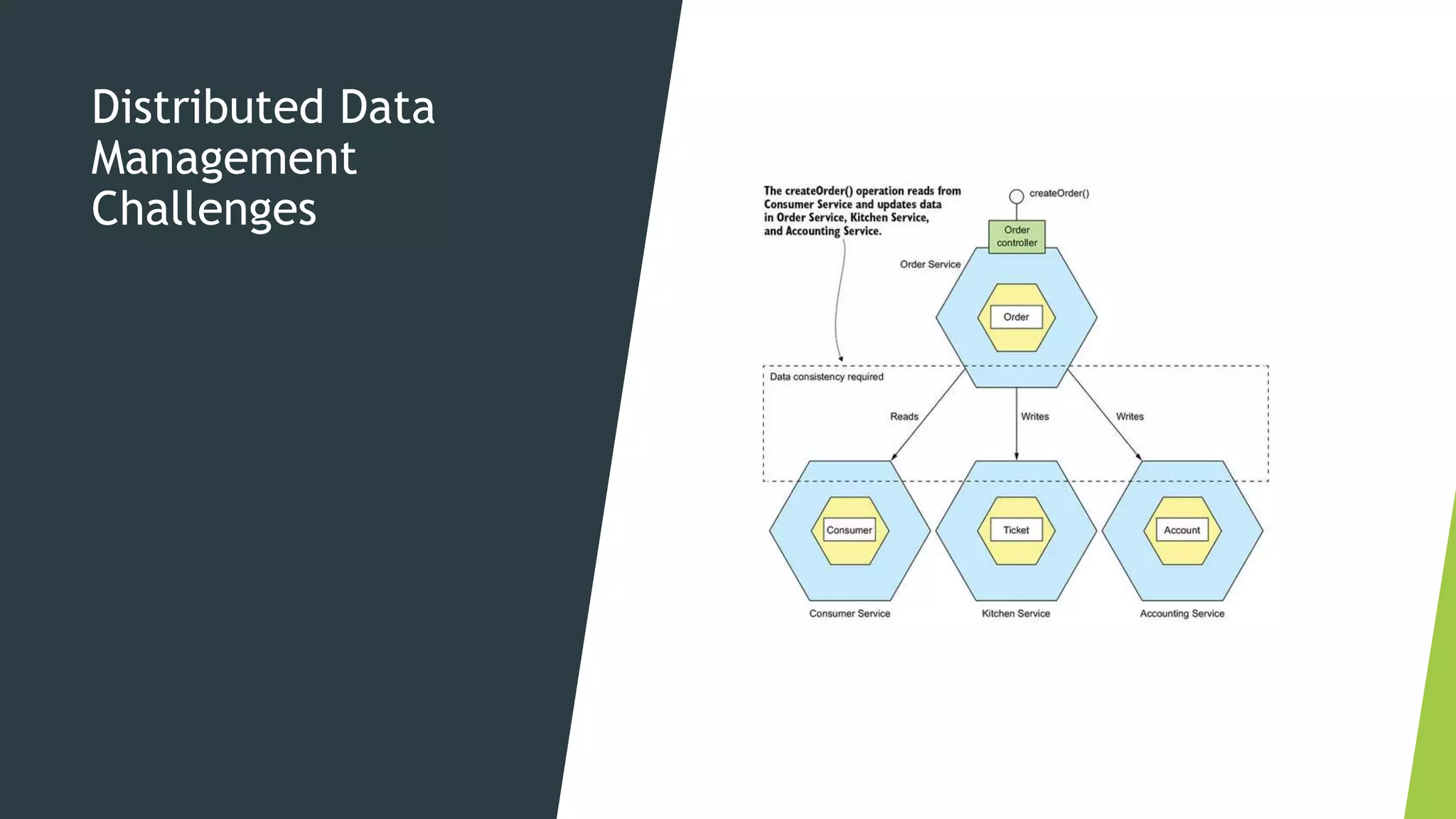
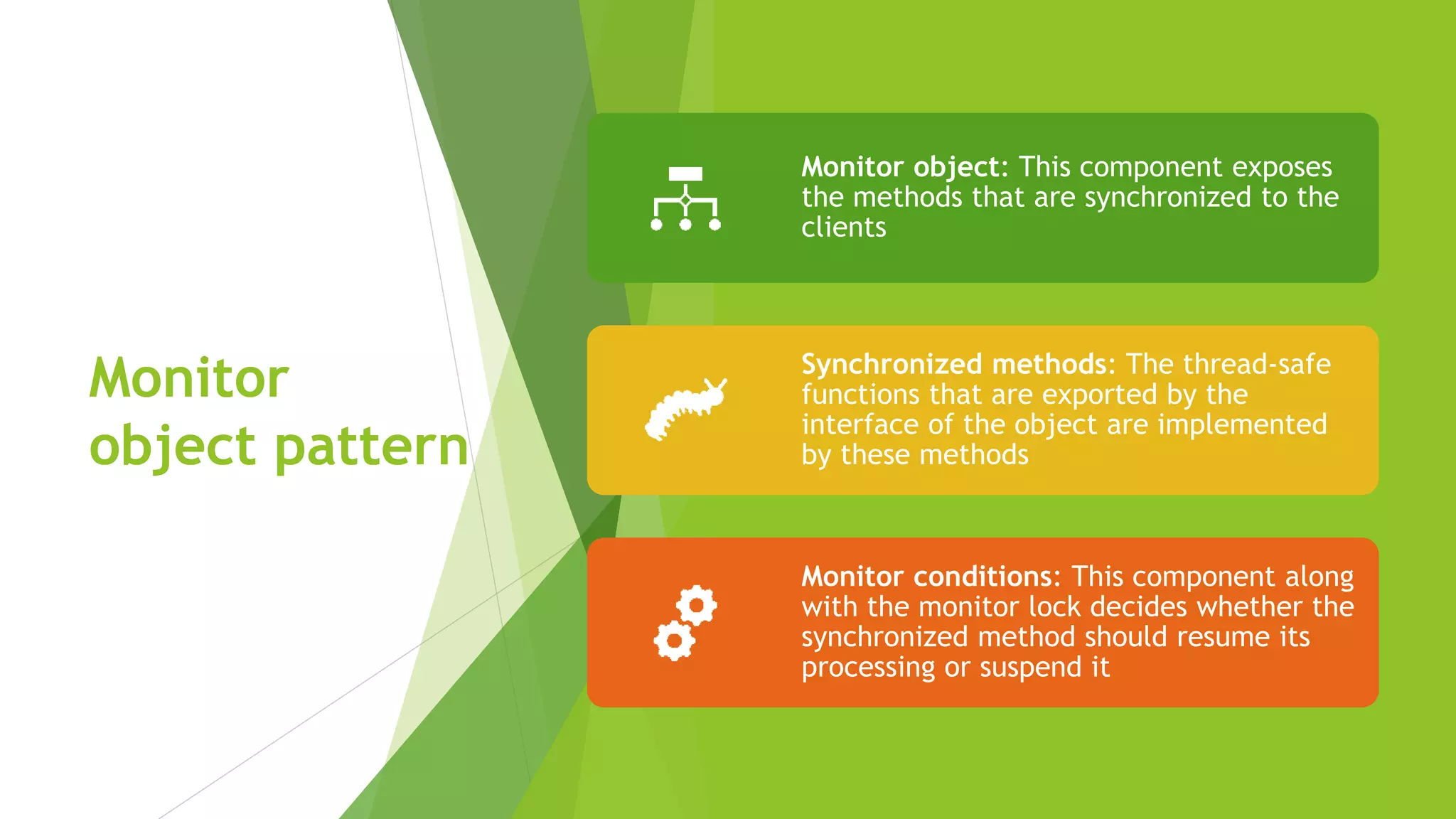
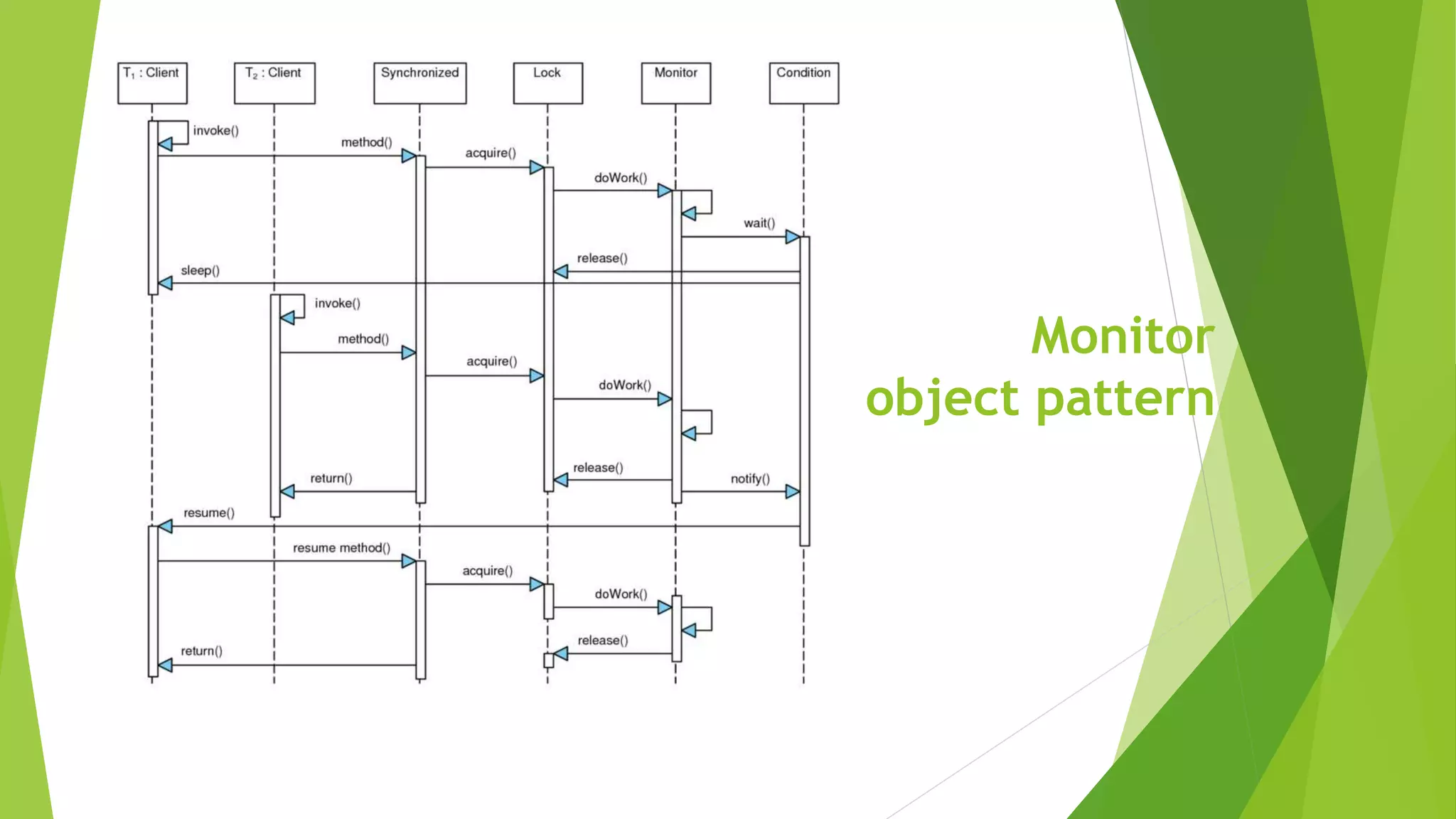
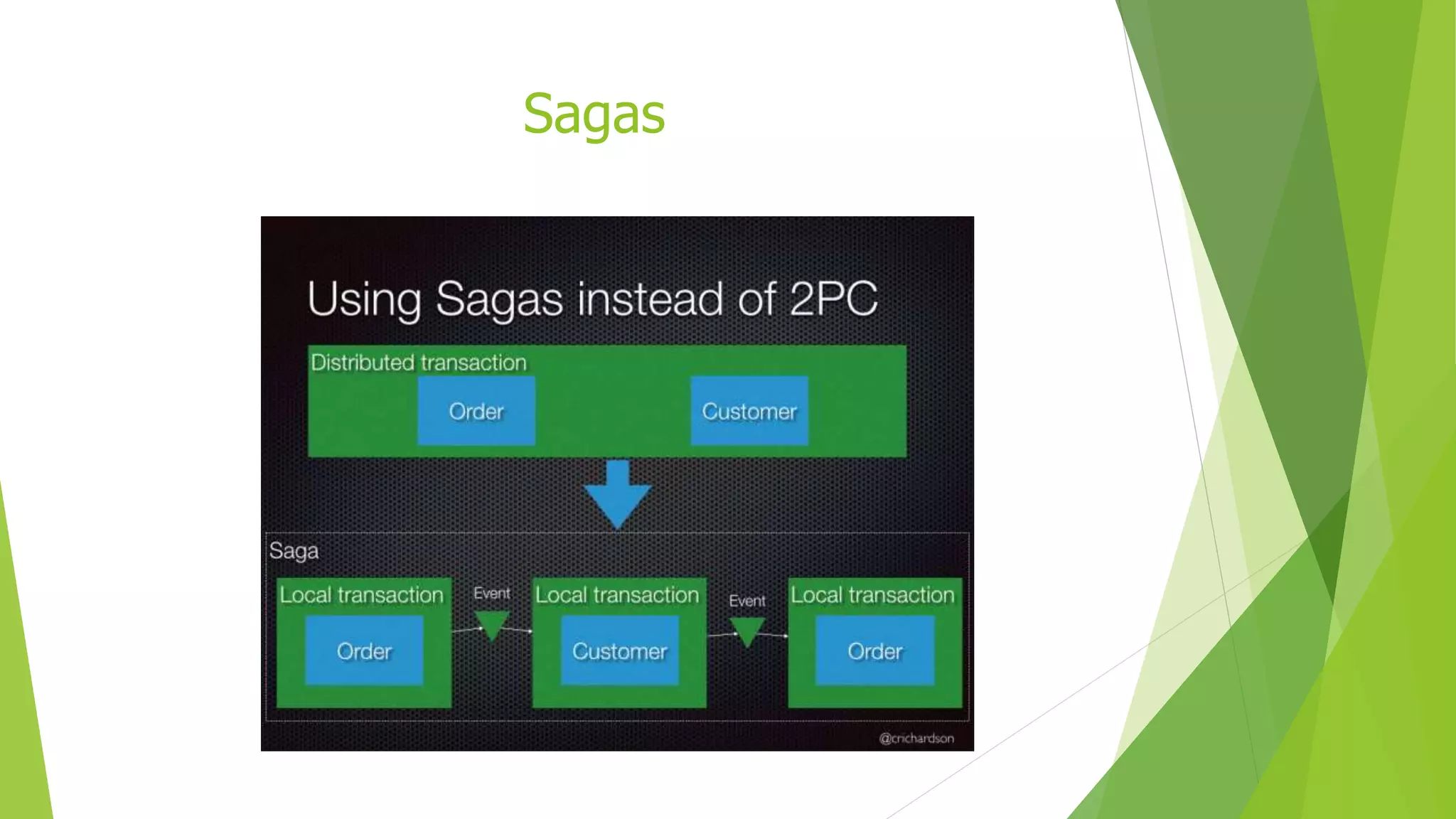
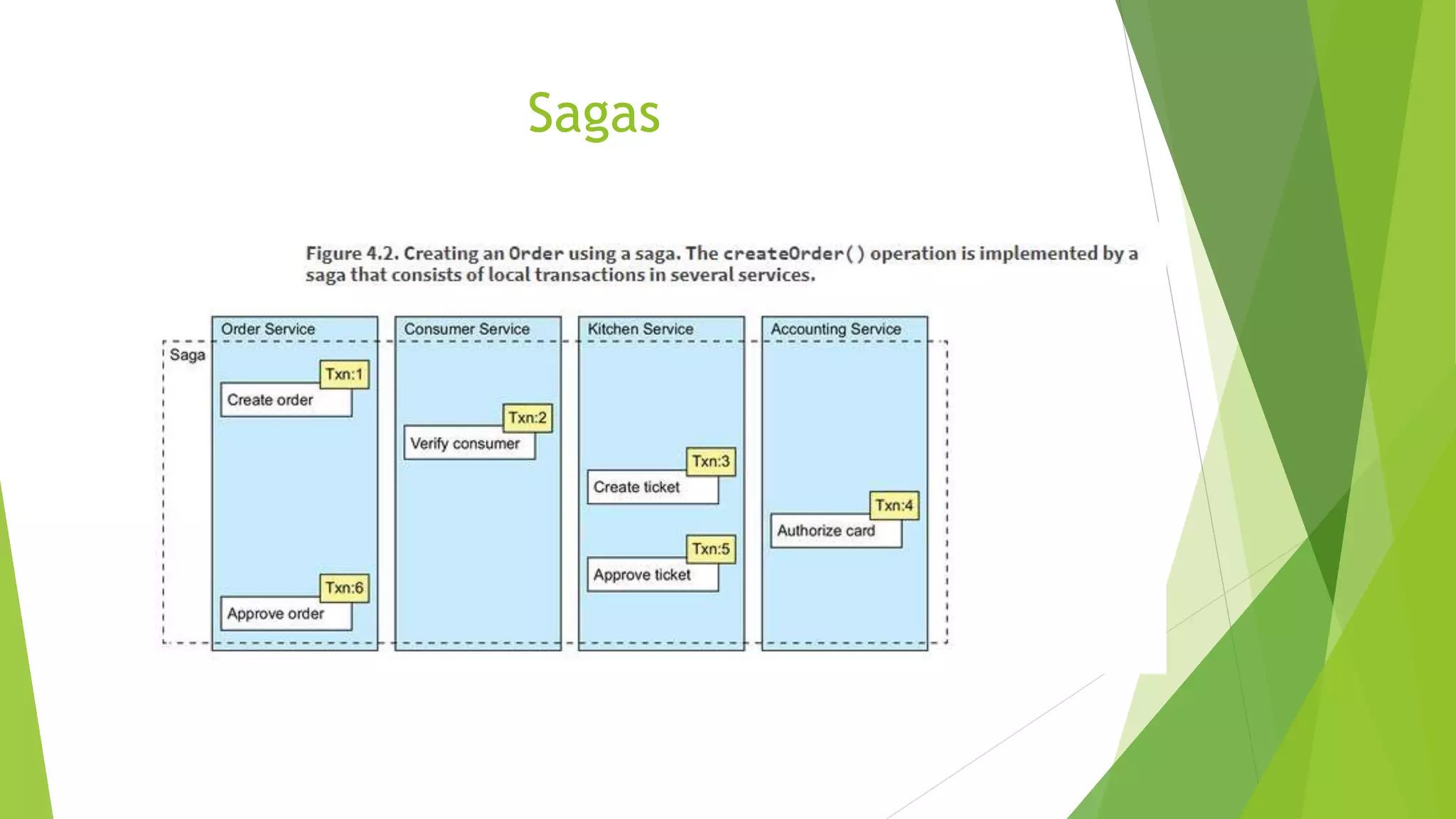
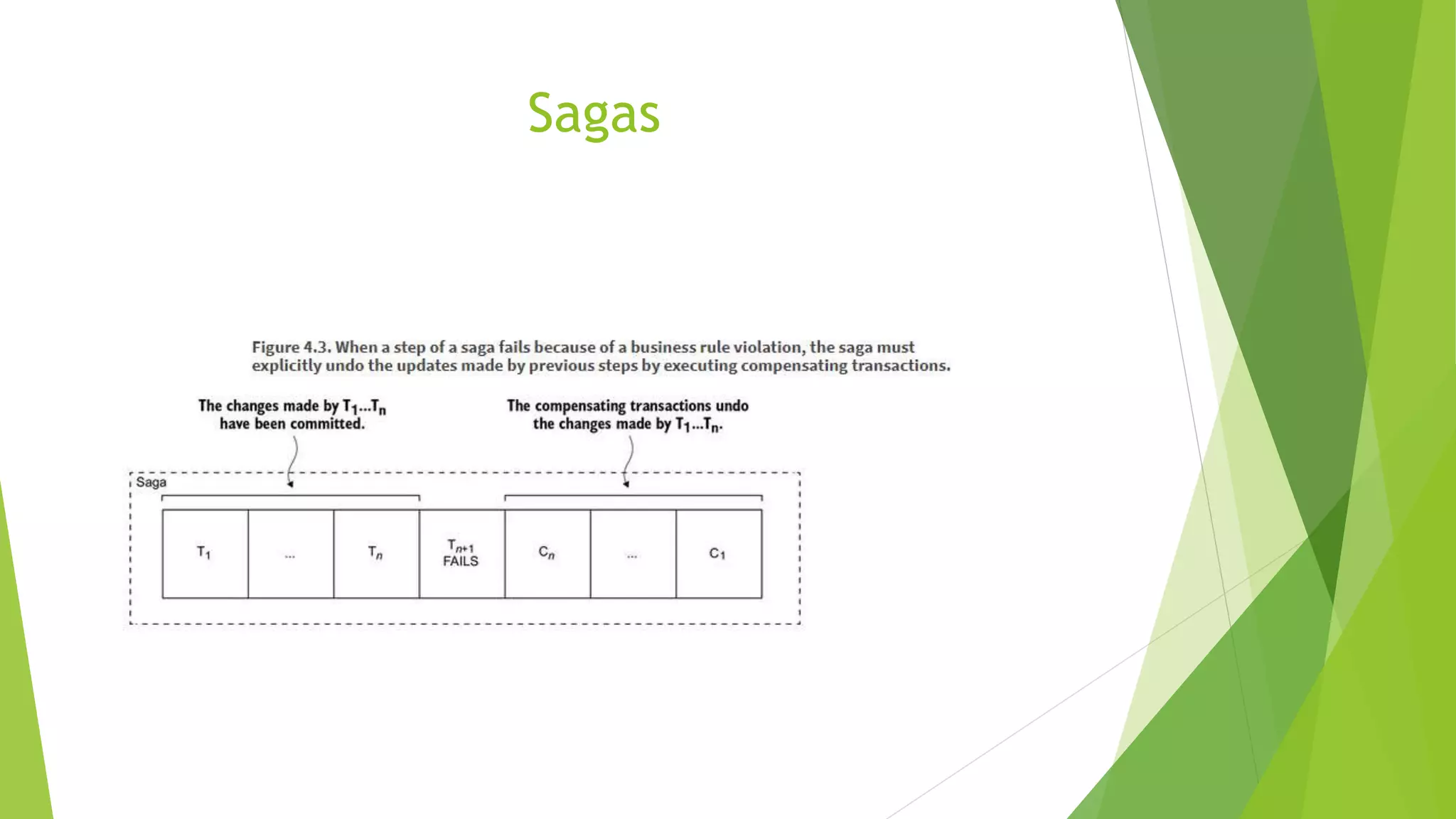
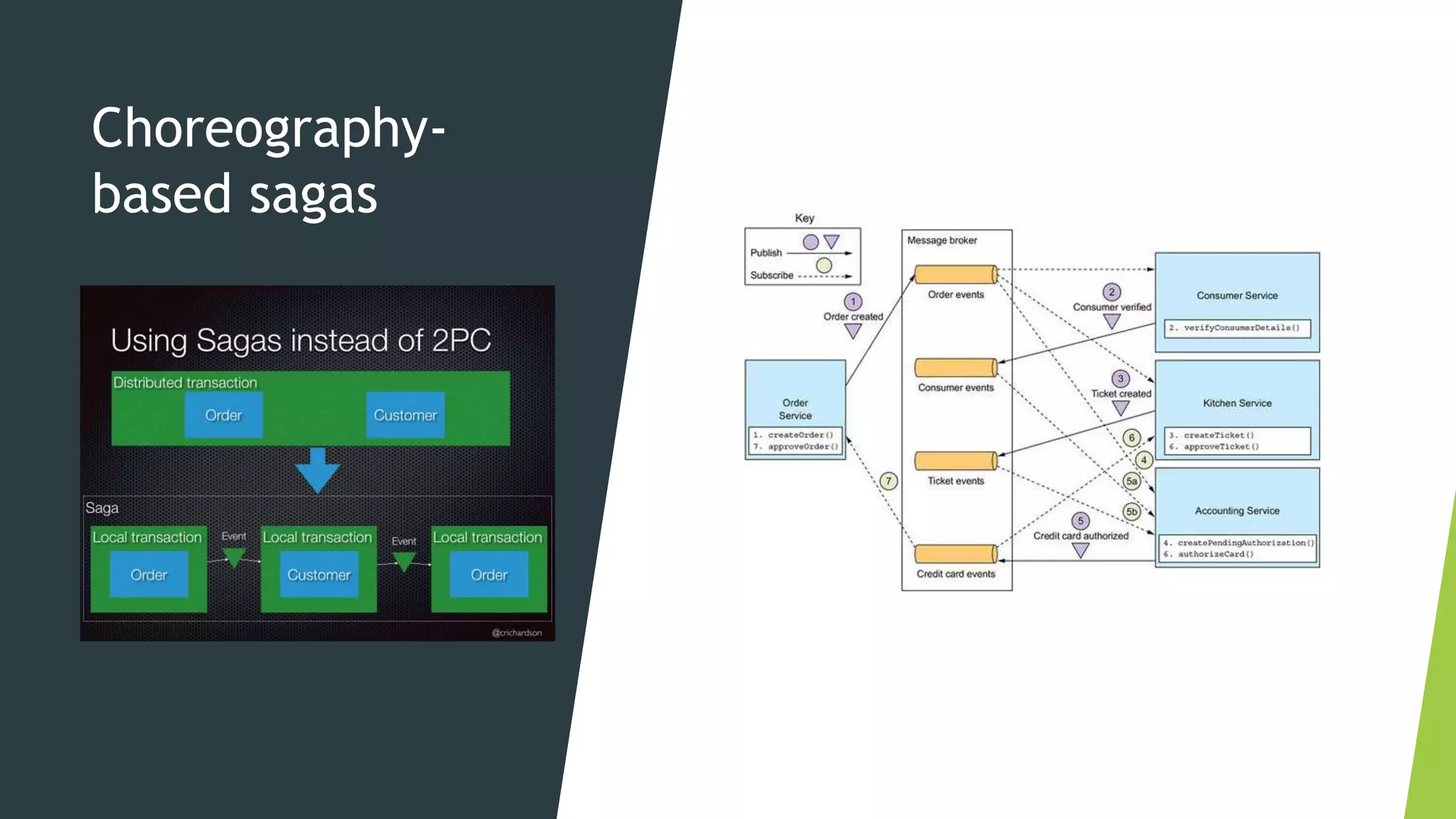
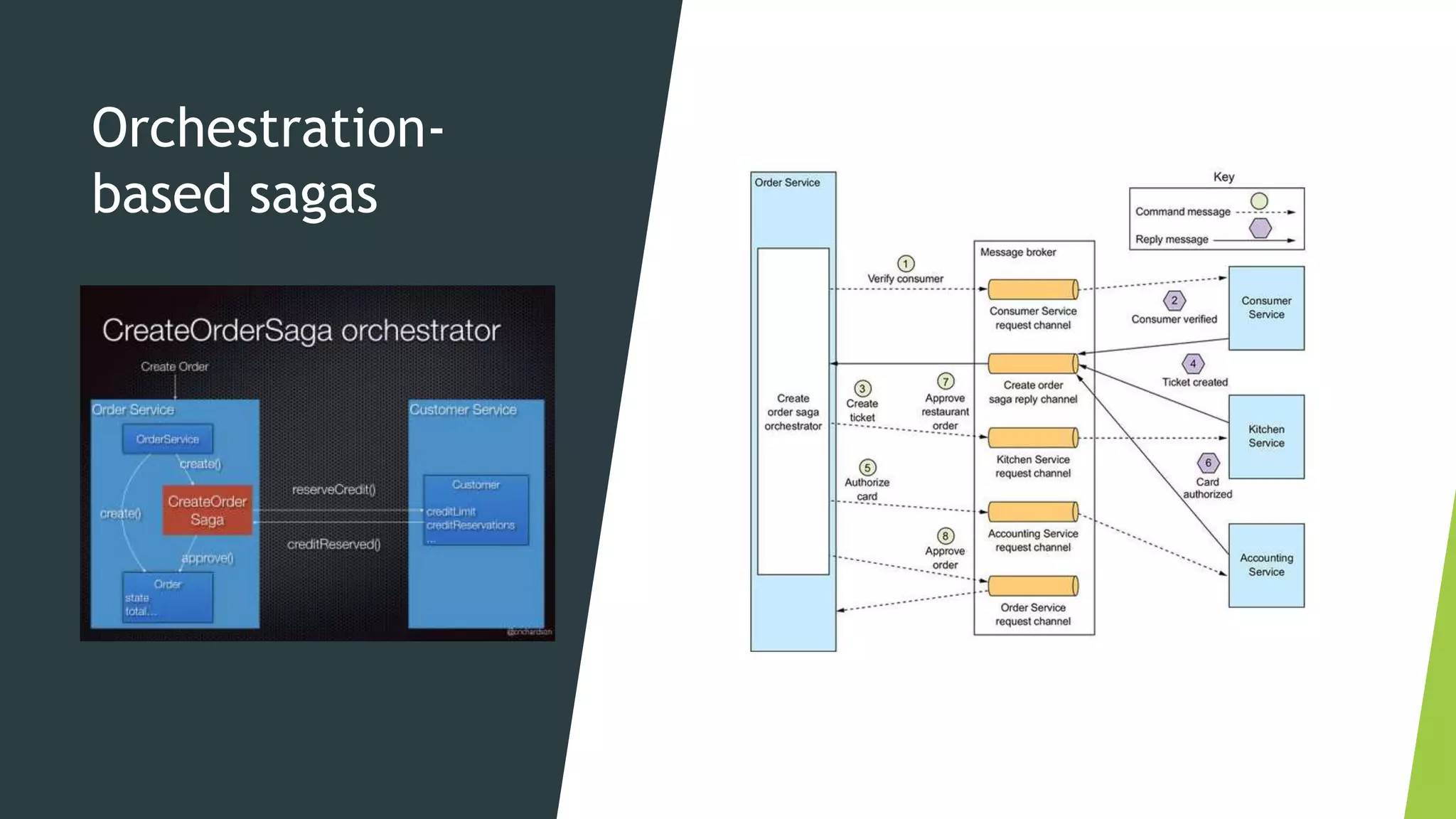
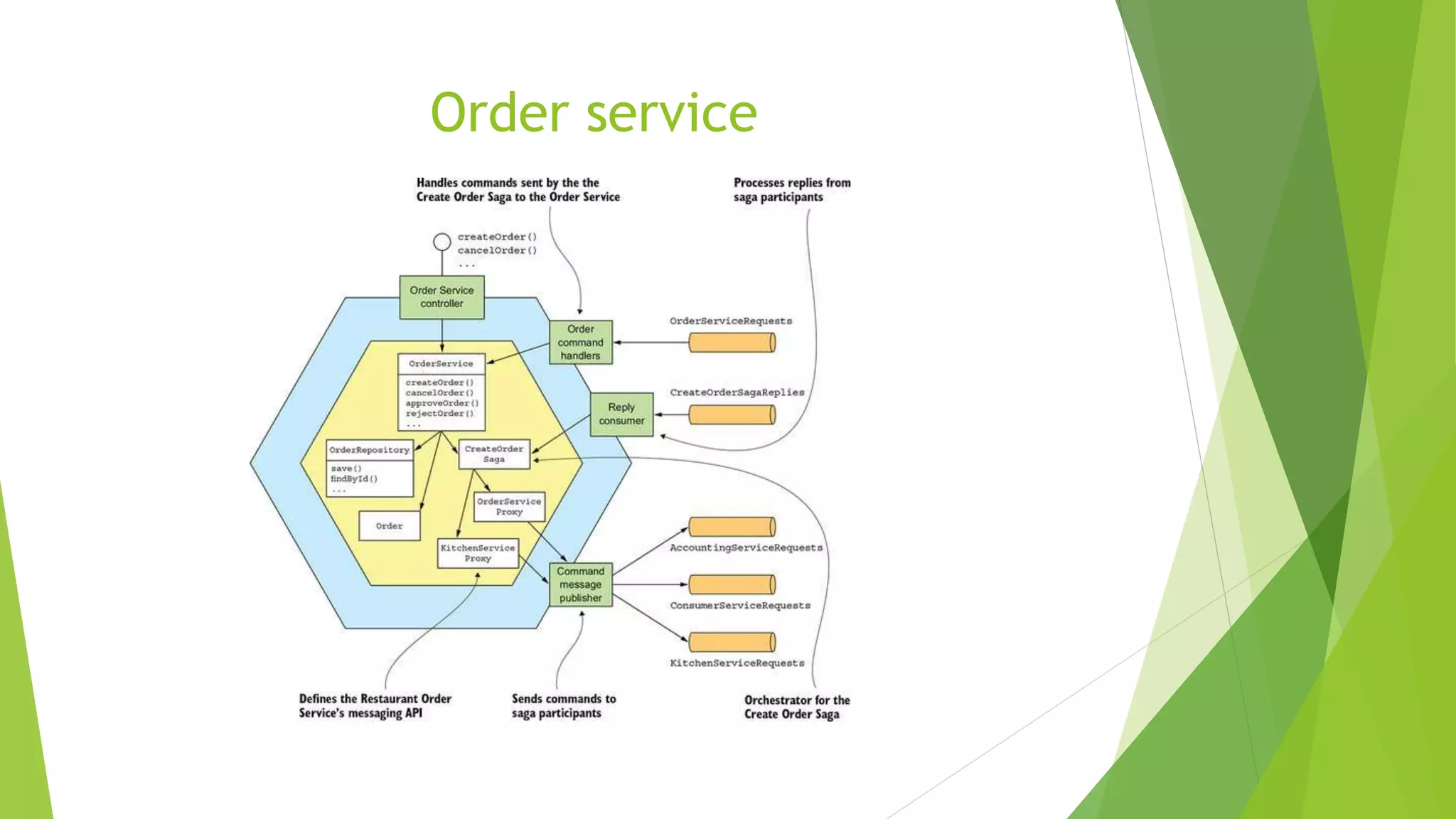
The document discusses several concepts related to distributed data management including ACID properties, monitor object pattern, and sagas. The monitor object pattern describes how synchronized methods are used to control access to shared resources. Sagas are long-running transactions that coordinate multiple services through message passing. There are two types of sagas: choreography-based where the sequence is embedded in the message flow, and orchestration-based where a central process coordinates the steps. Issues like lost updates and dirty reads can occur without transactional isolation, and various countermeasures are proposed to handle the lack of isolation in a saga.