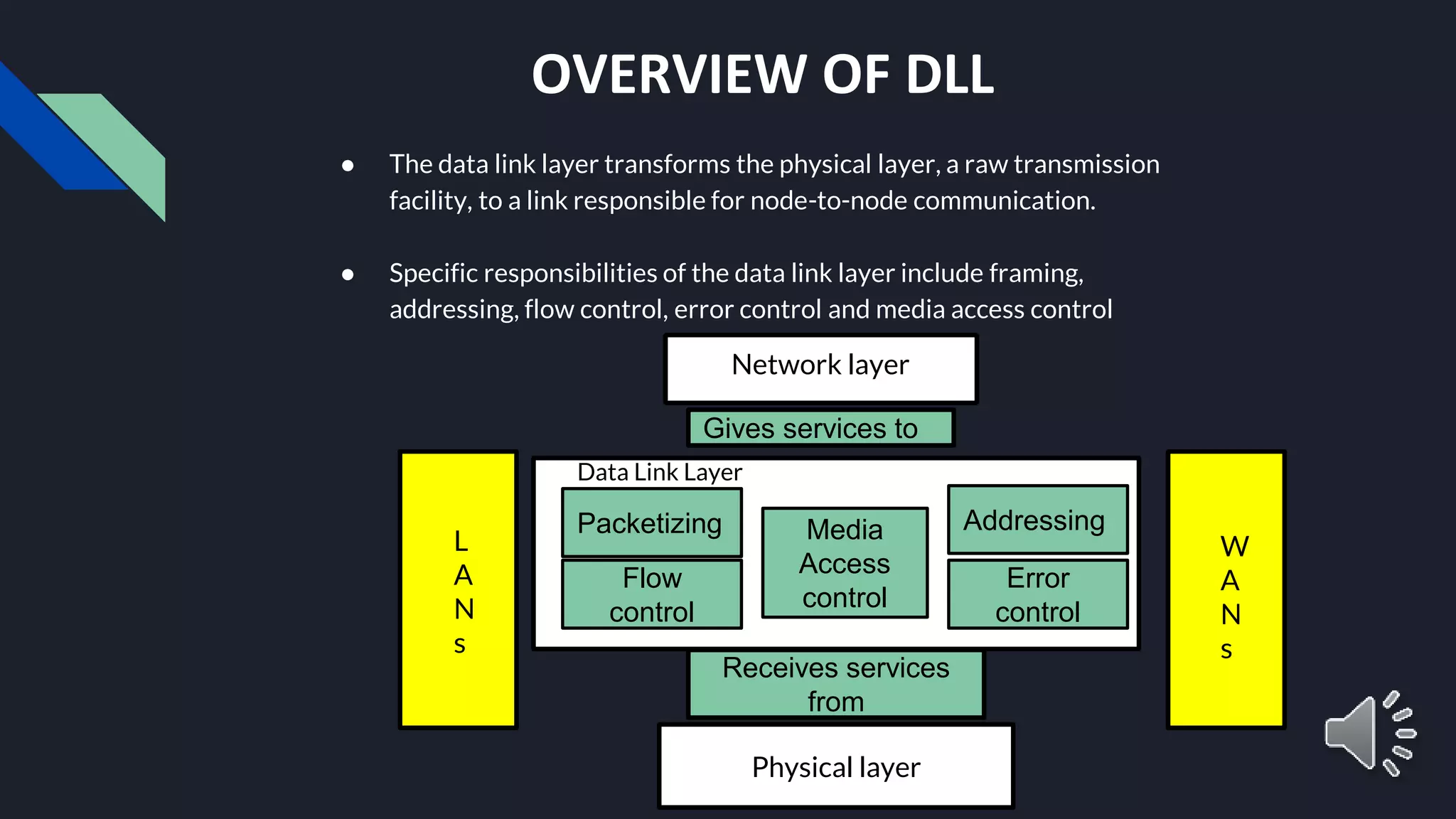
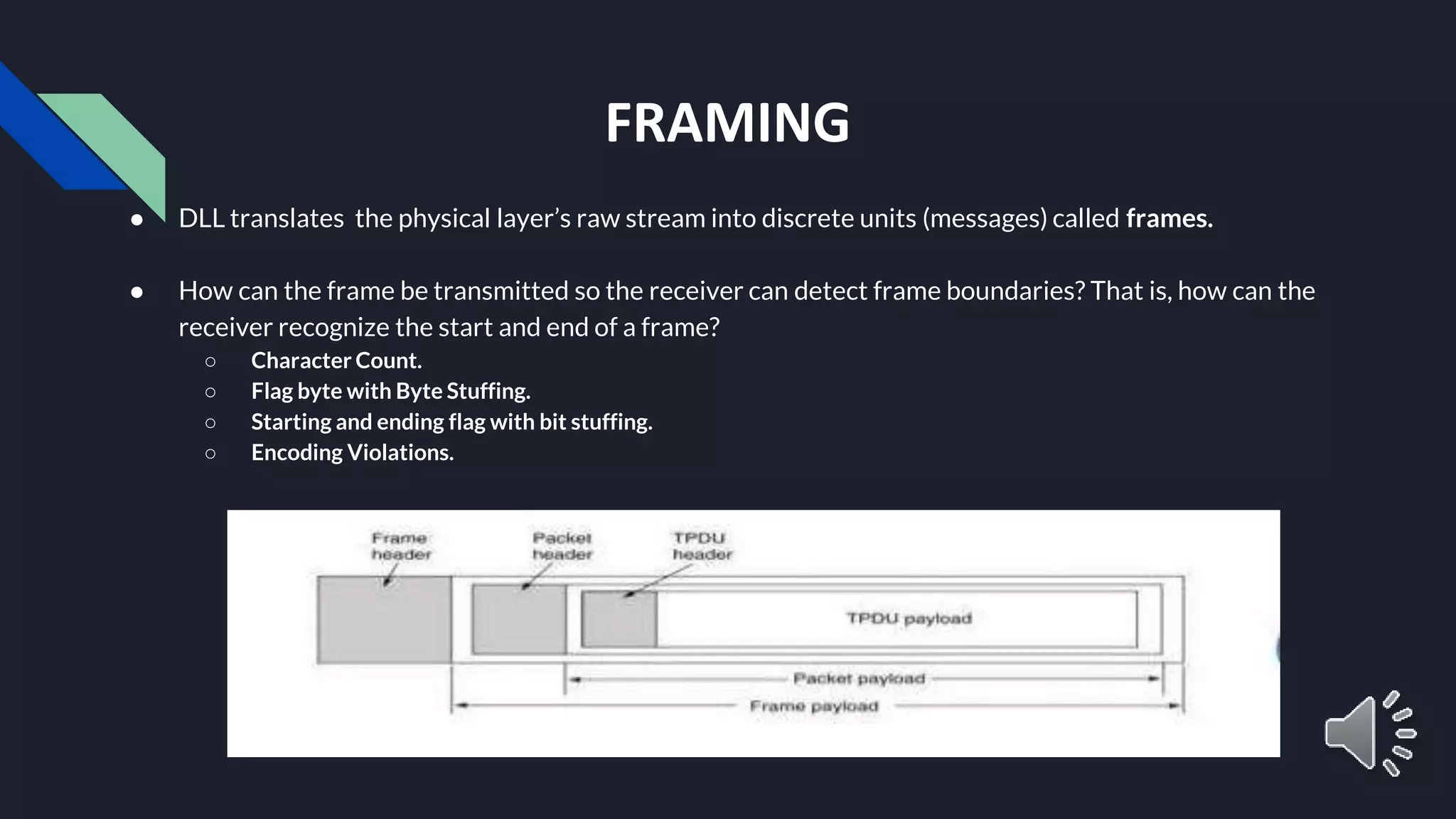
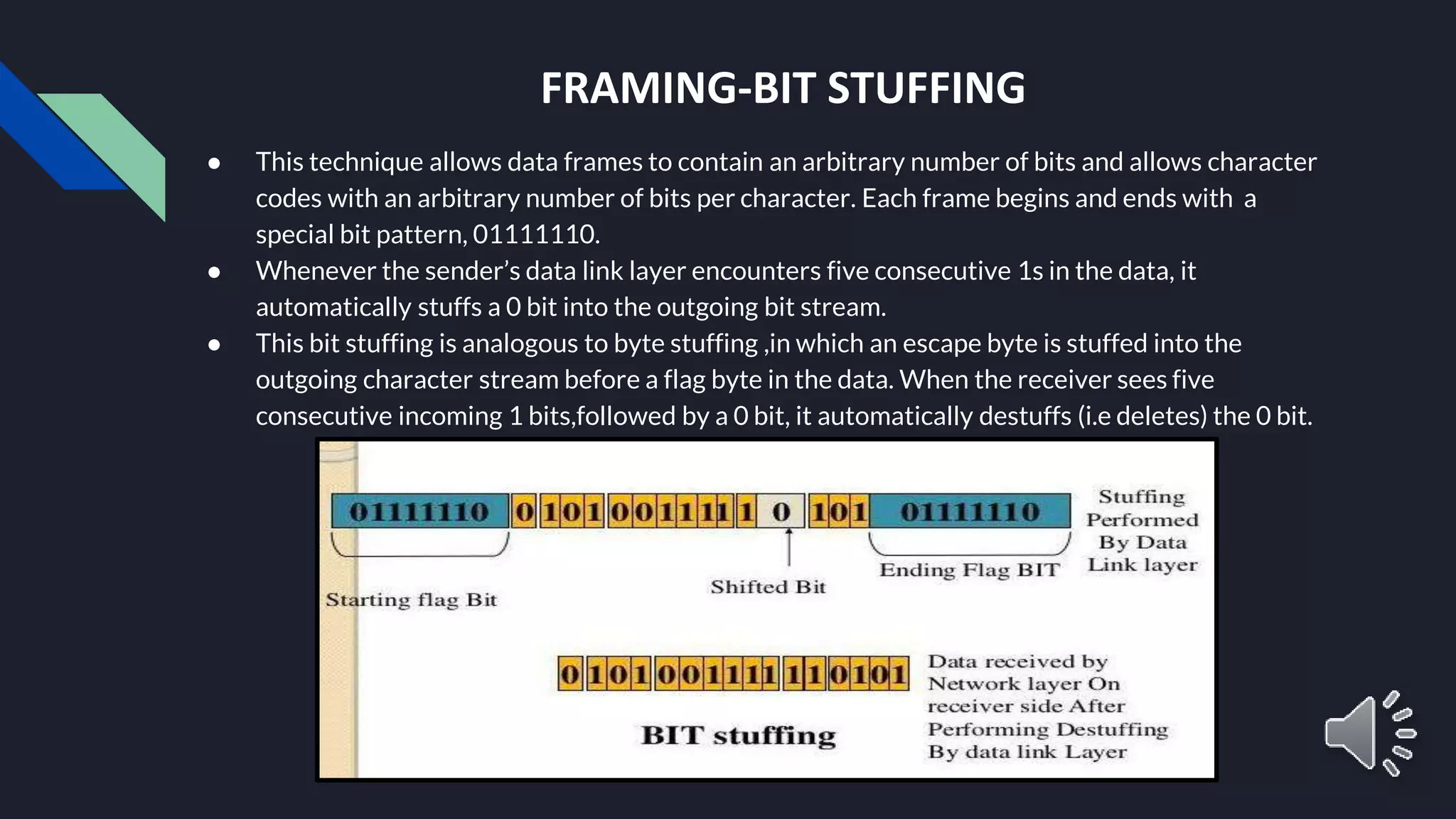
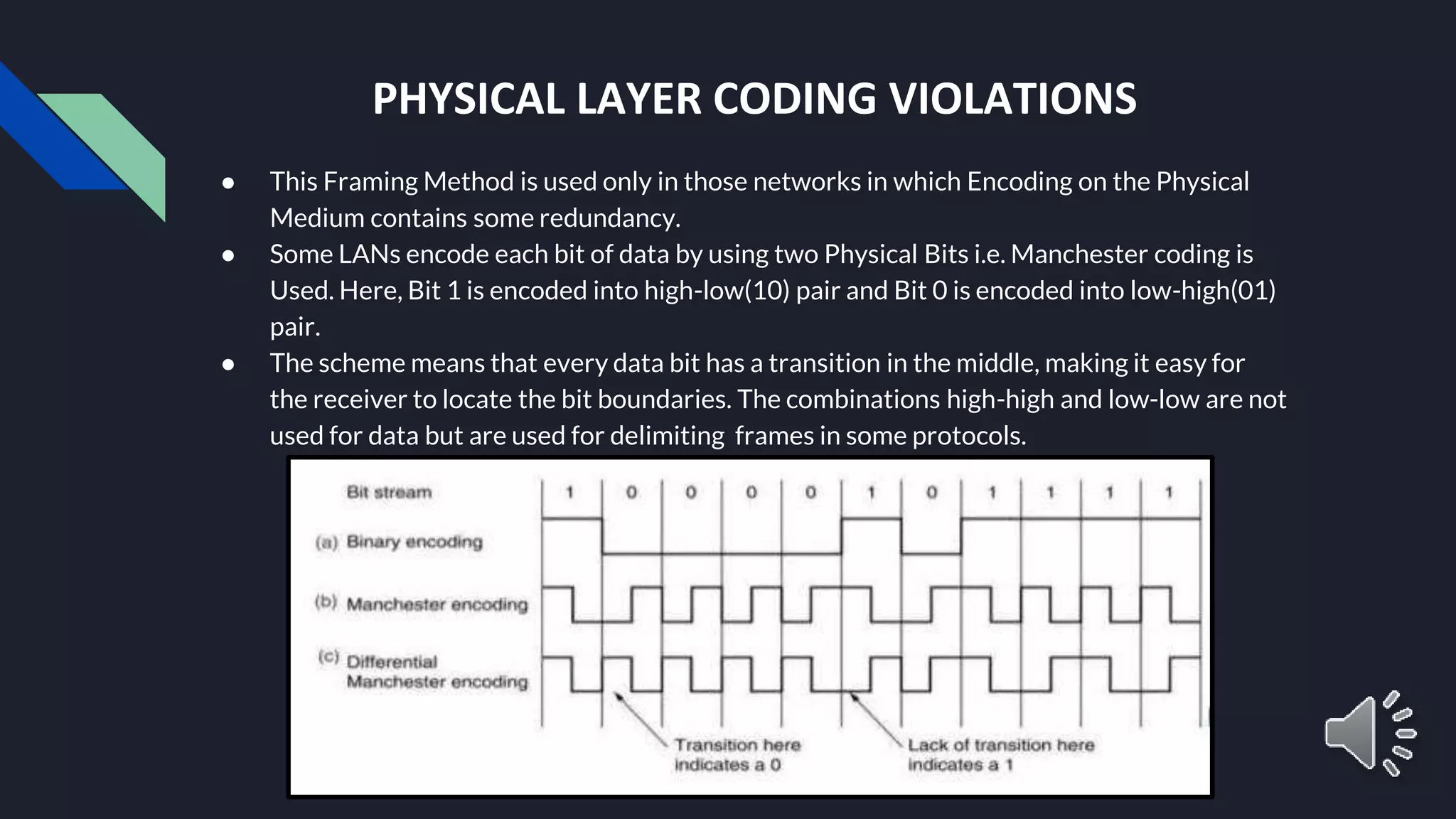
The document provides an overview of the Data Link Layer (DLL) in data communication, detailing its responsibilities, including framing, error control, flow control, and media access control. It explains various framing methods like character count, byte stuffing, and bit stuffing, as well as error detection and correction techniques such as parity check and cyclic redundancy check (CRC). Additionally, it touches on flow control mechanisms to ensure that data transmission rates match between sender and receiver.