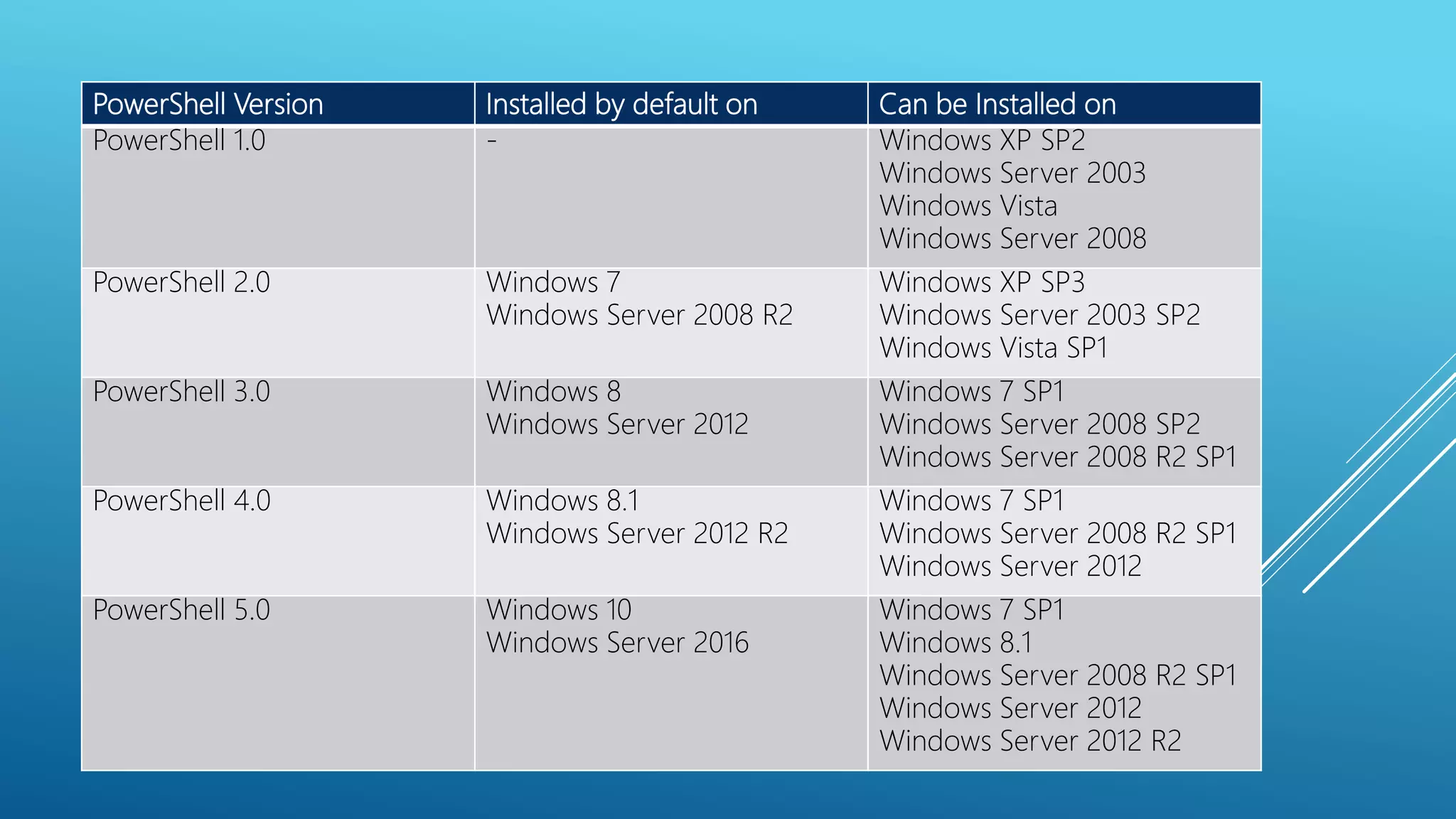
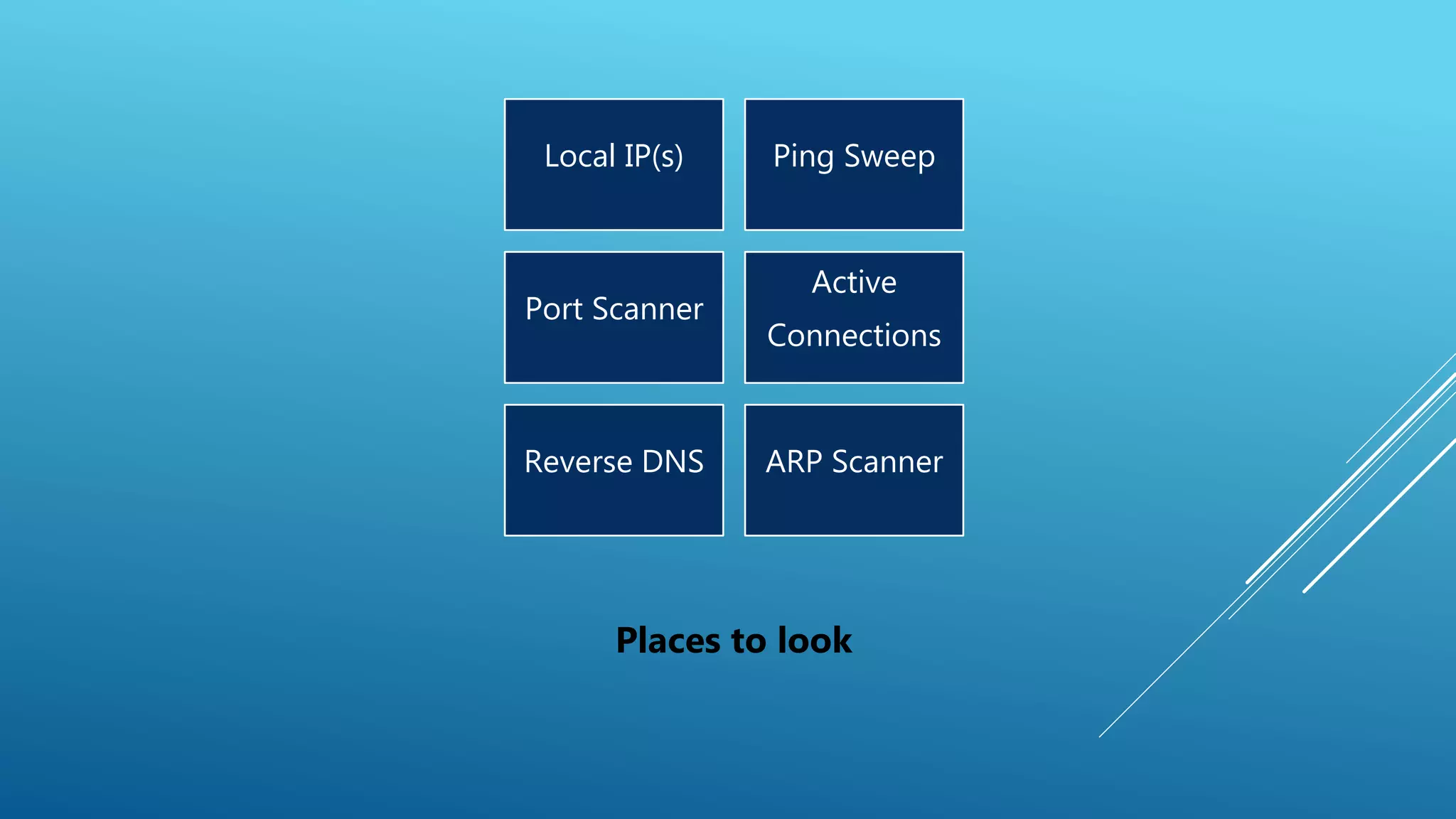
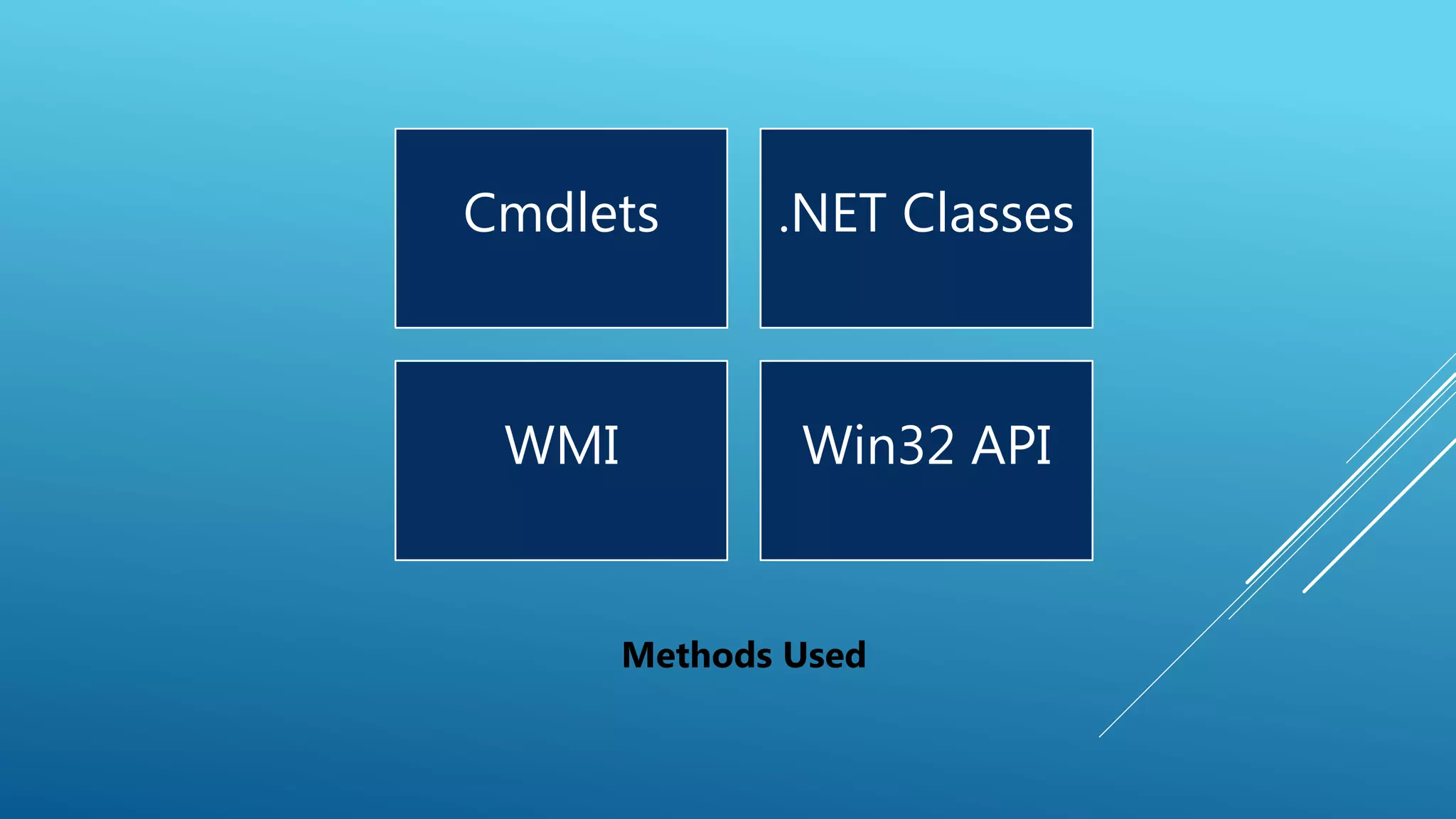
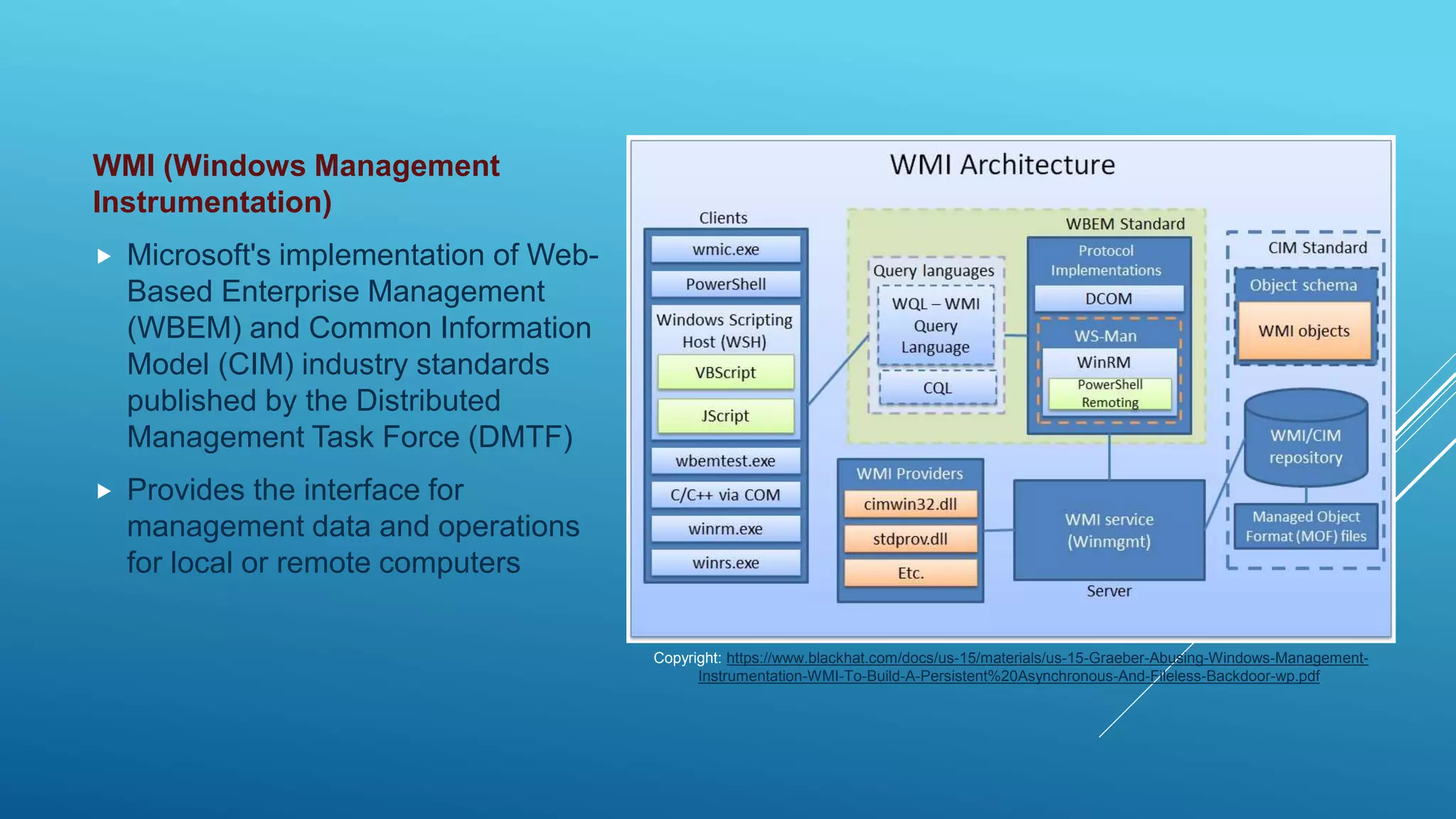
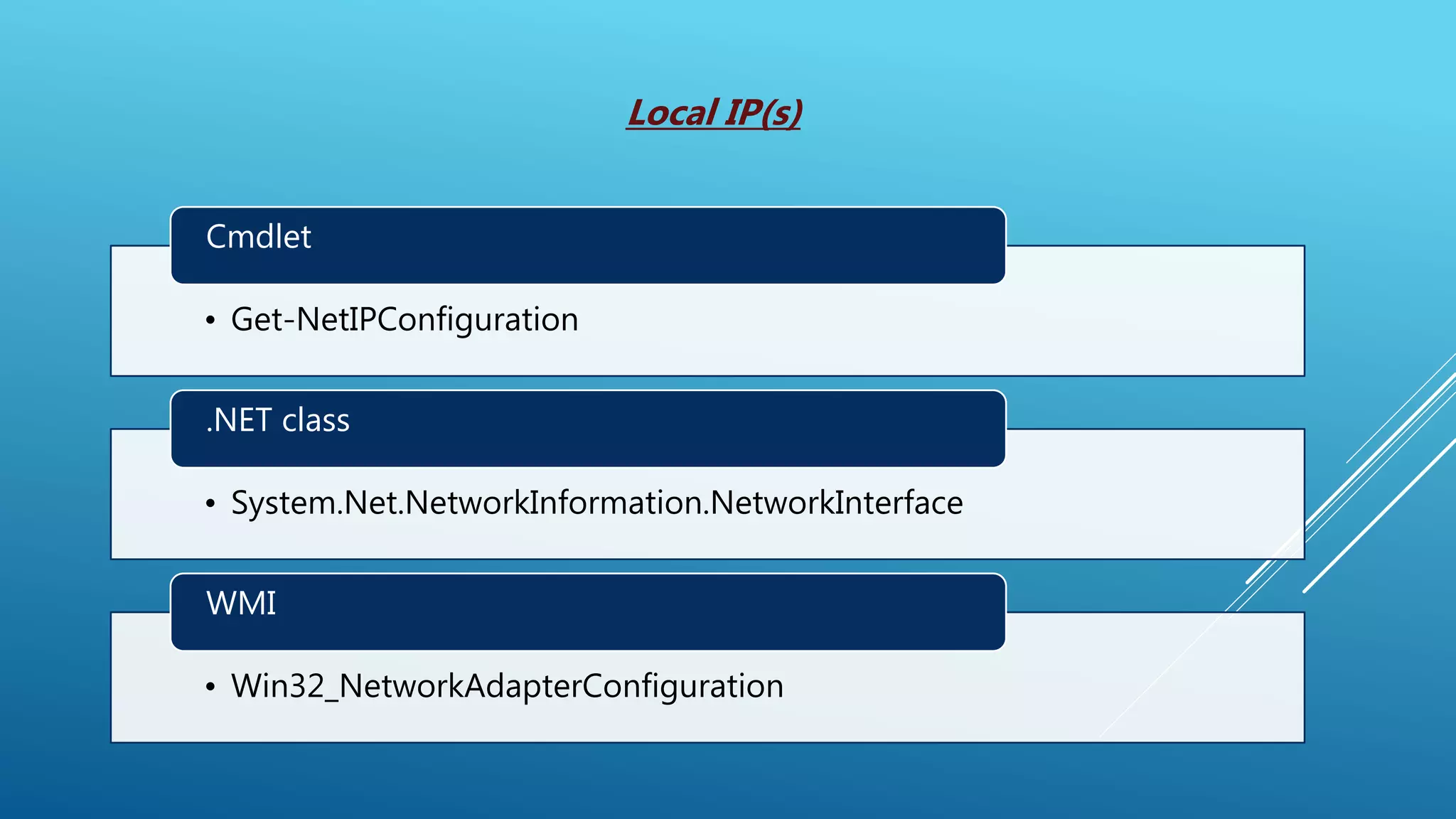
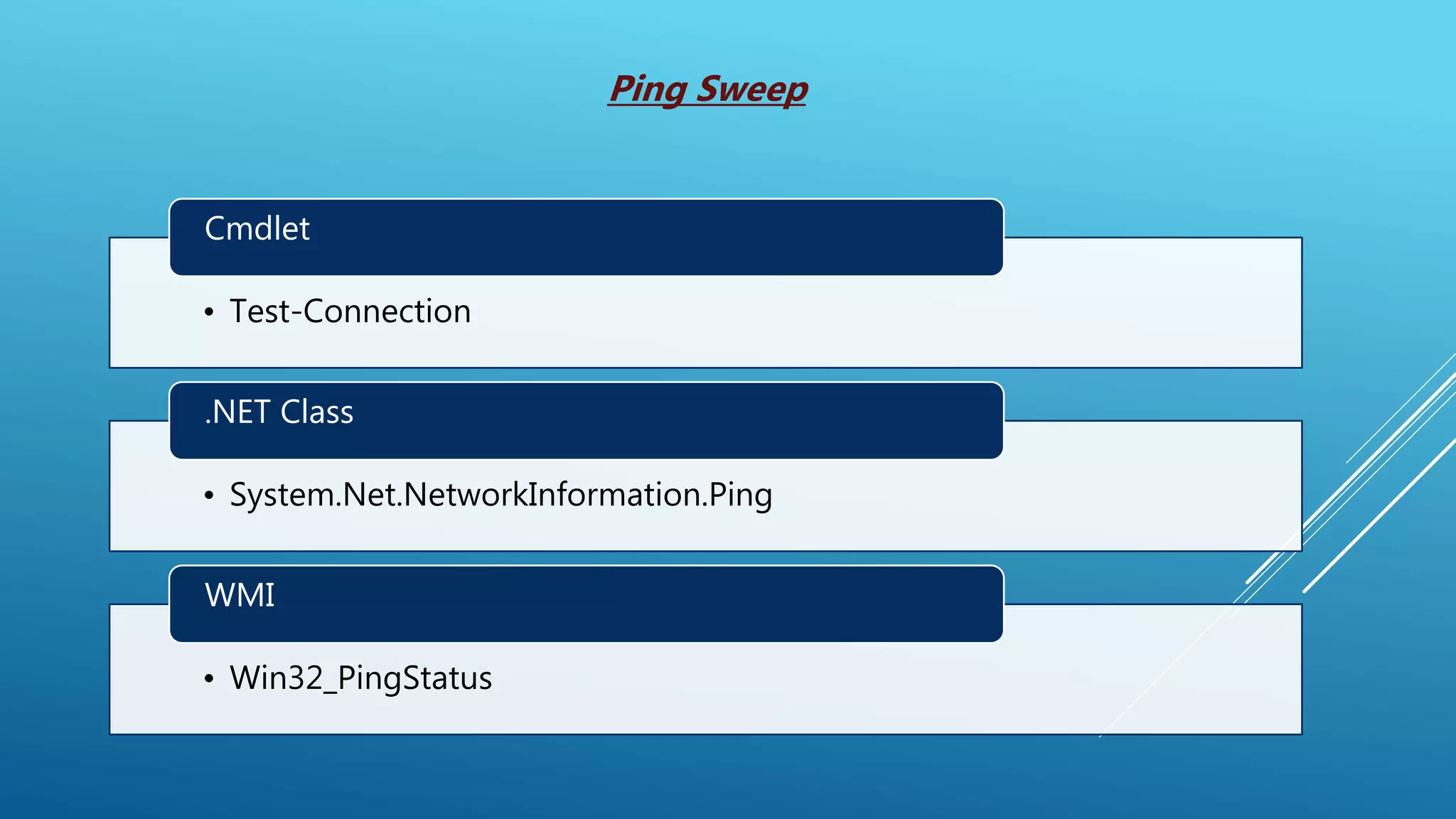
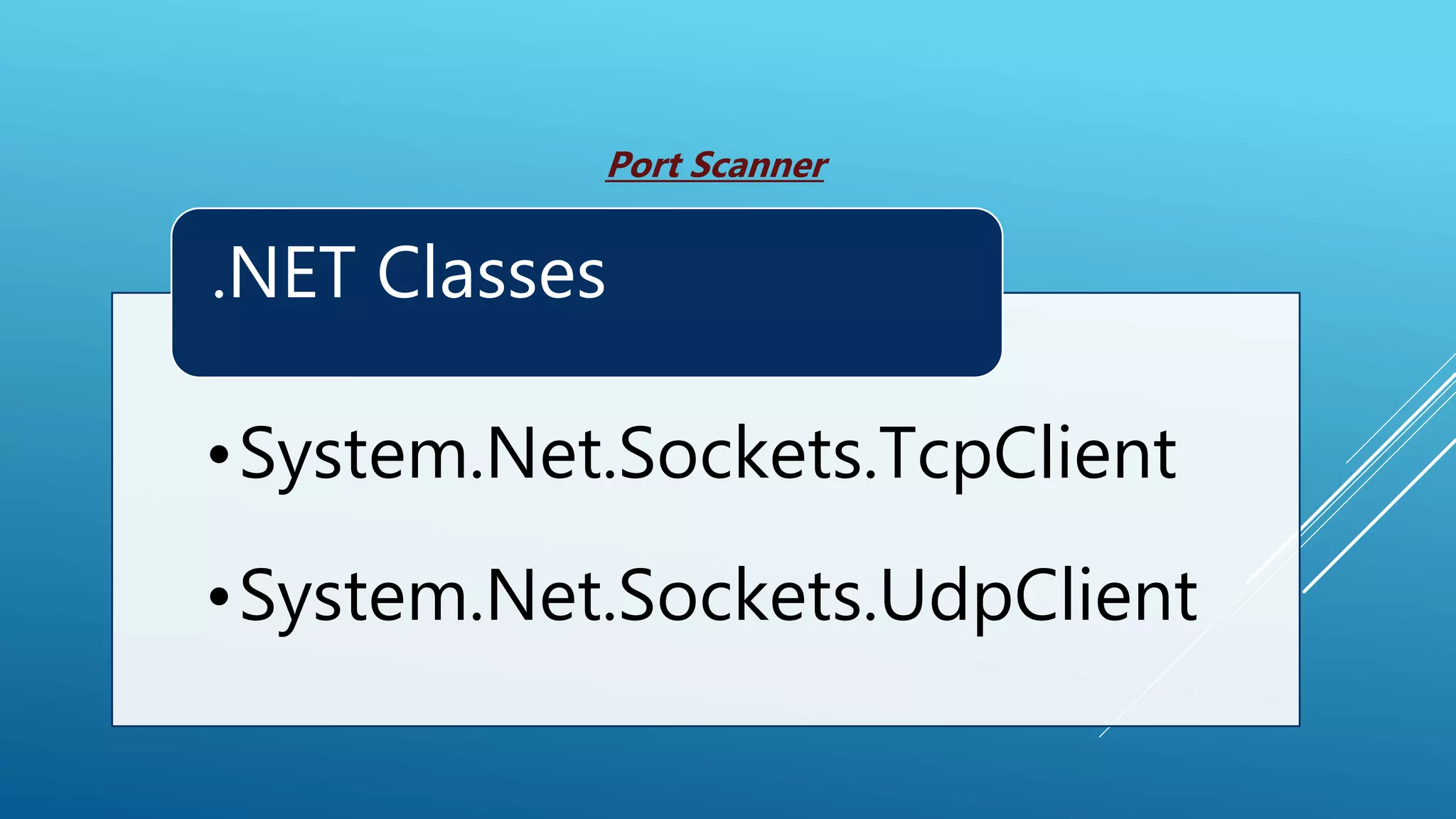
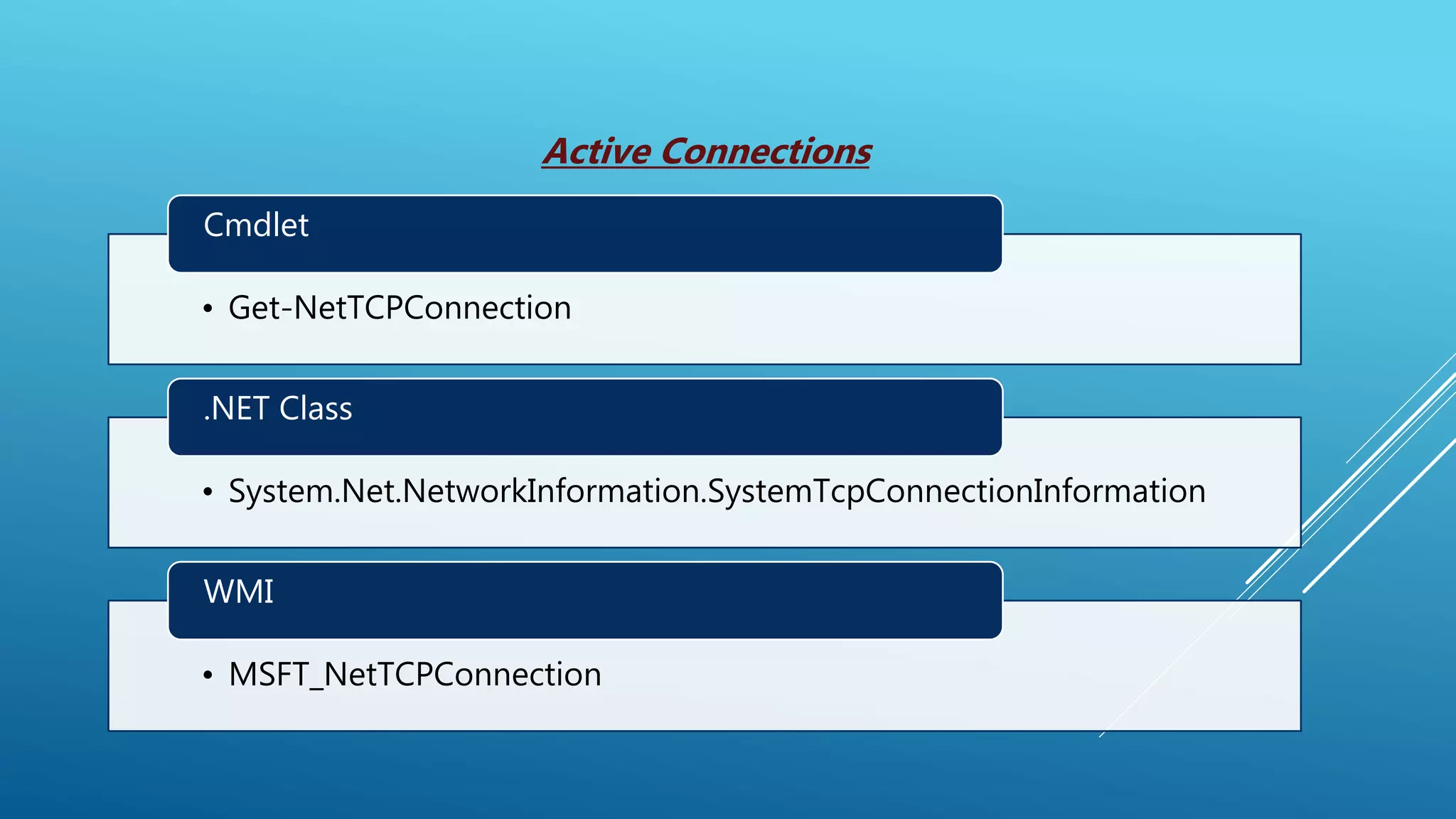
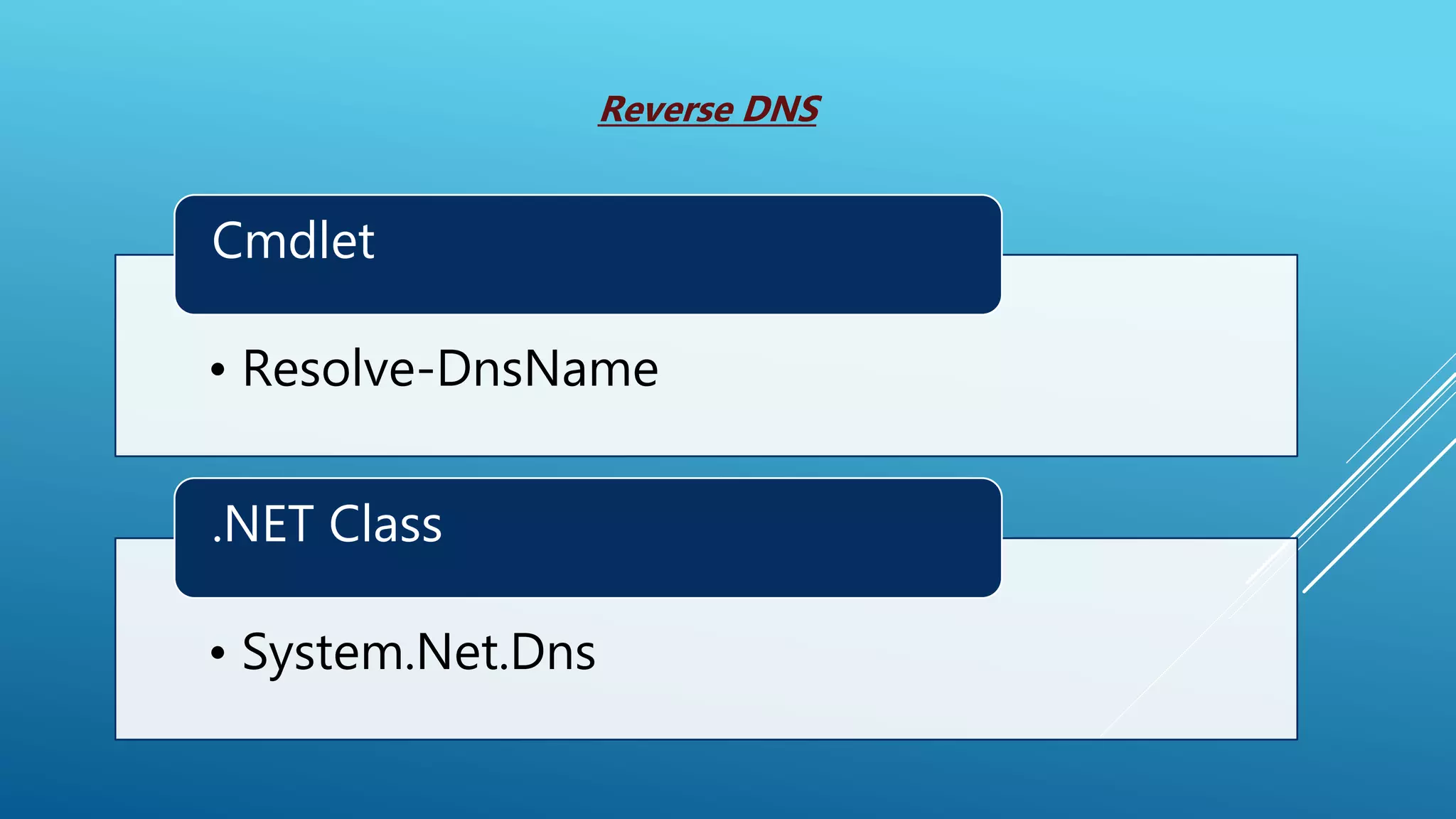
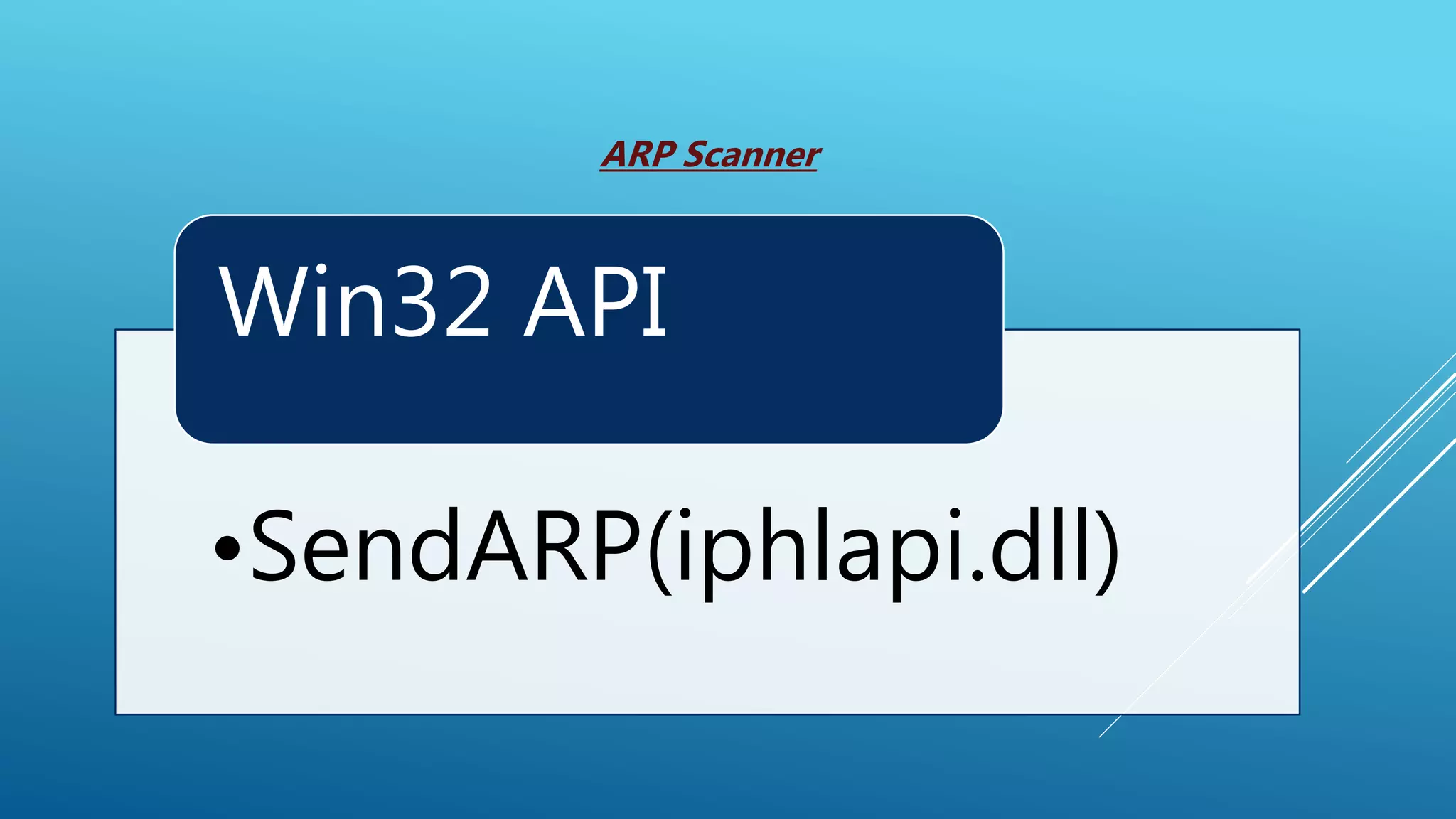
This document summarizes a presentation given at the 5th meeting of the Romanian Powershell User Group on February 28th, 2017. The presentation introduced several methods for network mapping and discovery using Powershell, including ping sweeps, port scanning, querying active connections, reverse DNS lookups, and ARP scanning. Code examples were provided demonstrating how to perform these tasks with Powershell cmdlets, .NET classes, WMI, and Win32 APIs. The presentation concluded that Powershell allows non-privileged users to query local network information through various techniques and contacted the presenter for any additional questions.