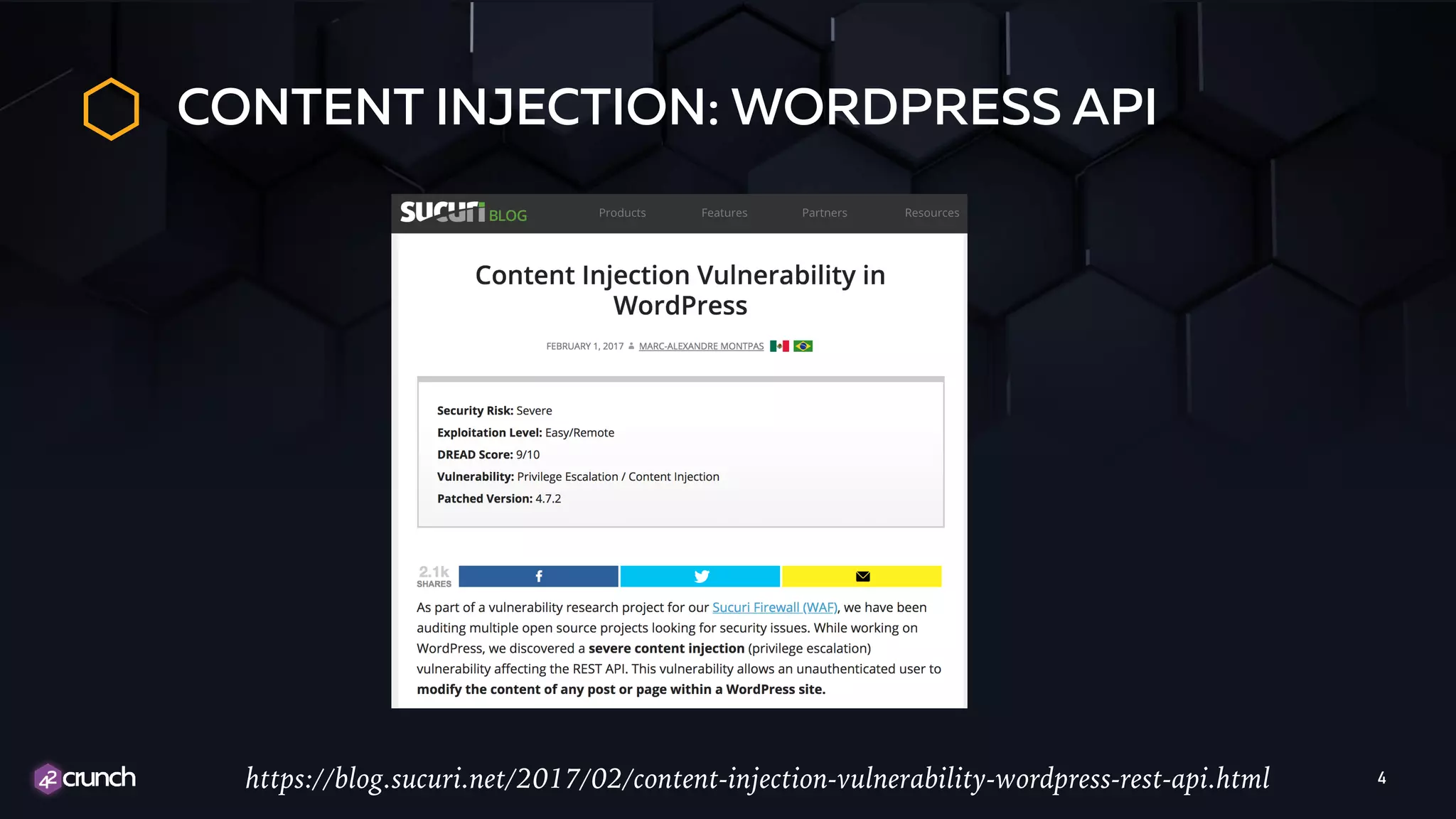
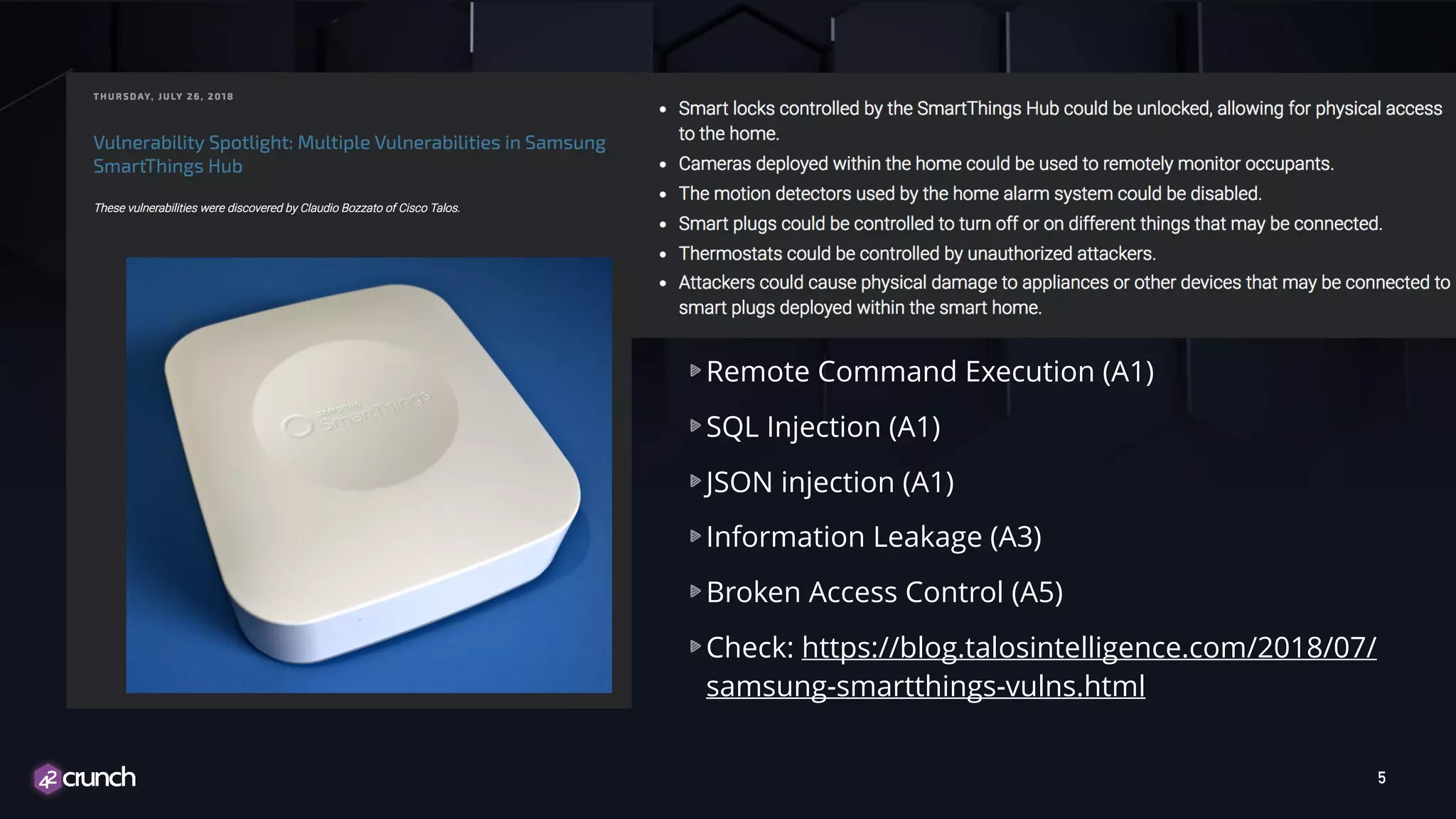
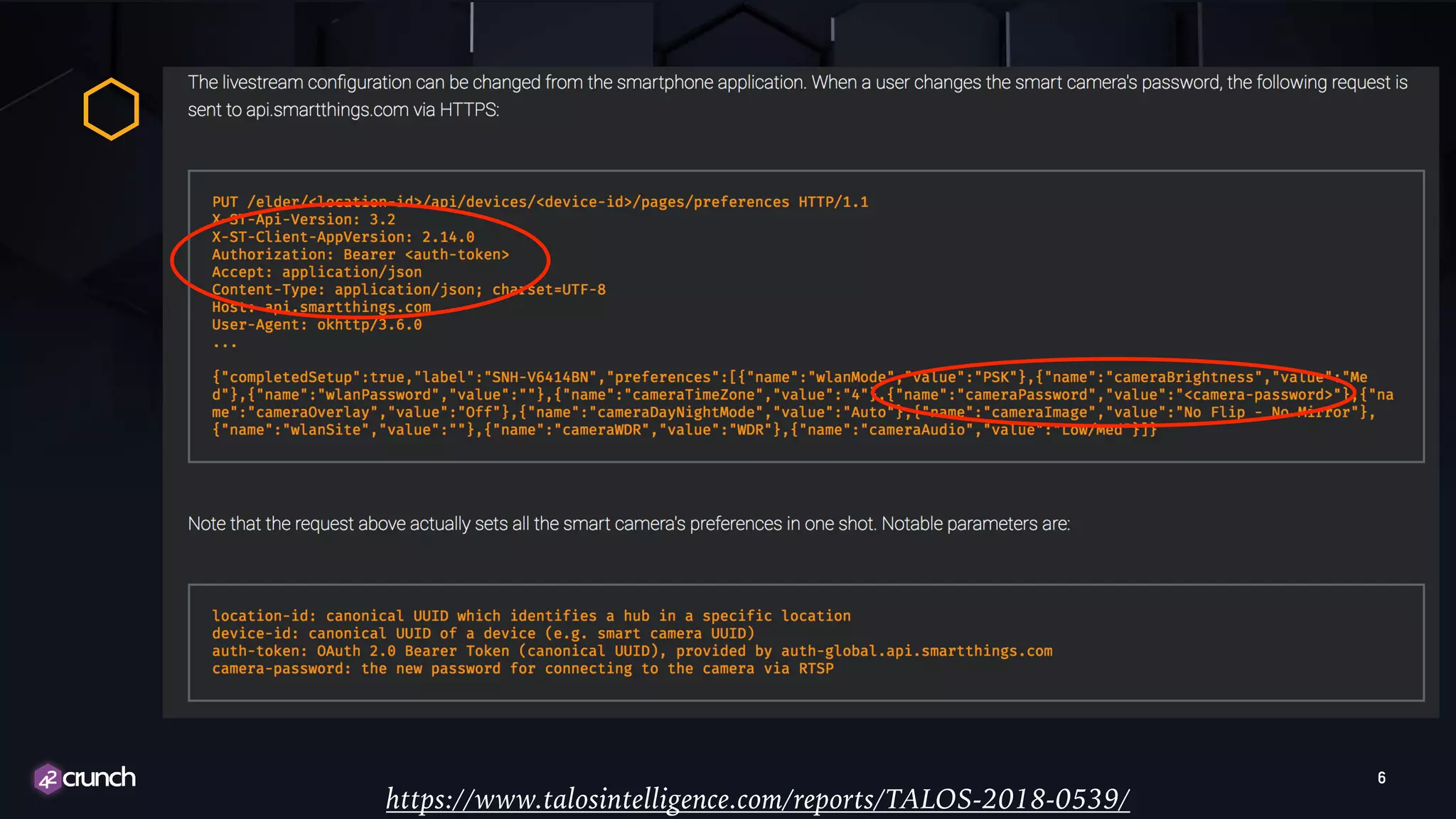
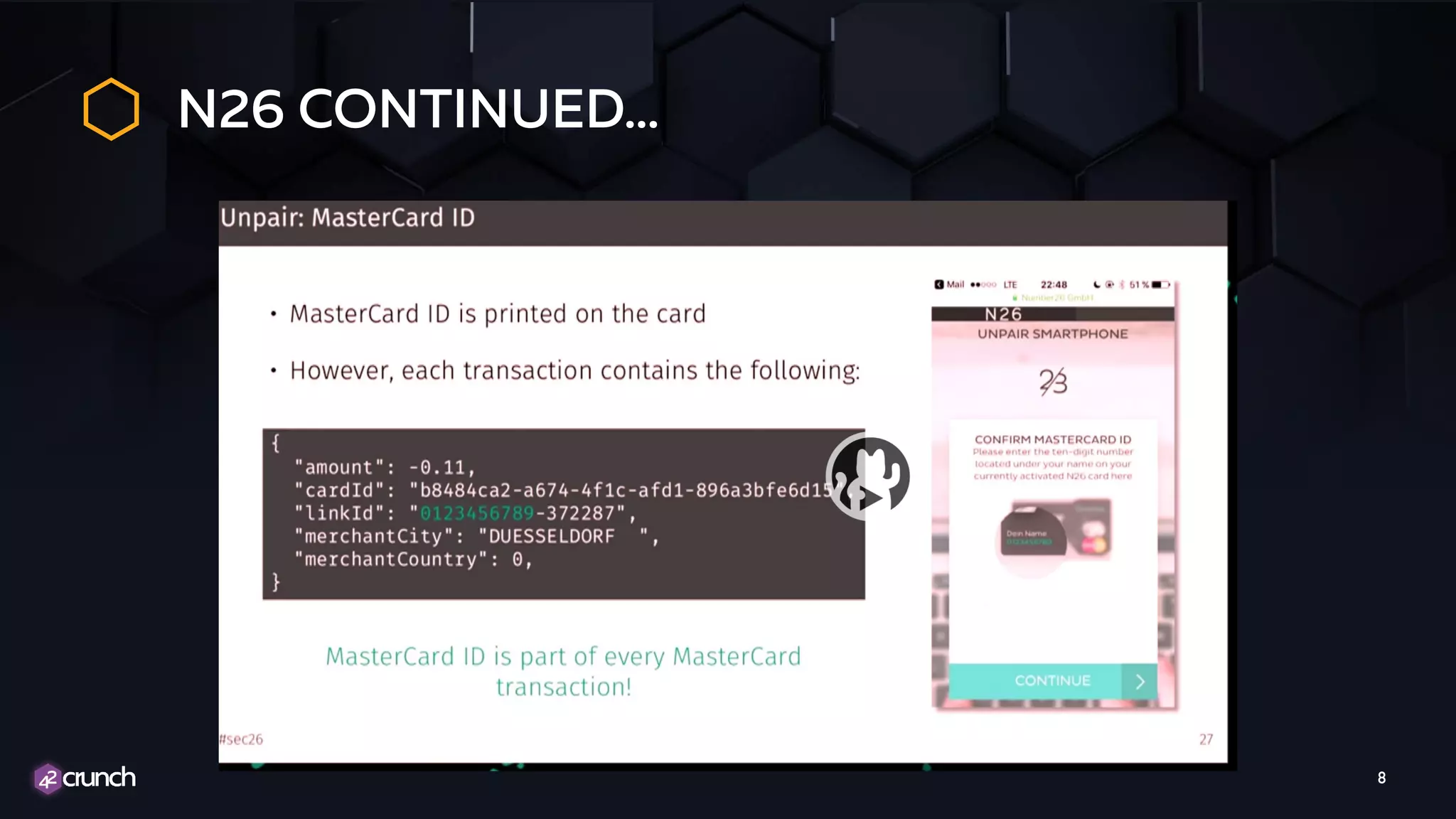
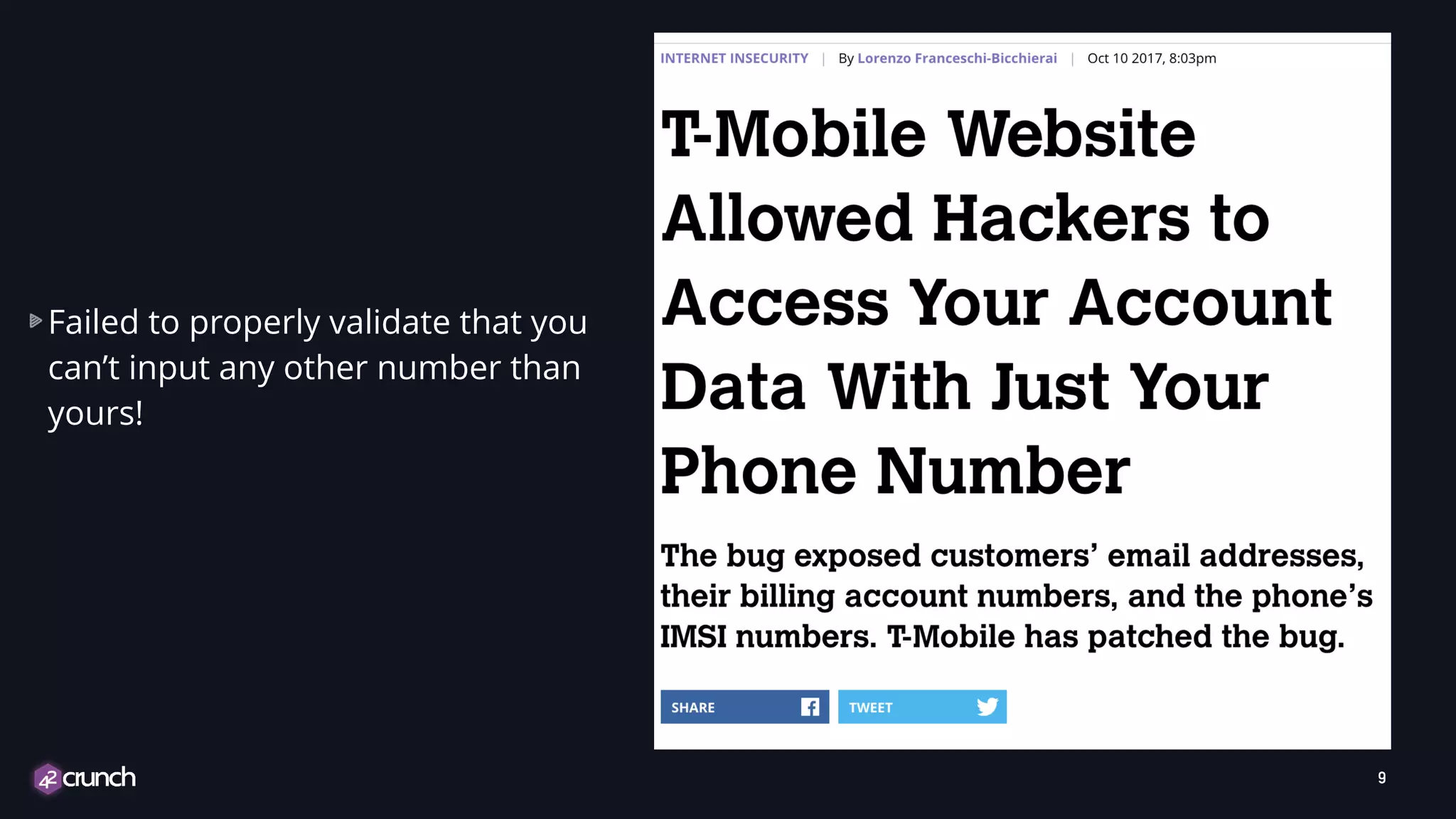
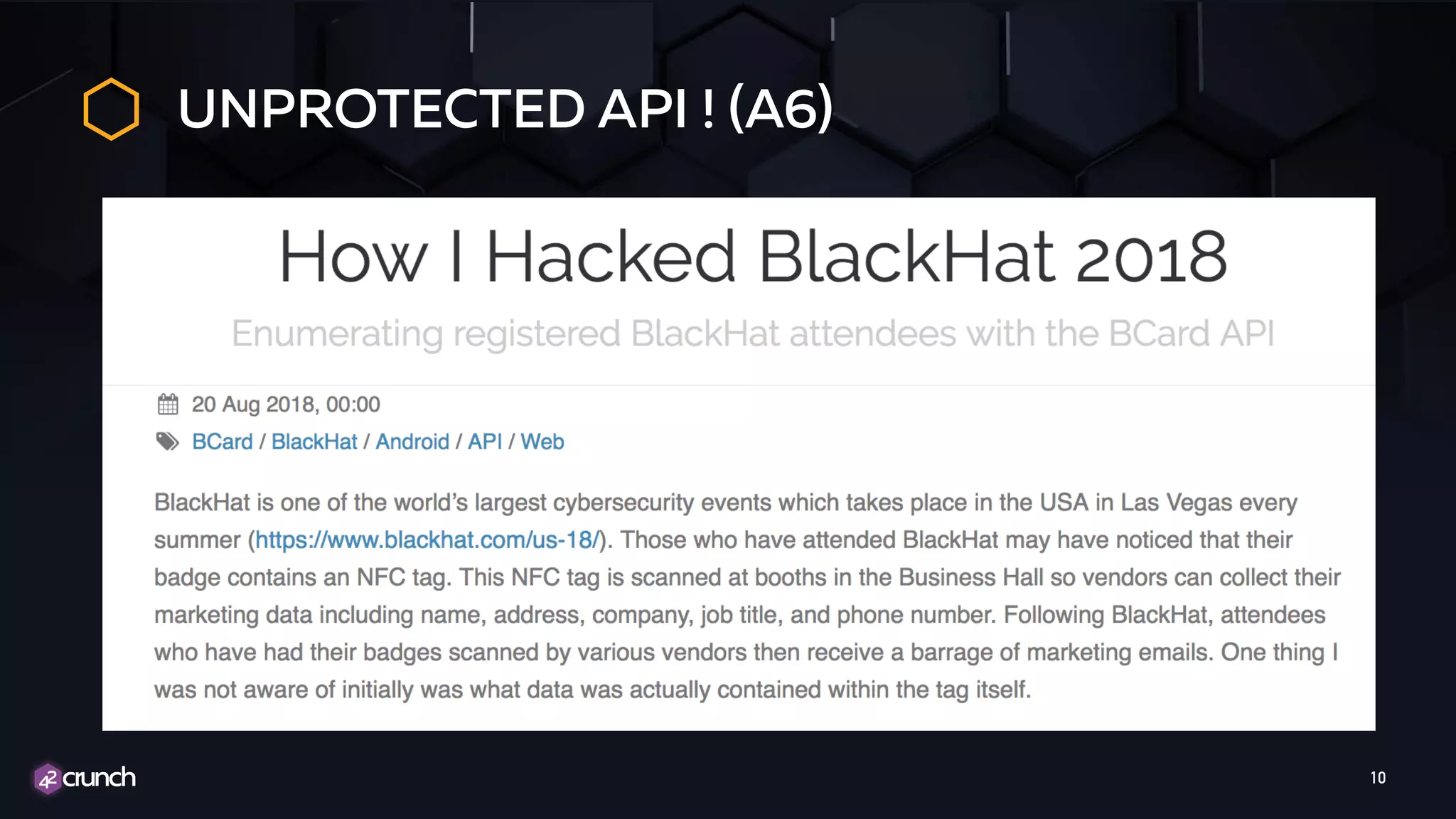
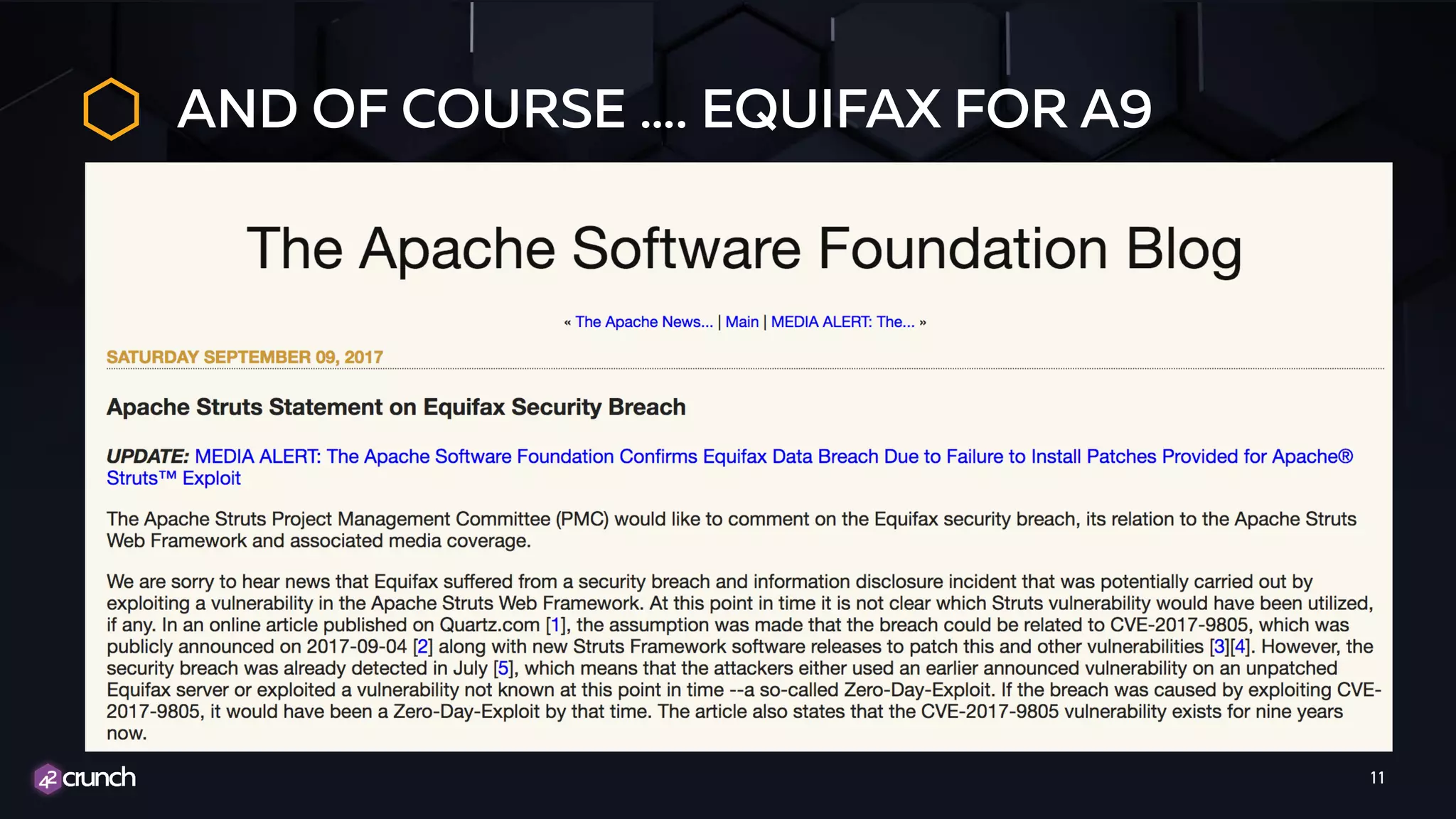
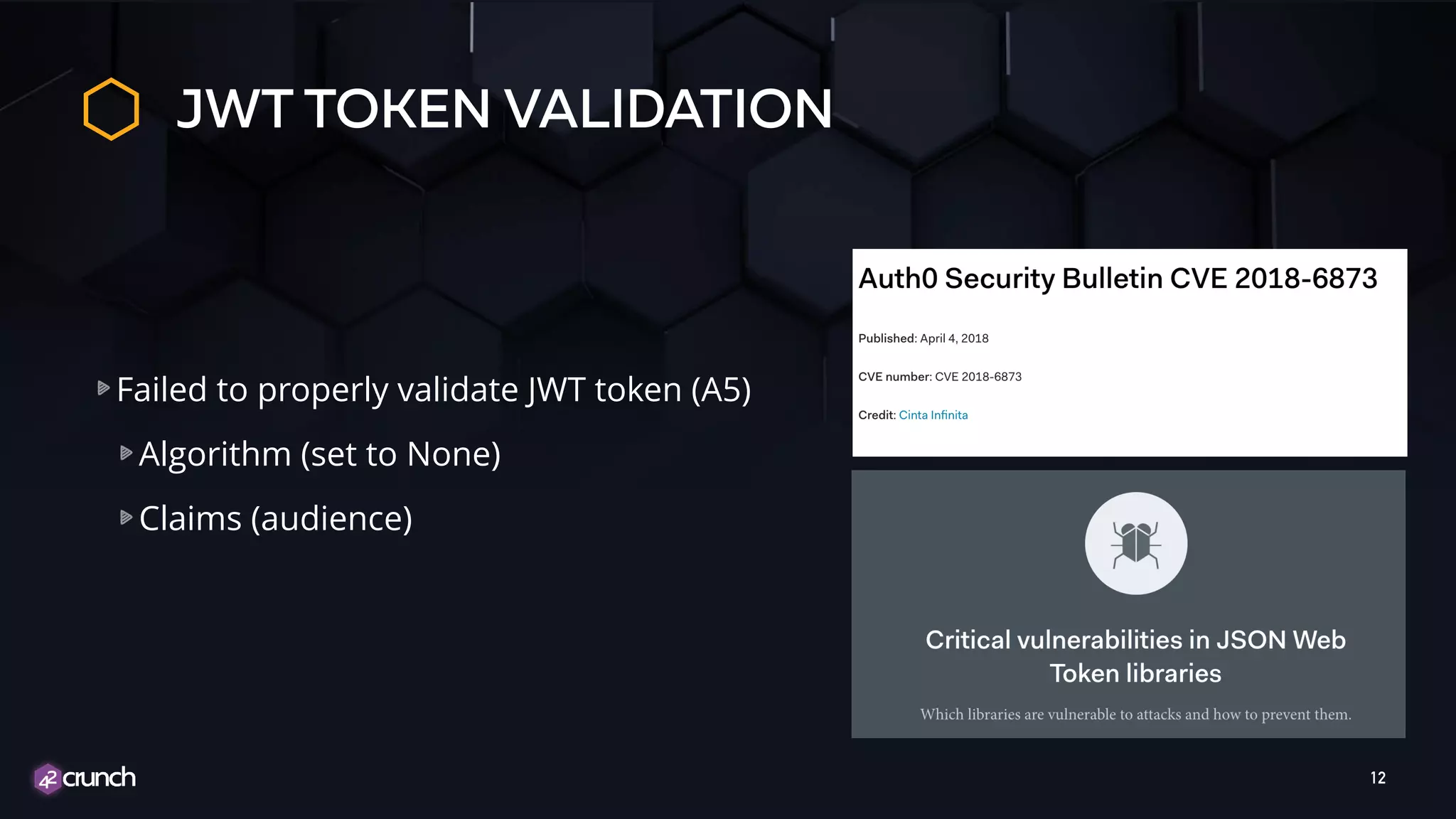
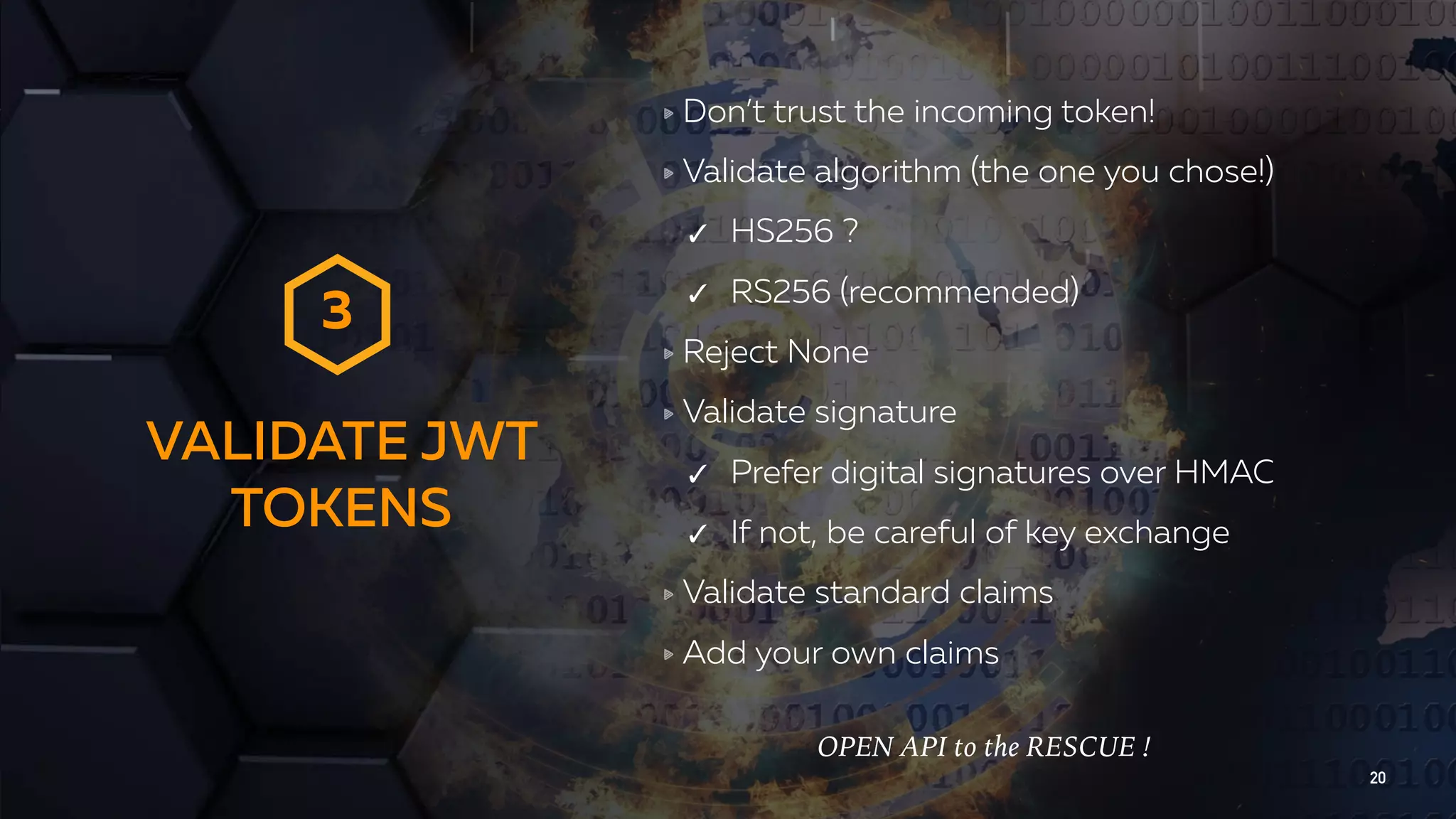
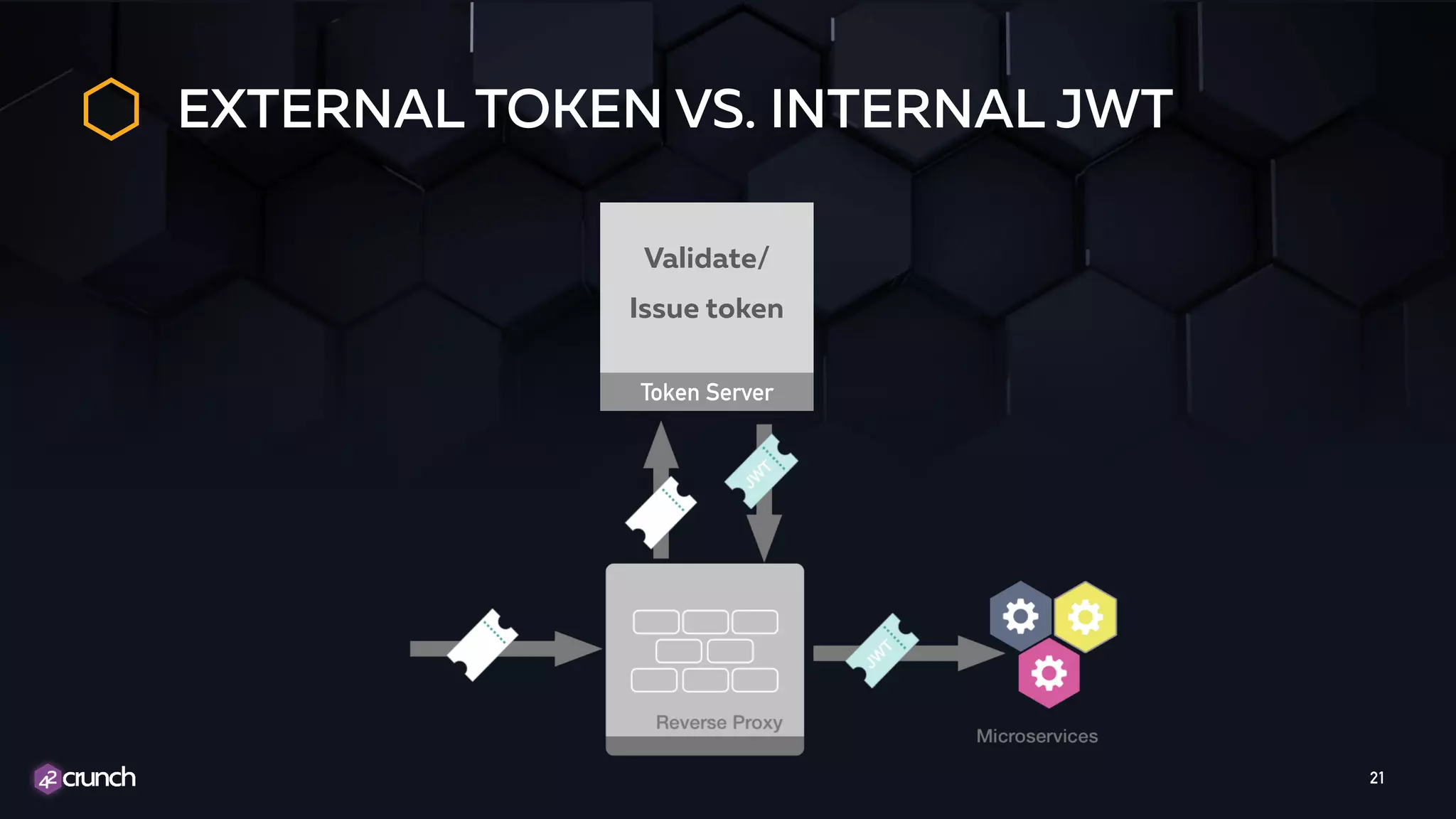
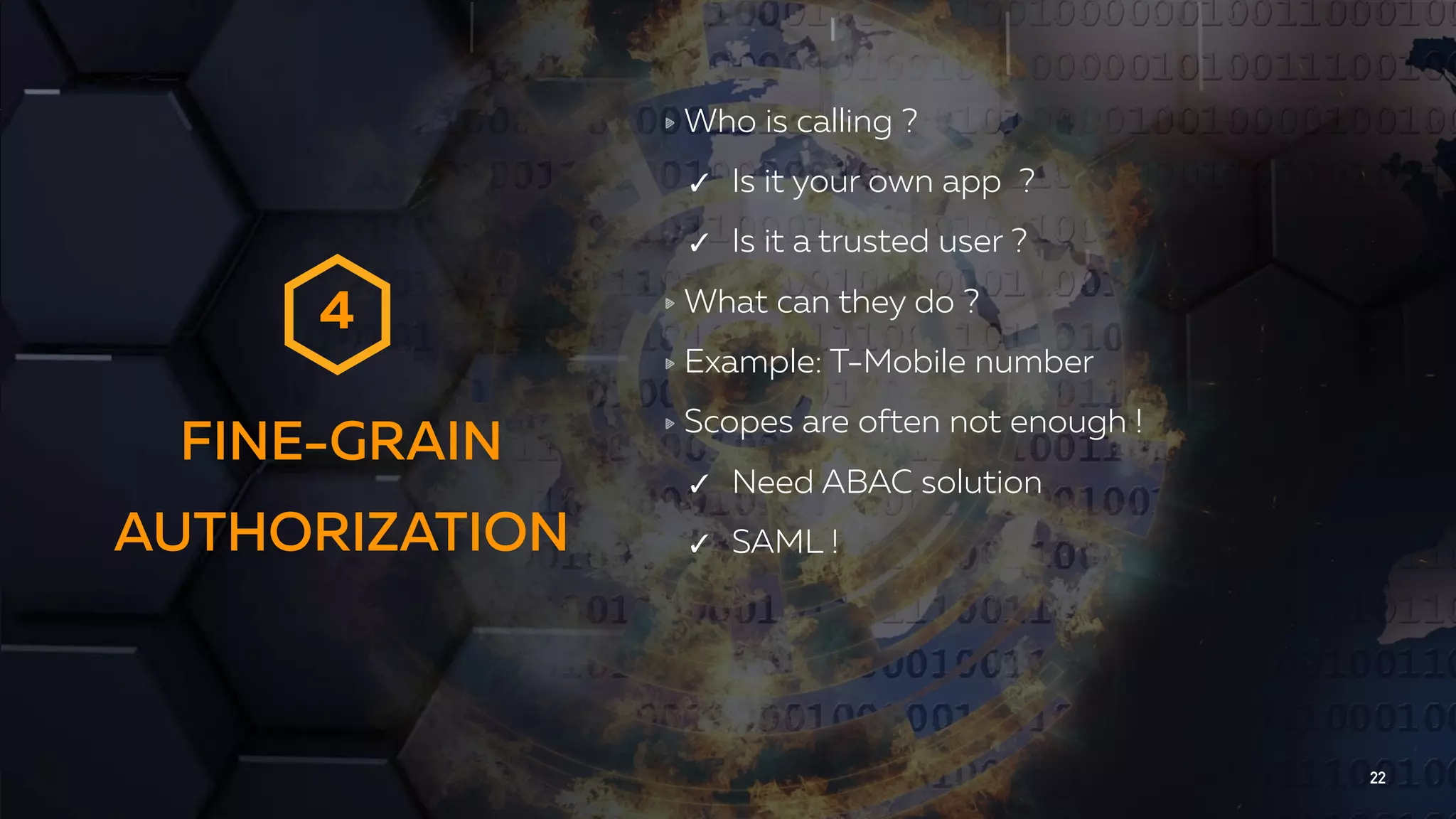
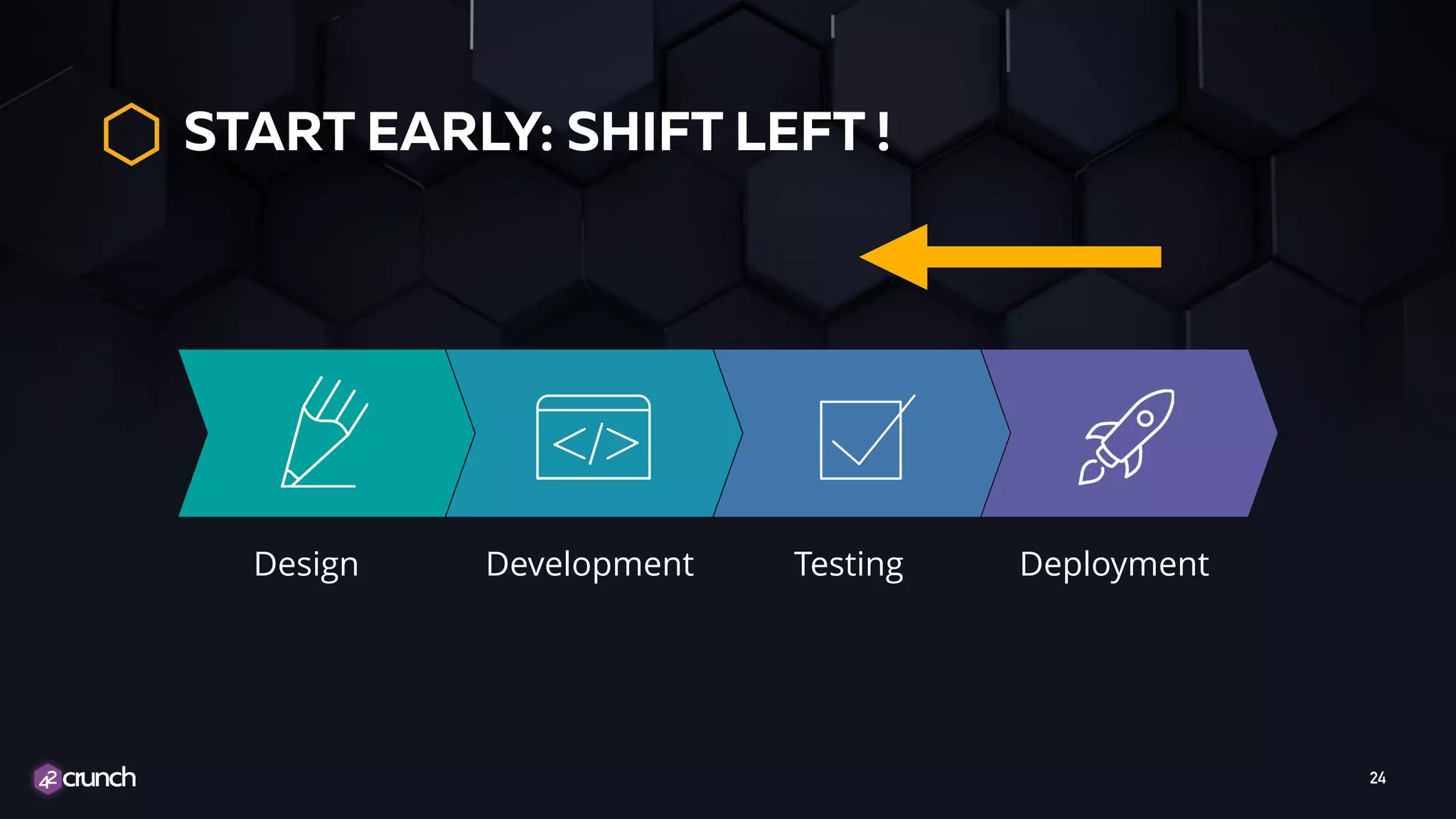
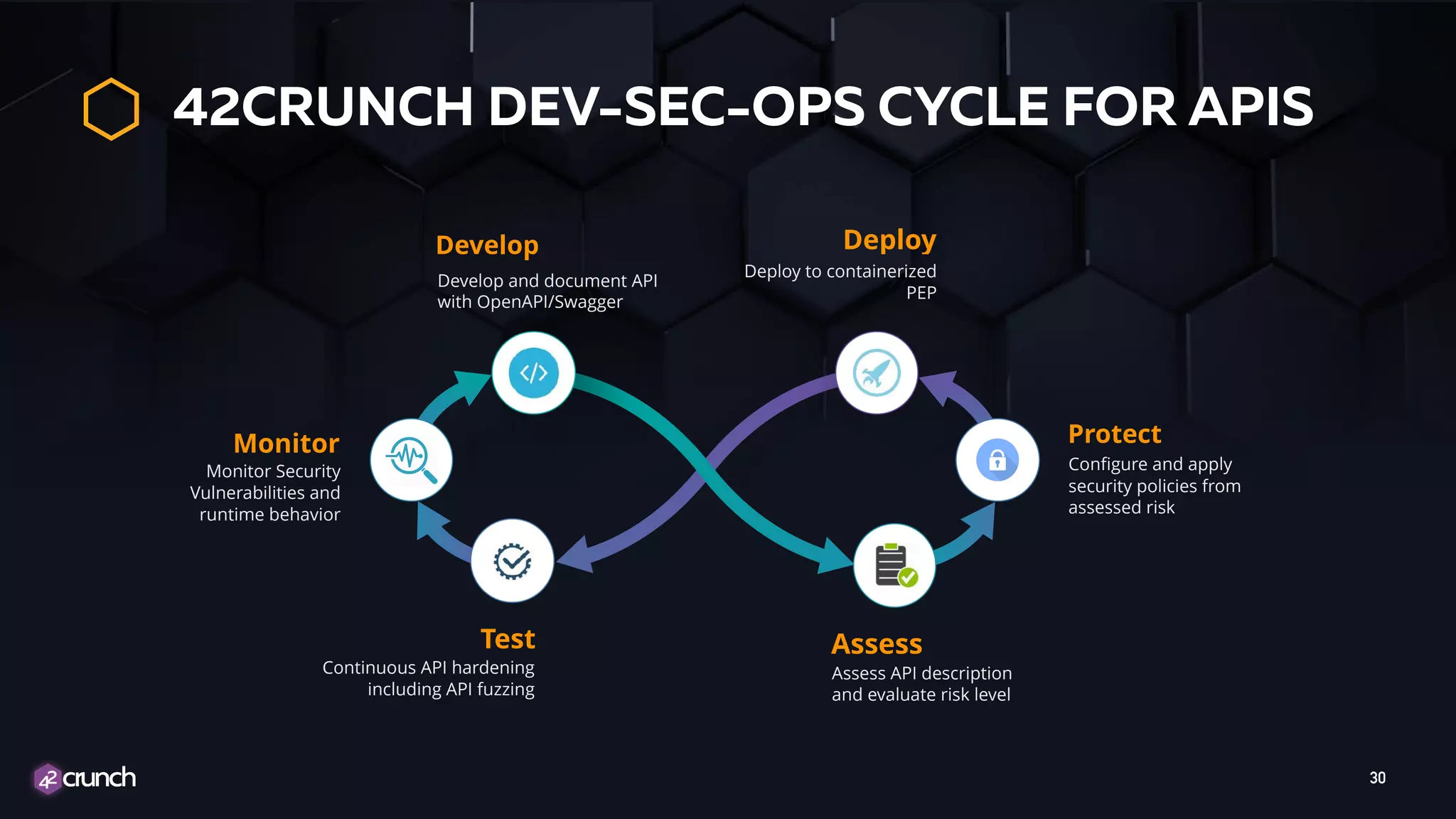
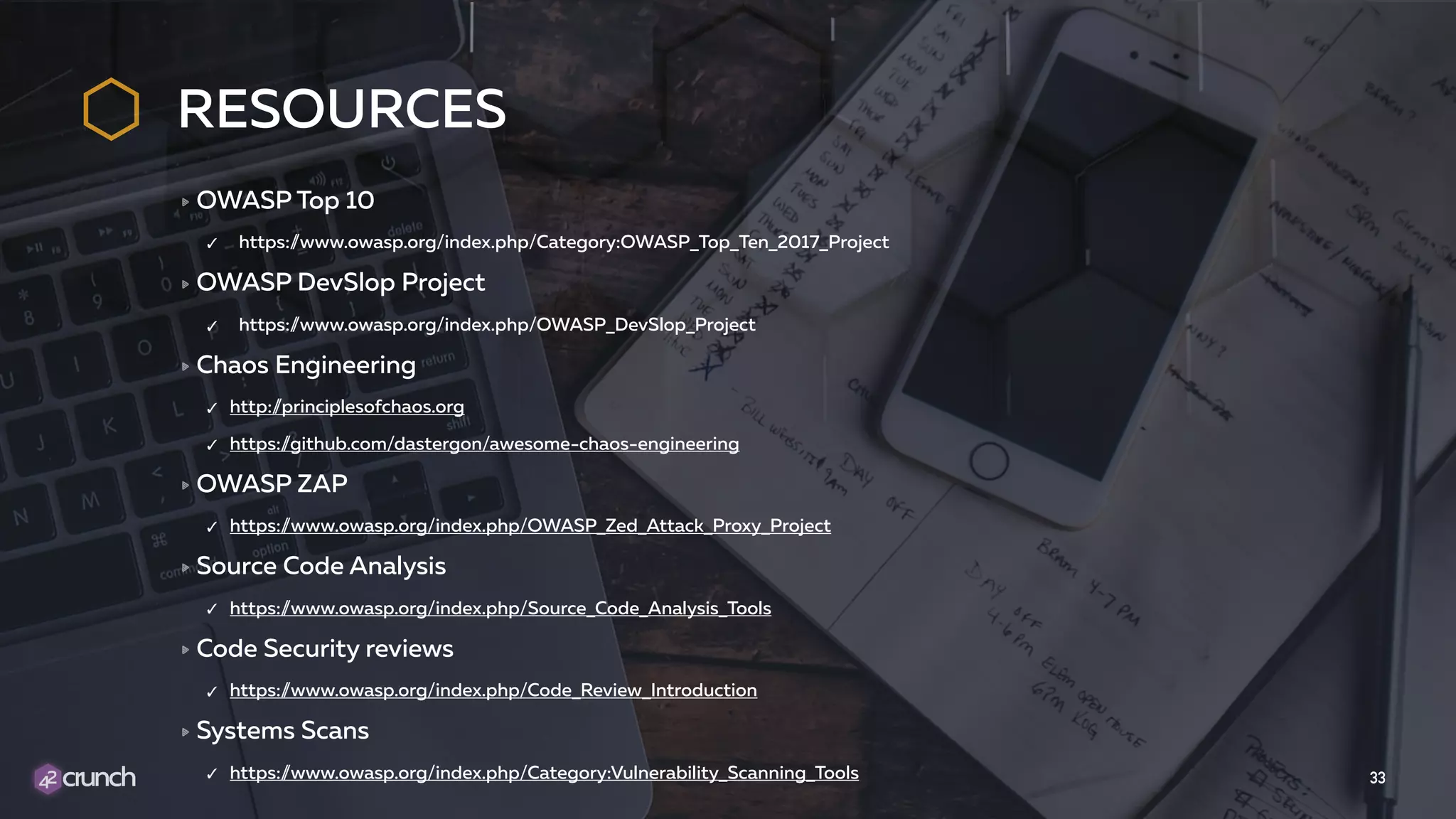
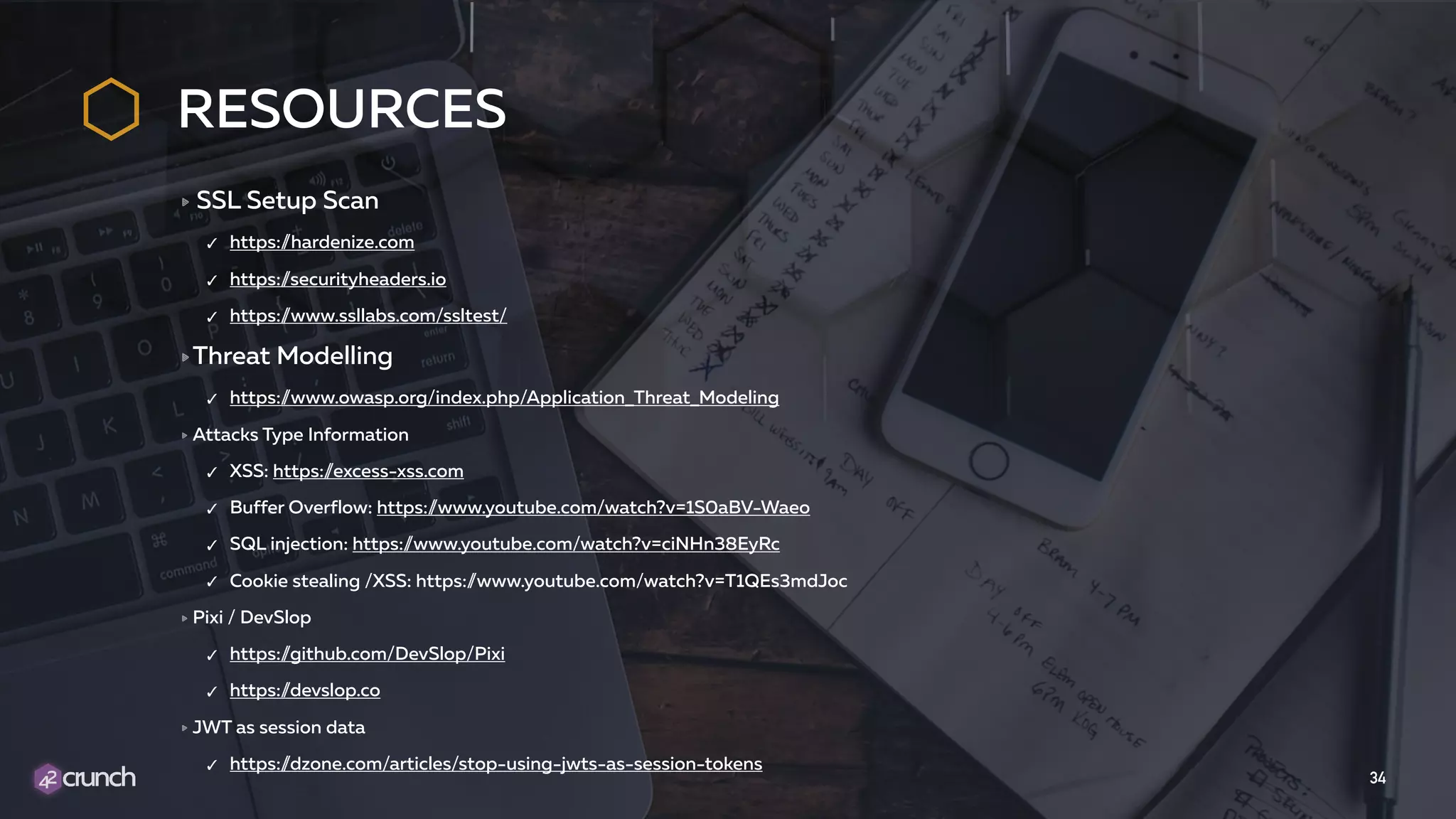
The document discusses the importance of API security and presents the OWASP Top 10 security risks from 2010 to 2017. It emphasizes automated approaches to API security, including input validation, monitoring, and protecting APIs through security measures like API gateways. Key recommendations include ongoing vulnerability scanning, proper JWT token validation, and implementing a DevSecOps cycle for continuous improvement of API security.