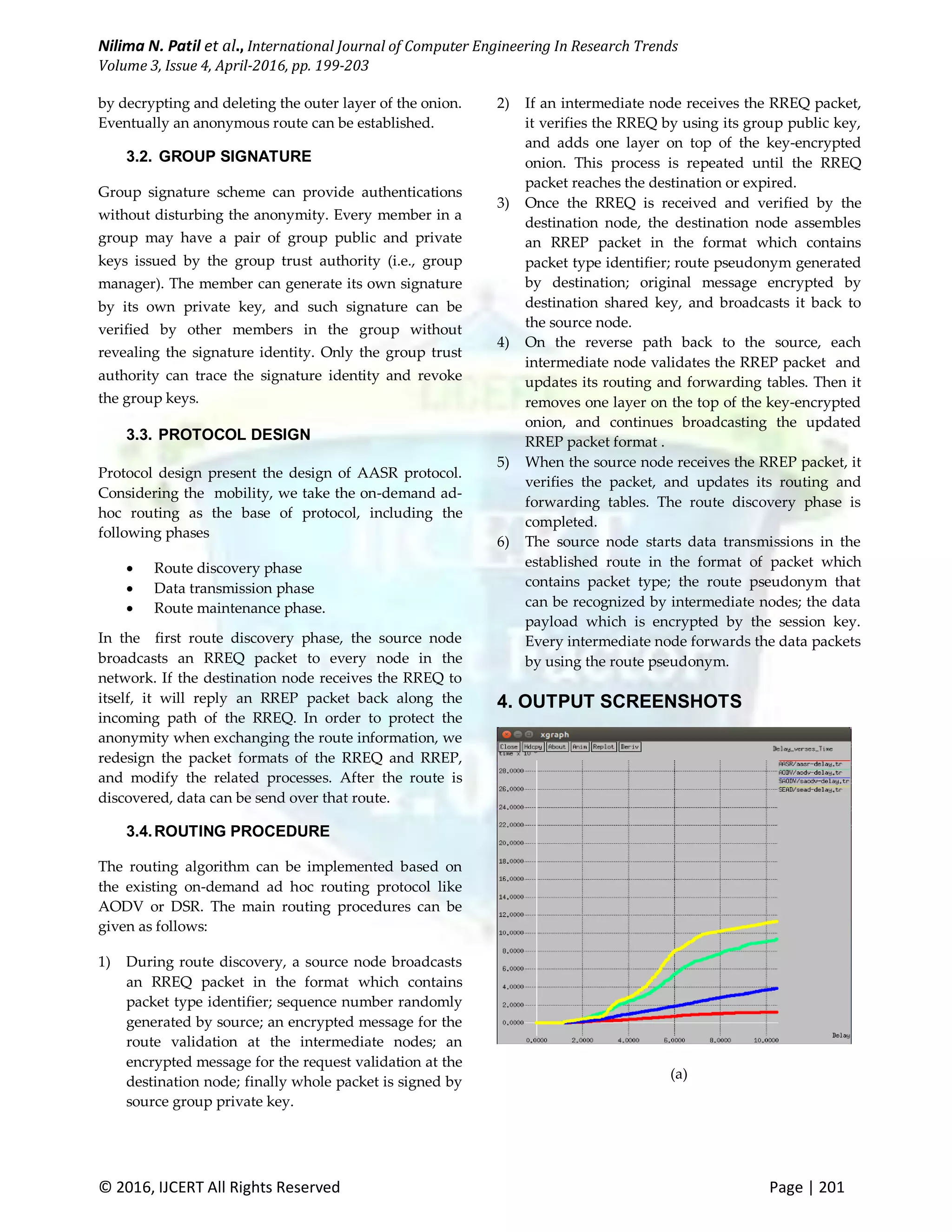
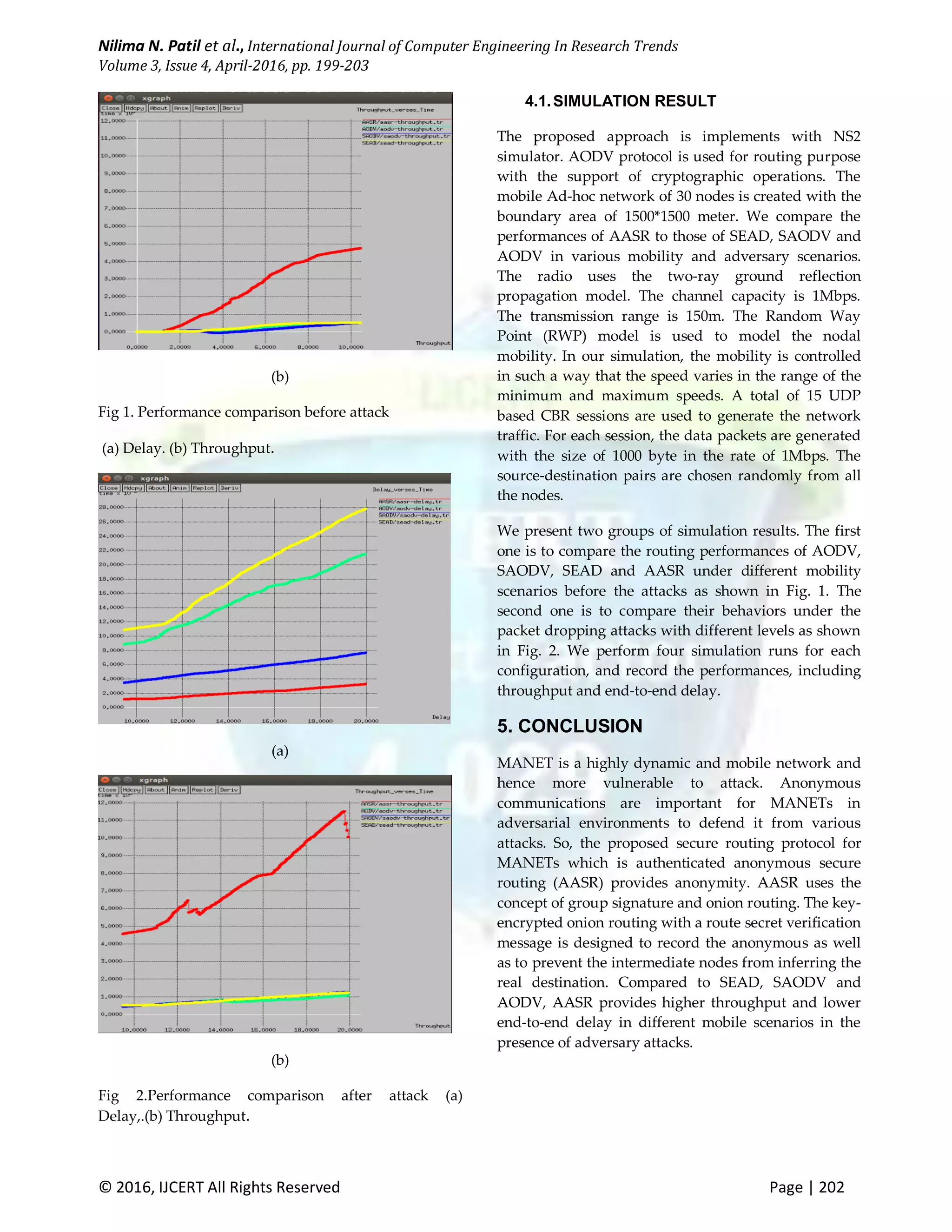
The document discusses the vulnerabilities of mobile ad hoc networks (MANETs) to security threats in adversarial environments and proposes a new secure routing protocol called Authenticated Anonymous Secure Routing (AASR). AASR aims to achieve anonymity and defend against attacks such as denial-of-service by utilizing a combination of group signatures and key-encrypted onion routing for secure communication. Simulation results indicate that AASR outperforms existing protocols like AODV, SAODV, and SEAD in terms of throughput and end-to-end delay.

![Nilima N. Patil et al., International Journal of Computer Engineering In Research Trends Volume 3, Issue 4, April-2016, pp. 199-203 © 2016, IJCERT All Rights Reserved Page | 200 so many anonymous routing protocols proposed. Our main aim is the type of topology based on-demand anonymous routing protocols, which are general for MANETs in adversarial environments. The commonly used on-demand ad hoc routing protocols are AODV [2] and DSR . Secure Ad-hoc On-demand Distance Vector RoutingProtocol (SAODV) [4] is advance version of AODV routing protocol. SAODV make use of asymmetric cryptography with the help of group signatures. When a node wants to send a message it digitally signs the RREQ packet and send it to the neighboring nodes.On receiving a RREQ, intermediate nodes verifies the signature before updating or creating a reverse route to the hostwith the help of cryptography. Secure Efficient Ad-hoc Distance Vector Routing (SEAD) [3] protocolis a proactive routingprotocol which maintains fresh lists of destinations and their routes by periodically distributing routing tables throughout the network. This protocol makes use of hash chain method for checking the authenticity of the data packet. This hash chainvalue is used for transmitting a routing update. A node that receives a routing update, verifies theauthentication of eachentry of the message. SEAD make use of destination sequence number in order to remove looping. Both SAODV and SEAD cannot satisfy the requirement of anonymous communications. Now, we focus on the MANETs in adversarial environments, where the public and group key can be initially deployed in the mobile nodes. We propose an authenticated anonymous secure routing (AASR) to overcome the above problems. We use a key-encrypted onion to record a discovered route and design an encrypted secret message to verify the RREQ-RREP. To authenticate the RREQ packet at each hop is necessary which is achieved by group signature. 2. RELATED WORK G. Anandhi, Dr. S. K. Srivatsa [1], provide a detailed survey of different kind of attacks and proposed solutions for handling those attacks. Their paper also gives a brief comparison of various protocols available for secured routing in MANET like Secure Ad-hoc On- demand Distance Vector Routing Protocol (SAODV), Secure Efficient Ad-hoc Distance Vector Routing (SEAD), and Security-Aware ad hoc Routing (SAR). Sheng Liu, Yang, Weixing Wang [2], propose the basic characteristic, key techniques of Ad Hoc networks, and compared with other mobile communication systems. Through analyzing and comparing with DSR, TORA, ABR, AODV, it researched on-demand routing protocol for Ad Hoc networks. It introduces AODV routing protocol in details. Prasuna V G, Dr. S. Madhusudhana Verma [3], propose Secure Efficient Ad hoc Distance Vector with fixed hash chain length in short SEAD-FHC protocol to minimize and stabilize the computational complexity that leads minimization in delay time and maximization in throughput. A series of simulation experiments are conducted to evaluate the performance. C. Sreedhar, Dr. S. Madhusudhana Verma, Dr. N. Kasiviswanath [4], describes Secure AODV routing protocol which was designed to enhance security services to the original AODV. SAODV protocol was designed with cryptographic techniques such as digital signatures, which can have significant impact on the routing performance of AODV routing protocol. 3. PROPOSED WORK There are many anonymous on-demand routing protocols. But these protocols arevulnerable to the denial-of-service (DoS) attacks, such as RREQ based broadcasting. Due to thelack of packet authentication, it is difficult for the protocolsto check whether a packet has been modified by a malicious node. So, we proposed the other routing protocol known as authenticated anonymous secure routing (AASR) which is topology-based routing rather than location- based routing. To avoid theinformation leakage during RREQ and RREP processes, AASR uses the nodes pseudonym instead of its real identifier. We choose the onion based routing to record the anonymous routes, because the onion is more scalable than othermechanisms and can be extended, for example to multiple paths.We assume that the nodes are equipped with public and private keys during network initializationphase and can generate the shared symmetric key in an on-demand manner. 3.1. ONION ROUTING It is a mechanism to provide private communications over a public network. The source nodesets up the core of an onion with a specific route message.During a route request phase, each forwarding node adds an encrypted layer to the route request message. The sourceand destination nodes do not necessarily know the ID of a forwarding node. The destination node receives the onion and delivers it along the route back to the source. The intermediate node can verify its role](https://image.slidesharecdn.com/v3i415-160518191343/75/Secure-Routing-for-MANET-in-Adversarial-Environment-2-2048.jpg)
![Nilima N. Patil et al., International Journal of Computer Engineering In Research Trends Volume 3, Issue 4, April-2016, pp. 199-203 © 2016, IJCERT All Rights Reserved Page | 203 REFERENCES [1] Sneddon, G.Anandhi, Dr.S.K.Srivatsa, “Secured Routing in MANETs”, International Journal of Computer Science and Information Technology, Vol. 2, Issue 2, pp.: (311-318), Month: April-June 2014. [2] Sheng Liu, Yang, Weixing Wang, “Research of AODV Routing Protocol for AdHoc Networks”, 2013 AASR, Conference on Parallel and Distributed Computing and Systems. [3] Prasuna V. G, Dr. S. Madhusudhana Verma, “SEAD-FHC: Secure Efficient Distance Vector Routing with Fixed Hash Chain length”, Global Journal of Computer Science and Technology Volume 11 Issue 20 Version 1.0 December 2011 [4] C. Sreedhar, Dr. S. Madhusudhana Verma, Dr. N. Kasiviswanath,“Performance Analysis of Secure Routing Protocols in Mobile Ad-Hoc Networks”, International Journal of Computer Science And Technology .](https://image.slidesharecdn.com/v3i415-160518191343/75/Secure-Routing-for-MANET-in-Adversarial-Environment-5-2048.jpg)