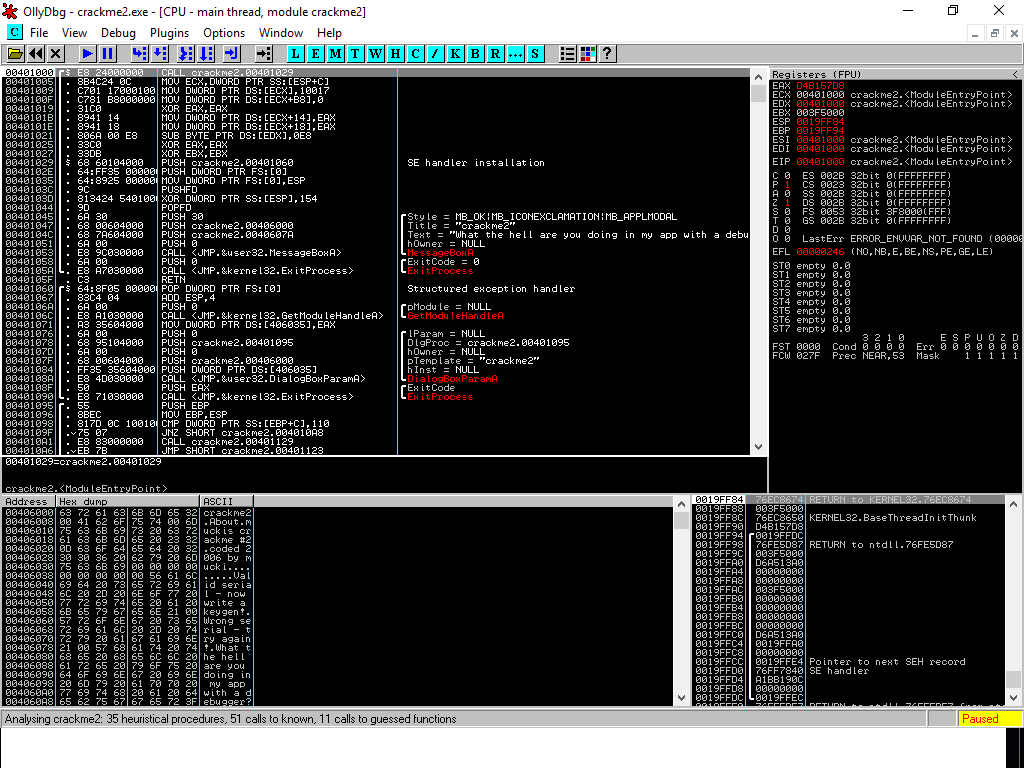
I am trying to reverse a program which is employing some kind of anti-debugging trick based on the use of SEHs and the TF. The code stars with:
So apparently it's generating an exception with
XOR DWORD PTR [ESP], 154h Which ultimately terminates with a call to ExitProcess() without even running the program.
I tried using NOPs to bypass this but since upon execution the EP is already pointing to this problematic piece of code it did not work.
How can I bypass this and what's really triggering the exception?