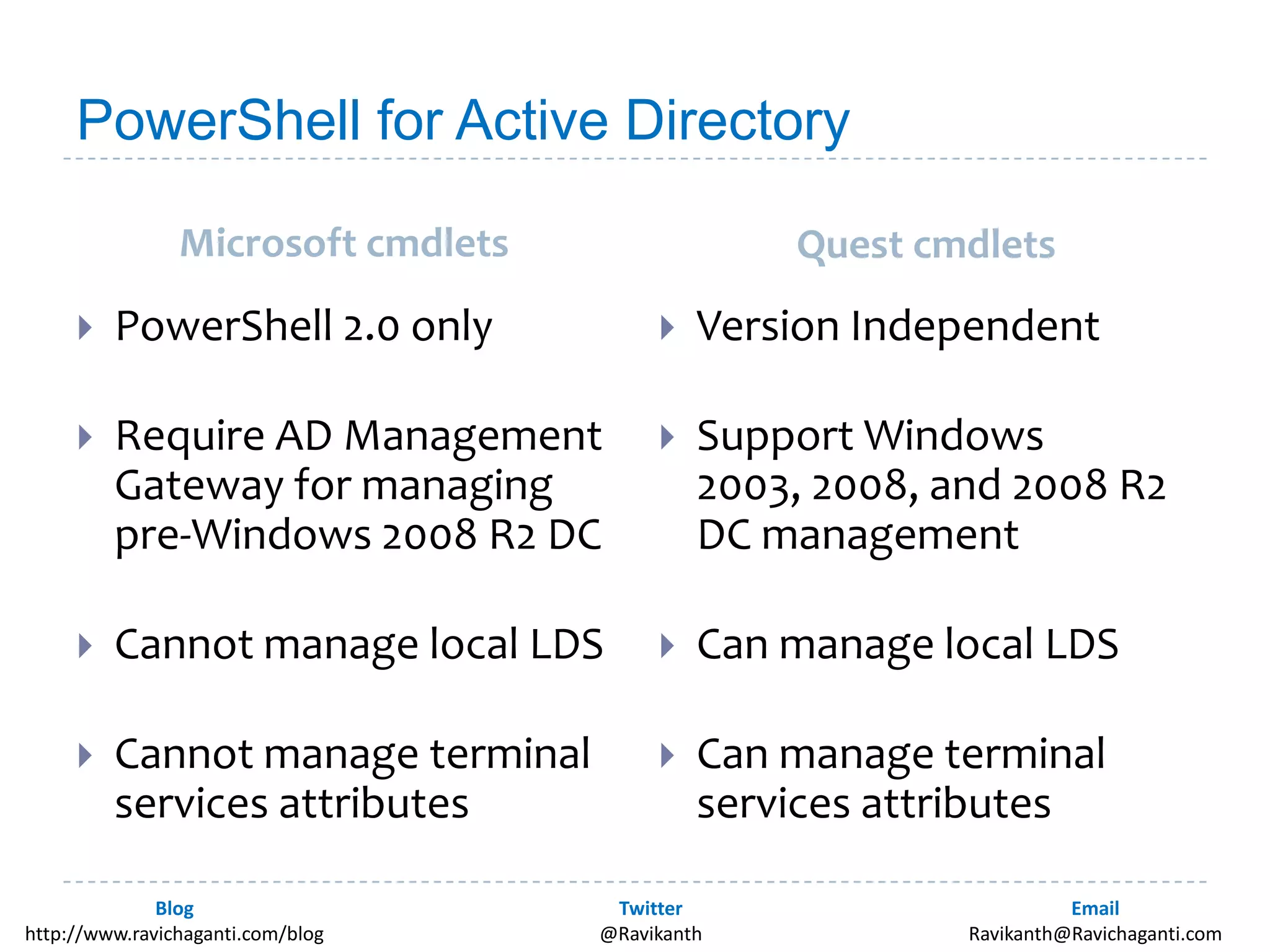
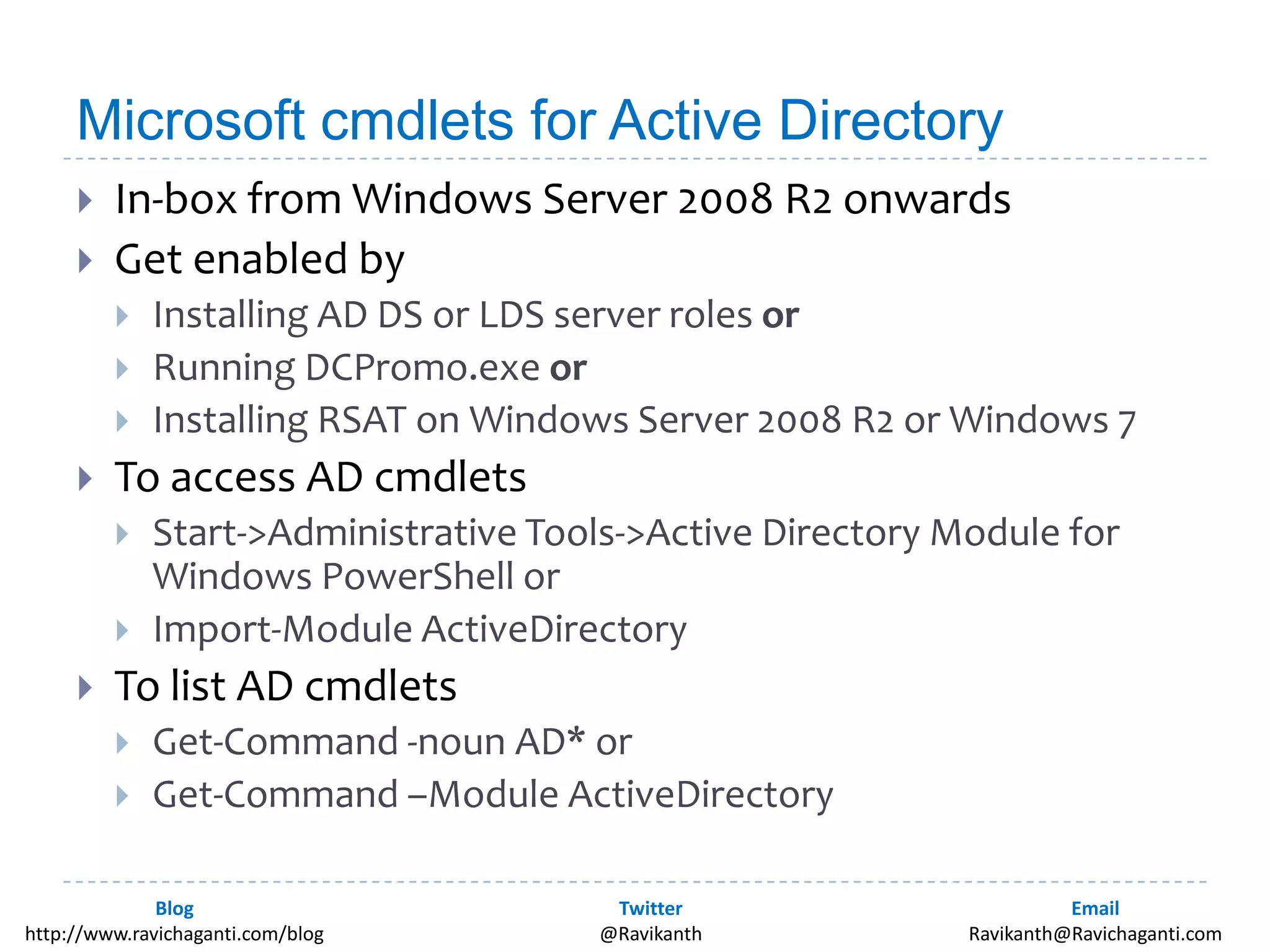
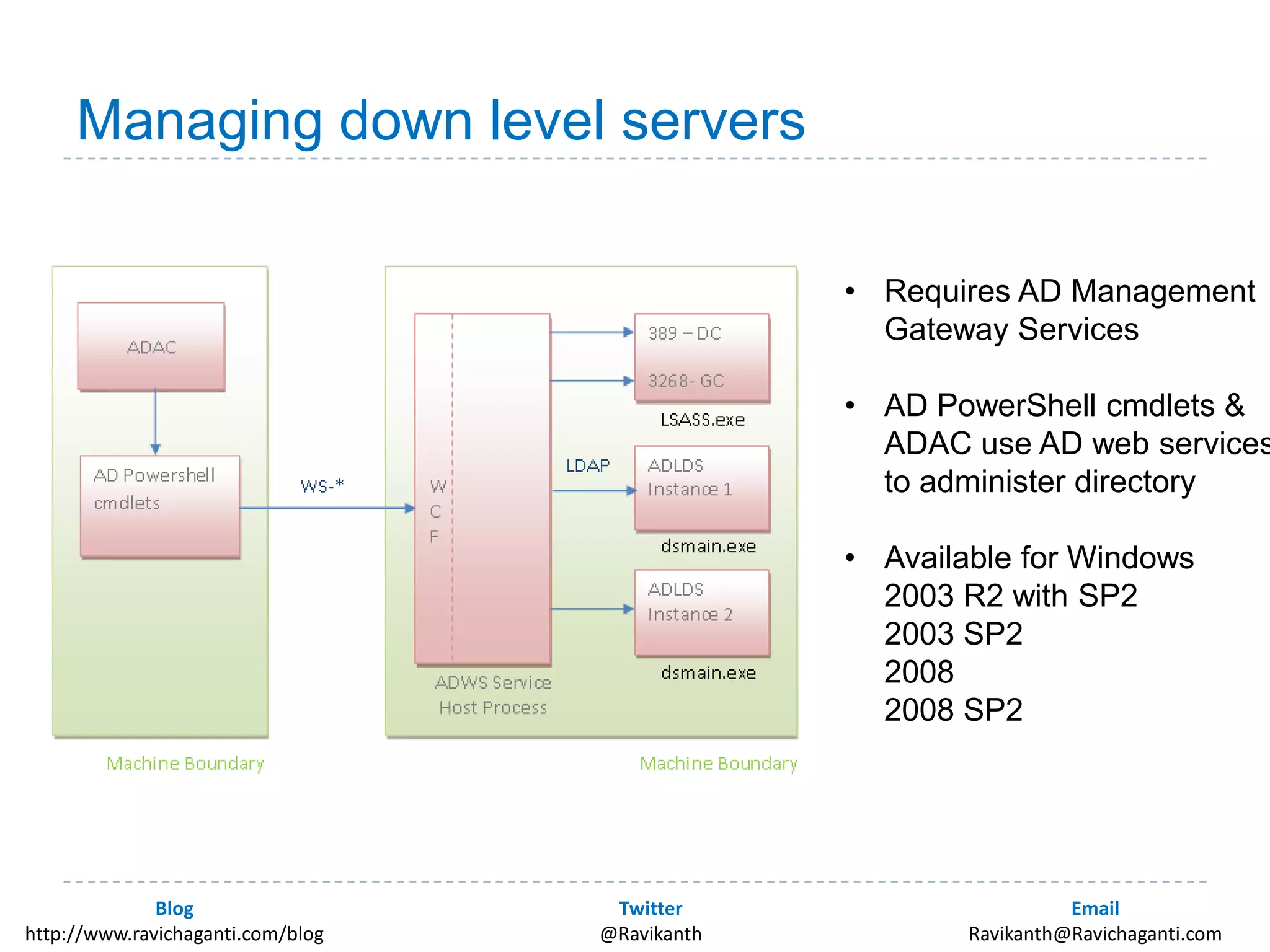
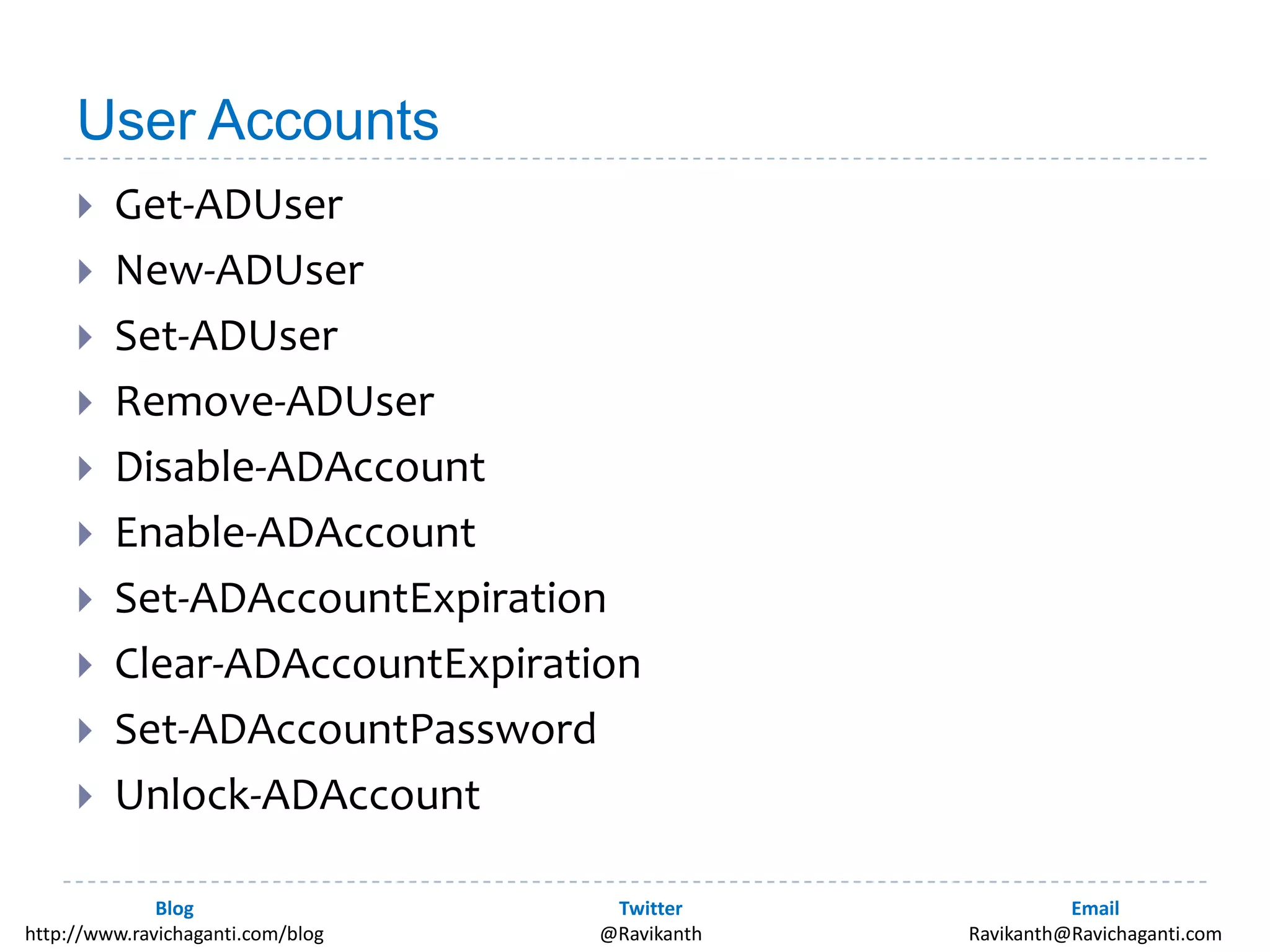
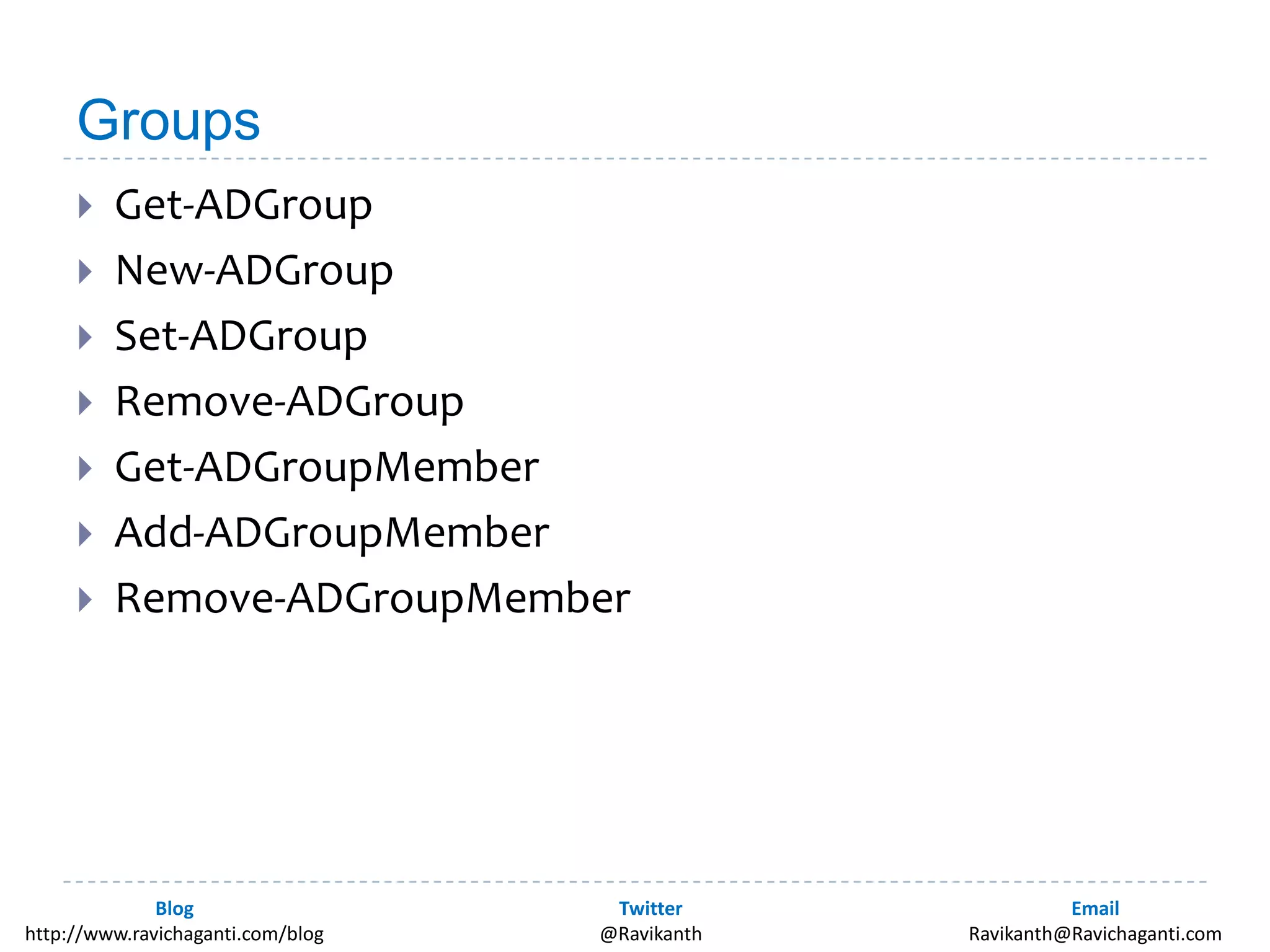
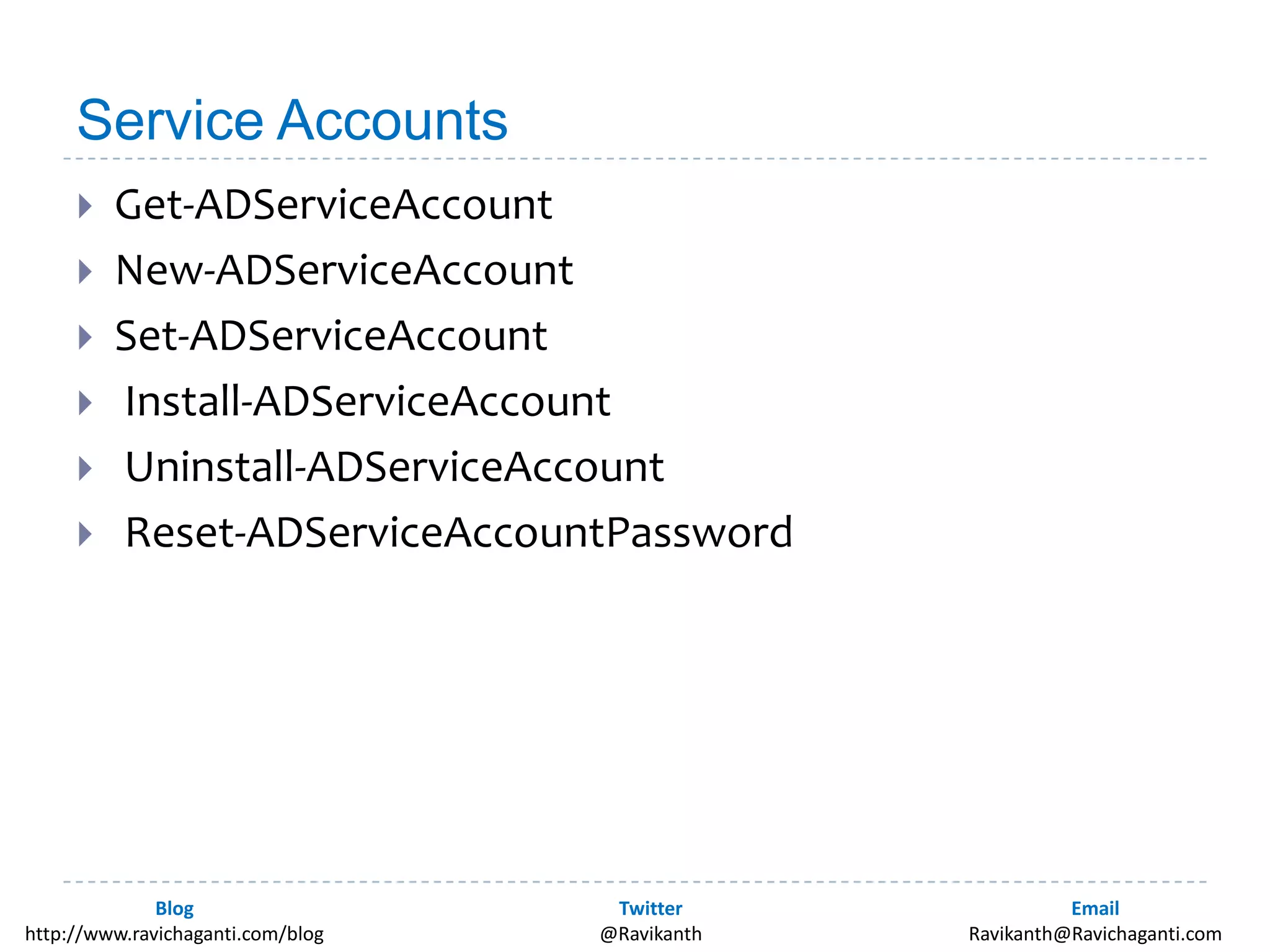
This document discusses using PowerShell to manage Active Directory. It introduces the author and his background in PowerShell. It then discusses the various options for using PowerShell with Active Directory, including the in-box Microsoft cmdlets and third party tools. It provides examples of common Active Directory management tasks that can be done with PowerShell like managing users, groups, passwords policies and more. It also provides learning resources for getting started with PowerShell and Active Directory management.


![PowerShell for Active Directory[ADSI] adapterIn-boxWindows Server 2008 R2 includes a PowerShell moduleIn-boxQuest Software ActiveRoles Management ShellFree downloadSofterra Adaxes 2010.2Commercial productIdera Scripts for Active DirectoryFree; uses [ADSI]](https://image.slidesharecdn.com/usingpowershellforactivedirectorymanagement-101218033215-phpapp01/75/Using-PowerShell-for-active-directory-management-4-2048.jpg)