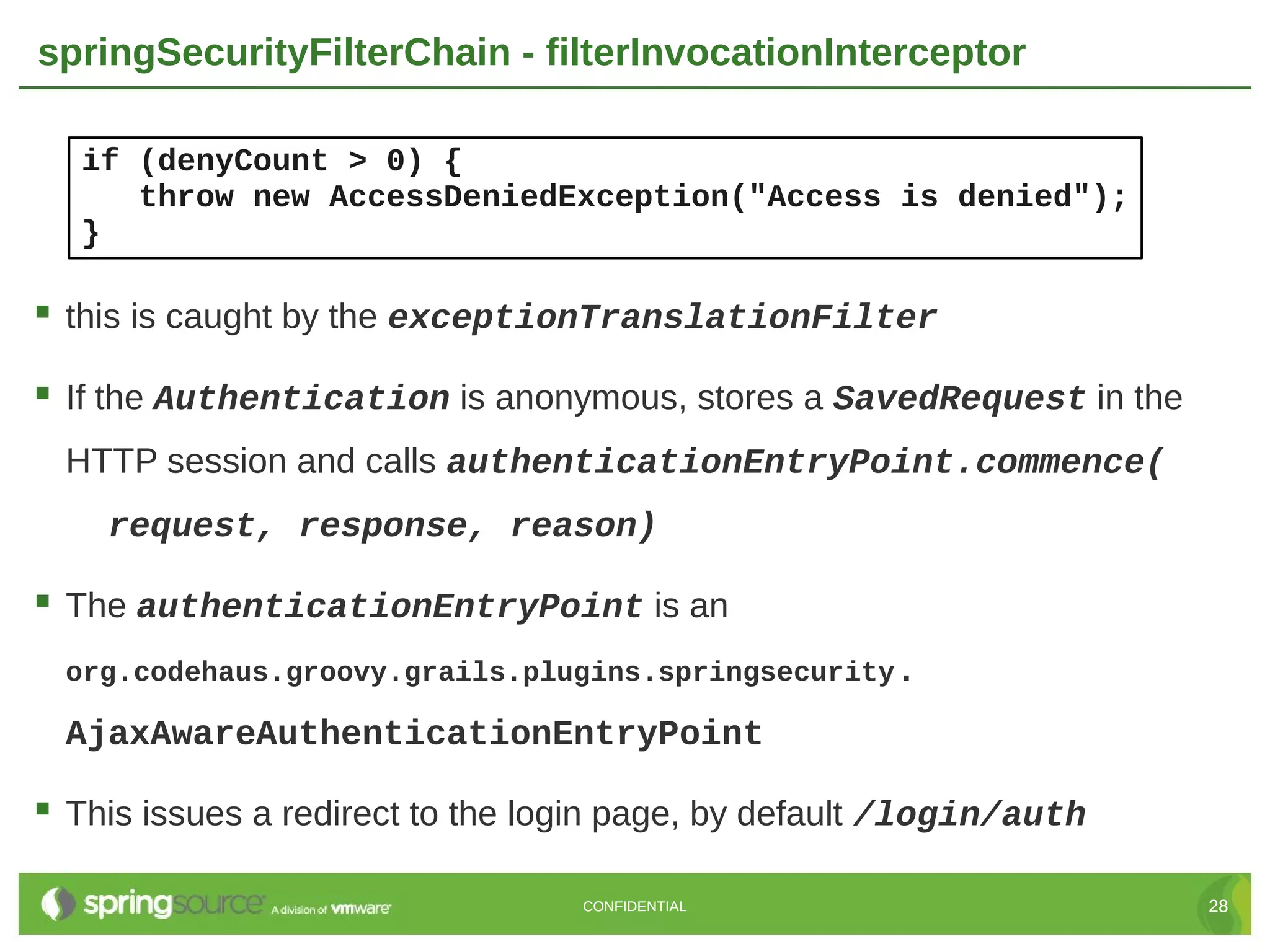
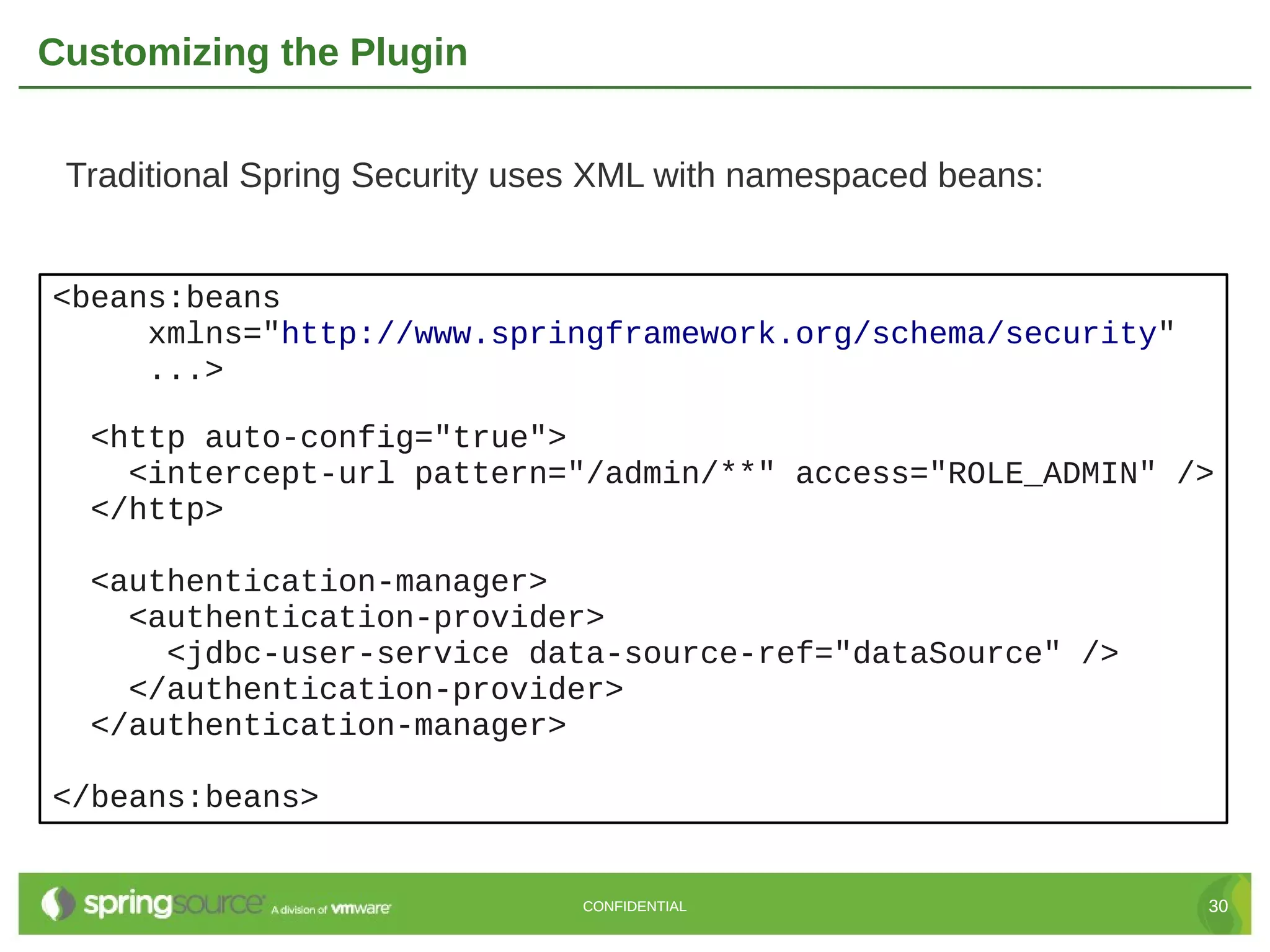
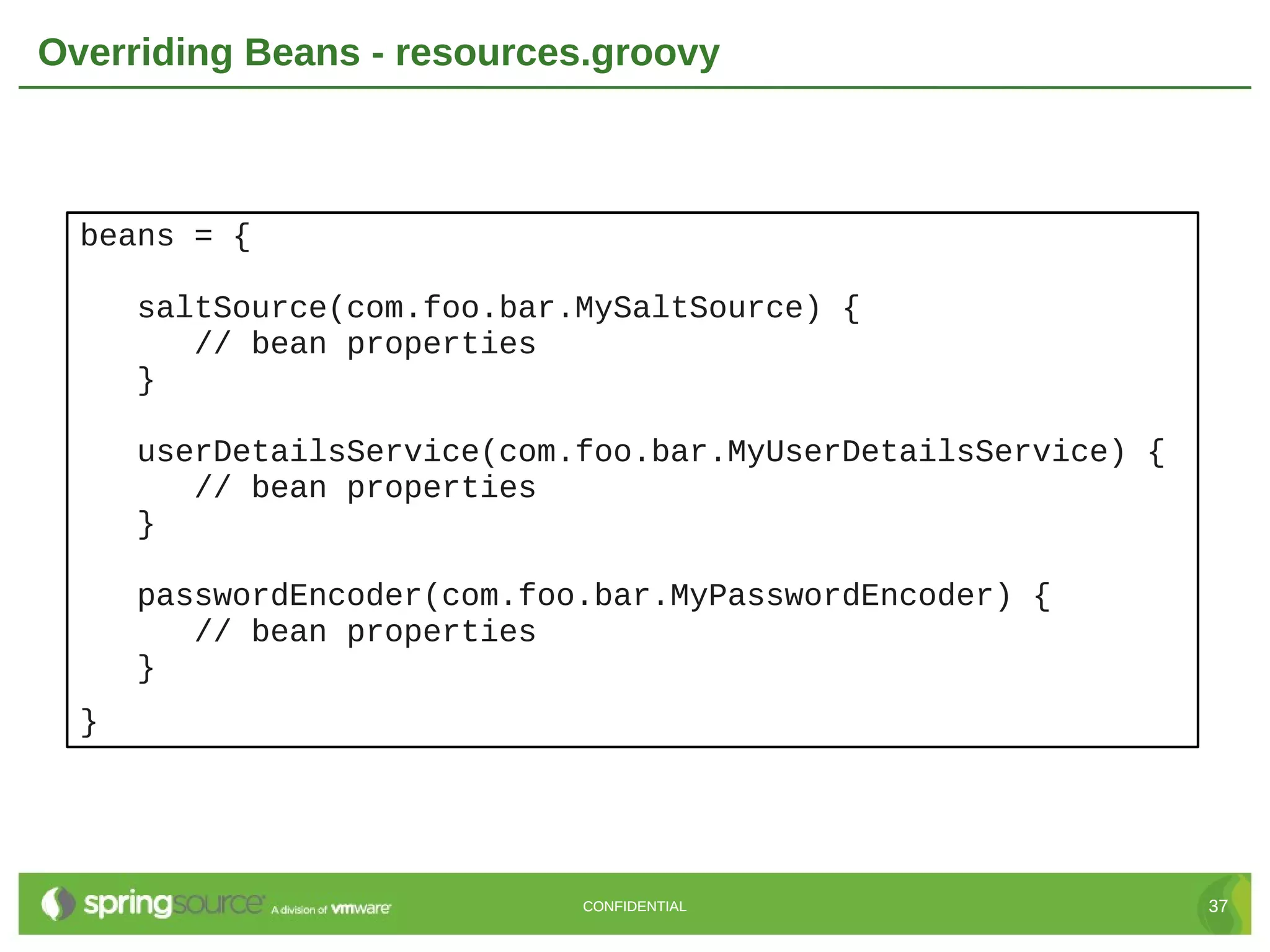
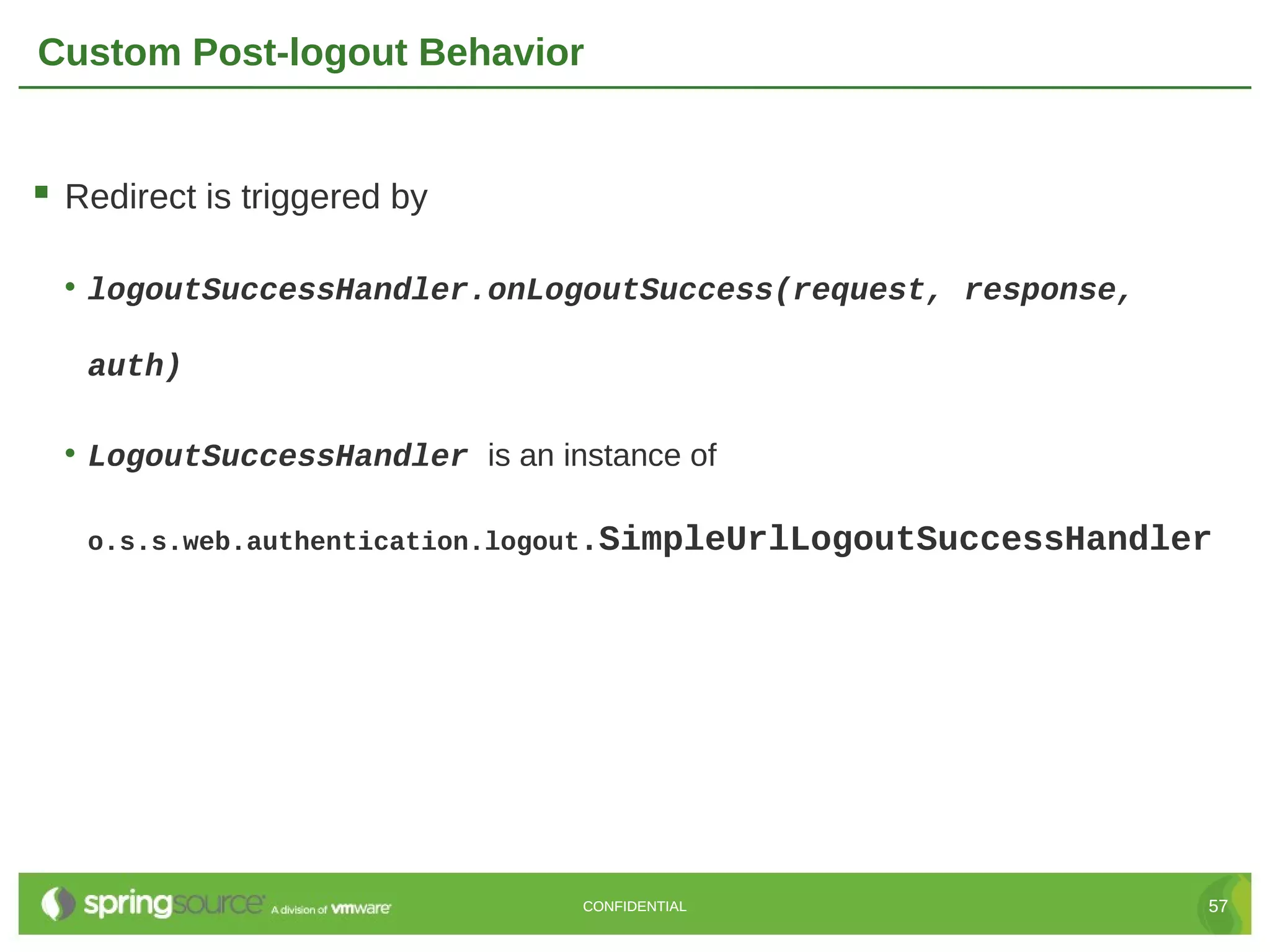
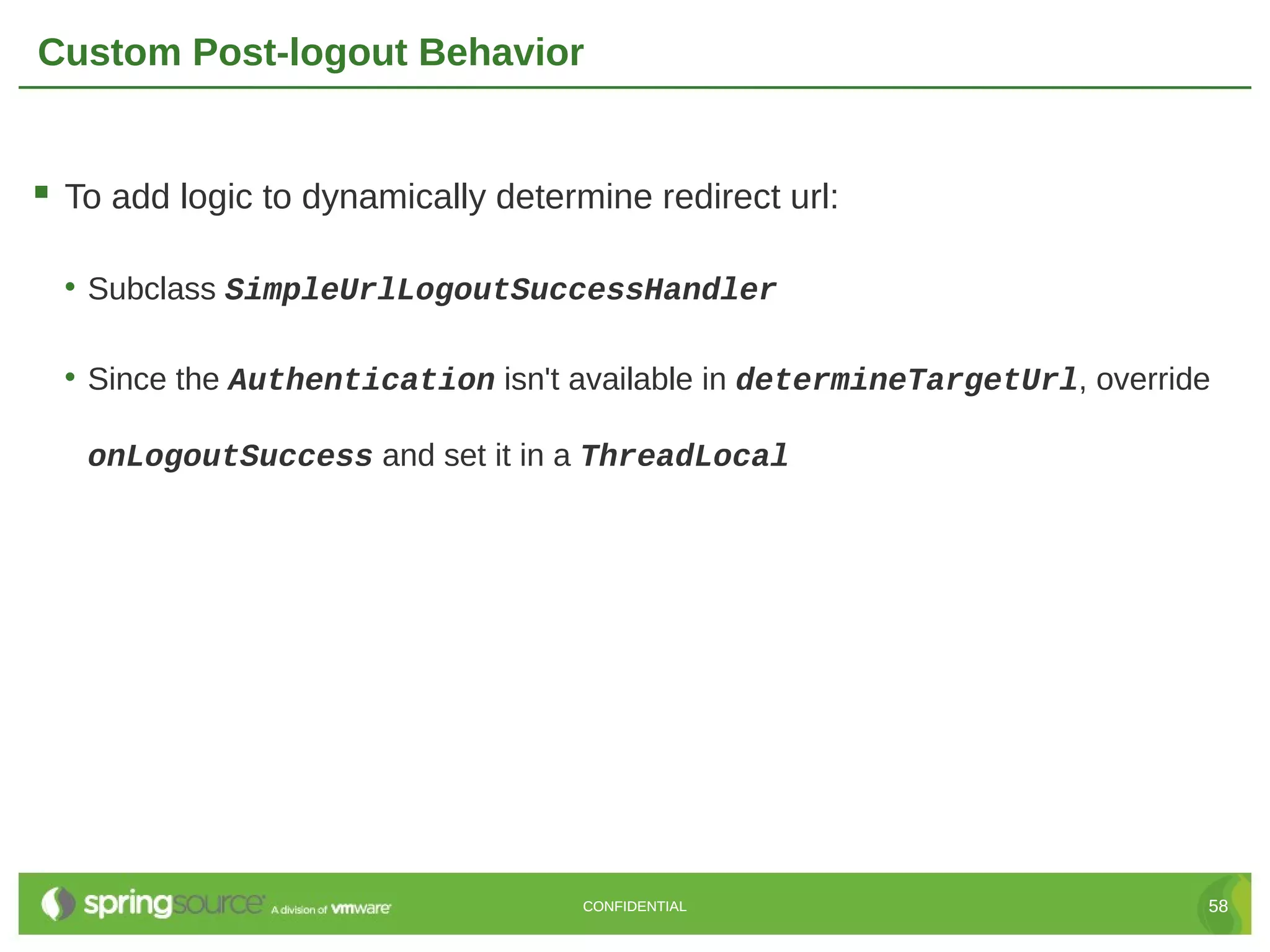
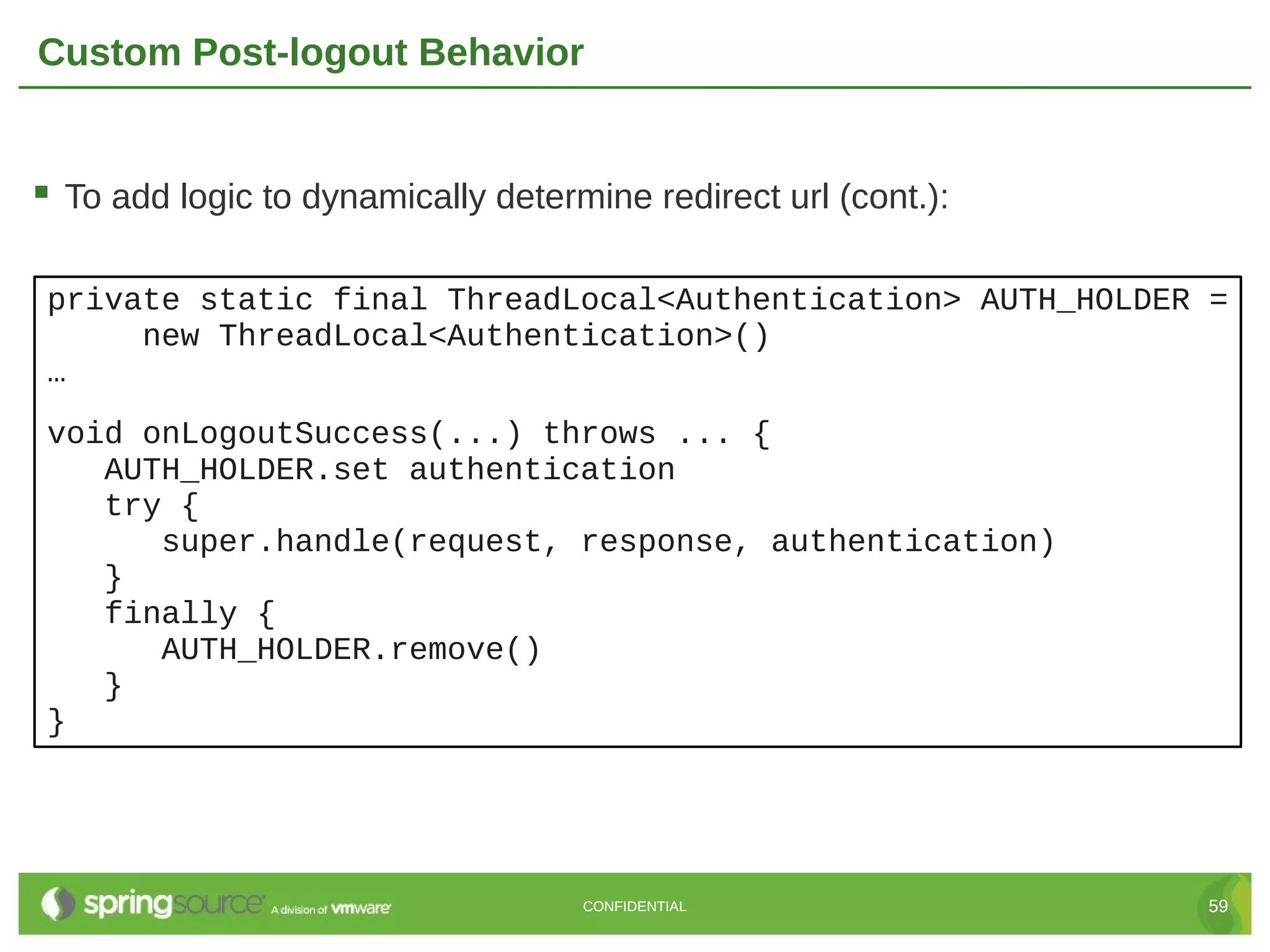
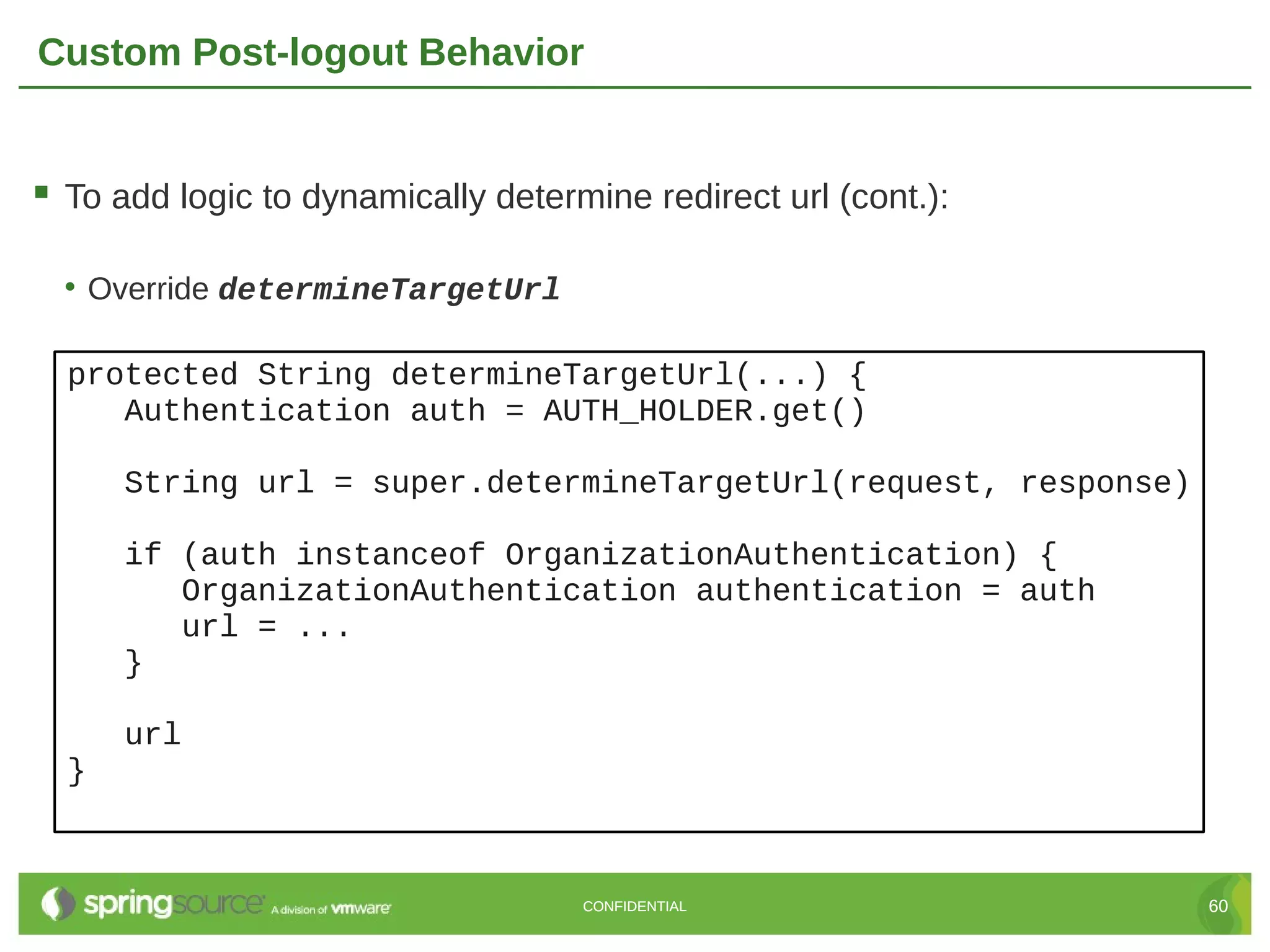
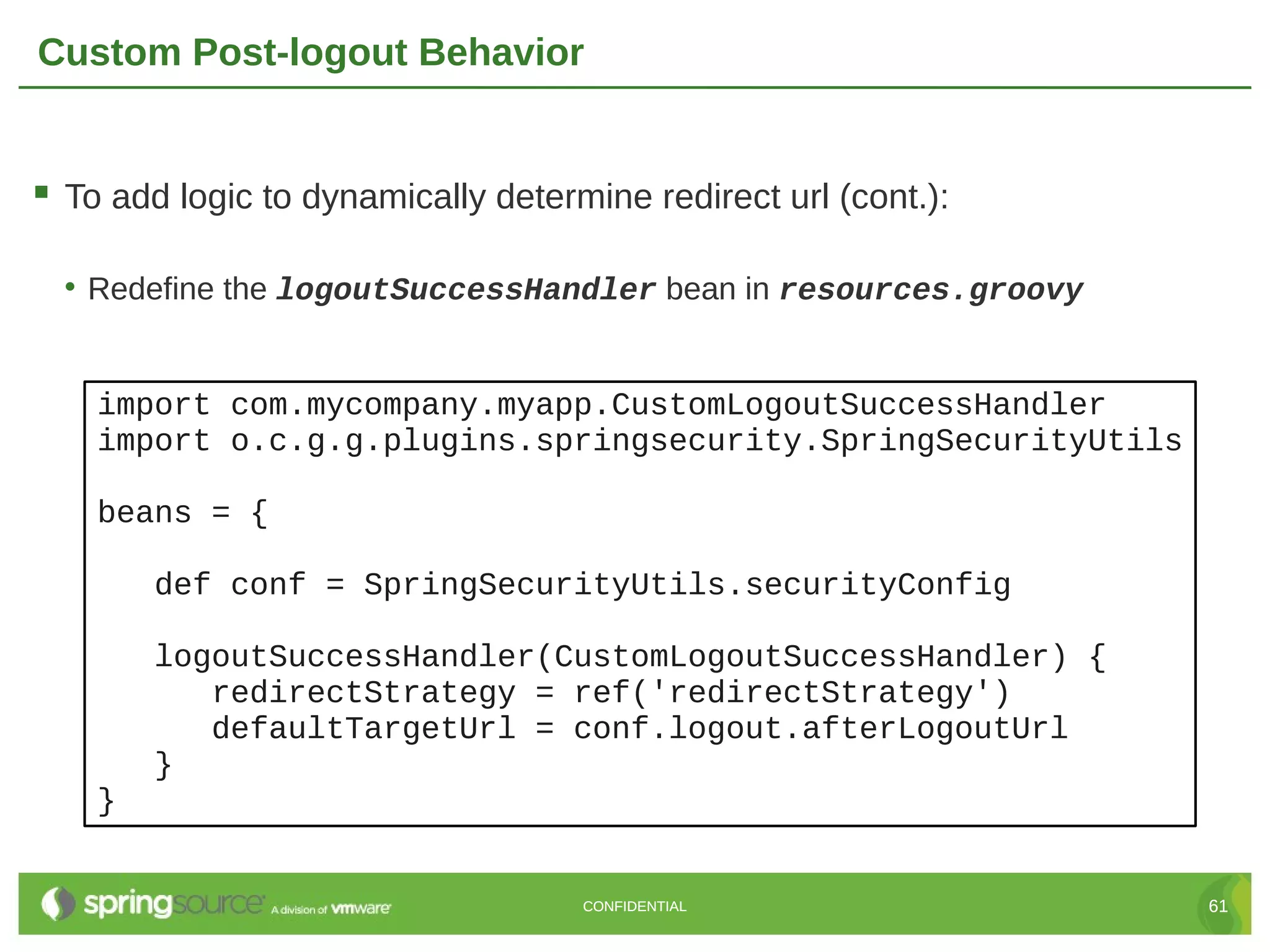
Here are the key steps to create a custom UserDetailsService in Grails Spring Security: 1. Create a class that implements the Spring Security UserDetailsService interface. 2. Override the loadUserByUsername() method to retrieve the user details (usually from the database) based on the username. 3. Return a UserDetails object (like GrailsUser) containing the user's credentials and authorities. 4. Register the custom UserDetailsService bean in resources.groovy, overriding the default. 5. The authentication manager will now use the custom service to retrieve user details during authentication. This allows full customization of how users are loaded from the data store for authentication. The custom service can





![springSecurityFilterChain - filterInvocationInterceptor Common built-in expressions Expression Description hasRole([role]) Returns true if the current principal has the specified role. hasAnyRole([role1,role2]) Returns true if the current principal has any of the supplied roles (given as a comma-separated list of strings) principal Allows direct access to the principal object representing the current user authentication Allows direct access to the current Authentication object obtained from the SecurityContext permitAll Always evaluates to true denyAll Always evaluates to false isAnonymous() Returns true if the current principal is an anonymous user isRememberMe() Returns true if the current principal is a remember-me user isAuthenticated() Returns true if the user is not anonymous isFullyAuthenticated() Returns true if the user is not an anonymous or a remember-me user CONFIDENTIAL 27](https://image.slidesharecdn.com/hackingthegrailsspringsecurityplugins-120608094126-phpapp02/75/Hacking-the-Grails-Spring-Security-Plugins-27-2048.jpg)