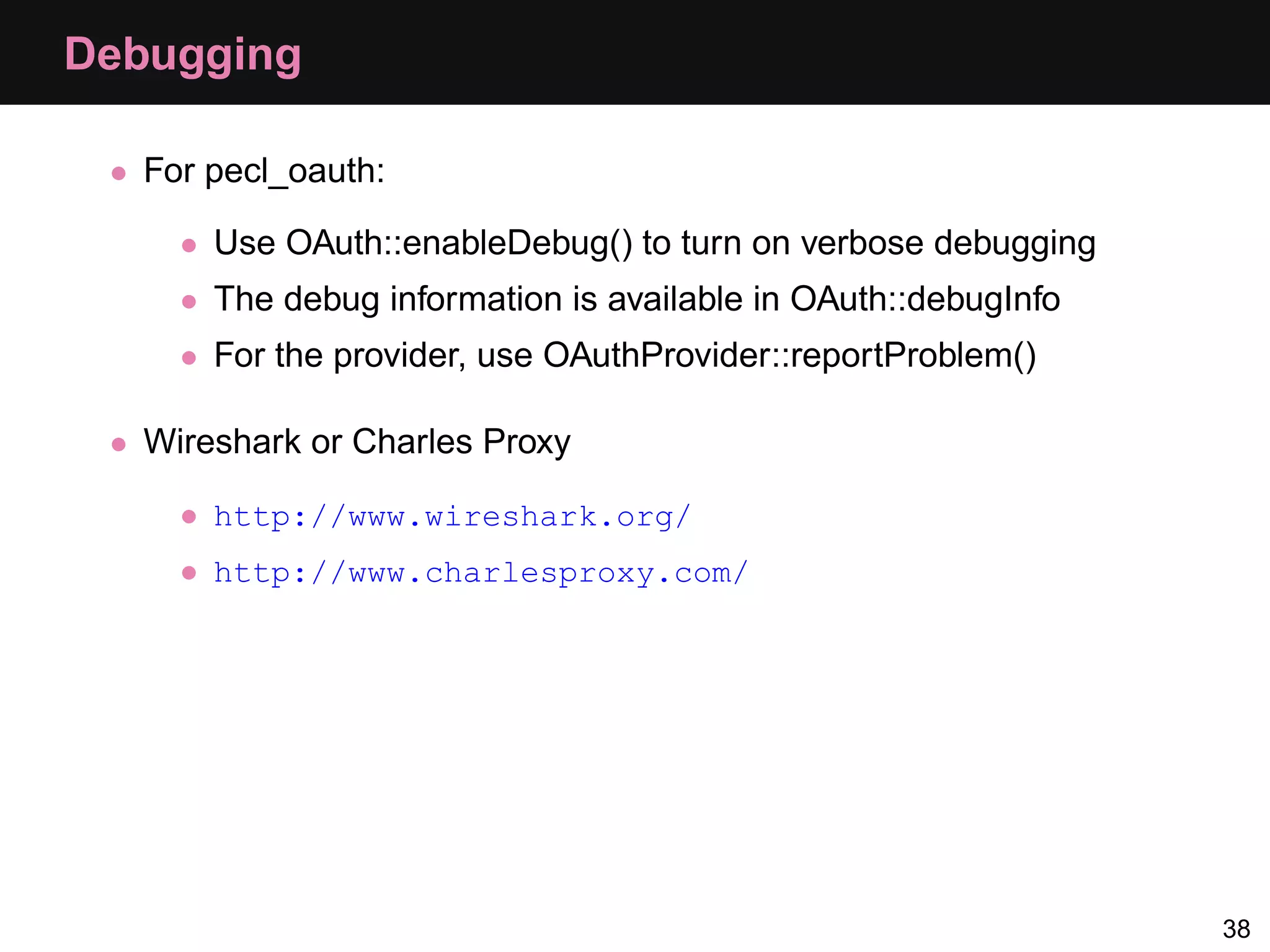
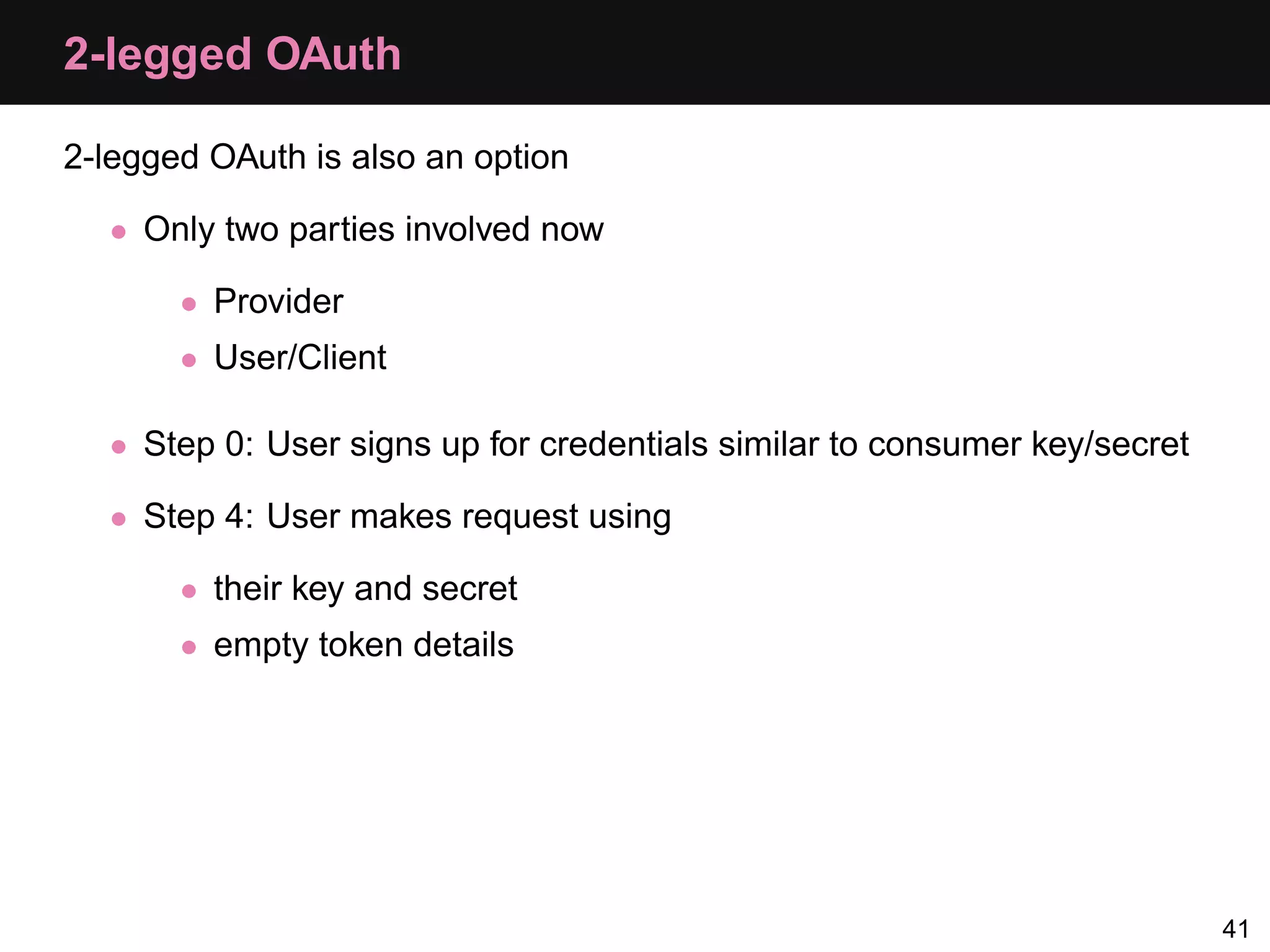
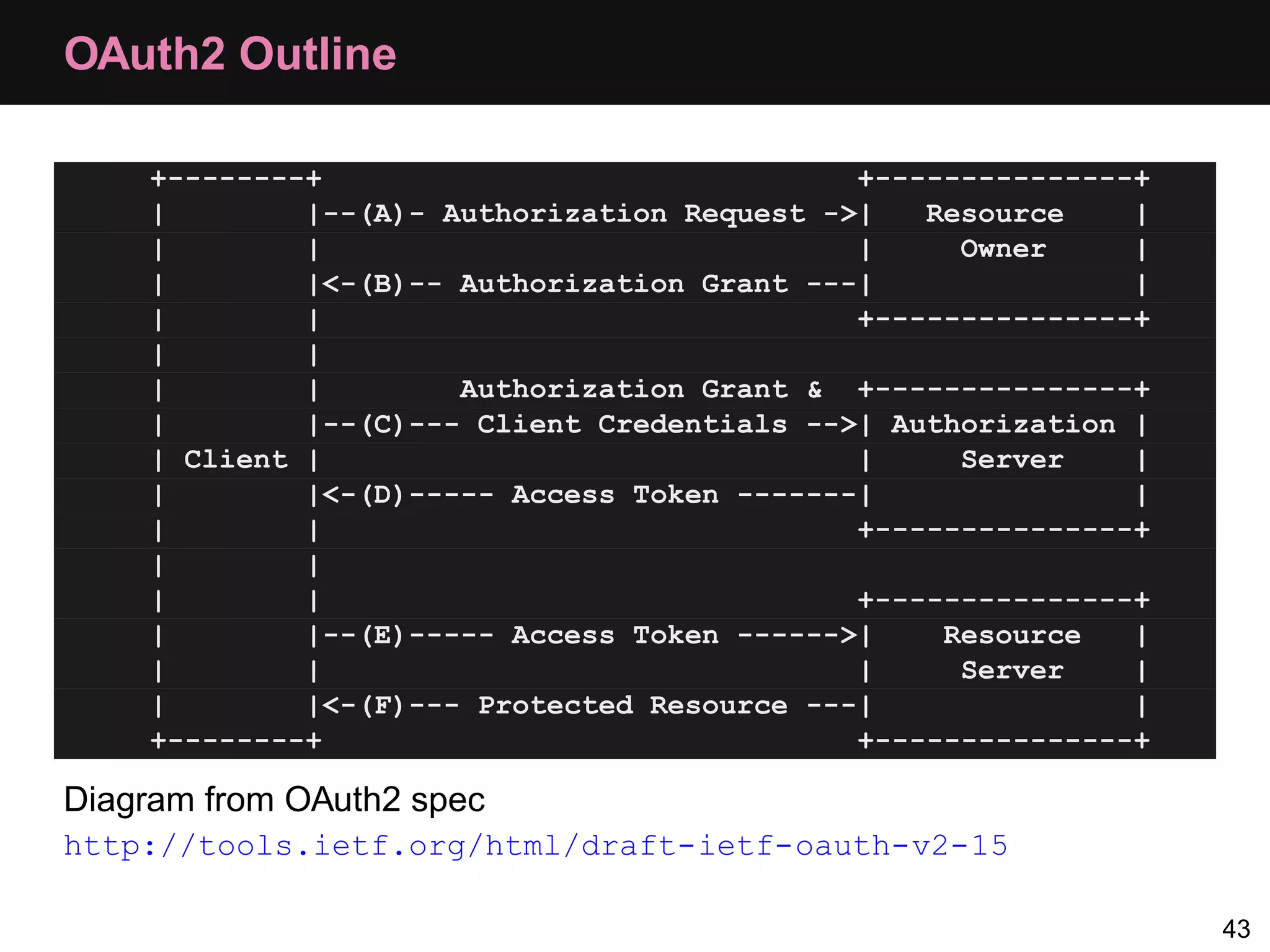
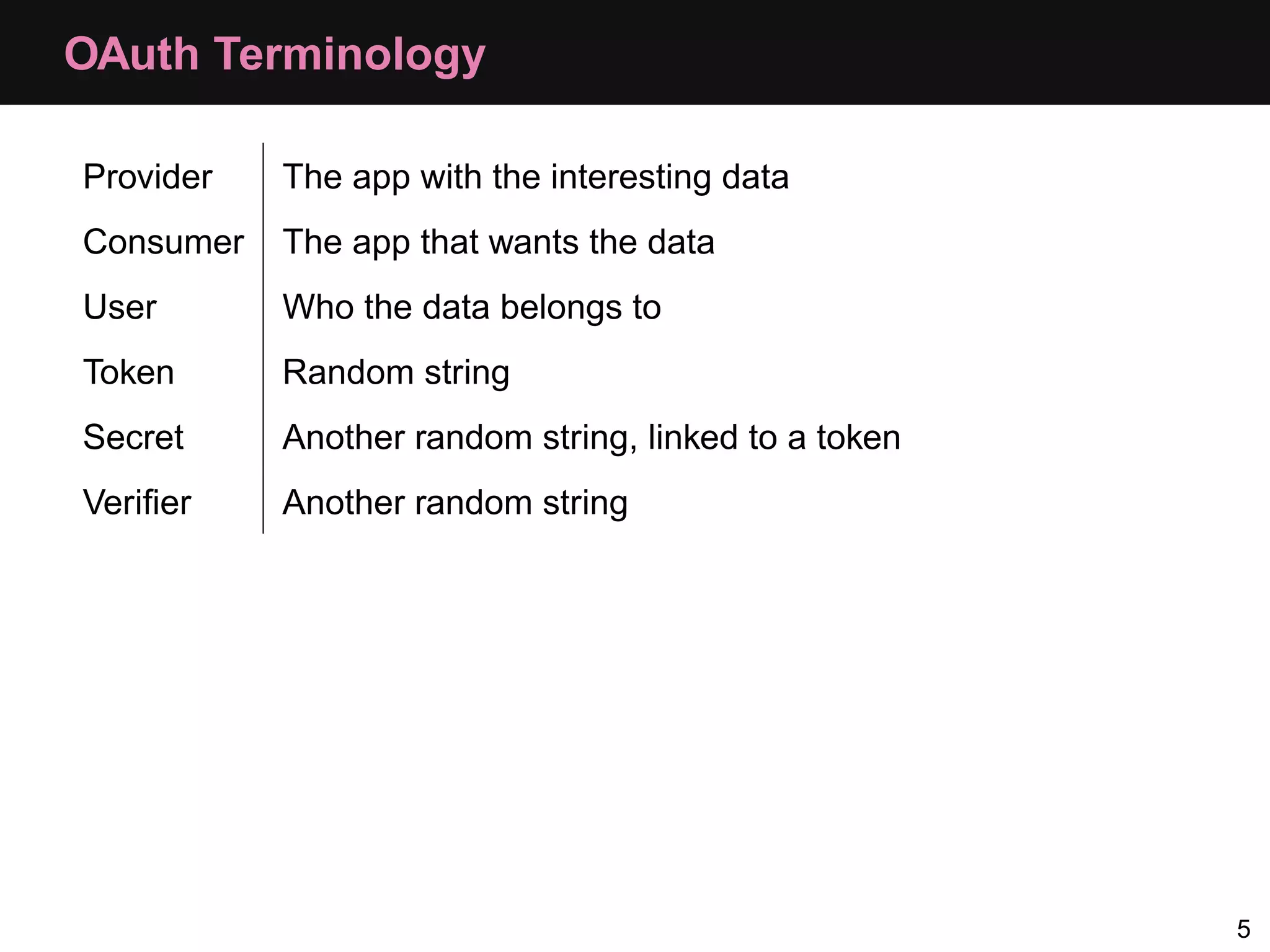
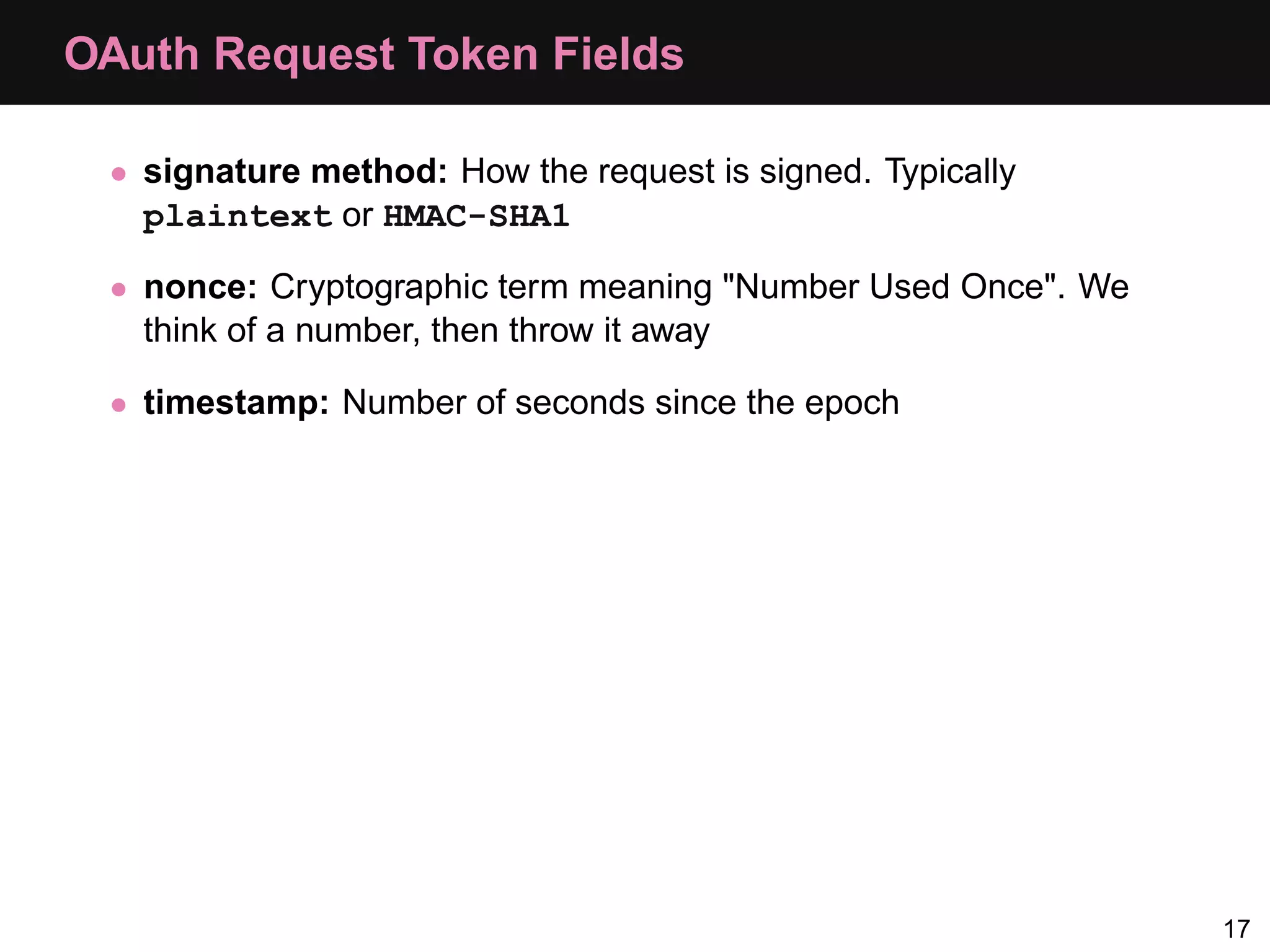
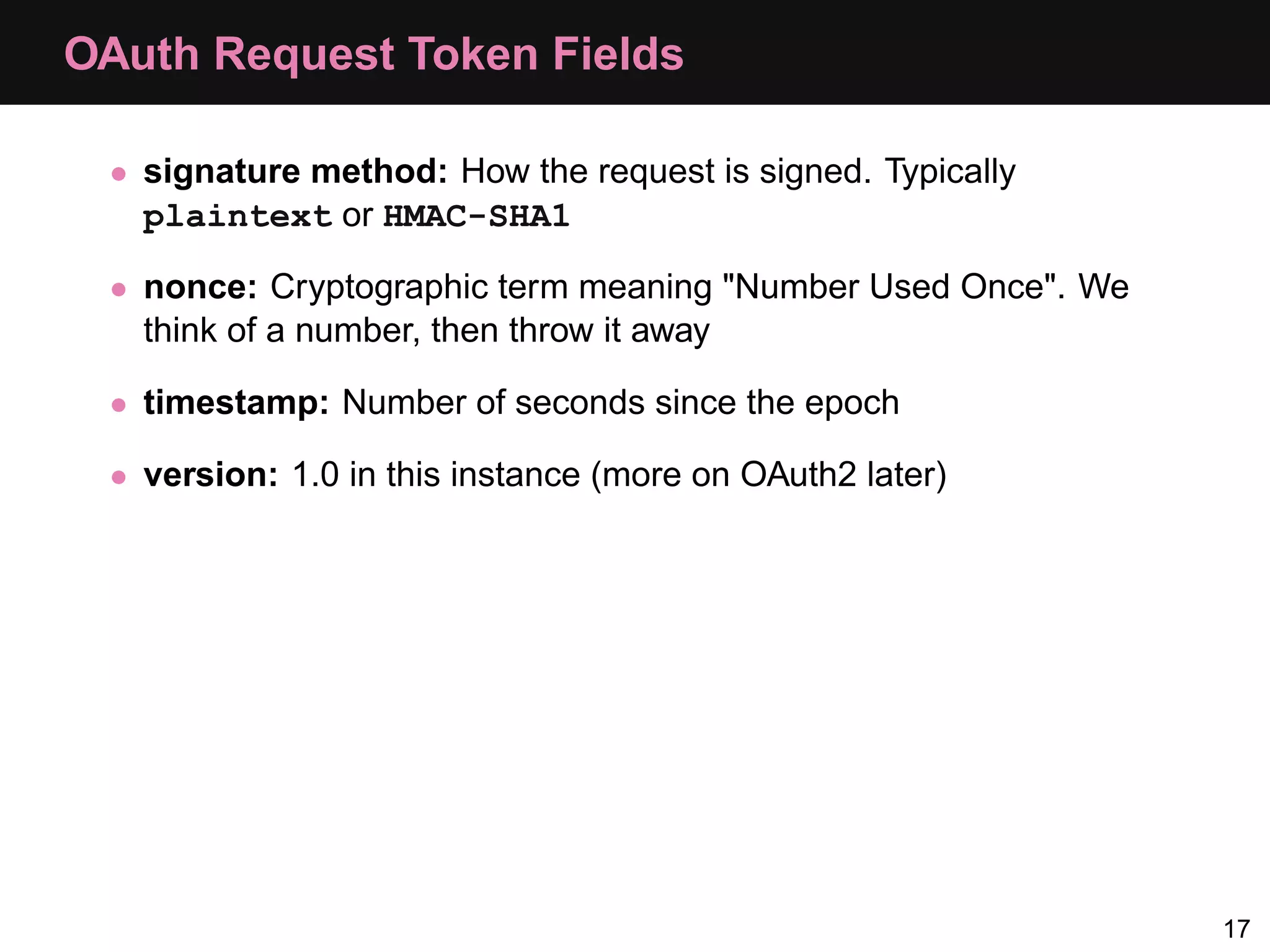
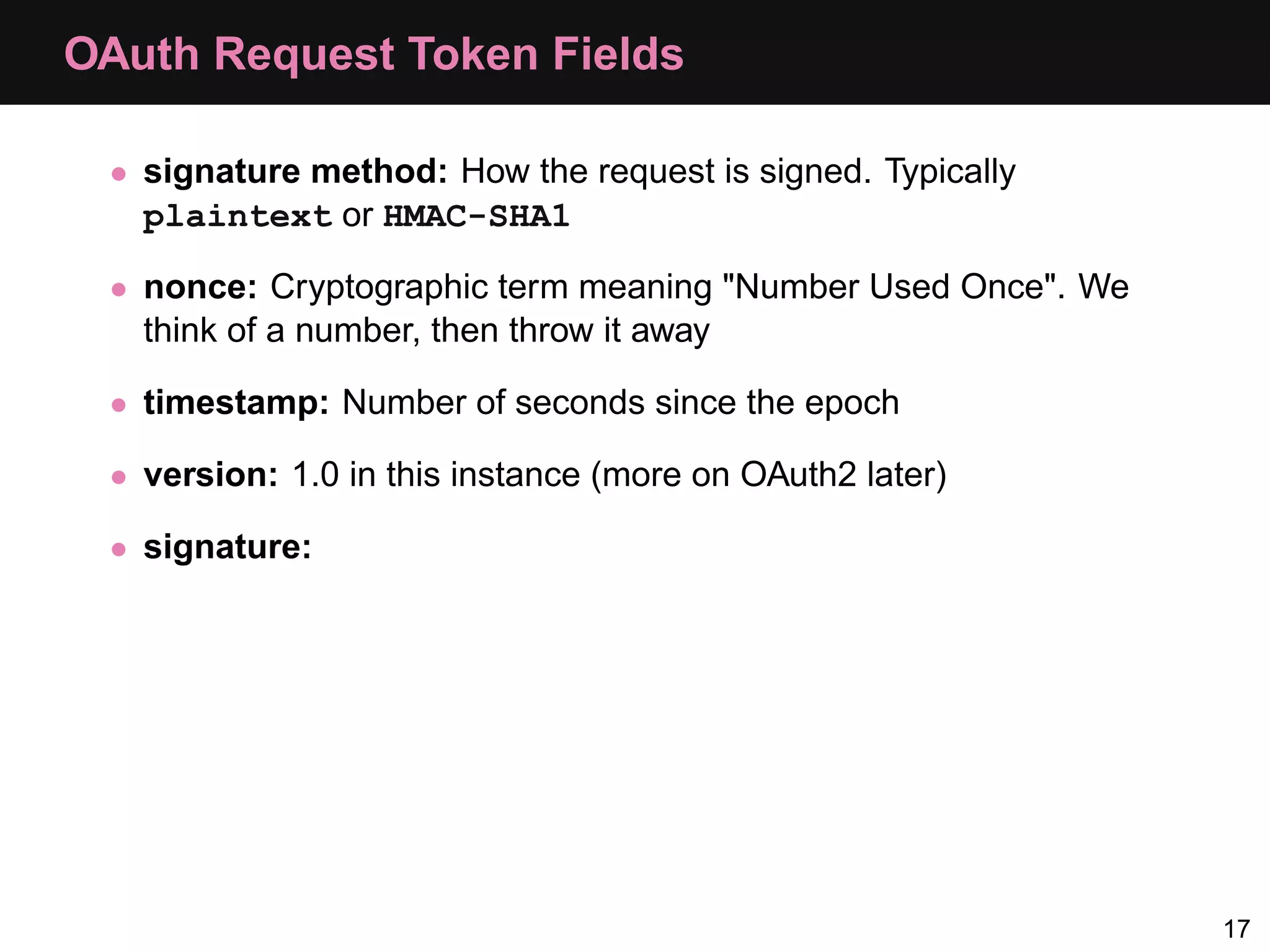
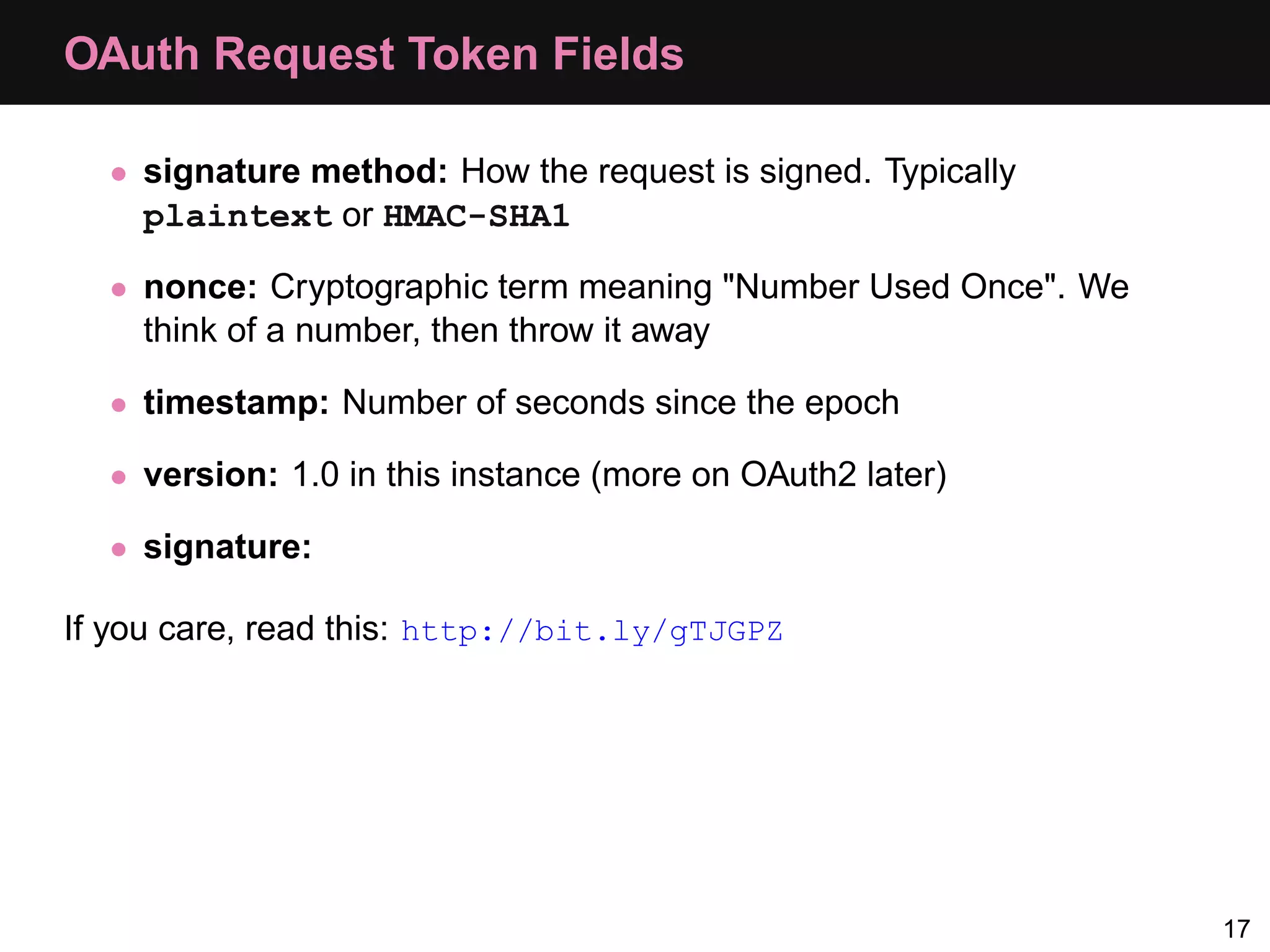
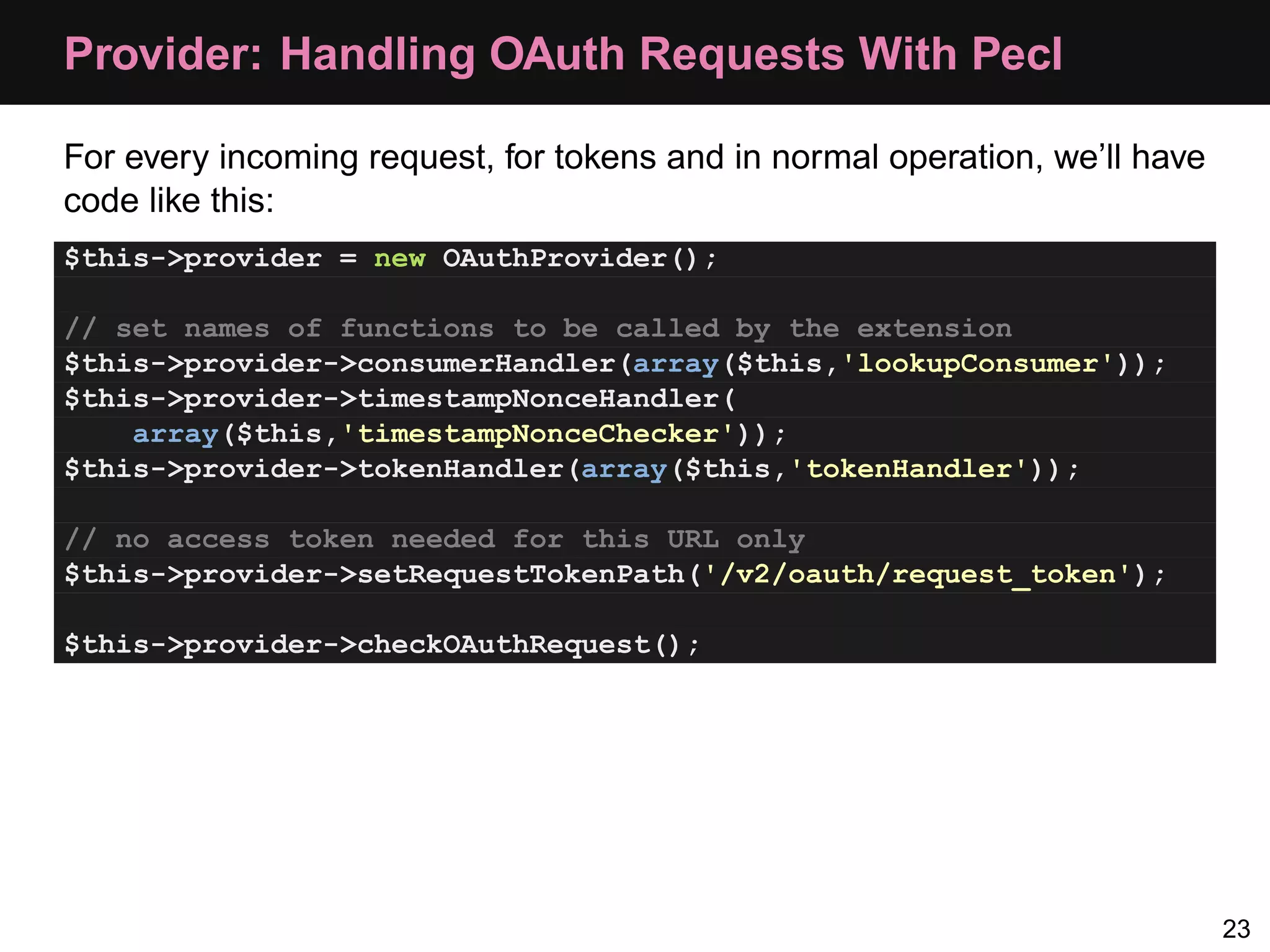
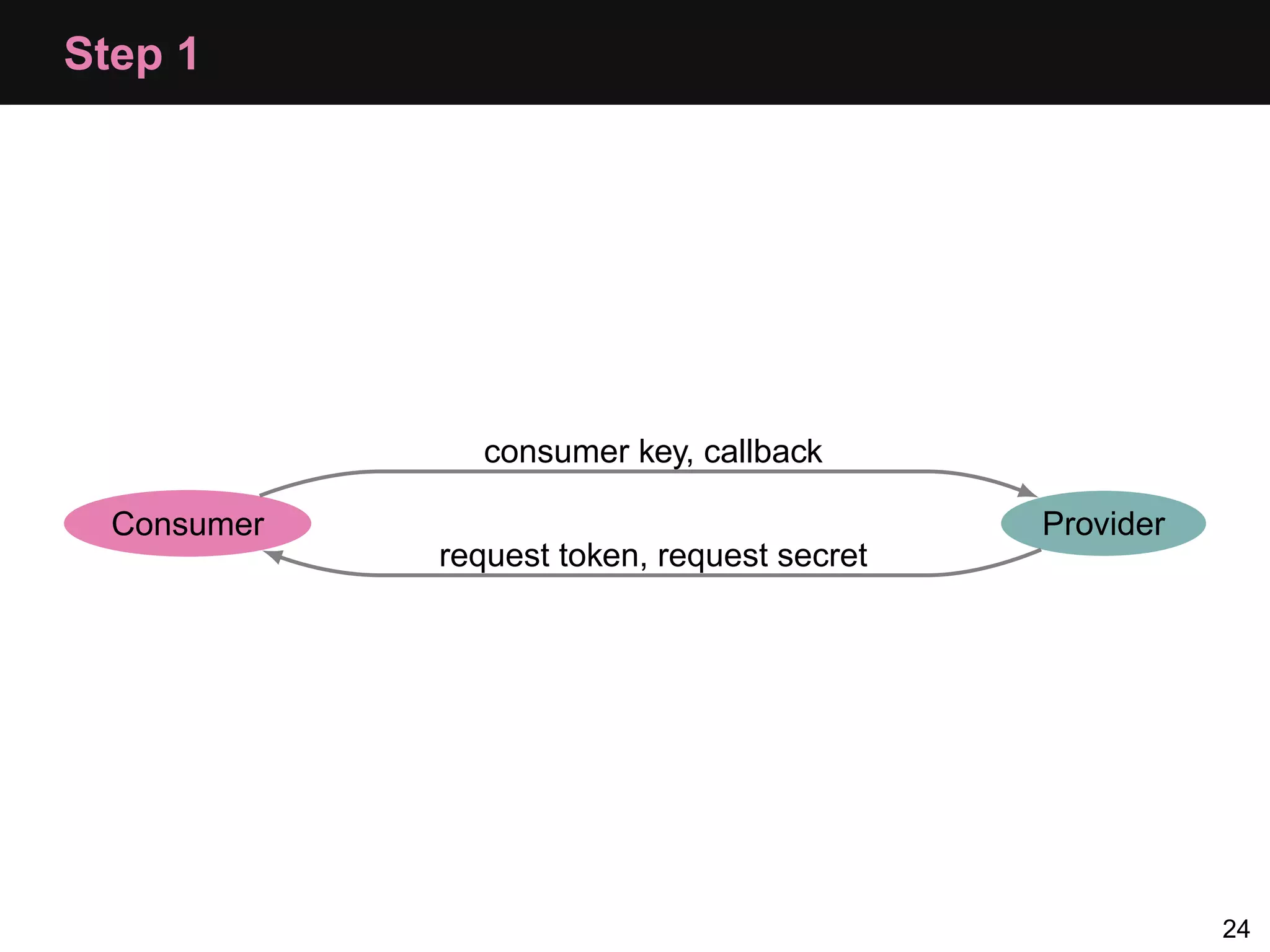
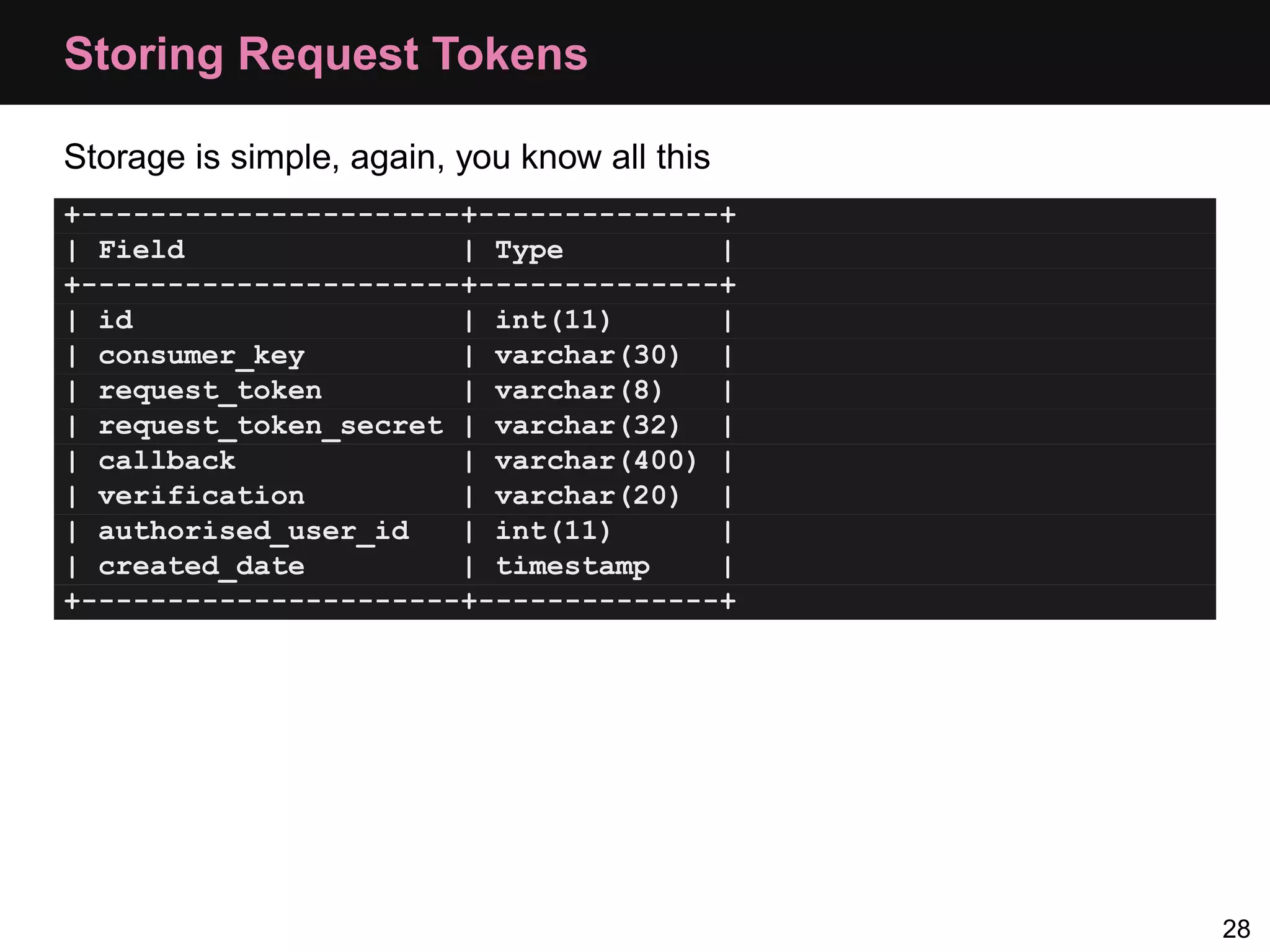
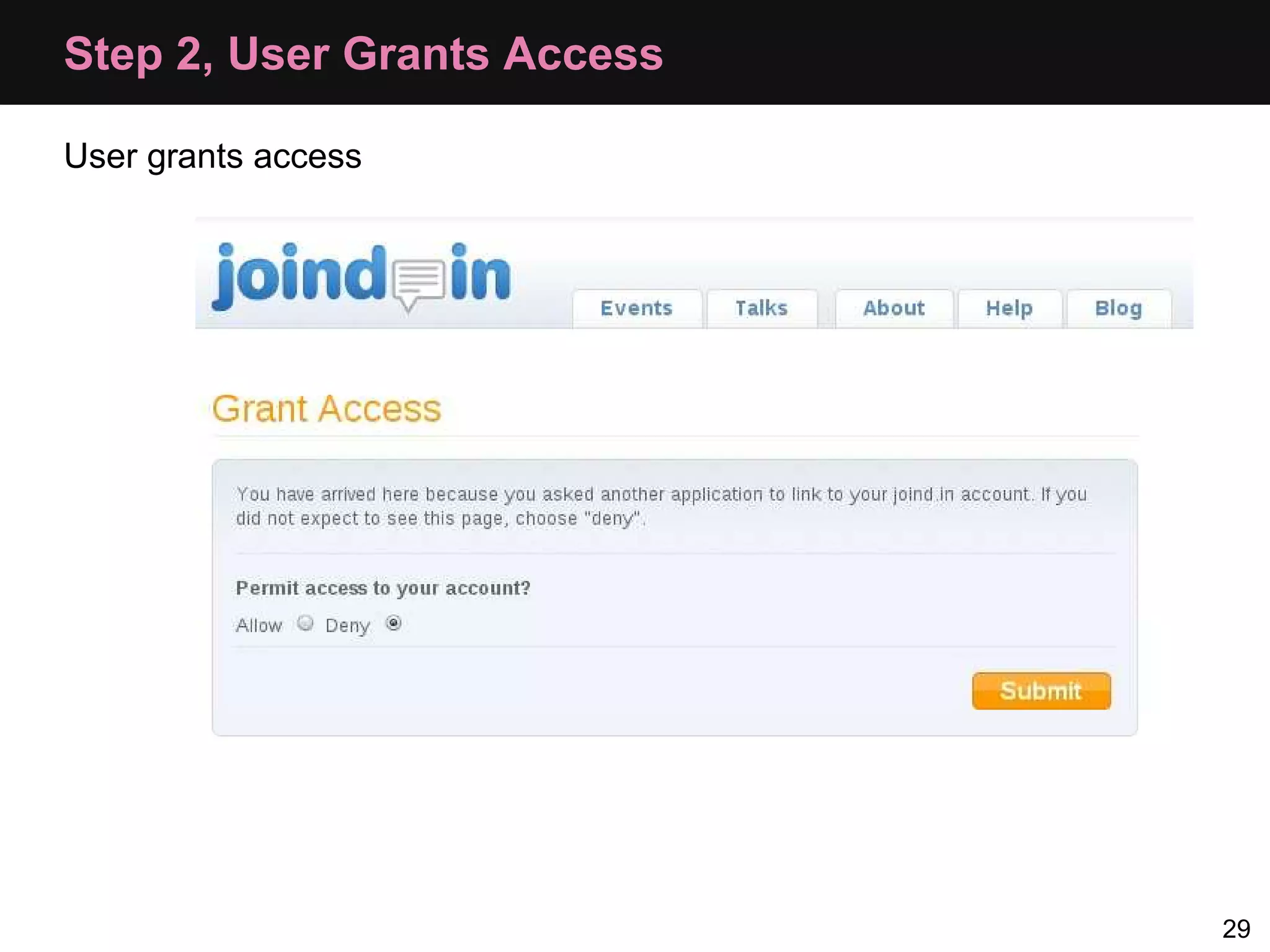
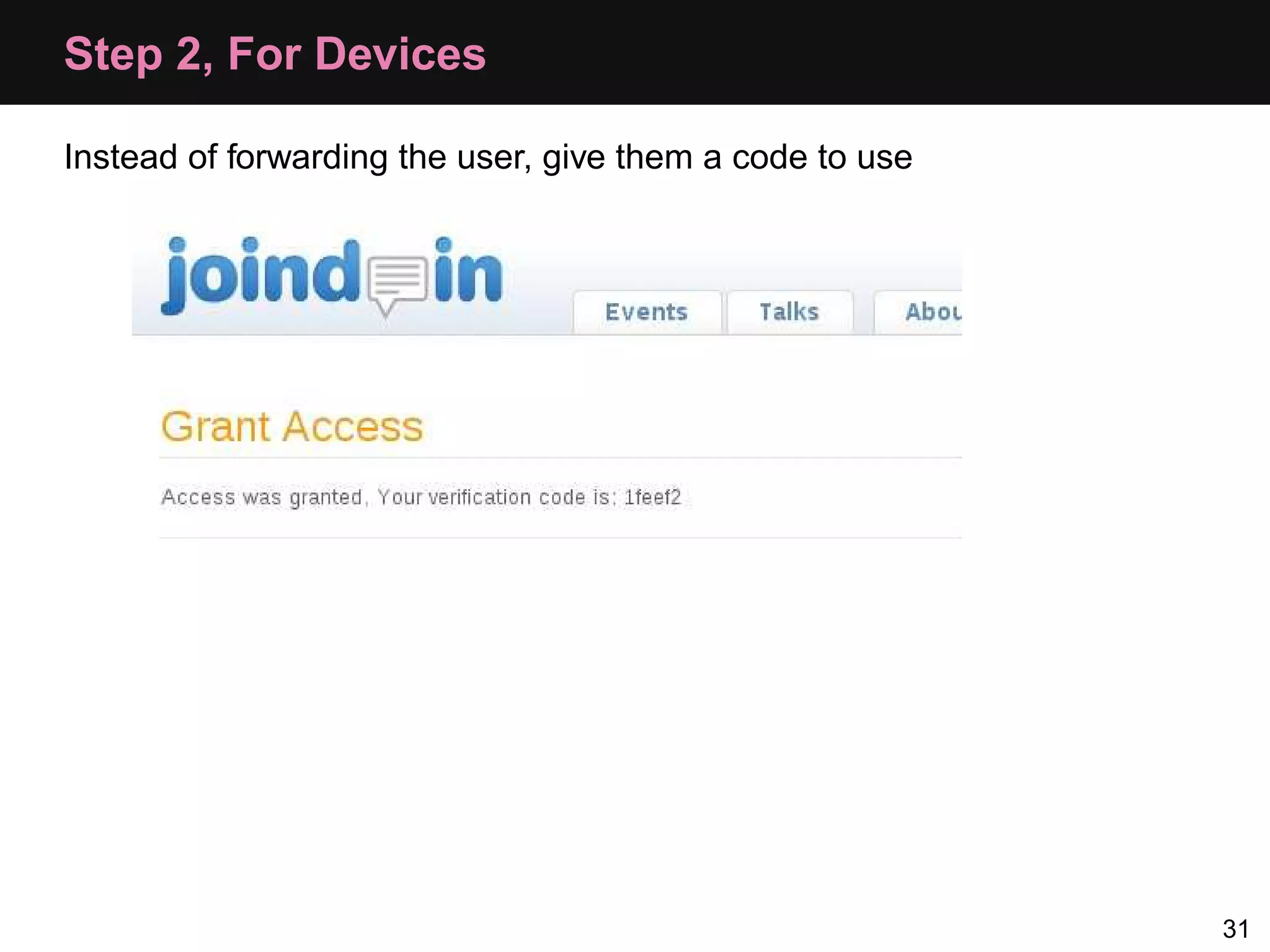
The document provides an overview of implementing OAuth authentication. It discusses: 1) The key steps in the OAuth process including registering an application, obtaining a request token, redirecting the user to authenticate, and exchanging the request token for an access token. 2) Key terminology used in OAuth like provider, consumer, user, token, and secret. 3) Examples of OAuth flows and code for both providers (websites with protected data) and consumers (applications wanting access to that data).




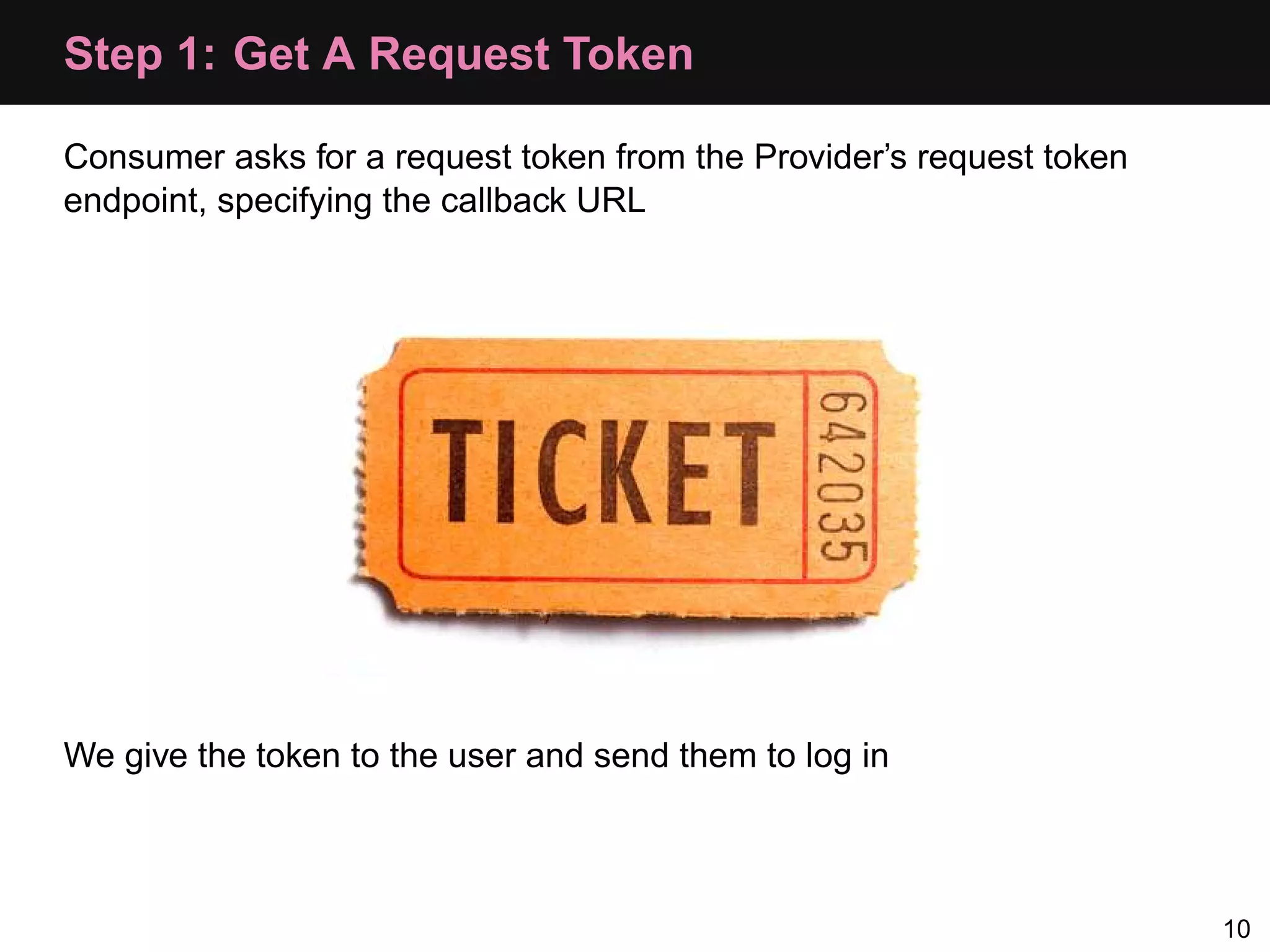


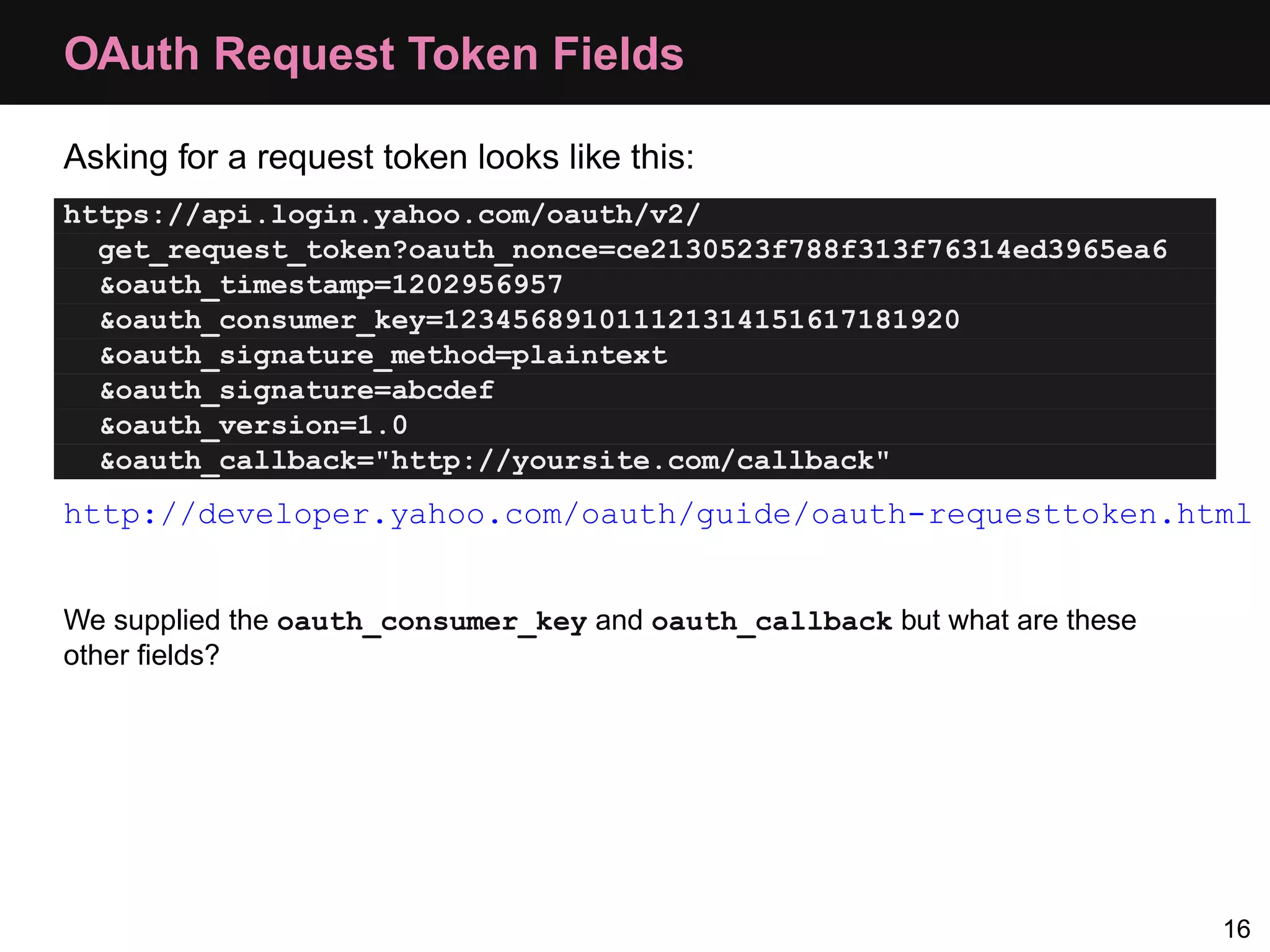
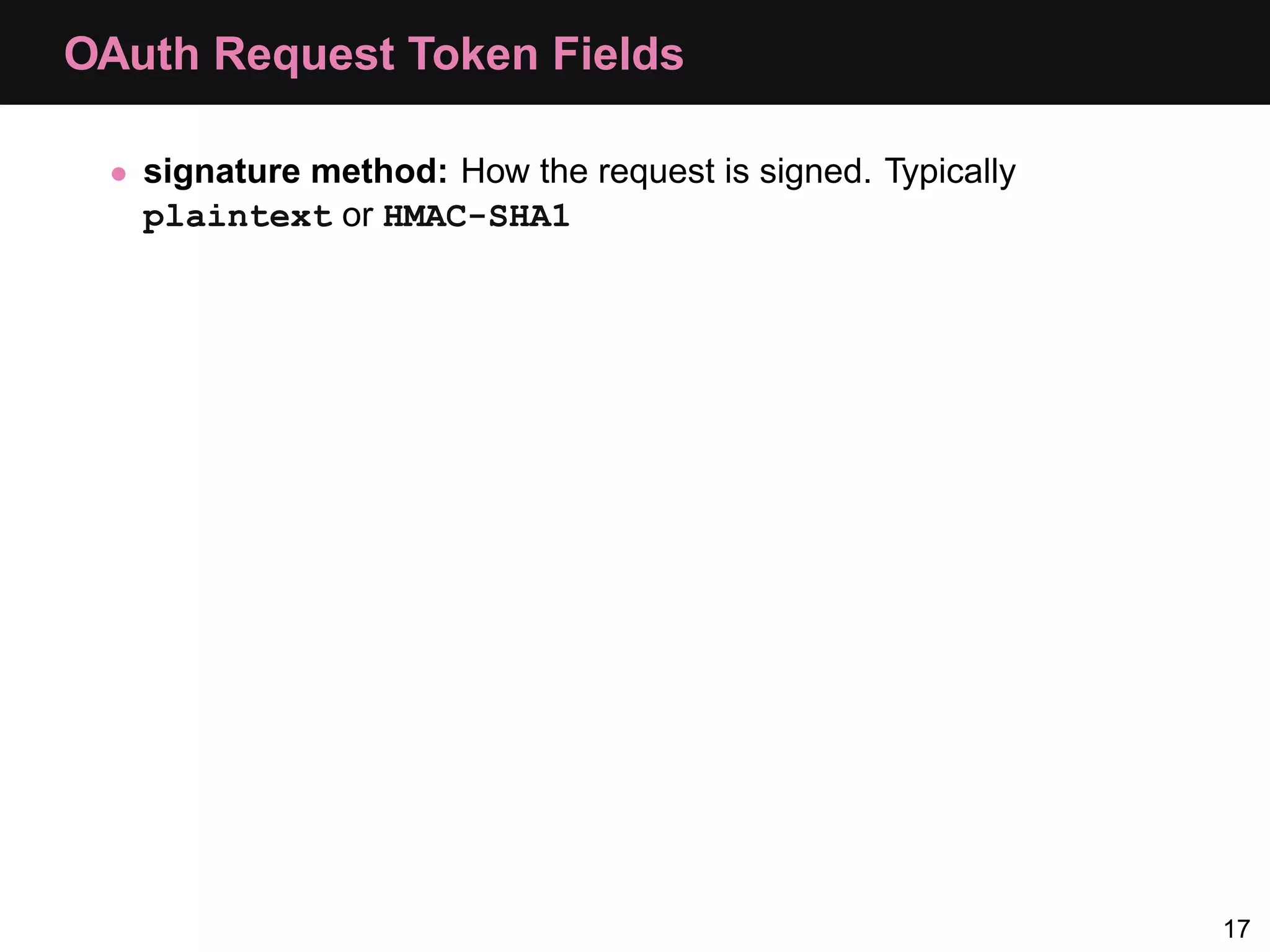
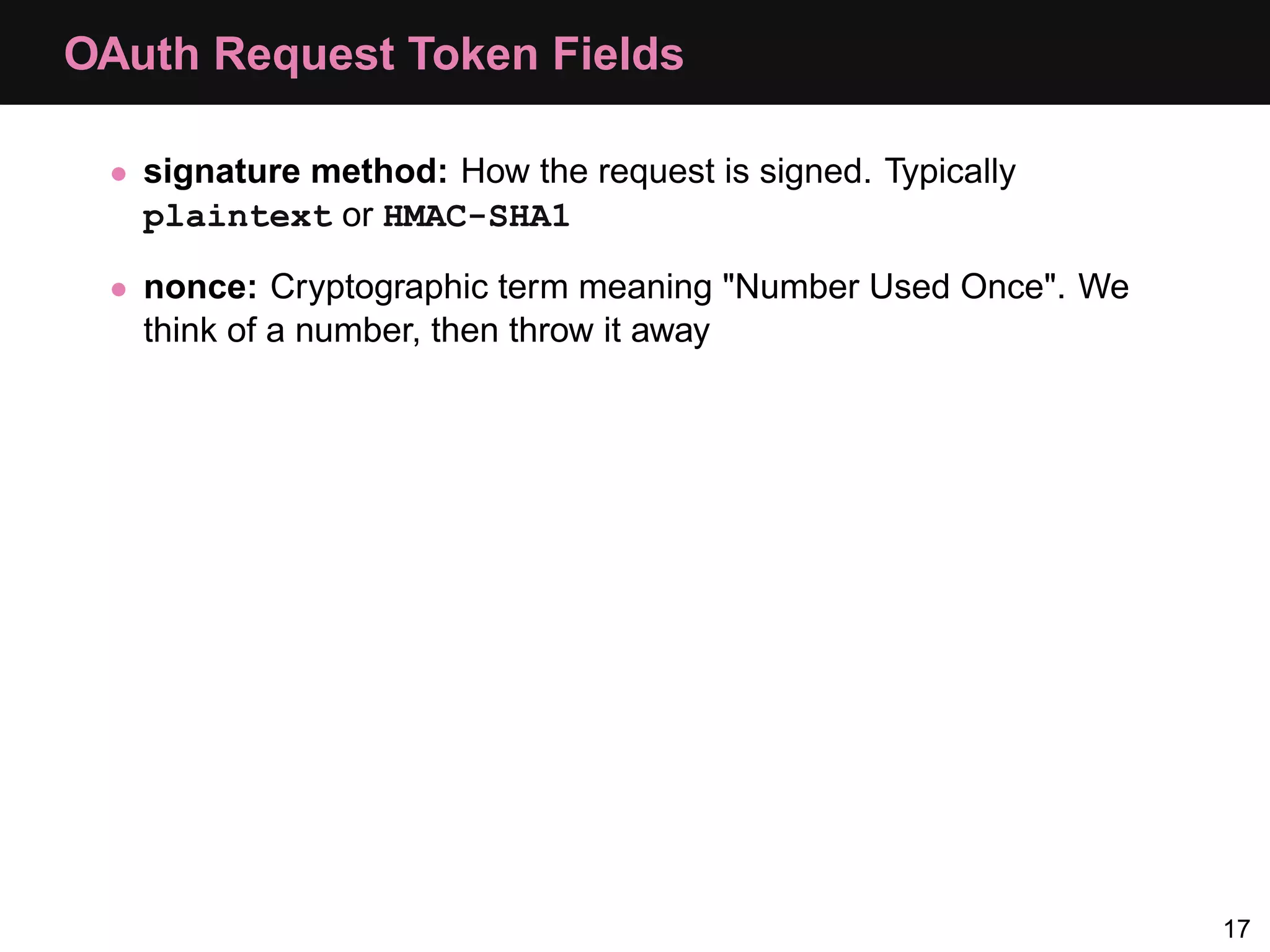

![Consumer: Step 1, Request Token $config = array(); $config['request_uri'] = 'http://api.local/v2/oauth/request_token'; $config['consumer_key'] = 'akey'; $config['consumer_secret'] = 'asecret'; $oauth = new OAuth($config['consumer_key'], $config['consumer_secret'] ); $oauth->setAuthType(OAUTH_AUTH_TYPE_URI); $req = $oauth->getRequestToken($config['request_uri'], "oob"); 25](https://image.slidesharecdn.com/oauth-110517020413-phpapp02-120328105532-phpapp02/75/Oauth-Php-App-33-2048.jpg)
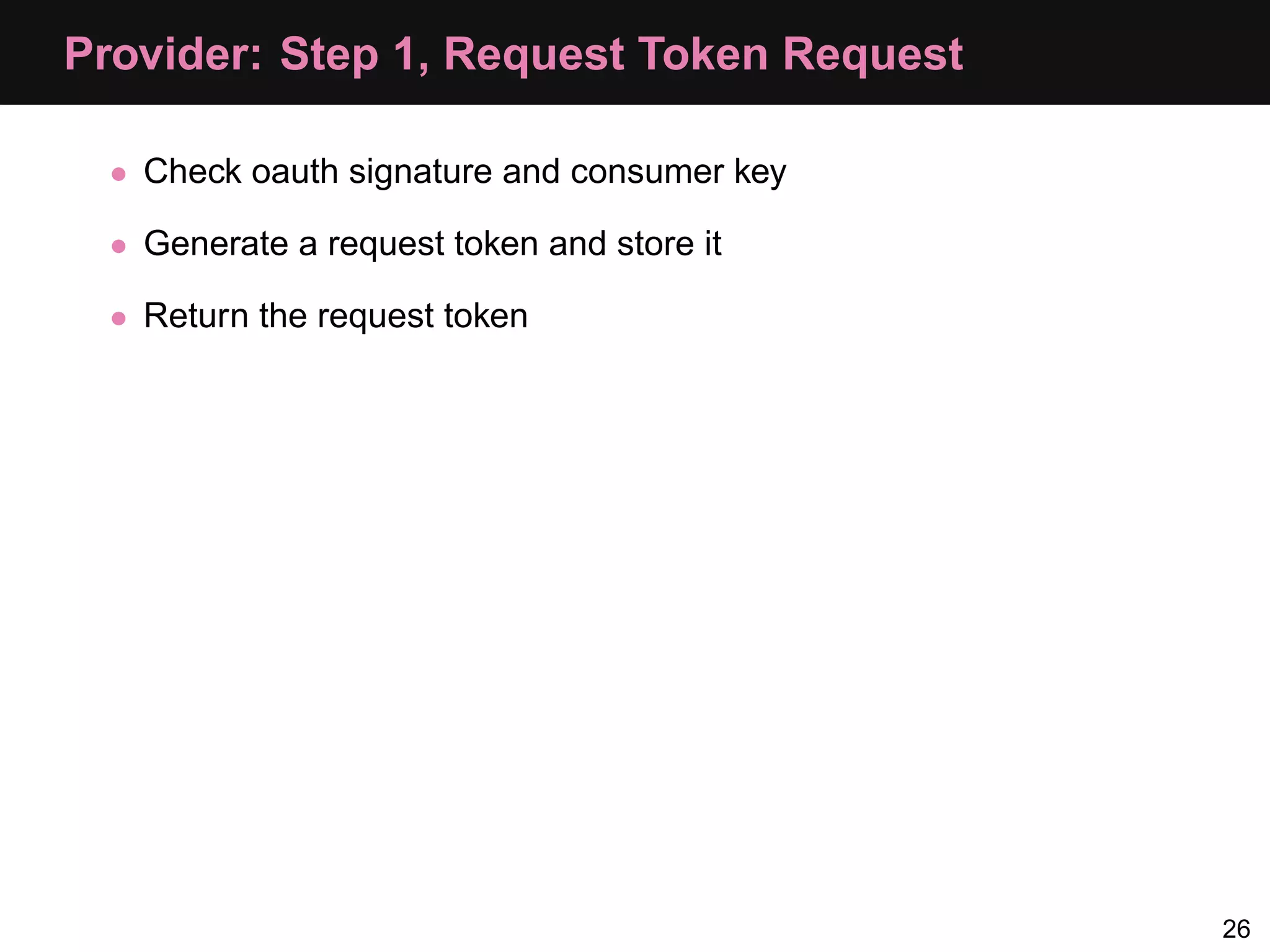
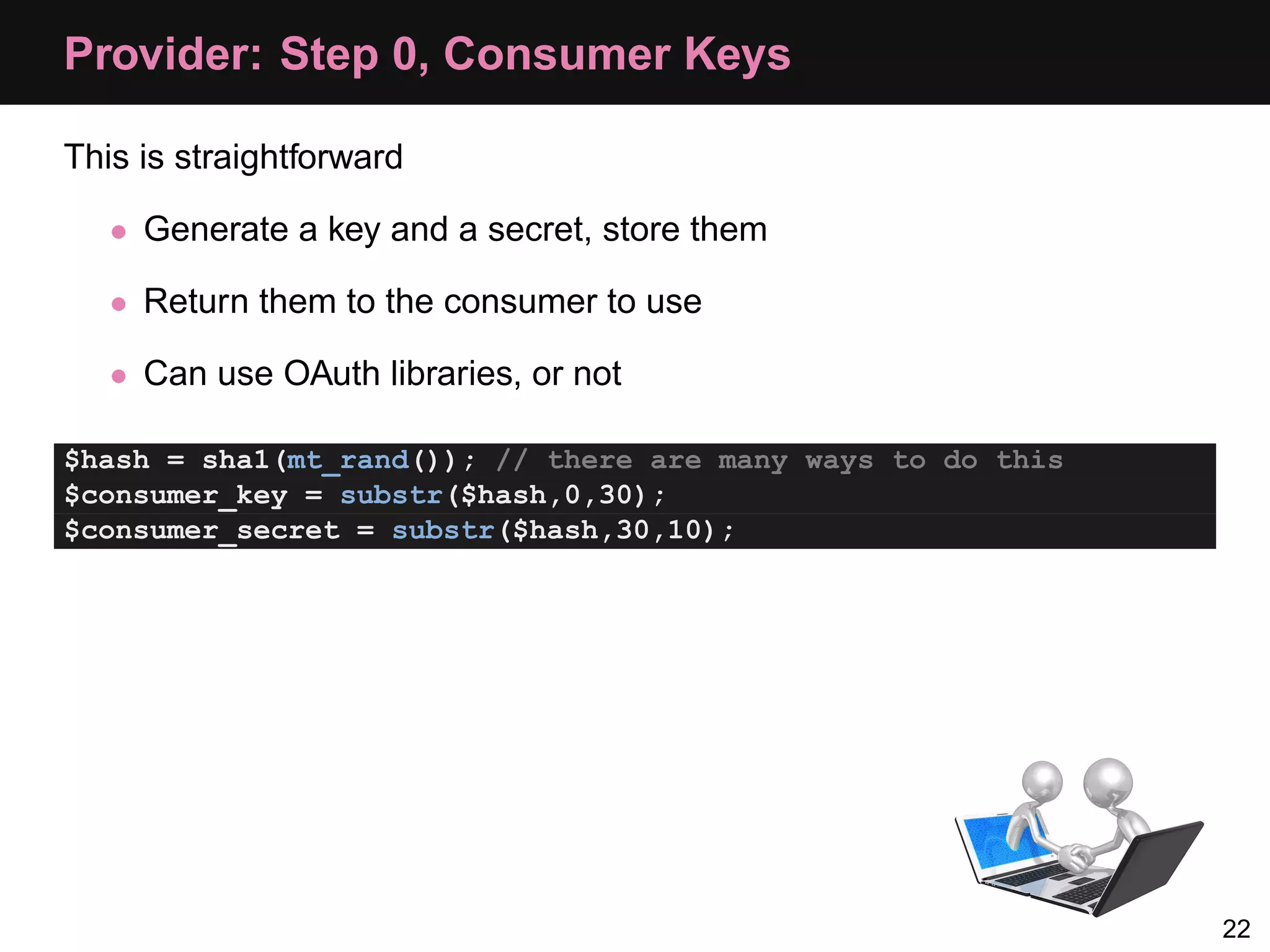
![Provider: Step 1, Generate Request Token Retrieve the callback, and make the token and secret: // remember we're in URI mode parse_str($_SERVER['QUERY_STRING'], &$parameters); $callback = $parameters['oauth_callback']; $request_token = bin2hex($provider->generateToken(4)); $request_token_secret = bin2hex($provider->generateToken(12)); We then simply echo the resulting variables in query format, e.g. echo 'login_url = http://api.joindin.local/user/oauth_allow?' . 'request_token = ' . $request_token . '&request_token_secret = ' . $request_token_secret . '&oauth_callback_confirmed = true'; 27](https://image.slidesharecdn.com/oauth-110517020413-phpapp02-120328105532-phpapp02/75/Oauth-Php-App-35-2048.jpg)

![Consumer: Step 3, Request an Access Token $oauth = new OAuth($config['consumer_key'], $config['consumer_secret']); // request token, request token secret and verification all set // by earlier steps, and loaded into $config try{ $oauth->setToken( $config['request_token'], $config['request_token_secret']); $access = $oauth->getAccessToken($config['access_uri'], null, $config['verification']); } catch (OAuthException $e) { echo $e->getMessage(); } 33](https://image.slidesharecdn.com/oauth-110517020413-phpapp02-120328105532-phpapp02/75/Oauth-Php-App-41-2048.jpg)
![Provider: Step 3, Generate Access Token Generate and store access token and secret, then return: echo "oauth_token=" . $tokens['oauth_token'] . '&oauth_token_secret=' . $tokens['oauth_token_secret']; 34](https://image.slidesharecdn.com/oauth-110517020413-phpapp02-120328105532-phpapp02/75/Oauth-Php-App-42-2048.jpg)
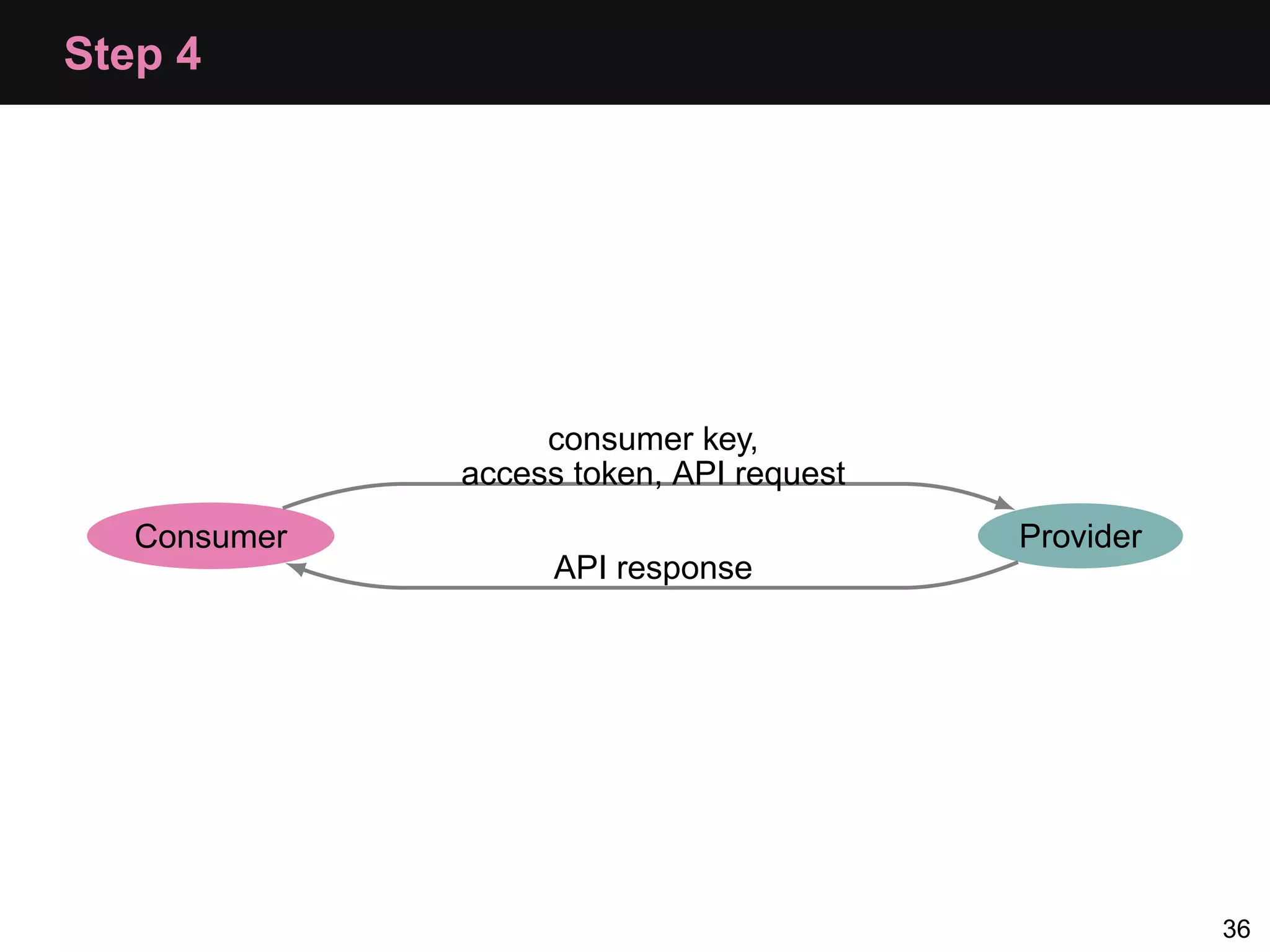
![Consumer: Step 4, Subsequent Requests $oauth = new OAuth($config['consumer_key'], $config['consumer_secret']); // from the getAccessToken call $oauth->setToken($oauth_token, $oauth_token_secret); $result = $oauth->fetch("http://api.local/usual/call/here"); if($result) { $response = $oauth->getLastResponse(); } 37](https://image.slidesharecdn.com/oauth-110517020413-phpapp02-120328105532-phpapp02/75/Oauth-Php-App-45-2048.jpg)