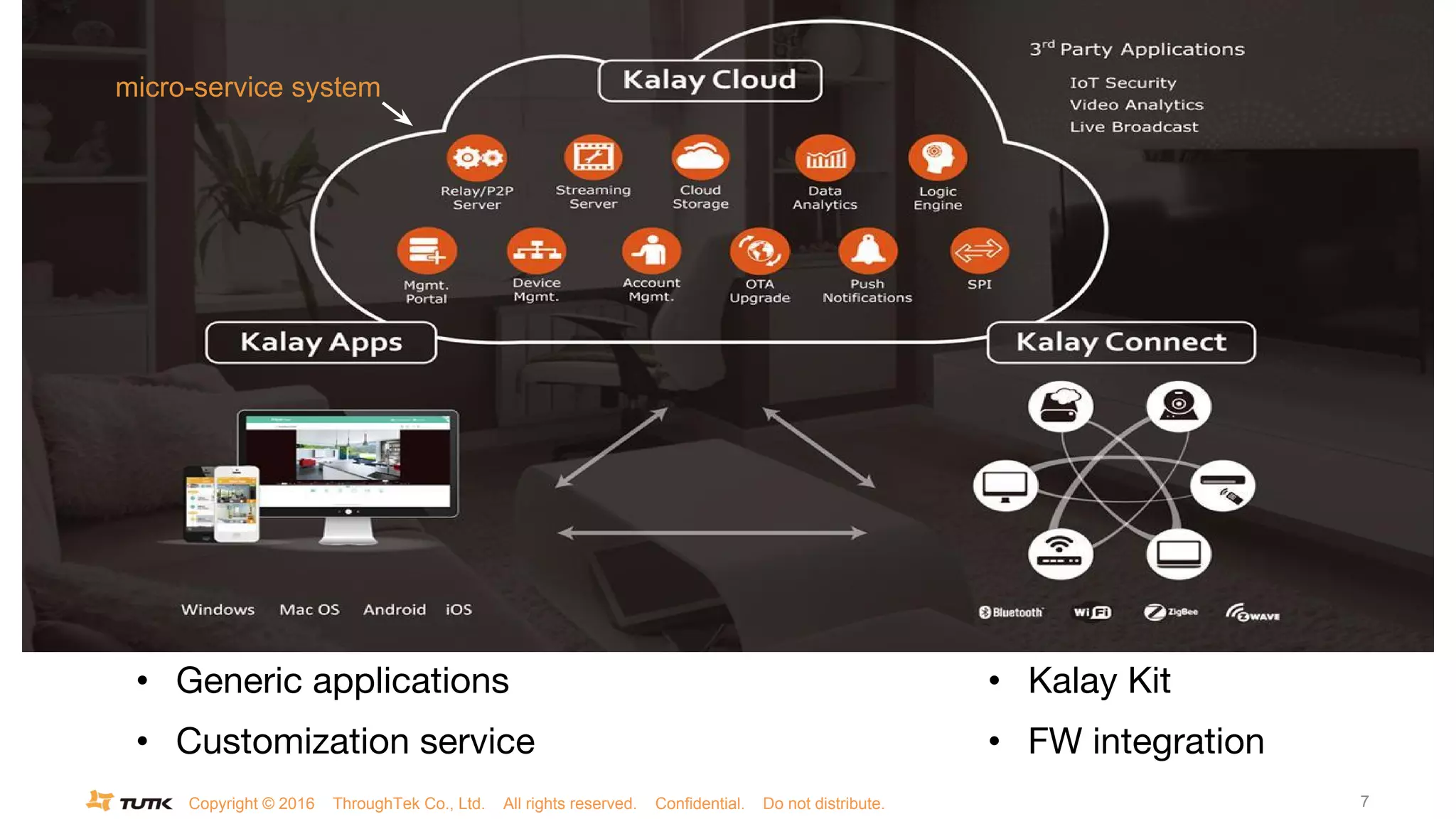
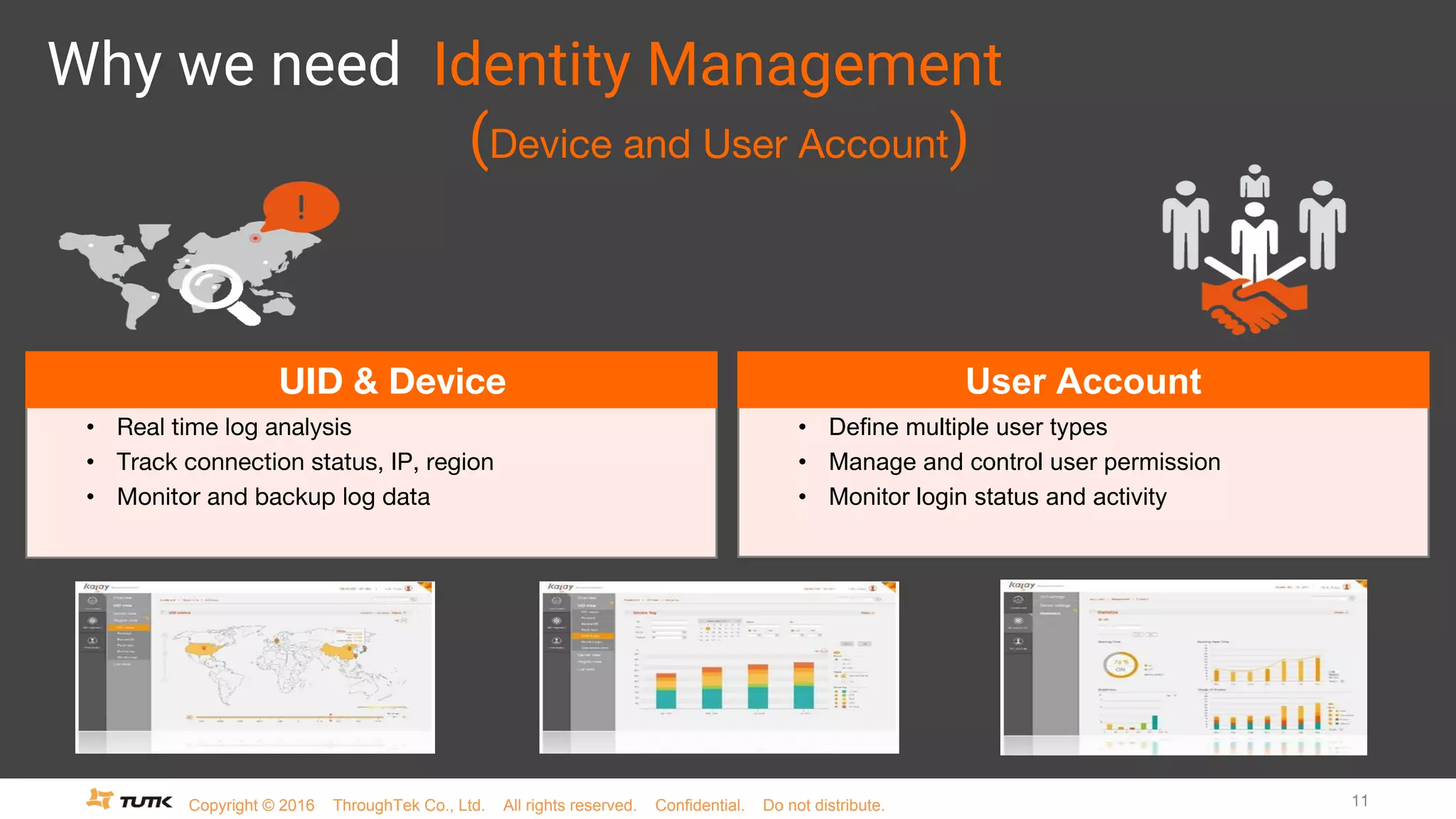
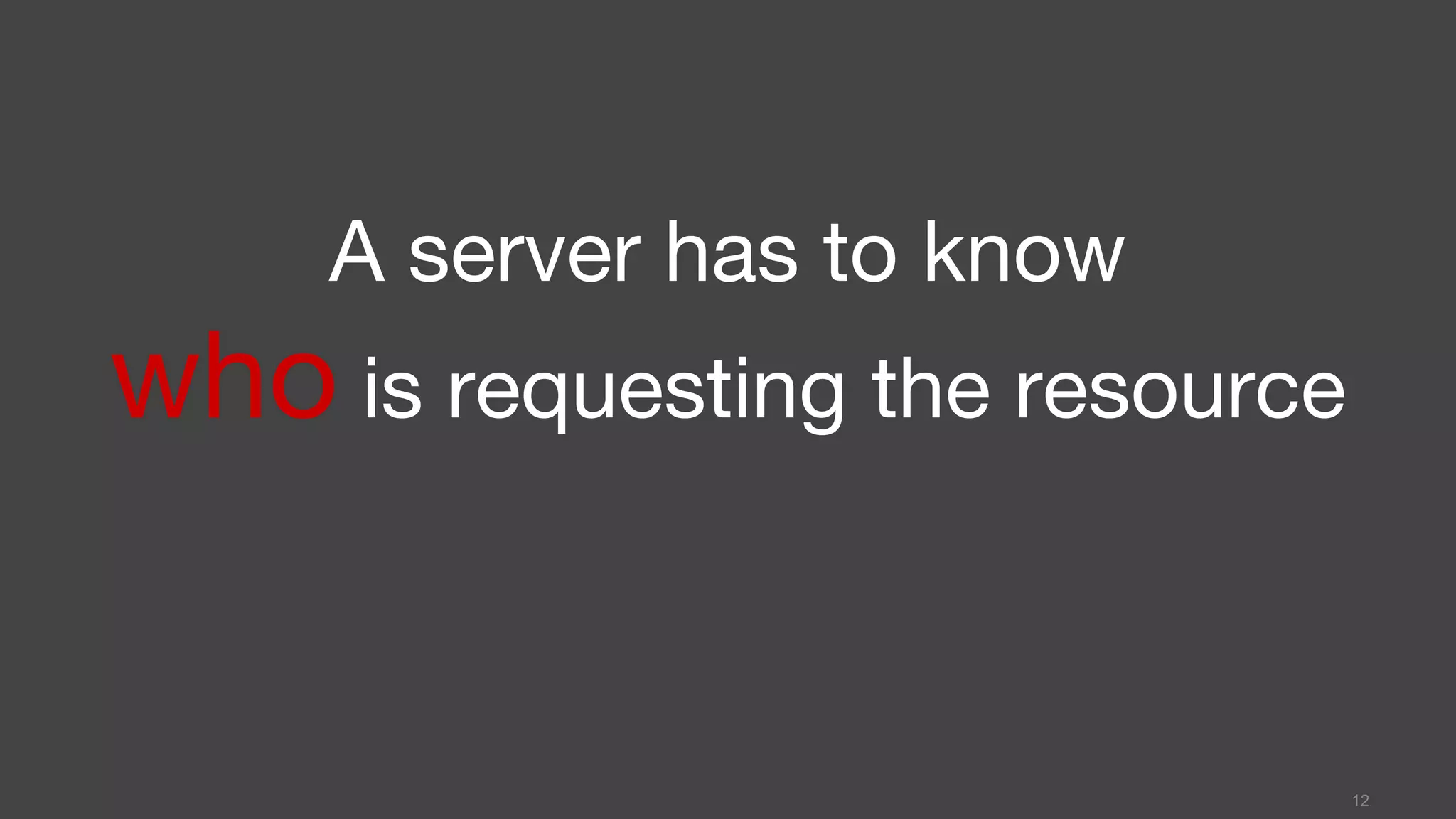
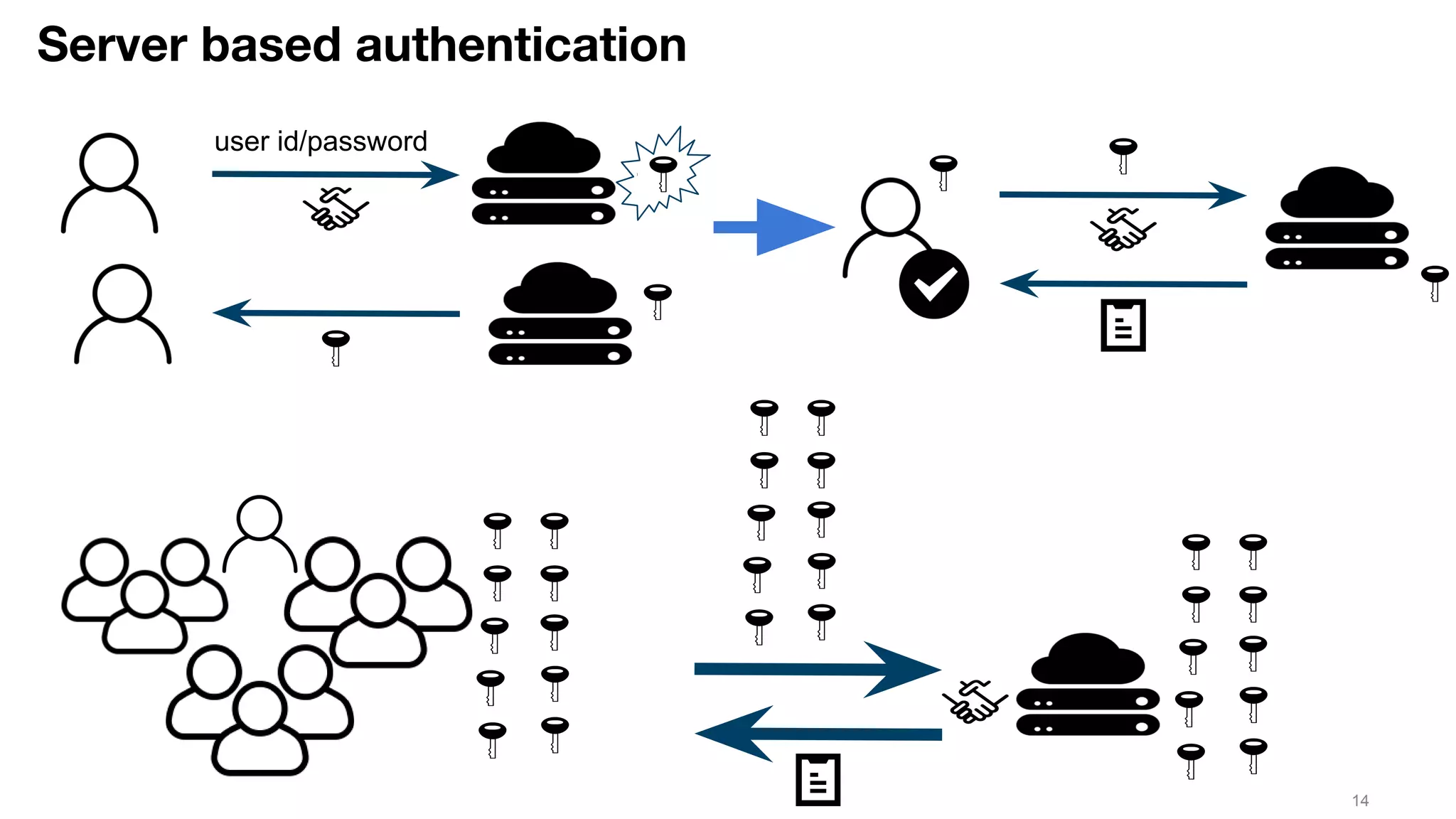
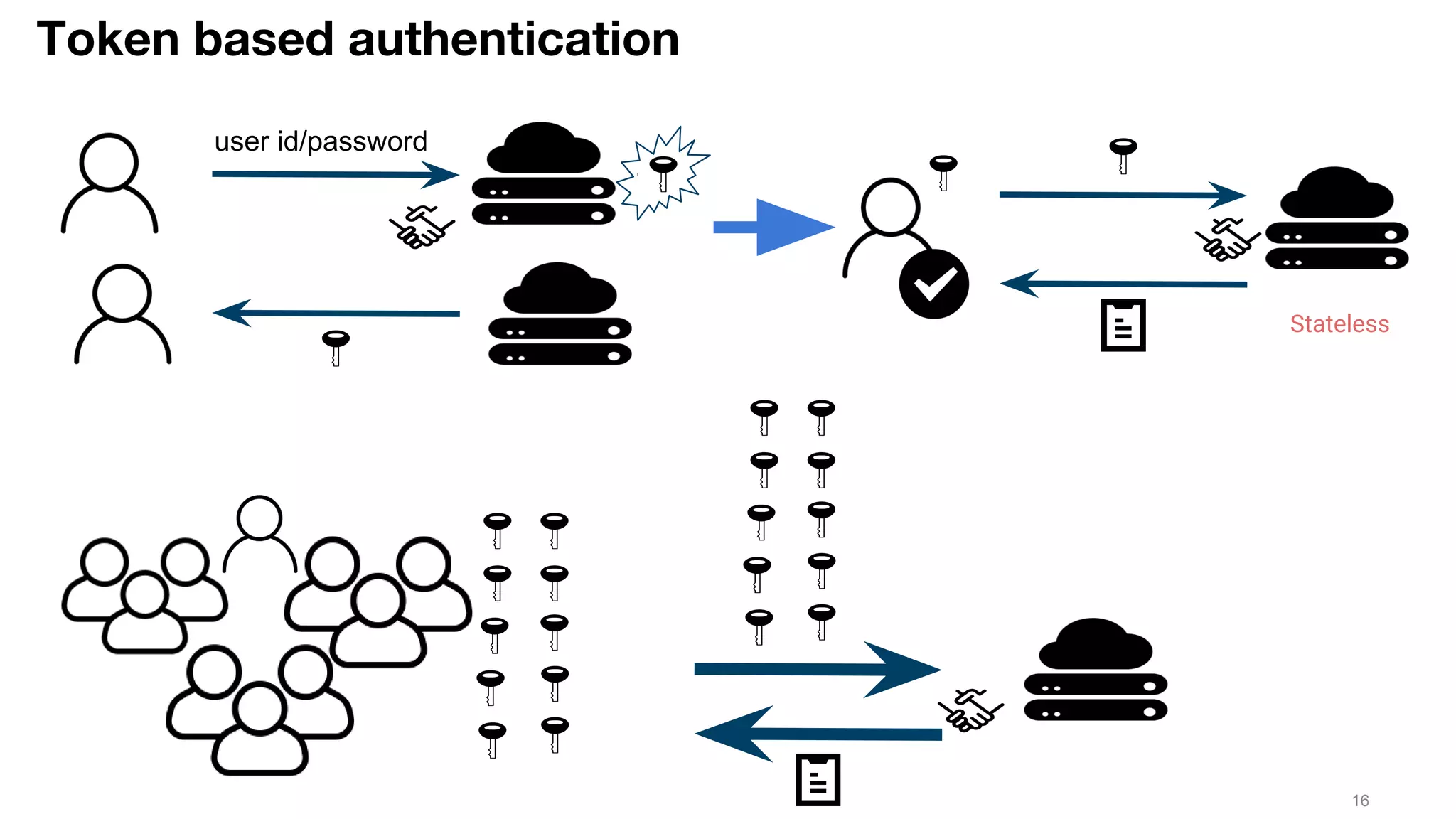
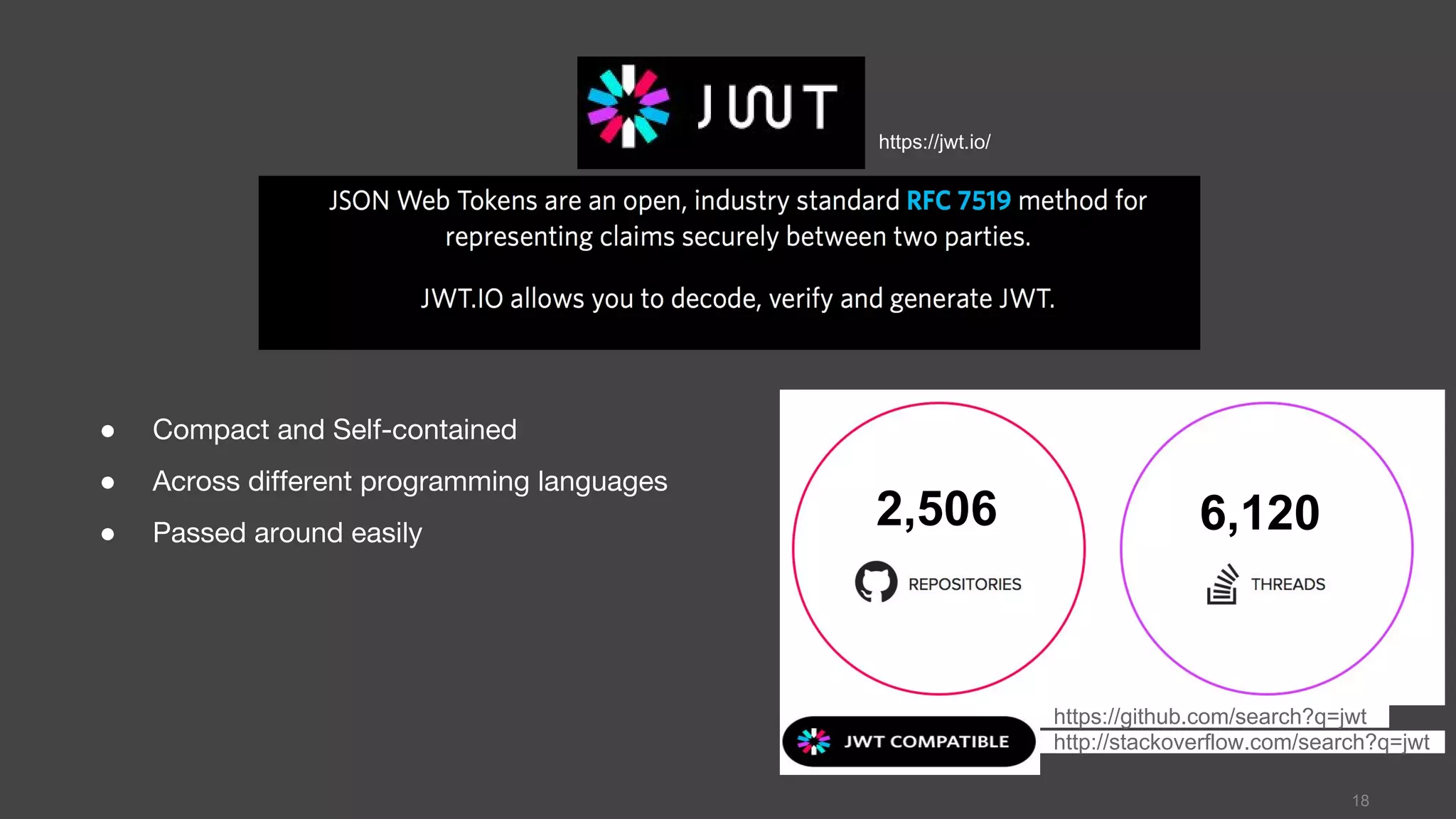
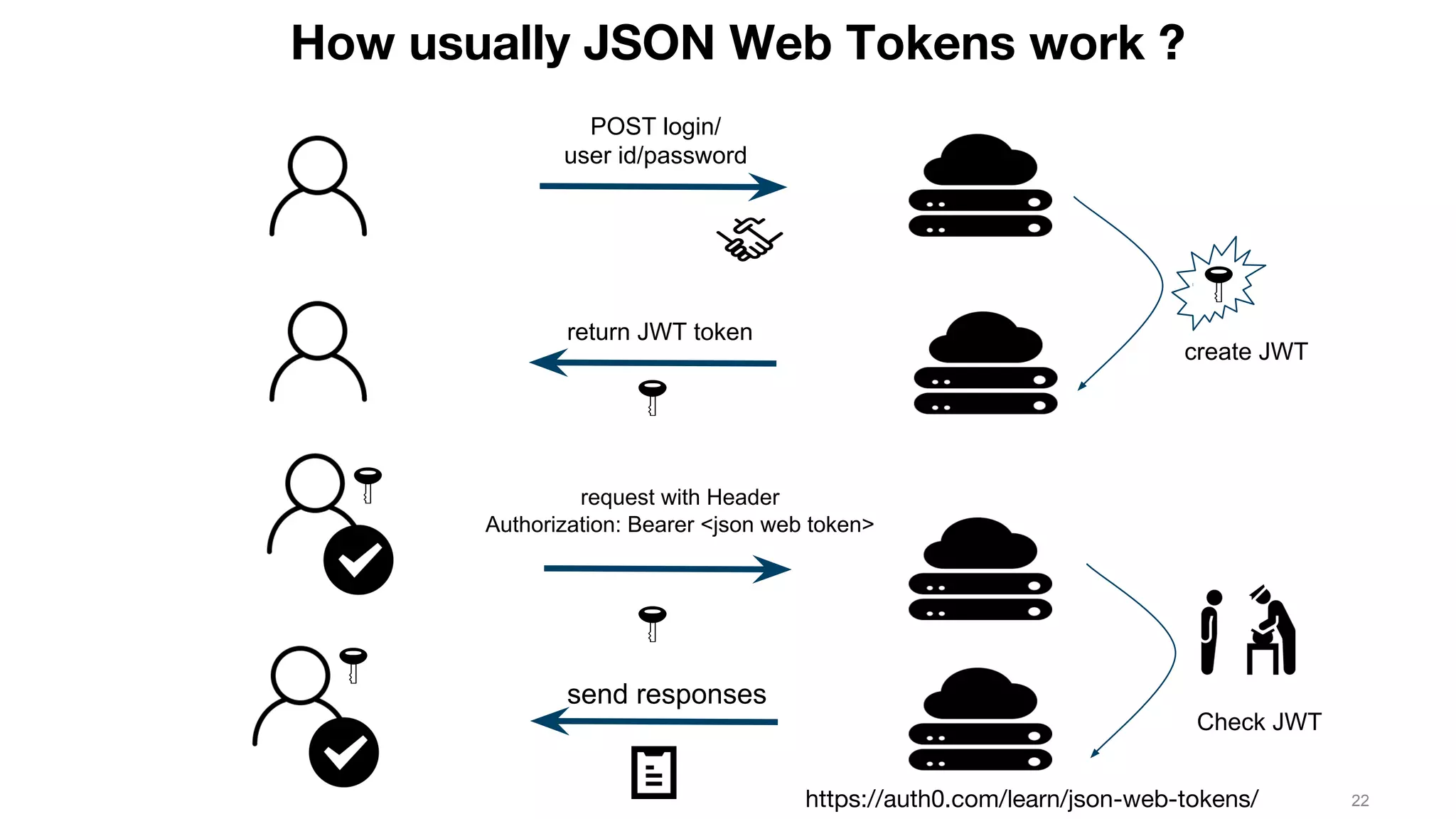
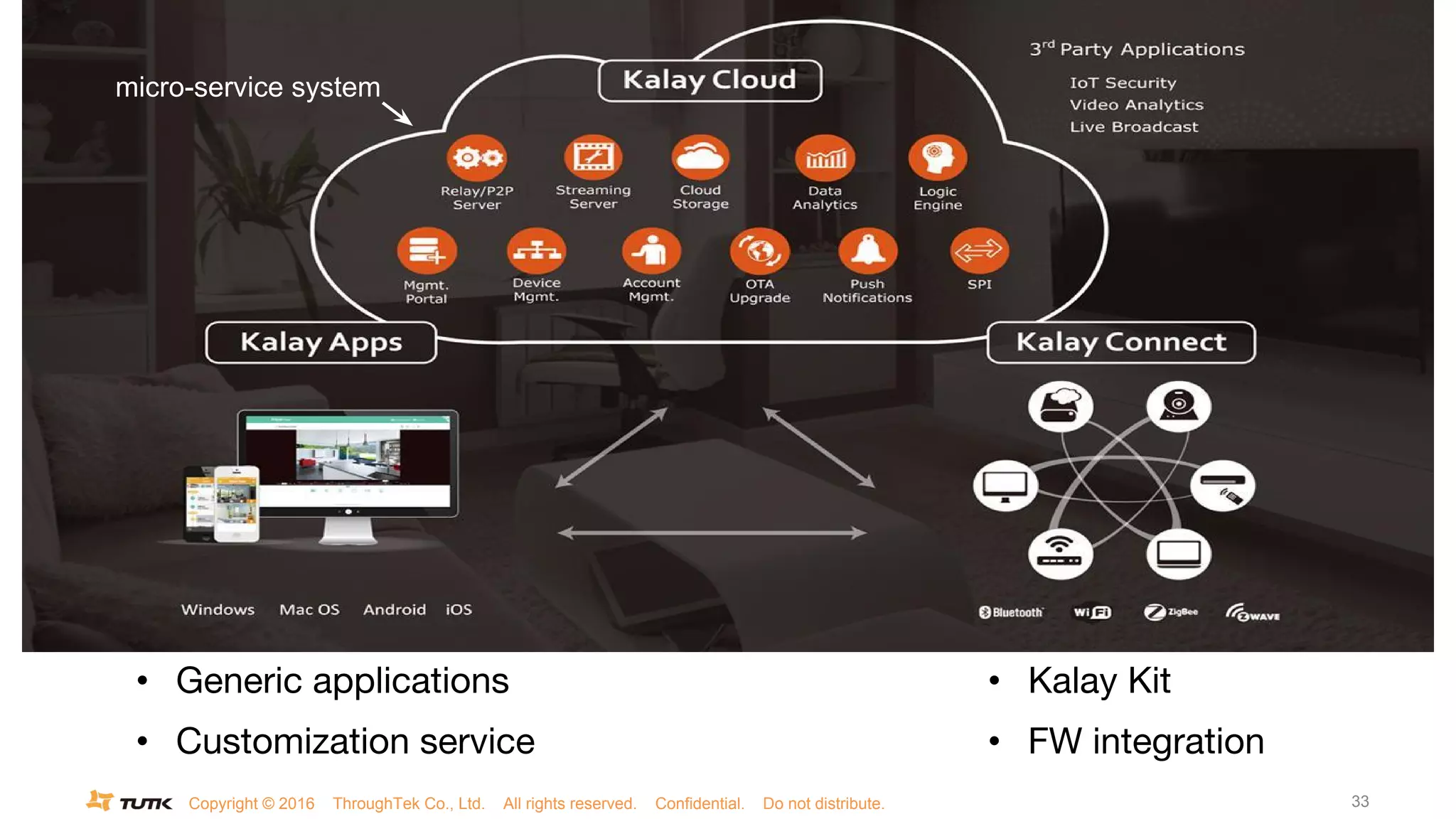
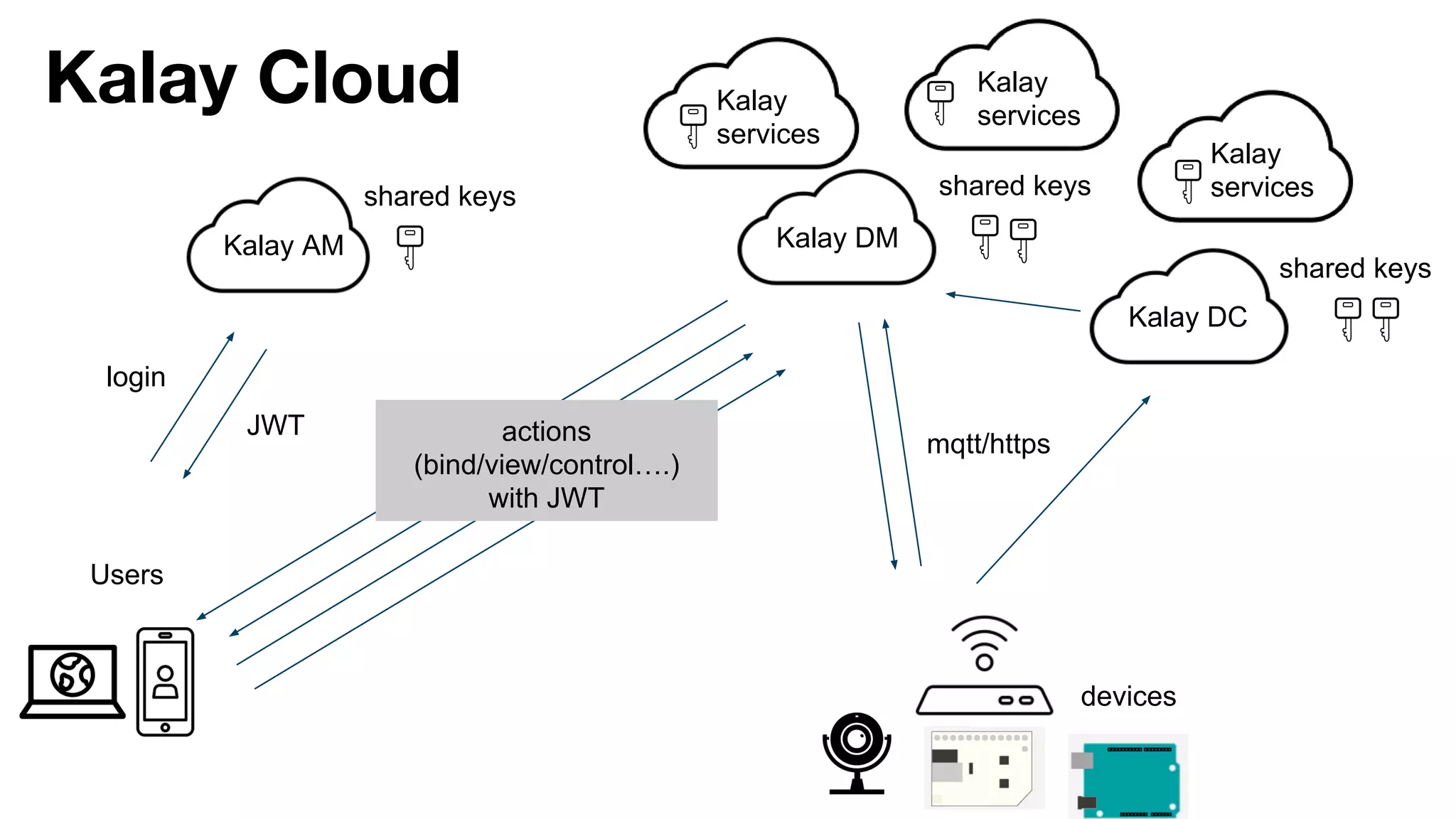
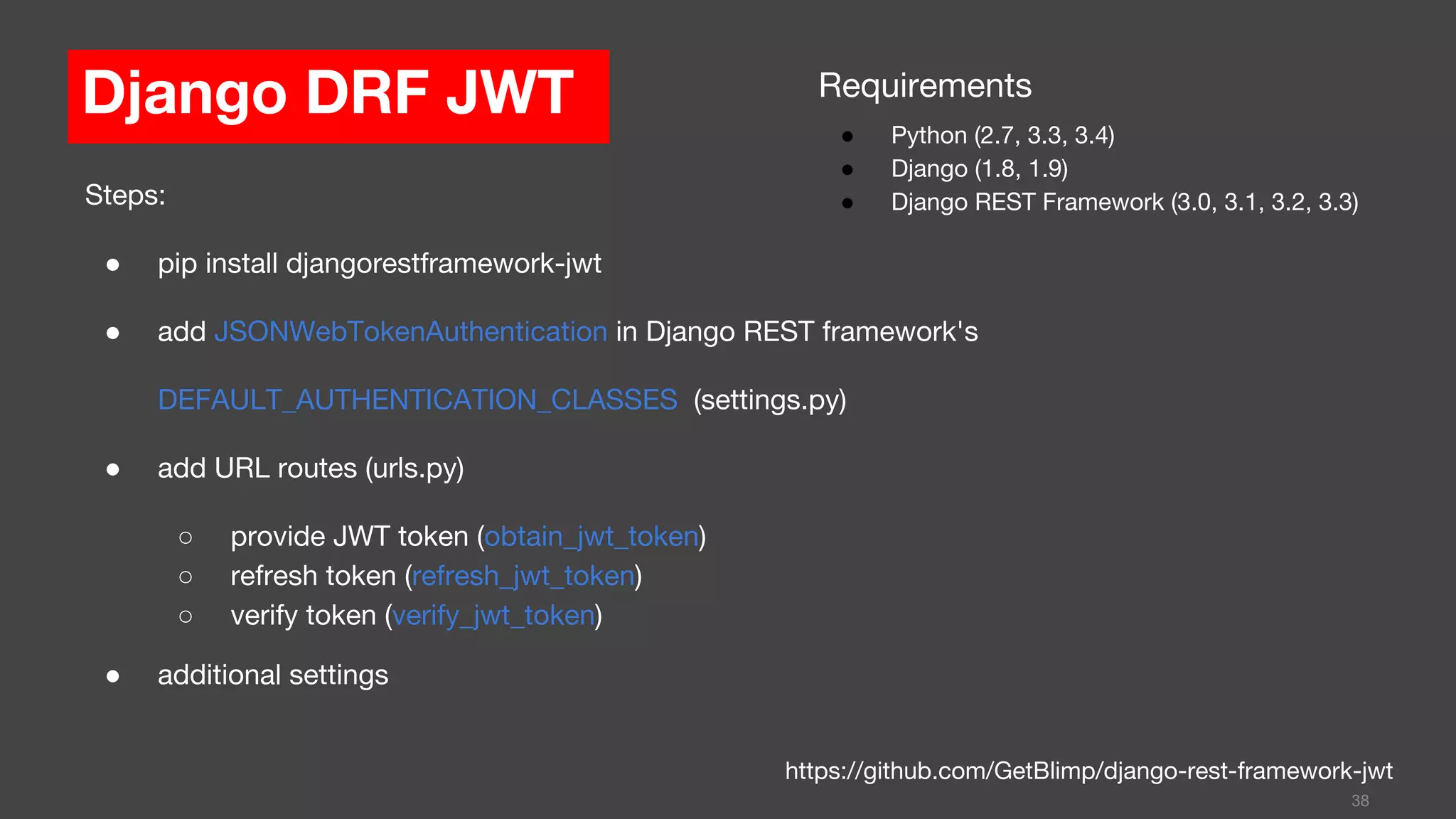
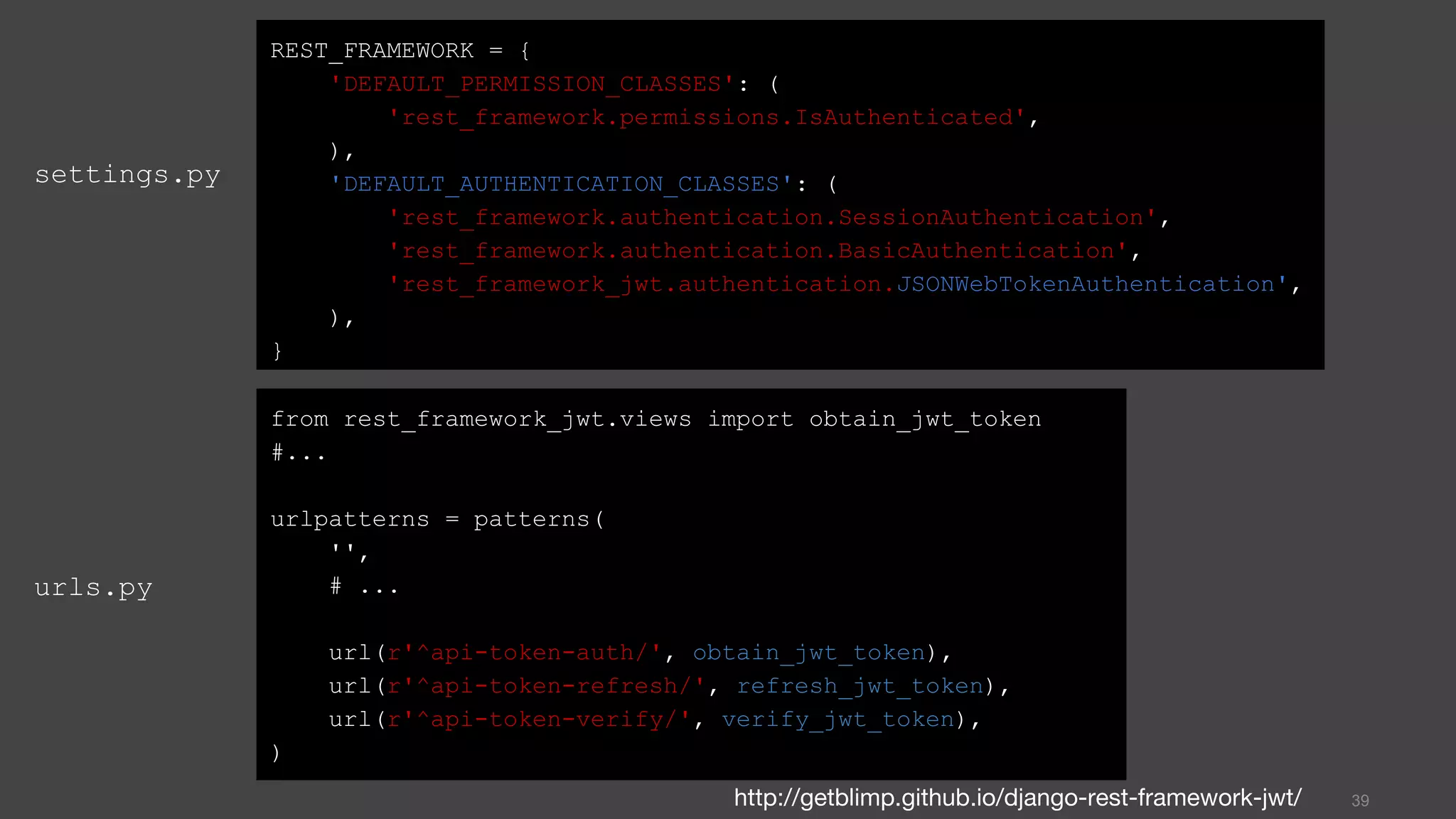
This document discusses JSON Web Tokens (JWT) for authentication. It begins by explaining the need for authorization in web applications and how token-based authentication addresses issues with server-based authentication. The structure of a JWT is described as a JSON object with a header, payload, and signature. Python libraries for working with JWT like PyJWT, Django REST Framework JWT, and Flask-JWT are presented. The document demonstrates generating and verifying JWT in Python code. Examples of using JWT for authentication in the Kalay IoT platform and Diuit messaging API are provided.













![25 In [1]: import json In [2]: import hmac In [3]: from hashlib import sha256 In [4]: from base64 import urlsafe_b64encode In [5]: segments =[] In [6]: header_dict = { ...: 'typ': 'JWT', ...: 'alg': 'HS256' ...: } In [7]: json_header = json.dumps(header_dict).encode('utf-8') In [8]: header = urlsafe_b64encode(json_header) In [9]: segments.append(header) In [10]: segments Out[10]: [b'eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9']](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-25-2048.jpg)
![26 In [11]: payload_dict = { ....: 'user_id':'pythontw2016' ....: } In [12]: json_payload =json.dumps(payload_dict).encode('utf-8') In [13]: payload = urlsafe_b64encode(json_payload) In [14]: segments.append(payload) In [15]: segments Out[15]: [b'eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9', b'eyJ1c2VyX2lkIjogInB5dGhvbnR3MjAxNiJ9']](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-26-2048.jpg)
![27 In [16]: SECRET = b'secret' In [17]: signing_input = b'.'.join(segments) In [18]: sig = hmac.new (SECRET, signing_input, sha256) In [19]: signature = urlsafe_b64encode(sig.digest()) In [20]: segments.append(signature) In [21]: segments Out[21]: [b'eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9', b'eyJ1c2VyX2lkIjogInB5dGhvbnR3MjAxNiJ9', b'qhevGfl16LBHjRG2wb6xDitbGt3lDK-2iUYCsLseCJY='] In [22]: token = b'.'.join(segments) In [23]: token Out[23]: b'eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9. eyJ1c2VyX2lkIjogInB5dGhvbnR3MjAxNiJ9.qhevGfl16LBHjRG2wb6xDitbGt3lDK- 2iUYCsLseCJY=' Test this token in https://jwt.io/](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-27-2048.jpg)

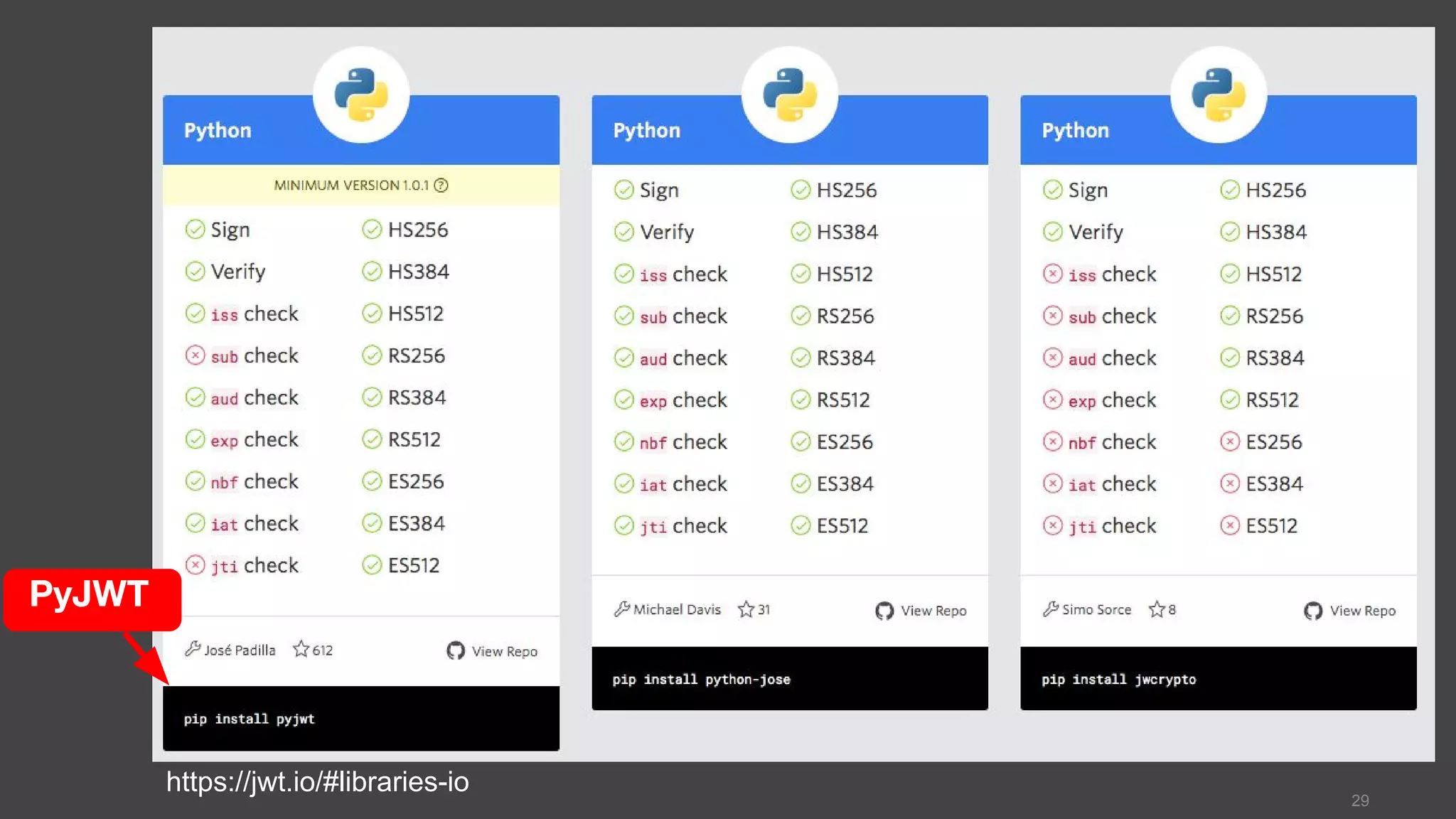
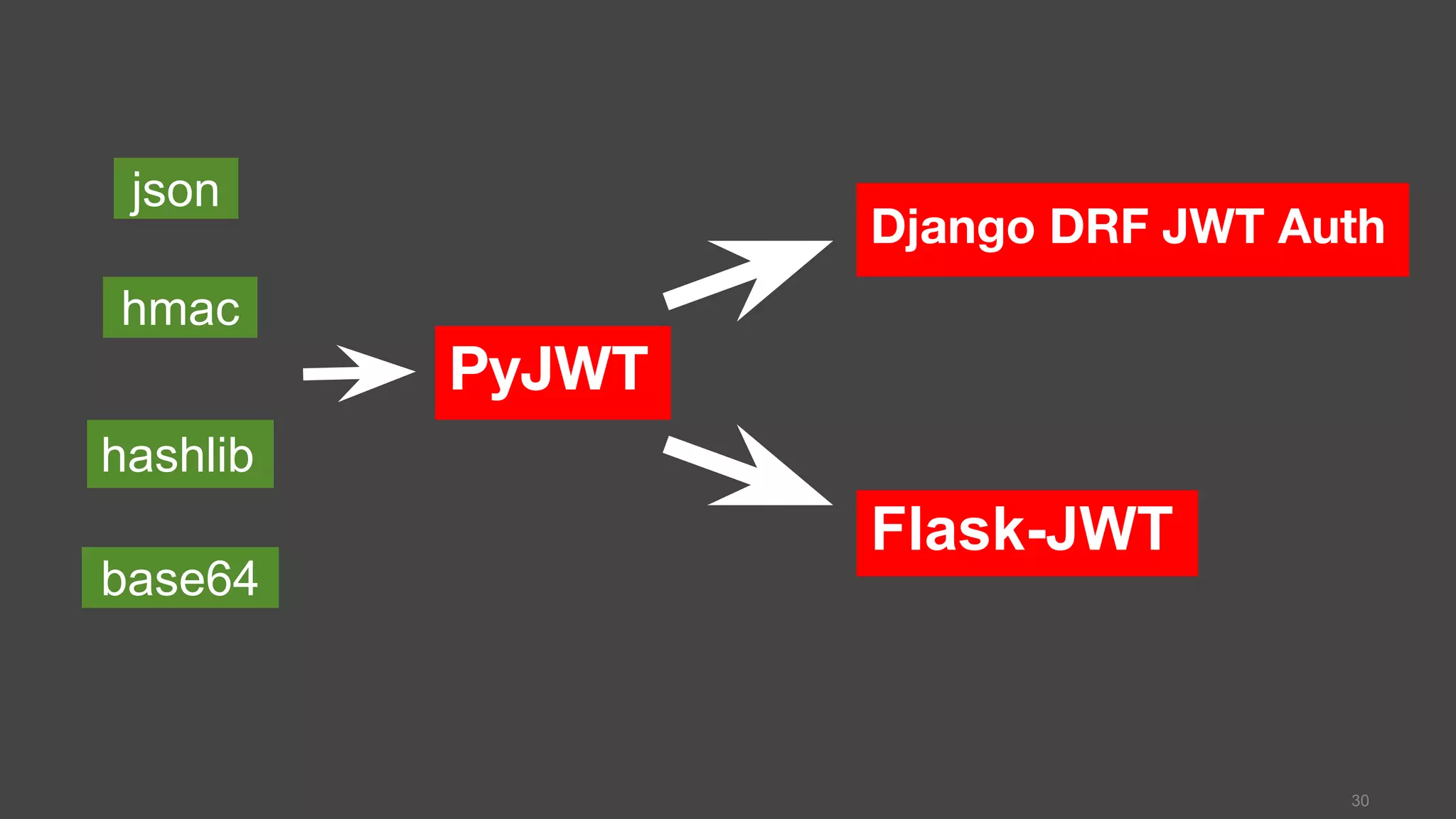
![PyJWT >>> import jwt >>> jwt_token = jwt.encode({ 'payload': ‘pycontw 2106’ }, 'secret', algorithm='HS256') 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9. eyJwYXlsb2FkIjoicHljb250dyAyMDE2In0. TRRENrqd8lc3_AQeo3IRheVkZpMkcqXqYQi891pFL6w’ >>> jwt.decode(jwt_token, 'secret', algorithms=[ 'HS256']) {'payload': 'pycontw 2016'} 31 https://github.com/jpadilla/pyjwt pip install PyJWT see more in Registered Claim Names](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-31-2048.jpg)




![Flask-JWT from flask import Flask from flask_jwt import JWT, jwt_required, current_identity from werkzeug.security import safe_str_cmp 41 https://pythonhosted.org/Flask-JWT/ pip install Flask-JWT class User(object): def __init__(self, id, username, password): self.id = id self.username = username self.password = password def __str__(self): return "User(id='%s')" % self.id users = [ User(1, 'user1', 'abcxyz'), User(2, 'user2', 'abcxyz'), ] username_table = {u.username: u for u in users} userid_table = {u.id: u for u in users} Minimum viable application configuration:](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-41-2048.jpg)
![42 app = Flask(__name__) app.debug = True app.config['SECRET_KEY'] = ' super-secret' jwt = JWT(app, authenticate, identity ) def identity(payload): user_id = payload['identity'] return userid_table.get(user_id, None) def authenticate(username, password): user = username_table.get(username, None) if user and safe_str_cmp(user.password.encode('utf-8'), password.encode('utf-8')): return user @app.route('/protected') @jwt_required() def protected(): return '%s' % current_identity if __name__ == '__main__': app.run() Configuration JWT_AUTH_URL_RULE: The authentication endpoint URL. Defaults to /auth https://pythonhosted.org/Flask-JWT/ jwt working](https://image.slidesharecdn.com/2016pycontwwebapiauthentication-160604081733/75/2016-pycontw-web-api-authentication-42-2048.jpg)