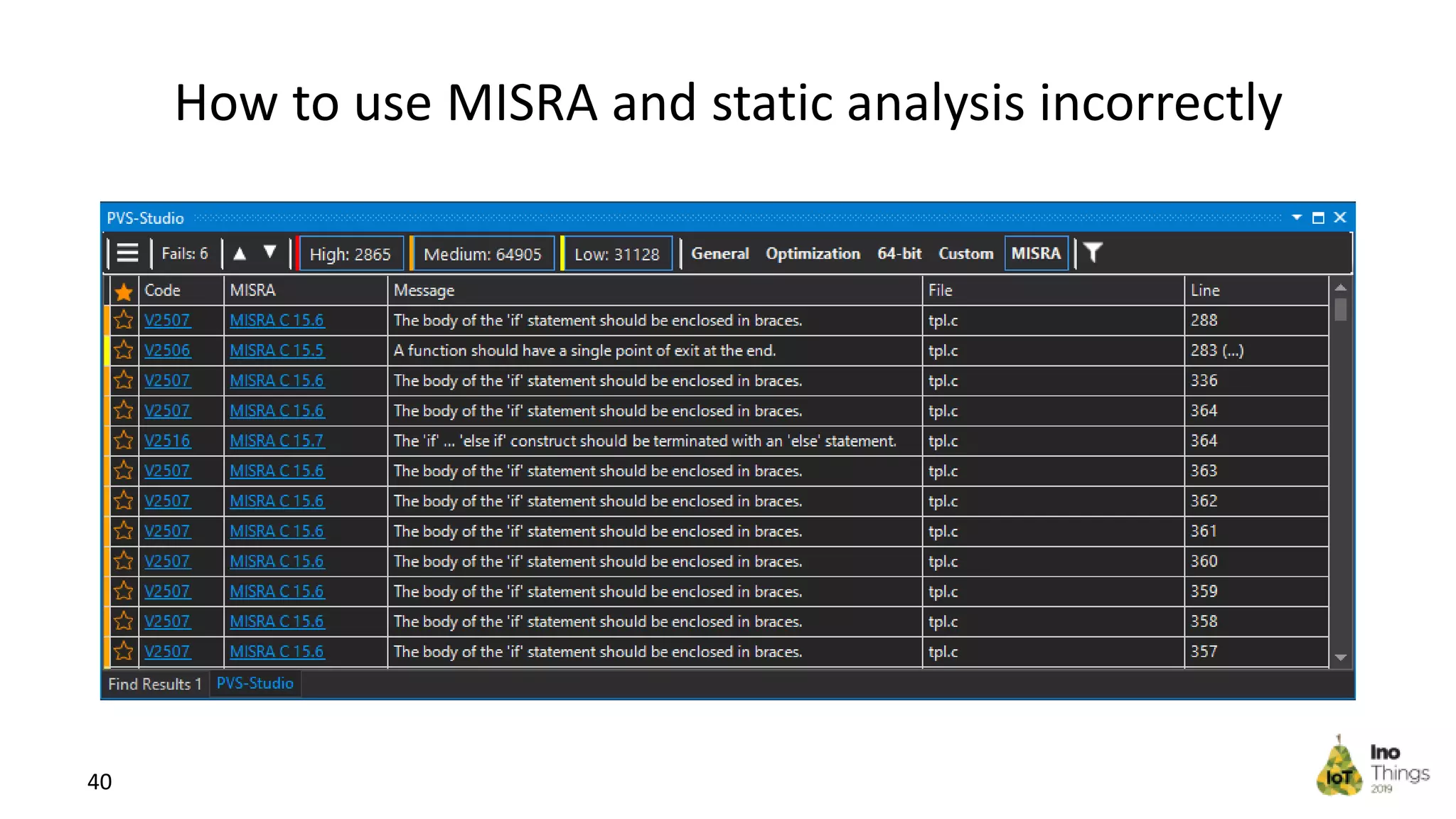
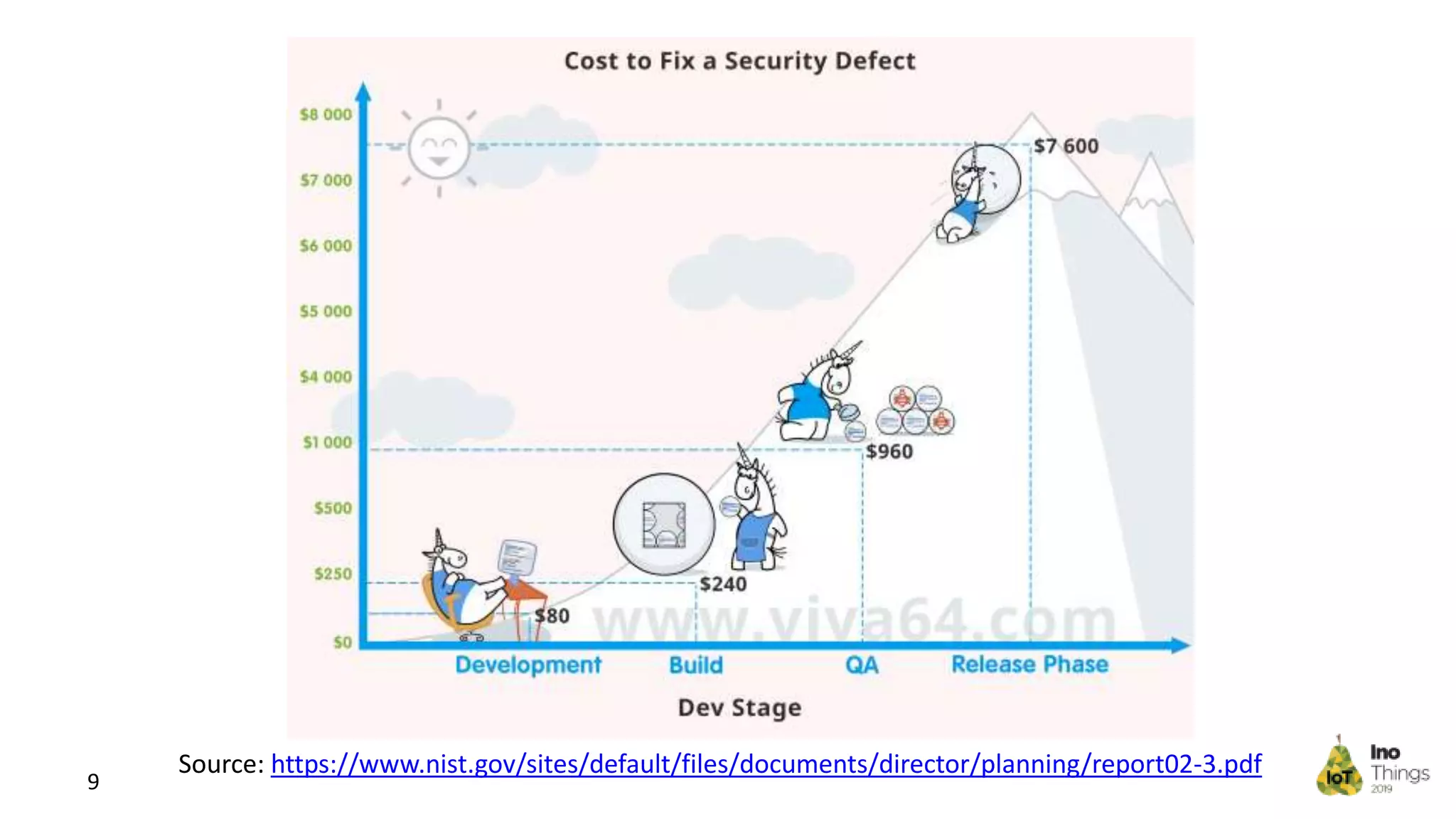
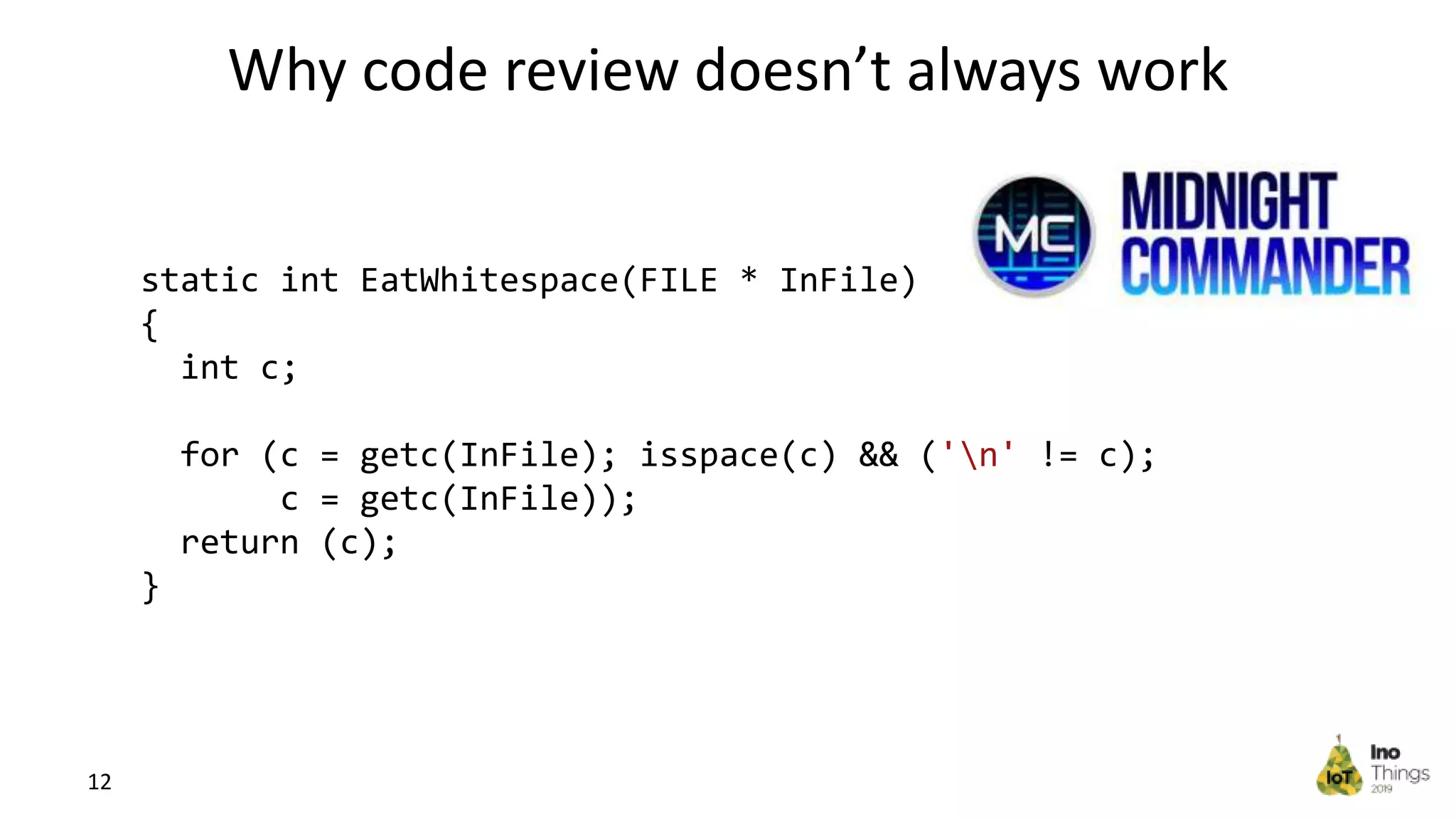
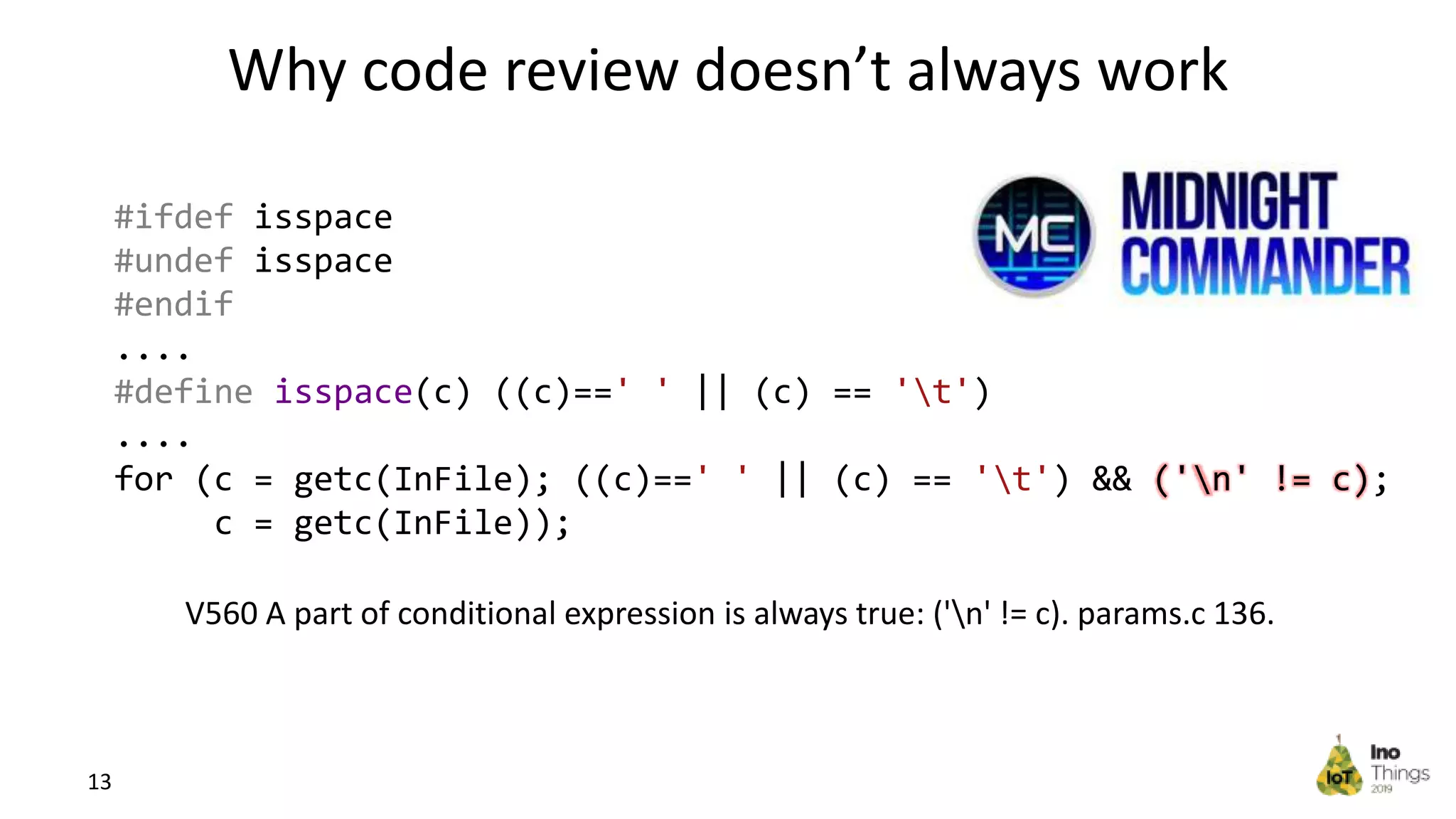
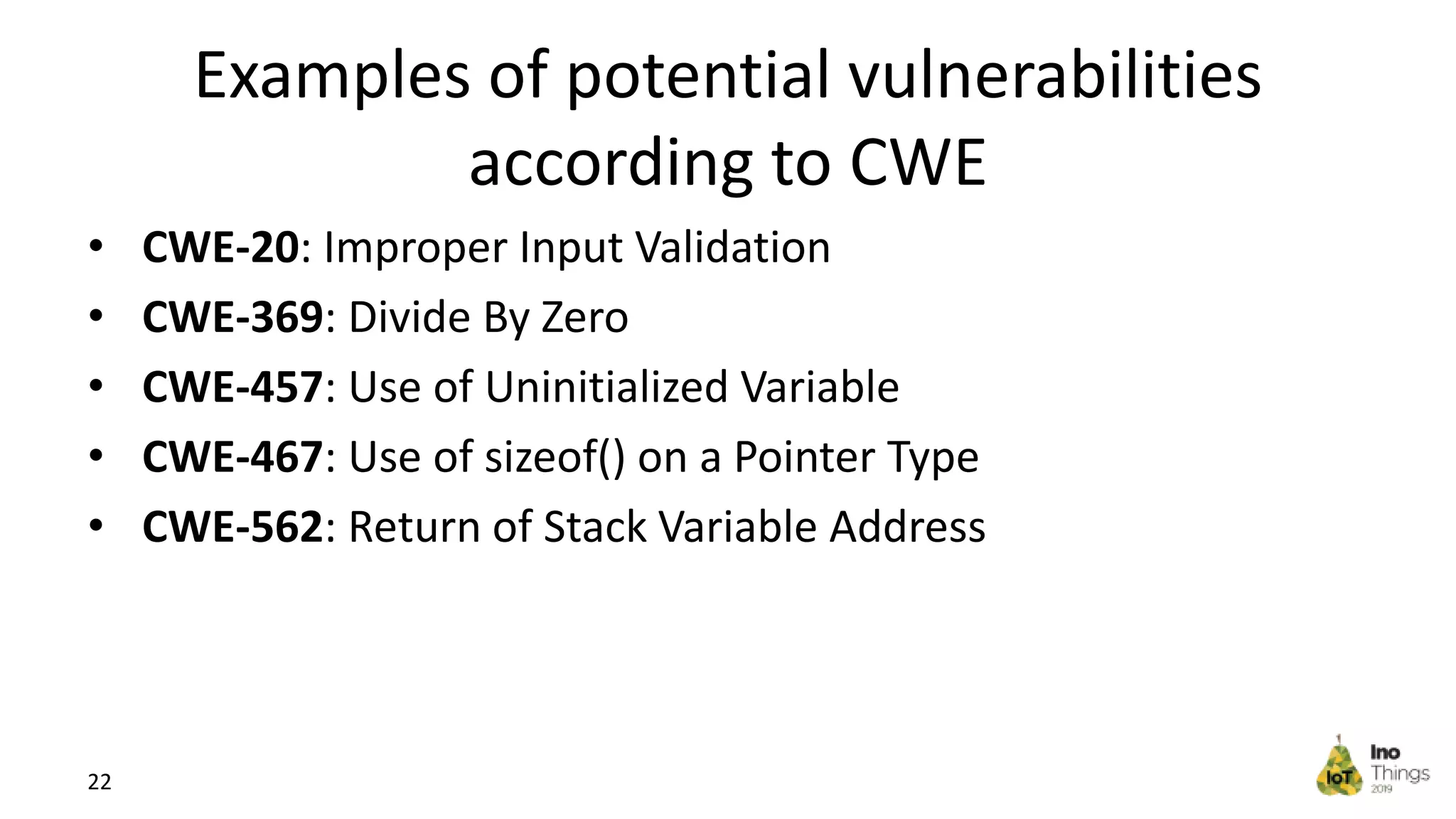
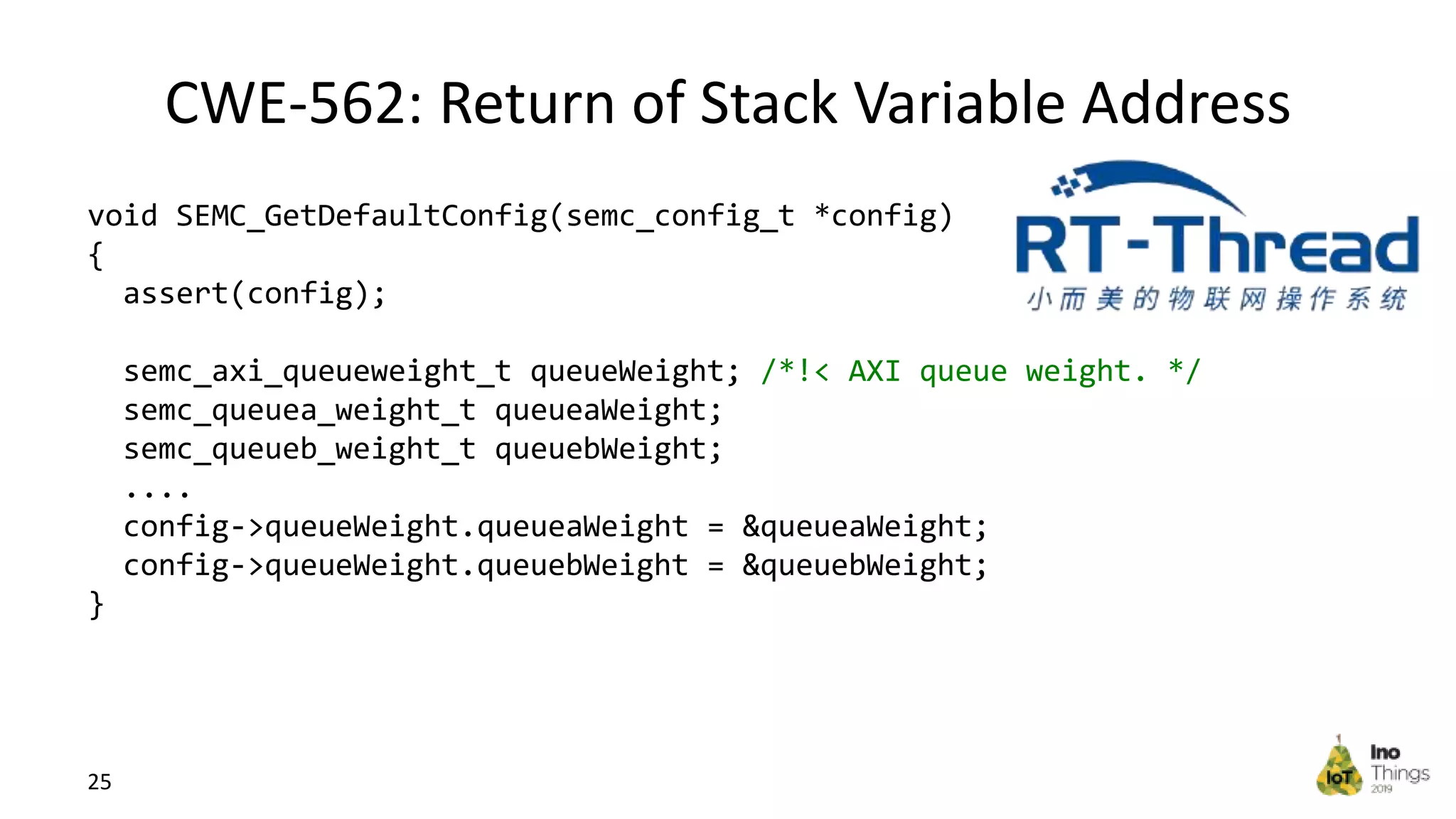
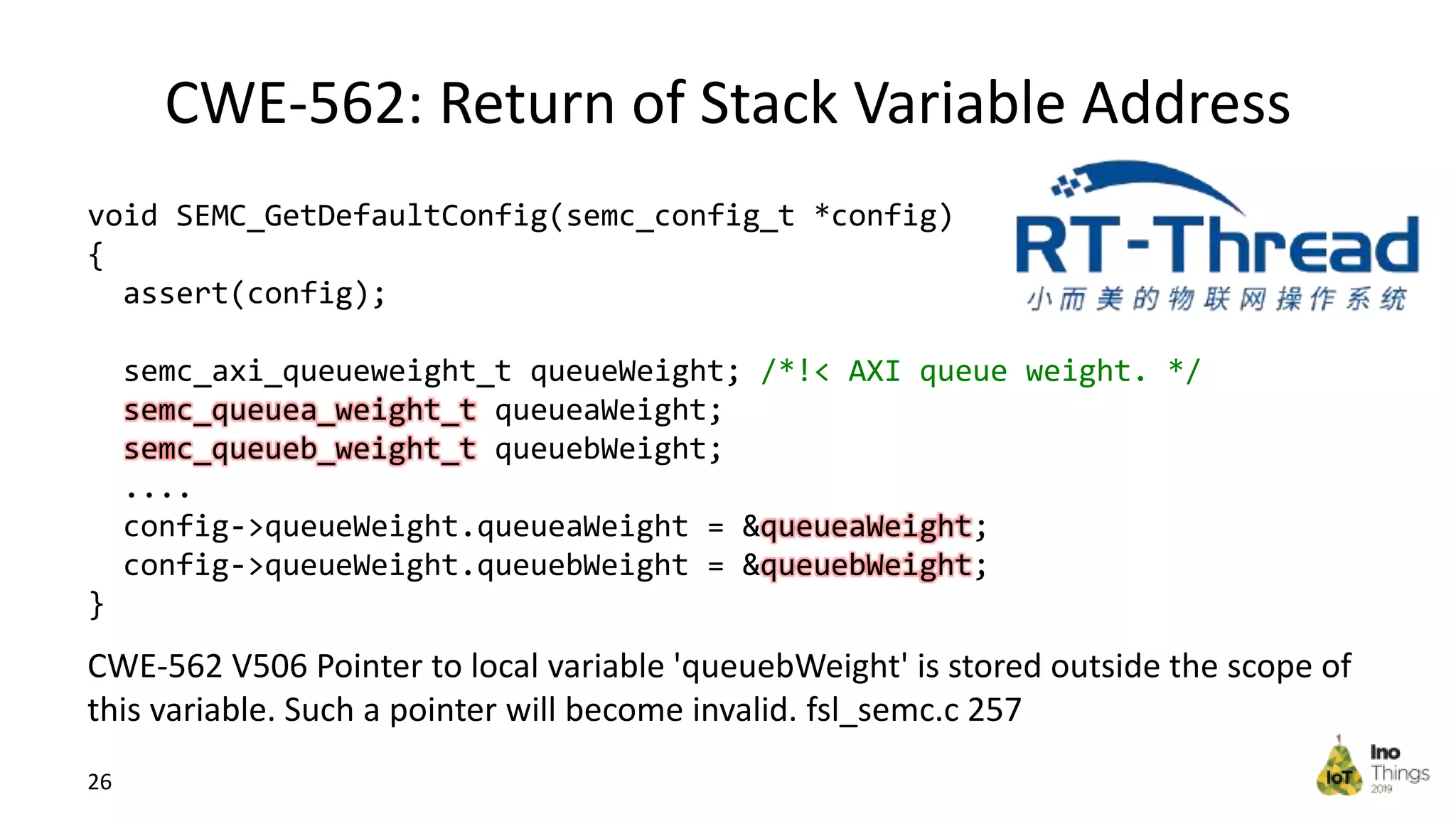
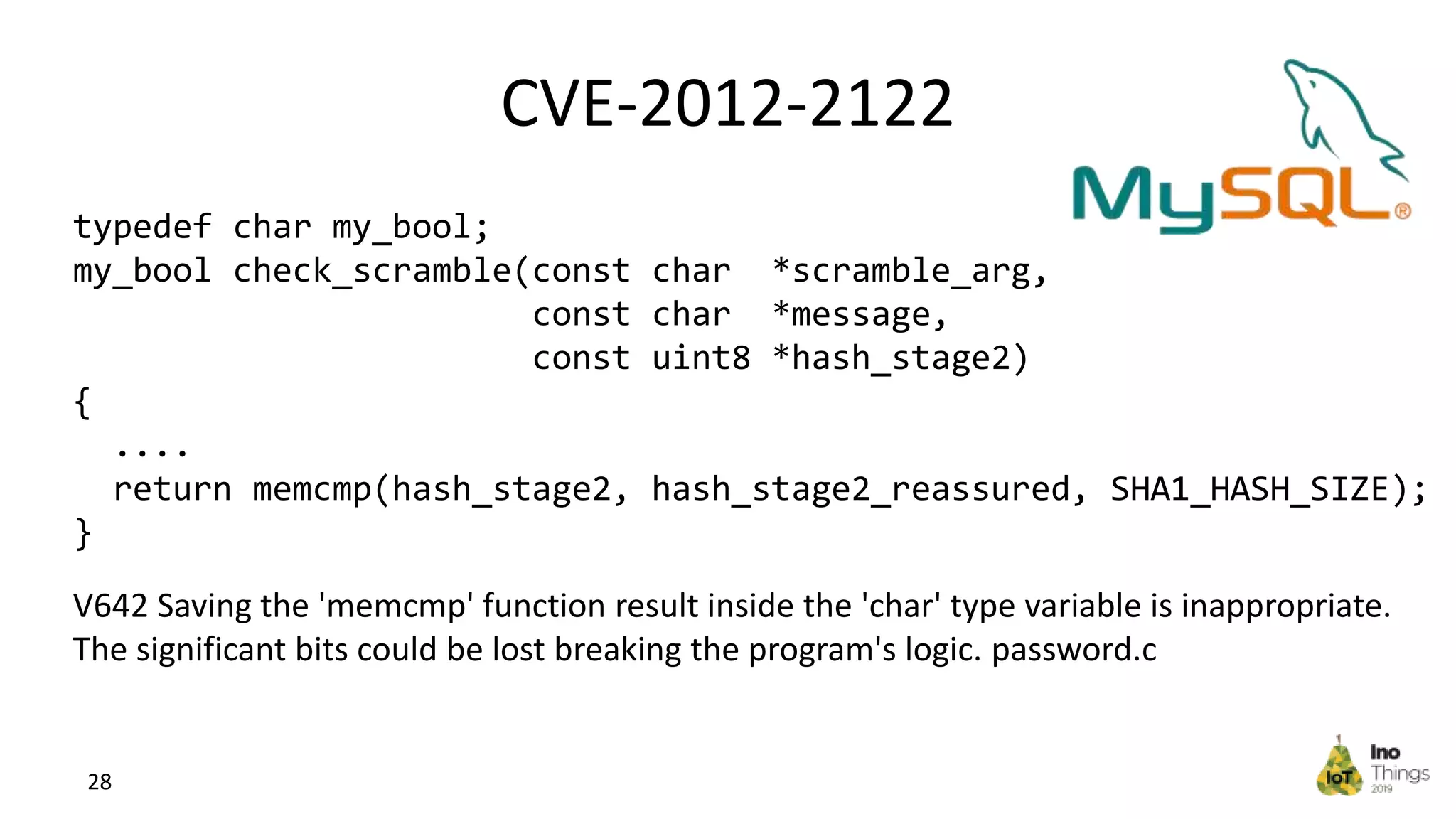
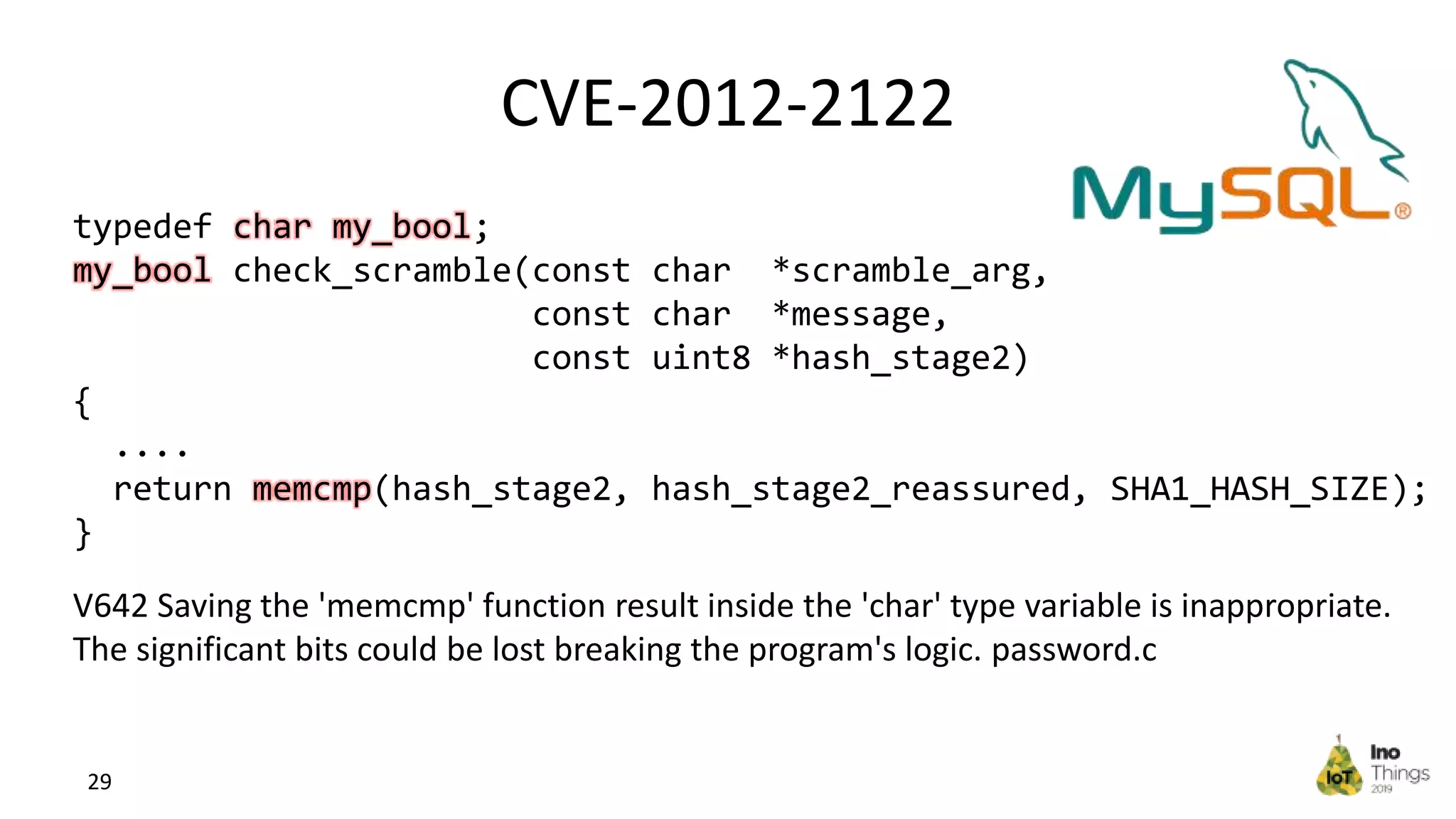
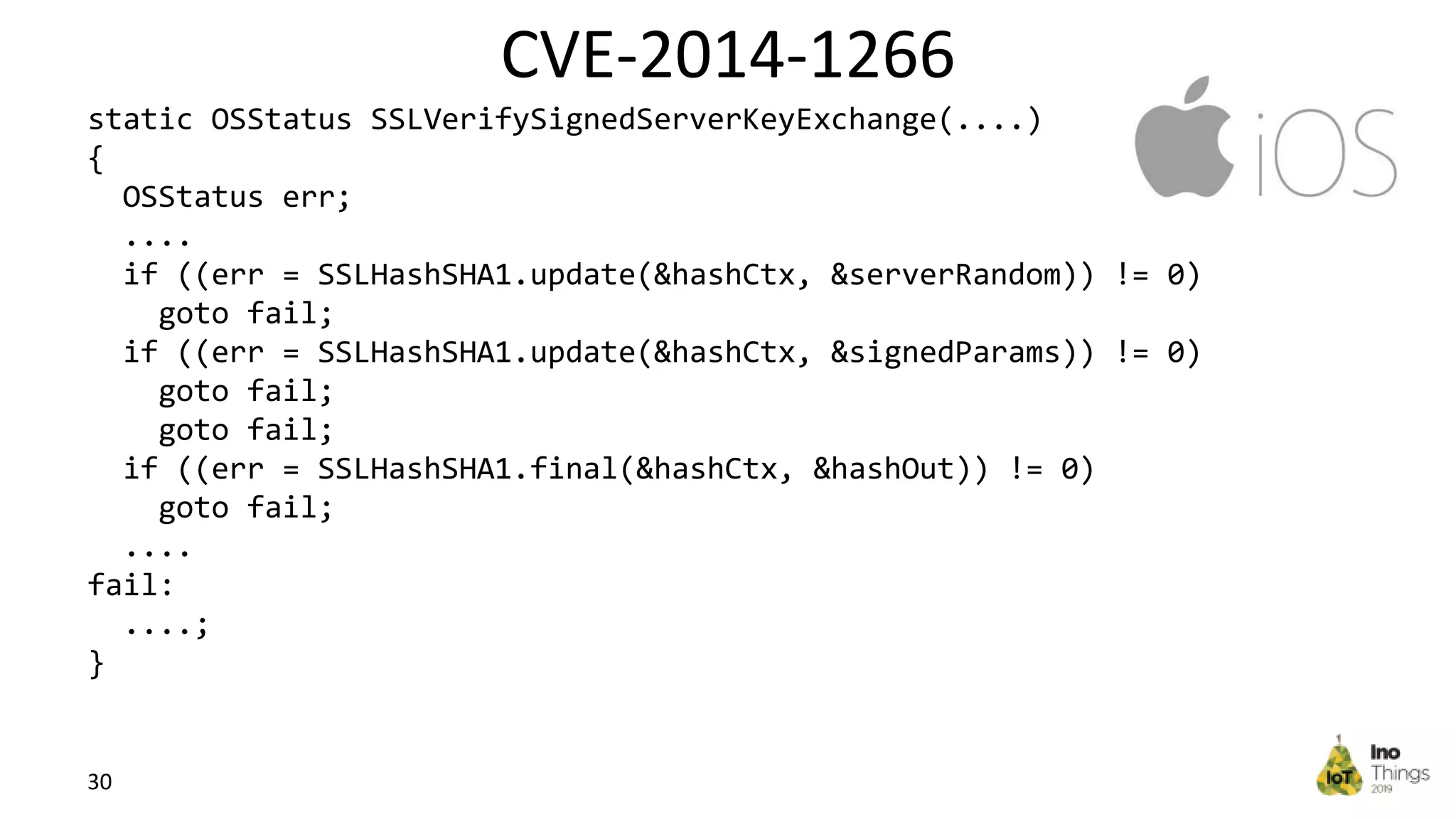
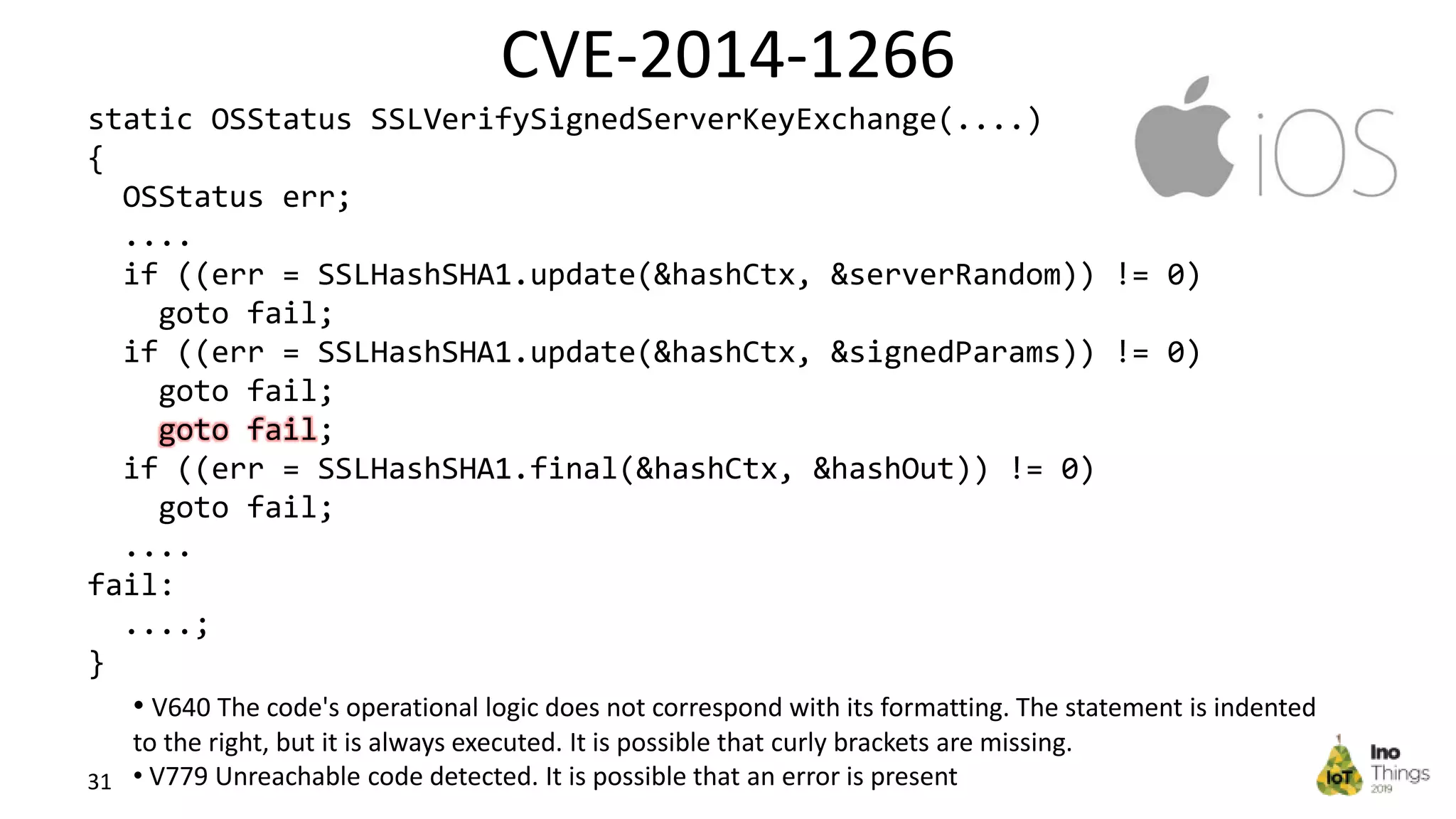
This document discusses static analysis for improving code quality in embedded systems. It begins by introducing the speaker and providing background on trends in IoT devices and code size growth. Examples are given of potential errors like divide by zero, use of uninitialized variables, and returning addresses of stack variables. Frameworks for finding vulnerabilities like CWE and real vulnerabilities like CVE are described. The value of code reviews and dynamic analysis are discussed but their limitations for embedded code. Finally, standards like MISRA and SEI CERT for preventing errors and examples of correctly using static analysis are provided.









![Where has the error crept? 17 static void SHA1Final(unsigned char digest[20], SHA1_CTX *context) { u32 i; unsigned char finalcount[8]; .... memset(context->count, 0, 8); memset(finalcount, 0, 8); }](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-17-2048.jpg)
![Here it is! 18 CWE-14 V597 The compiler could delete the 'memset' function call, which is used to flush 'finalcount' buffer. The memset_s() function should be used to erase the private data. wifi_generate_pin.c 185 static void SHA1Final(unsigned char digest[20], SHA1_CTX *context) { u32 i; unsigned char finalcount[8]; .... memset(context->count, 0, 8); memset(finalcount, 0, 8); }](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-18-2048.jpg)

![CWE-20: Improper Input Validation 23 if (c < 0) { if (fgets(command_buf, sizeof(command_buf) - 1, stdin) != command_buf) { break; } command_buf[strlen(command_buf) - 1] = '0'; /* remove endline */ break; }](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-23-2048.jpg)
![CWE-20: Improper Input Validation 24 if (c < 0) { if (fgets(command_buf, sizeof(command_buf) - 1, stdin) != command_buf) { break; } command_buf[strlen(command_buf) - 1] = '0'; /* remove endline */ break; } '0' 0 -1 CWE-20 V1010 Unchecked tainted data is used in index: 'strlen(command_buf)'.](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-24-2048.jpg)


![EXP34-C. Do not dereference null pointers, C/C++ 35 EOLIAN void _evas_canvas_key_lock_add( ...., Evas_Public_Data *e, ....) { .... e->locks.lock.list = realloc(e->locks.lock.list, e->locks.lock.count * sizeof(char *)); e->locks.lock.list[e->locks.lock.count - 1] = strdup(keyname); eina_hash_free_buckets(e->locks.masks); }](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-35-2048.jpg)
![EXP34-C. Do not dereference null pointers, C/C++ 36 EXP34-C V701 realloc() possible leak: when realloc() fails in allocating memory, original pointer 'e->locks.lock.list' is lost. Consider assigning realloc() to a temporary pointer. evas_key.c 142 EOLIAN void _evas_canvas_key_lock_add( ...., Evas_Public_Data *e, ....) { .... e->locks.lock.list = realloc(e->locks.lock.list, e->locks.lock.count * sizeof(char *)); e->locks.lock.list[e->locks.lock.count - 1] = strdup(keyname); eina_hash_free_buckets(e->locks.masks); }](https://image.slidesharecdn.com/he-190508205848/75/Static-analysis-and-writing-C-C-of-high-quality-code-for-embedded-systems-36-2048.jpg)