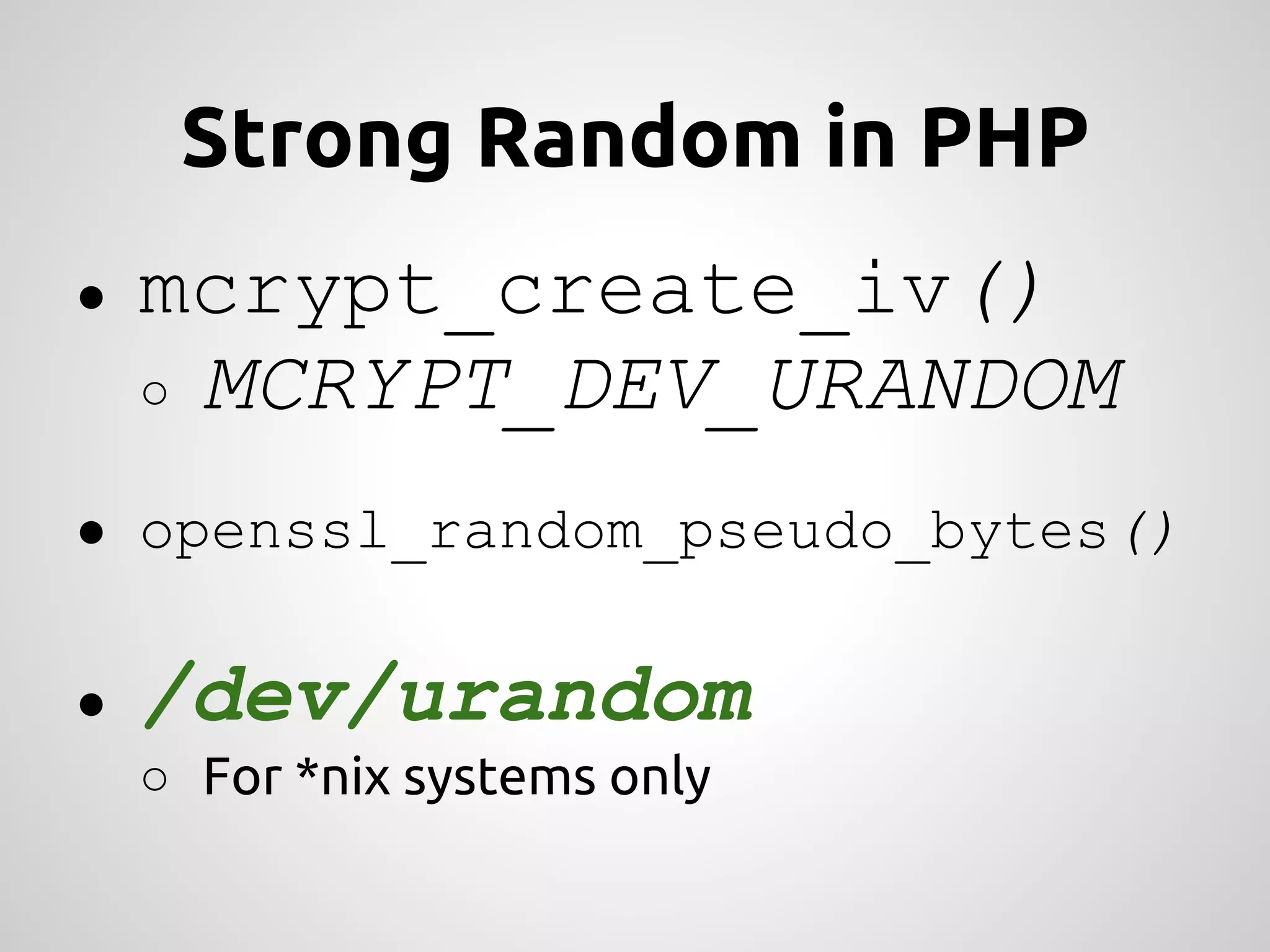
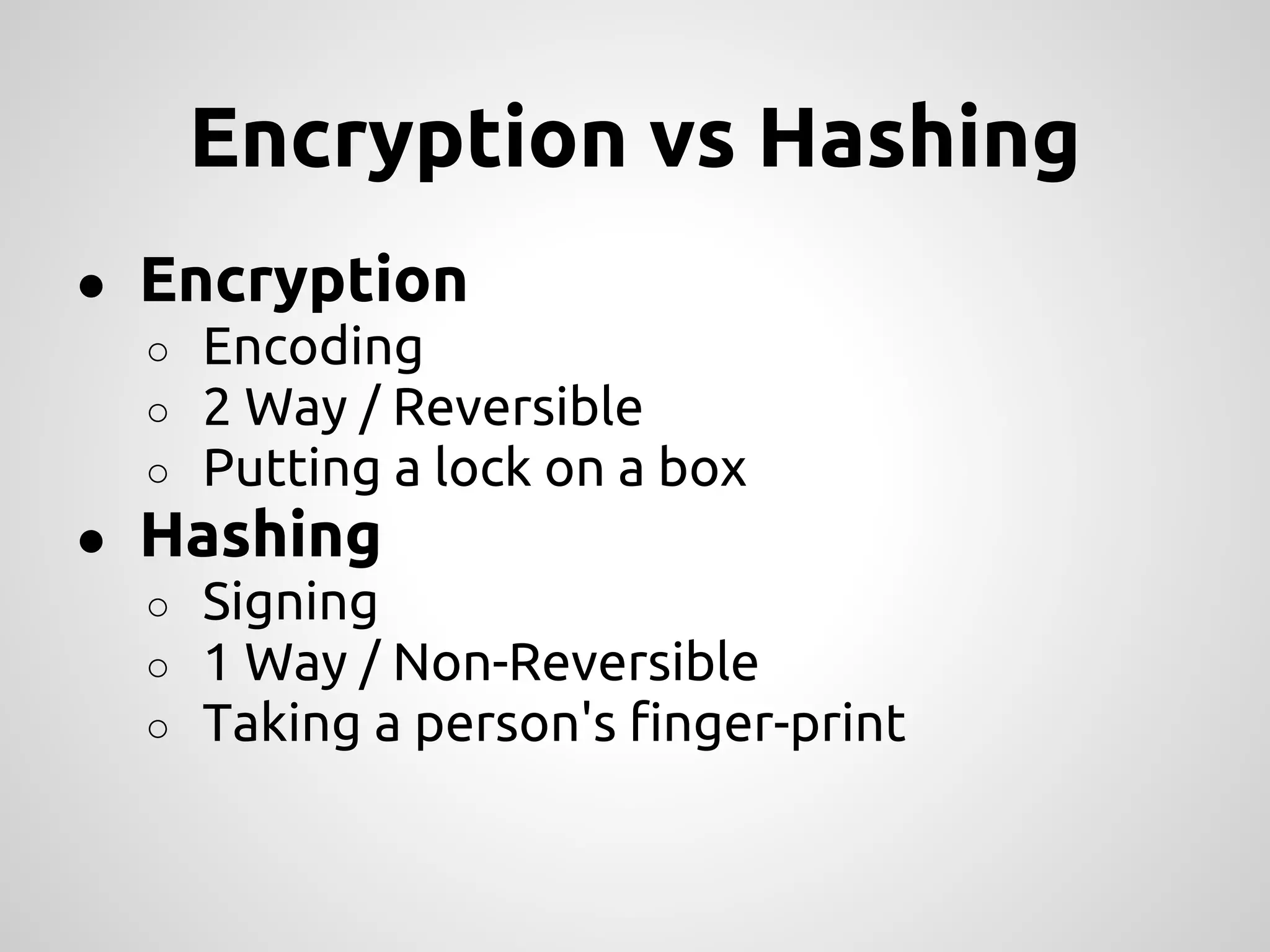
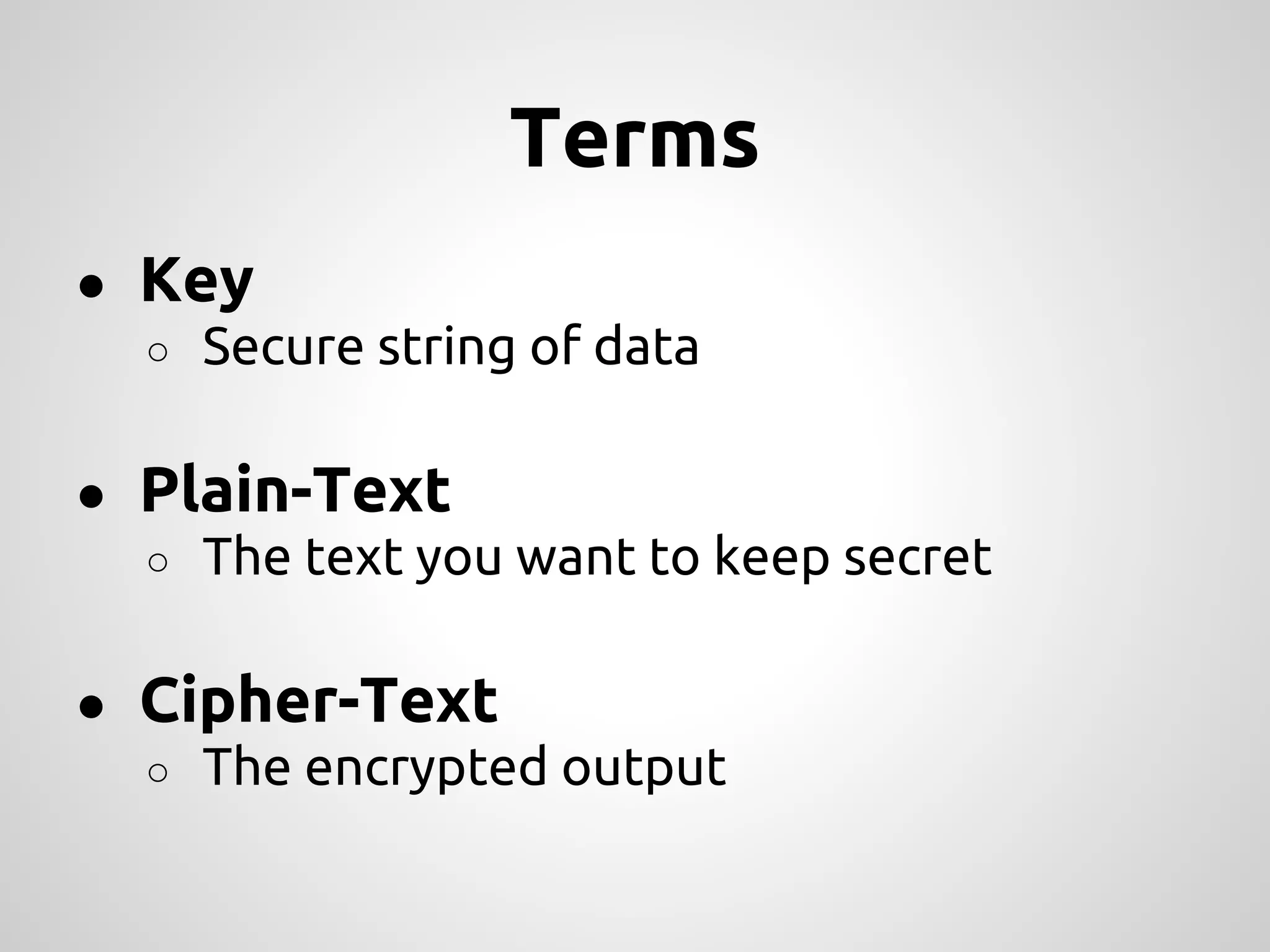
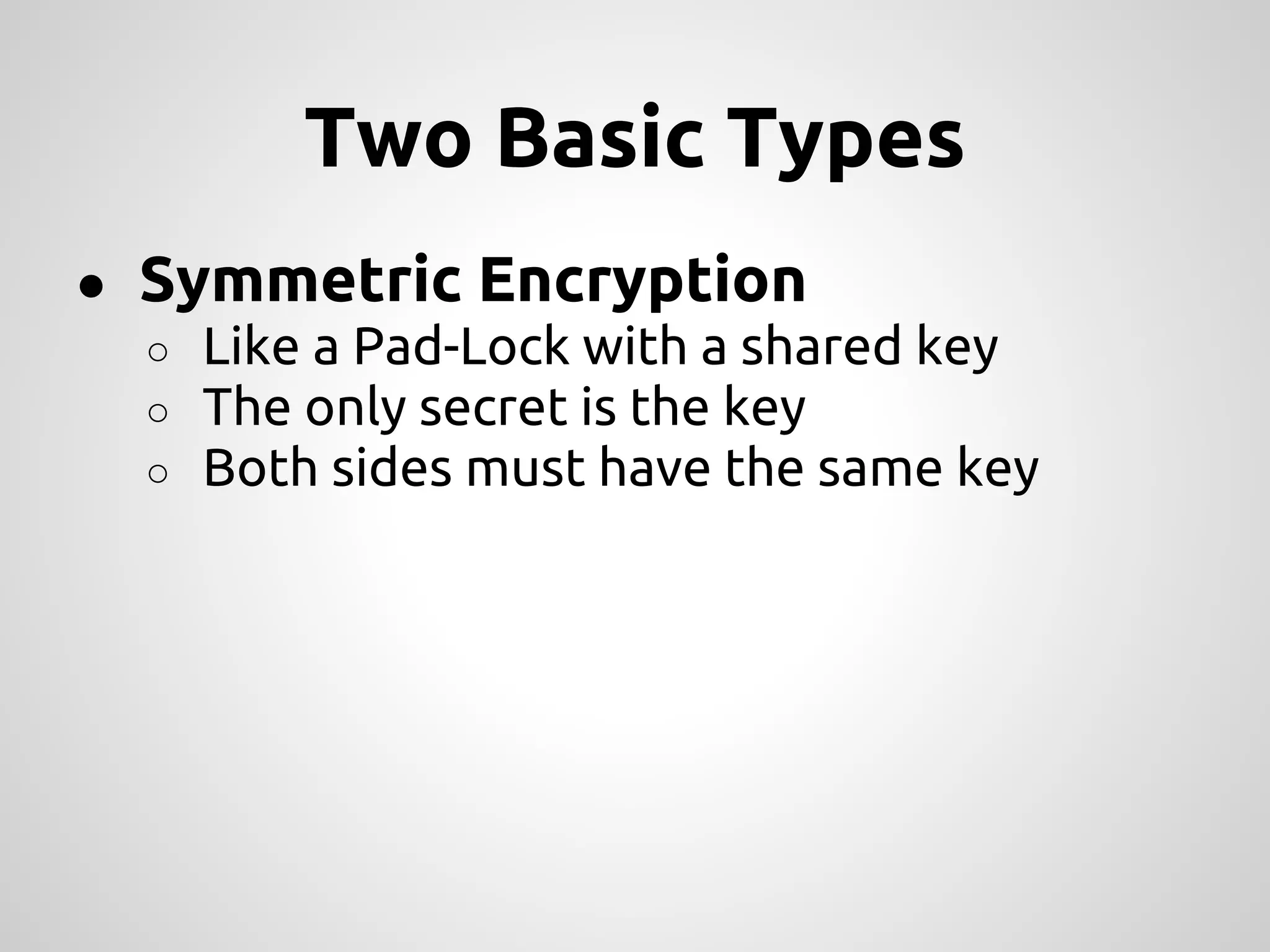
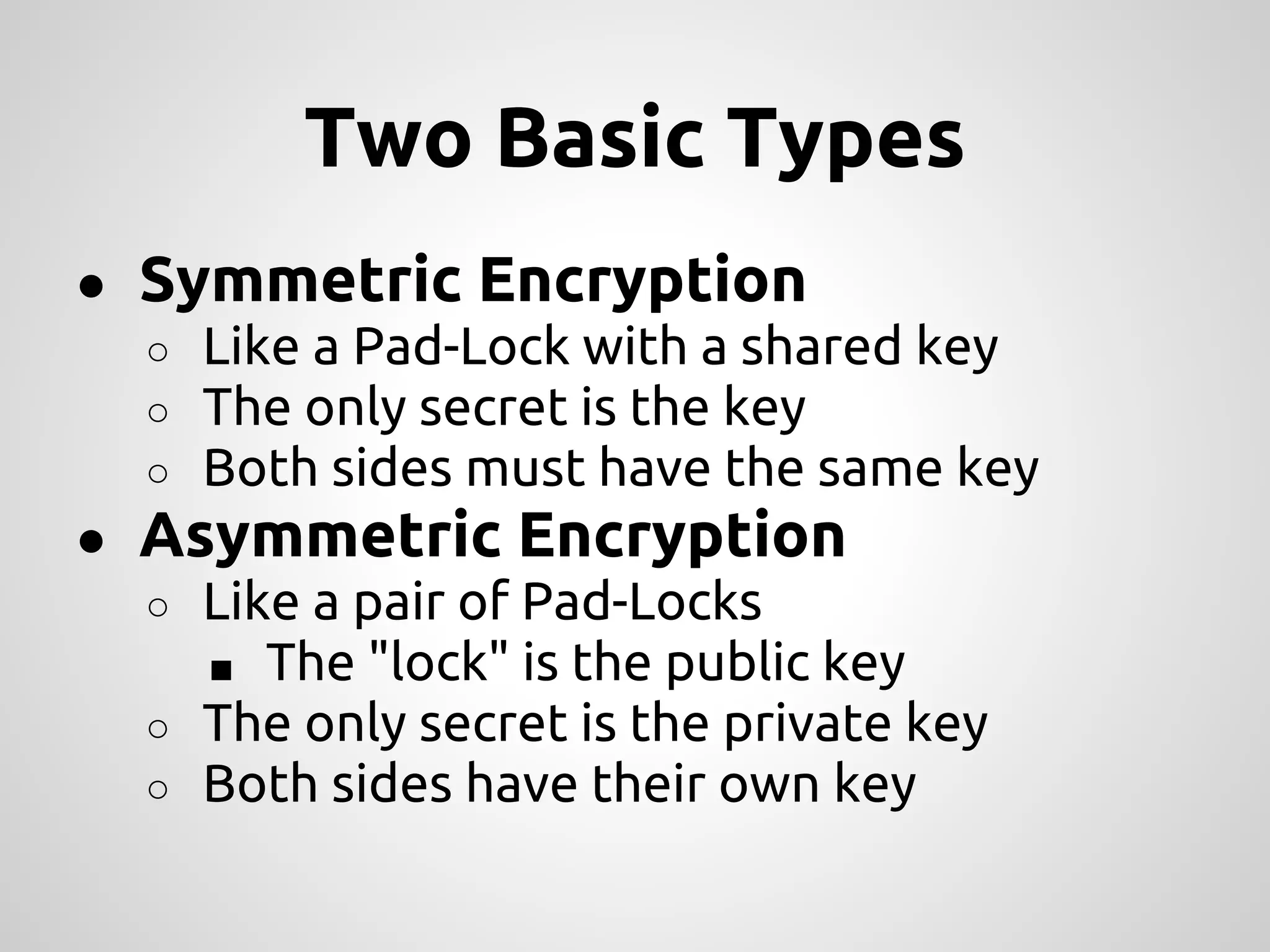
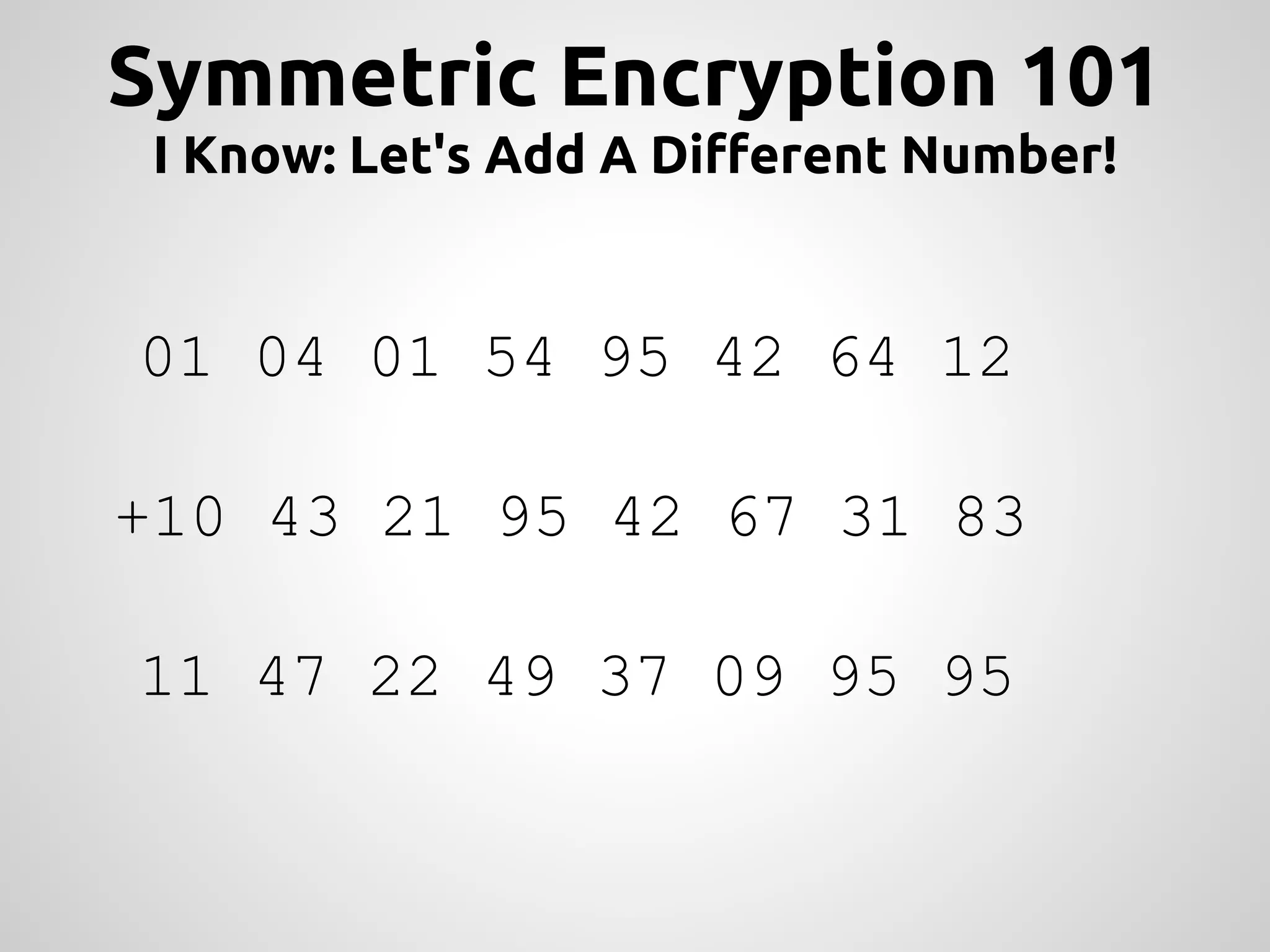
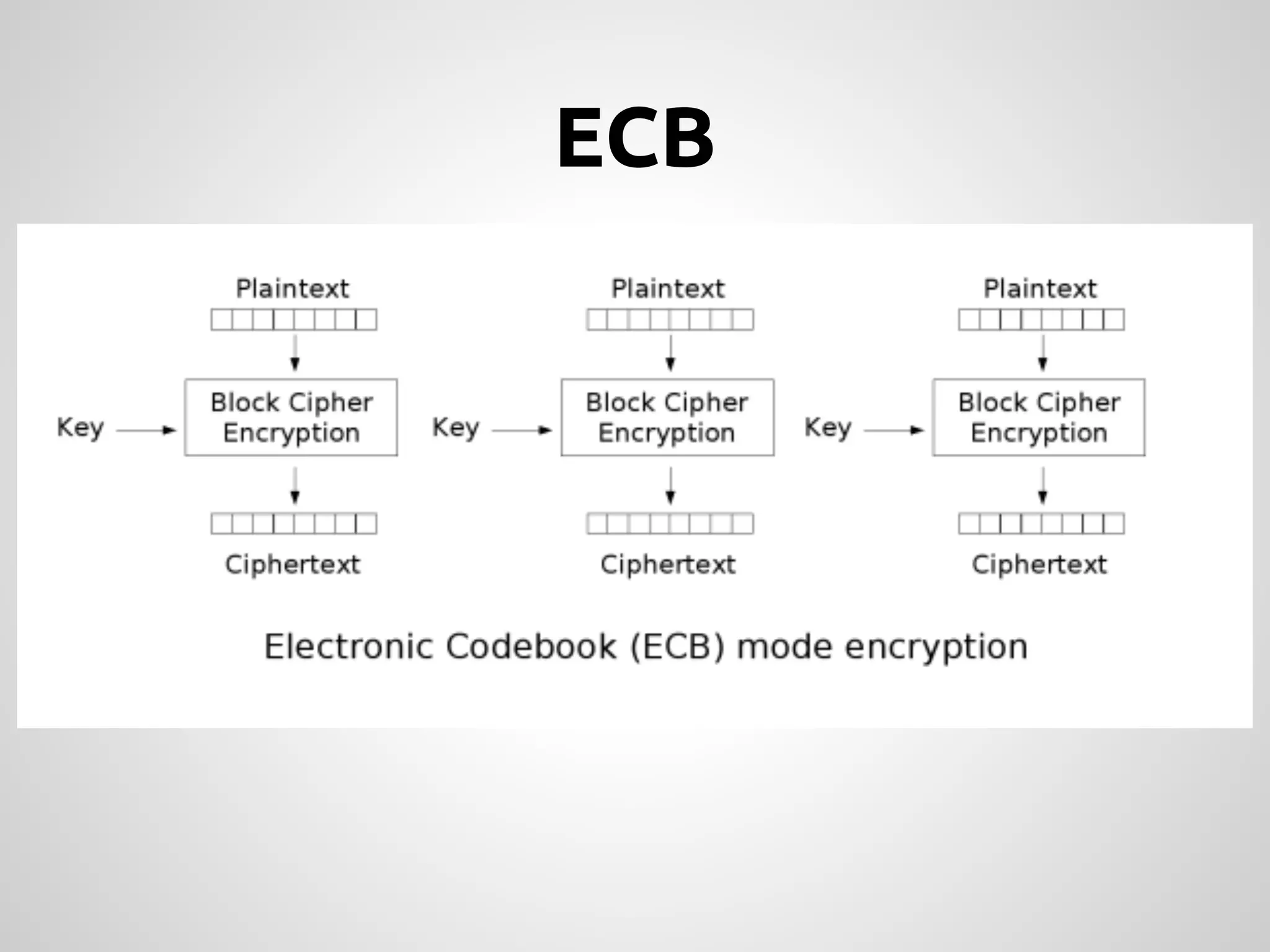
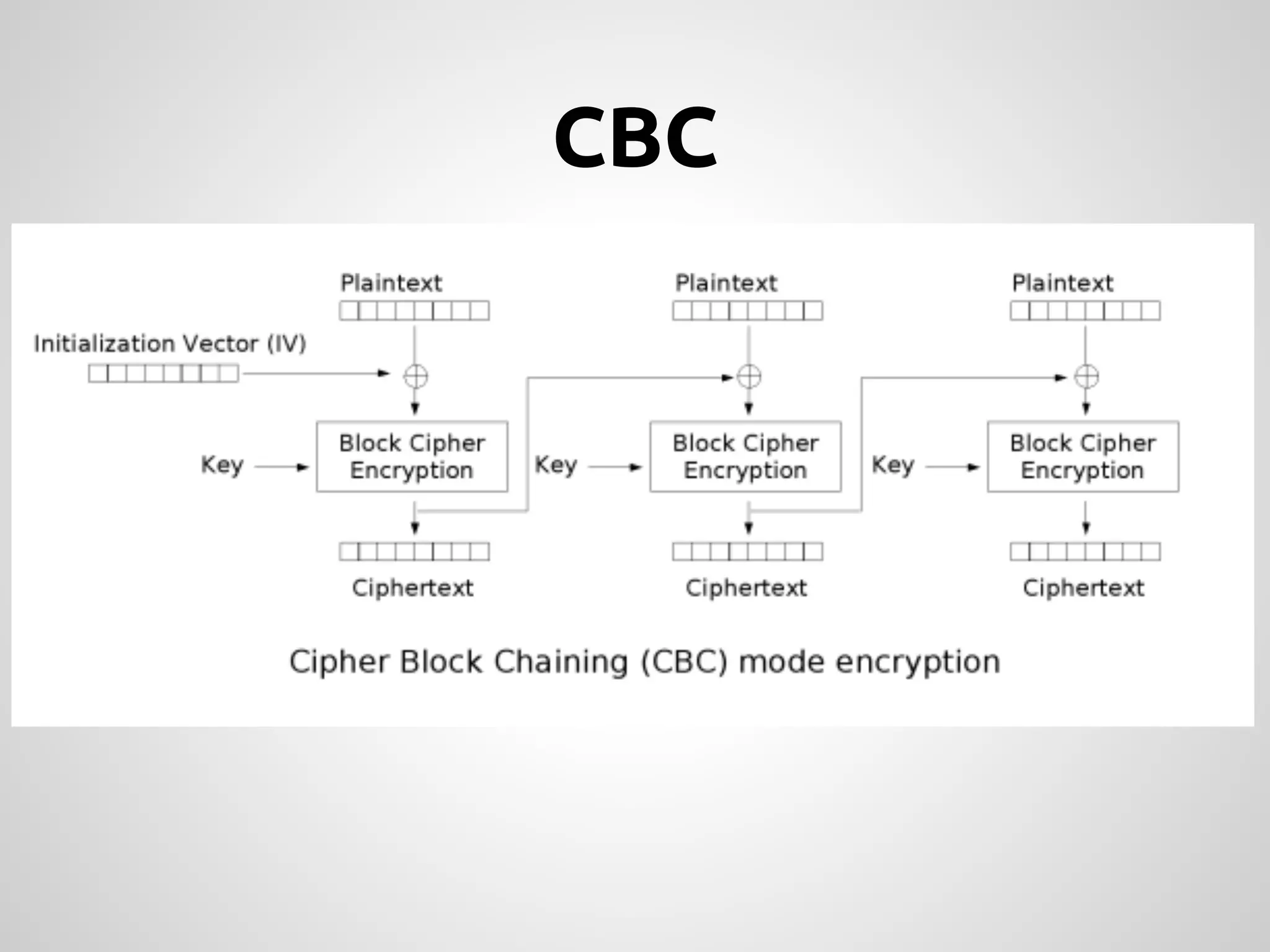
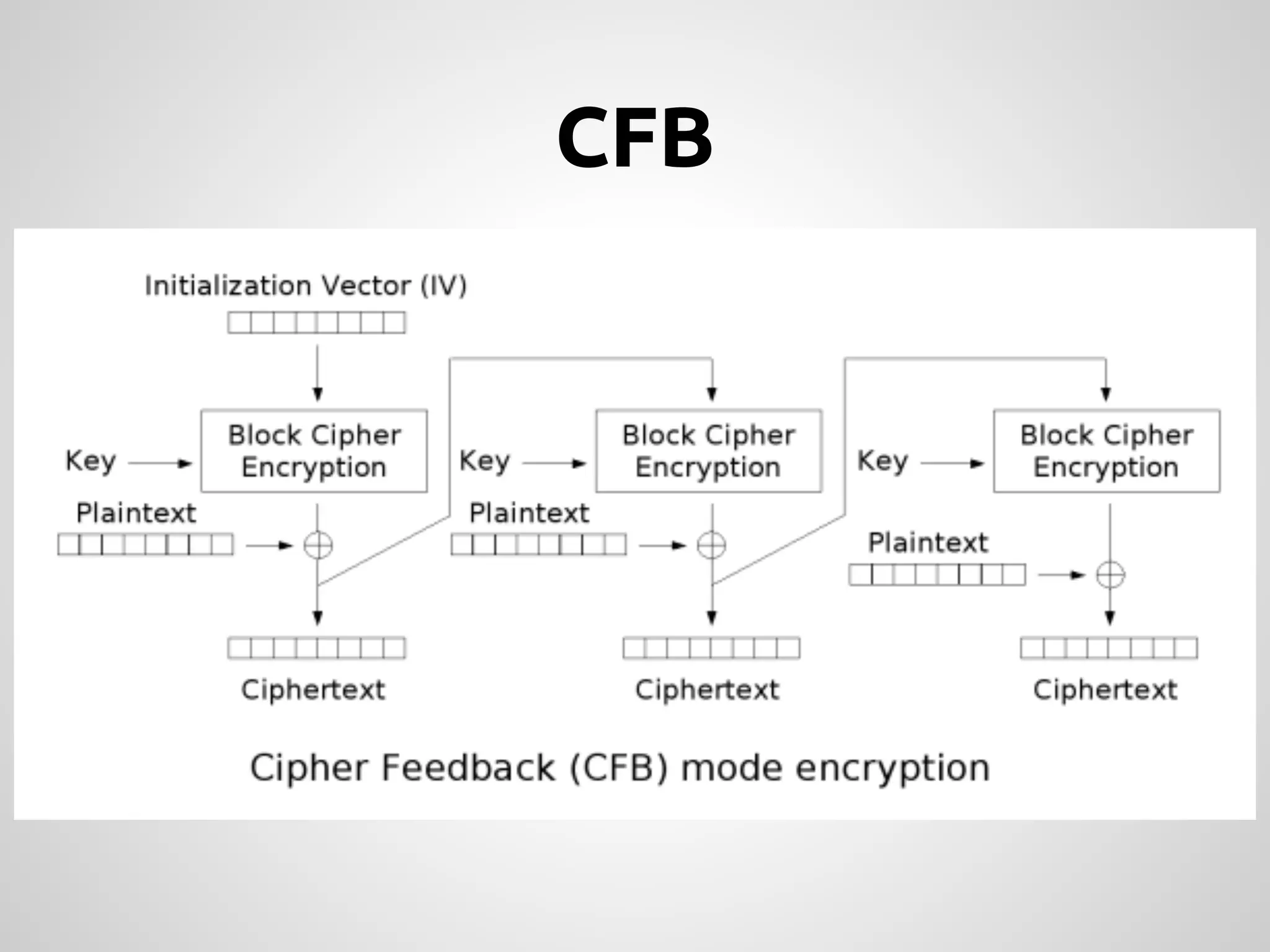
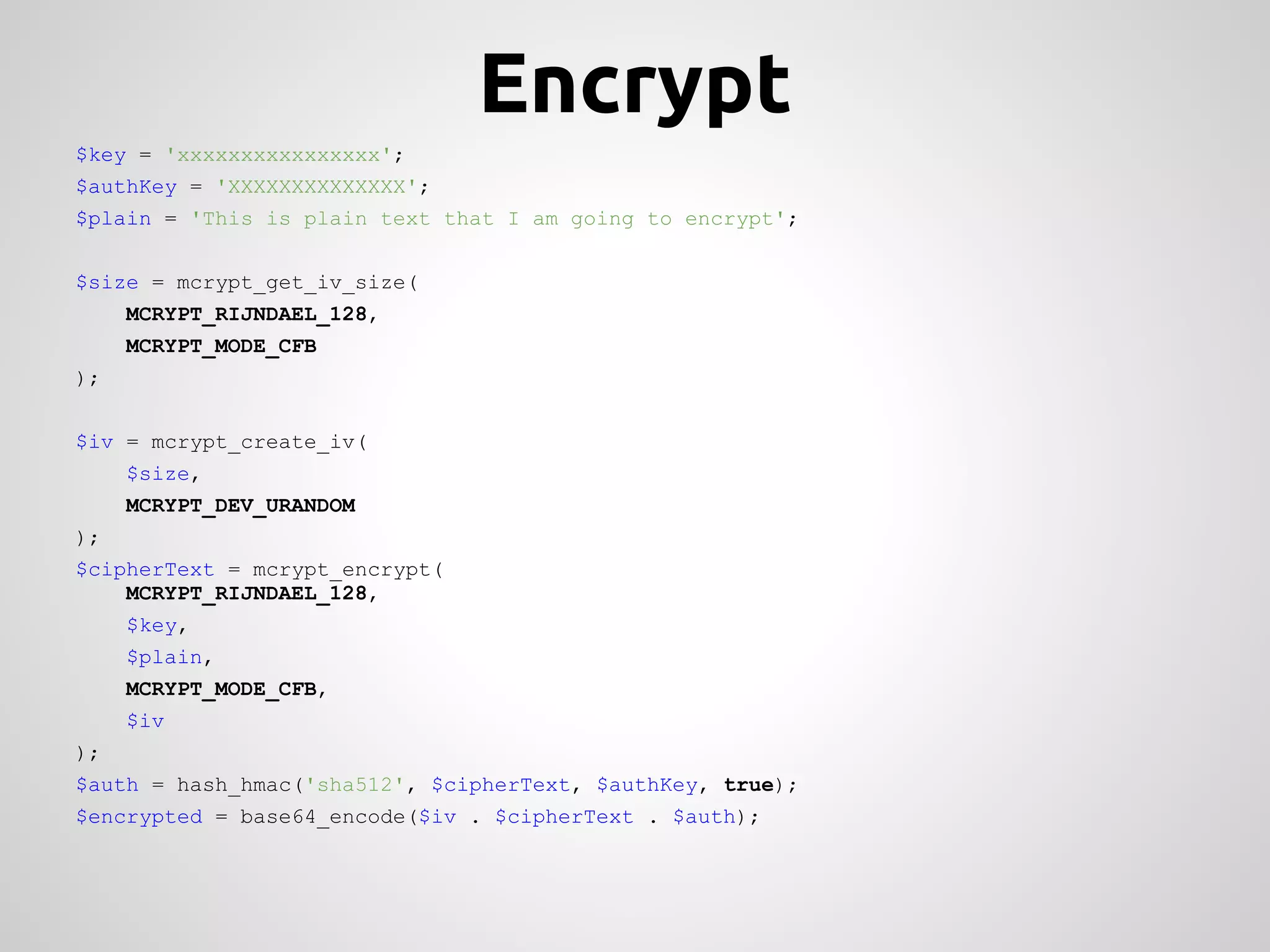
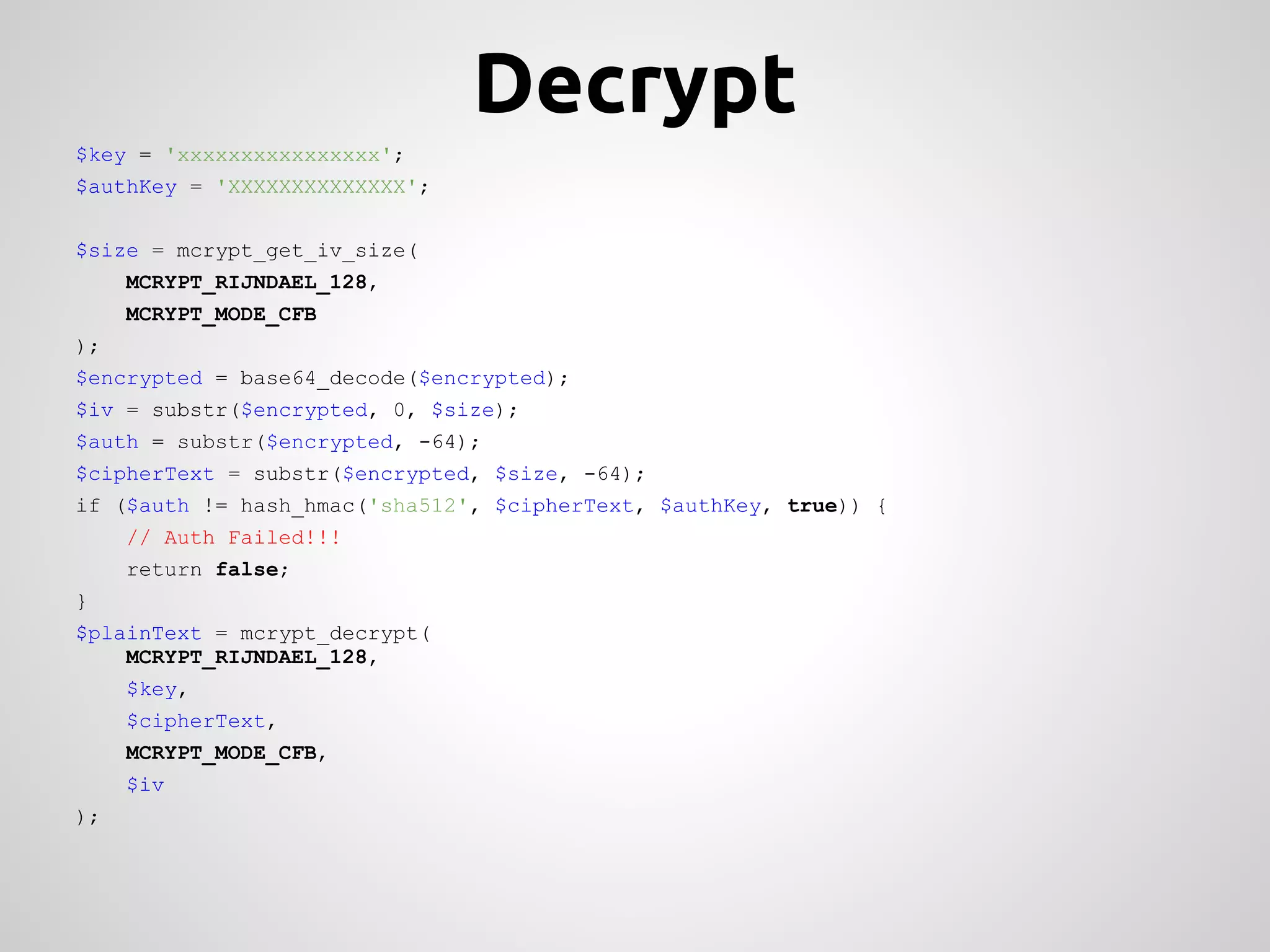
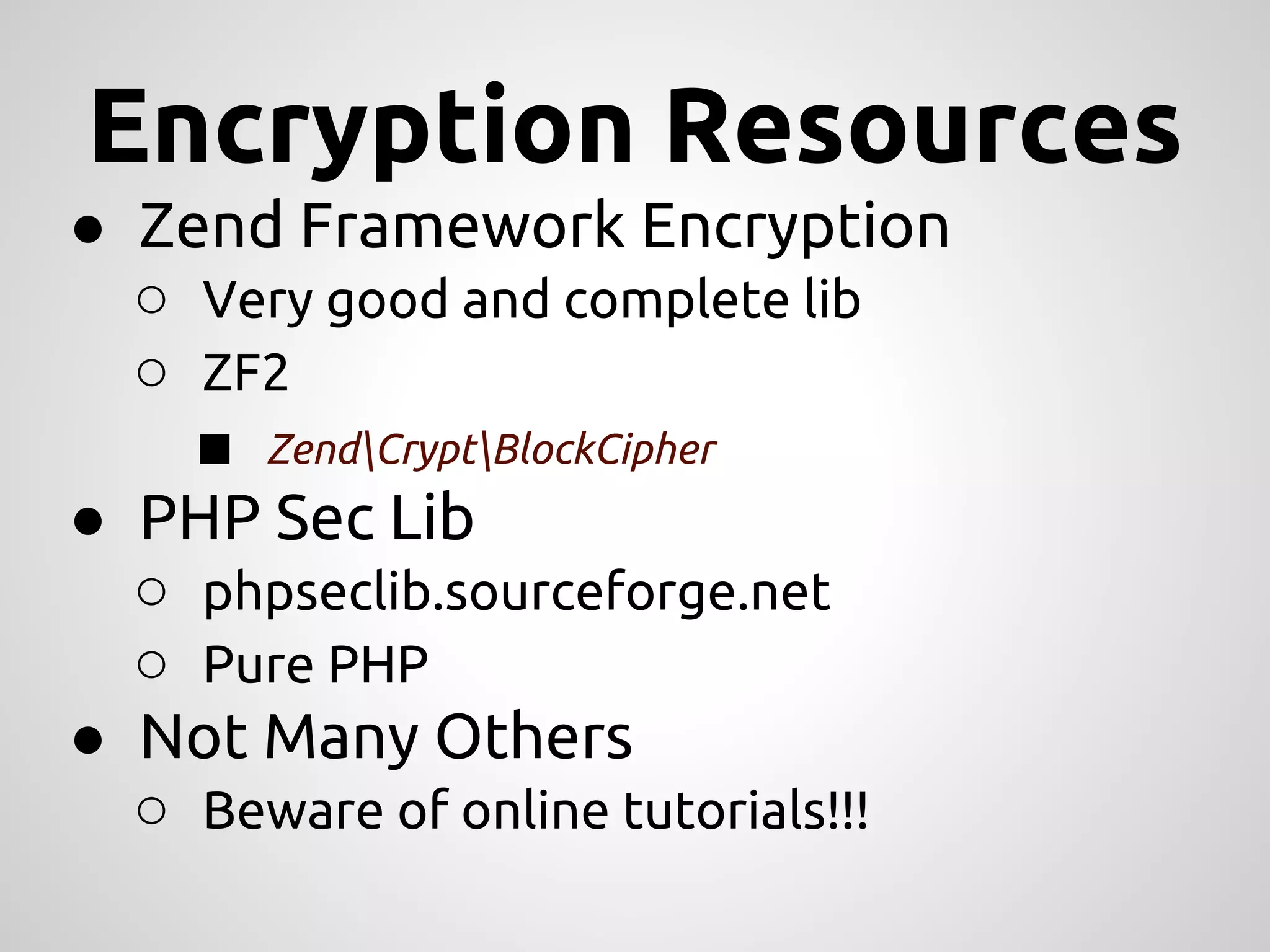
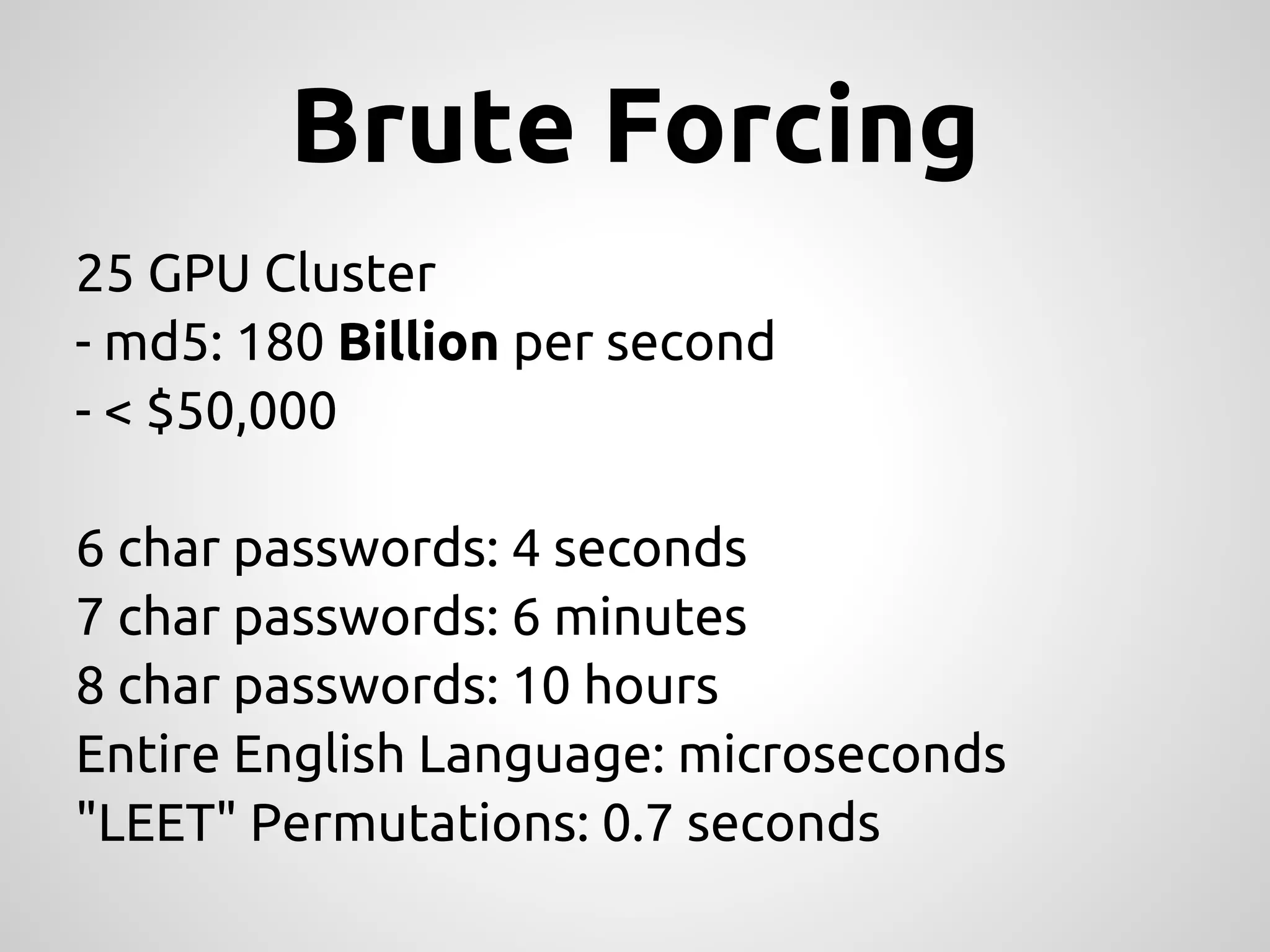
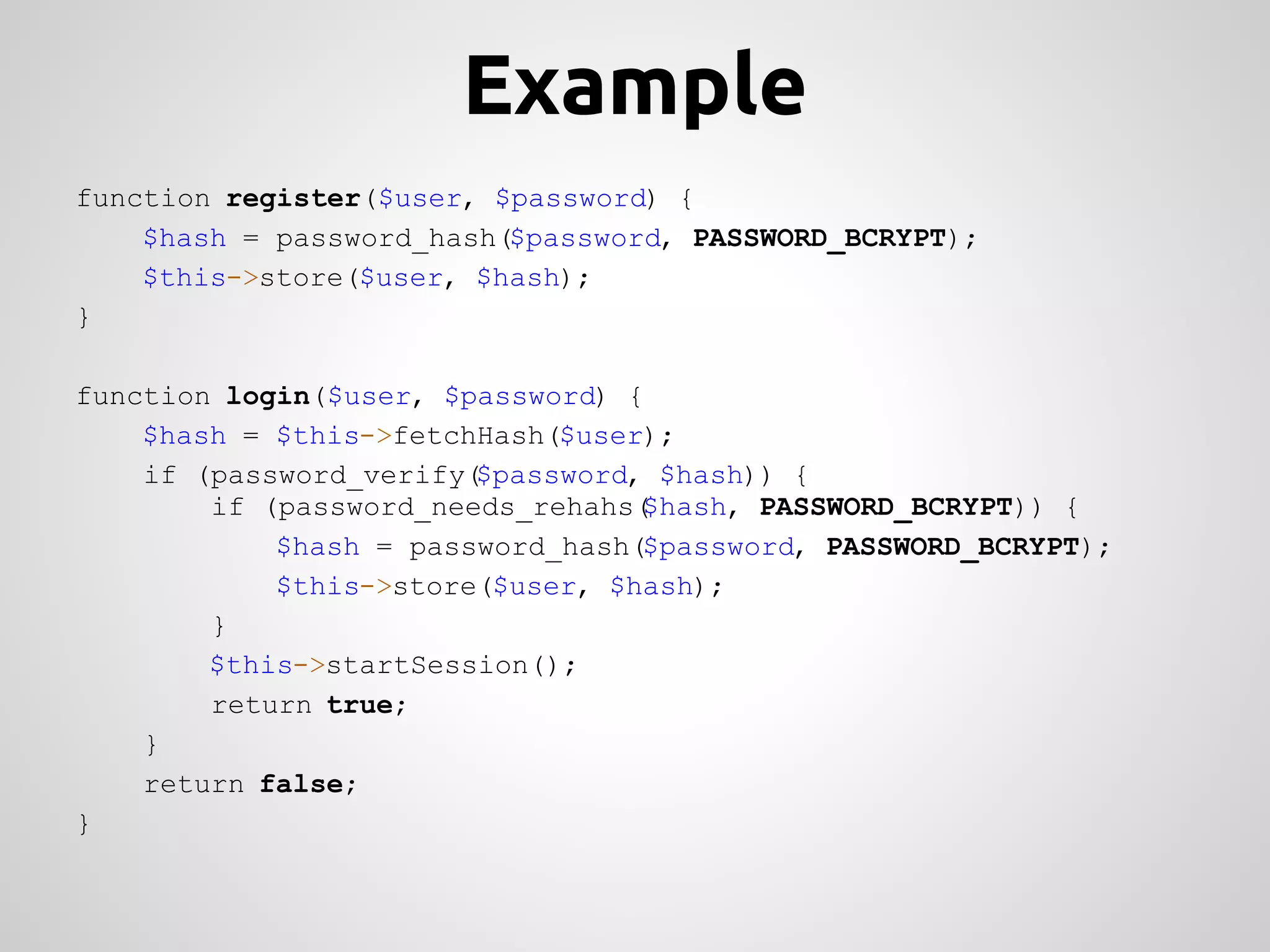
This document provides an overview of cryptography concepts for PHP developers. It discusses keeping data secure from viewing, tampering and forgery without cryptography being a "silver bullet" solution. The document covers random number generation, symmetric and asymmetric encryption, hashing, common ciphers and modes, authentication, and password storage best practices like hashing passwords instead of encrypting them. The key messages are that cryptography is very difficult to implement securely and developers should rely on expert libraries or hire an expert instead of rolling their own solutions.