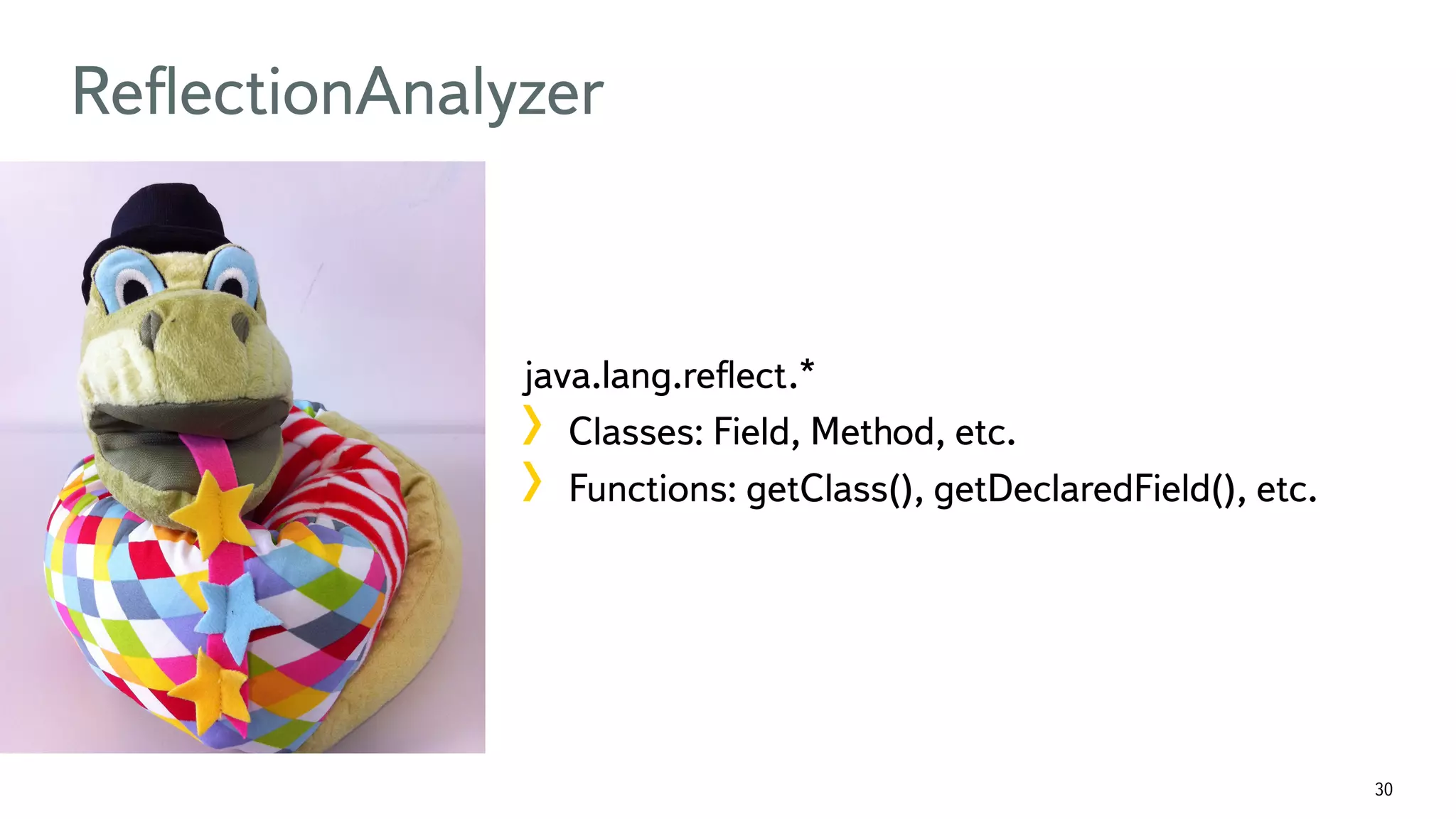
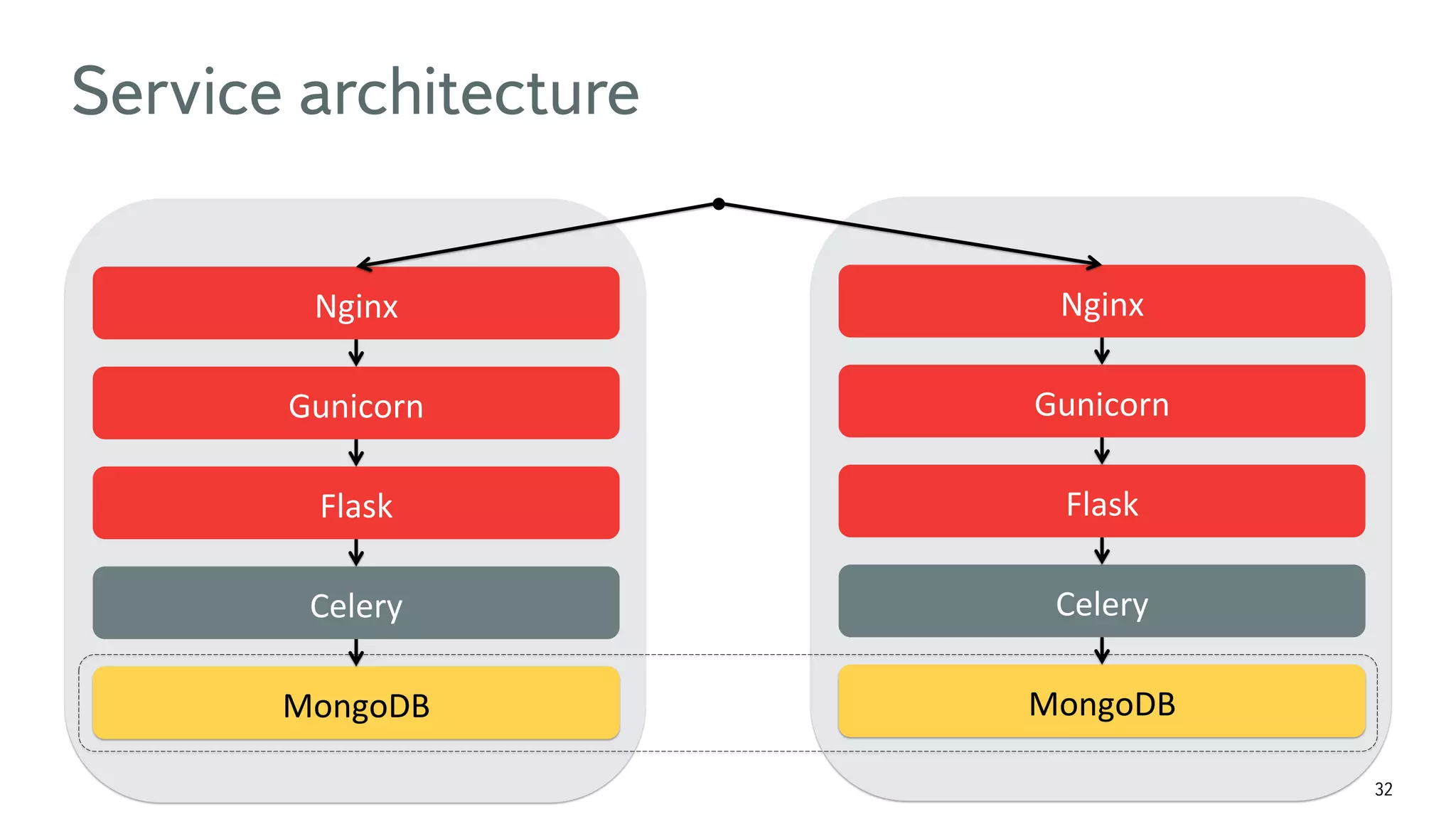
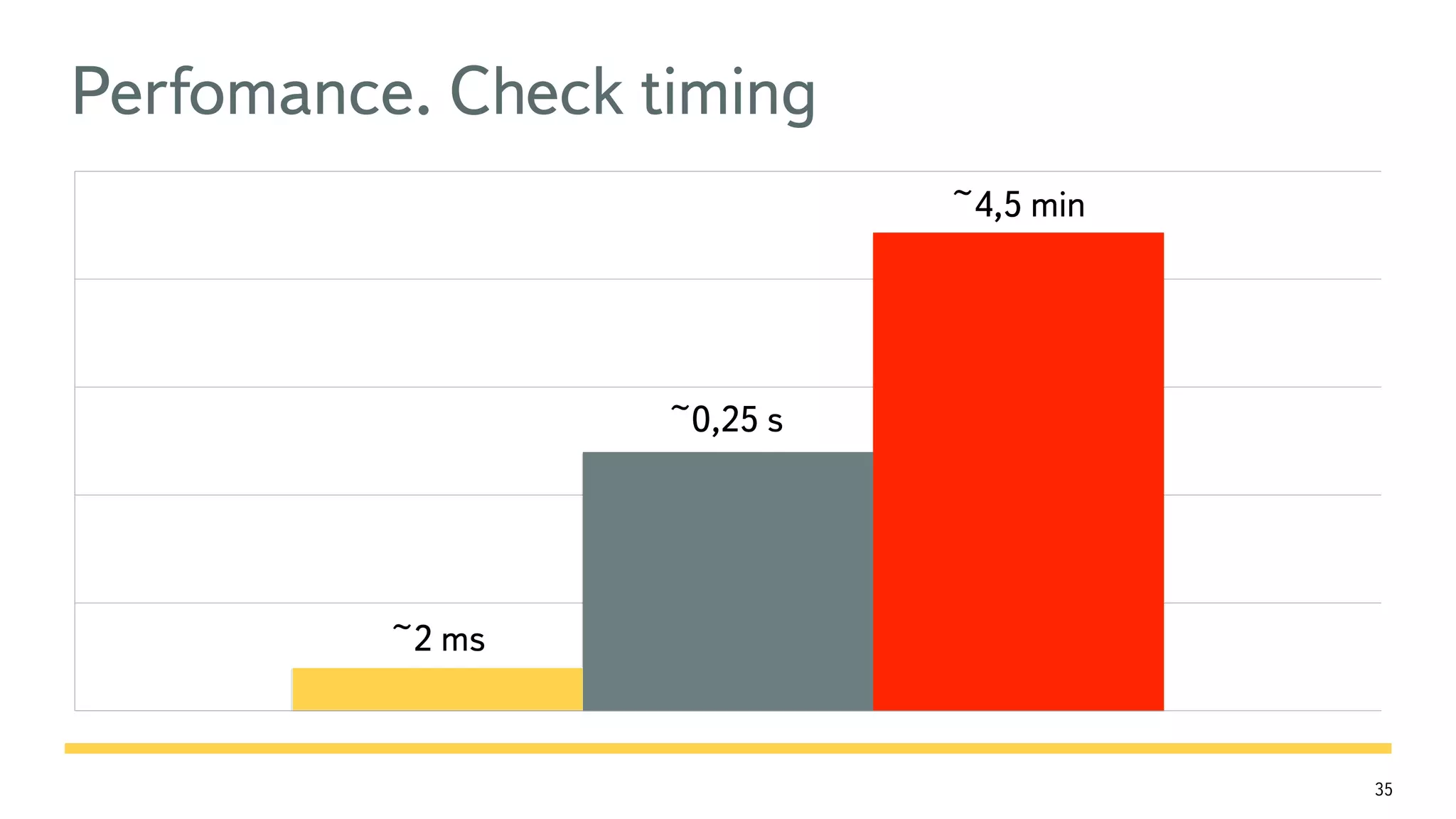
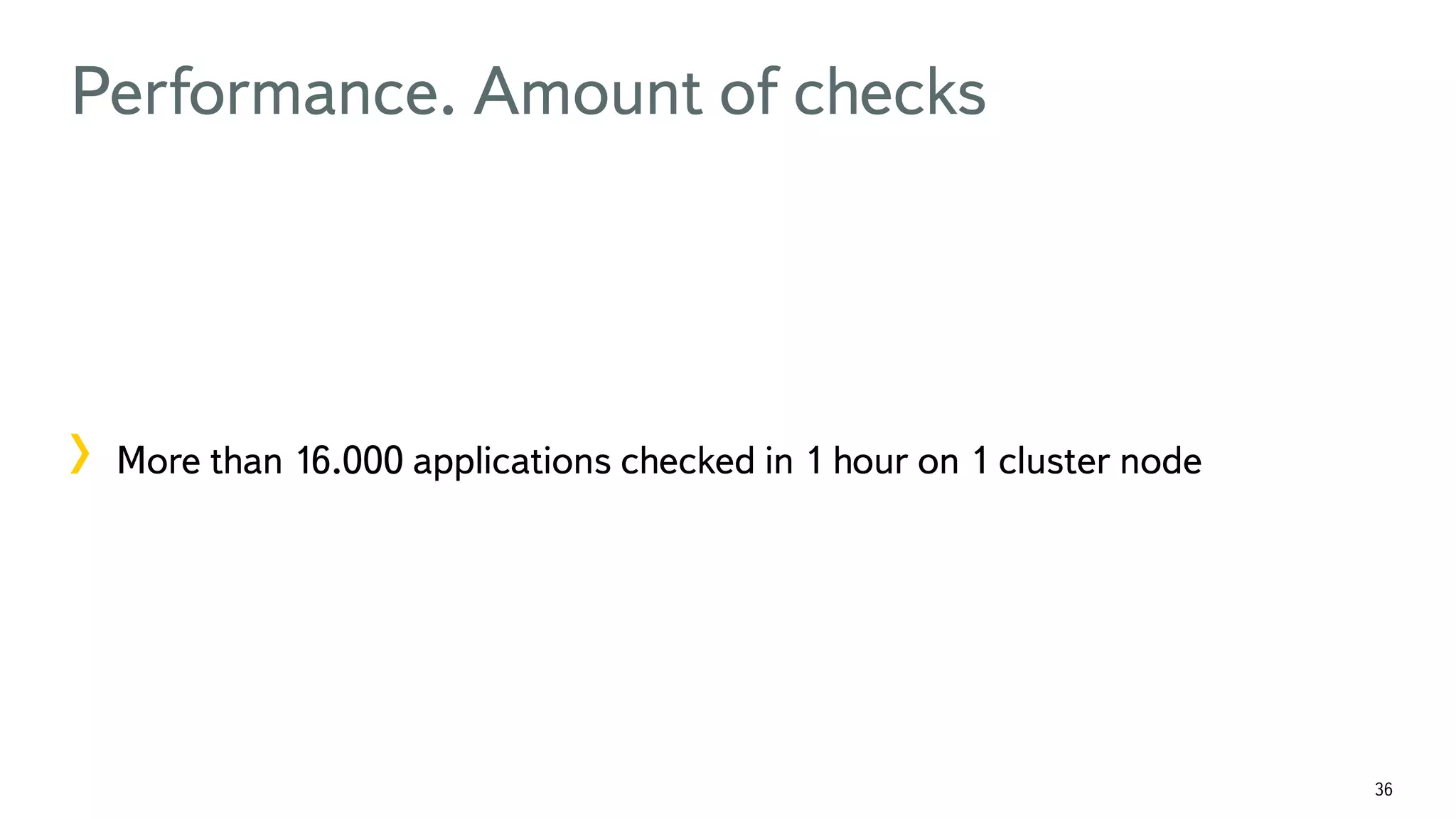
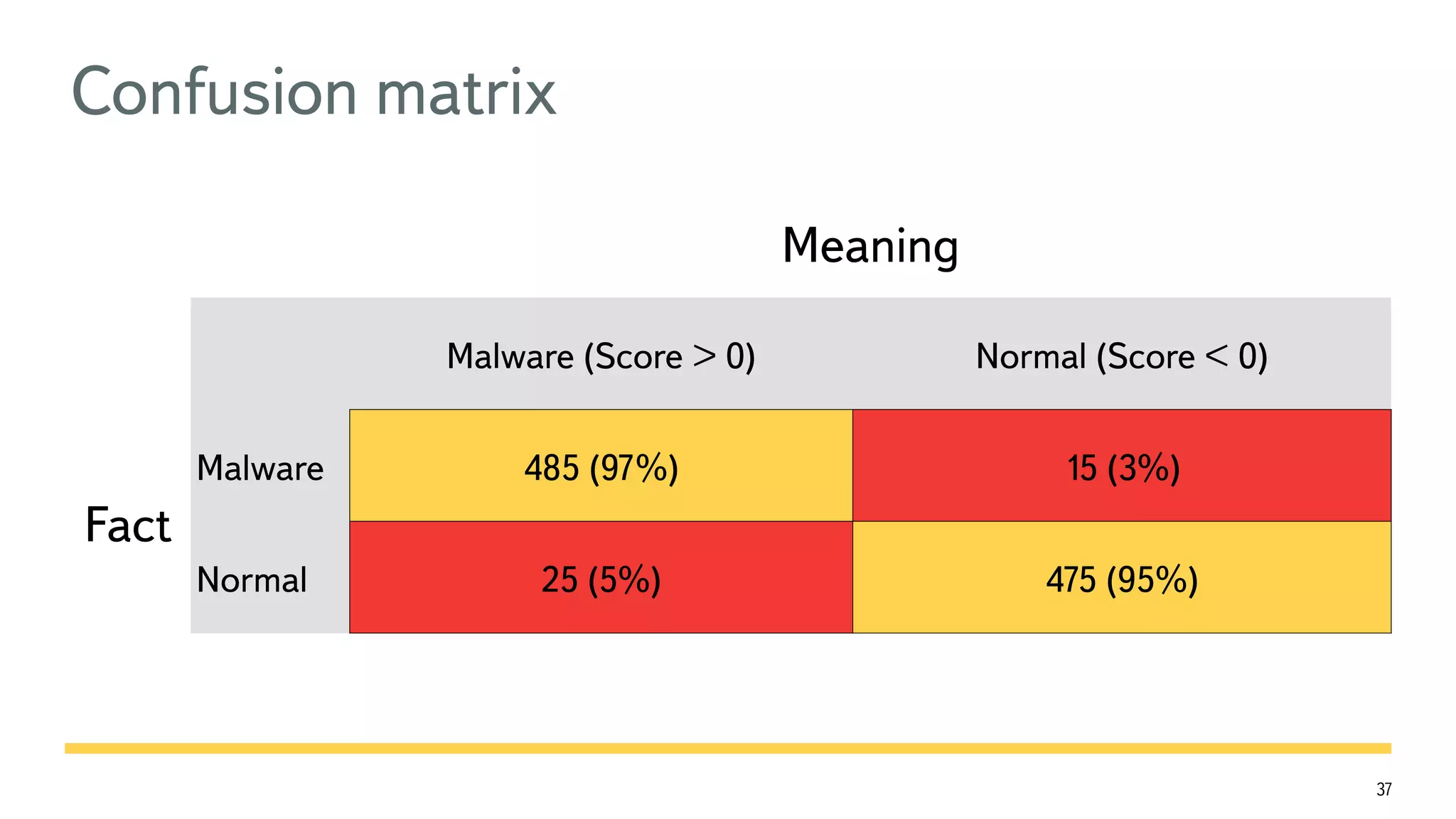
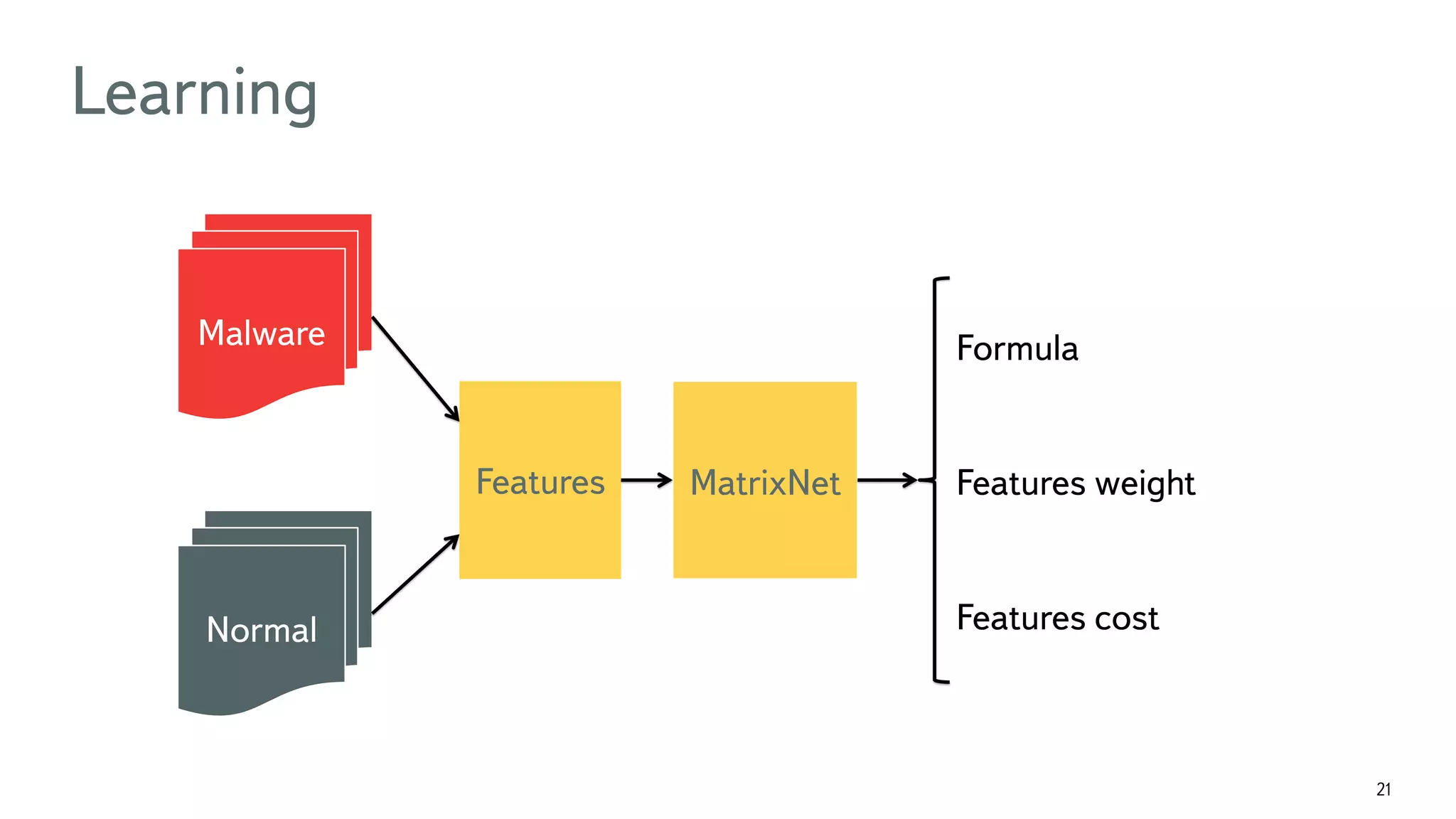
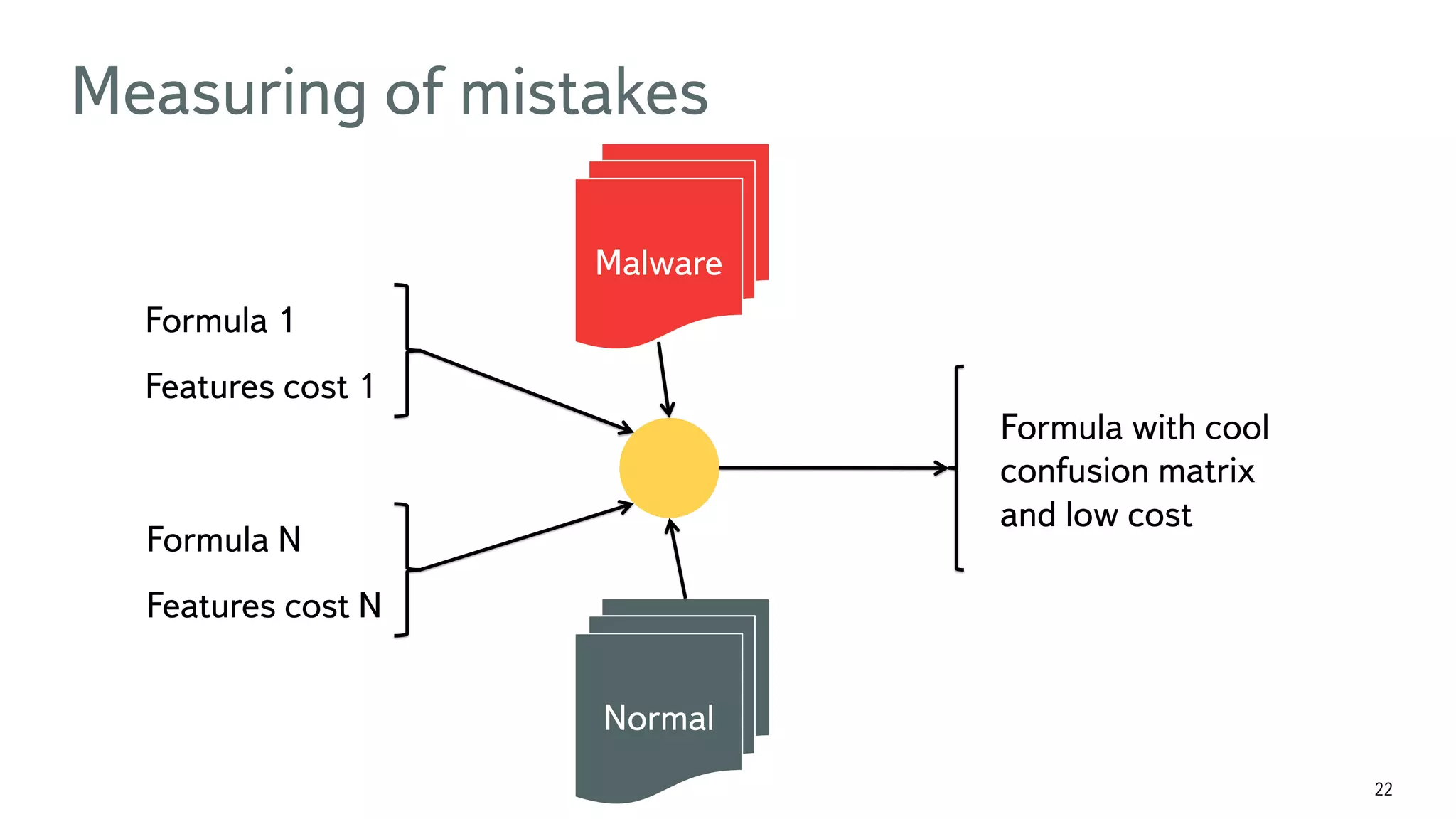
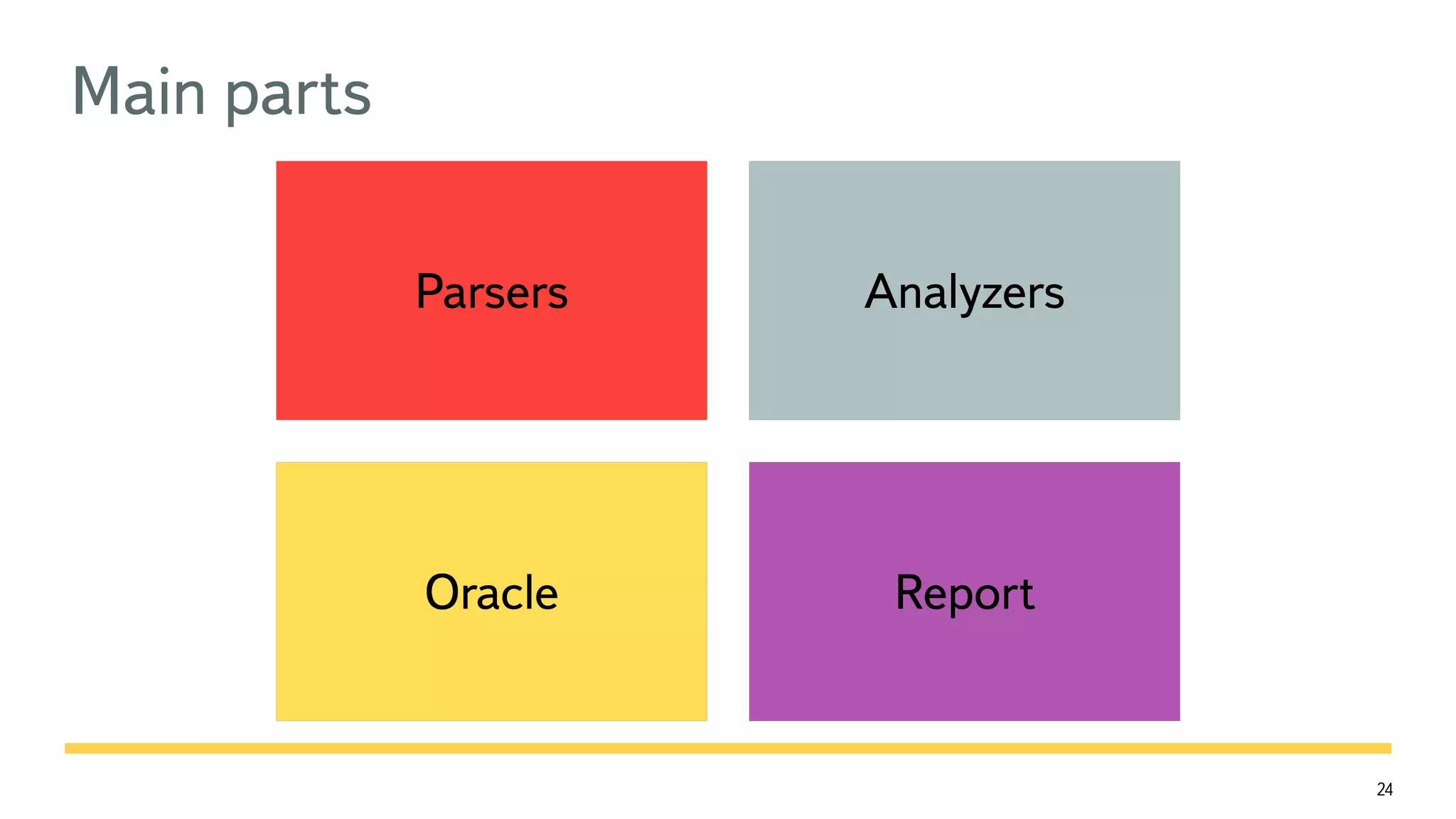
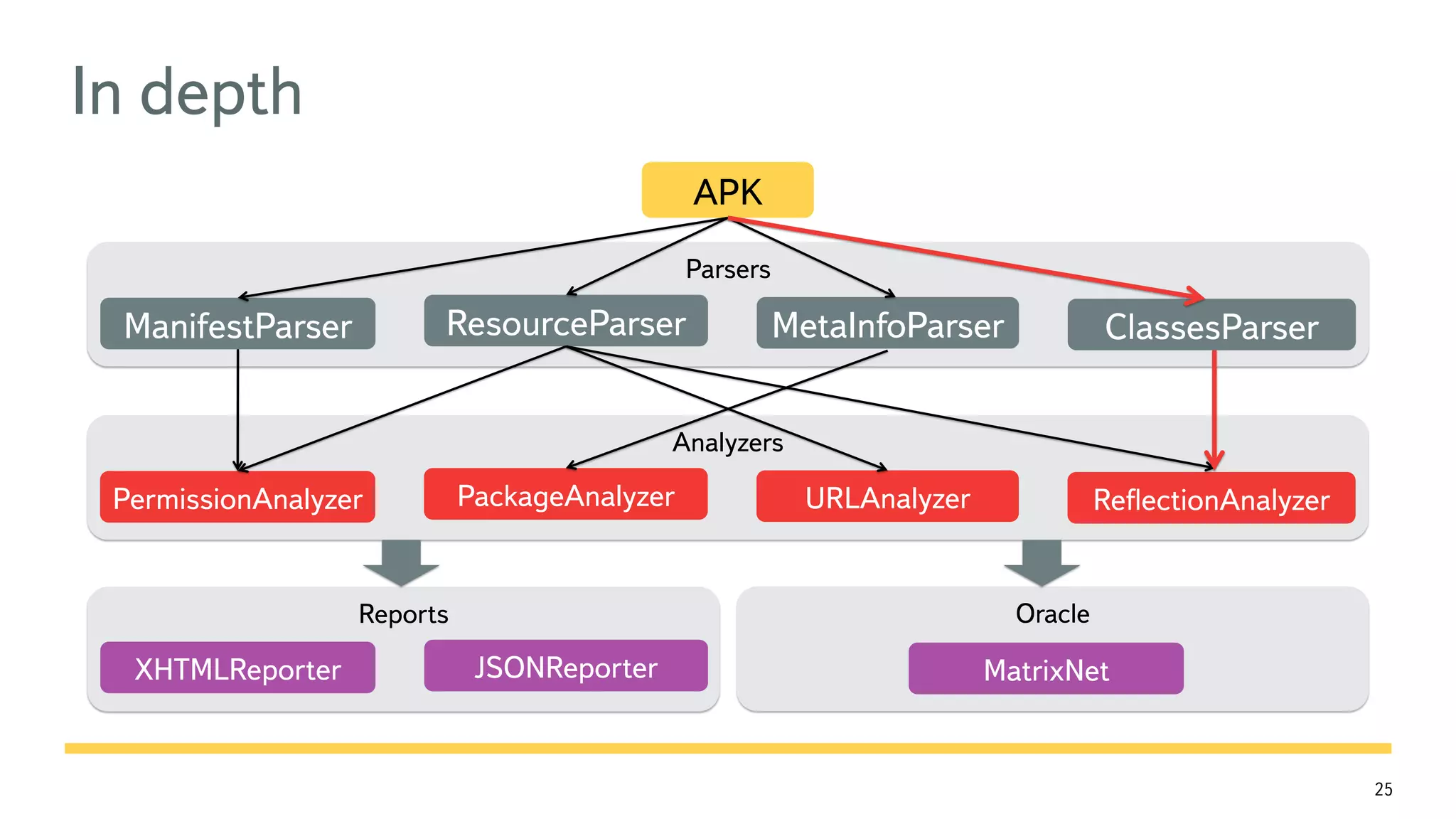
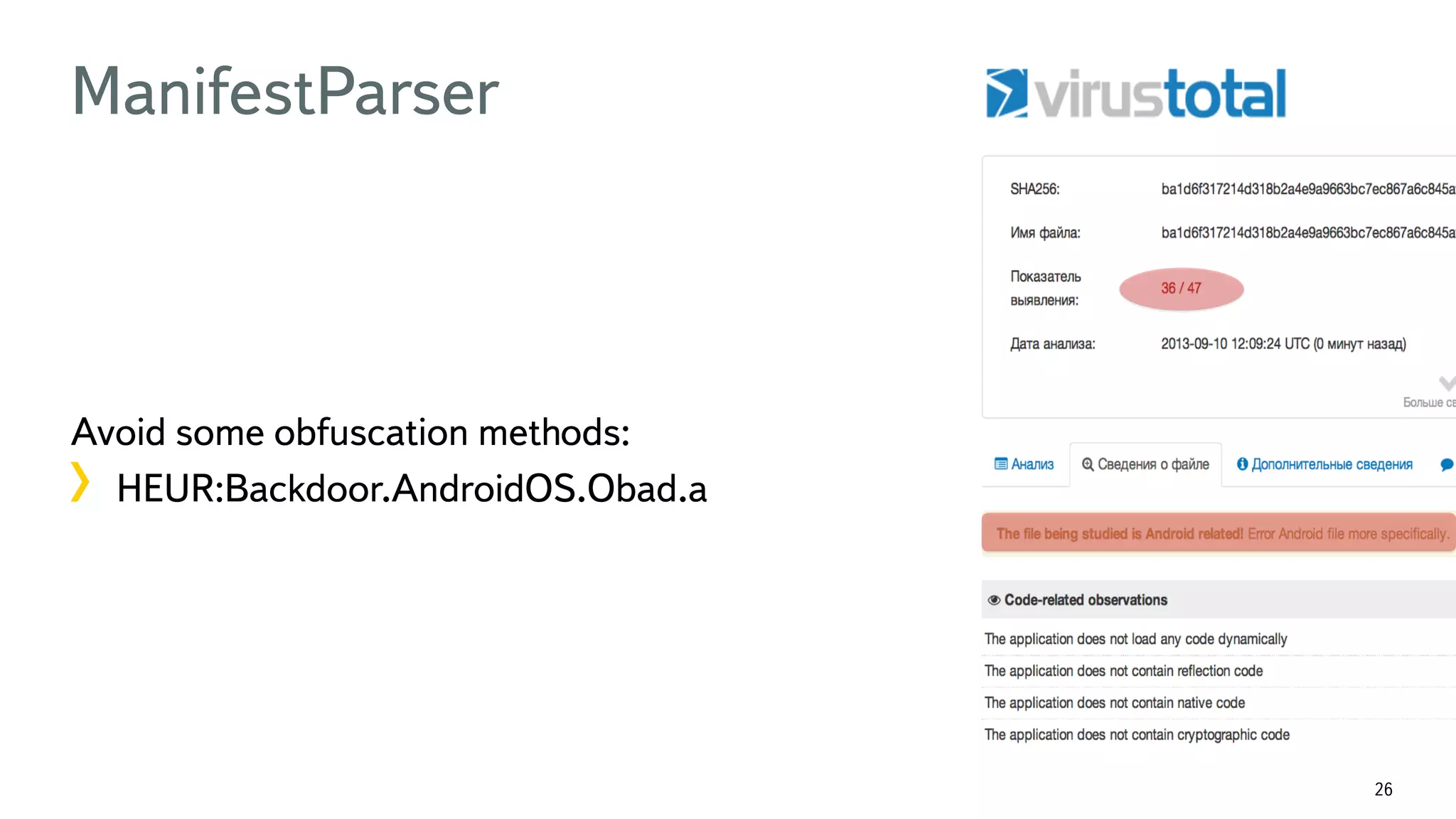
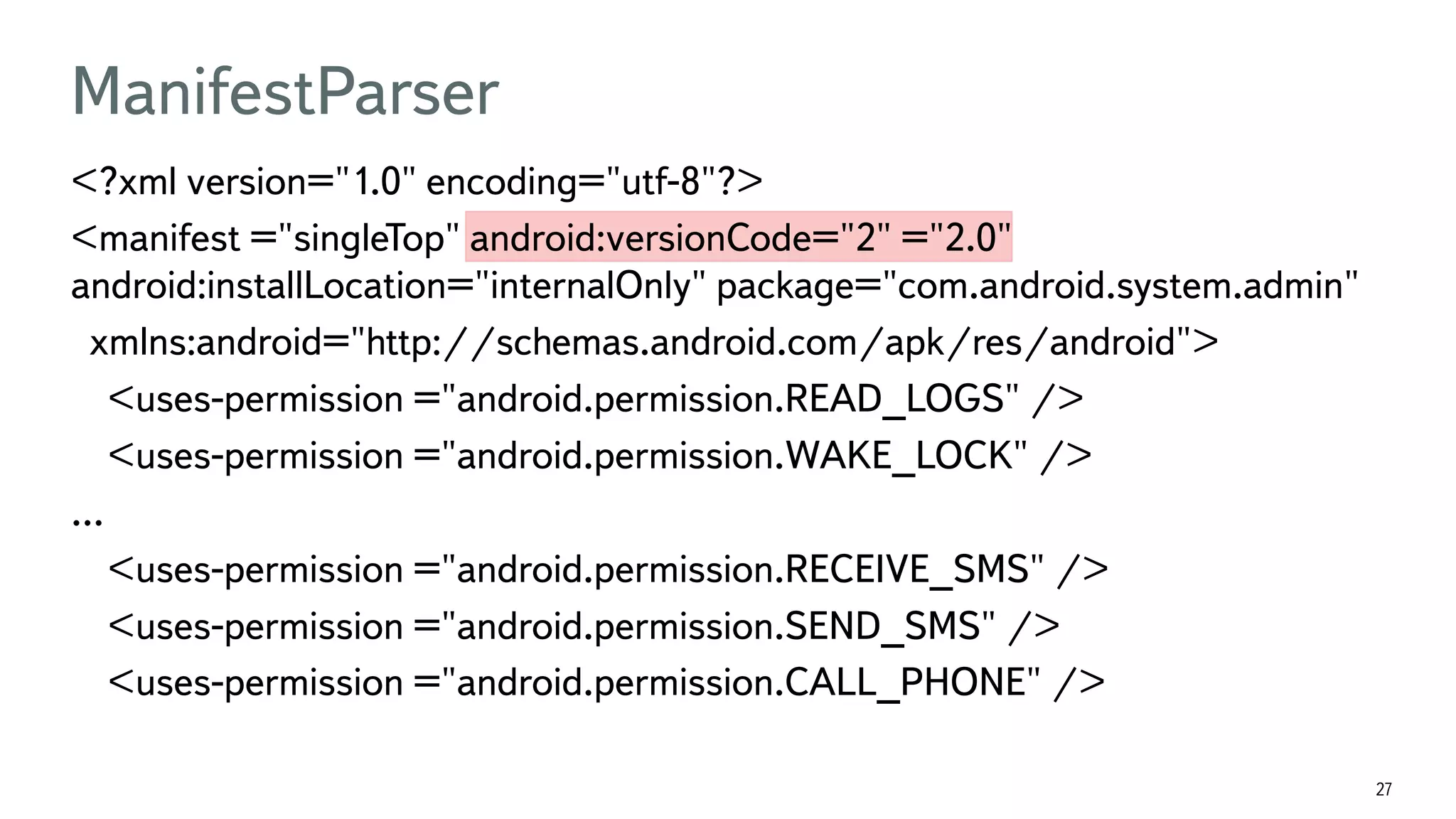
The document discusses the fast detection of Android malware using various analysis techniques, including static, dynamic, and hybrid methods. It highlights the implementation of MatrixNet, a machine learning algorithm based on gradient boosted decision trees, which efficiently classifies APK files as malware or normal based on certain features. The document emphasizes the effectiveness of analytic methods in detecting malware while also addressing the significance of open APIs for future use.











![29 ClassesParser Disassembler https://github.com/tracer0tong/de Example: ./de.py test1.dex.dat [[0, 'sget-object v0, {type} [{class}].{field} // field@2225'], [2, 'invoke-virtual v0 @13970 // {class}->{method}'], [5, 'move-result-object v0'], [6, 'check-cast v0, [{type_name}] // type@0958'], [8, 'return-object v0']]](https://image.slidesharecdn.com/003-android-131001135019-phpapp01-160314104615/75/Fast-detection-of-Android-malware-machine-learning-approach-29-2048.jpg)