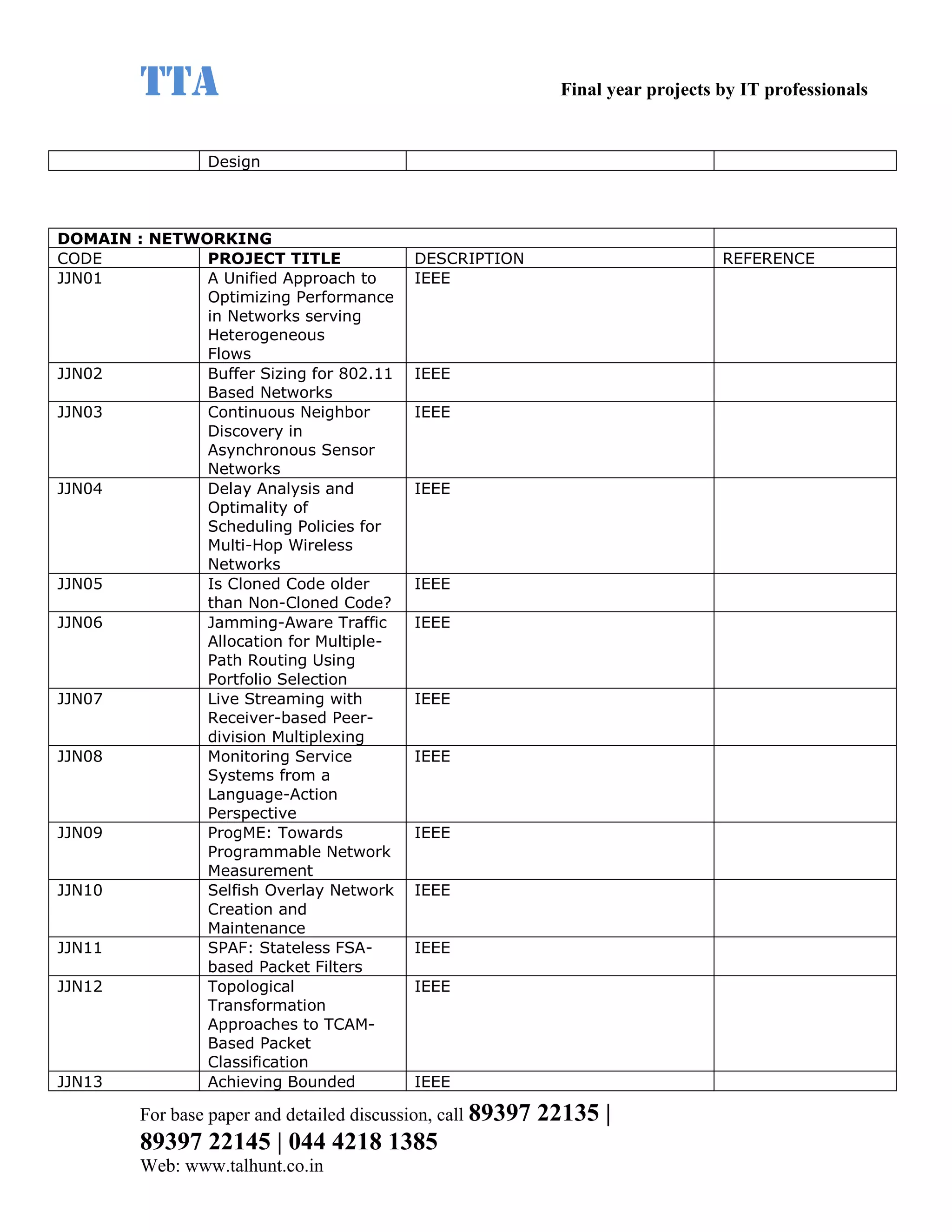
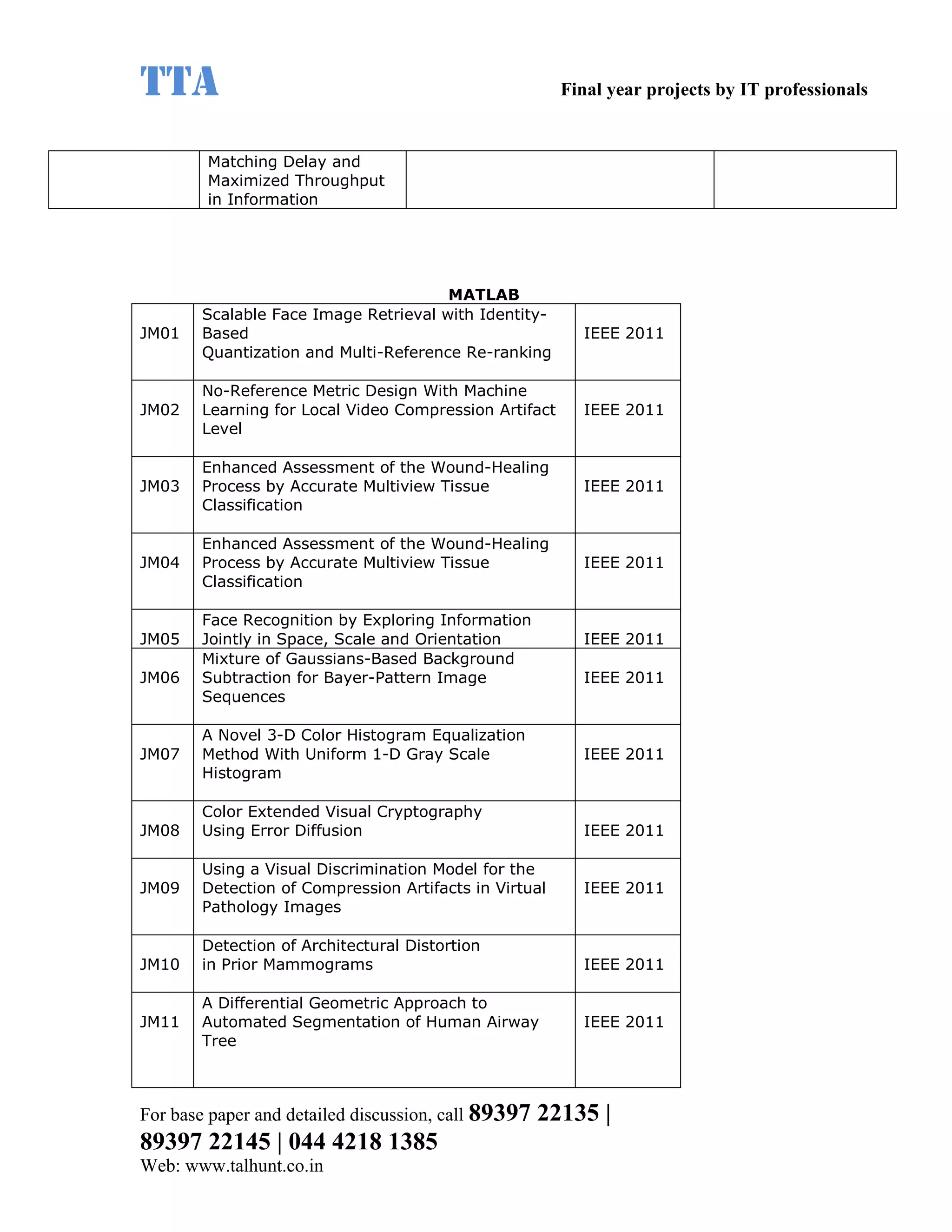
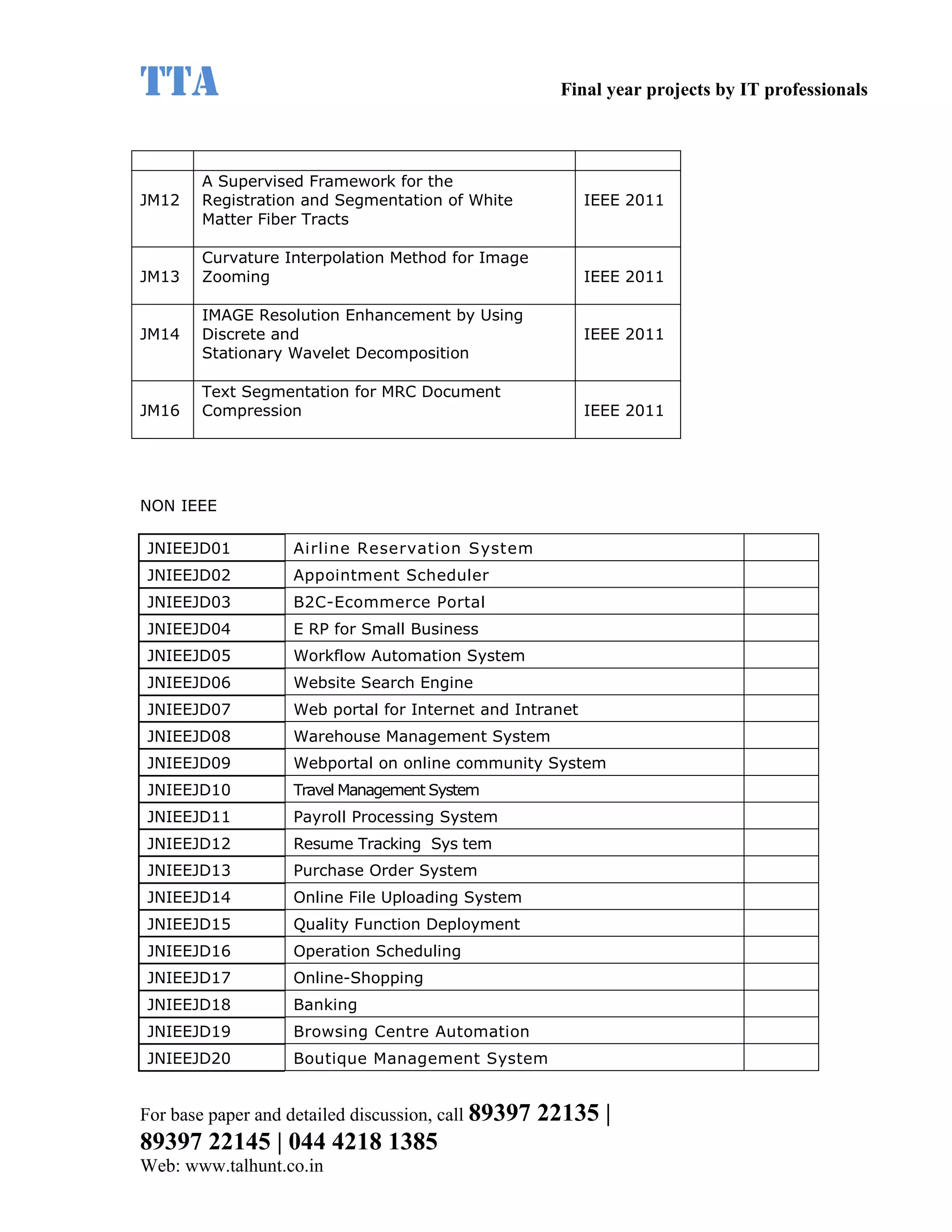
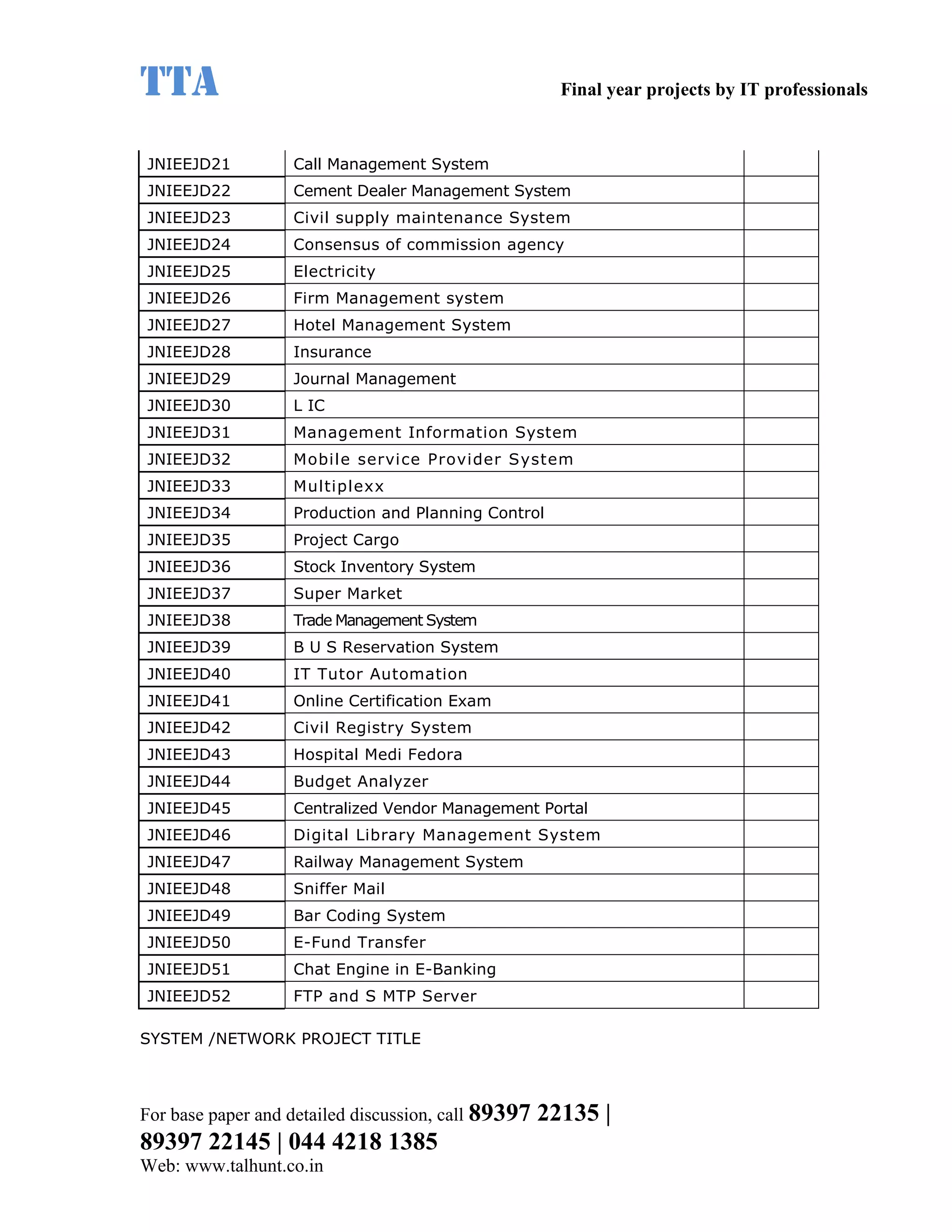
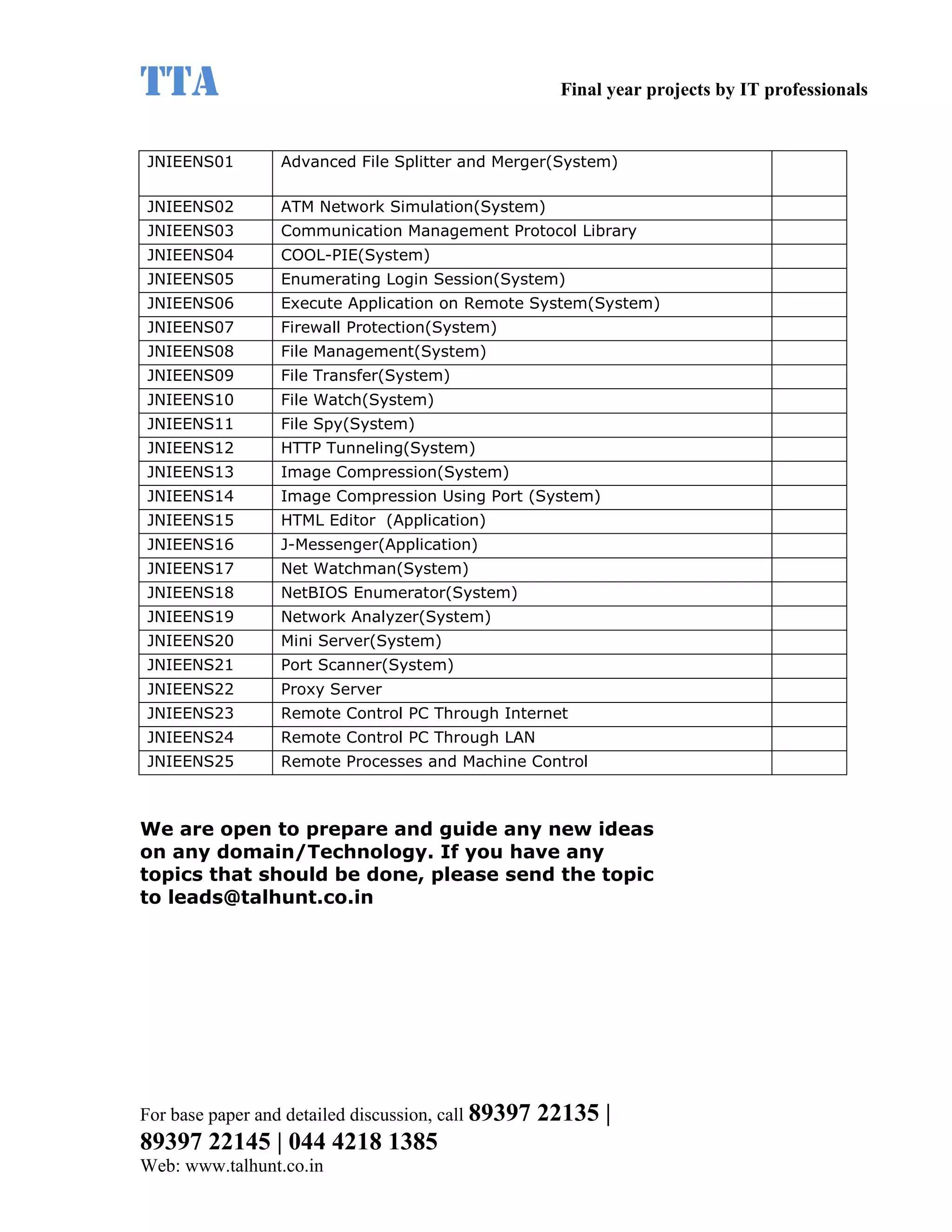
This document provides a summary of 11 mobile computing final year project titles from IEEE papers between 2011-2008. It includes the project title, description, and reference for each. The projects relate to topics like reliability improvement in device-to-device communication, location tracking in mobile networks, environment partitioning in robotic networks, photo retrieval on mobile devices, routing in wireless mesh networks, using smart antennas in multi-hop wireless networks, scheduling in multi-hop wireless networks, network connectivity with group mobility models, reliable data delivery in dynamic ad hoc networks, local broadcast algorithms in wireless ad hoc networks, and privacy-preserving location monitoring. The document provides contact information to obtain full paper details.