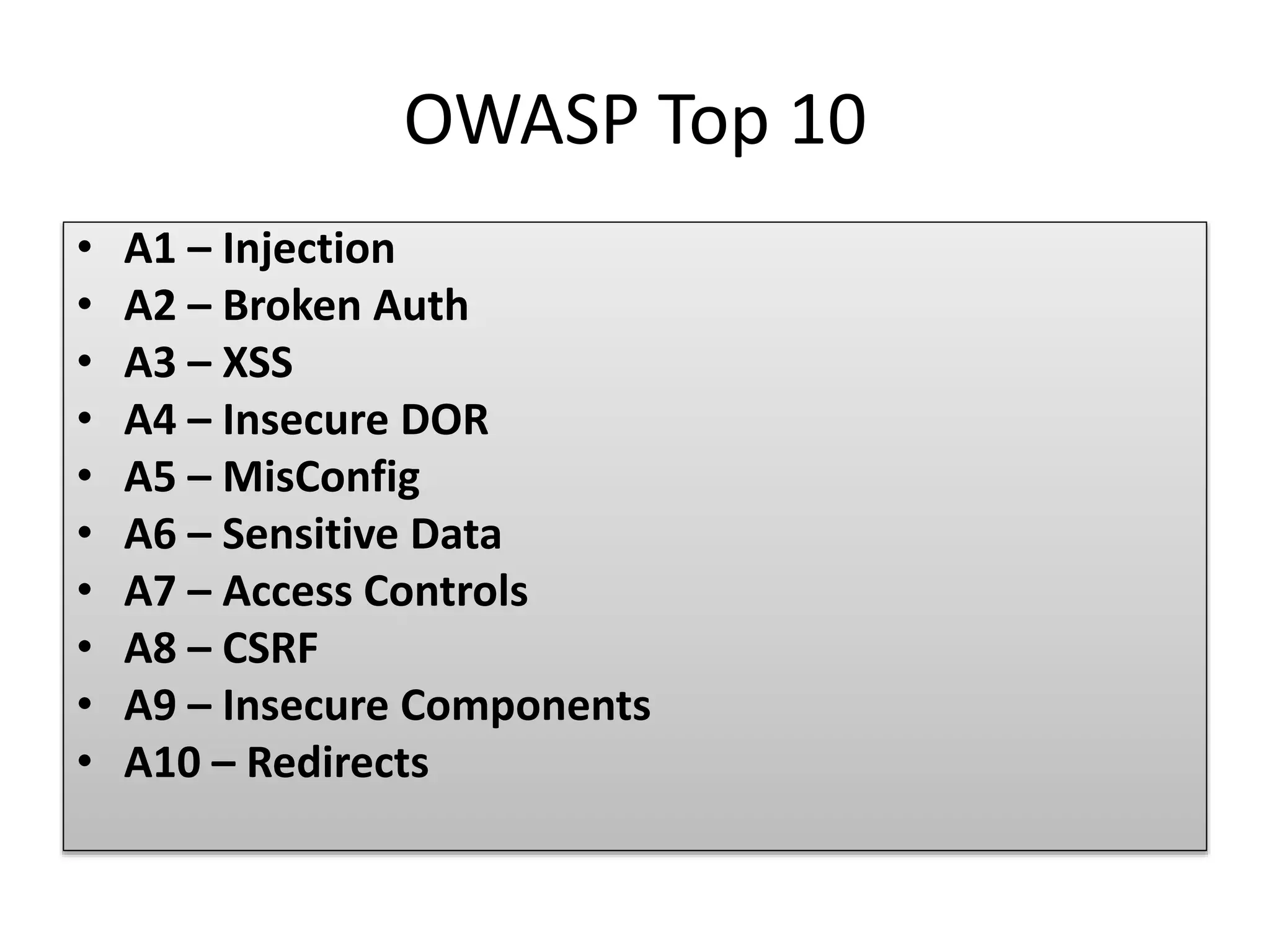
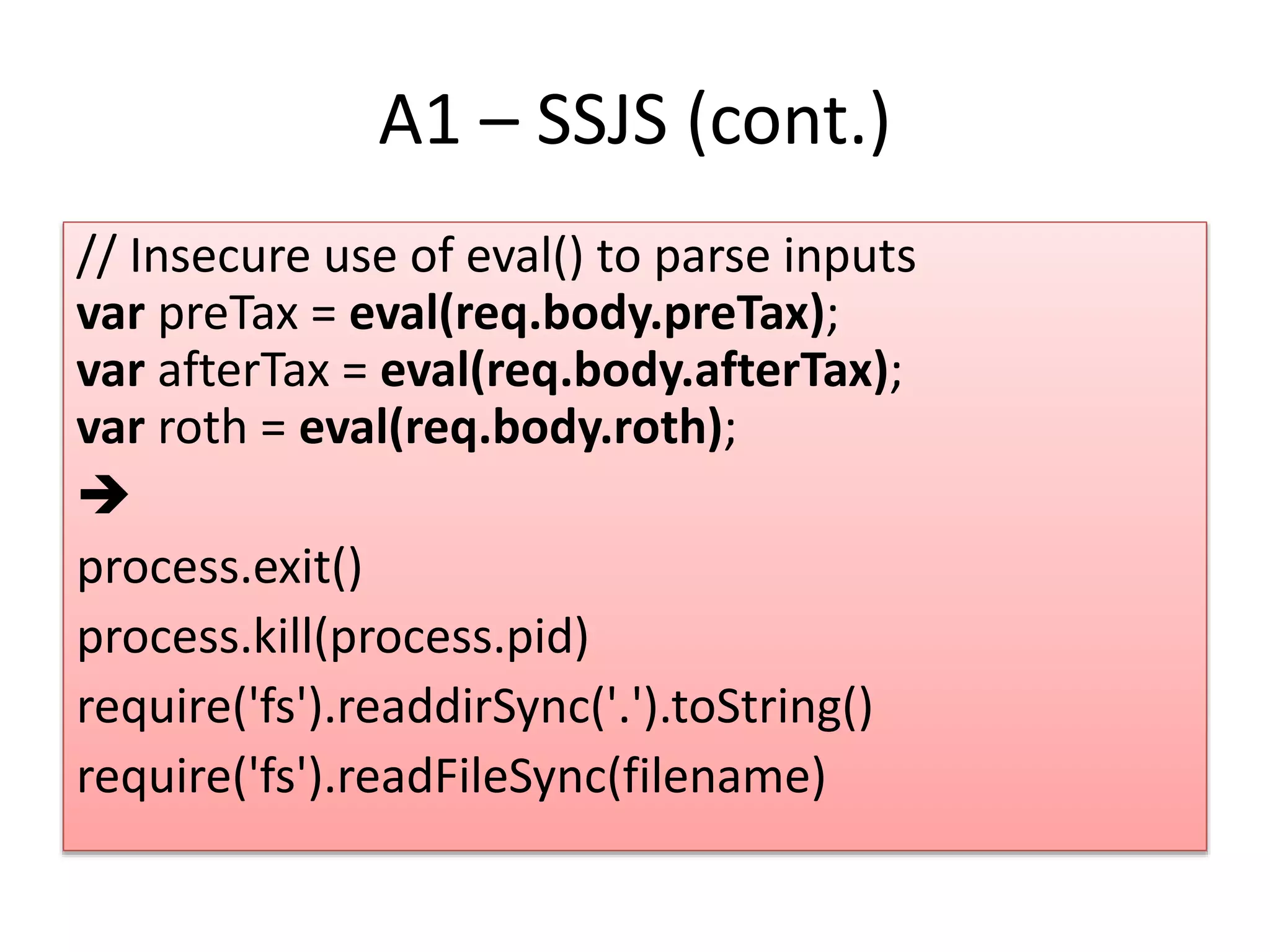
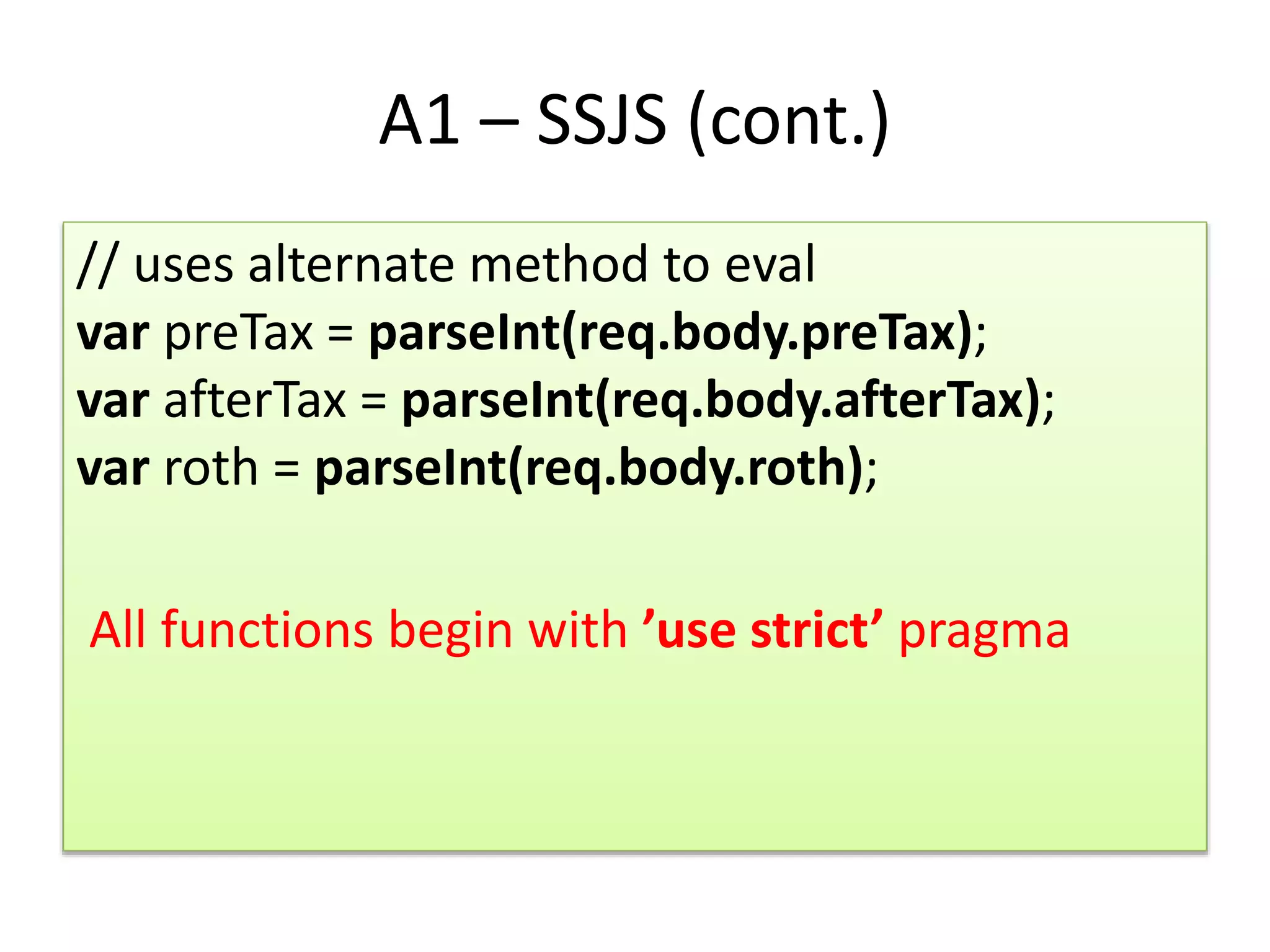
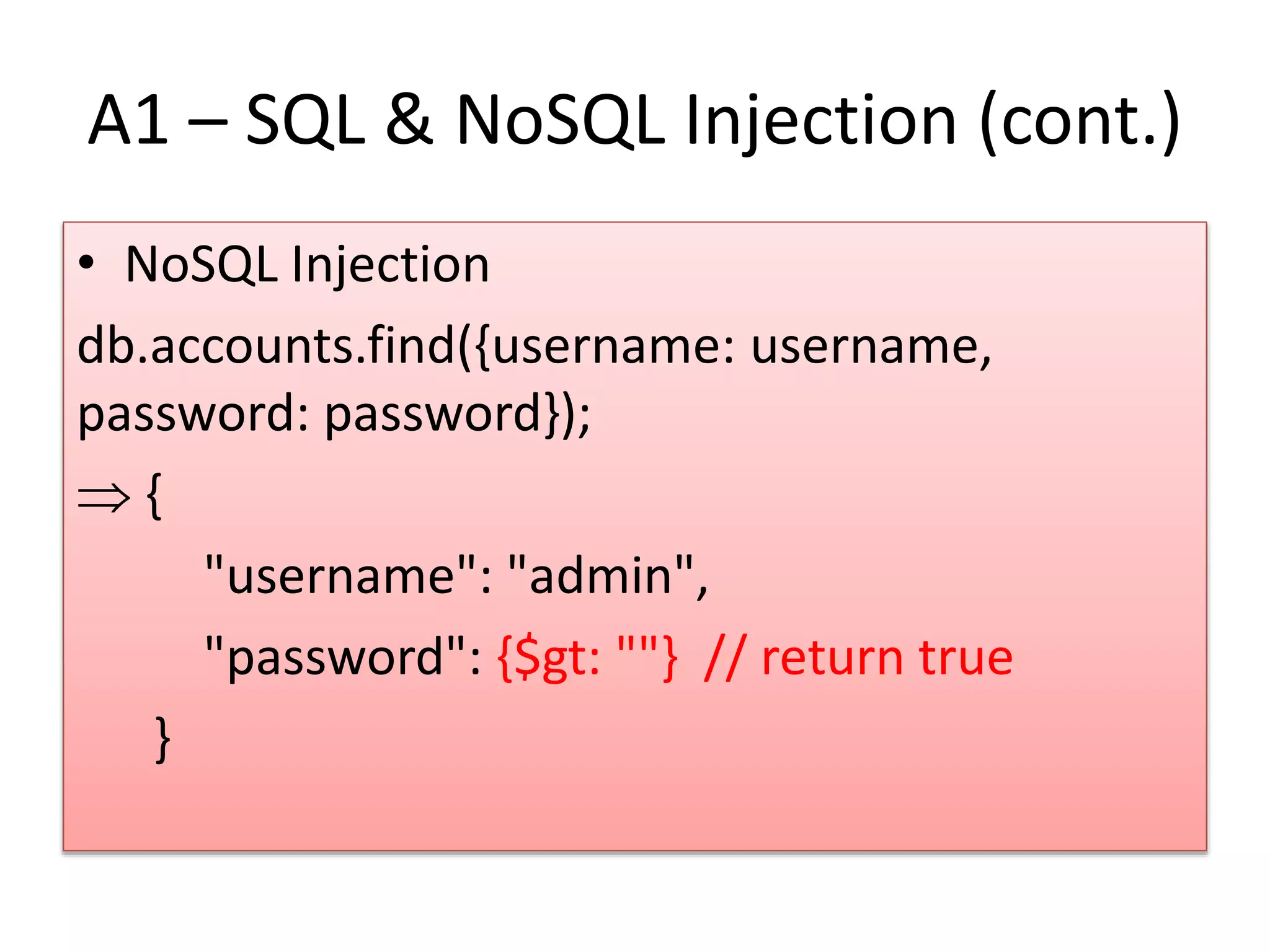
This document provides an overview of secure coding practices for Node.js applications. It discusses common vulnerabilities like injection, broken authentication, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, lack of access controls, CSRF, use of vulnerable components, and unvalidated redirects. For each issue, it provides examples of insecure code and suggestions for more secure implementations using input validation, encryption, access control checks, HTTPS, CSRF tokens, and other best practices. It also lists some useful security tools and resources for Node.js applications.




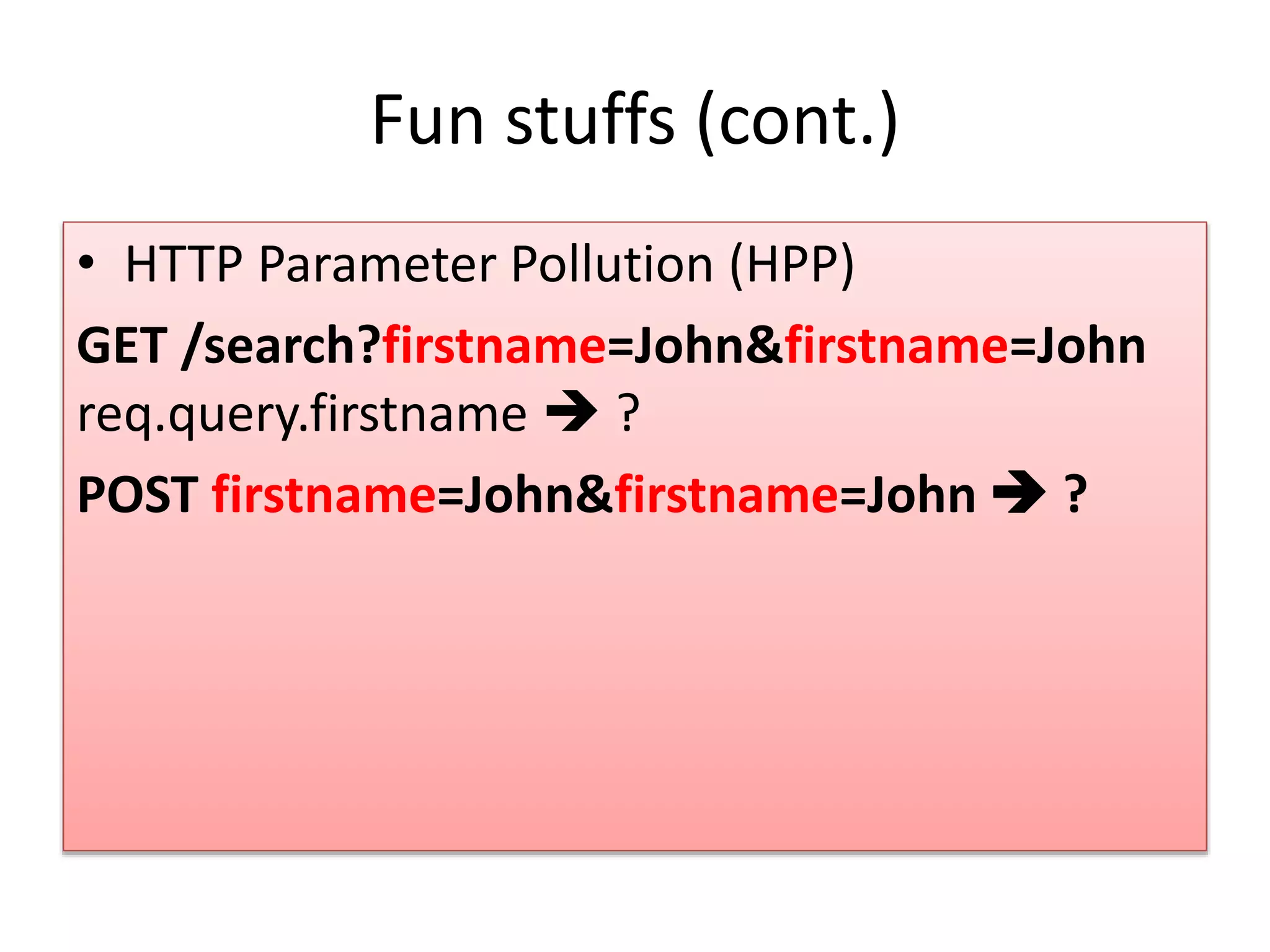
![Fun stuffs (cont.) Commonly used URL validator regex /^(?!mailto:)(?:(?:https?|ftp)://)?(?:S+(?::S*)? @)?(?:(?:(?:[1-9]d?|1d d|2[01]d|22[0- 3])(?:.(?:1?d{1,2}|2[0-4]d|25[0-5])){2}(?:.(?: [0-9]d?|1dd|2[0-4]d|25[0-4]))|(?:(?:[a- zu00a1- uffff0-9]+-?)*[a-zu00a1-uffff0- 9]+)(?:.(?:[a-zu00a1- uffff0-9]+-?)*[a-zu00a1- uffff0-9]+)*(?:.(?:[a-zu00a1-uffff]{2,})))| localhost)(?::d{2,5})?(?:/[^s]*)?$/I Input pattern: aaaaaaaaaaaaaaaa!](https://image.slidesharecdn.com/securecodingfornodejs-160316184929/75/Secure-Coding-for-NodeJS-5-2048.jpg)














![A2 – Password Guessing Attacks (cont.) var PASS_RE = /^.{1,20}$/; var PASS_RE =/^(?=.*d)(?=.*[a-z])(?=.*[A- Z]).{8,}$/;](https://image.slidesharecdn.com/securecodingfornodejs-160316184929/75/Secure-Coding-for-NodeJS-25-2048.jpg)