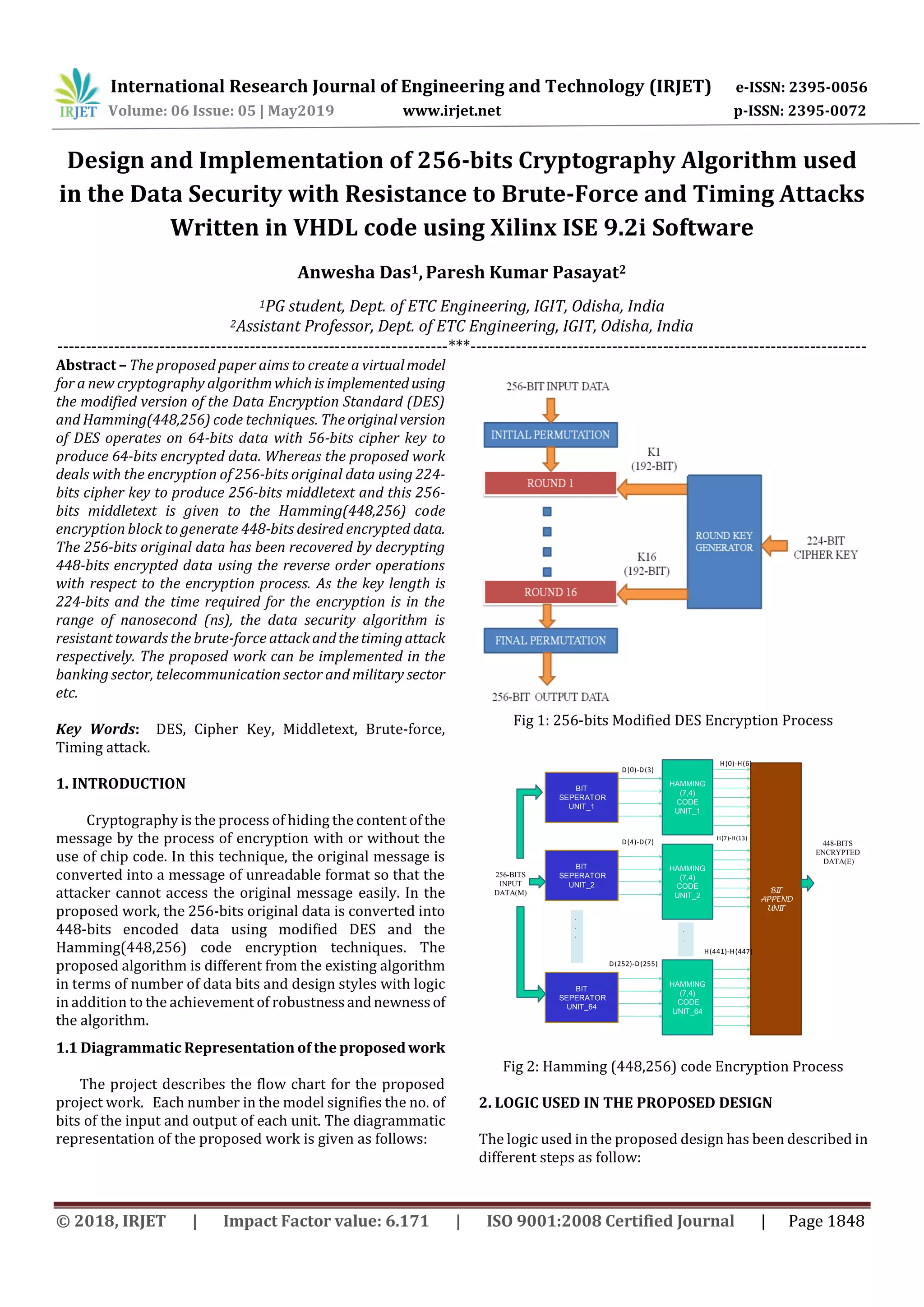
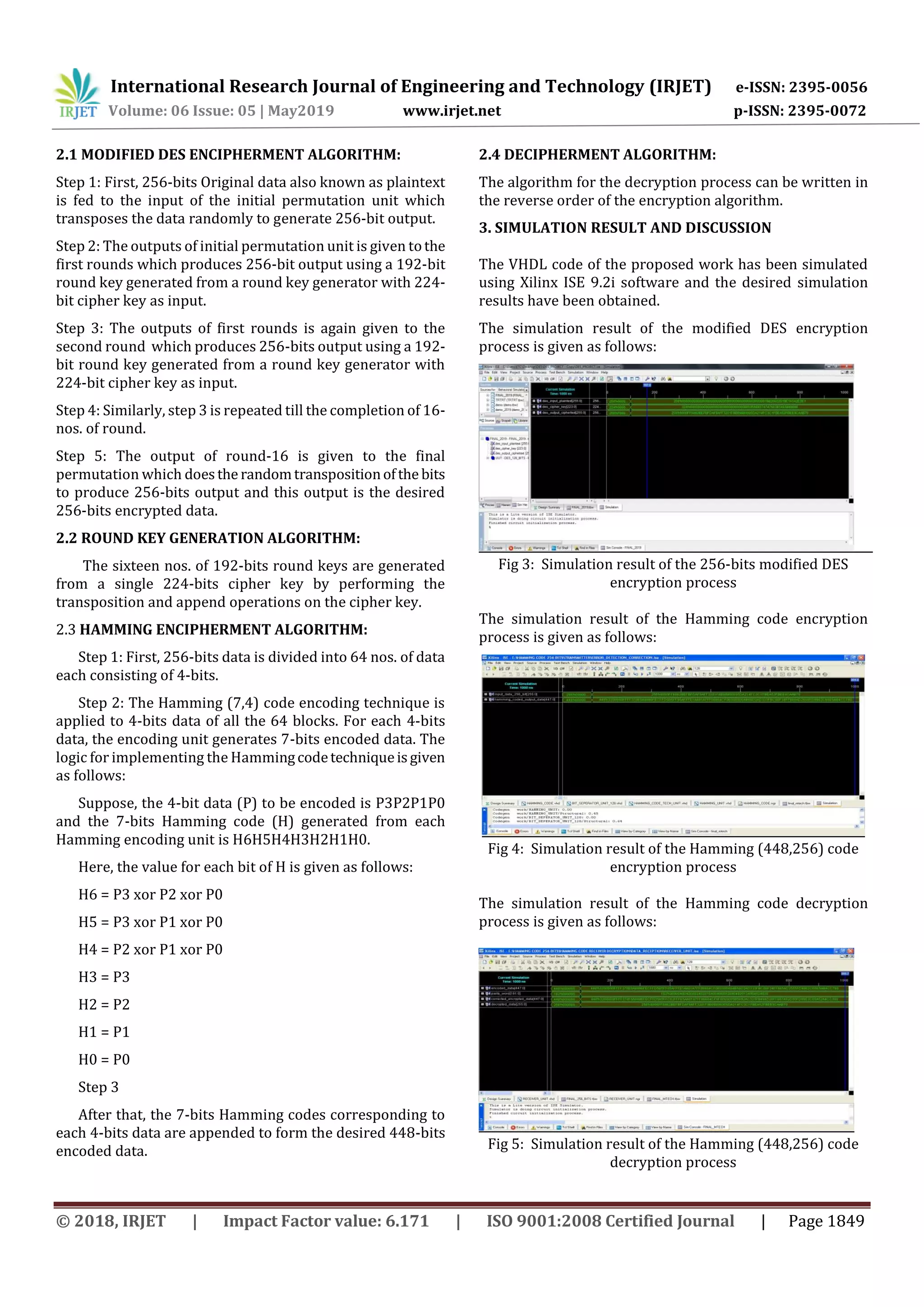
The document describes a proposed 256-bit cryptography algorithm implemented in VHDL that is resistant to brute-force and timing attacks. The algorithm uses a modified version of the Data Encryption Standard (DES) to encrypt 256-bit plaintext into 256-bit ciphertext using a 224-bit cipher key. It then applies a Hamming(448,256) error correcting code to the ciphertext to generate the final 448-bit encrypted data. Simulation results show the encryption and decryption processes encrypt the plaintext into ciphertext and recover the original plaintext, with an encryption time of 19.231 nanoseconds, making the algorithm resistant to brute-force and timing attacks.
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056 Volume: 06 Issue: 05 | May2019 www.irjet.net p-ISSN: 2395-0072 © 2018, IRJET | Impact Factor value: 6.171 | ISO 9001:2008 Certified Journal | Page 1850 The simulation result of the modified DES decryption process is given as follows: Fig 6: Simulation result of the 256-bits modified DES decryption process 4. CONCLUSION It is concluded that the proposedwork isbestsuitedin the field of data security to provide protection to the 256-bits original data from unauthorized access by the attackers available in the network. It is resistant to the brute-force attack, timing attack which makes the algorithm more robust. The VHDL code of the proposed design is compiled and simulated using Xilinx ISE 9.2i software. The maximum combinational path delay required to convert 256-bits plaintext into 448-bits ciphertext is 19.231ns. REFERENCES [1] Dr. Sandeep Tayal, Dr. Nipin Gupta, Dr. Pankaj Gupta, Deepak Goyal, Monika Goyal, “A Review paper on Network Security and Cryptography”, Advances in Computational Sciences and Technology, Volume 10, Number 5,pp. 763- 770,2017. [2] J. G. Pandey,Aanchal Gurawa, Heena Nehra,A. Karmakar, “An efficient VLSI architecture for data encryption standard and its FPGA implementation”,VLSISATA,IEEEInternational Conference,pp.1-5,2016. [3] W.Stallings,“Cryptography and Network Security”, 2nd Edition, Prentice Hall. [4] Douglas L. Perry. “VHDL Programming by Examples”, TMH. [5] Soufiane Oukili,Seddik Bri,”FPGAimplementationofData Encryption Standard using time variable permutations”, International Conference on Microelectronics (ICM),IEEE,pp.126-129,2015. [6] Ramadhan J. Mstafa; Khaled M. Elleithy, “A highly secure video steganography using Hamming code (7, 4)”, Systems, Applications and Technology Conference (LISAT), IEEE Conference,pp.1-6,2014. [7] Ravikumar M.Raypure, Prof. Vinay Keswani, “Implementation For Data Hiding Using Visual Cryptography”, IRJET, Volume: 04, Issue: 07, 2017. .](https://image.slidesharecdn.com/irjet-v6i5364-190909112540/75/IRJET-Design-and-Implementation-of-256-Bits-Cryptography-Algorithm-used-in-the-Data-Security-with-Resistance-to-Brute-Force-and-Timing-Attacks-Written-in-VHDL-Code-using-Xilinx-ISE-9-2i-Software-3-2048.jpg)