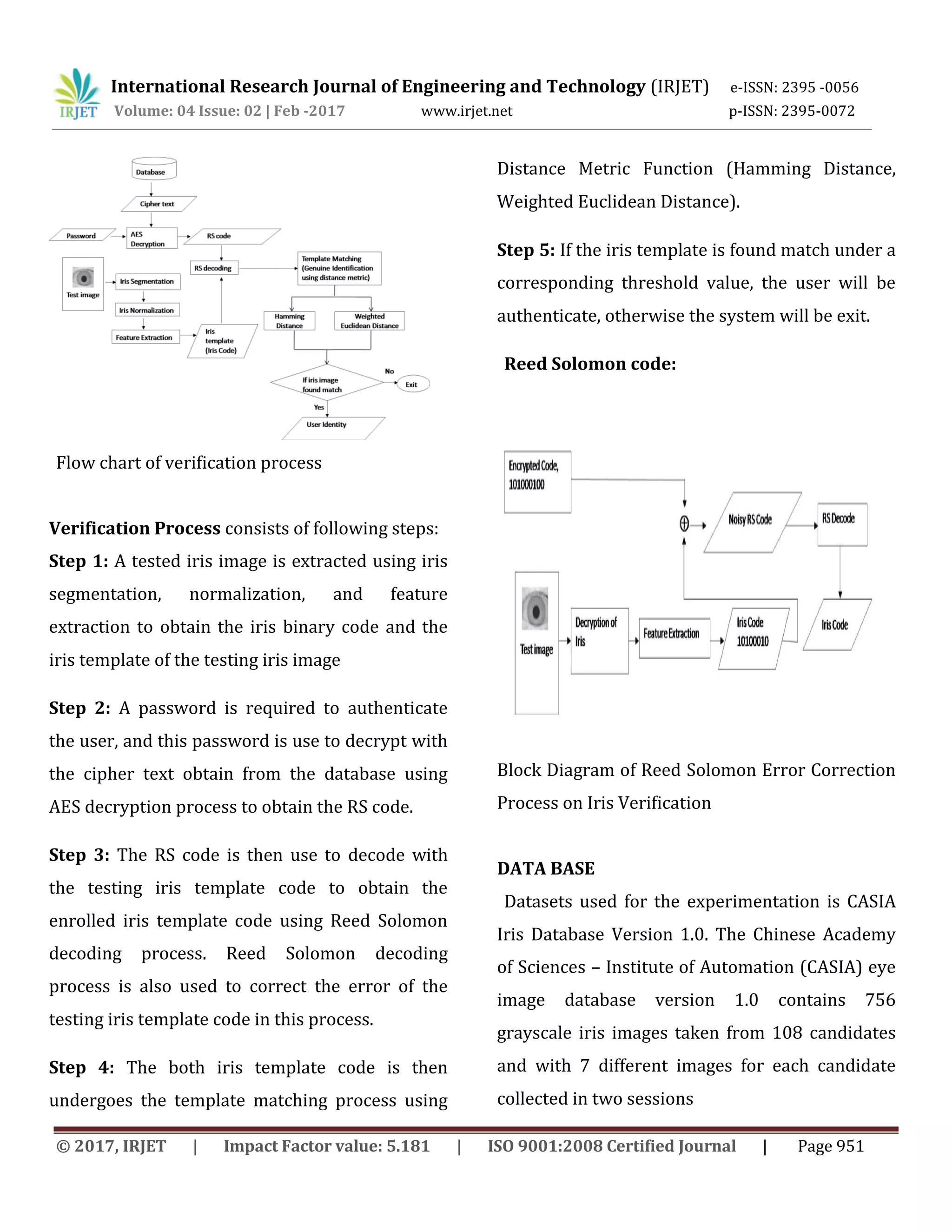
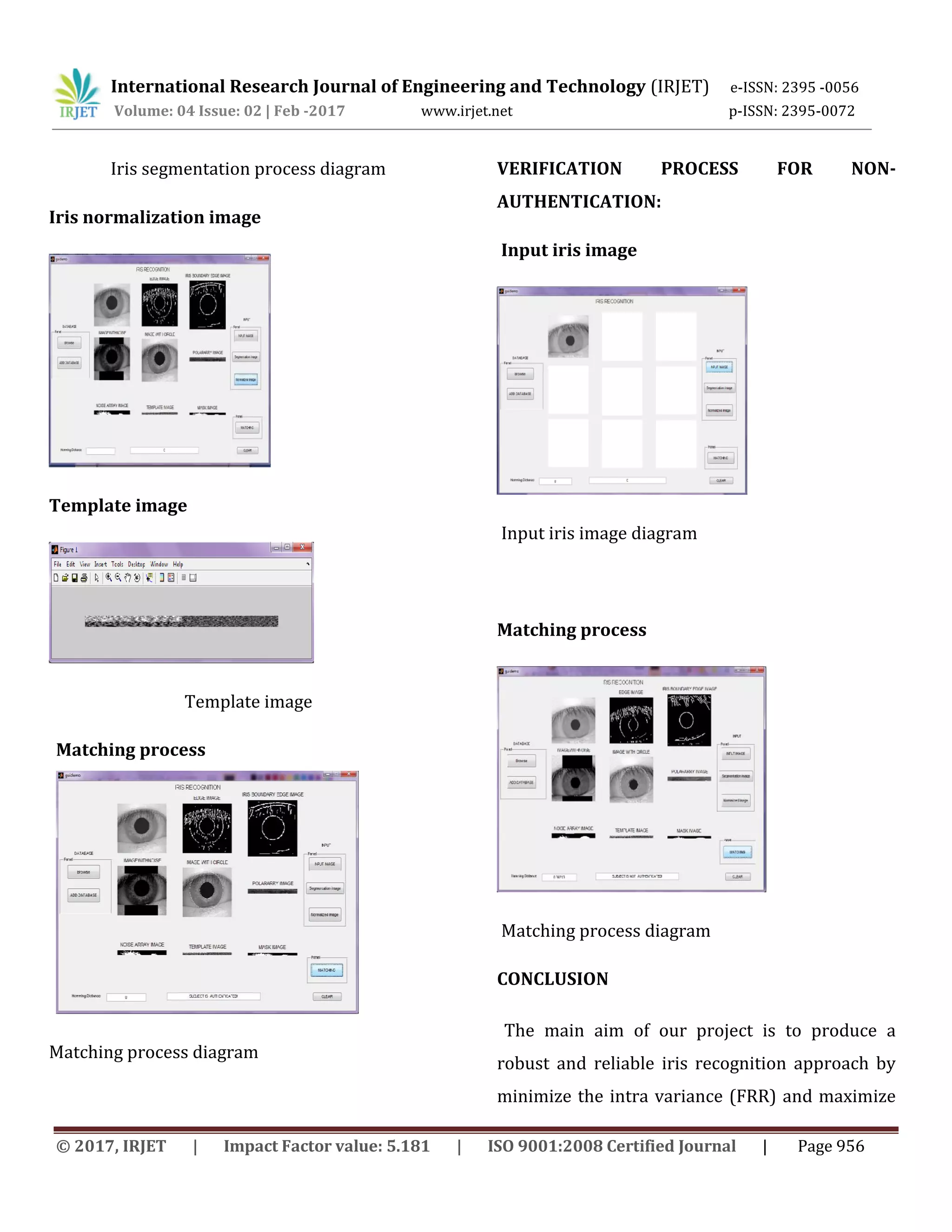
This document summarizes a research paper on using cryptography and error correction codes for iris biometric recognition systems. It discusses how iris biometrics are variable between scans due to noise and errors, compromising security. The paper proposes combining iris biometrics with a password and using error correction codes to correct variations in iris scans and improve recognition accuracy. It describes the enrollment and verification processes, including iris image segmentation, normalization, feature extraction, error correction encoding, encryption, and template matching using Hamming distance and weighted Euclidean distance metrics.









![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395 -0056 Volume: 04 Issue: 02 | Feb -2017 www.irjet.net p-ISSN: 2395-0072 © 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal | Page 957 the inter variance of the iris. Conventional biometric system store templates directly in database, hence if stolen, they will lose permanently and become unusable in that system and other system based on that biometric. In our approach, an iris biometric template is secured using iris biometric and passwords. Error Correction Code, ECC is also introduce to reduce the variability and noisy of the biometric data. The Error Correction Code used in this research is Reed Solomon Codes. Reed Solomon Codes is proven as a very powerful cryptography error correction codes and very suitable for iris biometric cryptography Using Reed Solomon Codes, the FRR is reduced from our previous work [23] of 26% to around 2.92% which enhanced the recognition performance of the iris. Both of the performance is nearly the same between two of the distance metric functions. Among the two distance function which is Hamming Distance and Weighted Euclidean Distance, we found that Hamming Distance provides the best result. Advanced Encryption System (AES) is utilized to assure a more secured transaction on the password. With the combination of password usage, the security of the iris biometric authentication has also increase to a higher level. The security of AES has been identified as a world standard algorithm that has been used for many protections on sensitive information. Since this is the preliminary works, only one dataset has been used for the experimental results, different dataset of the iris will be tested in the future. REFERENCE [1] John Daugman, University of Cambridge, How Iris Recognition works. Proceedings at International conference on Image Processing. [2] Reed I. S. and Solomon G., “Polynomial Codes Over Certain Finite Fields” SIAM Journal of Applied Mathematics, Volume 8. [3] Wildes, R.P.: Iris Recognition: An Emerging Biometric Technology. Proceedings of IEEE 85, 1348–1363 (1997). [4] Pattraporn A., Nongluk C., “An Improvement of Iris Pattern Identification Using Radon Transform,” ECTI Transactions On Computer And Information Technology, vol. 3, No.1 May 2007, pp.45–50. [5] Wu, X., Qi, N., Wang, K., and Zhang, D., “ A Novel Cryptosystem Based on Iris Key Generation”. In Proceedings of the 2008 Fourth international Conference on Natural Computation - Volume 04 (October 18 - 20, 2008). ICNC. IEEE Computer Society, Washington, DC, 53-56.](https://image.slidesharecdn.com/irjet-v4i2183-171117095202/75/Cryptography-and-error-correction-code-for-iris-biometric-recognition-system-12-2048.jpg)