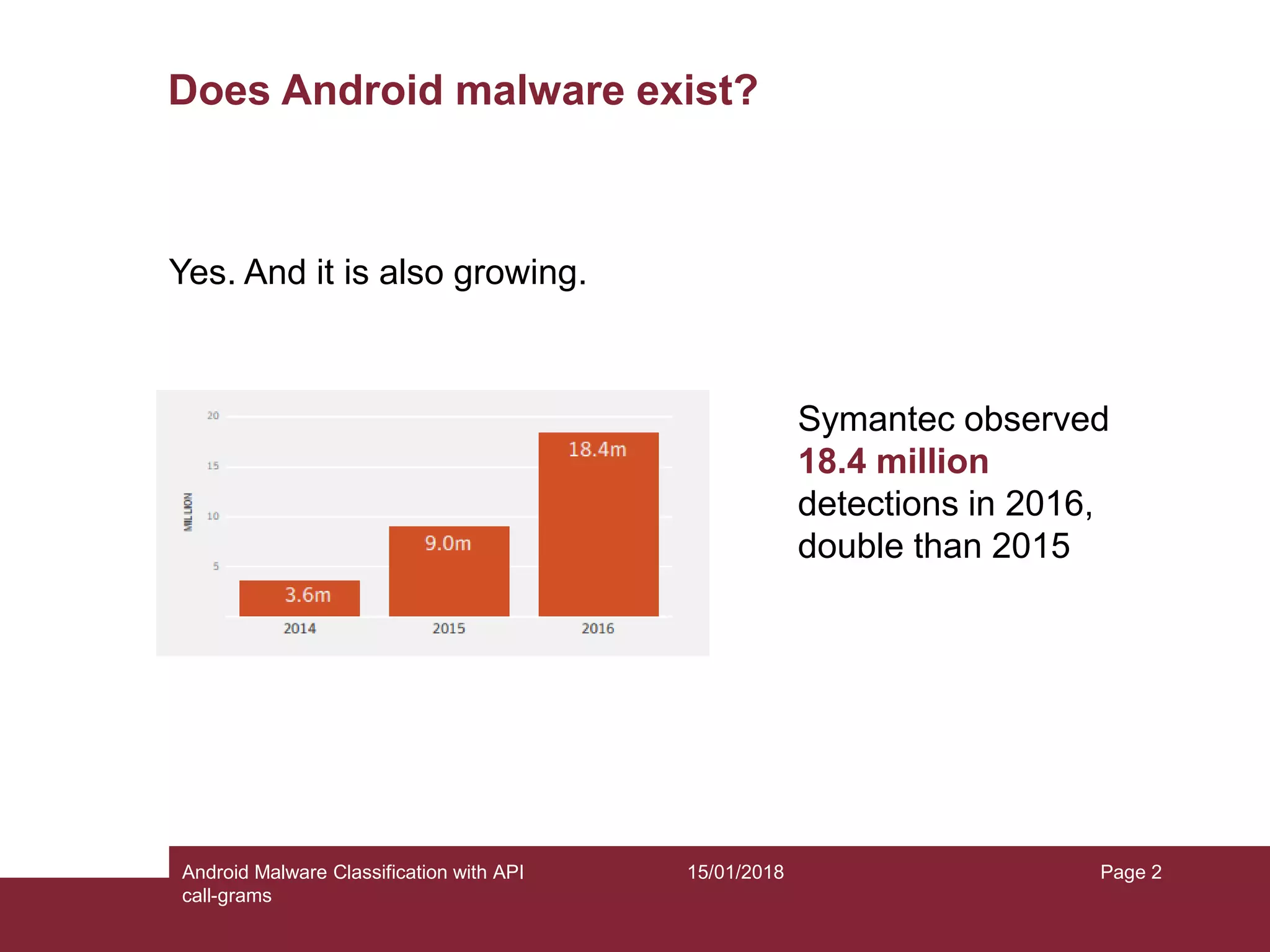
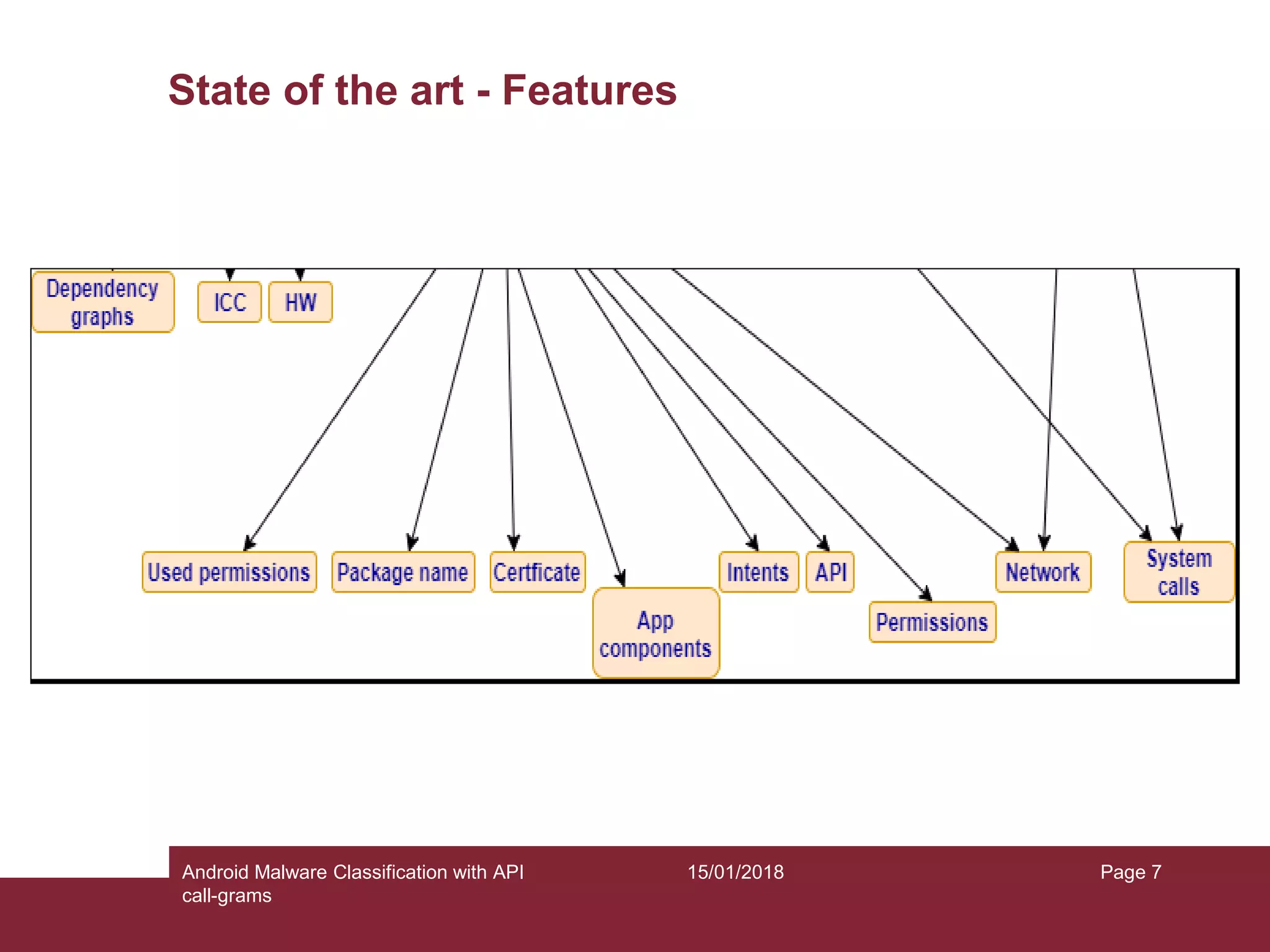
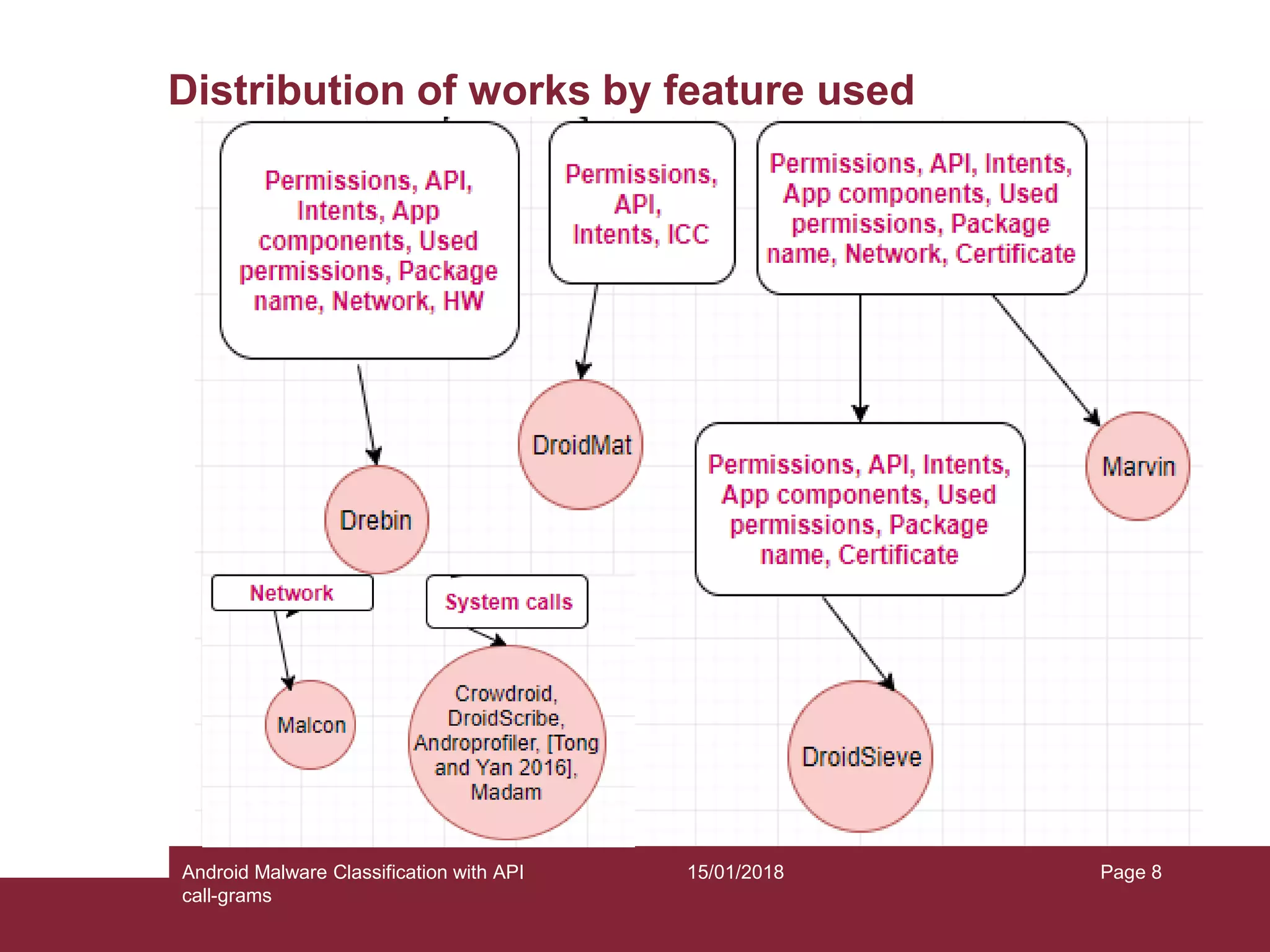
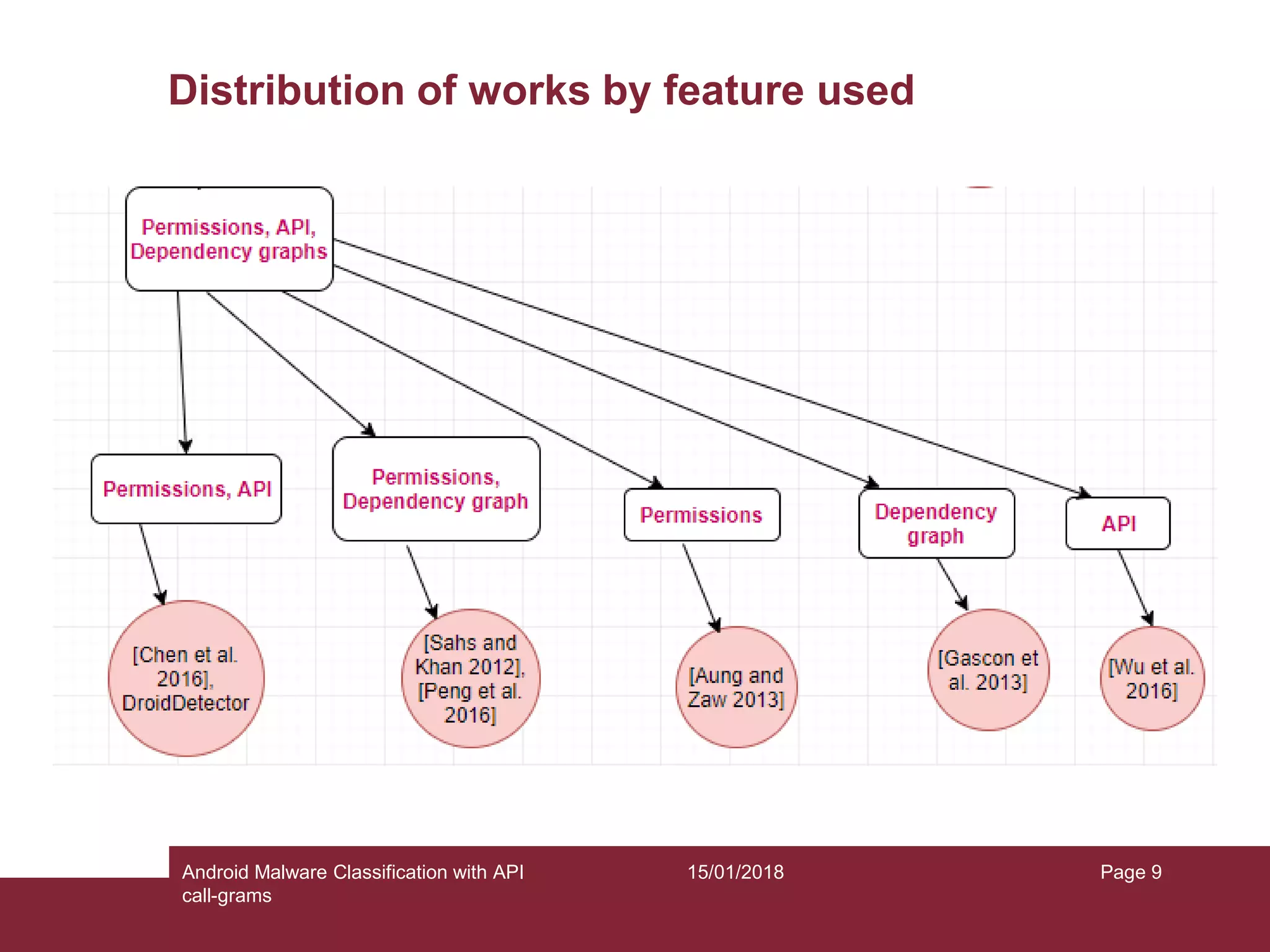
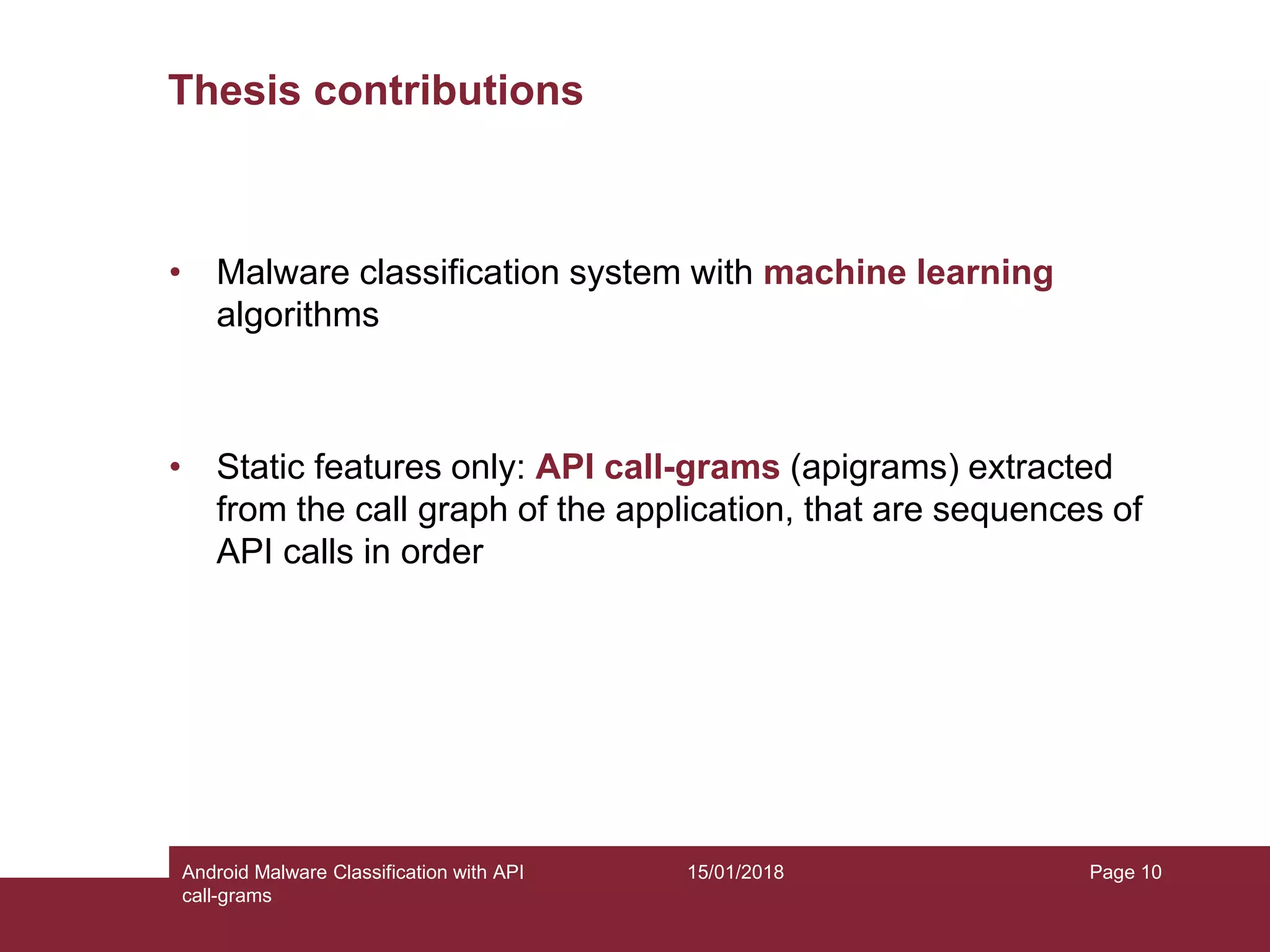
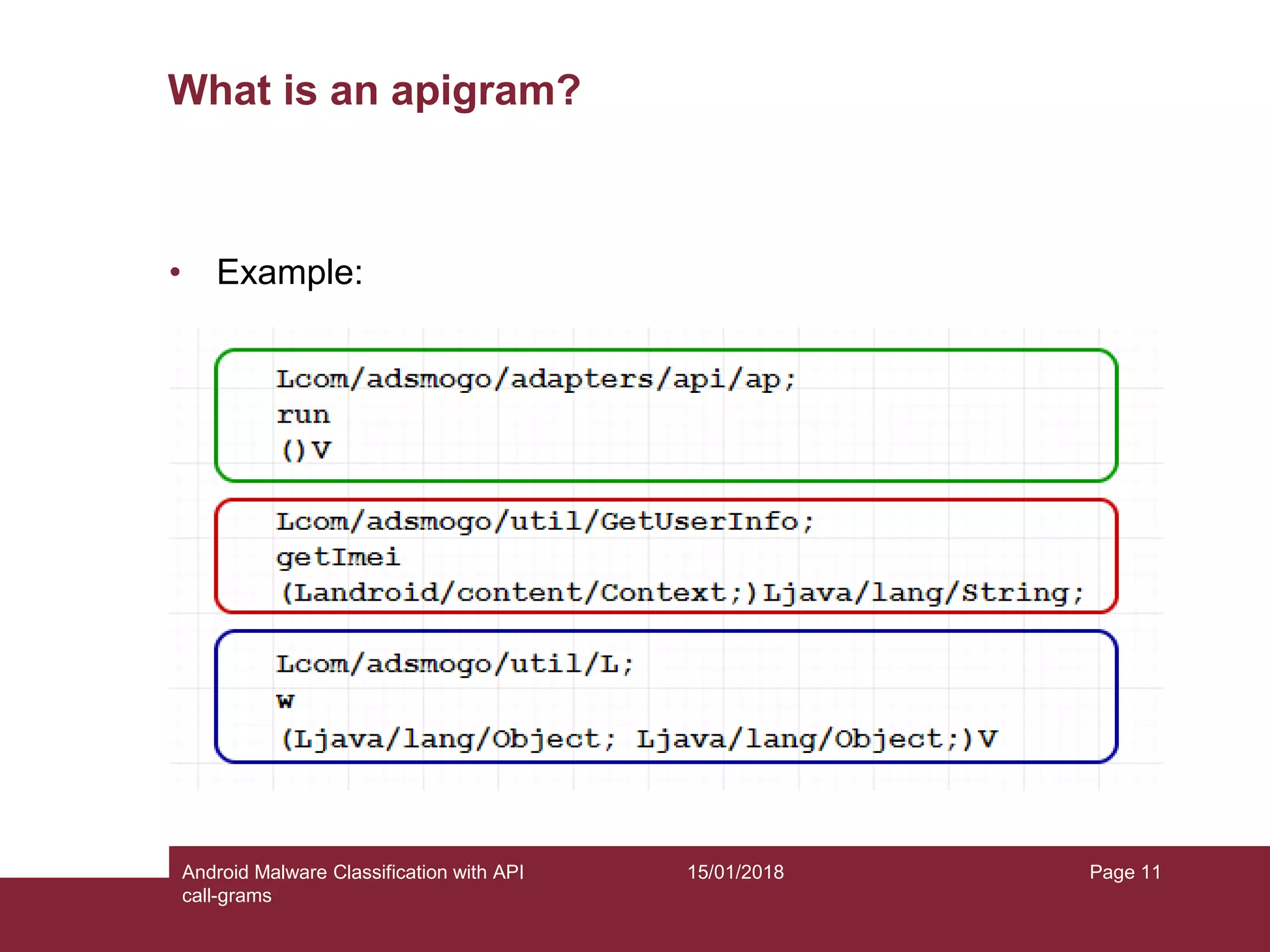
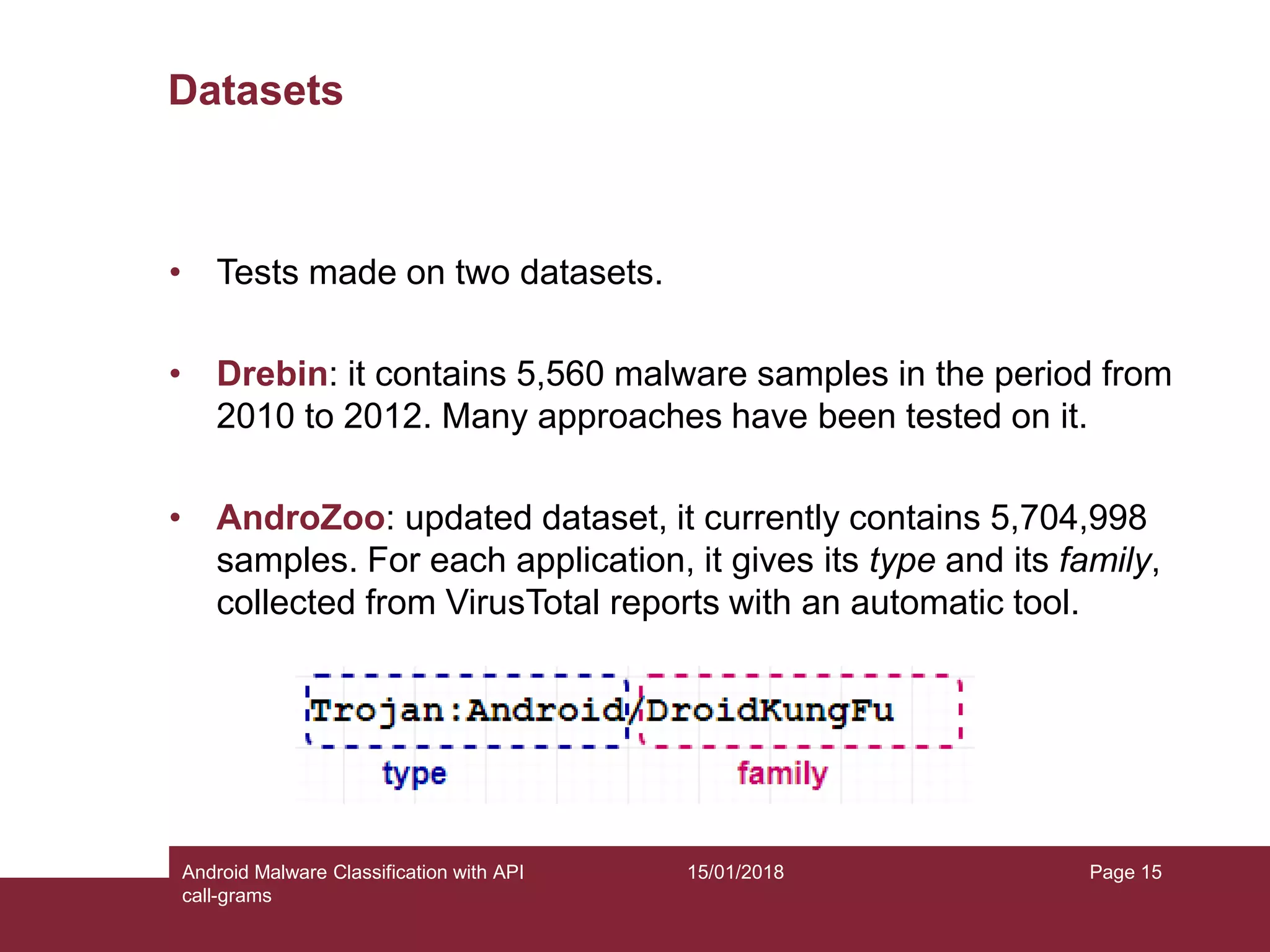
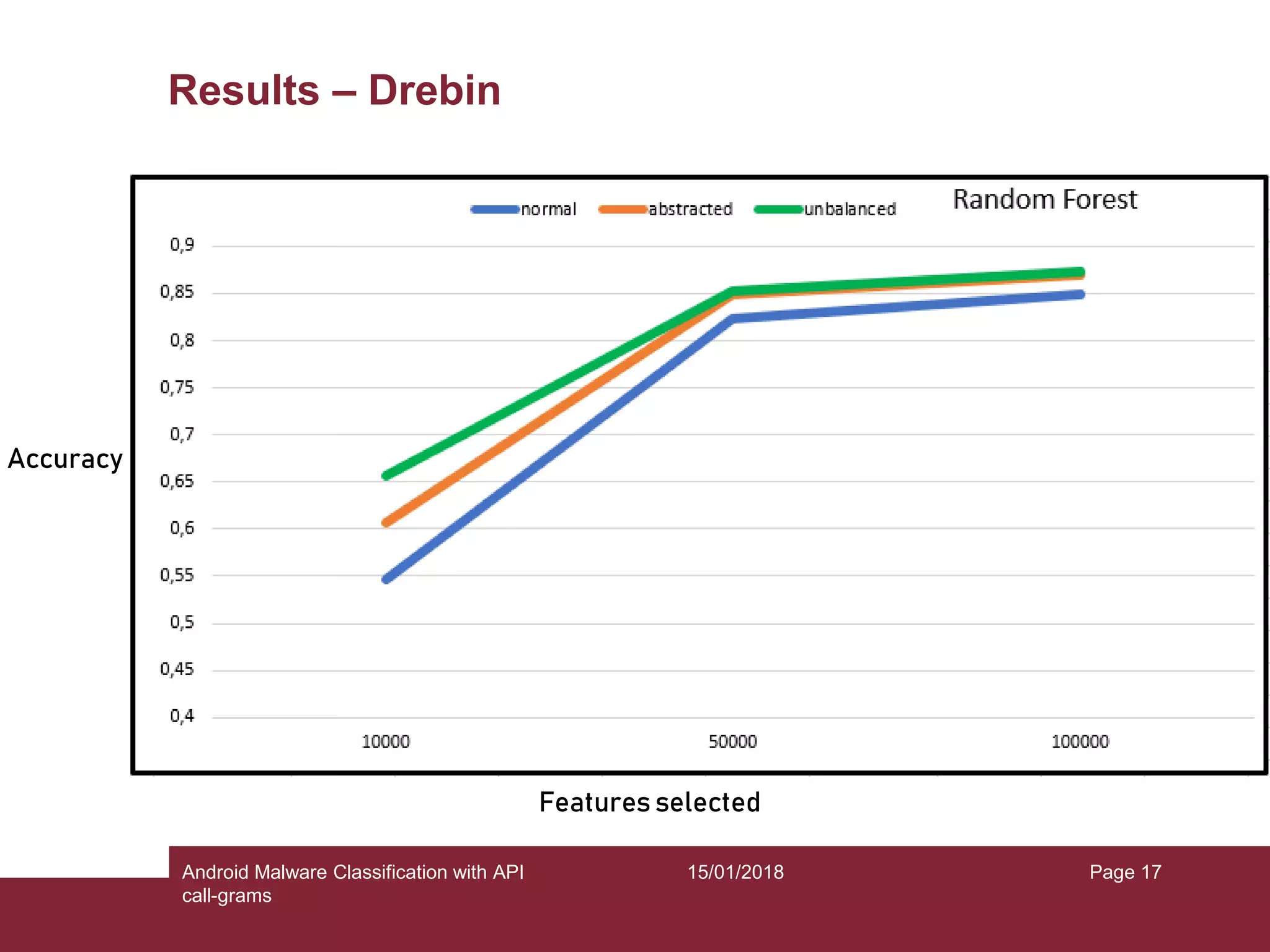
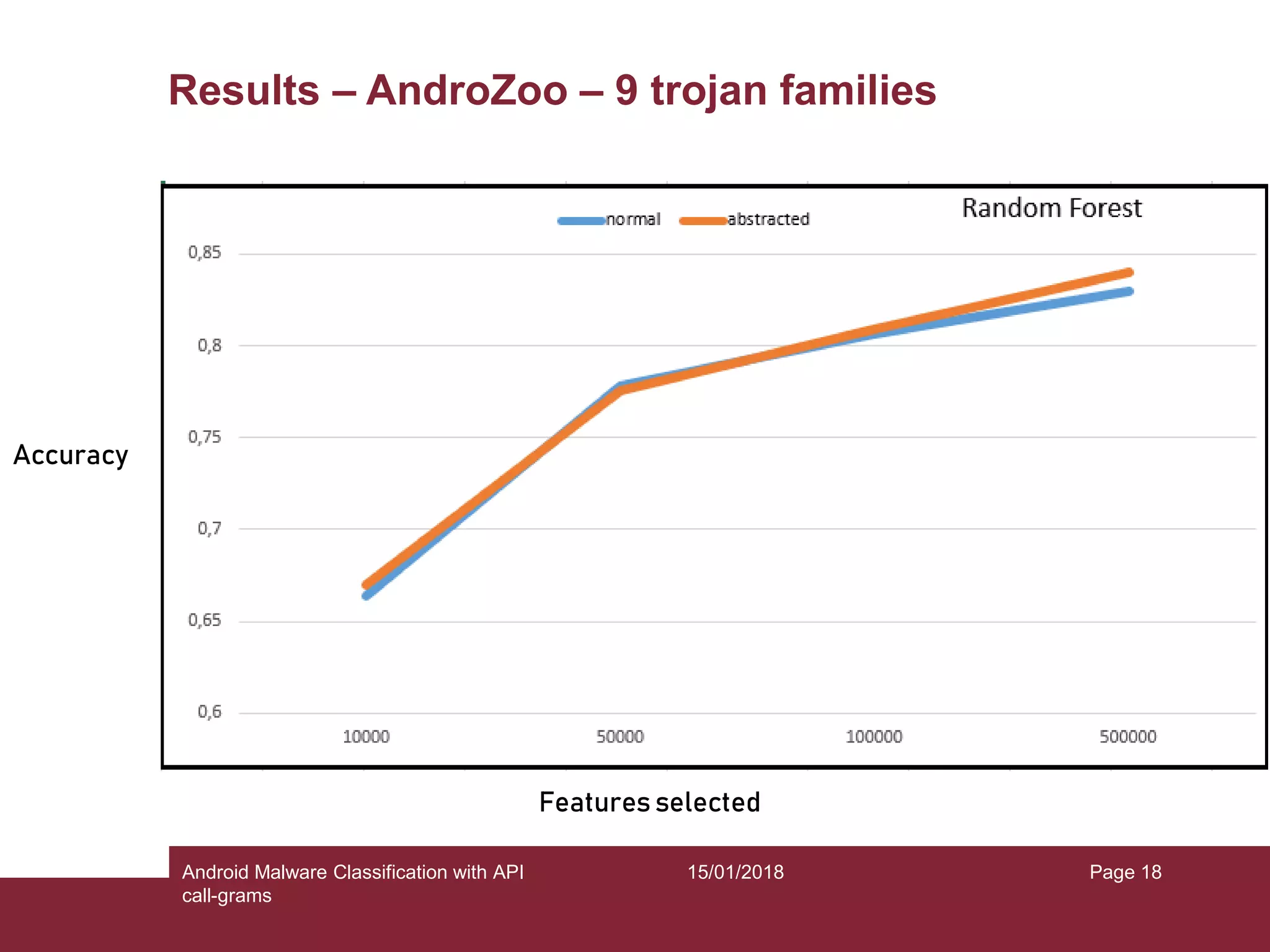
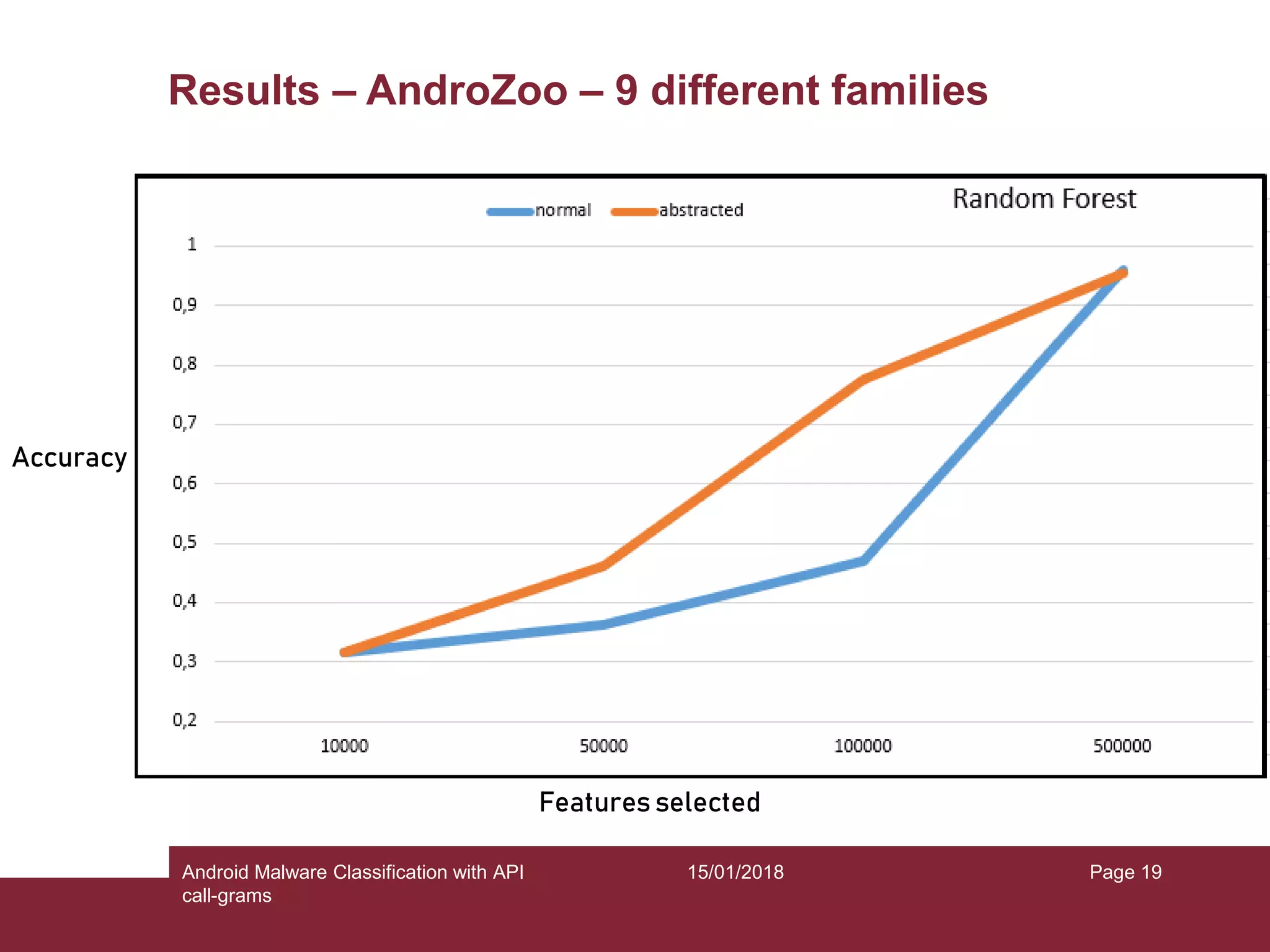
The document discusses the classification of Android malware using API call-grams, highlighting its increase and the vulnerabilities smartphones present. It outlines the methodology for extracting and classifying malware samples through machine learning techniques, featuring datasets like Drebin and AndroZoo. Results indicate accuracies ranging from 82-95% depending on the testing methodology, with recommendations for future research on abstraction levels of API call-grams and other malware types.