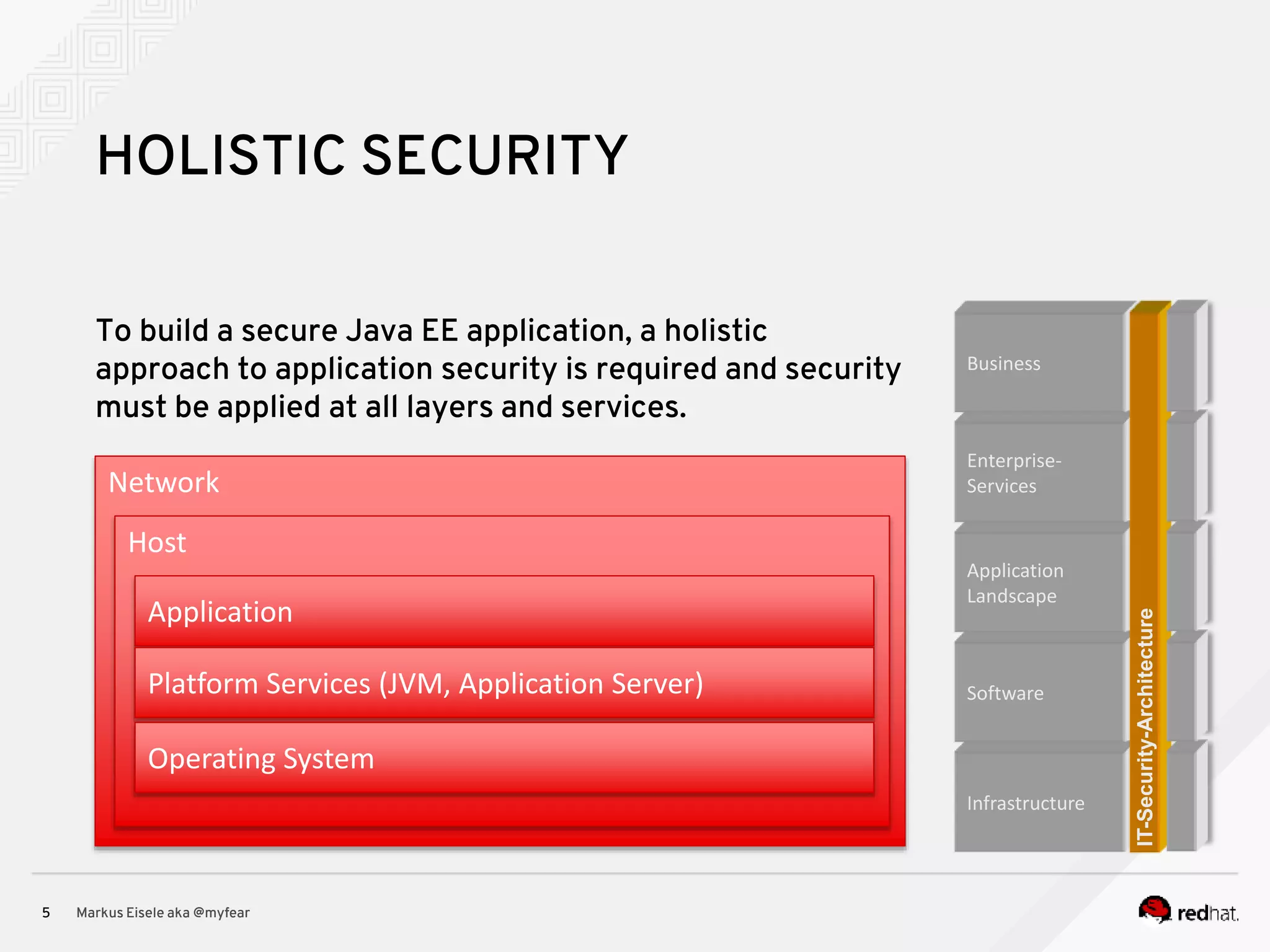
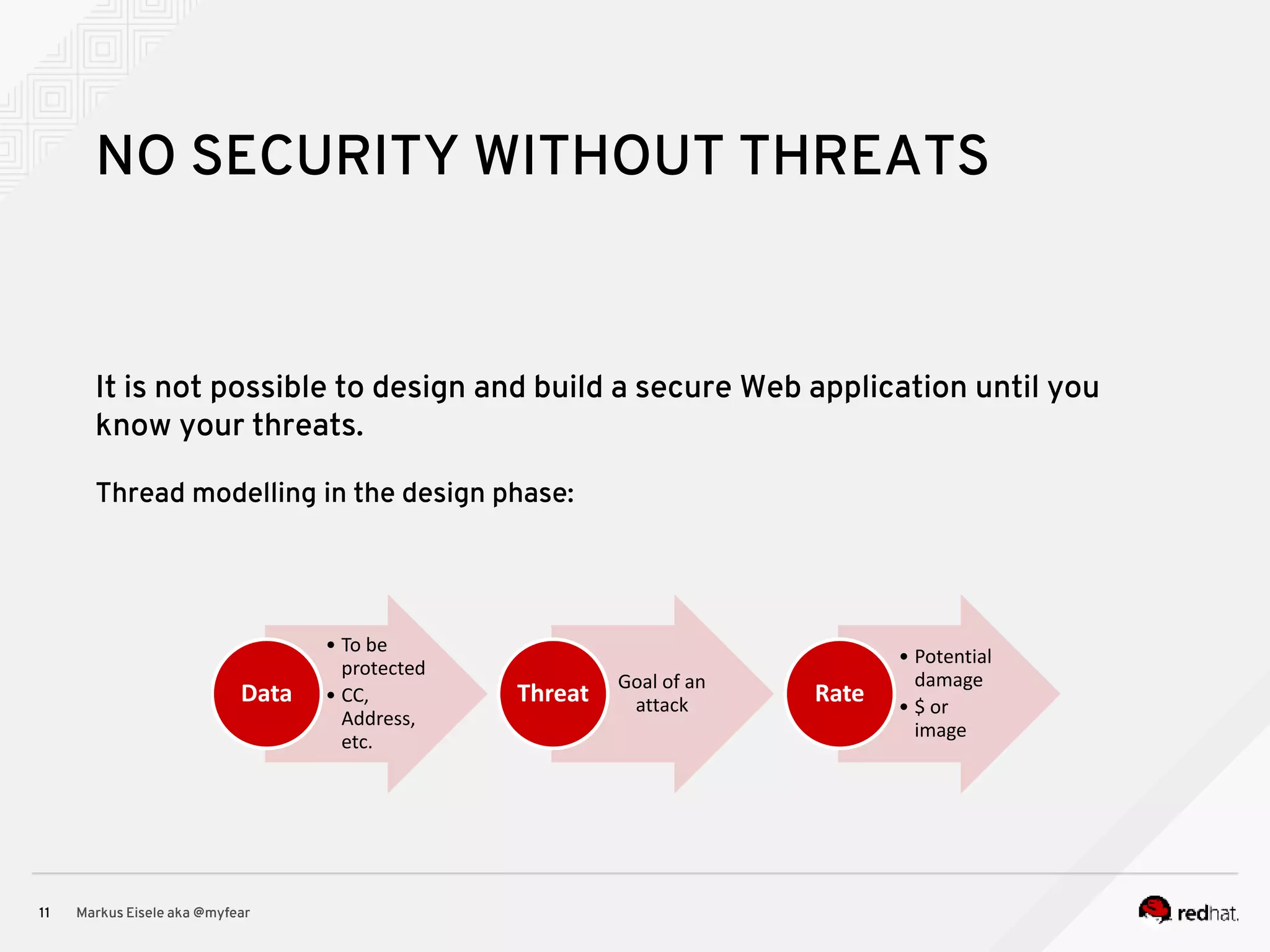
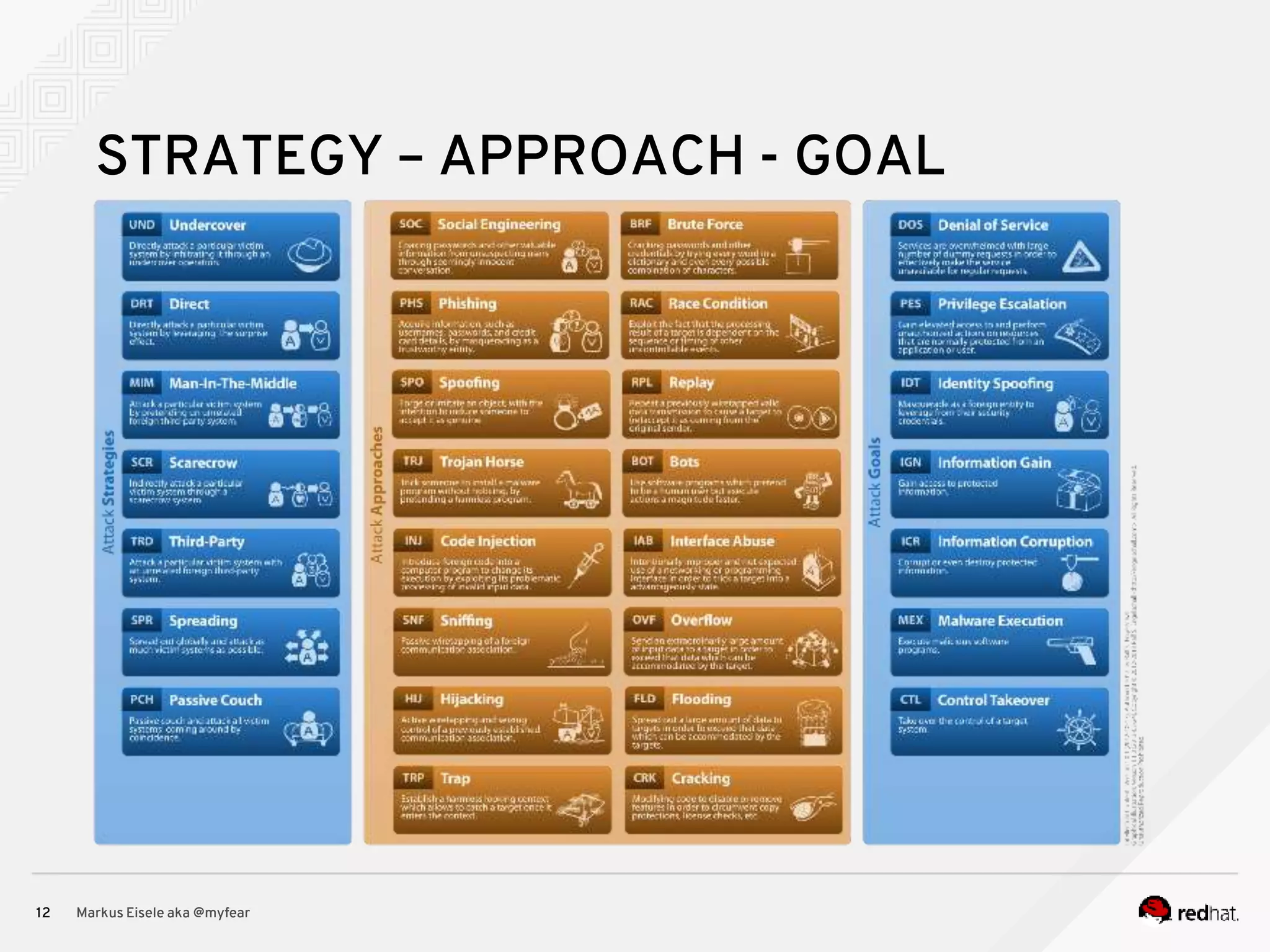
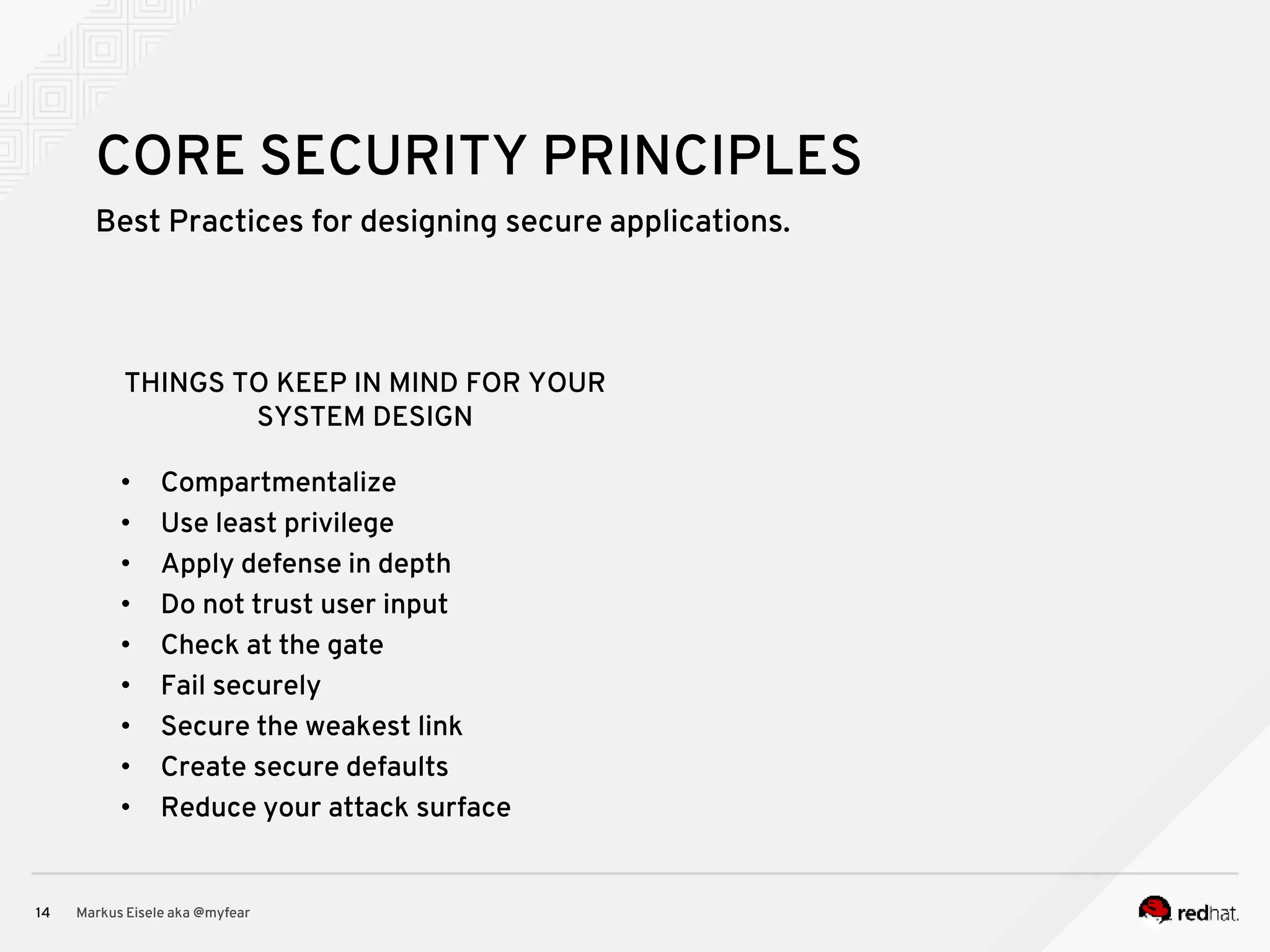
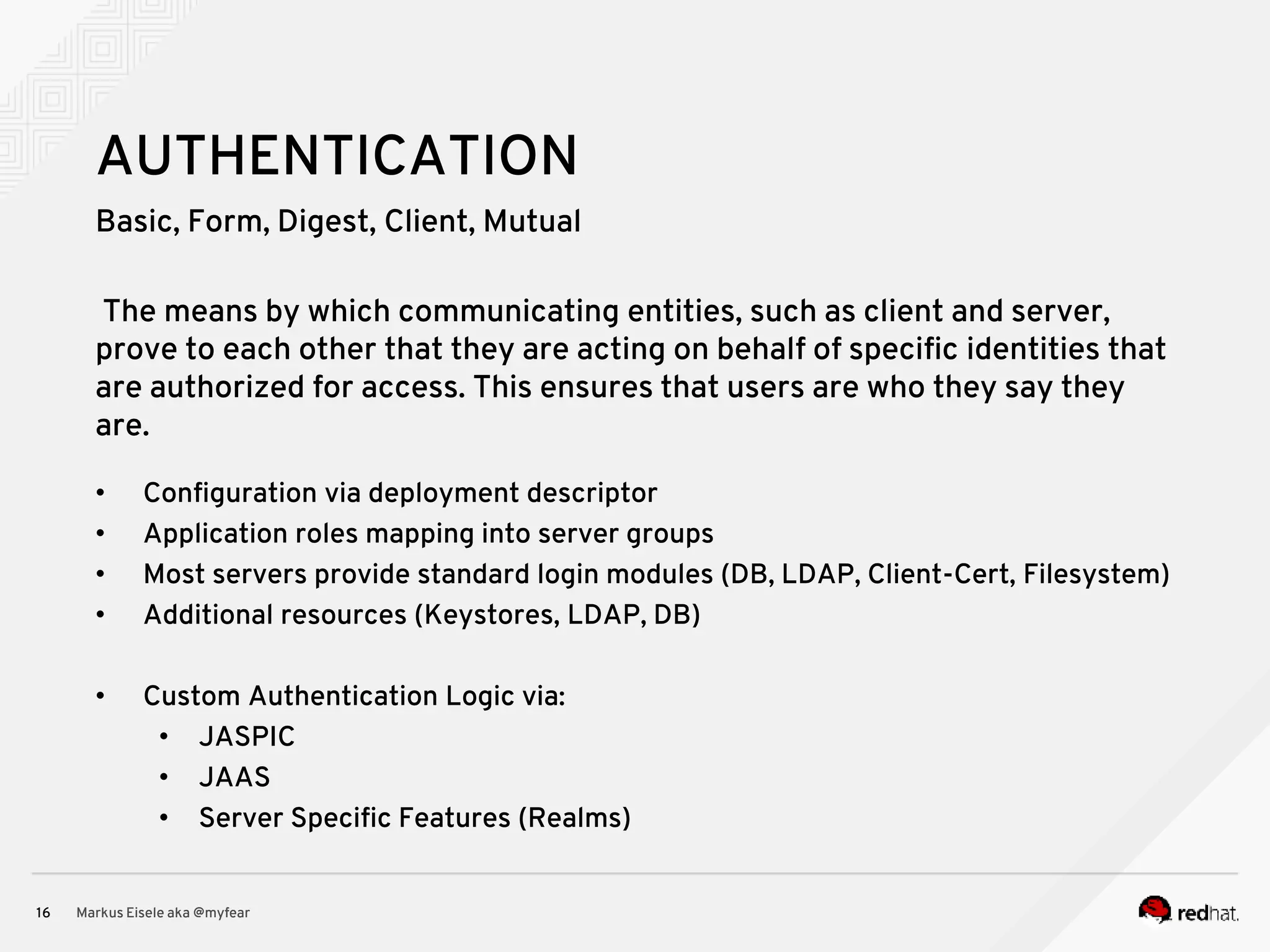
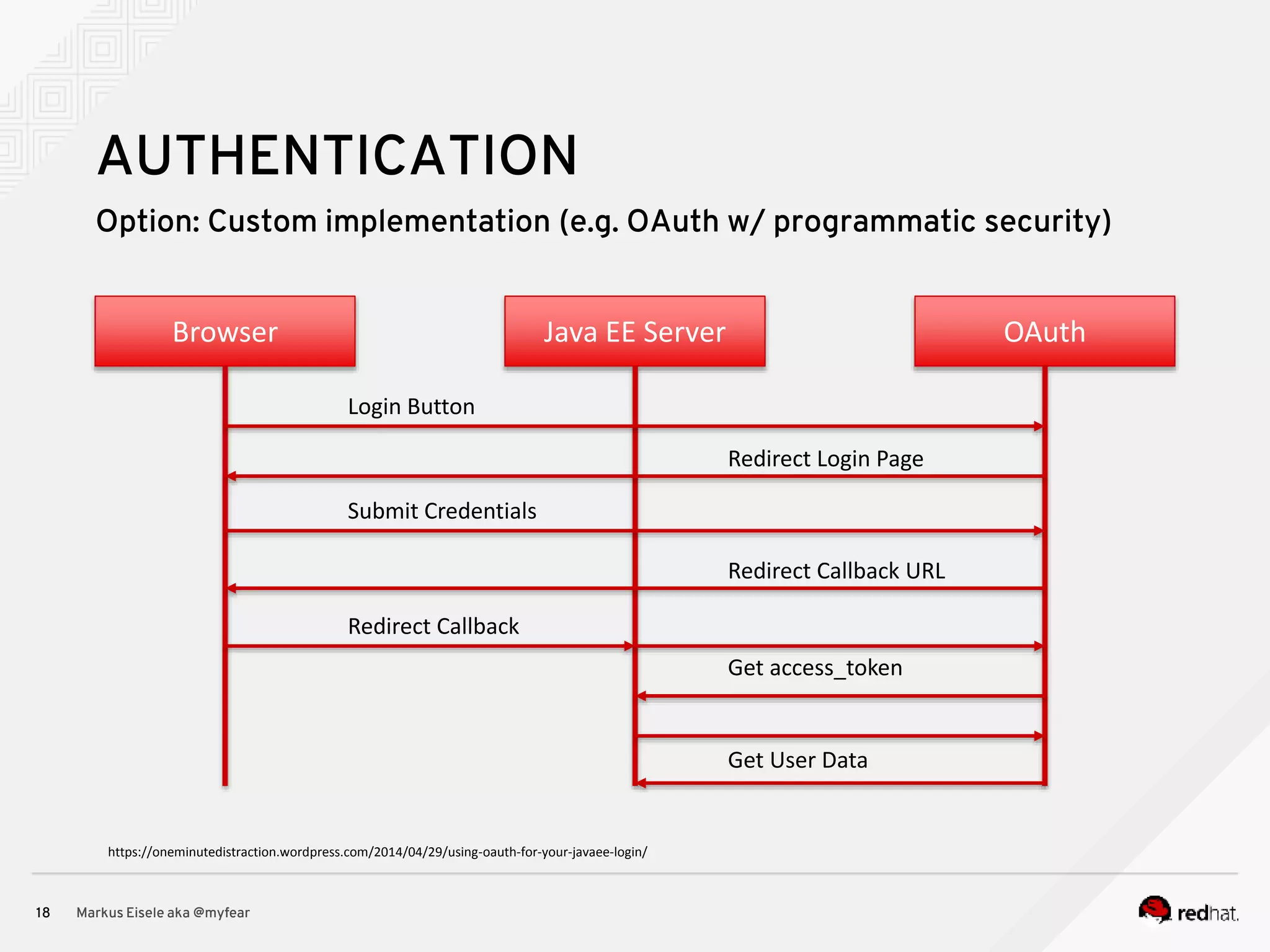
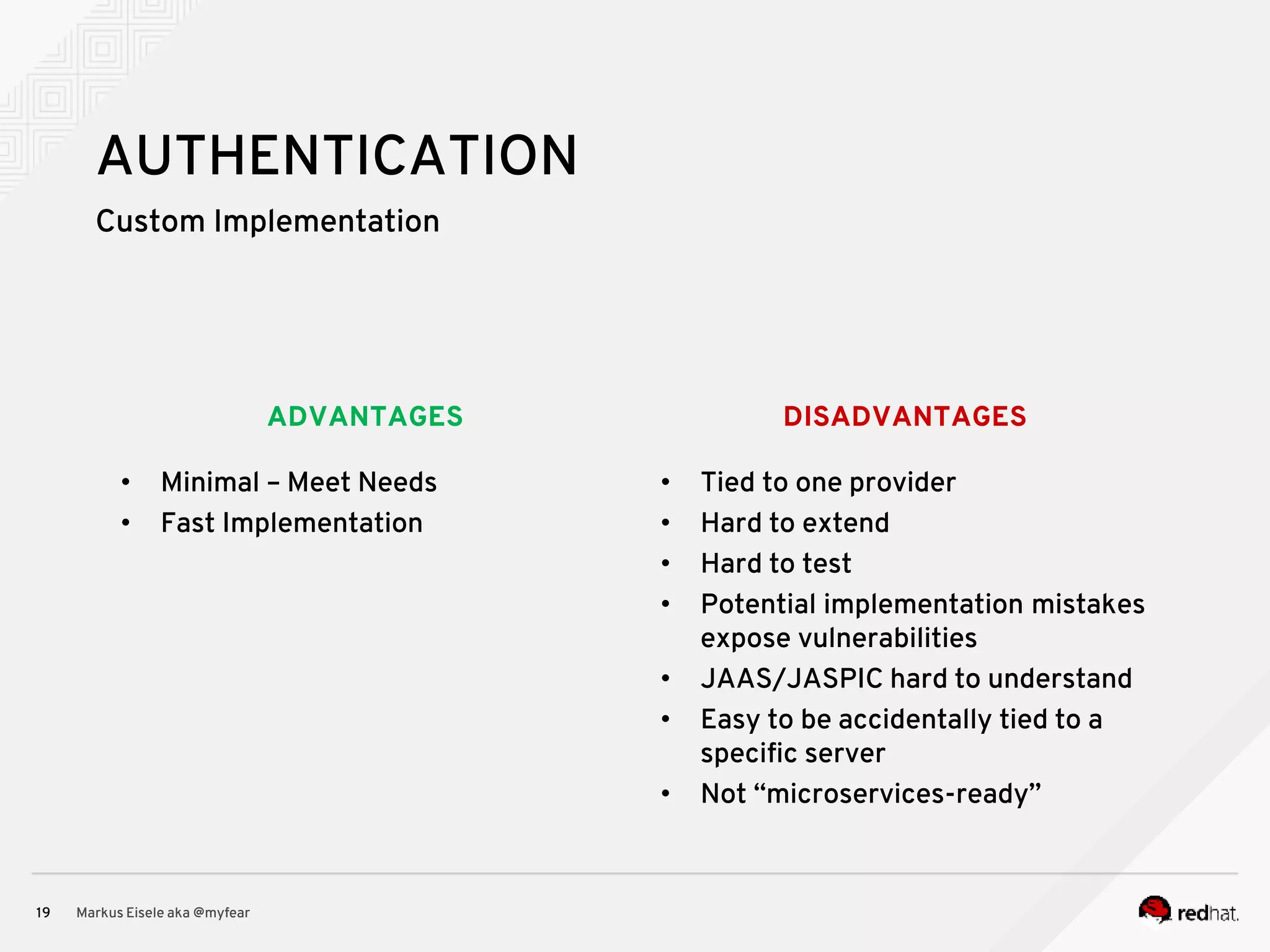
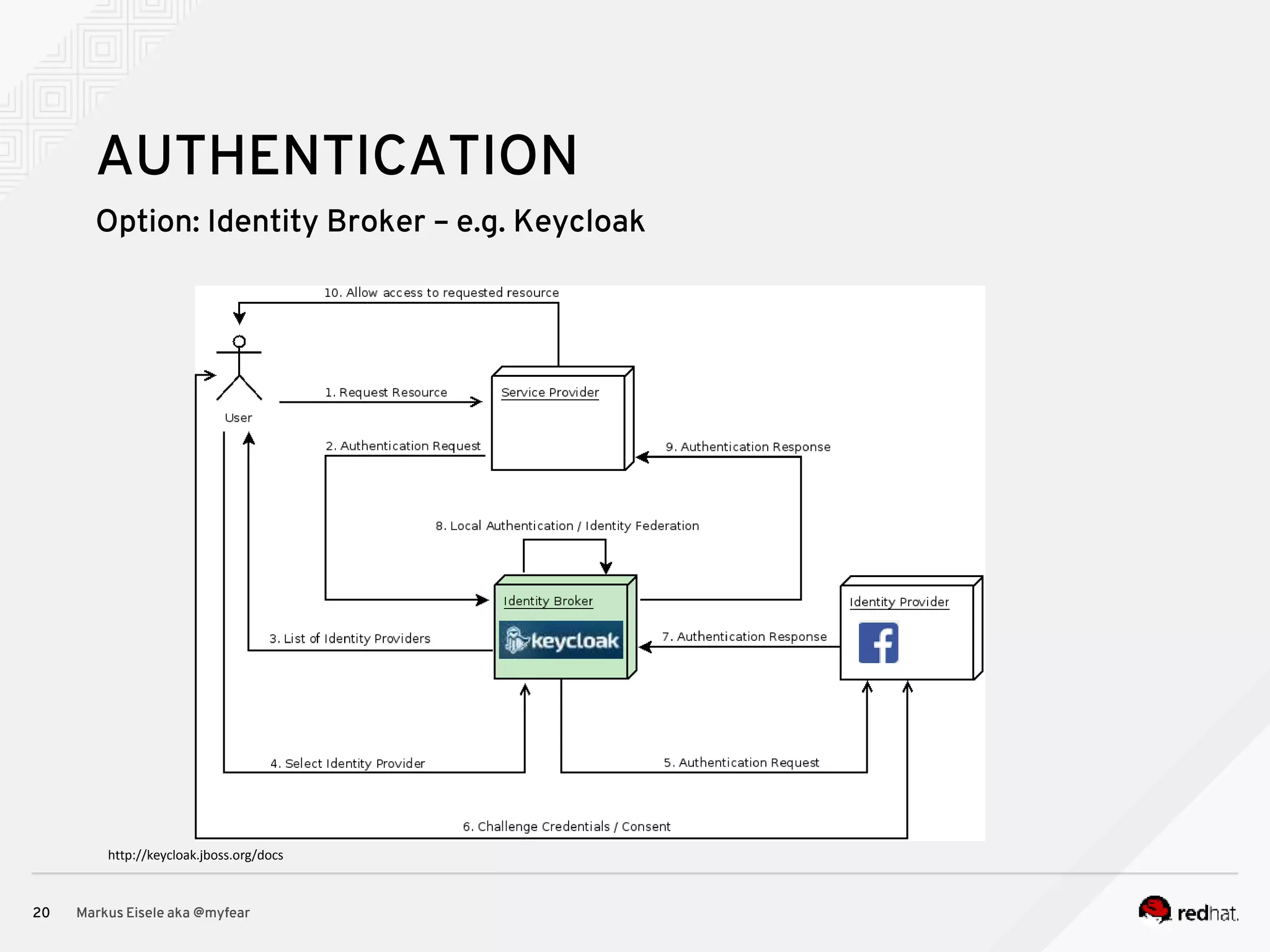
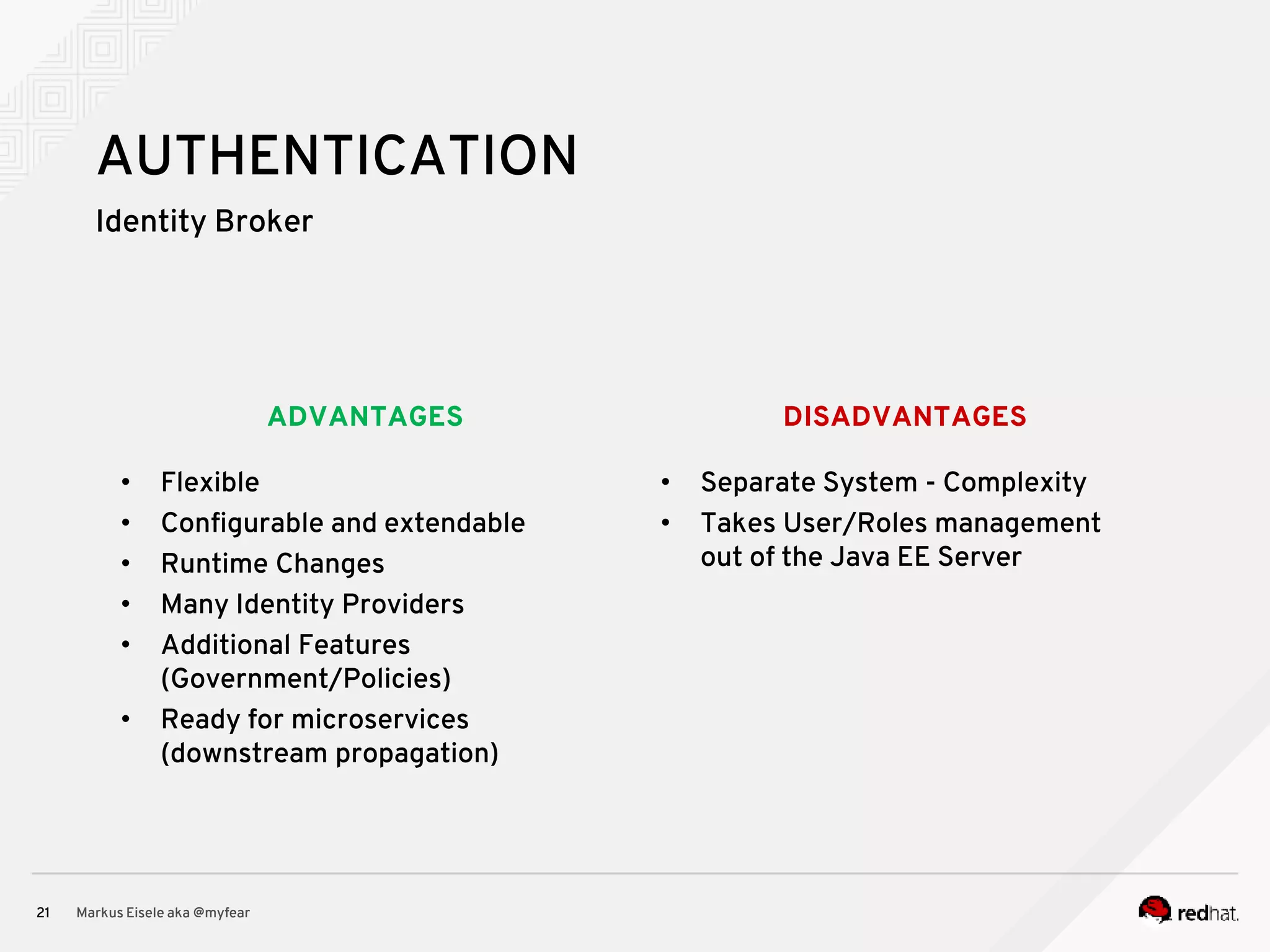
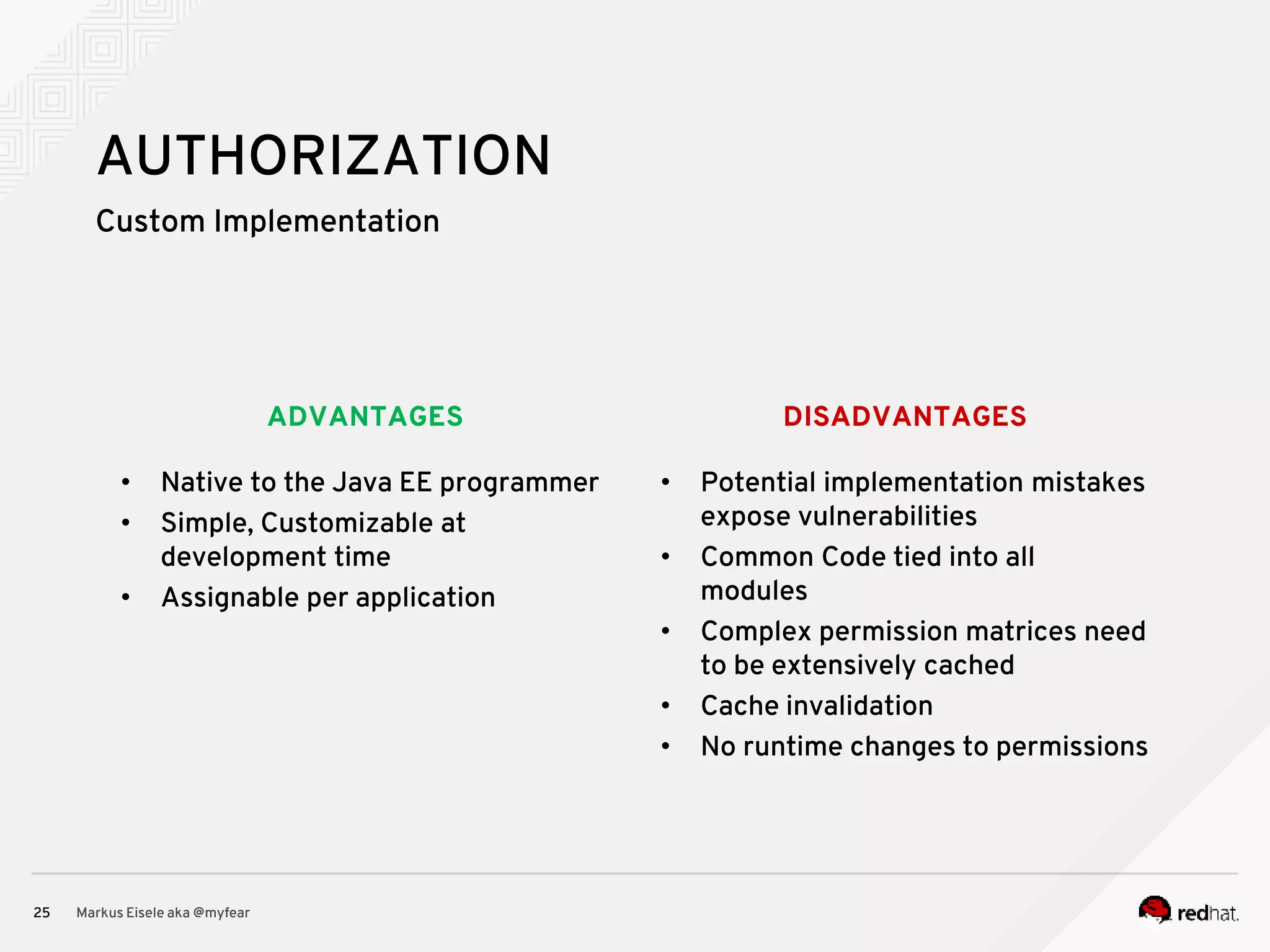
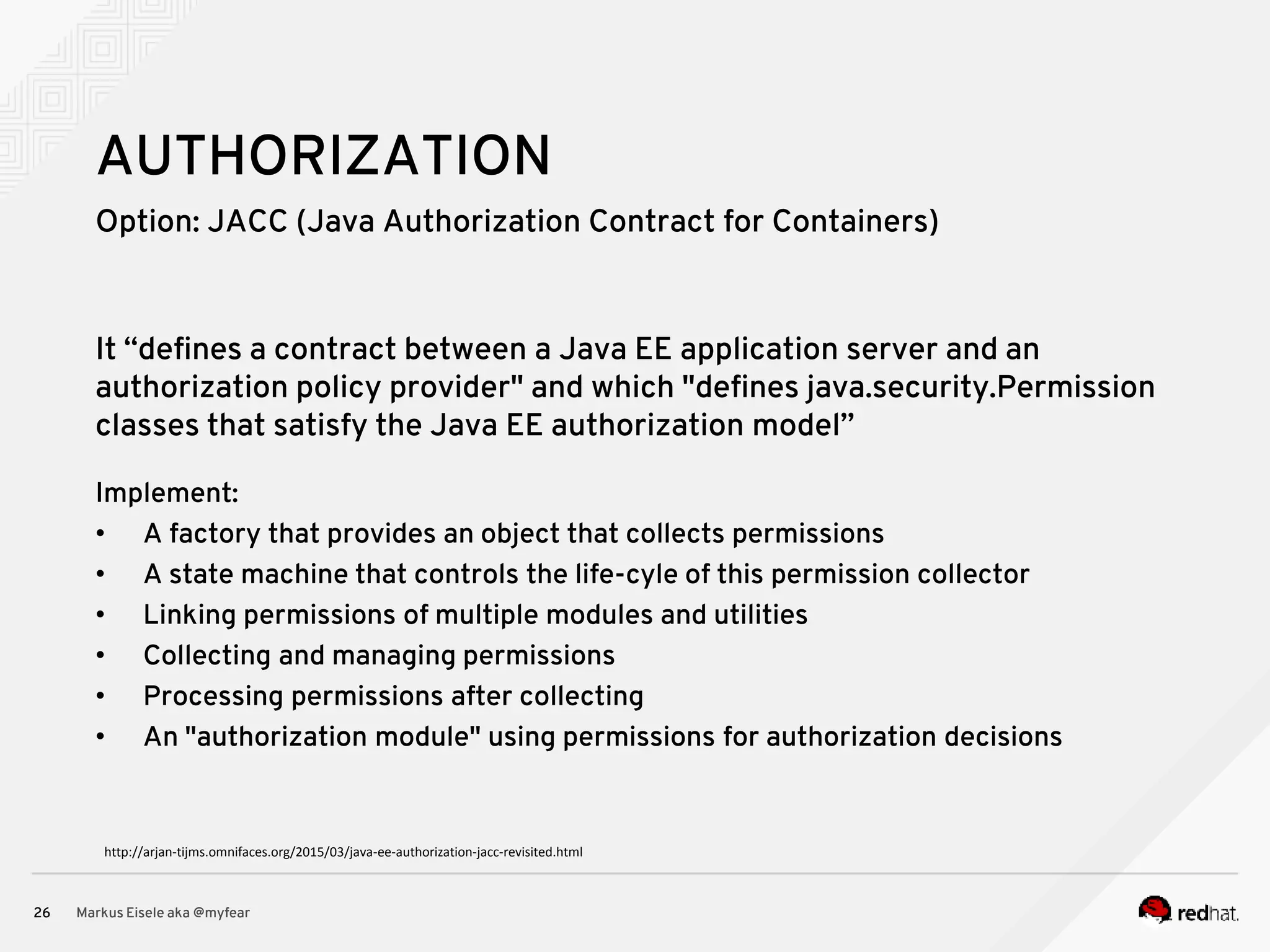
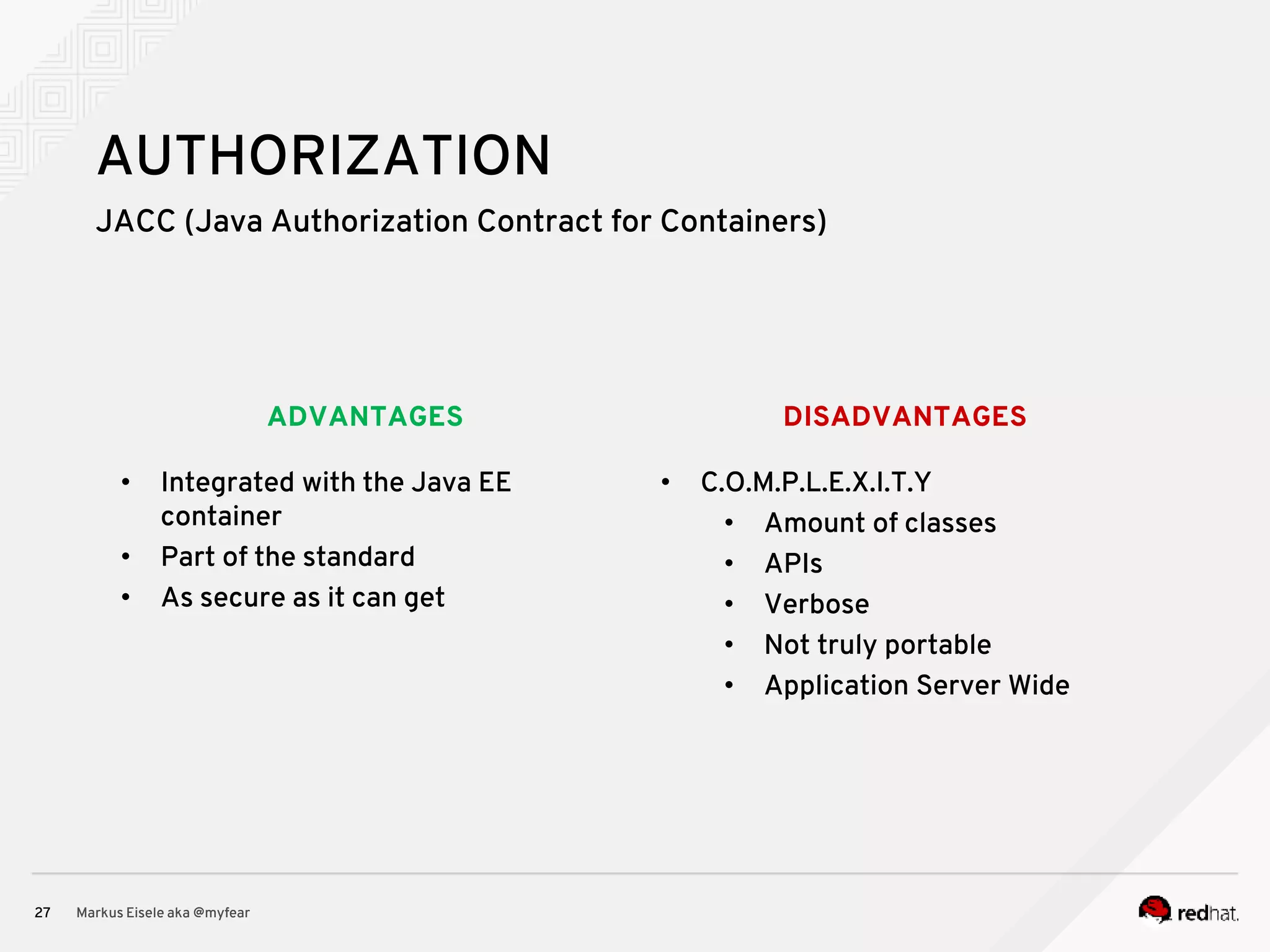
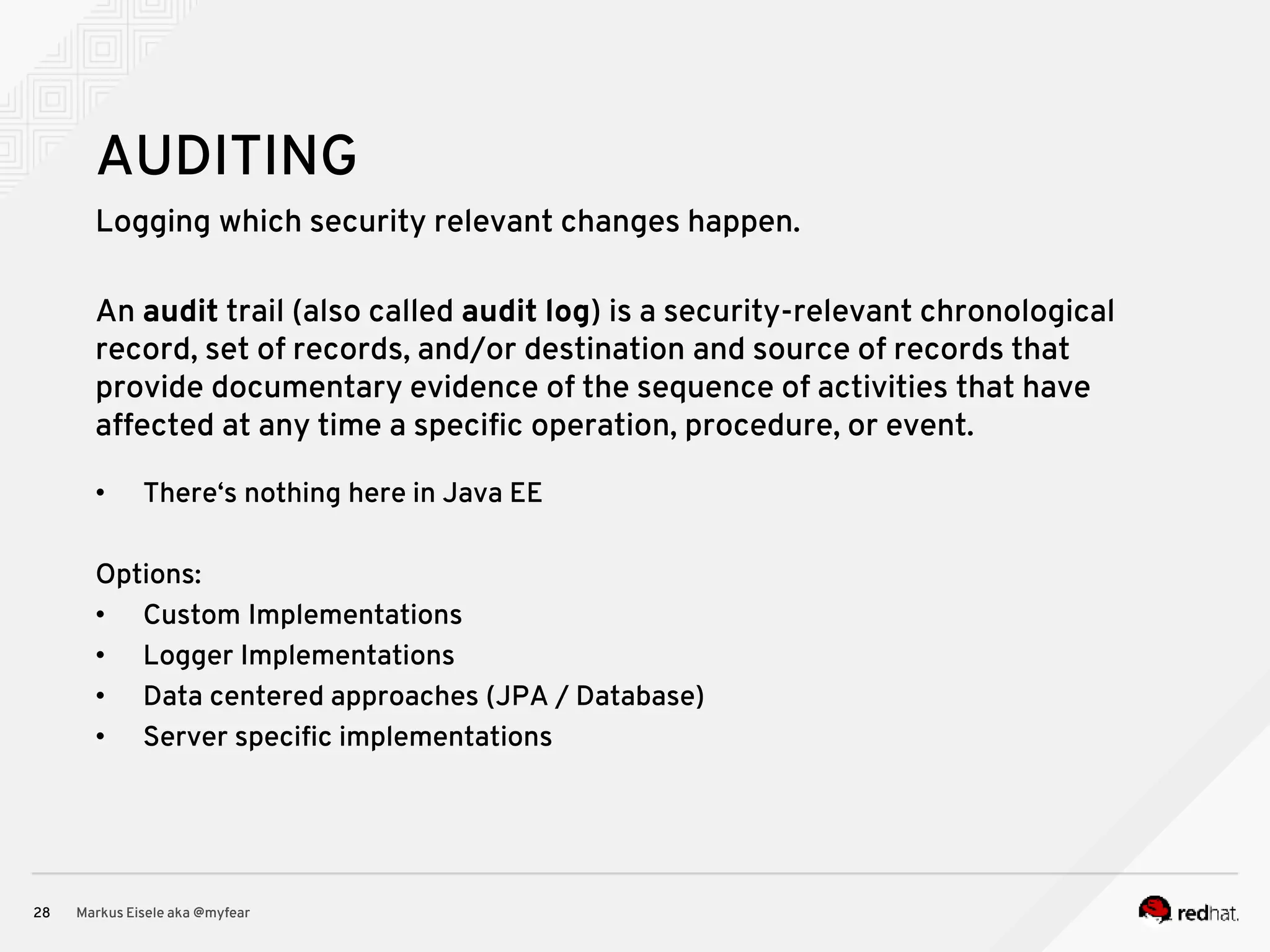
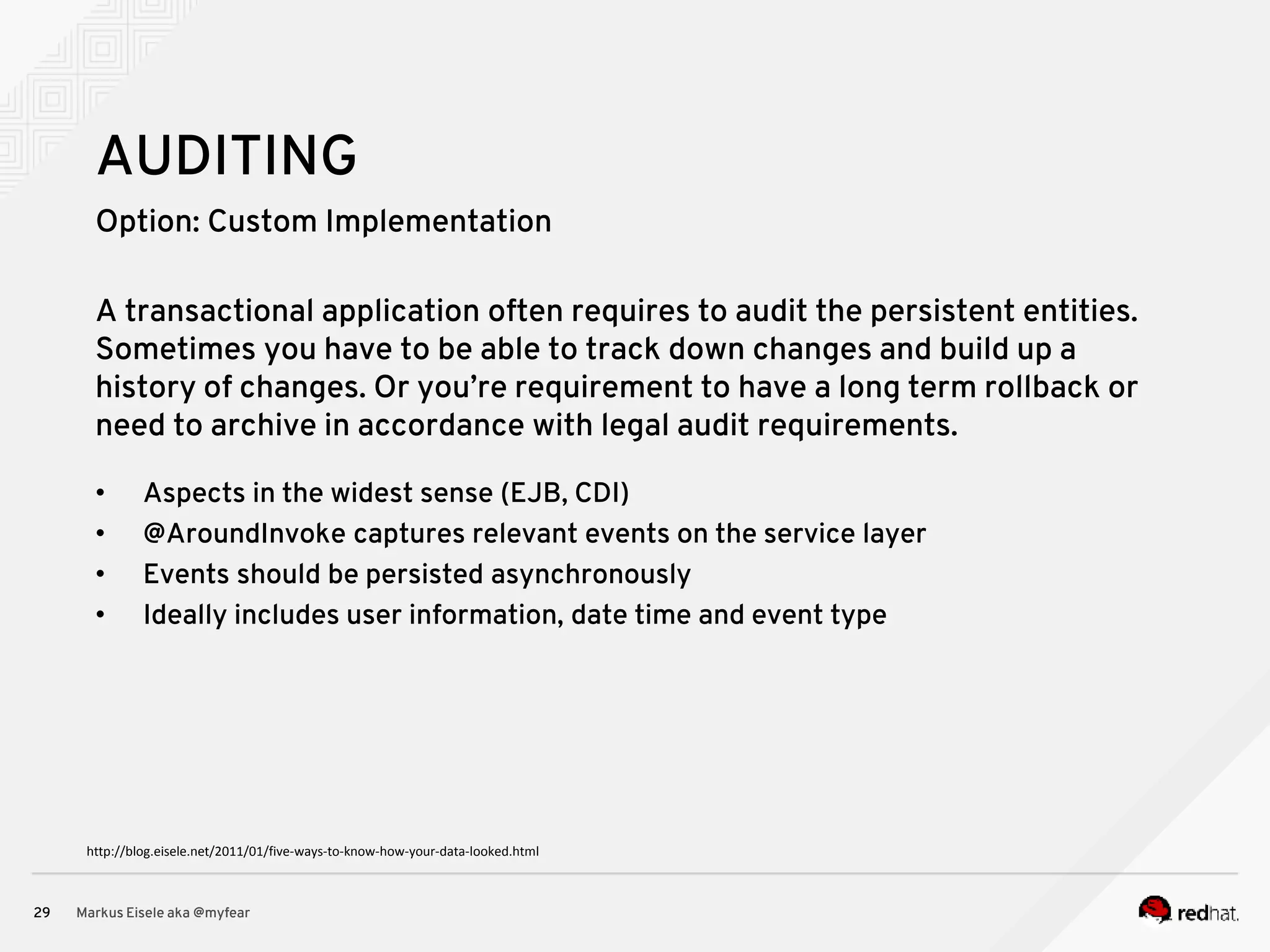
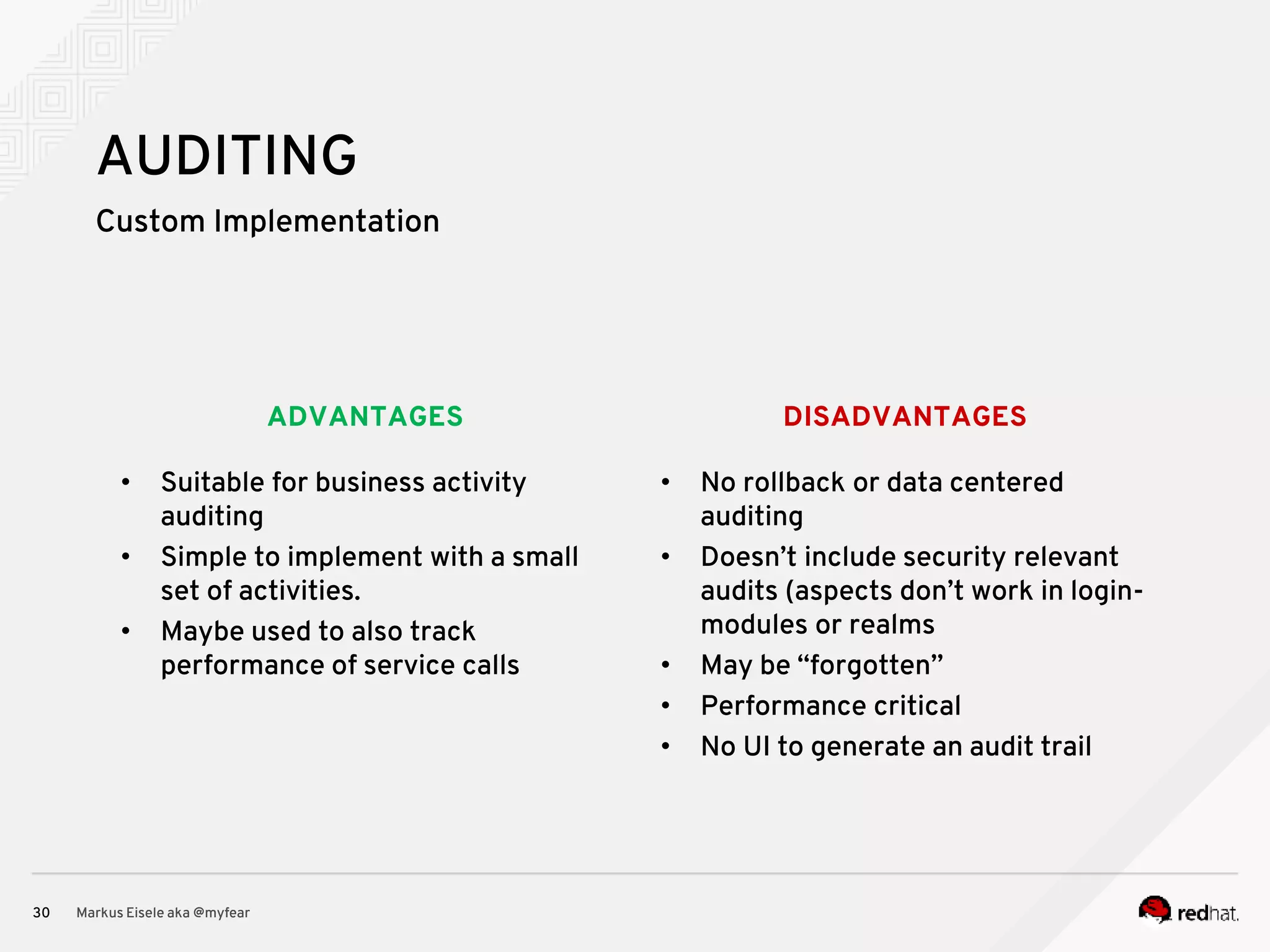
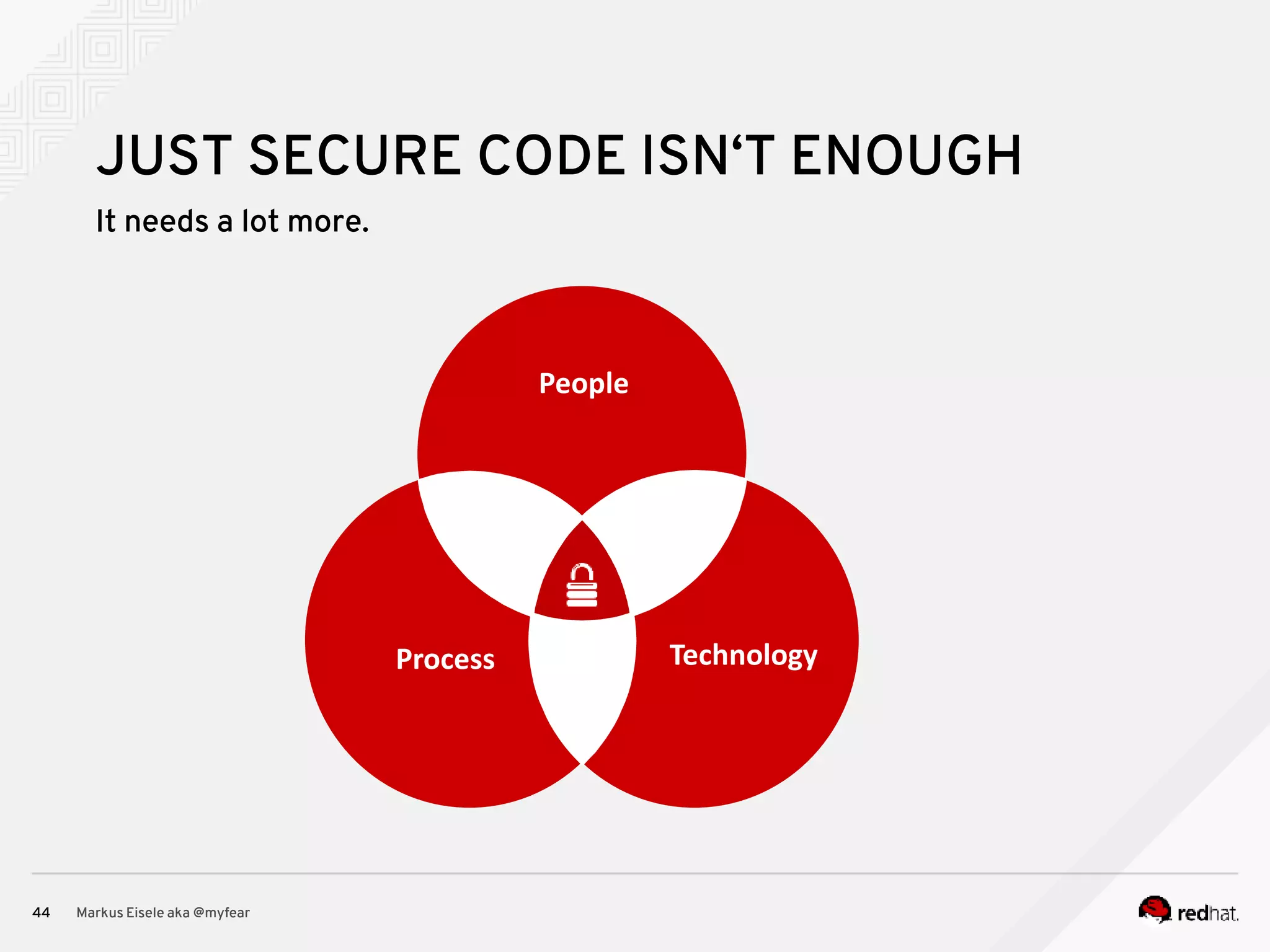
The document discusses the essential principles for securing Java EE applications, emphasizing a holistic approach to security across various layers such as network, operating system, and application services. Key topics include managing threats and vulnerabilities, effective authentication and authorization strategies, and ensuring data confidentiality, integrity, and availability. Best practices are highlighted, alongside the limitations of Java EE in supporting these security measures, with suggestions for custom implementations and external tools.