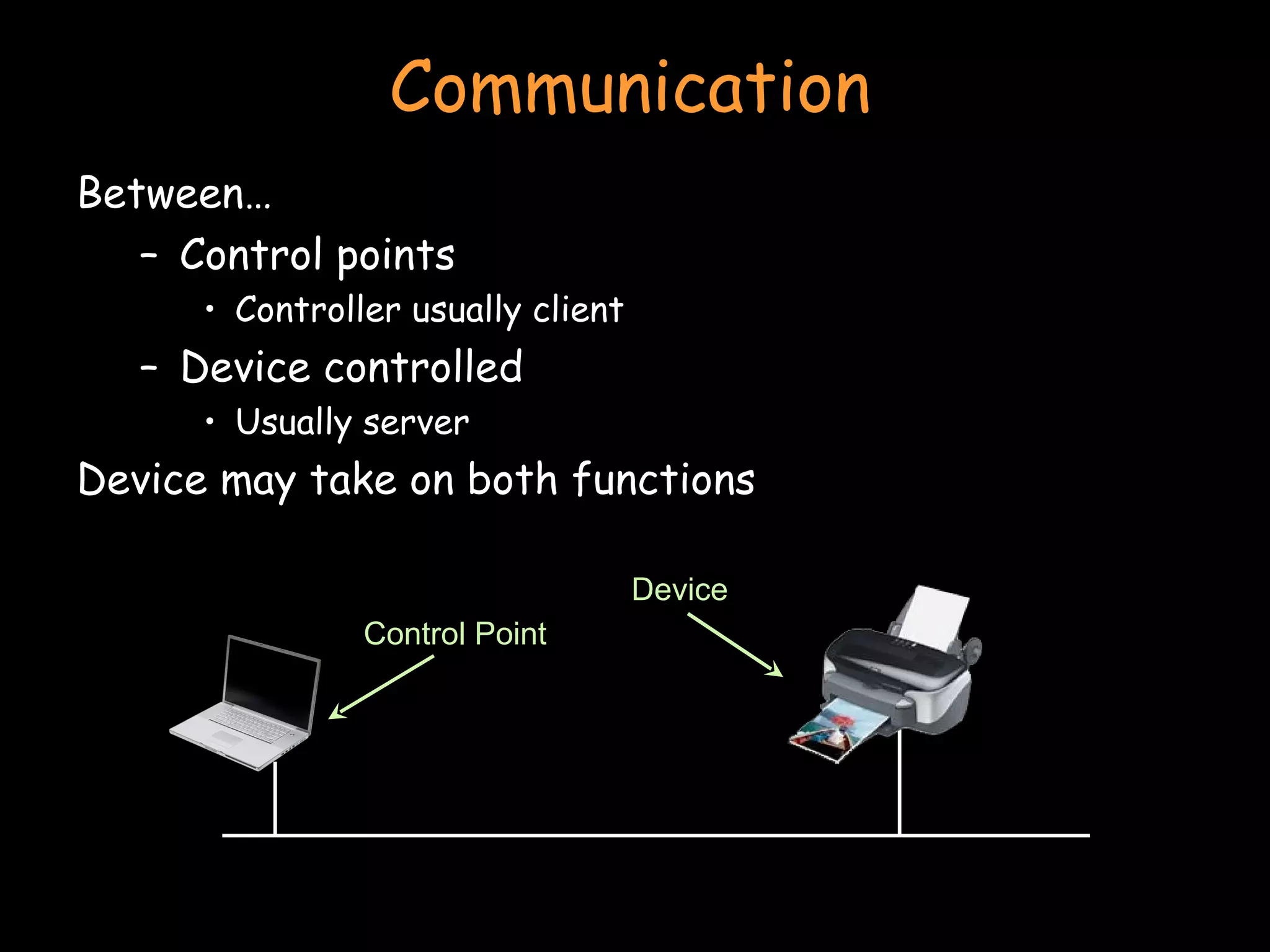
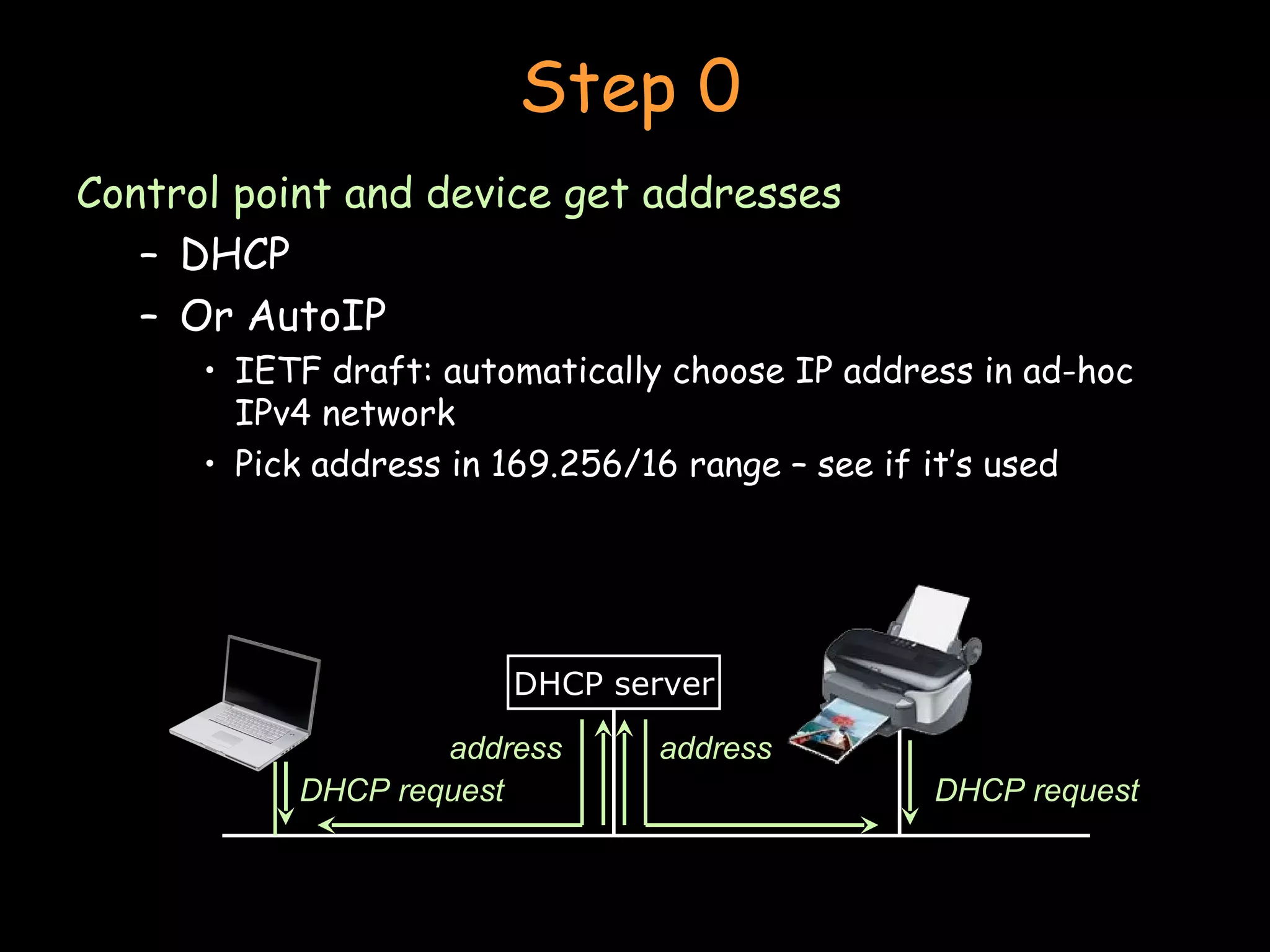
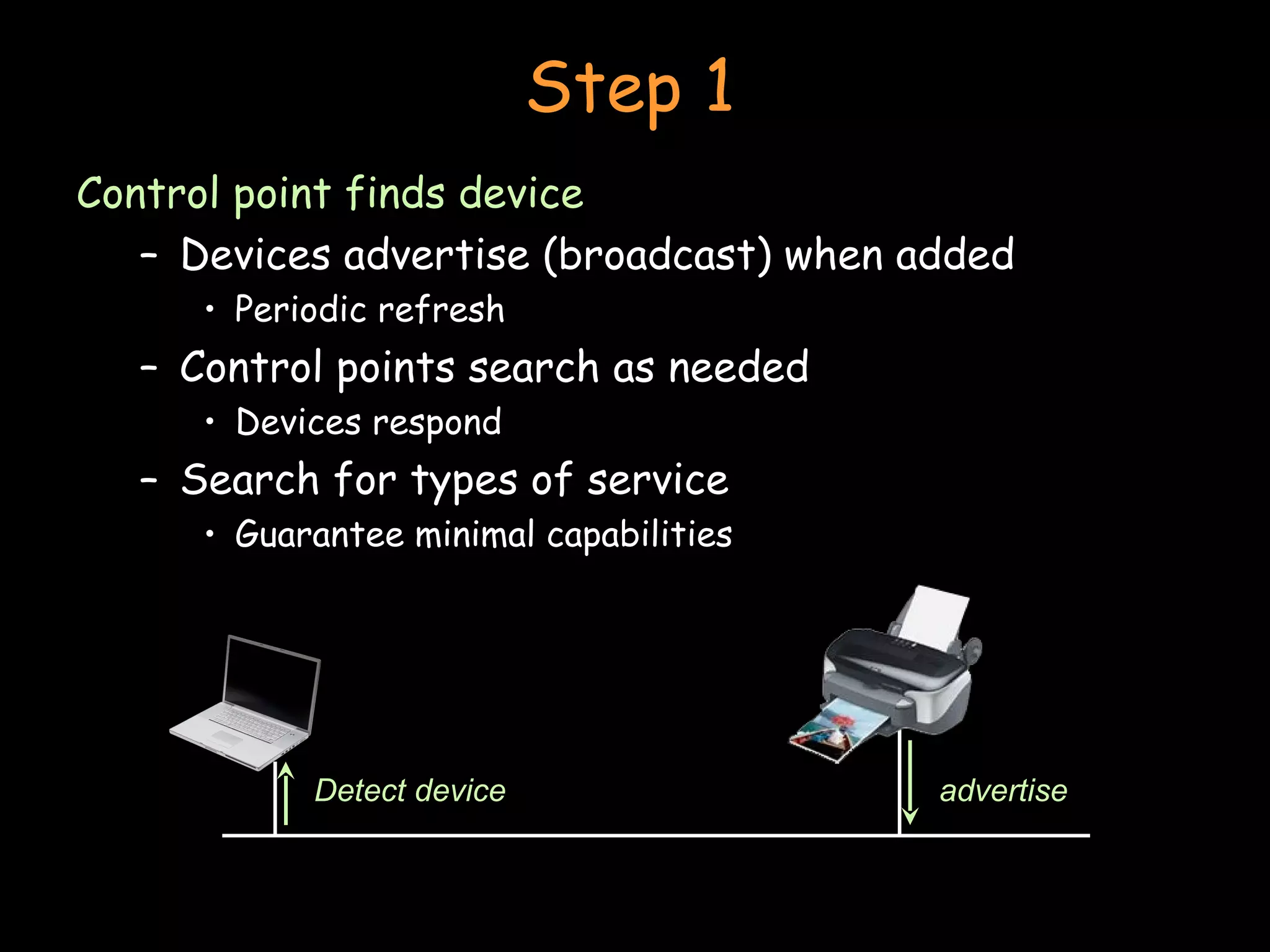
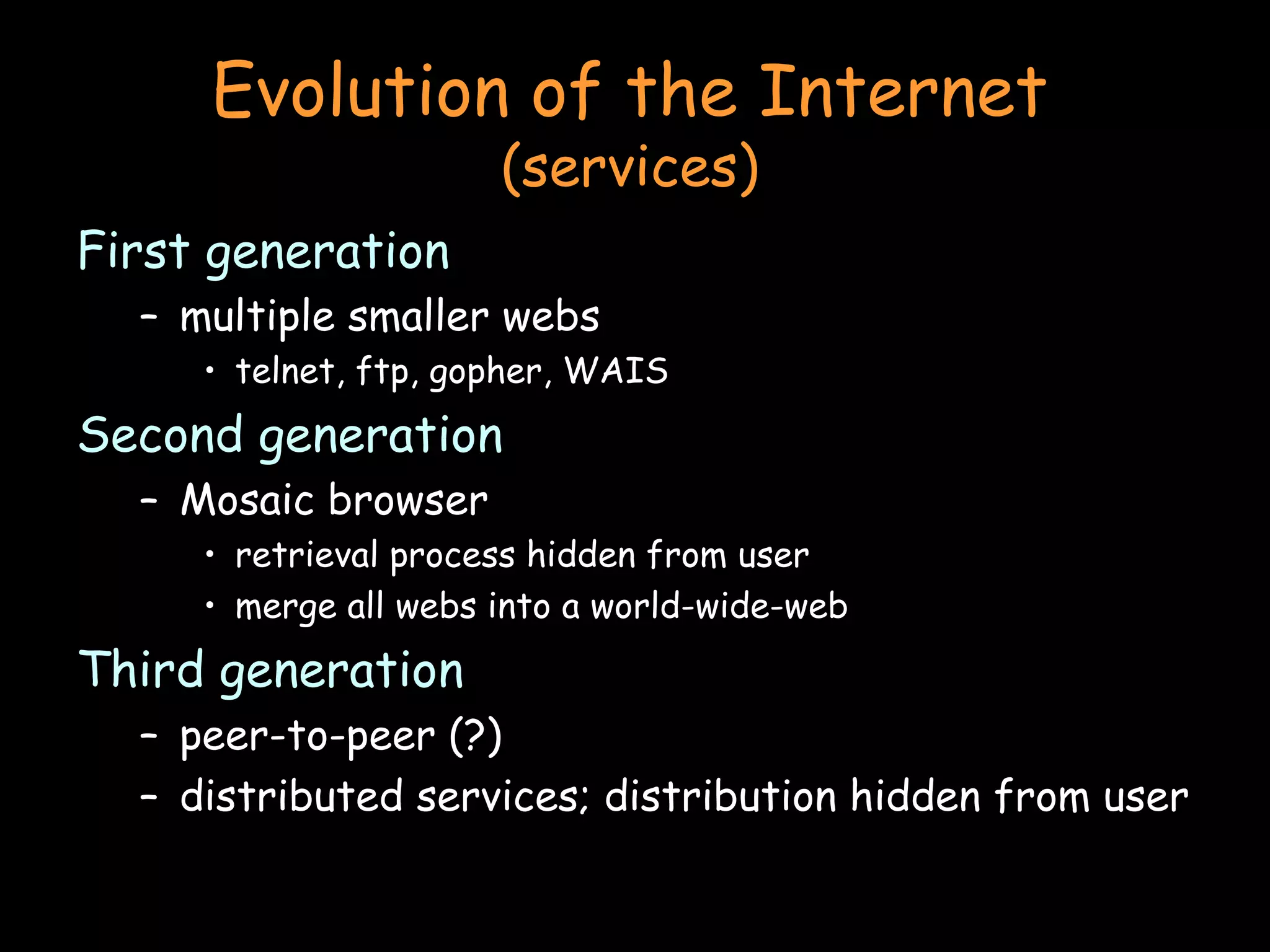
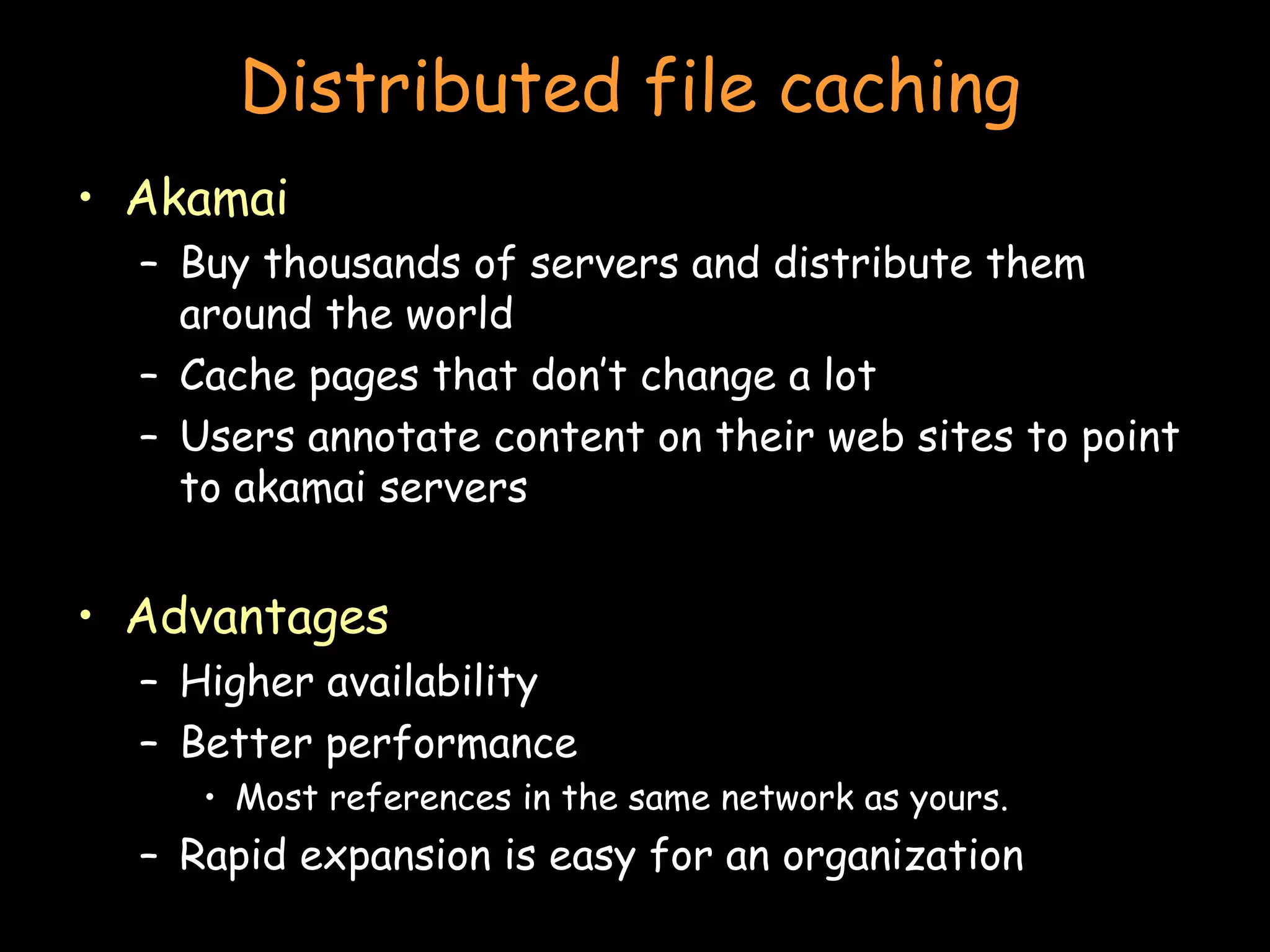
The document discusses peer-to-peer and serverless networking models. It describes how clients in peer-to-peer networks can provide unused storage and computing resources. Examples of current peer-to-peer file sharing systems like BitTorrent are explained. The benefits of distributed and grid computing systems are discussed. Issues around security, privacy, and standards in peer-to-peer networks are also covered.
![Serverless (peer-to-peer) networking Paul Krzyzanowski [email_address] [email_address] Distributed Systems Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License.](https://image.slidesharecdn.com/25-serverless-090902071054-phpapp02/75/Serverless-Distributed-computing-1-2048.jpg)







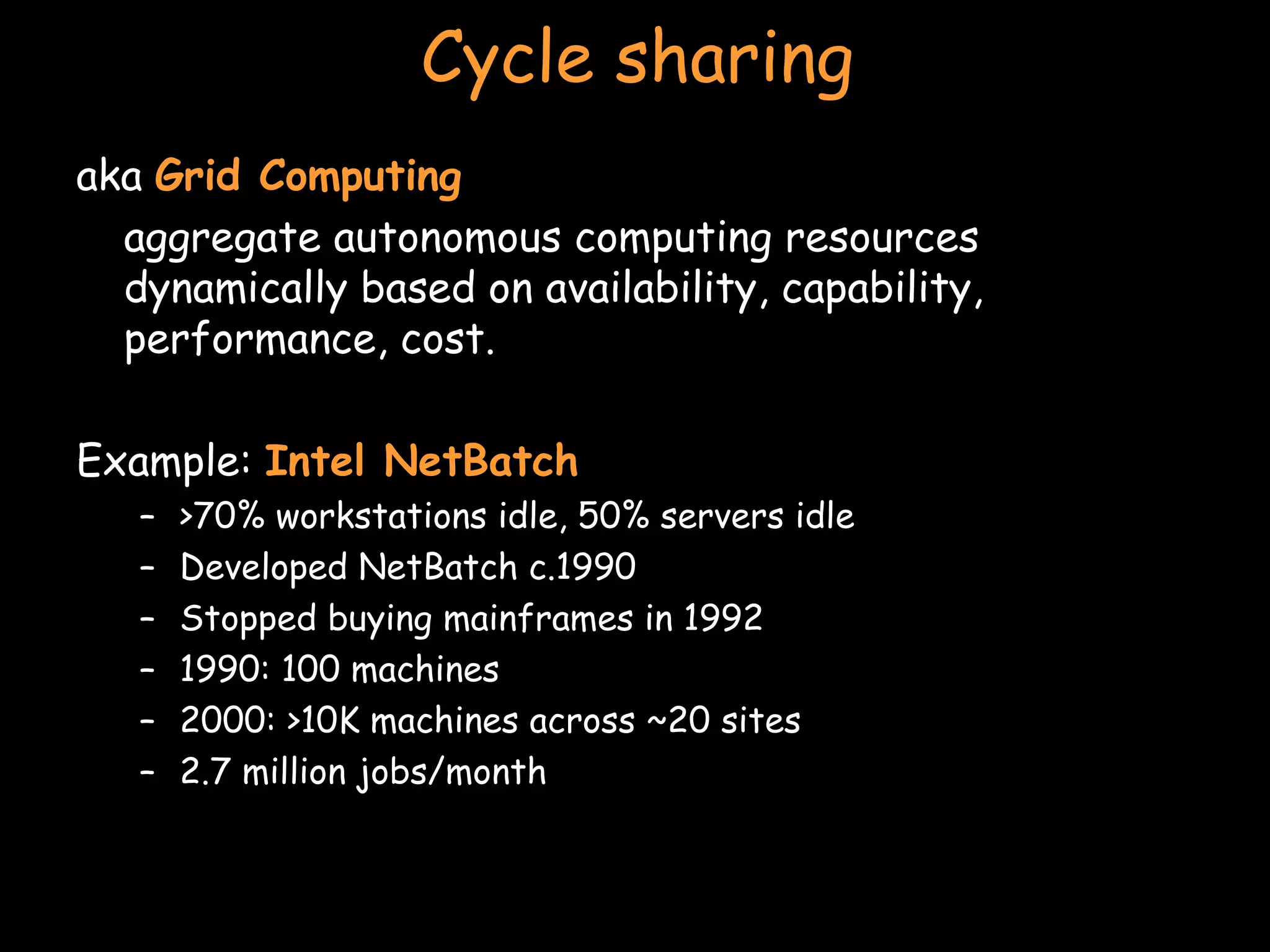
![Cycle sharing Example: [email_address] Scan radio telescope images Chunks of data sent to client in suspend mode (runs as screensaver) Data processed by clients when not in use and results returned to server](https://image.slidesharecdn.com/25-serverless-090902071054-phpapp02/75/Serverless-Distributed-computing-12-2048.jpg)

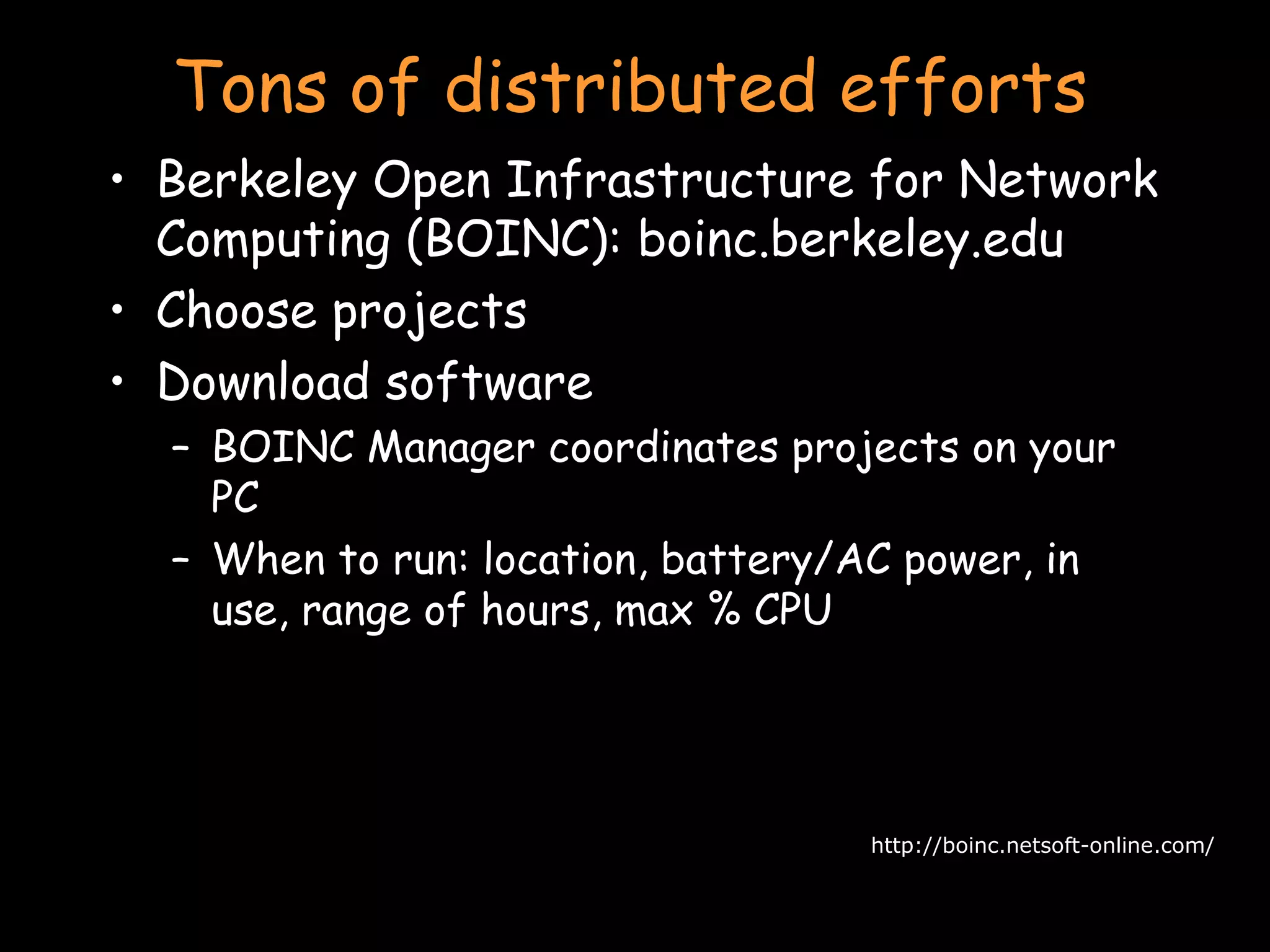
![Tons of distributed efforts [email_address] Climateprediction.net [email_address] [email_address] [email_address] BBC Climate Change Experiment [email_address] World Community Grid SIMAP SZTAKI Desktop Grid PrimeGrid uFluids MalariaControl and lots more… http://boinc.netsoft-online.com/](https://image.slidesharecdn.com/25-serverless-090902071054-phpapp02/75/Serverless-Distributed-computing-15-2048.jpg)