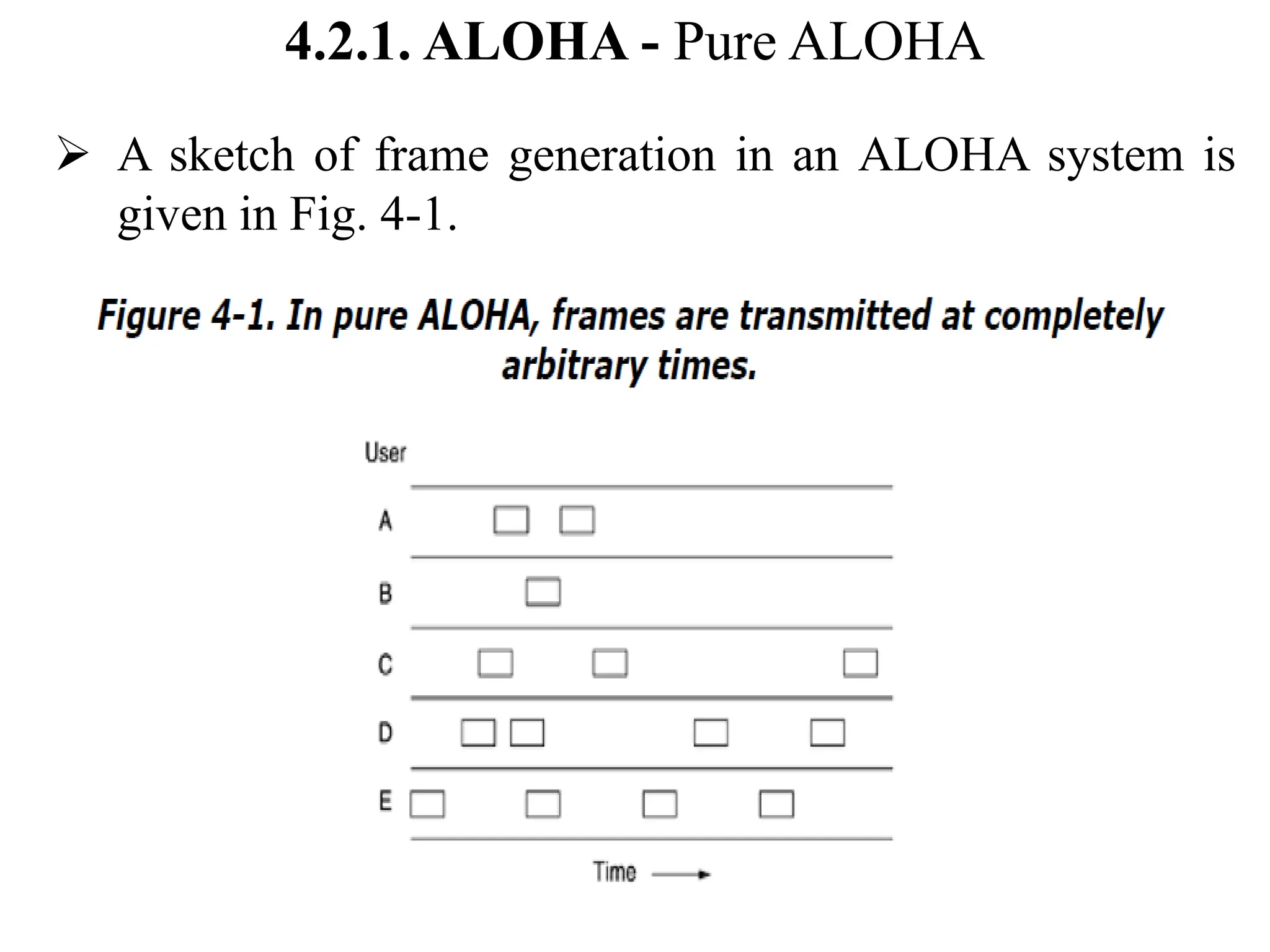
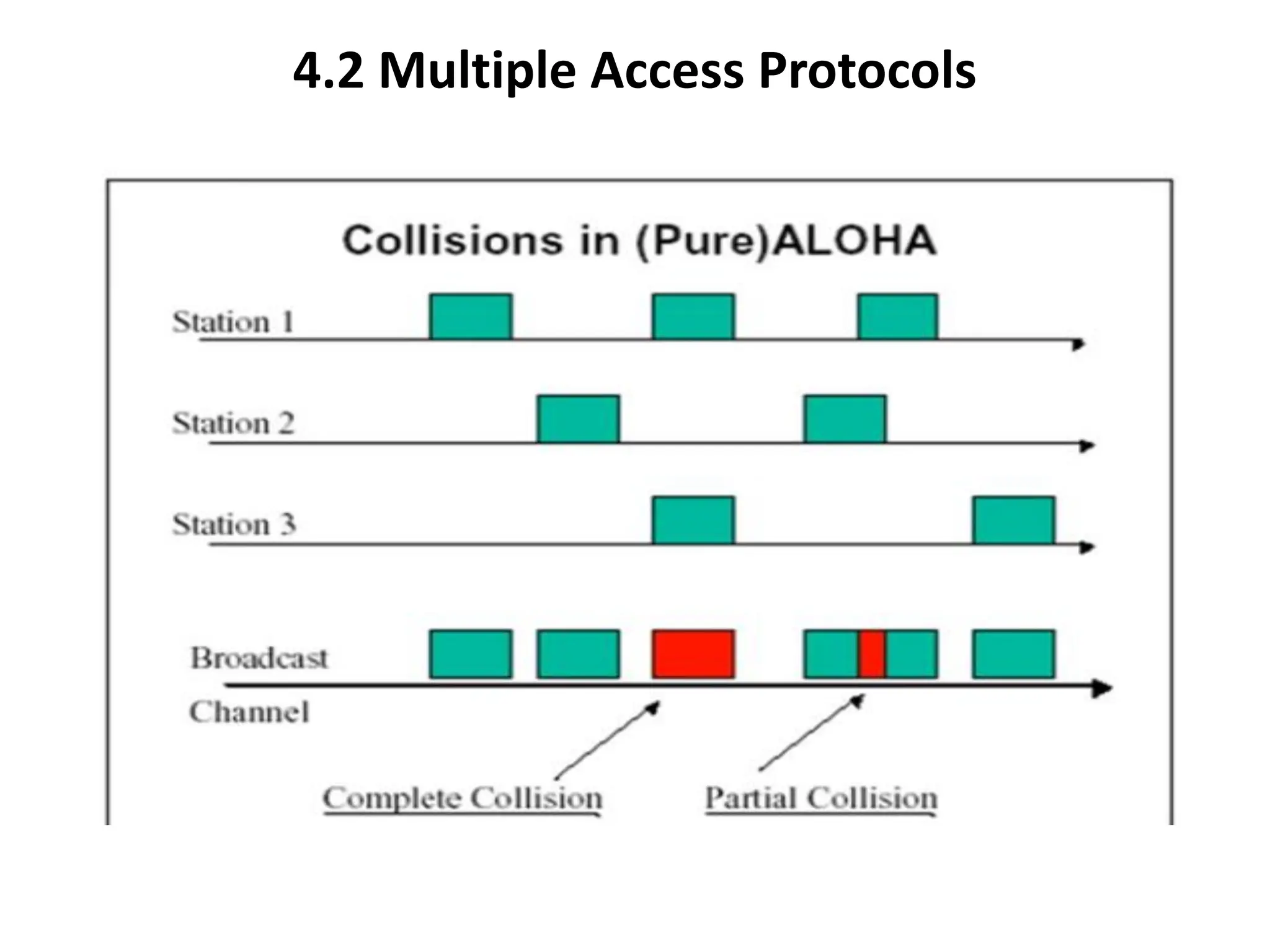
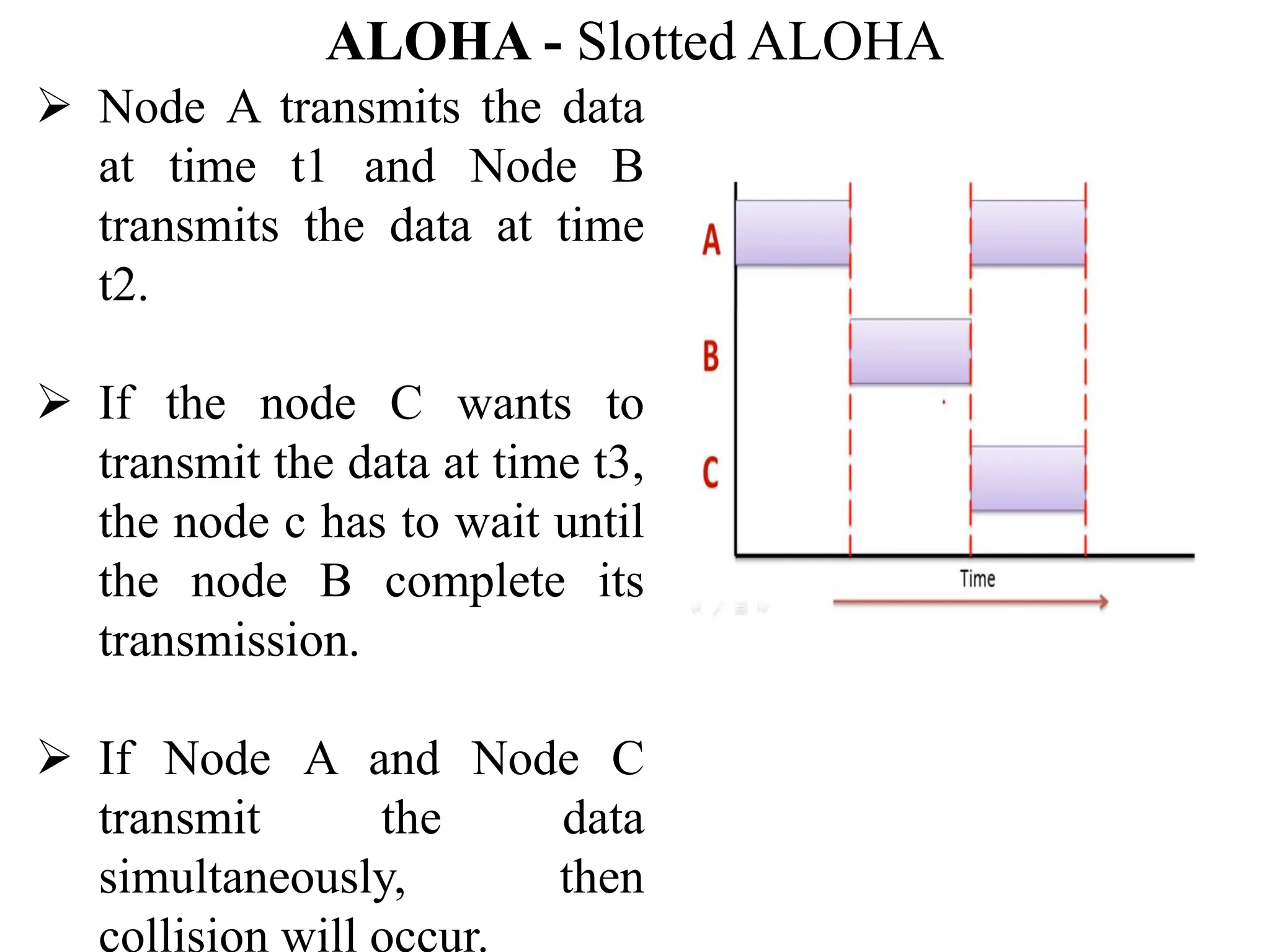
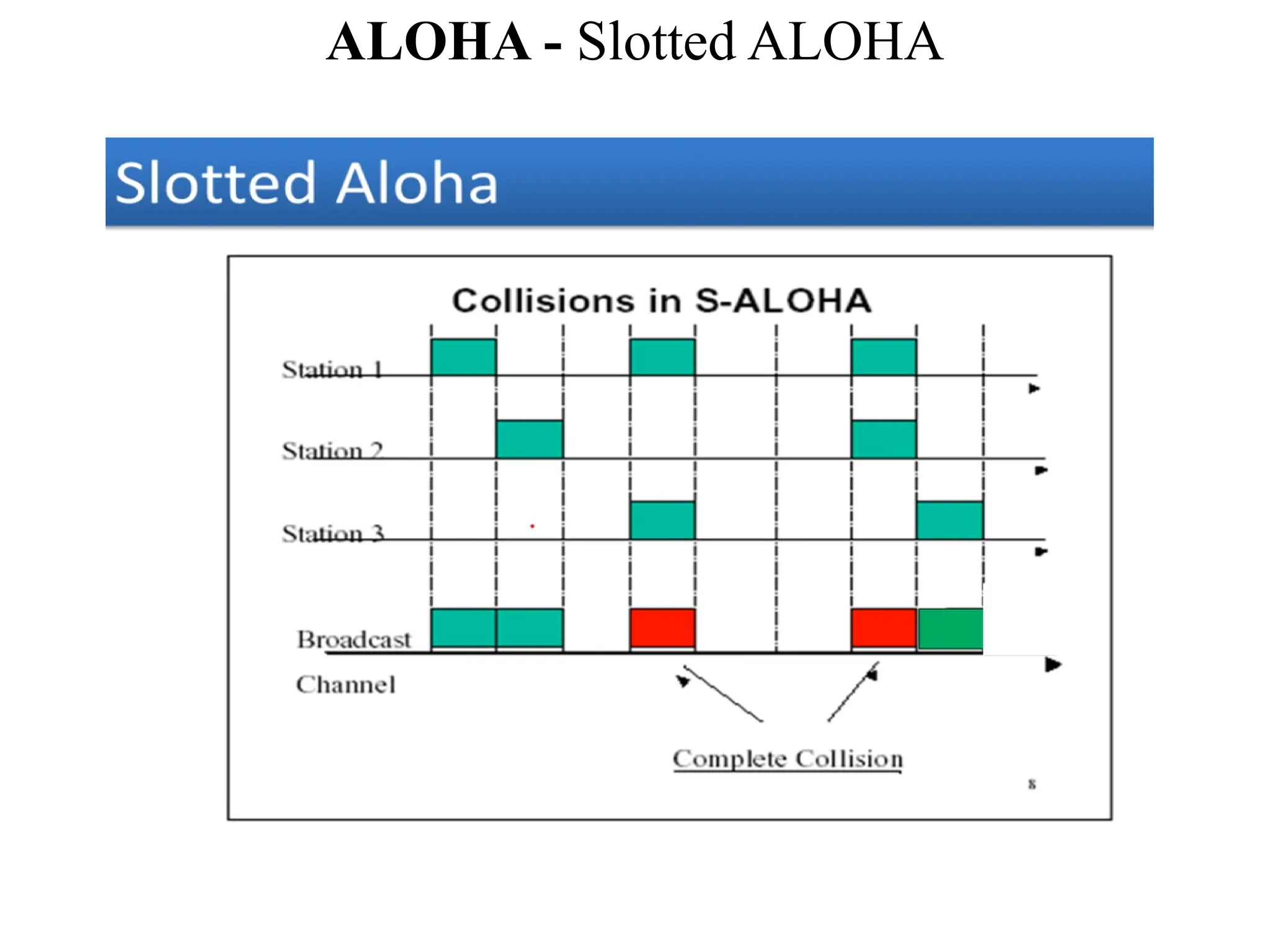
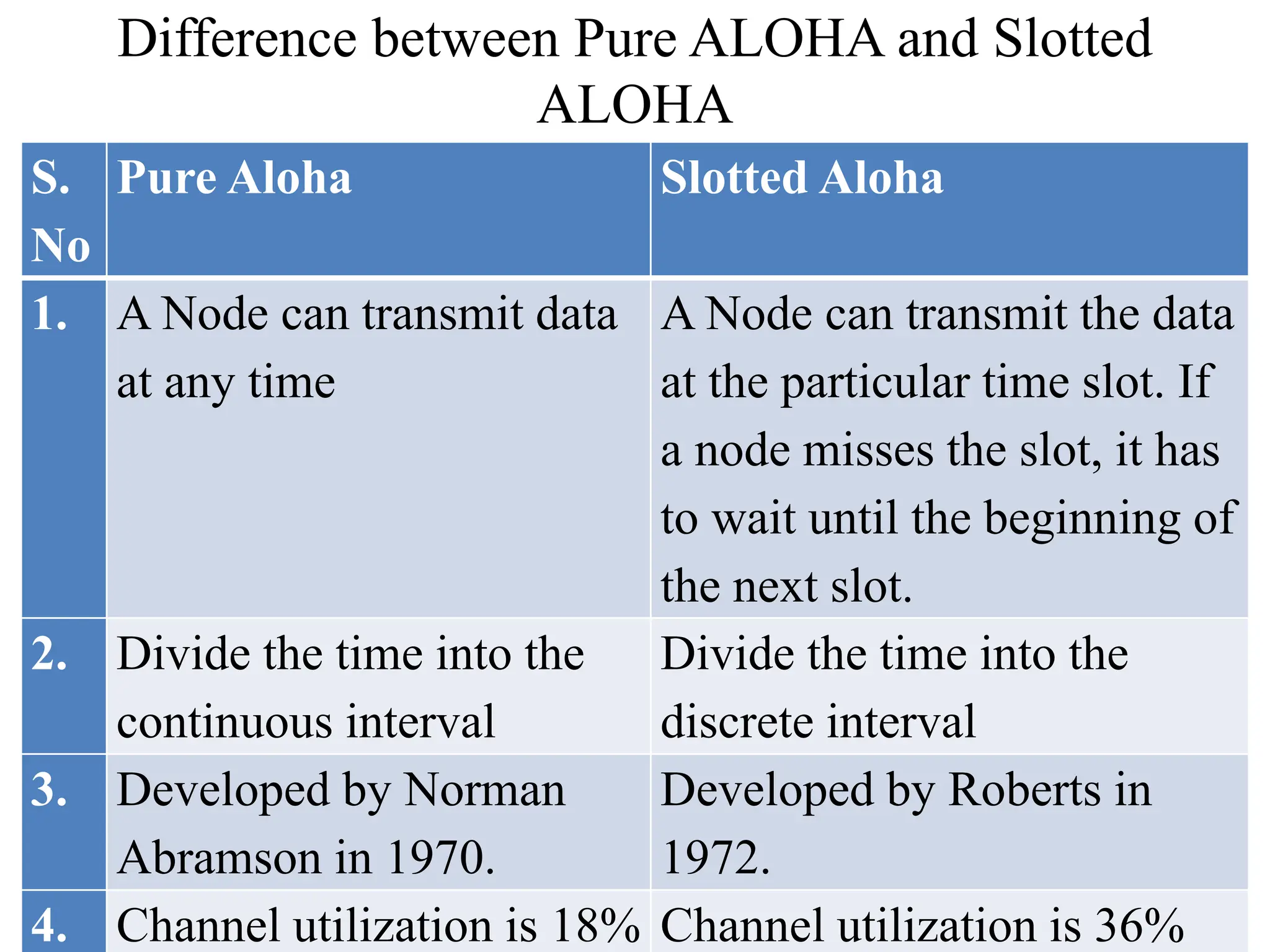
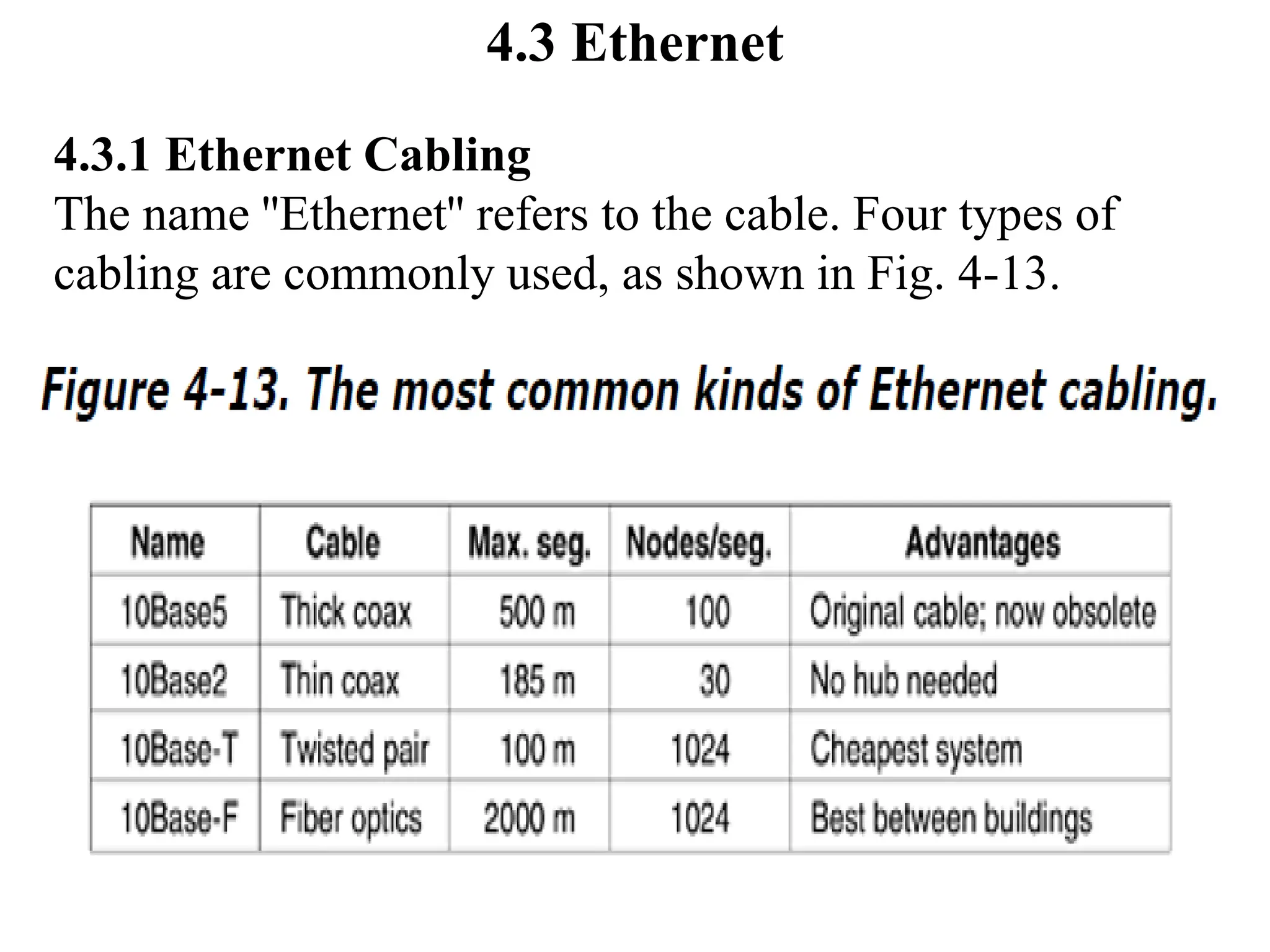
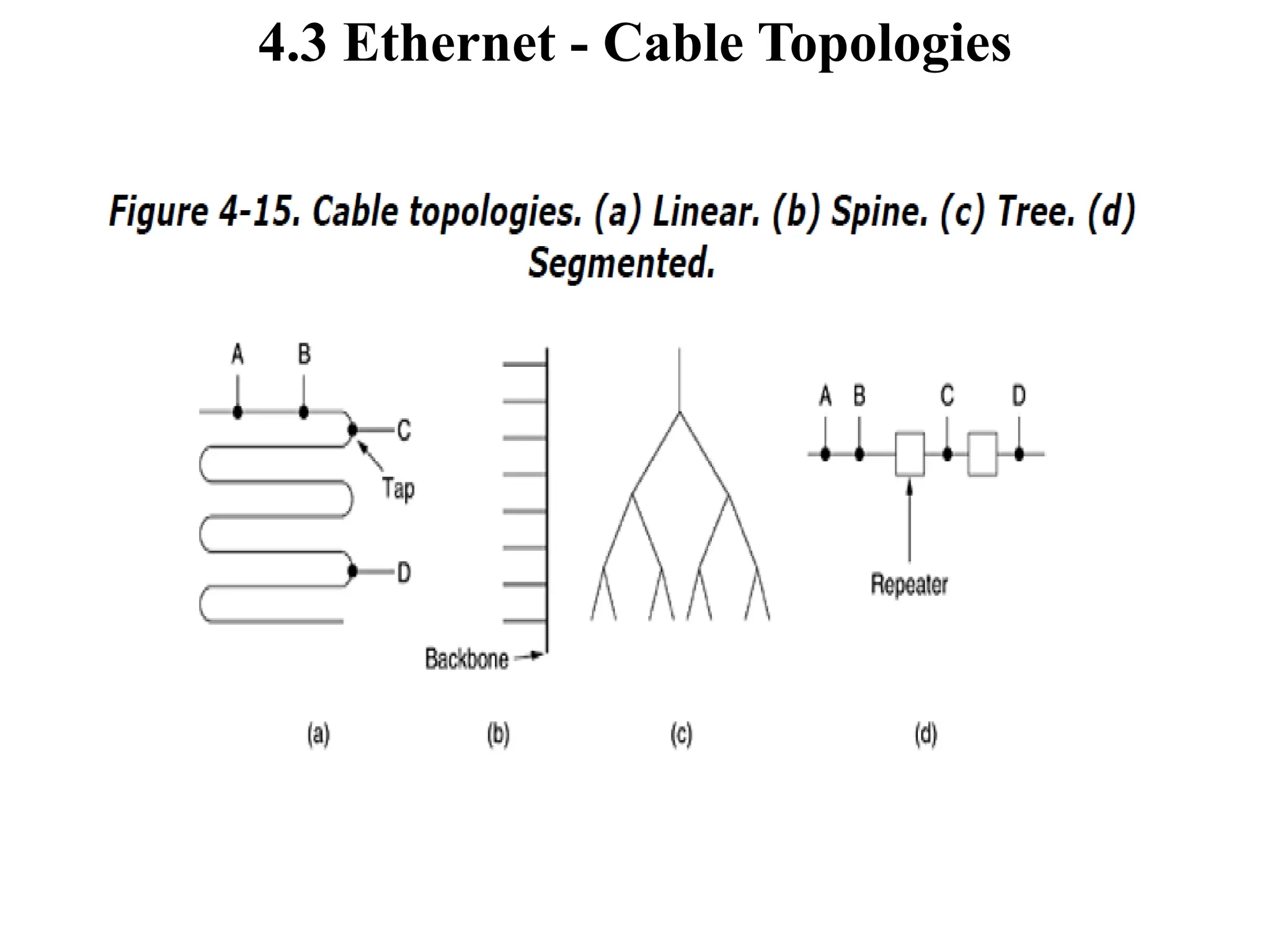
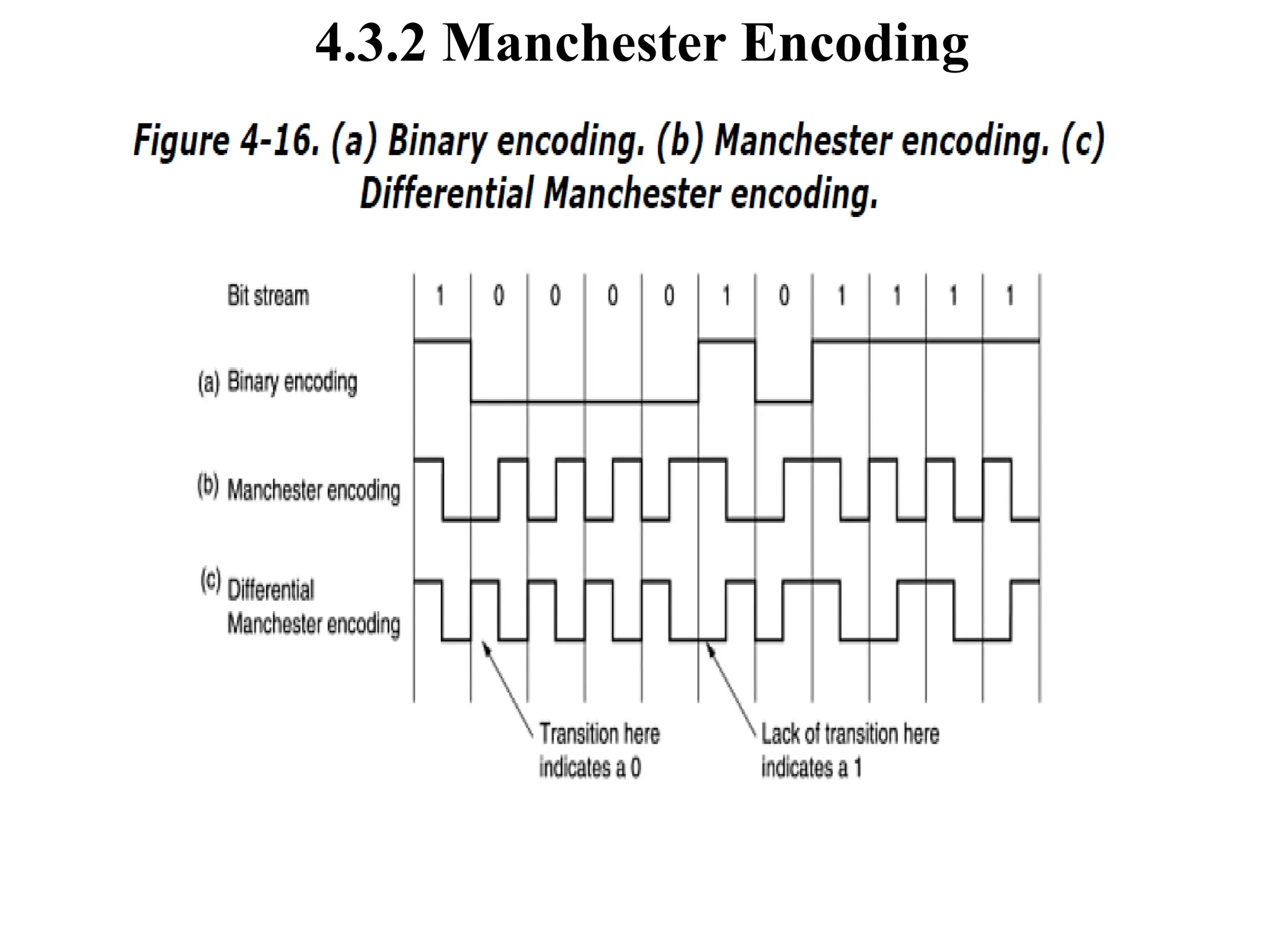
The document discusses the Medium Access Control (MAC) sublayer in data link layer protocols, detailing how broadcast networks manage channel access among competing users. It compares static and dynamic channel allocation methods, as well as various multiple access protocols, including ALOHA and Carrier Sense Multiple Access (CSMA), explaining their collision handling and efficiency metrics. Additionally, it highlights ethernet cabling types and encoding techniques used in data communication networks.