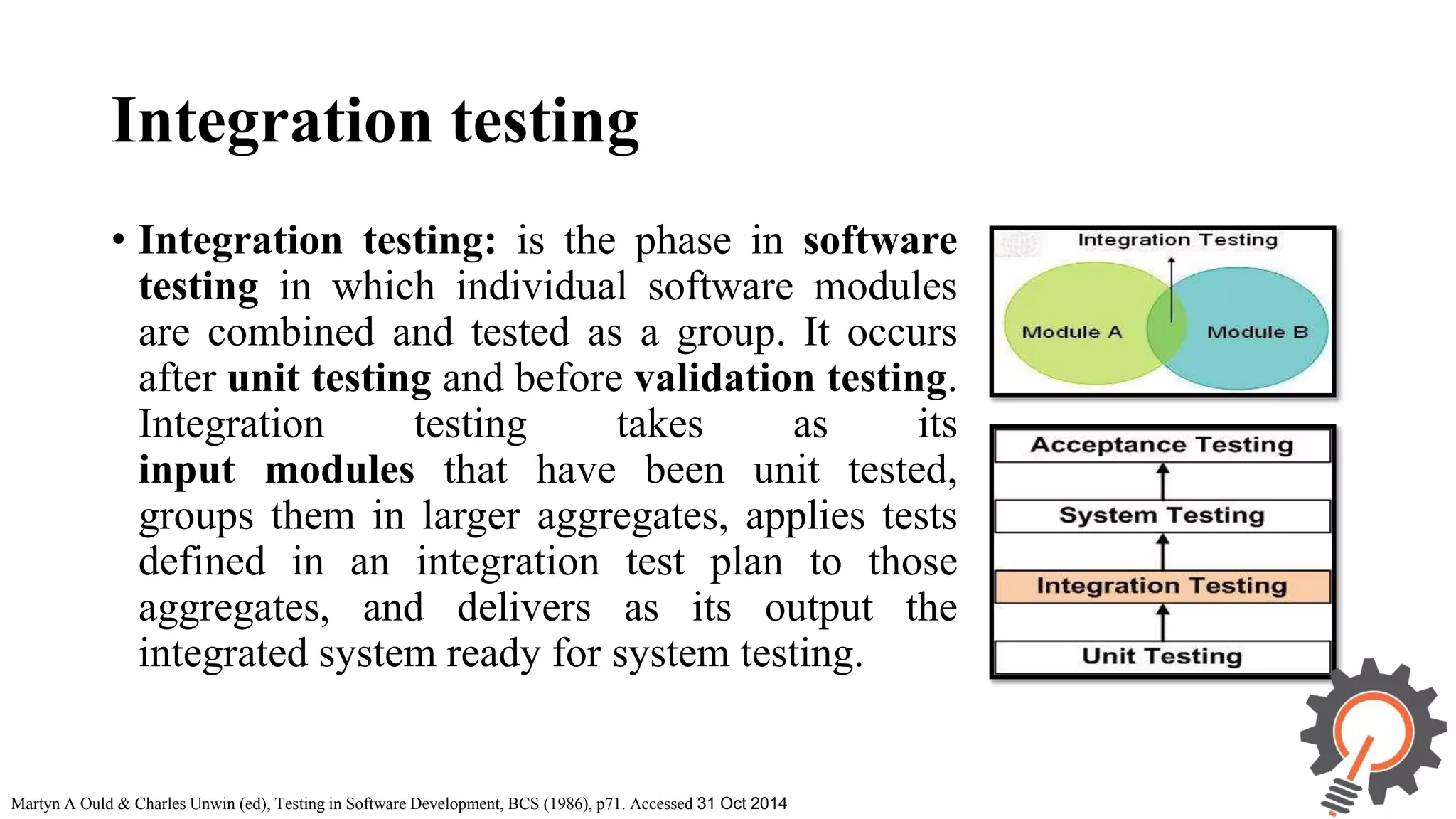
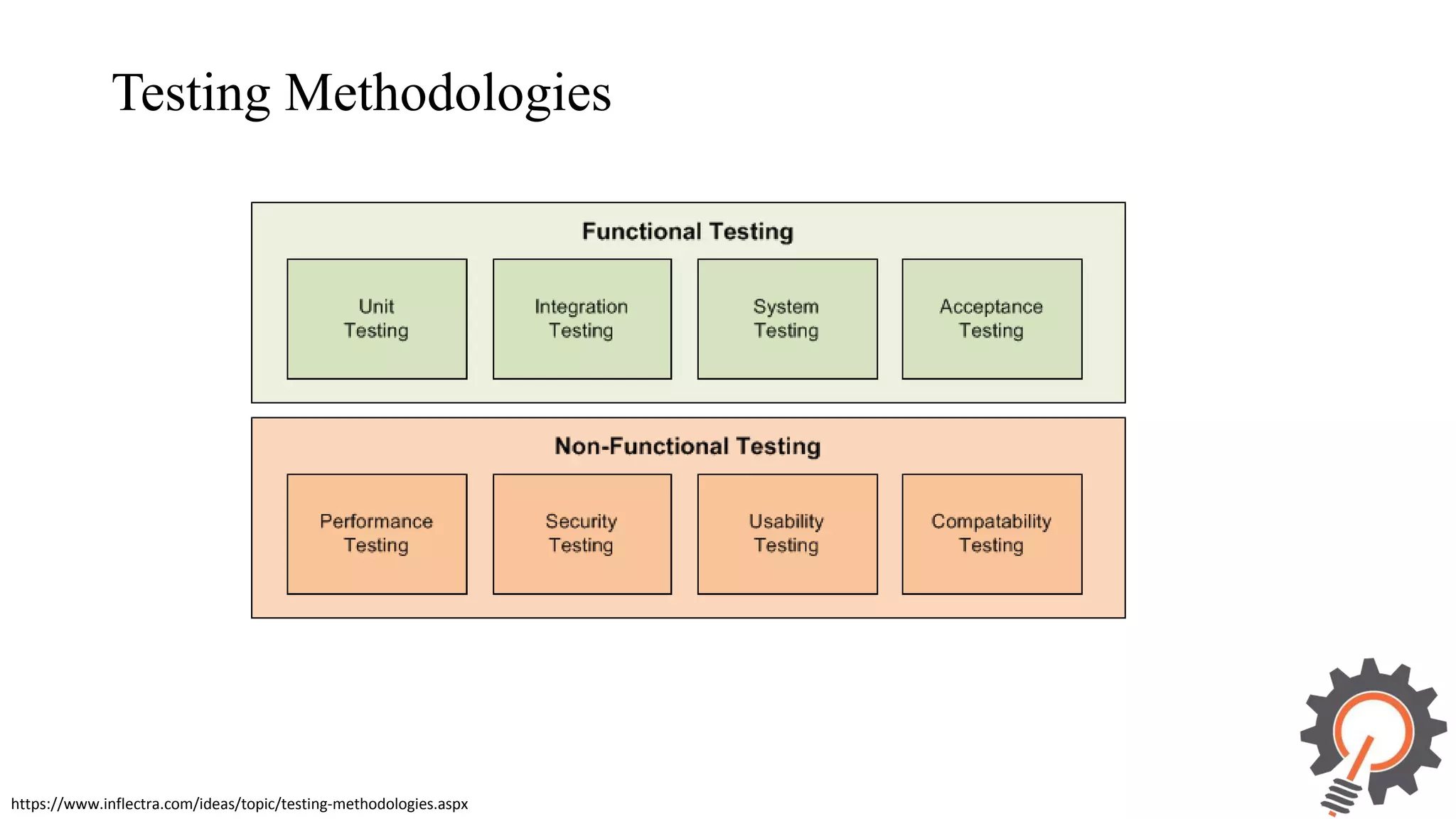
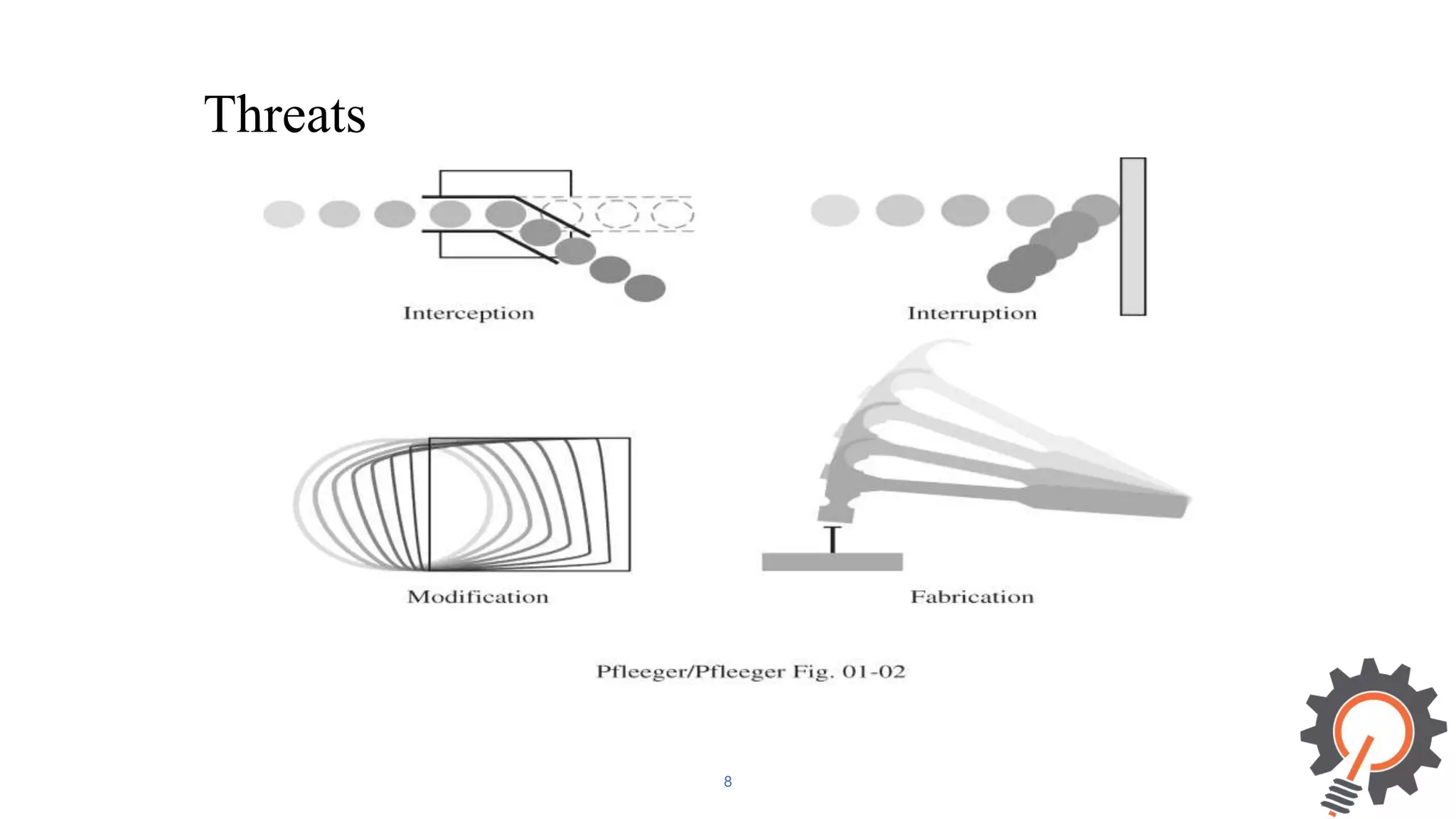
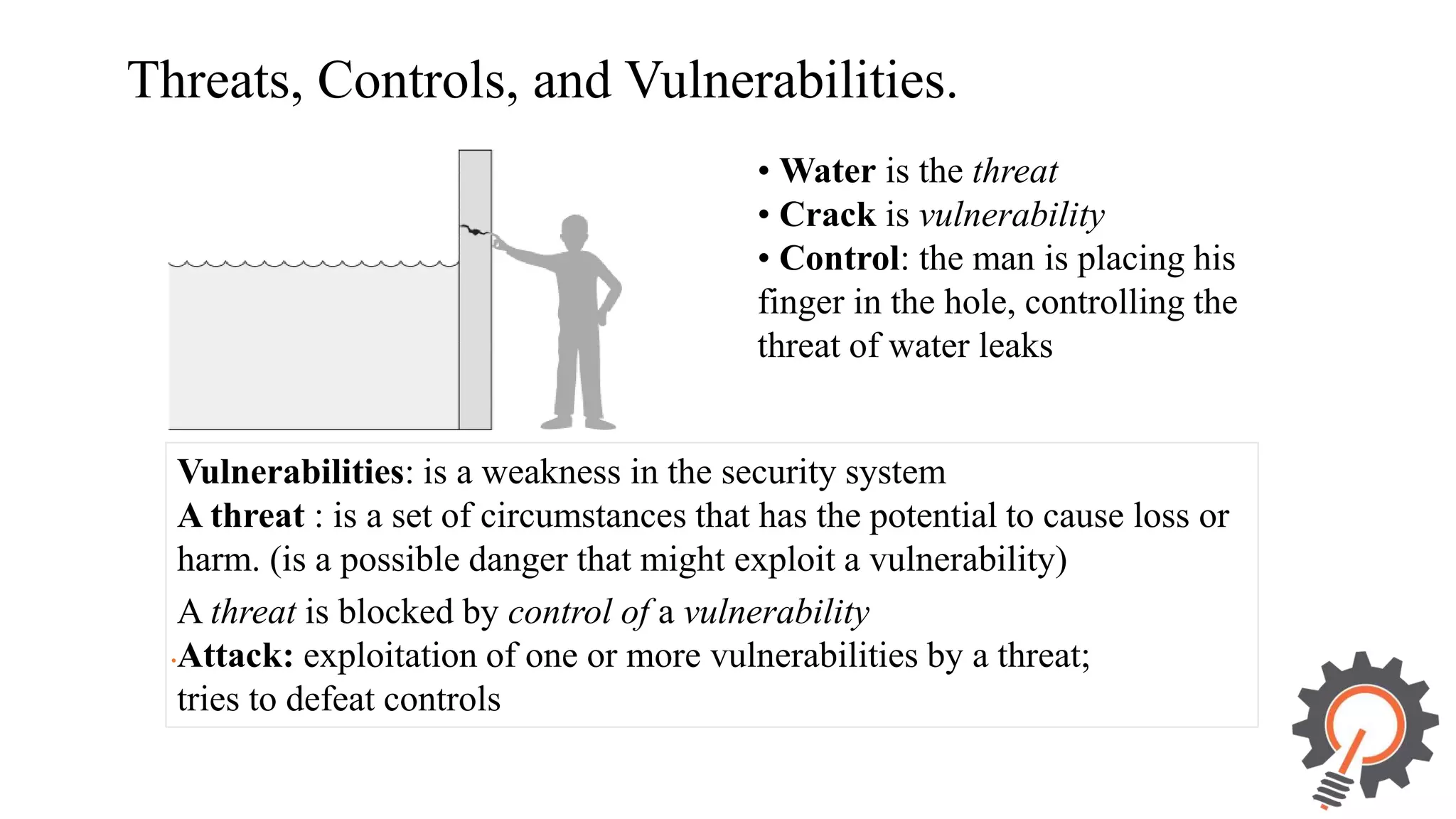
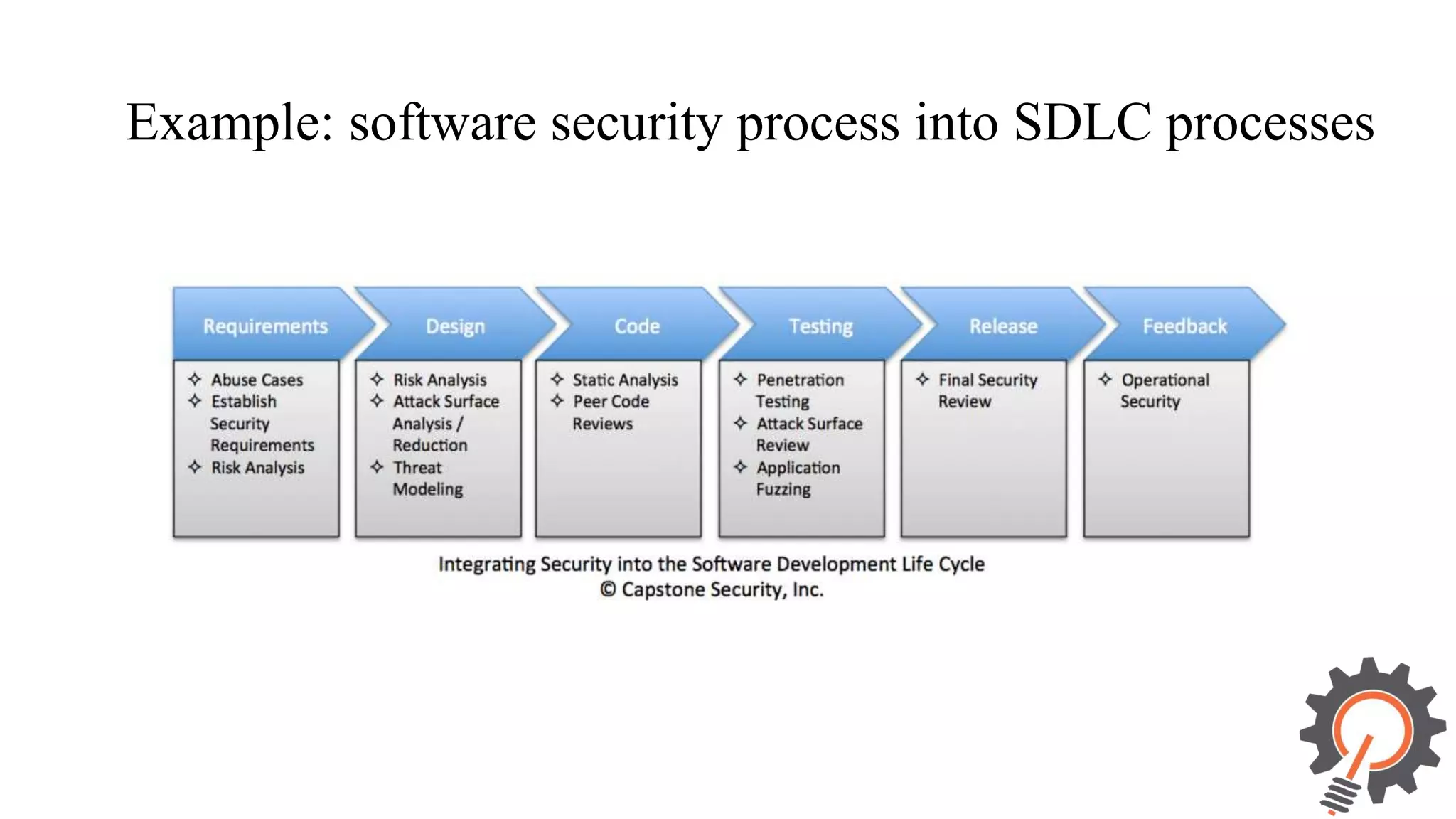
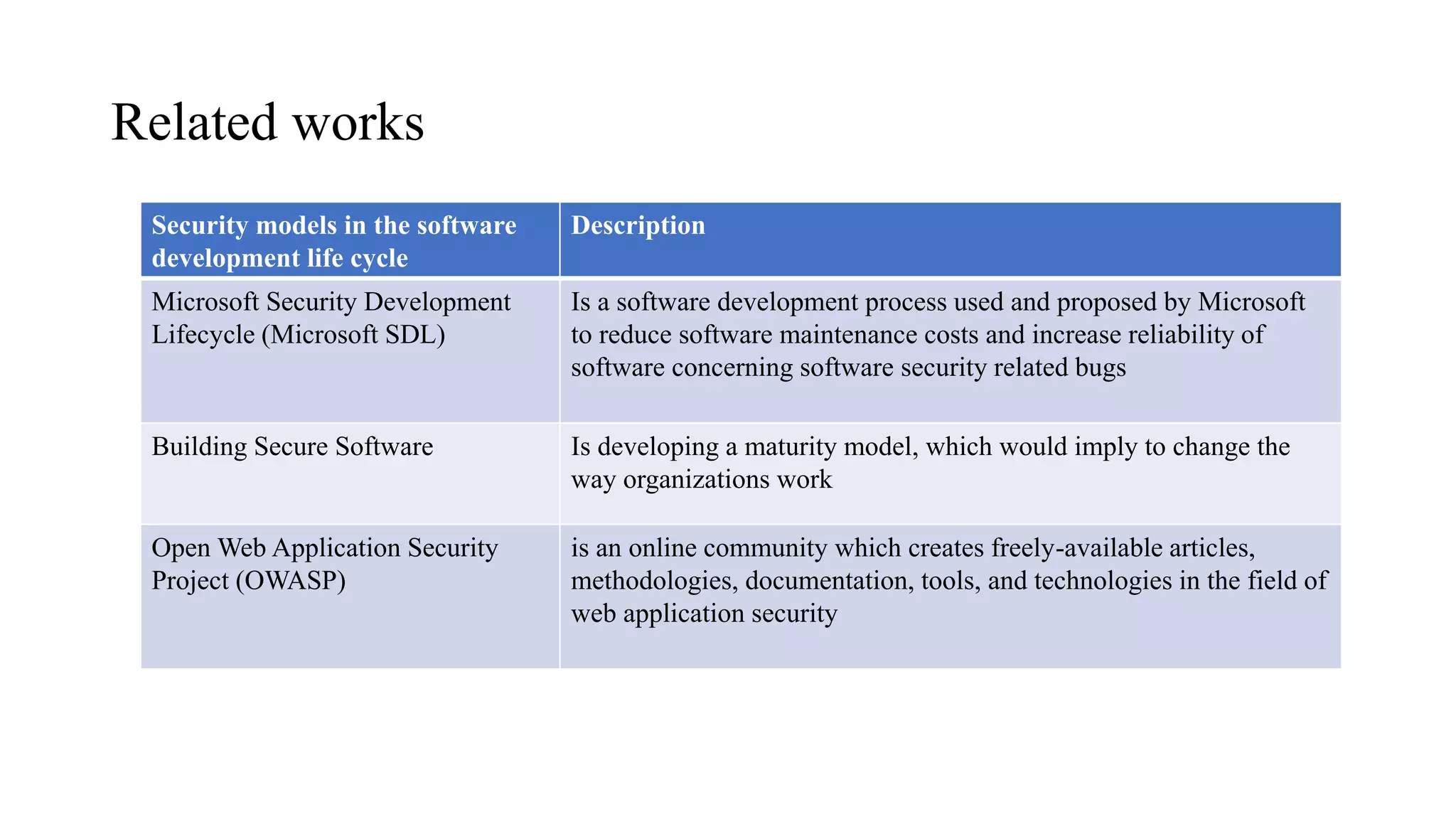
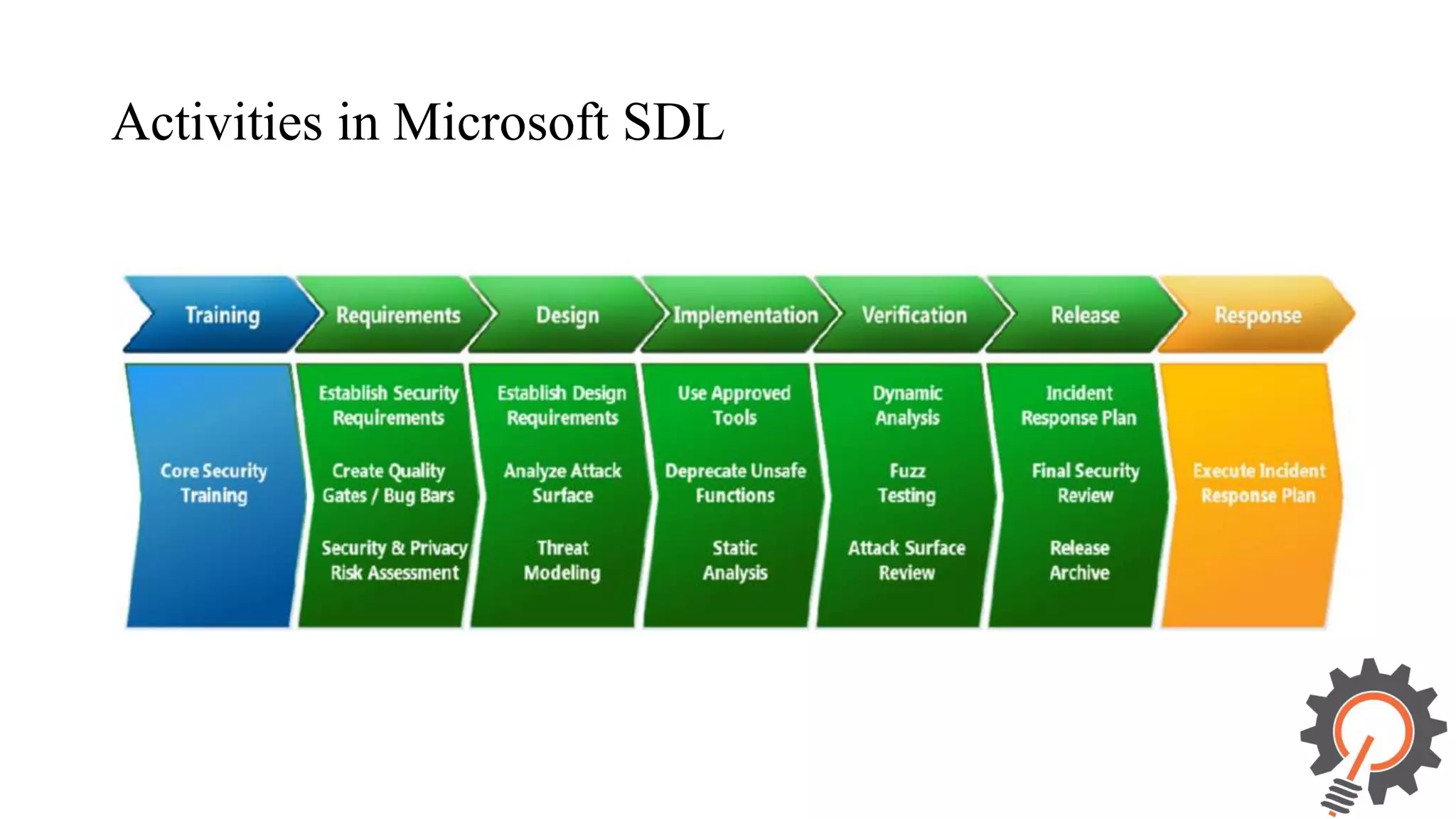
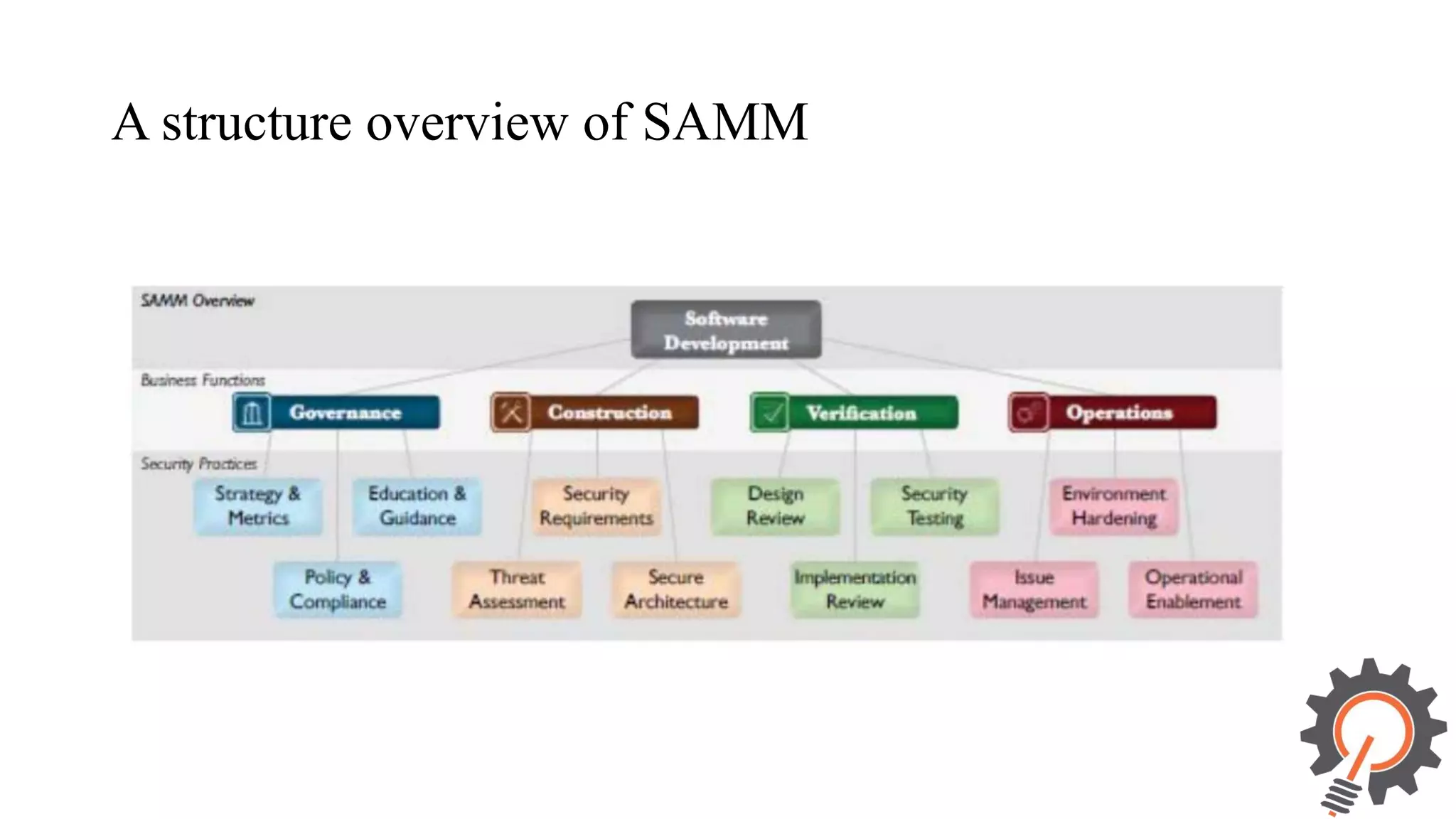
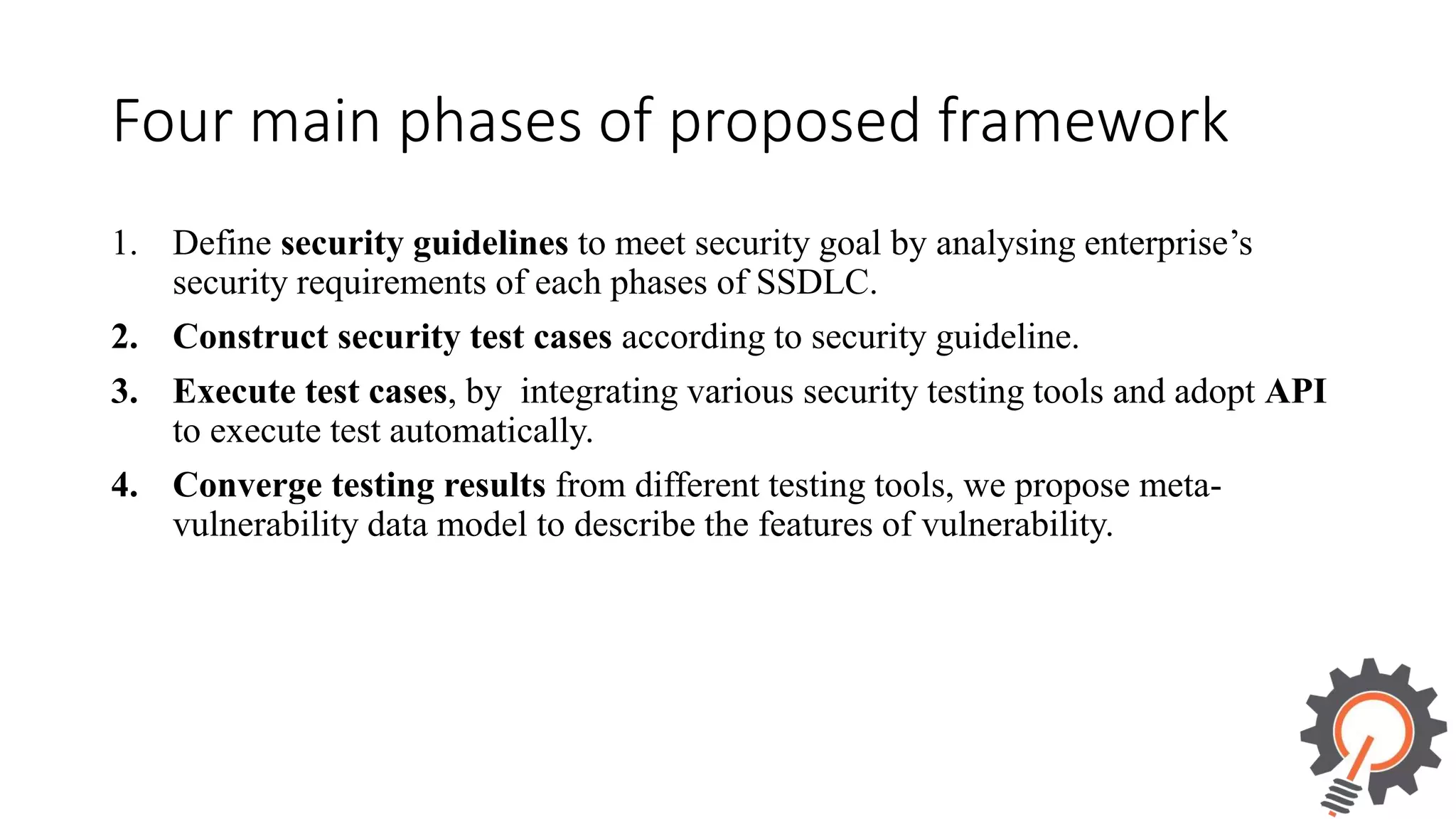
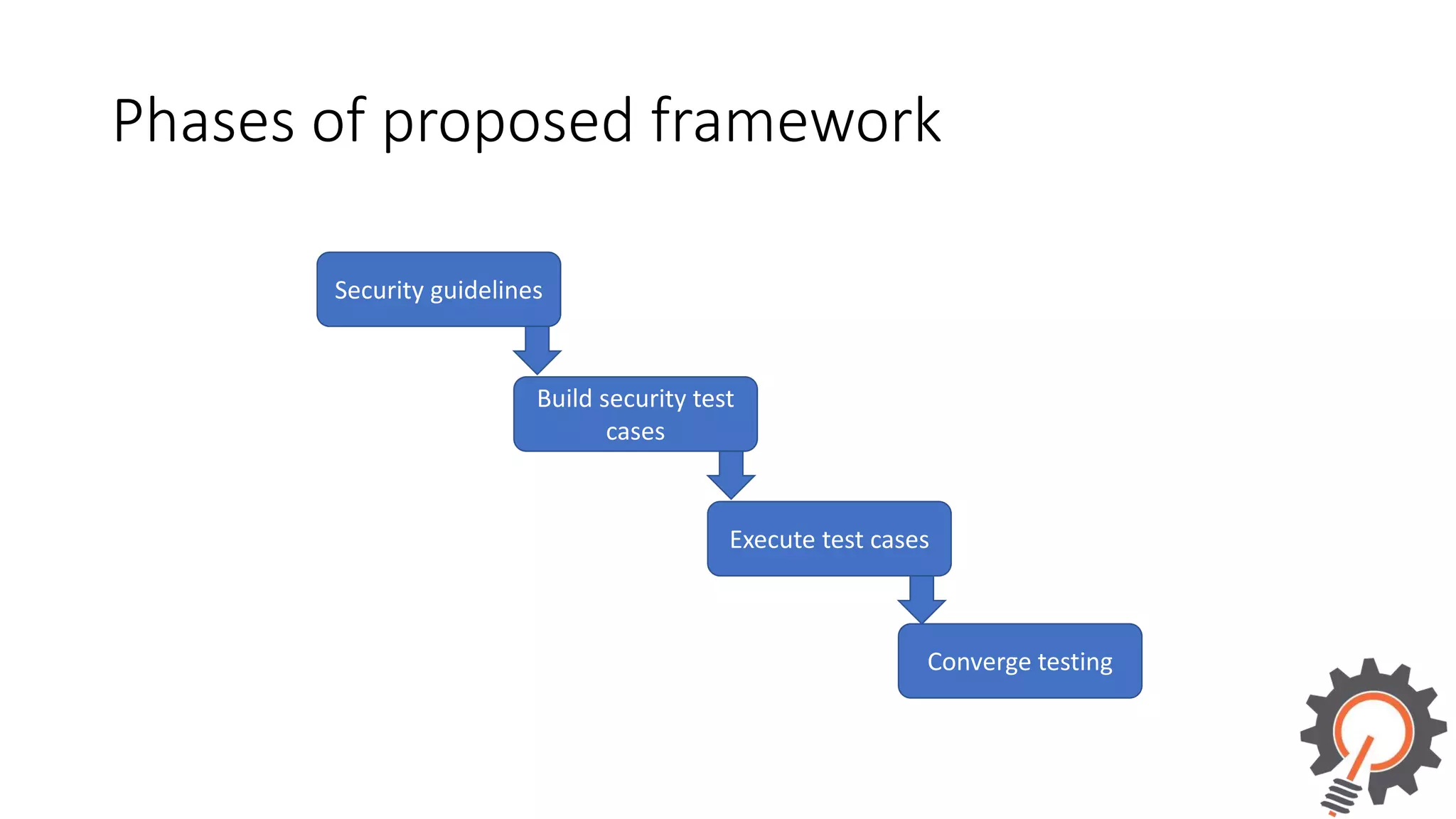
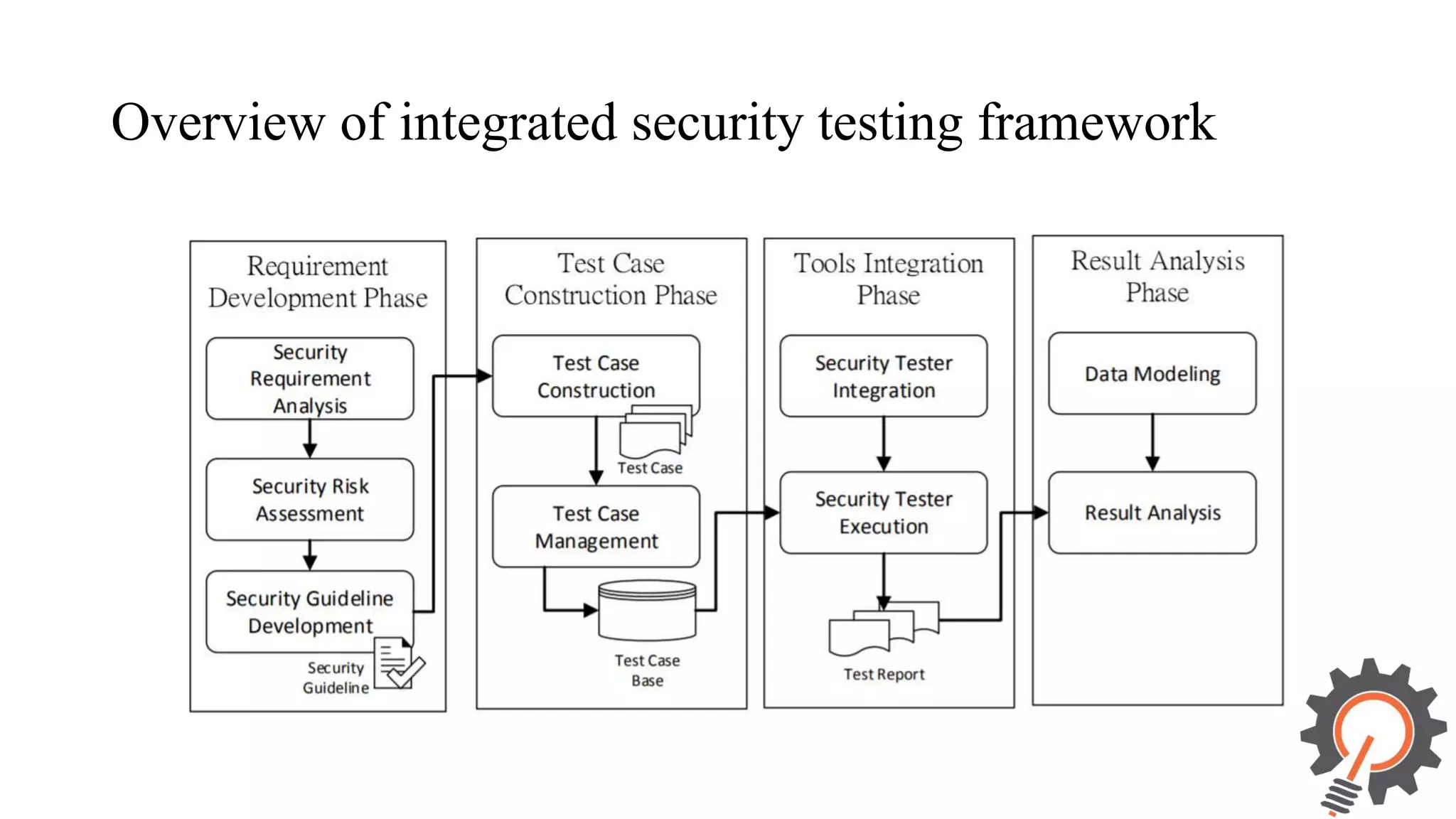
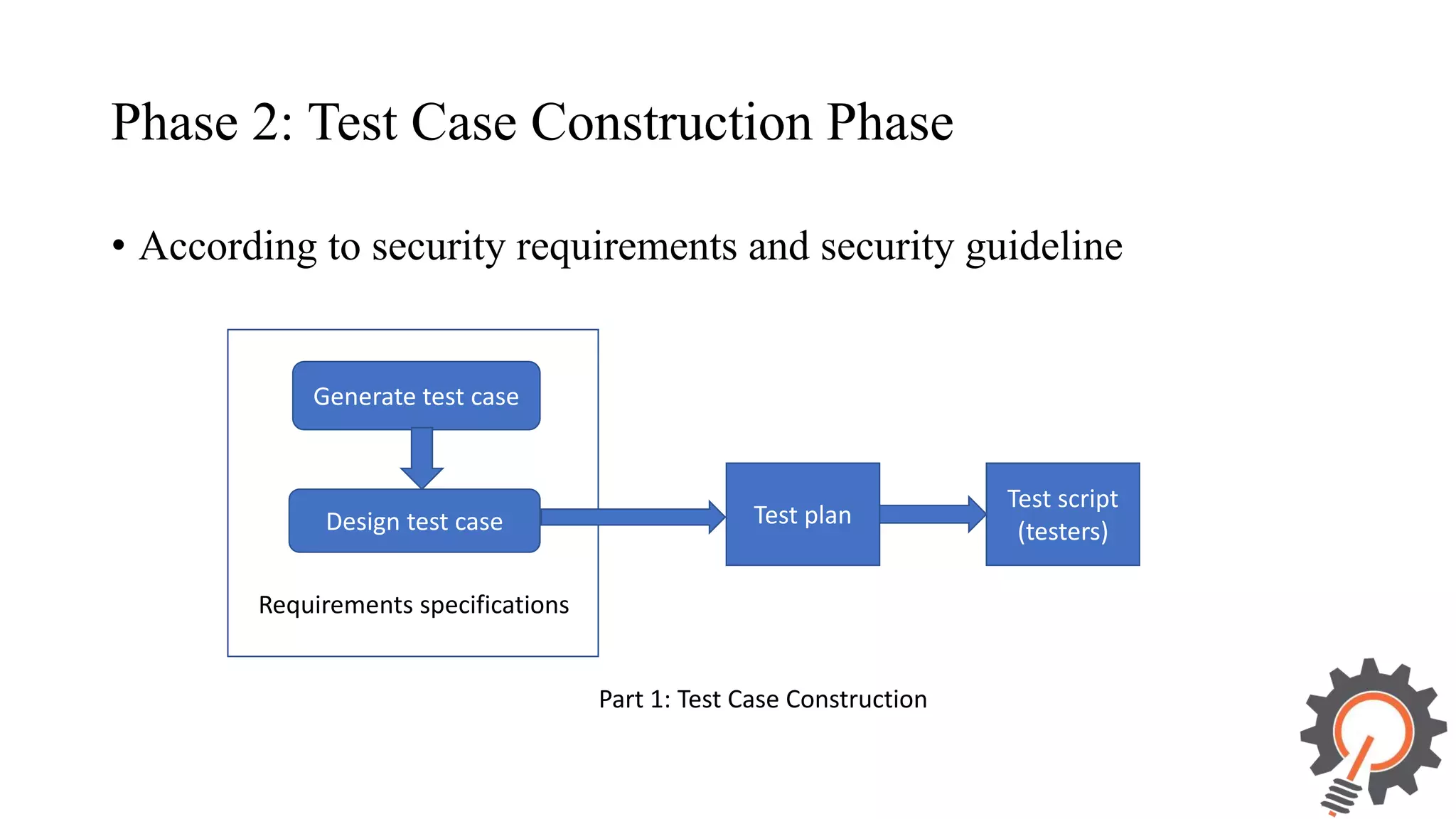
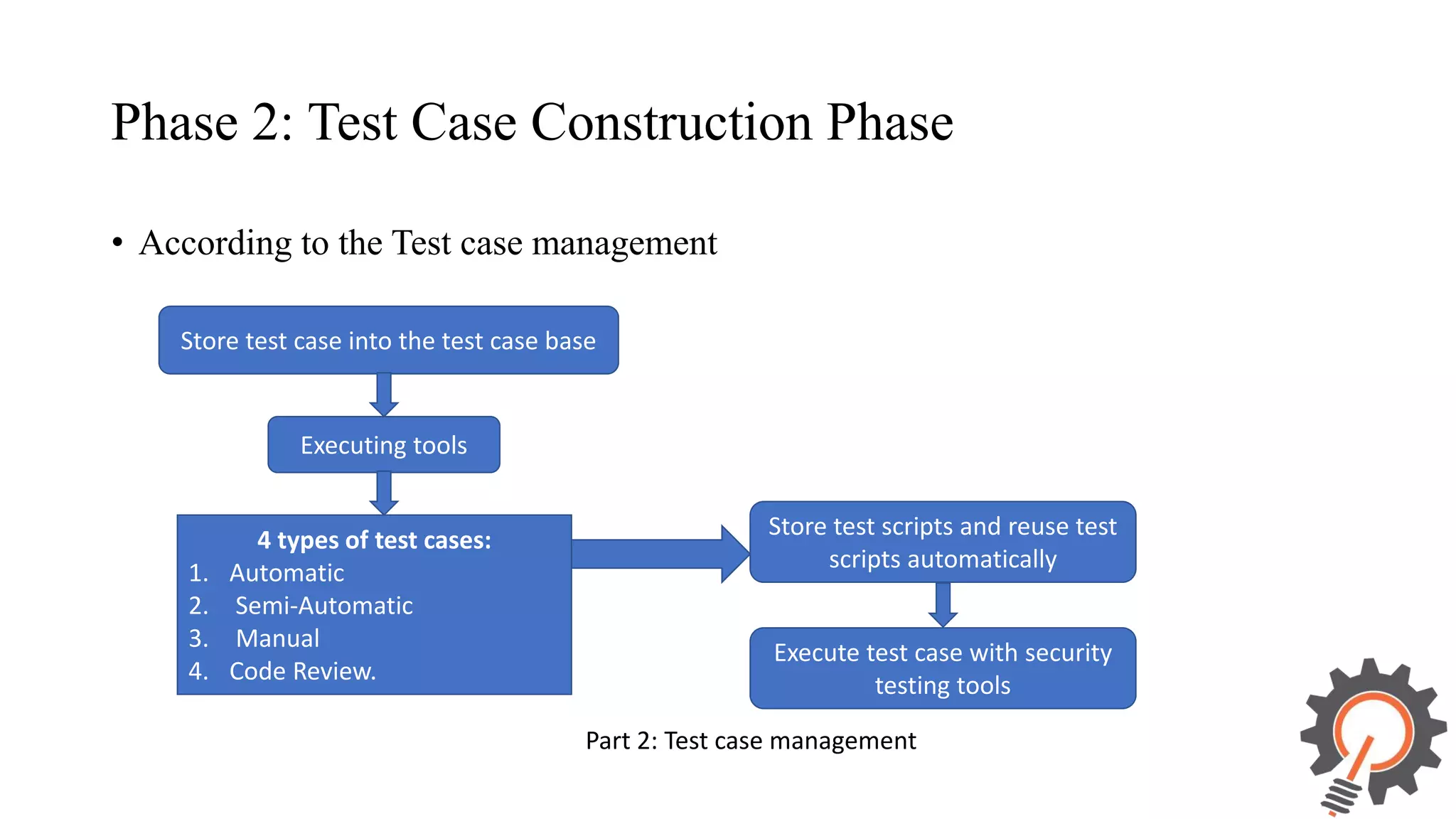
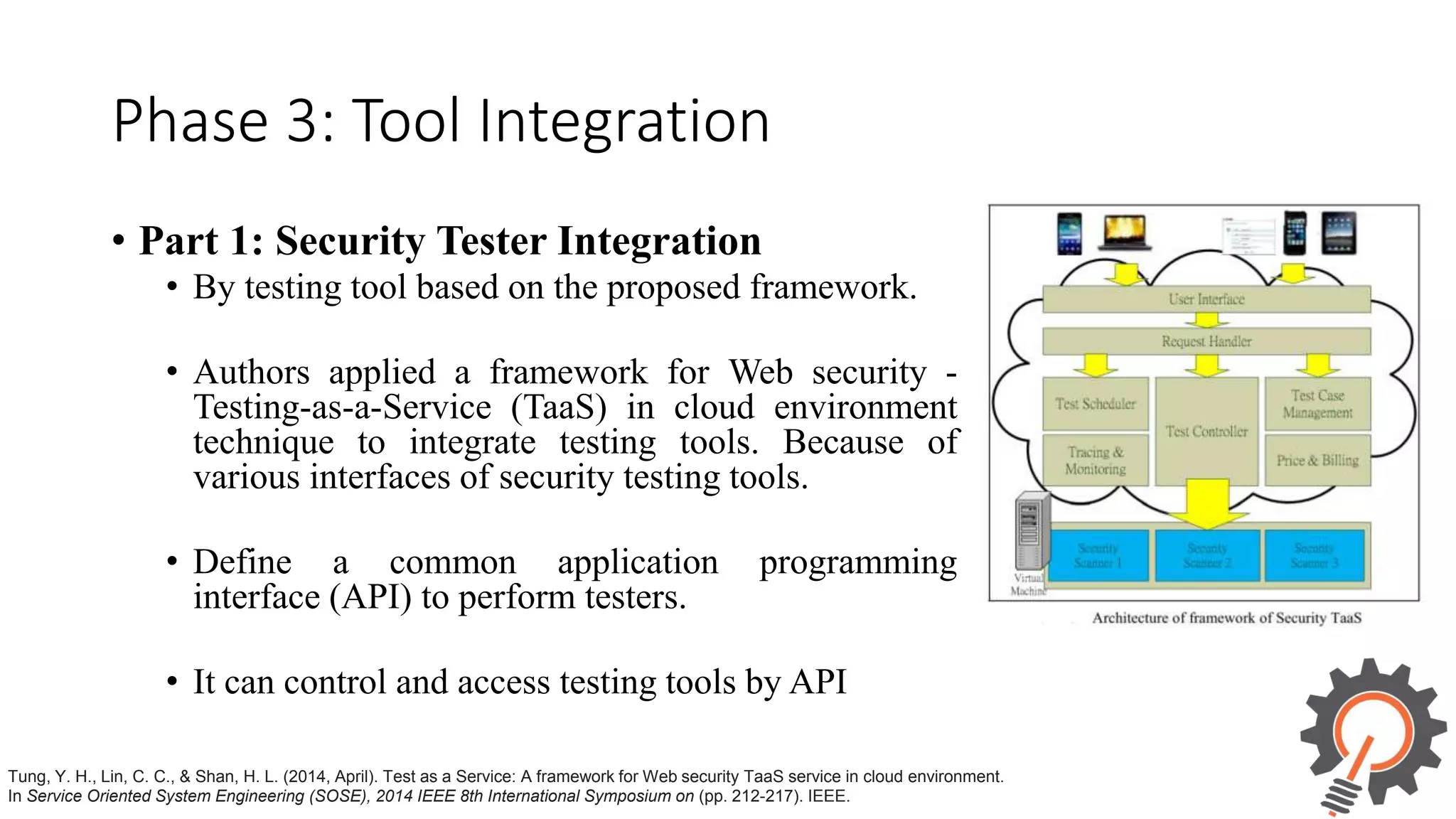
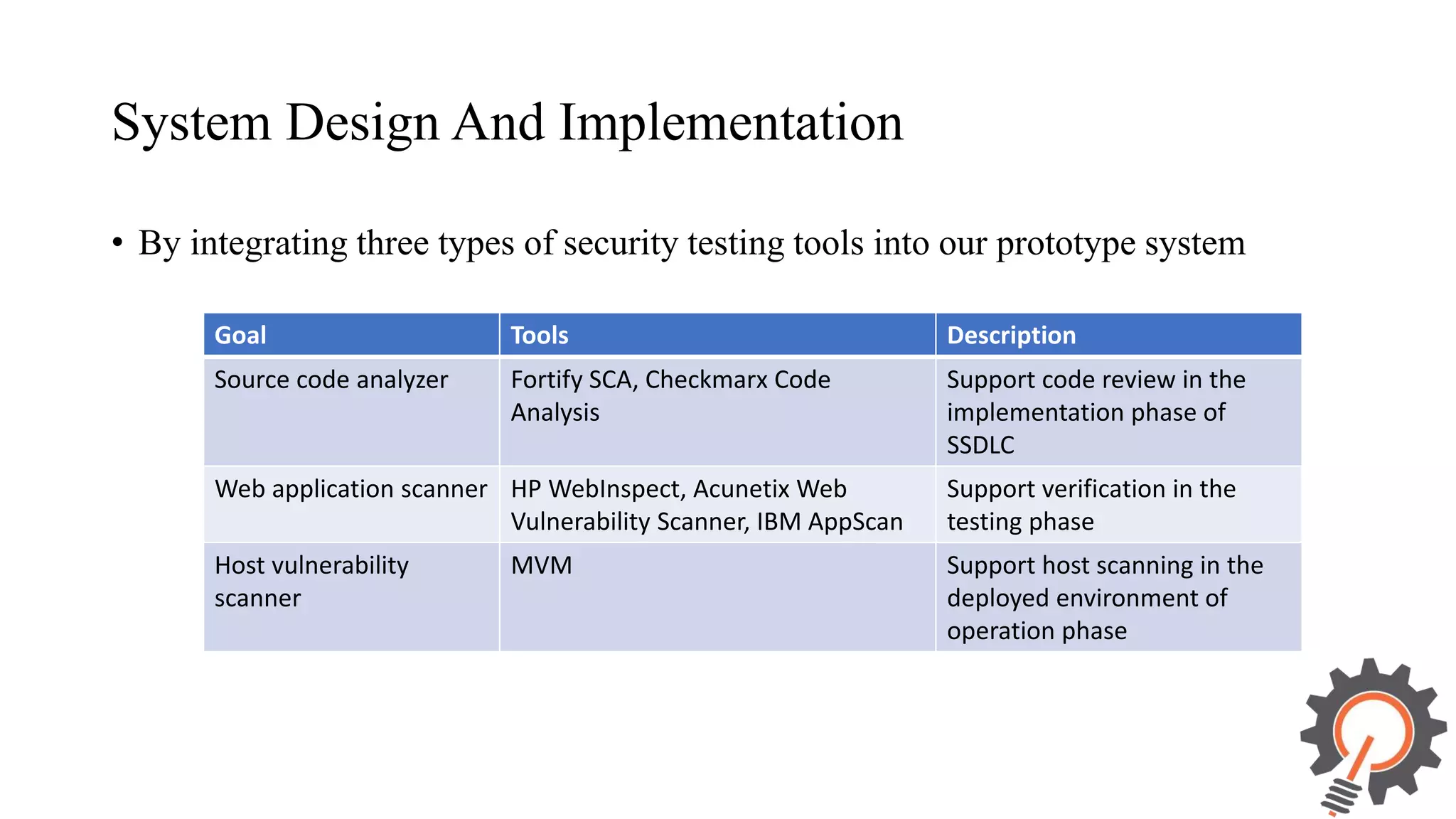
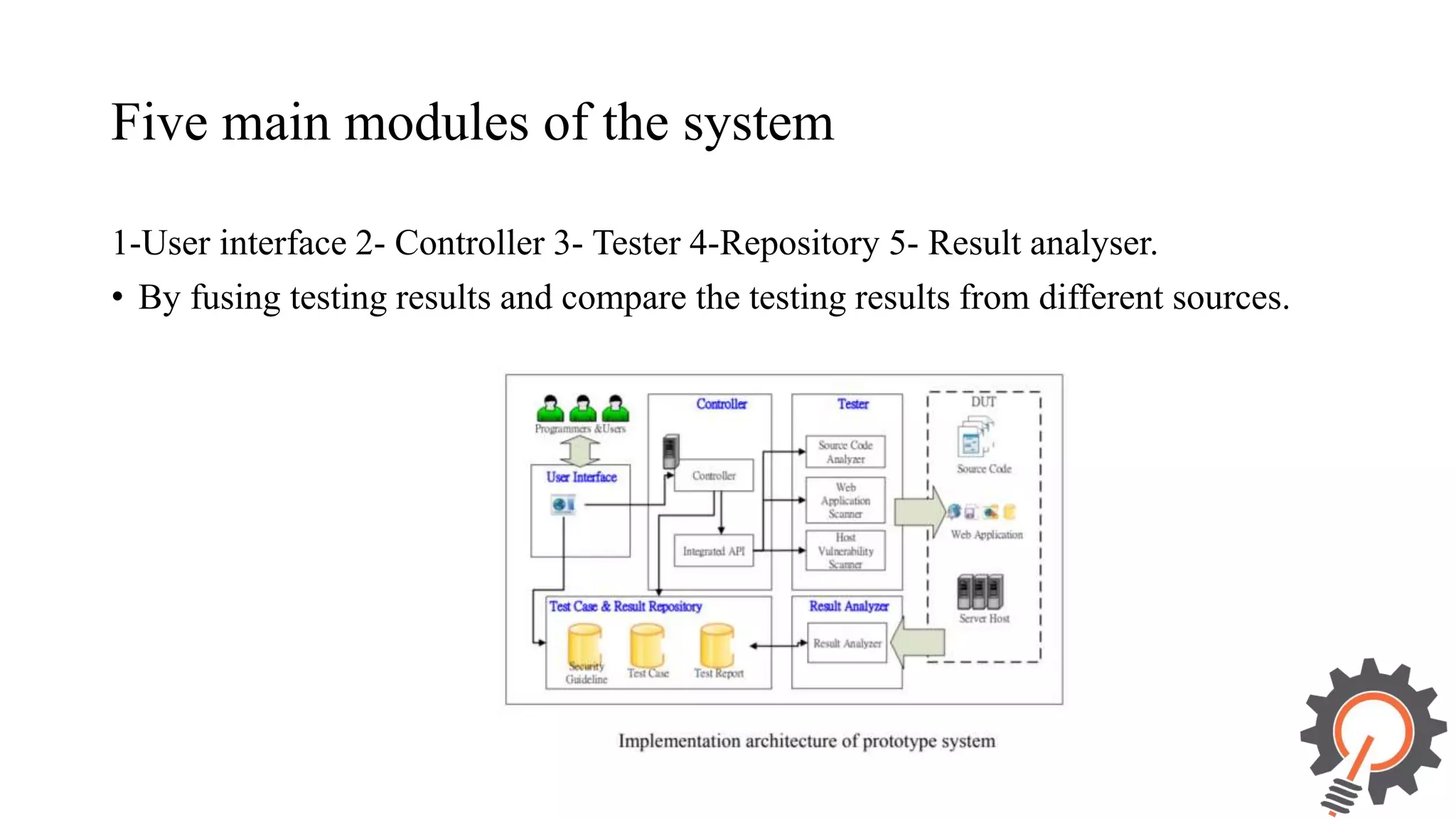
The document presents an integrated security testing framework for the secure software development life cycle (SSDLC). The framework includes four main phases: 1) defining security guidelines based on enterprise security requirements for each SSDLC phase, 2) constructing security test cases based on the guidelines, 3) executing test cases by integrating various security testing tools, and 4) converging results from different tools using a meta-vulnerability data model. The framework aims to adopt security activities into each SSDLC phase to improve security, generate test cases, integrate testing tools, and provide accurate results. It was evaluated through prototype testing of 50 software projects.