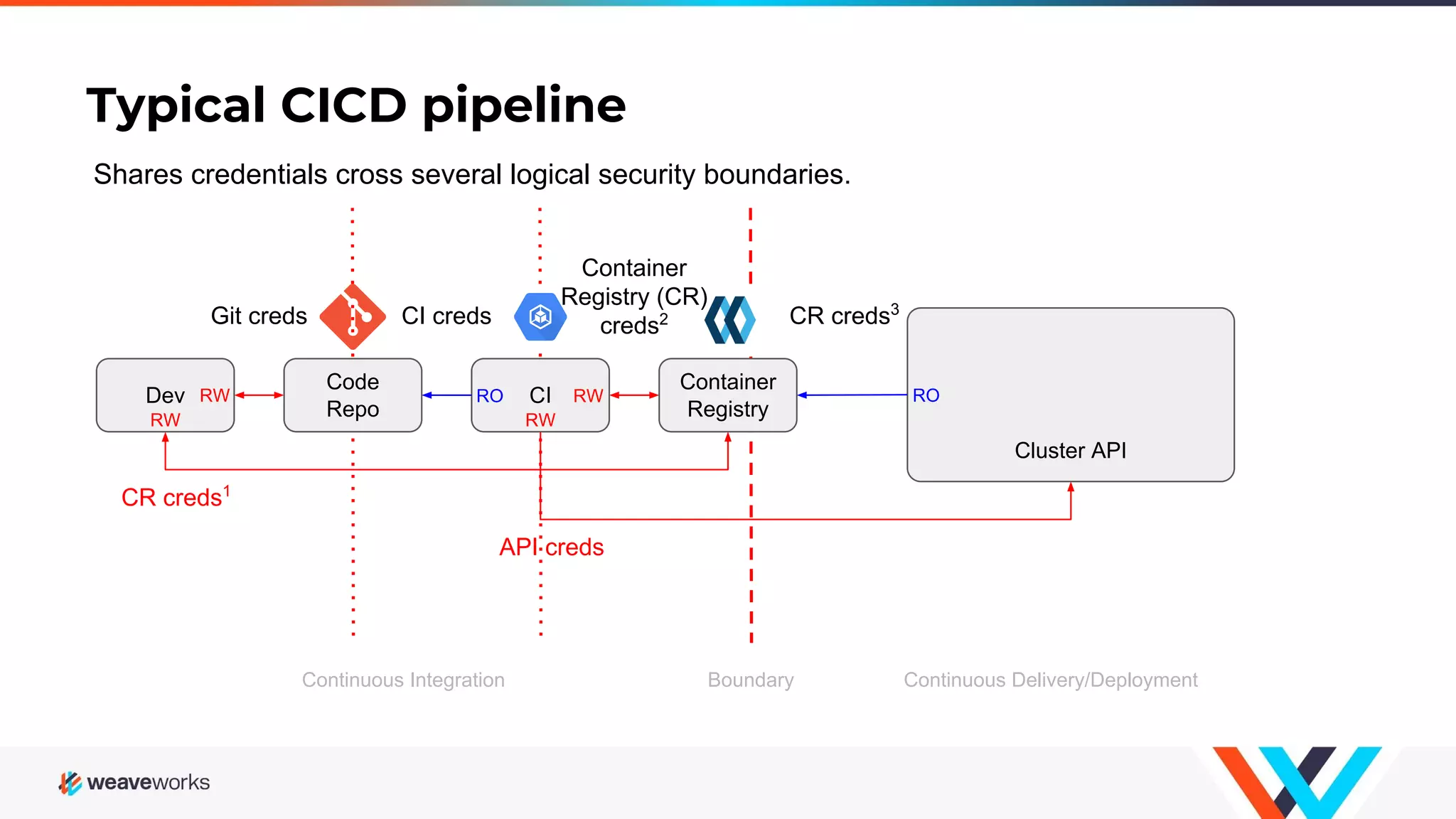
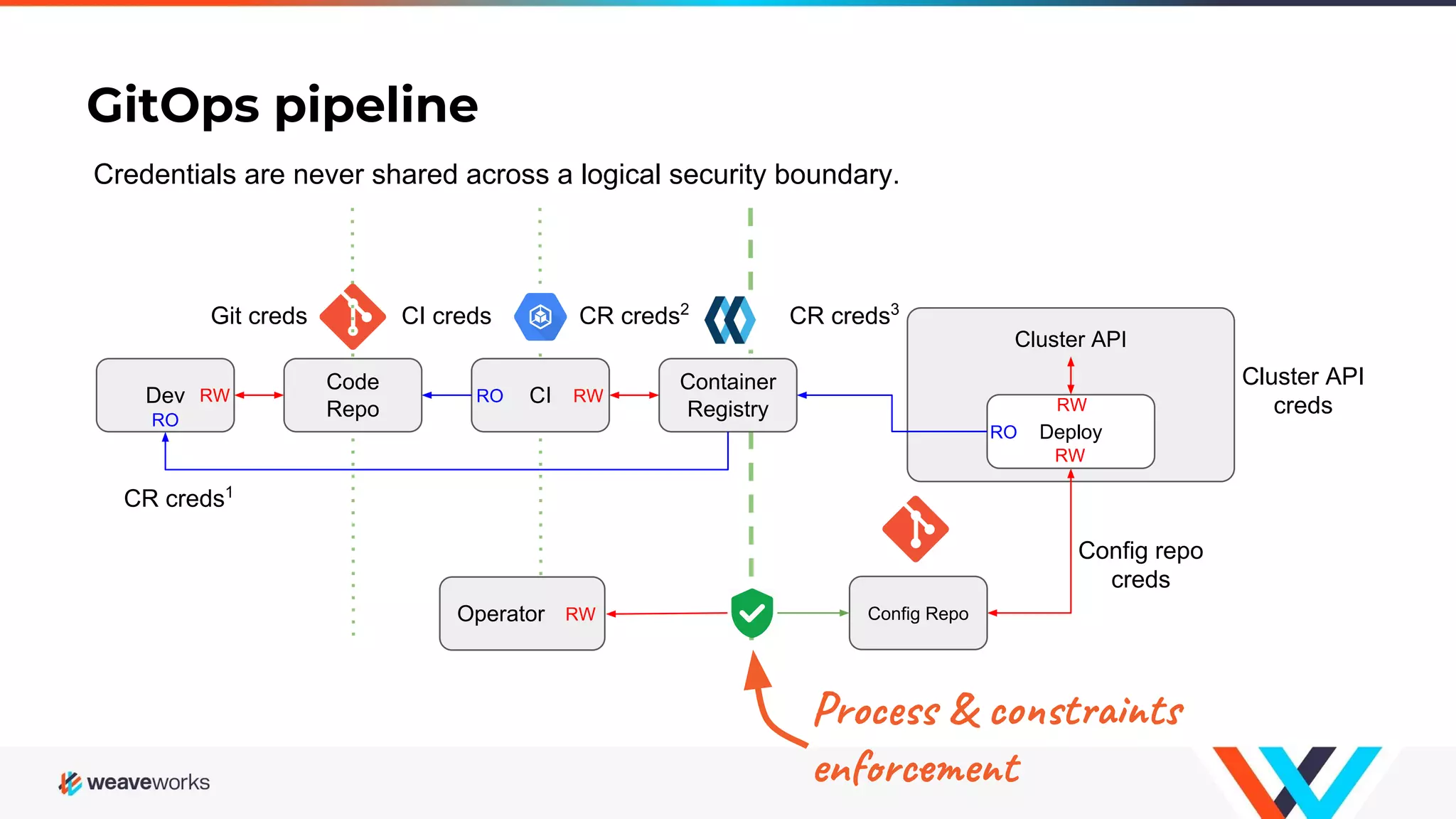
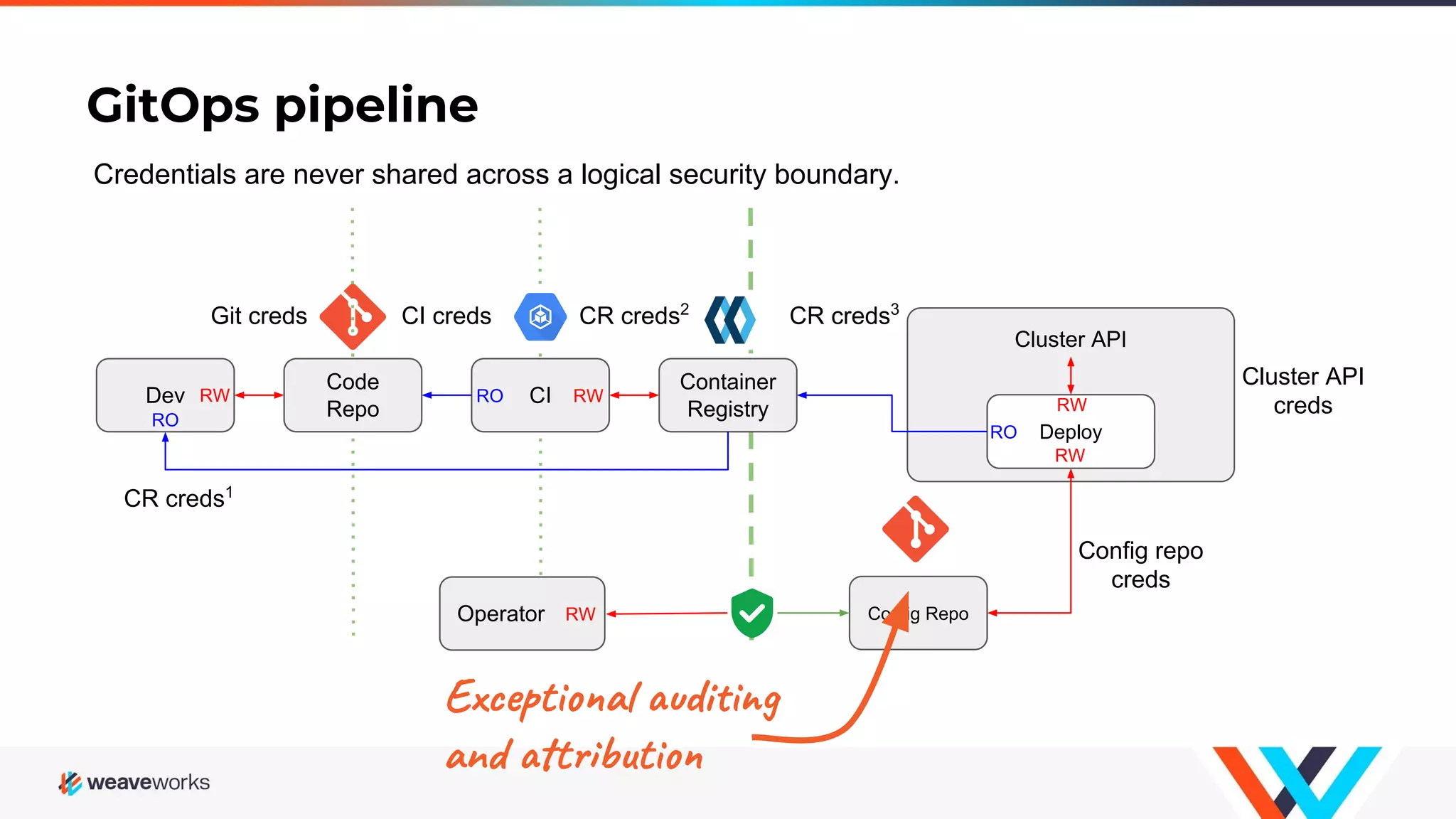
1. The webinar discussed securing developer workflows through implementing GitOps principles and securing repositories. 2. GitOps is described as an operations model that defines the entire system declaratively with the canonical desired system state versioned in Git. 3. Approved changes to the desired state are automatically applied to the system by software agents that ensure correctness and alert on any divergence from the declared state. 4. The presentation provided recommendations for securing repositories by enforcing strong identity, preventing history rewrites and removal of security features, and avoiding deprecated software.